Smali+: An Operational Semantics for Low-Level Code Generated from Reverse Engineering Android Applications
Abstract
:1. Introduction
2. Related Work
3. Preliminaries
3.1. Registers
3.2. Method Invocation
3.3. Types in Smali
4. Operational Semantics for a Single-Threaded Application
4.1. Notations
- to designate a stack, where A is the top-most value of the stack, B is the underlying element and C is the remaining portion of the stack. An empty stack is presented by .
- ⊥ to denote any undefined value.
- is domain of a function f. The notation expresses the domain where the value of a functionf is updated to x.
- expresses the function f where value x maps to y so .
4.2. Syntax
4.3. Semantics
5. Operational Semantics for a Multi-Threaded Program
5.1. Syntax
5.2. Semantics
- Each thread in the program has a call stack for methods being invoked, their arguments and local variables, with the same syntax used in Table 3.
- is a set of pending threads. Each thread is presented by its call stack for method invoked information, plus a special register holding the thread reference. Threads in this set are in a “runnable” state (i.e., waiting to be selected by the scheduler).
- H and S are dynamic and static heaps which are shared between all threads in the program and have the same semantics domain used for the single-threaded program in Table 3.
- -
- initialized to an undefined value, which means that initially the object is in a free state and could be acquired by a given thread.
- -
- , an empty set of blocked threads, which means that initially there is no thread waiting for the monitor to be released.
- -
- , an empty set of waiting to be notified threads.
- -
- .
- -
- , an empty set of join threads, which means that initially there is no thread waiting to join the current thread.
- -
- .
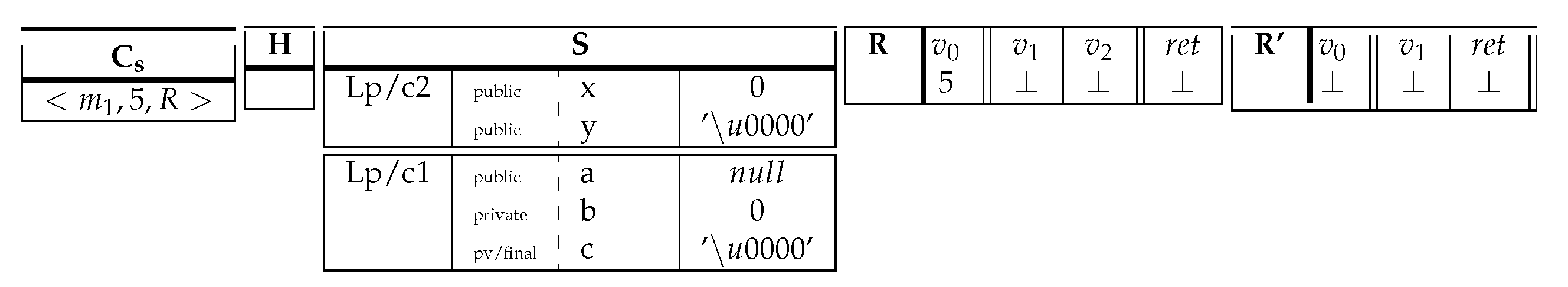
6. Practical Aspects
 |
 |
 |
 |
 |
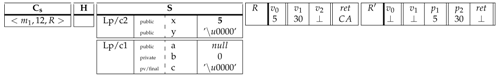 |
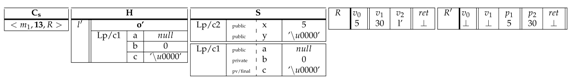 |
 |
7. Discussion
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- IDC Corporation. Smartphone Market Share. Available online: https://www.idc.com/promo/smartphone-market-share/os (accessed on 19 February 2020).
- Zhou, Y.; Jiang, X. Dissecting Android Malware: Characterization and Evolution. In Proceedings of the 2012 IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 20–23 May 2012. [Google Scholar] [CrossRef] [Green Version]
- Sergiu, G. Anubis Android Trojan Spotted with Almost Functional Ransomware Module. Available online: https://www.bleepingcomputer.com/news/security/anubis-android-trojan-spotted-with-almost-functional-ransomware-module/ (accessed on 20 February 2020).
- Barrett, L. SMS-Sending Trojan Targets Android Smartphones. Available online: https://www.esecurityplanet.com/trends/article.php/3898041/SMSSending-Trojan-Targets-Android-Smartphones.htm/ (accessed on 2 January 2020).
- Collier, N. New Android Trojan Malware Discovered in Google Play. Available online: https://blog.malwarebytes.com/cybercrime/2017/11/new-trojan-malware-discovered-google-play// (accessed on 2 January 2020).
- F-Secure. Trojan:Android/GGTracker. Available online: https://www.f-secure.com/v-descs/trojan_android_ggtracker.shtml (accessed on 2 January 2020).
- Arzt, S.; Rasthofer, S.; Fritz, C.; Bodden, E.; Bartel, A.; Klein, J.; Le Traon, Y.; Octeau, D.; McDaniel, P. FlowDroid: Precise Context, Flow, Field, Object-sensitive and Lifecycle-aware Taint Analysis for Android Apps. SIGPLAN Not. 2014, 49, 259–269. [Google Scholar] [CrossRef]
- Felt, A.P.; Chin, E.; Hanna, S.; Song, D.; Wagner, D. Android Permissions Demystified. In Proceedings of the 18th ACM Conference on Computer and Communications Security, New York, NY, USA, October 2011. [Google Scholar] [CrossRef] [Green Version]
- Davis, B.; Sanders, B.; Khodaverdian, A.; Chen, H. I-arm-droid: A rewriting framework for in-app reference monitors for android applications. In Proceedings of the Mobile Security Technologies 2012, San Francisco, CA, USA, May 2012; Available online: http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.298.7191&rep=rep1&type=pdf (accessed on 2 January 2020).
- Xu, R.; Saïdi, H.; Anderson, R.J. Aurasium: Practical Policy Enforcement for Android Applications. In Proceedings of the 21th USENIX Security Symposium, Bellevue, WA, USA, 8–10 August 2012; pp. 539–552. [Google Scholar]
- Jeon, J.; Micinski, K.K. SymDroid: Symbolic Execution for Dalvik; CS-TR-5022; University of Maryland: College Park, MD, USA, July 2012; Available online: http://www.cs.tufts.edu/~jfoster/papers/symdroid.pdf (accessed on 4 January 2020).
- Apktool. A Tool for Reverse Engineering Android Apk Files. Available online: https://ibotpeaches.github.io/Apktool/ (accessed on 19 February 2019).
- Na, G.; Lim, J.; Kim, K.; Yi, J.H. Comparative Analysis of Mobile App Reverse Engineering Methods on Dalvik and ART. J. Internet Serv. Inf. Secur. 2016, 6, 27–39. [Google Scholar]
- El-Zawawy, M.A. An Operational Semantics for Android Applications. In Proceedings of the Computational Science and Its Applications - ICCSA 2016 - 16th International Conference, Beijing, China, 4–7 July 2016; pp. 100–114. [Google Scholar]
- Payet, E.; Spoto, F. An Operational Semantics for Android Activities. Available online: https://doi.org/10.1145/2543728.2543738 (accessed on 5 December 2019).
- Wognsen, E.; Karlsen, S. Static Analysis of Dalvik Bytecode and Reflection in Android. Master’s Thesis, Department of Computer Science Aalborg University, Aalborg, Denmark, 6 June 2012. Available online: https://projekter.aau.dk/projekter/files/63640573/rapport.pdf (accessed on 10 December 2019).
- Wognsen, E.; Søndberg Karlsen, H.; Chr. Olesen, M.; Hansen, R. Formalisation and analysis of Dalvik bytecode. Sci. Comput. Program. 2014, 92, 25–55. [Google Scholar] [CrossRef]
- Cousot, P.; Cousot, R. Abstract Interpretation: A Unified Lattice Model for Static Analysis of Programs by Construction or Approximation of Fixpoints. In Proceedings of the 4th ACM SIGACT-SIGPLAN Symposium on Principles of Programming Languages, New York, NY, USA, January 1977; pp. 238–252. [Google Scholar] [CrossRef] [Green Version]
- Payet, E.; Spoto, F. Static Analysis of Android Programs. Inf. Softw. Technol. 2012, 54, 1192–1201. [Google Scholar] [CrossRef] [Green Version]
- Gunadi, H. Formal Certification of Non-interferent Android Bytecode (DEX Bytecode). In Proceedings of the 2015 20th International Conference on Engineering of Complex Computer Systems ICECCS, Gold Coast, Australia, 9–12 December 2015; pp. 202–205. [Google Scholar]
- Gunadi, H.; Tiu, A.; Gore, R. Formal Certification of Android Bytecode. arXiv 2015, arXiv:1504.01842v5. Available online: https://arxiv.org/abs/1504.01842 (accessed on 19 February 2020).
- Barthe, G.; Pichardie, D.; Rezk, T. A certified lightweight non-interference Java bytecode verifier. Math. Struct. Comput. Sci. 2013, 23, 1032–1081. [Google Scholar] [CrossRef] [Green Version]
- Maiya, P.; Kanade, A.; Majumdar, R. Race detection for Android applications. In Proceedings of the ACM SIGPLAN Conference on Programming Language Design and Implementation, PLDI ’14, Edinburgh, UK, 9–11 June 2014; pp. 316–325. [Google Scholar]
- Kanade, A. Chapter Seven - Event-Based Concurrency: Applications, Abstractions, and Analyses. Adv. Comput. 2019, 112, 379–412. [Google Scholar]
- Bouajjani, A.; Emmi, M.; Enea, C.; Ozkan, B.K.; Tasiran, S. Verifying Robustness of Event-Driven Asynchronous Programs Against Concurrency. In Proceedings of the Programming Languages and Systems 26th European Symposium on Programming, ESOP 2017, Held as Part of the European Joint Conferences on Theory and Practice of Software, Uppsala, Sweden, 22–29 April 2017; pp. 170–200. [Google Scholar]
- Calzavara, S.; Grishchenko, I.; Koutsos, A.; Maffei, M. A Sound Flow-Sensitive Heap Abstraction for the Static Analysis of Android Applications. arXiv 2017, arXiv:1705.10482v2. Available online: https://arxiv.org/pdf/1705.10482.pdf (accessed on 15 December 2019).
- Calzavara, S.; Grishchenko, I.; Maffei, M. HornDroid: Practical and Sound Static Analysis of Android Applications by SMT Solving. In Proceedings of the 2016 IEEE European Symposium on Security and Privacy (EuroSP), aarbrucken, Germany, 21–24 March 2016. [Google Scholar] [CrossRef] [Green Version]
- Chaudhuri, A. Language-based security on Android. In Proceedings of the 2009 Workshop on Programming Languages and Analysis for Security, Dublin, Ireland, 15–21 June 2009. [Google Scholar] [CrossRef] [Green Version]
- Chen, T.; He, J.; Song, F.; Wang, G.; Wu, Z.; Yan, J. Android Stack Machine. Computer Aided Verification. In Proceedings of the 30th International Conference, CAV 2018, Held as Part of the Federated Logic Conference, Oxford, UK, 14–17 July 2018; pp. 487–504. [Google Scholar] [CrossRef] [Green Version]
- He, J.; Chen, T.; Wang, P.; Wu, Z.; Yan, J. Android Multitasking Mechanism: Formal Semantics and Static Analysis of Apps. In Proceedings of the Programming Languages and Systems - 17th Asian Symposium, Nusa Dua Bali, Indonesia, 1–4 December 2019; pp. 291–312. [Google Scholar] [CrossRef]
- Bagheri, H.; Kang, E.; Malek, S.; Jackson, D. Detection of Design Flaws in the Android Permission Protocol Through Bounded Verification. In Proceedings of the FM 2015: Formal Methods - 20th International Symposium, Oslo, Norway, 24–26 June 2015; pp. 73–89. [Google Scholar] [CrossRef] [Green Version]
- Ren, L.; Chang, R.; Yin, Q.; Man, Y. A Formal Android Permission Model Based on the B Method. In Proceedings of the Security, Privacy, and Anonymity in Computation, Communication, and Storage 10th International Conference, Guangzhou, China, 12–15 December 2017; pp. 381–394. [Google Scholar] [CrossRef]
- Khan, W.; Kamran, M.; Ahmad, A.; Khan, F.A.; Derhab, A. Formal Analysis of Language-Based Android Security Using Theorem Proving Approach. IEEE Access 2019, 7, 16550–16560. [Google Scholar] [CrossRef]
- Qin, J.; Zhang, H.; Wang, S.; Geng, Z.; Chen, T. Acteve++: An Improved Android Application Automatic Tester Based on Acteve. IEEE Access 2019, 7, 31358–31363. [Google Scholar] [CrossRef]
- Anand, S.; Naik, M.; Harrold, M.J.; Yang, H. Automated concolic testing of smartphone apps. In Proceedings of the 20th ACM SIGSOFT Symposium on the Foundations of Software Engineering (FSE-20), Cary, NC, USA, 11–16 November 2012; p. 59. [Google Scholar] [CrossRef] [Green Version]
- Nisi, D.; Bianchi, A.; Fratantonio, Y. Exploring Syscall-Based Semantics Reconstruction of Android Applications. In Proceedings of the 22nd International Symposium on Research in Attacks, Intrusions and Defenses, Beijing, China, 23–25 September 2019; pp. 517–531. [Google Scholar]
- Chin, E.; Felt, A.P.; Greenwood, K.; Wagner, D. Analyzing Inter-application Communication in Android. In Proceedings of the 9th International Conference on Mobile Systems, Applications, and Services, New York, NY, USA, June 2011; pp. 239–252. [Google Scholar] [CrossRef] [Green Version]
- Drake, J.J.; Lanier, Z.; Mulliner, C.; Fora, P.O.; Ridley, S.A.; Wicherski, G. Android Hacker’s Handbook; Wiley Publishing: Hoboken, NJ, USA, 2014. [Google Scholar]
- Android Open Source Project (AOSP). Dalvik Bytecode. Available online: https://source.android.com/devices/tech/dalvik/dalvik-bytecode (accessed on 30 January 2020).
- Oracle Corporation. Java Documentation on Thread. Available online: https://docs.oracle.com/javase/8/docs/api/java/lang/Thread.html (accessed on 2 October 2019).
- Oracle Corporation. Java Documentation on Object. Available online: https://docs.oracle.com/javase/8/docs/api/java/lang/Object.html (accessed on 2 October 2019).
- Göransson, A. Efficient Android Threading: Asynchronous Processing Techniques for Android Applications, 1st ed.; O’Reilly Media: Sebastopol, CA, USA, 2014; ISBN 978-1449364137. [Google Scholar]
- Davi, L.; Dmitrienko, A.; Sadeghi, A.; Winandy, M. Privilege Escalation Attacks on Android. In Proceedings of the Information Security 13th International Conference, Boca Raton, FL, USA, 25–28 October 2010; pp. 346–360. [Google Scholar]
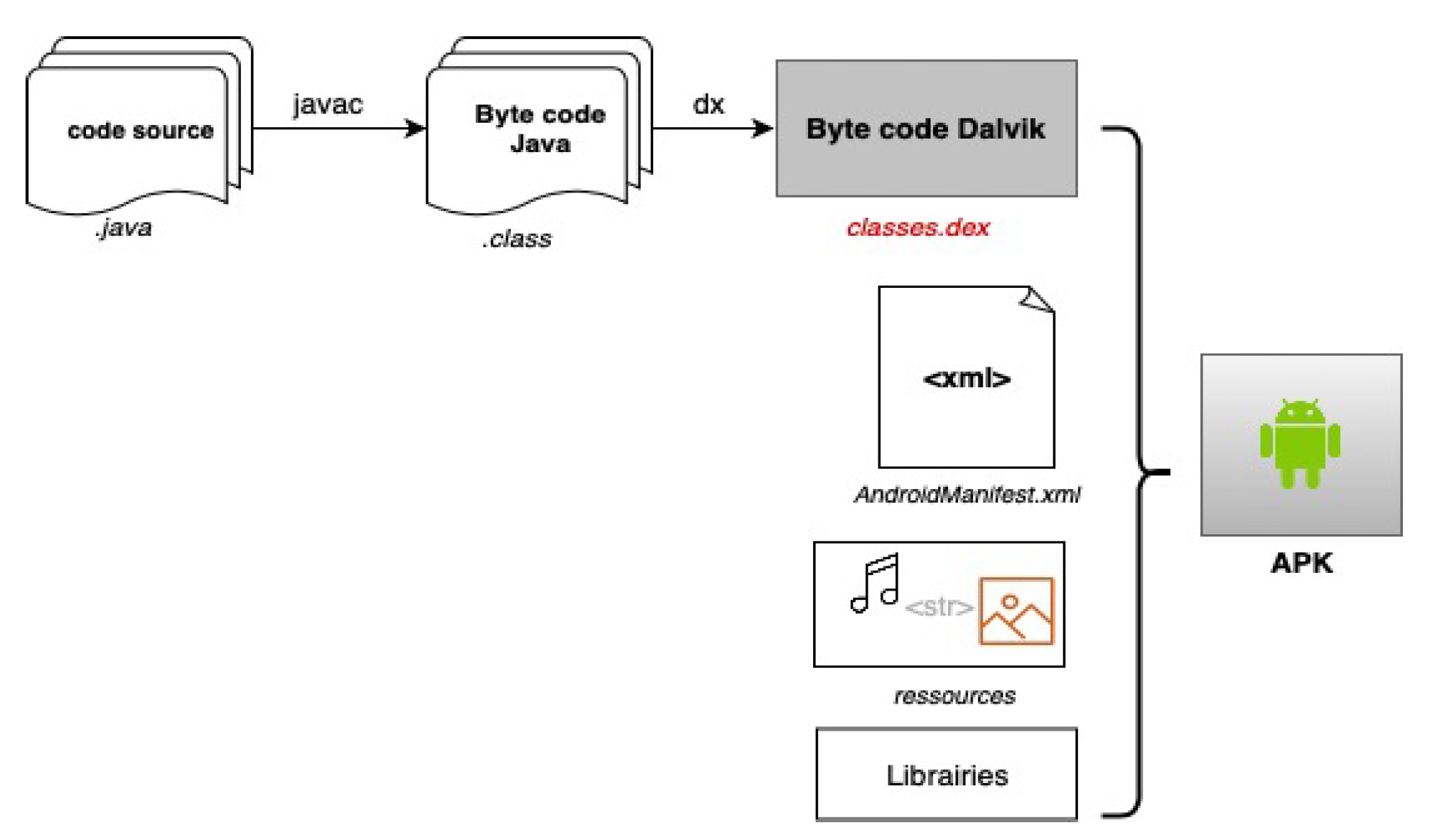

| Primitive Types | |
|---|---|
| B | byte |
| C | char |
| F | float |
| I | int |
| J | long |
| S | short |
| V | void |
| Z | boolean |
| Reference Types | |
| Lpackagename/Classname; | Object |
| Object or Primitives | Array |
| (Package) | |||
| (Class definition) | |||
| (Super class ) | |||
| (Interface definition) | |||
| (Super interface ) | |||
| (Field definition) | |||
| (Constant Field definition) | |||
| (Method definition) | |||
| (Method signature) | |||
| (Access flags) | |||
| (Labeled Instruction) | |||
| (Label) | i | ||
| (Instructions) | (unconditional jump) | ||
| (move from source to destination) | |||
| (binary operation) | |||
| (unary operation) | |||
| (conditional jump) | |||
| (object creation) | |||
| (static method invocation) | |||
| (instance method invocation) | |||
| (retrun from non-void method ) | |||
| (retrun from a void method ) | |||
| (Destination register) | (register name) | ||
| (instance field) | |||
| (static field) | |||
| (Source register) | (des or constant) | ||
| (Operators) | ⊕ | (binary operator) | |
| ⊙ | (unary operator) | ||
| ⧀ | (comparison operator) | ||
| (Program counter) | i | ||
| (Num. of loc. registers ) | |||
| (Local registers name) | v | ||
| (Parameter registers name) | |||
| (Constant) | (constant) | ||
| (Type) | |||
| (ReturnType) | |||
| (Names) | (class full name) | ||
| / | (interface full name) | ||
| (package, class, interface, field and method names) |
| (Local configuration) | ||
| (Call stack) | ||
| (Method frame) | ||
| (Registers array) | R | |
| (Registers names) | ||
| (Heap) | H | |
| (Object) | ||
| (Array) | ||
| (Static Heap) | S | |
| (Values) | ||
| (Local register) | v | |
| (Parameter register) | p | |
| (Return register) | ||
| (location) | l |
| int | 0 |
|---|---|
| long | |
| short | 0 |
| char | ’’ |
| byte | (byte) 0 |
| float | 0.0f |
| double | 0.0d |
| object | null |
| boolean(int) | false (0) |
| (start the thread in ) | |||
| (acquire the monitor for object in v) | |||
| (release the monitor for object in v) | |||
| (join the thread in ) | |||
| (release object’s monitor in and suspend current thread) | |||
| (notify one thread from those waiting on object’s monitor in ) | |||
| (notify all threads waiting on object’s monitor in ) |
| (Global configuration) | |||
| (Set of runnable threads) | |||
| (Object) | |||
| (A thread Object) | |||
| (Set of blocked threads) | |||
| (Set of waiting threads) | |||
| (Set of join threads) | |||
| (Acquiring field) | (field name) | ||
| (finished field) | (field name) | ||
| (Groups names) |
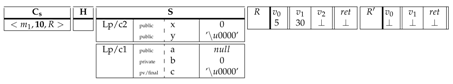
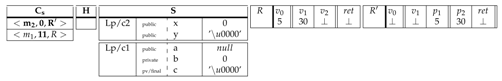
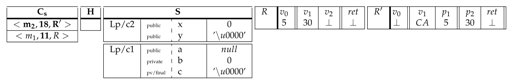
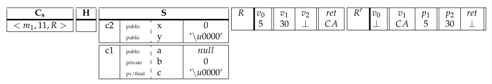
| .class public.super c1 { | .class public.super ⊥ { | ||
| .field publicx: int | .field public a: LJava/lang/String | ||
| .field publicy: char | .field publicb: int | ||
| .method public static()V .locals 3 { | .field private finalc: char | ||
| ... | .method public static(int,char)char .locals 2 { | ||
| 5 | move | ... | ... |
| 6 | goto 10 | ||
| ... | ... | ||
| 10 | |||
| 11 | move c2.x | ||
| 12 | new-instance Lp/c1 | ... | ... |
| 13 | move | 18 | return |
| ... | ... | } | |
| } |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ziadia, M.; Fattahi, J.; Mejri, M.; Pricop, E. Smali+: An Operational Semantics for Low-Level Code Generated from Reverse Engineering Android Applications. Information 2020, 11, 130. https://doi.org/10.3390/info11030130
Ziadia M, Fattahi J, Mejri M, Pricop E. Smali+: An Operational Semantics for Low-Level Code Generated from Reverse Engineering Android Applications. Information. 2020; 11(3):130. https://doi.org/10.3390/info11030130
Chicago/Turabian StyleZiadia, Marwa, Jaouhar Fattahi, Mohamed Mejri, and Emil Pricop. 2020. "Smali+: An Operational Semantics for Low-Level Code Generated from Reverse Engineering Android Applications" Information 11, no. 3: 130. https://doi.org/10.3390/info11030130
APA StyleZiadia, M., Fattahi, J., Mejri, M., & Pricop, E. (2020). Smali+: An Operational Semantics for Low-Level Code Generated from Reverse Engineering Android Applications. Information, 11(3), 130. https://doi.org/10.3390/info11030130







