An ECDSA Approach to Access Control in Knowledge Management Systems Using Blockchain
Abstract
1. Introduction
- ensuring an effective user authentication and verification method for knowledge workers in an organization, and therefore providing an efficient access control to knowledge resources;
- issuing roles and knowledge management to users, and access revocation to defaulting parties in the network; and
- designing an architecture that seeks to achieve security requirements such as adding, updating, sharing and providing information or knowledge in the organization by making use of the blockchain technology.
2. Related Works
3. Background
3.1. Blockchain
3.2. The Smart Contract
4. System Model and Implementation
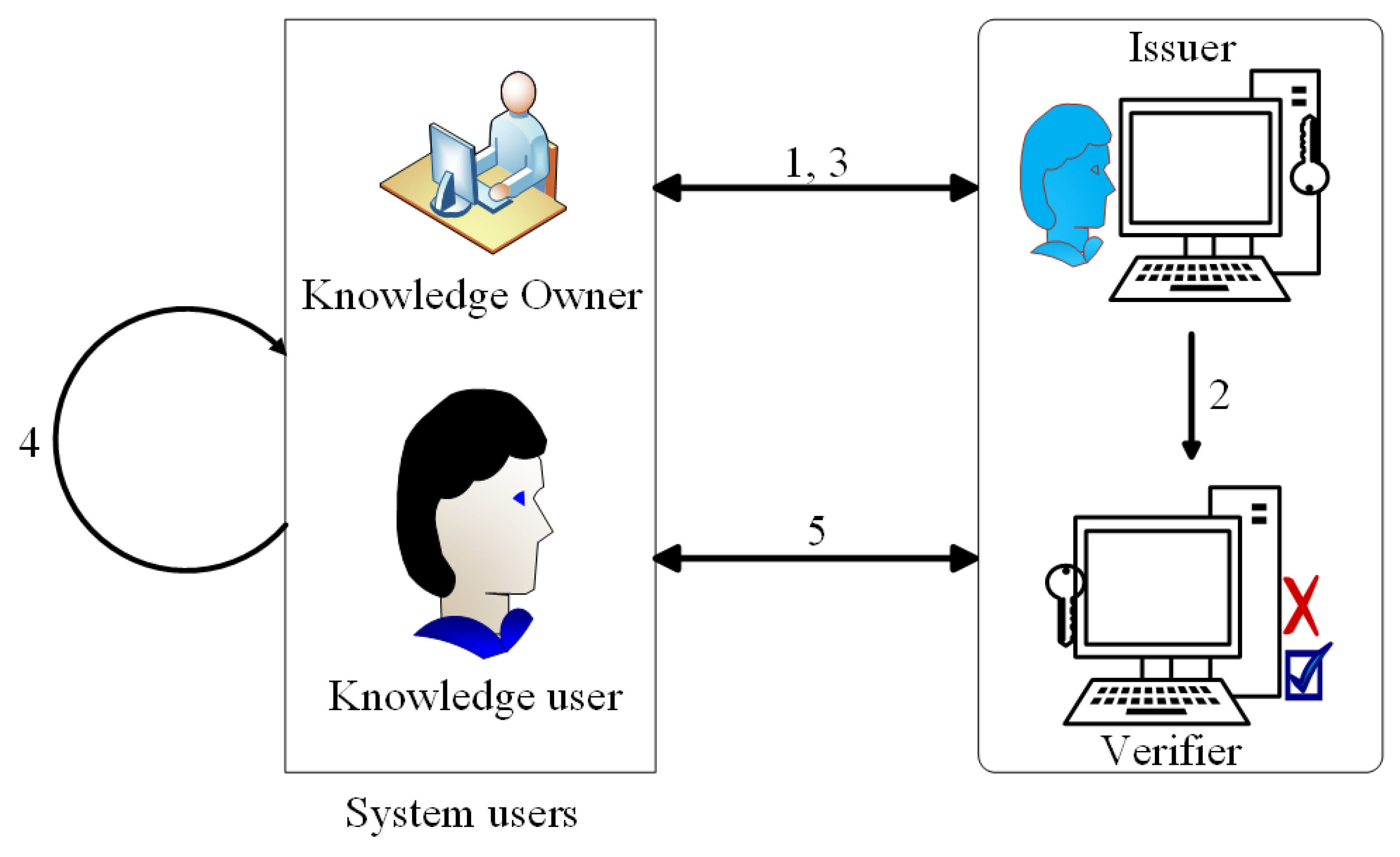
- User layer: The user layer comprises of the two major entities associated with the knowledge, the knowledge owner and the knowledge user. The knowledge owner uploads its knowledge onto the cloud repository and determines which user has access to which knowledge, and what privileges the user should enjoy. The knowledge user, on the other hand, requests for use of the knowledge, and, upon a successful verification, the request is granted.
- Knowledge Processing Unit: This unit consists of a key issuer, a verification unit, and a role assignment unit. The issuer is responsible for generating cryptographic keys, linked to the identities of the users, and are used for transactions on the network. Some typical transactions include knowledge requests, knowledge usage, etc. The verification unit, on the other hand, verifies all users on the network. Once the keys have been generated and given out to the users by the issuer, all users need to go through an authentication process before gaining access to the knowledge. With the help of the verification unit, an efficient access control is assured. The role assignment unit provides the rules of engagement of the system. It specifies what the roles of each entity are and the privileges each user gets to enjoy.
- Knowledge management center: This unit is the heartbeat of the system. It consists of a network processing node and a smart contract unit. The processing nodes are responsible for processing all requests on the network and managing all other processes on the blockchain. It works in tandem with the smart contract, which is responsible for generating policies on the knowledge. When requests are made, the processing nodes receive the requests from the knowledge processing center and act on them. After processing, it binds a contract to the result and the final output is given to the user.
- Blockchain: This is a growing list of all the knowledge records (knowledge blocks) that are cryptographically linked. In each block, there is a hash of the previous block, a timestamp, and a transaction. Once the processing nodes have completed their tasks, and with them collectively adhering to a protocol for internode communication and validation, the transactions are appended onto a block. Once recorded, the knowledge item cannot be altered without alteration of all the subsequent blocks, which requires all the nodes to reach a consensus.
- A user contacts the issuer for network membership registration. The parameters needed for registration will be given by the issuer, but, as in many networks, the basic parameters include a unique ID and keying parameters.
- The issuer generates a user membership key by fetching parameters from its key distribution center and sends the details to the verification unit.
- The keying parameters are given to the user.
- The user generates a private key to be used for all transactions by using the ECDSA protocol, which is given in detail in the sections that follow.
- The verifier and the user establish mutual authentication for key and/or user validity check. Details are obtained from the database. Upon a successful verification process, the user can now access knowledge items and perform actions on the knowledge items.
4.1. Setup Phase
4.2. Domain Parameter Generation and Validation
- We verify that q is an odd prime or a power of 2. (i.e., , ).
- We again verify that is a valid representation of .
- Verify that .
- Again, verify that has elements . These are integers in the interval if , and m-bit length bit strings, if .
- Verify that and accurately define the elliptic curve over (i.e., if if ).
- Verify that lies on the elliptic curve defined by and .
- Verify that is a prime number.
- Verify that and also .
- Verify that .
- Compute , and verify that .
- We then verify if .
- Verify that .
4.3. Key Pair Generation and Public Key Validation
- Verify that .
- Verify that has elements . These are integers in the interval if , and m-bit length bit strings, if .
- Check that lies on the elliptic curve characterized by and .
- Verify if .
4.4. Signature Generation and Verification
- Signature Generation
- (a)
- A random integer is selected, and it must lie in the interval .
- (b)
- Compute and convert to an integer .
- (c)
- Compute . Go to Step (a) if .
- (d)
- Compute , and compute SHA-1() and also covert this bit string to an integer .
- (e)
- Compute . Go to Step (a) if .
The signature of the user’s identity, is - Signature VerificationFor a successful verification process, the verifier obtains a copy of the user’s domain parameters , and the associated public key . The verifier then has to validate these parameters, by doing the following.
- (a)
- Verify that and s are integers in the interval .
- (b)
- Compute SHA-1() and convert to an integer .
- (c)
- Compute .
- (d)
- Compute and .
- (e)
- Compute .
- (f)
- If , reject the signature. Otherwise, convert of to an integer and compute .
- (g)
- Accept the signature iff .
4.5. Smart Contract Design
| Algorithm 1 Algorithm for addUser |
| Require: INPUT UserAddress (UA), UserName (UN), UserClass (UC), UserRole (UR), RoleIssuerAddress (RA), RoleIssuerOrganization (RO), RoleIssuerNote (RN) |
| Ensure: OUTPUT UserDetails (UD) and RoleIssuerDetails (RD) |
| 1: if RA is true, then |
| 2: if RO is true, then |
| 3: Set counter to 0; |
| 4: Add to UserDetails (UD), UA, UN, UC, UR |
| 5: Add RoleIssuerDetails (RD), RA, RO, RN |
| 6: endif |
| 7: increment counter to 1 |
| 8: end |
| Algorithm 2 Algorithm for removeUser |
| Require: INPUT UserAddress (UA), RoleIssuerAddress (RA), timestamp (TM) |
| Ensure: OUTPUT UserAddress (UA) and RoleIssuerAddress (RA) |
| 1: if RA is true, then |
| 2: Set counter to 0; |
| 3: Delete from UserDetails (UD), UA |
| 4: Add to RemovedUser (RU), UA, TM |
| 5: endif |
| 6: increment counter to 1 |
| 7: end |
| Algorithm 3 Algorithm for ServiceRequest |
| Require: INPUT UserAddress (UA), ServiceOrganizationAddress (SA) |
| Ensure: OUTPUT UserAddress (UA) and ServiceGrantedUsers (SGU) |
| 1: if SA is true, then |
| 2: if UA is ’User’, then |
| 3: Set counter to 0; |
| 4: ProvideAccess() |
| 5: Add to ServiceGrantedUser (SGU), UA |
| 6: endif |
| 7: increment counter to 1 |
| 8: end |
| Algorithm 4 Algorithm for ProvidingAccess |
| Require: INPUT UserAddress (UA), Nonce (NC), Signature (XG), Hashes (HS), ServiceOrganizationAddress (SA) |
| Ensure: OUTPUT Set Access (AX) to true |
| 1: if RecoverSigner (UA, HS, XG, NC) is true, then |
| 2: Set Access (AX) to true |
| 3: endif |
| 4: end |
5. Evaluation and Discussion
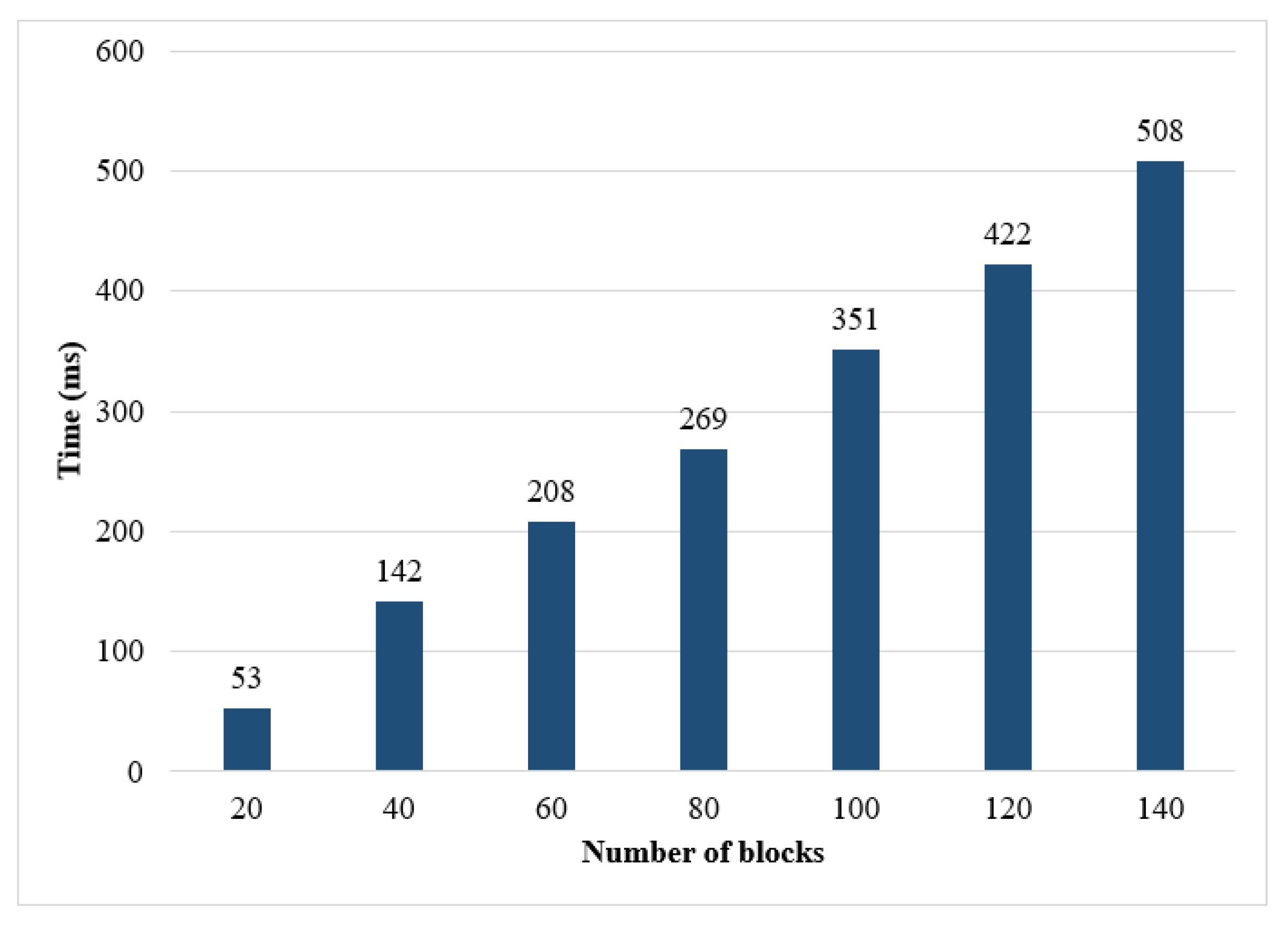
5.1. Evaluation
5.2. Discussion
- Security and Privacy: Security and privacy requirements are significantly important, particularly authentication and integrity, to prevent several attacks in a knowledge management system’s environment. ECDSA signature is a security mechanism that alleviates attacks such as modification, spoofing, denial of service and cyber attacks. The use of the algorithm ensures that only legitimate knowledge users are authorized in the network, and the knowledge items are accessible by these users. It ensures that the identities of the users are from a trusted source, and an unknown one is ignored. With the addition of blockchain, the integrity of the knowledge is also assured. The technology ensures that the transmitted knowledge package has not been tampered with. ECDSA signatures provide mutual authentication so as to protect the knowledge repository. It is capable of preventing man-in-the-middle (MITM) attacks, eavesdropping, impersonation, replay and duplication. Furthermore, the utilization of small keys in the ECDSA algorithm provides high performance and appropriate computation costs. Knowledge owners can check the validity of roles according to the timestamp of when the role was issued to the user.
- Access Control: The processing nodes in the blockchain allow for an efficient access control as they infer from the verifier the public keys of the legitimate users. Before any transaction can be completed, the node in charge of processing that request will have to confirm from the verifier if the user has its public key in the verifier’s knowledge base. The node can revoke access to a malicious entity, as it must ensure that the blockchain contains only valid knowledge transactions (transactions from legitimate knowledge users). However, malicious nodes can process transactions by granting access to knowledge users without verification. However, then, the smart contract center also performs verification checks, and, if unsuccessful, the transaction is dropped. The smart contract also permits roles and other information or knowledge package to legitimate knowledge users in the network efficiently and effectively. Users can also be revoked when the removeUser function is invoked. This function is very important in cases where a user with malicious intention has been found.
- Transparency: The system achieves transparency as all functions are executed by the smart contract and are logged on the blockchain. A secret action cannot be performed without the awareness of the other entities. In addition, entities will not be able to deny any action committed because every action is linked to their private keys.
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| RBAC | Role-Based Access Control |
| ECDSA | Elliptic Curve Digital Signature Authentication |
| KM | Knowledge Management |
| KMS | Knowledge Management Systems |
| PKI | Public Key Infrastructure |
| CA | Certificate Authority |
| PoW | Proof of Work |
| ECC | Elliptic Curve Cryptography |
| DSA | Digital Signature Algorithm |
| ECDLP | Elliptic Curve Discrete Logarithm Problem |
| DL | Discrete Logarithm |
| EC | Elliptic Curve |
| OSPF | Open Shortest Path First |
| MITM | Man-In-The-Middle |
References
- Nonaka, I.; Takeuchi, H. The Knowledge-Creating Company: How Japanese Companies Create the Dynamics of Innovation; Oxford University Press: New York, NY, USA, 1995; pp. 3–19. [Google Scholar]
- Nemetz, M. A meta-model for intellectual capital reporting. In International Conference on Practical Aspects of Knowledge Management; Springer: Berlin/Heidelberg, Germany, 2006. [Google Scholar]
- Quintas, P.; Lefrere, P.; Jones, G. Knowledge management: A strategic agenda. Long Range Plan. 1997, 30, 385–391. [Google Scholar] [CrossRef]
- Ogunseye, O.S.; Folorunso, O.; Zhang, J. Preventing Social Engineering and Espionage in Collaborative Knowledge Management Systems (KMSs). Int. J. E-Adopt. 2011. [Google Scholar] [CrossRef]
- Chen, T.Y. A multiple-Layer knowledge management system framework considering user knowledge privileges. Int. J. Softw. Eng. Knowl. Eng. 2009. [Google Scholar] [CrossRef]
- Ferraiolo, D.; Cugini, J.; Kuhn, D.R. Role based access control: Features and motivations. In Proceedings of the 11th Annual Conference on Computer Security Applications, New Orleans, LA, USA, 11–15 December 1995; IEEE Computer Society Press: Los Alamitos, CA, USA, 1995; pp. 241–248. [Google Scholar]
- Cruz, J.P.; Kaji, Y.; Yanai, N. RBAC-SC: Role-Based Access Control Using Smart Contract. IEEE Access 2018, 6, 12240–12251. [Google Scholar] [CrossRef]
- Ferraiolo, D.F.; Barkley, J.F.; Kuhn, D.R. A role-based access control model and reference implementation within a corporate intranet. ACM Trans. Inf. Syst. Secur. 1999. [Google Scholar] [CrossRef]
- Gupta, A.; Kirkpatrick, M.S.; Bertino, E. A formal proximity model for RBAC systems. Comput. Secur. 2013. [Google Scholar] [CrossRef]
- Malik, A.K.; Dustdar, S. Sharing and Privacy-Aware RBAC in Online Social Networks. In Proceedings of the 2011 IEEE Third International Conference on Privacy, Security, Risk and Trust and 2011 IEEE Third International Conference on Social Computing, Boston, MA, USA, 9–11 October 2011; pp. 1352–1355. [Google Scholar] [CrossRef]
- Nonaka, I.; Toyama, R.; Konno, N. SECI, Ba and Leadership: A Unified Model of Dynamic Knowledge Creation. Long Range Plan. 2000. [Google Scholar] [CrossRef]
- Ipe, M. Knowledge sharing Sharing in organizations: A conceptual framework. Hum. Resourc. Dev. Rev. 2003, 2, 337–359. [Google Scholar] [CrossRef]
- Panarello, A.; Tapas, N.; Merlino, G.; Longo, F.; Puliafito, A. Blockchain and IoT Integration: A Systematic Survey. Sensors 2018, 18, 2575. [Google Scholar] [CrossRef]
- Kshetri, N. Can Blockchain Strengthen the Internet of Things? IT Prof. 2017, 19, 68–72. [Google Scholar] [CrossRef]
- Joshi, A.D.; Gupta, S.M. Evaluation of design alternatives of End-Of-Life products using Internet of things. Int. J. Prod. Econ. 2019, 208, 281–293. [Google Scholar] [CrossRef]
- Queiroz, M.M.; Samuel, F.W. Blockchain adoption challenges in supply chain: An empirical investigation of the main drivers in India and the USA. Int. J. Inf. Manag. 2019, 46, 70–82. [Google Scholar] [CrossRef]
- Wang, Y.; Singgih, M.; Wang, J.; Rit, M. Making sense of blockchain technology: How will it transform supply chains? Int. J. Prod. Econ. 2019, 211, 221–236. [Google Scholar] [CrossRef]
- Sandhu, R.S.; Coyne, E.J.; Feinstein, H.L.; Youman, C.E. Role-based access control models. Computer 1996, 29, 38–47. [Google Scholar] [CrossRef]
- Xia, L.; Jing, J. An administrative model for role-based access control using hierarchical namespace. In Proceedings of the Pacific Asia Conference on Information Systems (PACIS), Kuala Lumpur, Malaysia, 6–9 July 2006; Volume 30. [Google Scholar]
- Lilin, M.; Li, H. A permission model of Saas system based on RBAC. Comput. Appl. Softw. 2010, 27, 42–44. [Google Scholar]
- Li, Q.; Xu, M.; Zhang, X. Towards a group-based RBAC model and decentralized user-role administration. In Proceedings of the 2008 28th International Conference on Distributed Computing Systems Workshops, Beijing, China, 17–20 June 2008. [Google Scholar]
- Alavi, M. Knowledge management and knowledge management systems: Conceptual foundations and research issues. MIS Q. 2001, 25, 107–136. [Google Scholar] [CrossRef]
- Feng, K.C.; Chen, E.T.; Liou, W.C. Implementation of knowledge management systems and firm performance: An empirical investigation. J. Comput. Inf. Syst. 2004, 45, 92–104. [Google Scholar]
- Kostova, T. Transnational Transfer of Strategic Organizational Practices: A Contextual Perspective. Acad. Manag. Rev. 1999, 24, 308. [Google Scholar] [CrossRef]
- St. Rose, V. An Empirical Study of the Characteristics of the Role Based Access Control (RBAC) Model in Securing Knowledge Management (KM) and Knowledge Management Systems (KMS). Ph.D. Thesis, Colorado Technical University, Colorado Springs, CO, USA, 2015. ProQuest LLC; ISBN 978-0-3558-2647-0. [Google Scholar]
- Bakar, A.; Abdullah, R. A framework of secure KMS with RBAC implementation. ARPN J. Eng. Appl. Sci. 2015, 10, 1051–1059. [Google Scholar]
- Fill, H.-G.; Felix, H. Knowledge Blockchains: Applying Blockchain Technologies to Enterprise Modeling. Available online: https://scholarspace.manoa.hawaii.edu/handle/10125/50398 (accessed on 17 February 2020). [CrossRef]
- Wang, H.; Guo, X.; Fan, Y.; Bi, J. Extended Access Control and Recommendation Methods for Enterprise Knowledge Management System. IERI Procedia 2014, 10, 224–230. [Google Scholar] [CrossRef]
- Farrell, S.; Housley, R. An Internet Attribute Certificate Profile for Authorization. RFC 3281. 2002. Available online: https://tools.ietf.org/html/rfc3281 (accessed on 17 February 2020).
- Ellison, C.; Frantz, B.; Lampson, B.; Rivest, R.; Thomas, B.; Ylonen, T. RFC 2693: SPKI Certificate Theory. The Internet Society, 1999. Available online: https://tools.ietf.org/html/rfc2693 (accessed on 17 February 2020).
- Gutmann, P. Simplifying public key management. Computer 2004, 37, 101–103. [Google Scholar] [CrossRef]
- Charette, R. DigiNotar certificate authority breach crashes e-Government in The Netherlands. IEEE Spectrum. Available online: https://spectrum.ieee.org/riskfactor/telecom/security/diginotar-certificate-authority-breach-crashes-egovernment-in-the-netherlands (accessed on 17 February 2020).
- Lewko, A.; Waters, B. Decentralizing attribute-based encryption. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Tallinn, Estonia, 15–19 May 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 568–588. [Google Scholar]
- Okamoto, T.; Katsuyuki, T. Decentralized attribute-based signatures. In Proceedings of the International Workshop on Public Key Cryptography, Nara, Japan, 26 February–1 March 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 125–142. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: http://bitcoin.org/bitcoin.pdf (accessed on 17 February 2020).
- Reyna, A.; Martín, C.; Chen, J. Enrique Soler, and Manuel Díaz. On blockchain and its integration with IoT. Challenges and opportunities. Future Gener. Comput. Syst. 2018, 88, 173–190. [Google Scholar] [CrossRef]
- Sifah, E.B.; Xia, Q.; Agyekum, K.O.-B.O.; Amofa, S.; Gao, J.; Chen, R.; Xia, H.; Gee, J.C.; Du, X.; Guizani, M. Chain-based big data access control infrastructure. J. Supercomput. 2018, 74, 4945–4964. [Google Scholar] [CrossRef]
- Merkle, R.C. Protocols for Public Key Cryptosystems. In Proceedings of the 1980 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 14–16 April 1980; p. 122. [Google Scholar]
- Vanstone, S. Responses to NIST’s Proposal. Commun. ACM 1992, 35, 50–52. [Google Scholar]
- National Institute of Standards and Technology. Digital Signature Standard; FIPS Publication: Gaithersburg, MD, USA, 1994; p. 186. [Google Scholar]
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Miller, V. Uses of elliptic curves in cryptography. In Advances in Cryptology—Crypto ’85; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1986; Volume 218, pp. 417–426. [Google Scholar]
- Wood, G. Ethereum: A Secure Decentralised Generalised Transaction Ledger. Available online: https://gavwood.com/paper.pdf (accessed on 17 February 2020).
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. LSB: A Lightweight Scalable Blockchain for IoT security and anonymity. J. Parall. Distribut. Comput. 2019, 134, 180–197. [Google Scholar] [CrossRef]


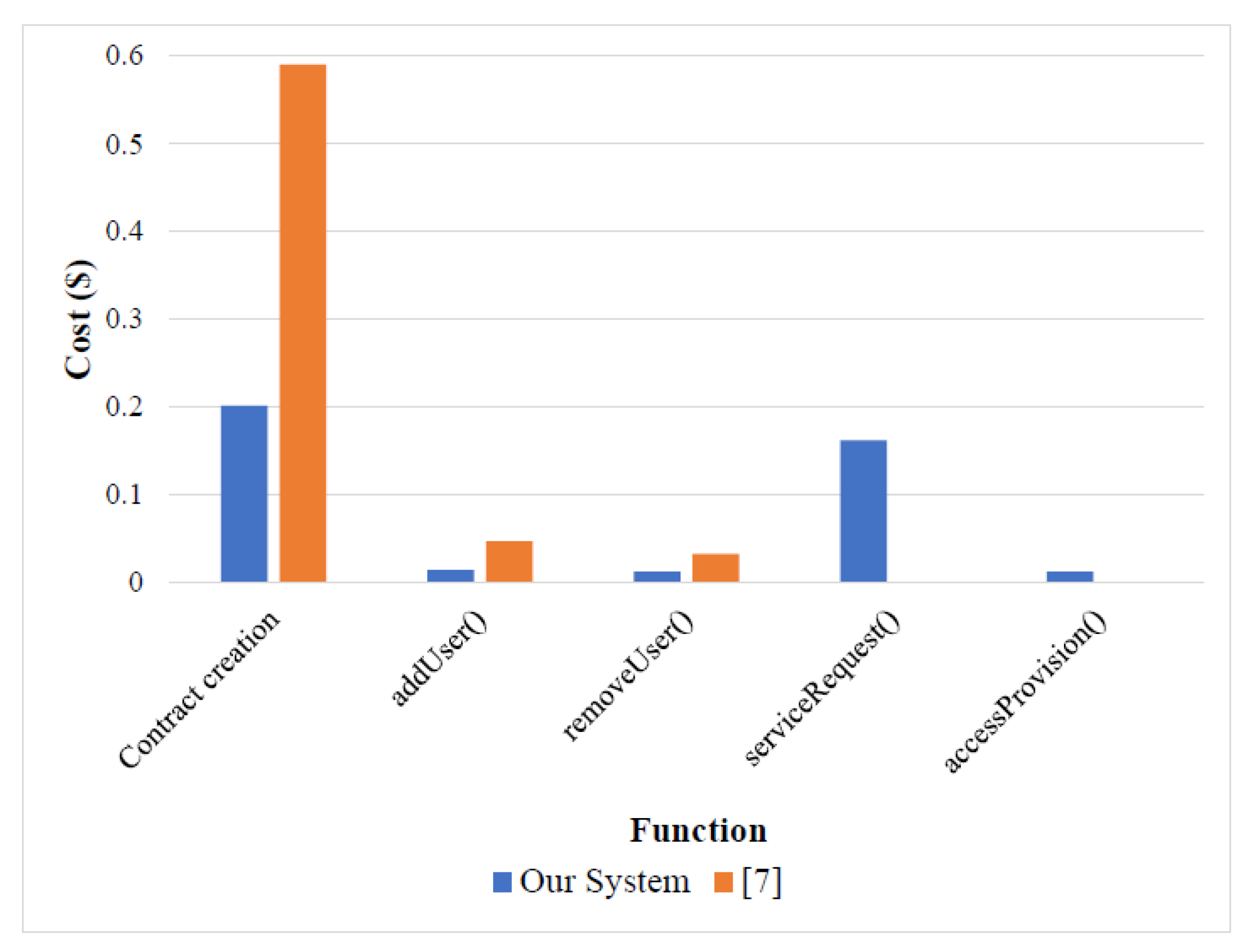
| Function | Our System [Gas (Gwei)] | Our System [Gas ($)] | Cruz et al. [7] [Gas ($)] |
|---|---|---|---|
| Contract creation | 1,560,740 | 0.2016 | 0.590 |
| addUser | 113,870 | 0.0147 | 0.047 |
| removeUser | 100,481 | 0.0130 | 0.033 |
| serviceRequest | 1,253,642 | 0.1619 | - |
| accessProvision | 97,213 | 0.0126 | - |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nyame, G.; Qin, Z.; Obour Agyekum, K.O.-B.; Sifah, E.B. An ECDSA Approach to Access Control in Knowledge Management Systems Using Blockchain. Information 2020, 11, 111. https://doi.org/10.3390/info11020111
Nyame G, Qin Z, Obour Agyekum KO-B, Sifah EB. An ECDSA Approach to Access Control in Knowledge Management Systems Using Blockchain. Information. 2020; 11(2):111. https://doi.org/10.3390/info11020111
Chicago/Turabian StyleNyame, Gabriel, Zhiguang Qin, Kwame Opuni-Boachie Obour Agyekum, and Emmanuel Boateng Sifah. 2020. "An ECDSA Approach to Access Control in Knowledge Management Systems Using Blockchain" Information 11, no. 2: 111. https://doi.org/10.3390/info11020111
APA StyleNyame, G., Qin, Z., Obour Agyekum, K. O.-B., & Sifah, E. B. (2020). An ECDSA Approach to Access Control in Knowledge Management Systems Using Blockchain. Information, 11(2), 111. https://doi.org/10.3390/info11020111





