Energy-Efficient Check-and-Spray Geocast Routing Protocol for Opportunistic Networks
Abstract
:1. Introduction
2. Related Work
3. Proposed EECSG Routing Protocol
- Acquiring the location information on-the-go. At this step, two tasks are involved in predicting the node movement. The first tasks consist of collecting the mobility traces, which deals with location sampling and node’s location information maintenance. The second task consists of extracting the information relevant to a given message from the available movement history. The following sub-steps are involved:
- (a)
- Location sampling: A node location may either be sampled periodically or triggered by an external event. In periodic sampling, the choice of the sampling interval presents a trade-off between accuracy and energy consumption in the sense that fine-grained intervals provide a more accurate movement history and higher energy consumption while larger intervals consume less energy, but may fail to record important locations. With an event-triggered approach, the location is sampled only when a node is encountered. While this approach records only the locations in which the encounter opportunities are available, some of the encounters may not be regular. As such, when using this technique, we have collected GPS traces at regular intervals and logged them into a file in order to analyze them and uncover some correlations on the number of visits between nodes to a given location.
- (b)
- Location information maintenance: This is taken care of as follows: the geographic area of the network is partitioned into a grid of square cells, where each cell is treated as a place (i.e., a collection of nearby locations in the network), and every node then maintains a list of its most visited places. It is worth noting that here, a location is obtained by using the Global Positioning System (GPS). After location sampling, the information that is relevant to a given message is extracted from the available movement history.
- Defining the destination cast as well as determining whether the current position is located within it. This involves the following sub-steps:
- (a)
- Identifying the message endpoint: A message in OppNet is created along with the Endpoint Identifier (EID), which specifies its destination address. Unlike unicasting and multicasting, the naming approach in geocasting depends on the geographical location/area and the membership of the location. A location could be a point, polygon, grid, circle, to name a few. Besides, the membership of a node is subject to time and space. This is different in the case of uni-casting and multicasting, where the message destination is assigned to a node along with its EID.
- (b)
- Cast definition: In geocasting, the message destination is defined as a cast, i.e., a geographical area considered as the destination of the transmitted message. All network users residing within a defined geographical area is a potential recipient of a message, i.e., a user is a recipient if a message destination address corresponds with its current location. A cast can be defined as a point, circle, polygon, grid, to name a few, and a user defines the cast as a point of Polygon, and the casts are defined as a set of pairs of two-dimensional coordinates. The strategies that are often used to identify the position of a point inside or outside the polygon include Crossing test, Angle Summation test and Triangle test [12]. In this work, we make use of the Crossing test algorithm.
- (c)
- Membership check: A node is identified with a location. To be qualified as a recipient of a message, a node is checked to determined whether it is a member of a location i.e., belongs to a cast. Frequently visited places also known as Point of Interests (PoIs) are locations of the nodes that are often visited. The nodes that are currently located in the PoIs in the polygon are checked.
- Computing a forwarding utility metric to quantify the routing contribution that can be made by the nodes encountered outside the destination cast. The forwarding algorithm is designed for a message carrier to always identify the best node with a higher chance to relay the message to its destination. This involves the following considerations:
- (a)
- Buffer scheduling policy: In order to reduce the energy consumption, buffer management should be taken care of, for instance, by deciding on which buffer scheduling policy is to be adopted, which will result in a minimum packets delivery loss. In that sense, in our simulation experiment, the following four scheduling policies can be considered: (1) the First-In-First-Out (FIFO)—where the messages are forwarded to the nodes in the that order that they have been received; (2) Last-In-First-Out (LIFO)—where the messages are forwarded to the nodes in the reverse order that they have been received; (3) Highest-Time-to-Live-First-Out (HTFO)—where the message with the longest lifetime is first forwarded, followed by others; and (4) Lowest-TTL-First-Out (LTFO)—where the message with the shortest lifetime is first forwarded, followed by others. For most of our simulations, we have considered the default buffer scheduling policy, i.e., random policy—meaning that the messages are randomly selected from the node’s buffer when a node encounters another one.
- (b)
- Energy efficiency: In an OppNet, the energy consumption of a node is a critical issue which frequently occurs when the node sends and receives the data packets or when one packet is sent many times by the node to other nodes. In order to save the node’s battery life, thereby increase the chance of successful packet delivery, it is desirable to route the packets only through those nodes that have enough remaining battery power, in such a way that the delivery ratio of packets is maximized. In our proposed EECSG protocol, the energy level of the receiving nodes have been taken into account when deciding on the suitable relay nodes to carry the message towards its destination. Indeed, during the first phase of the EECSG protocol, while forwarding the message to its destination, the energy level of any neighboring node n of a source node is checked. If it is below a prescribed energy threshold level, the message is not forwarded to that node n. Once in the geocast region, the energy level of the receiving nodes is again checked. If the energy level of such receiving node it is less than the prescribed energy threshold, such a node will only receive one data packet and will be prevented from transmitting the messages further.For the calculation of the energy threshold , the residual energy of each neighbour node of the source node is calculated. We consider CurrentEnergy(node) the residual energy of the source/intermediate node and neighbourEnergy(node) the residual energy of the neighbor node of the source node. These are calculated aswhere is a function that returns the residual energy of the corresponding node. The energy threshold level of a node is obtained as:where is the total number of neighbours of the current node.
It should be noted that in this work, is referred to as a forwarding utility metric because the selection of a suitable relay node to forward the message is based on the above mentioned formulae. - Selecting a relay node based on the forwarding utility metric.
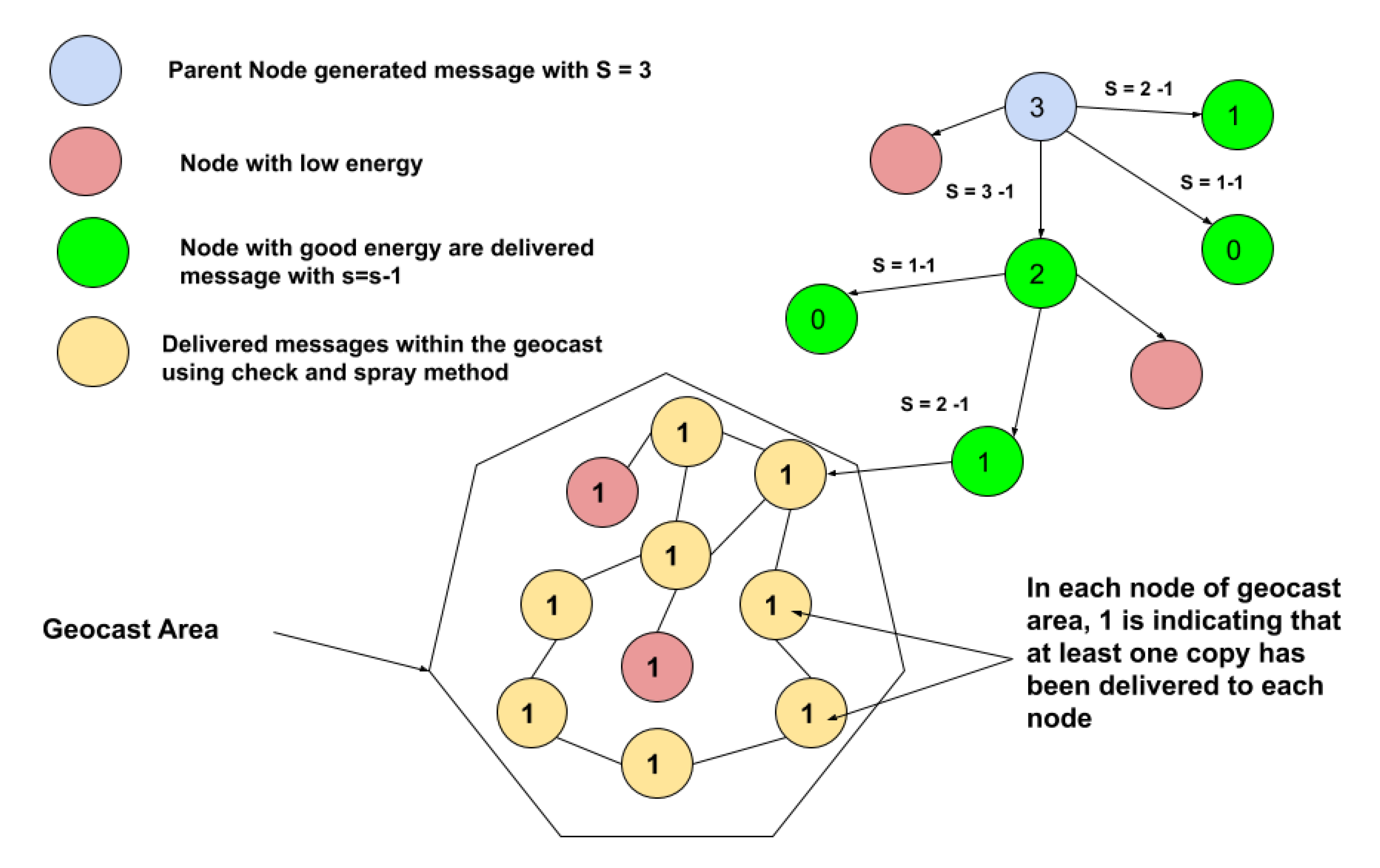
- Message dissemination using the Check-and-Spray controlled flooding methodology: The message dissemination within the cast is a typical floating content issue, which offers an opportunity to enable the localized information sharing without the need for an infrastructure, data collection or central control. Ultimately, it offers some degree of privacy by not allowing the remote access to the content within a defined geographical location. Besides, flooding a message is resource consuming, but can guarantee an optimum message delivery ratio. In our proposed EECSG routing protocol, an energy-efficient controlled flooding methodology (referred to as Check-and-Spray) is designed to distribute the geo messages to all the nodes within the geocast region. It consists of two parts. In the first part, the node’s energy level is checked against the threshold. The presence of the already existing message in the receiving node cast and the receiving node’s current location are checked. In the second part, the message is flooded to only those nodes which have passed all the checks mentioned in the first part. Afterwards, the receivers become the senders and the Check-and-Spray method is re-invoked. This process is continued until it is resumed. Due to the first part, this controlled flooded technique tend to consume less energy.
| Algorithm 1 EECSG protocol. |
|
4. Performance Evaluation
- Number of dead nodes: This represents the number of nodes whose remaining energy are less than the prescribed minimum energy threshold at the end of the simulations. Initially, 5000 J energy is given to the node. Transmit energy of a node is 0.2 J. The battery level threshold of the node is set to 600 J. When a node’s energy is less than 600 J then it is considered as a dead node. node [15].
- Delivery ratio: this is the ratio of messages successfully delivered to the destination at the end of the simulations vs. the total number of messages generated in the network.
- Overhead ratio: this is a measure of the bandwidth efficiency, calculated as:
5. Results Analysis Using Synthetic Models
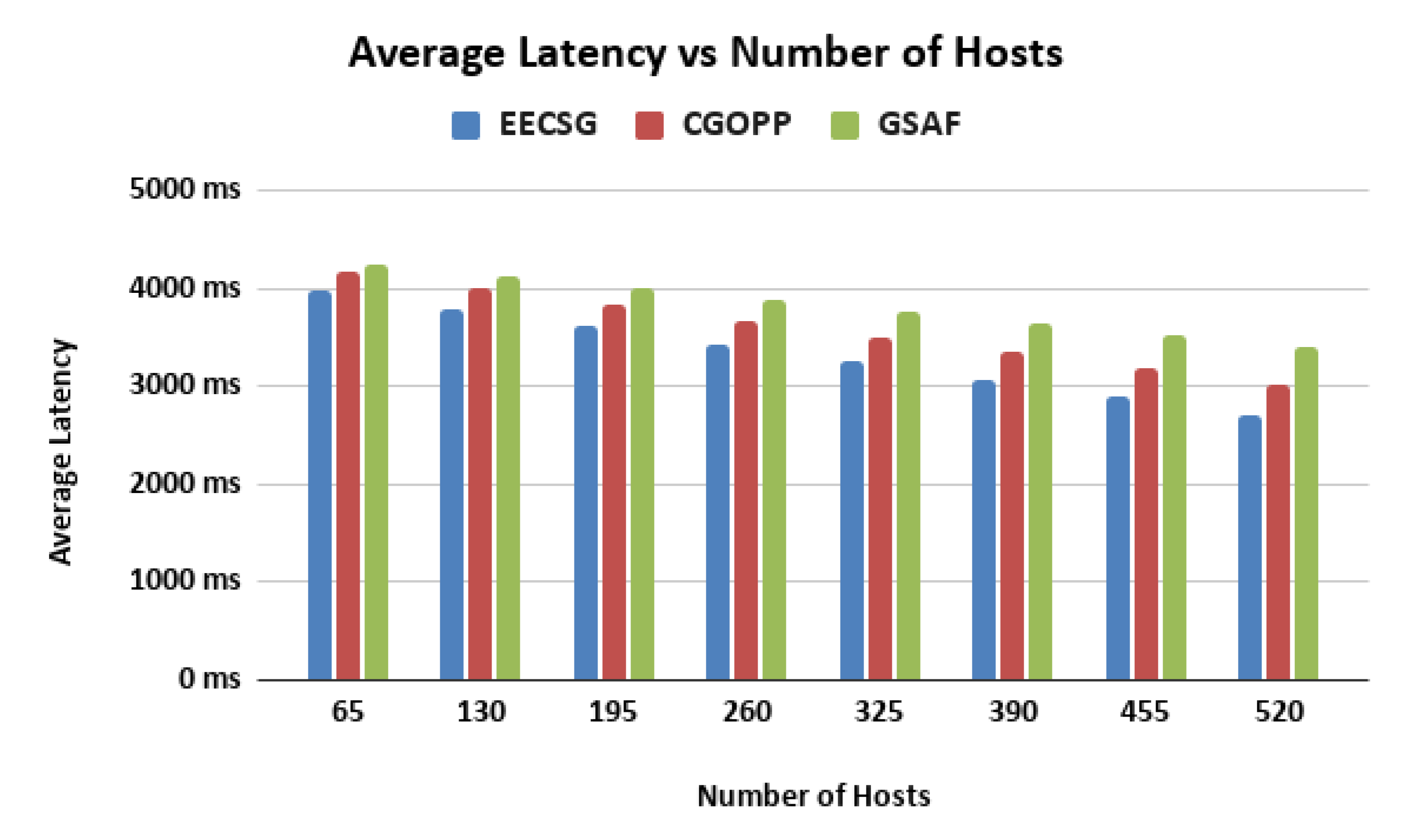
5.1. Varying the Number of Hosts
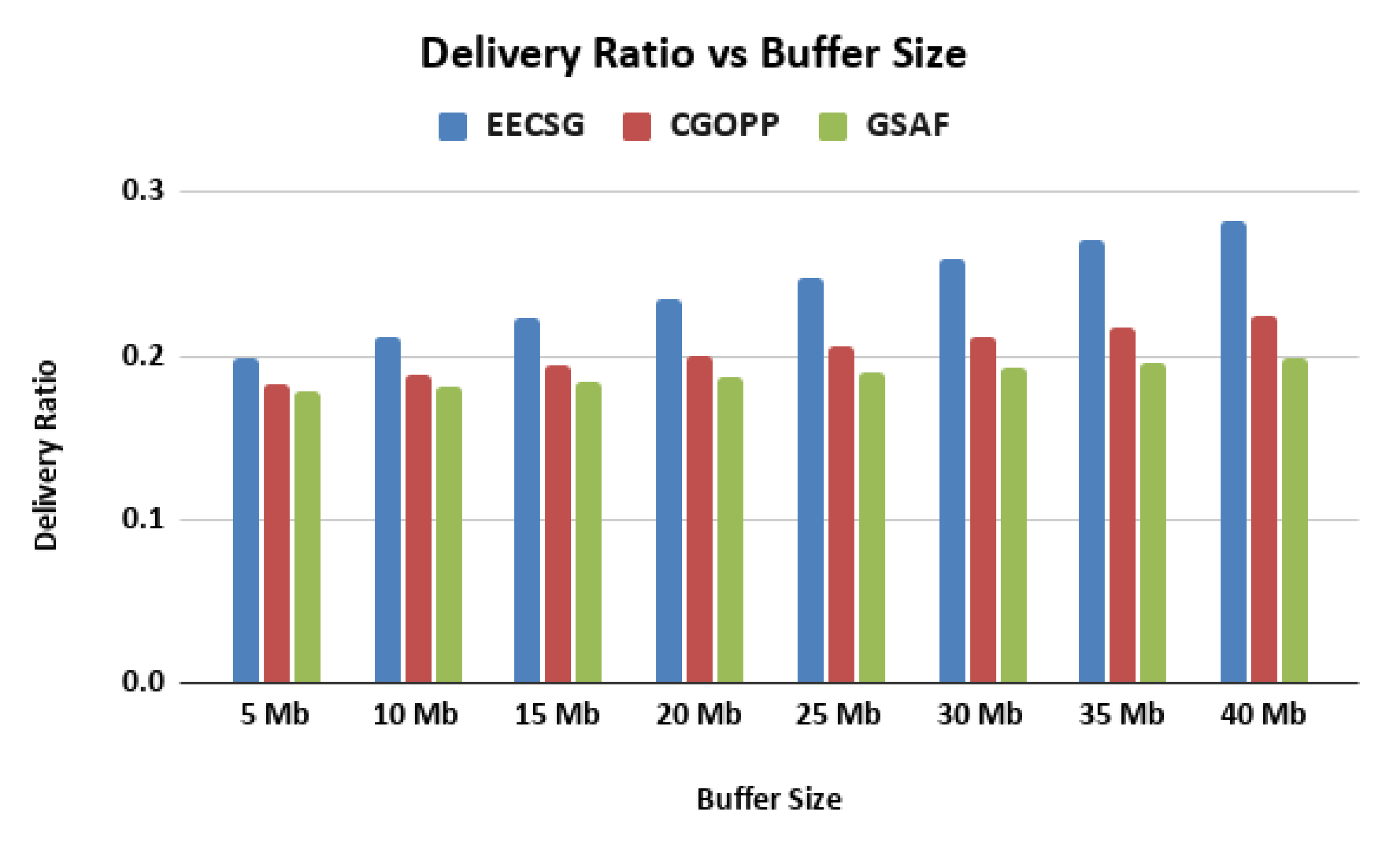
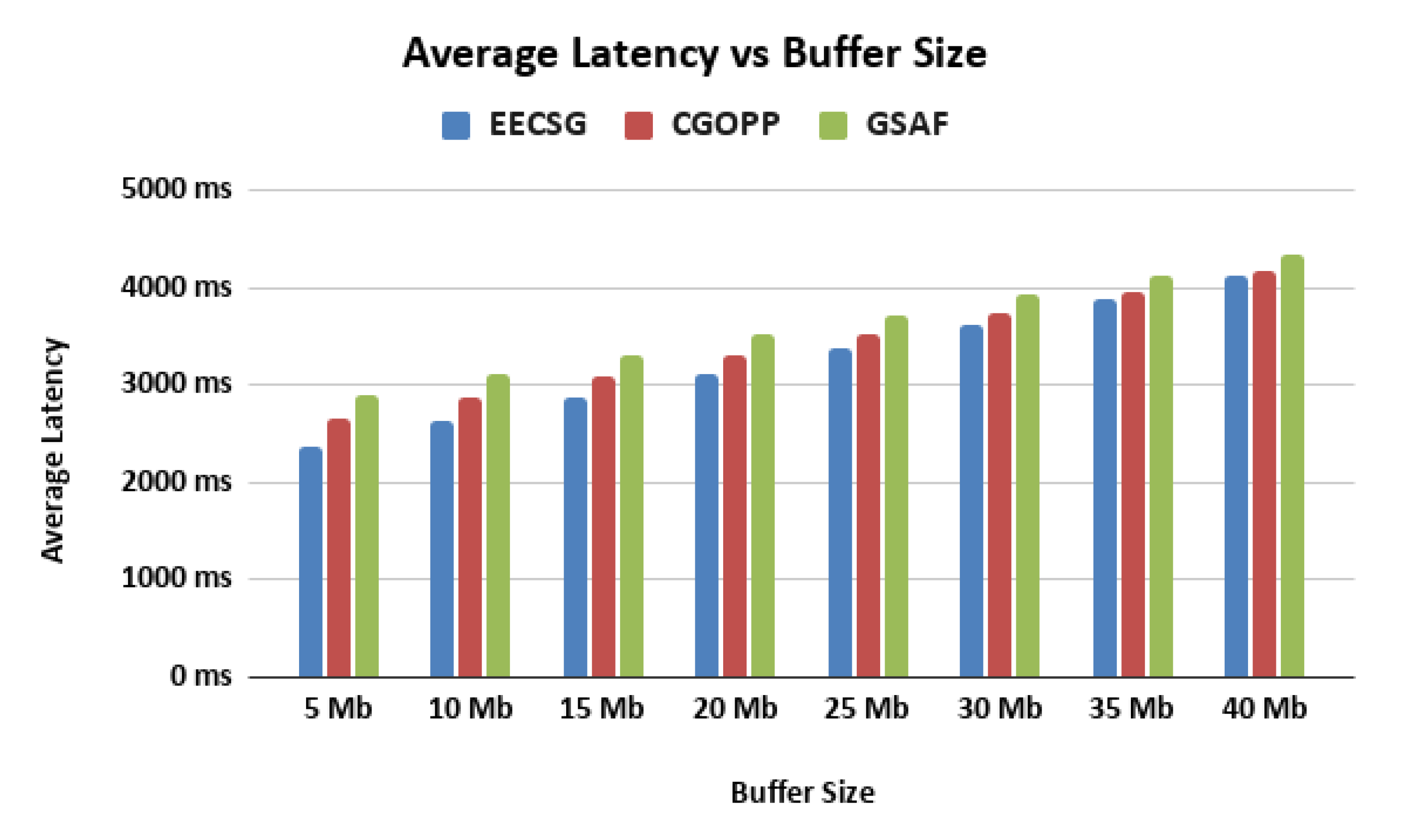
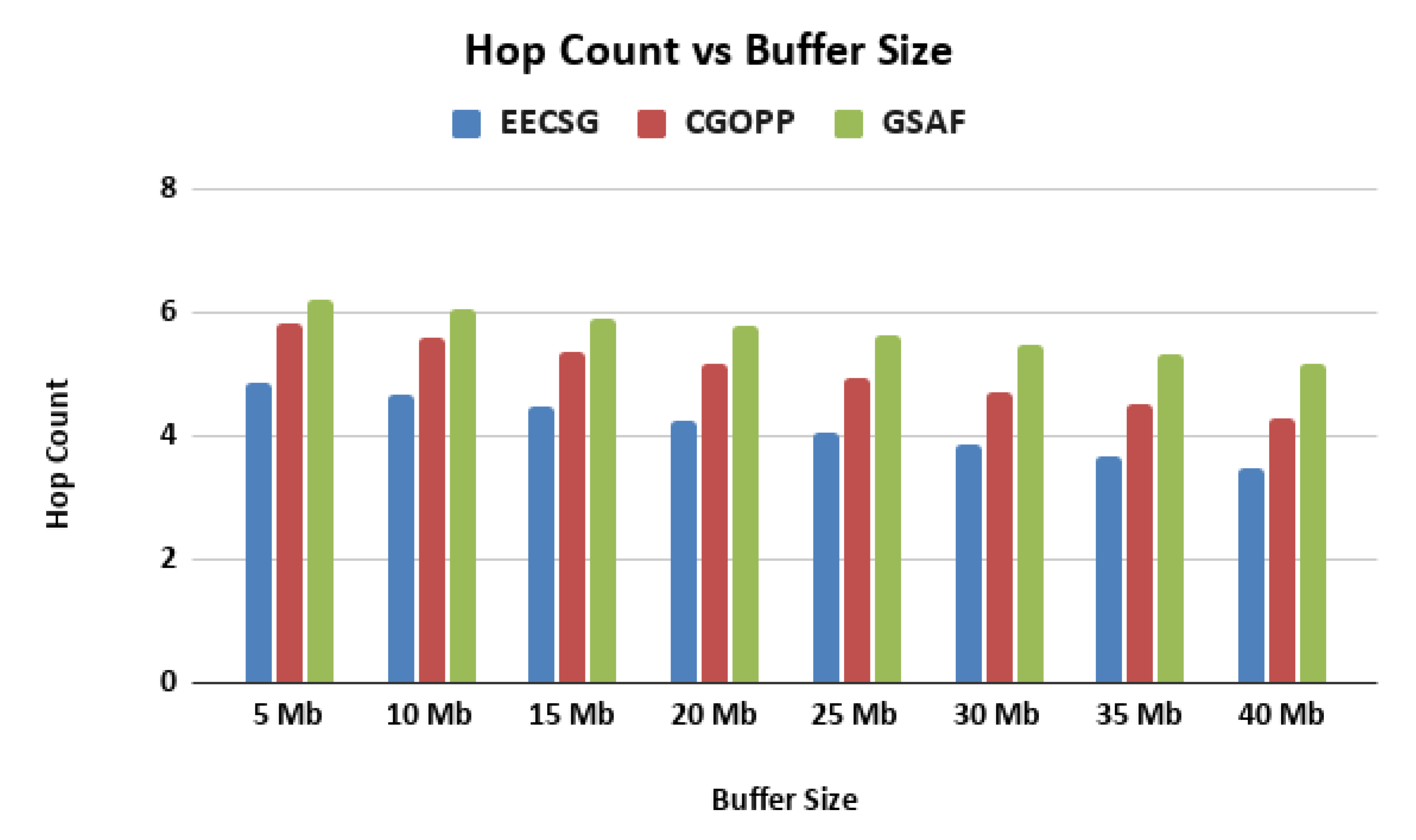
5.2. Varying the Buffer Size
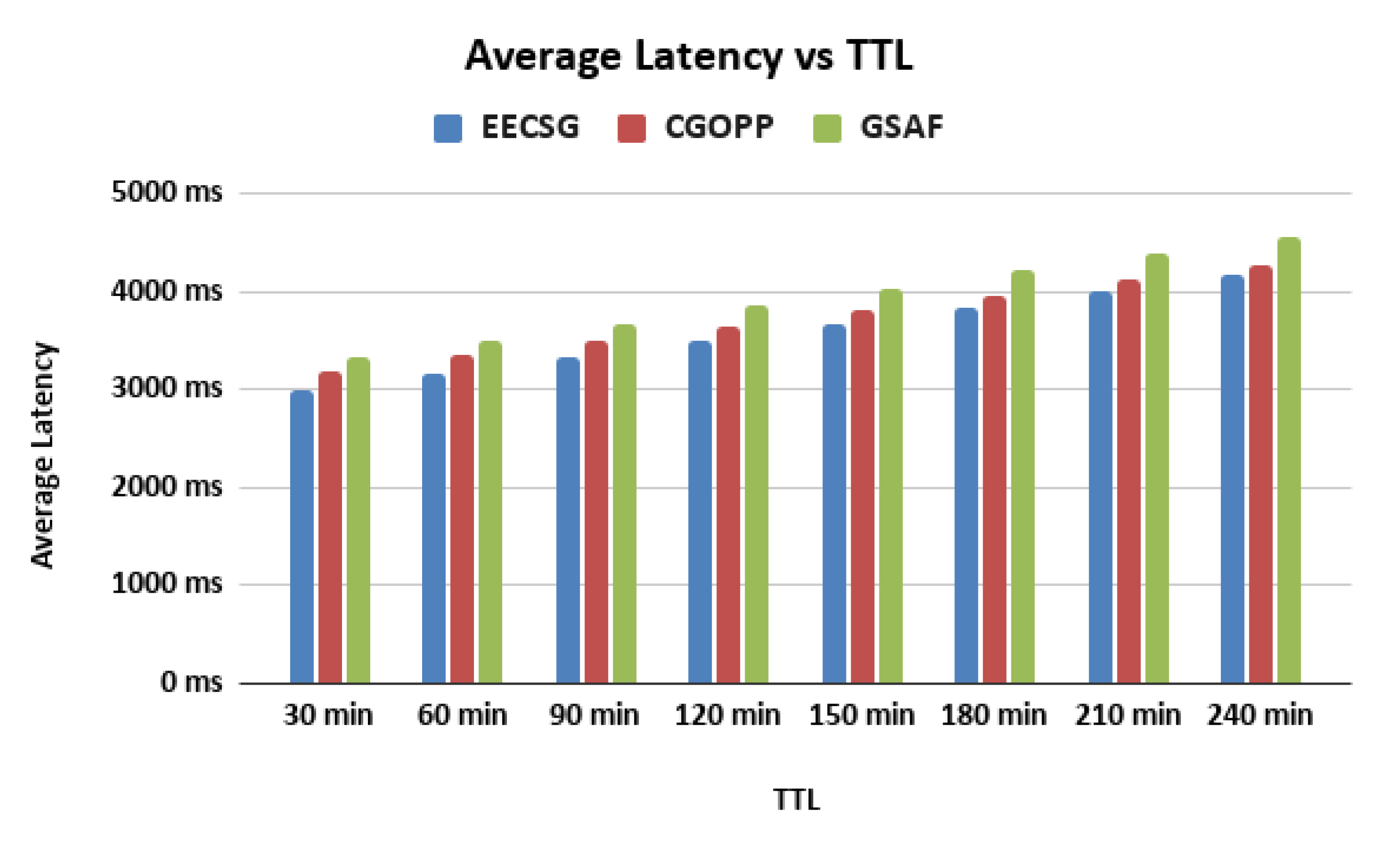
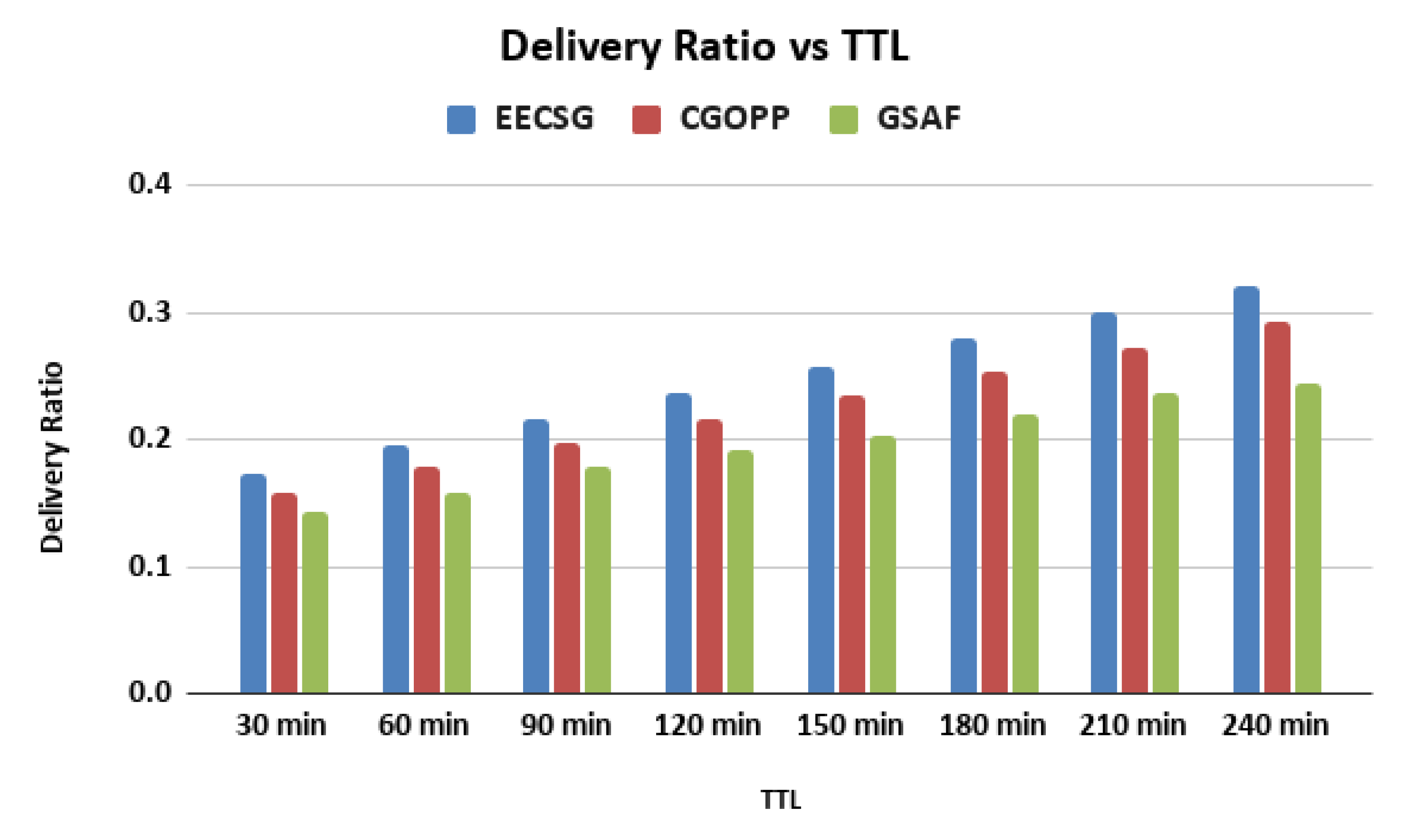
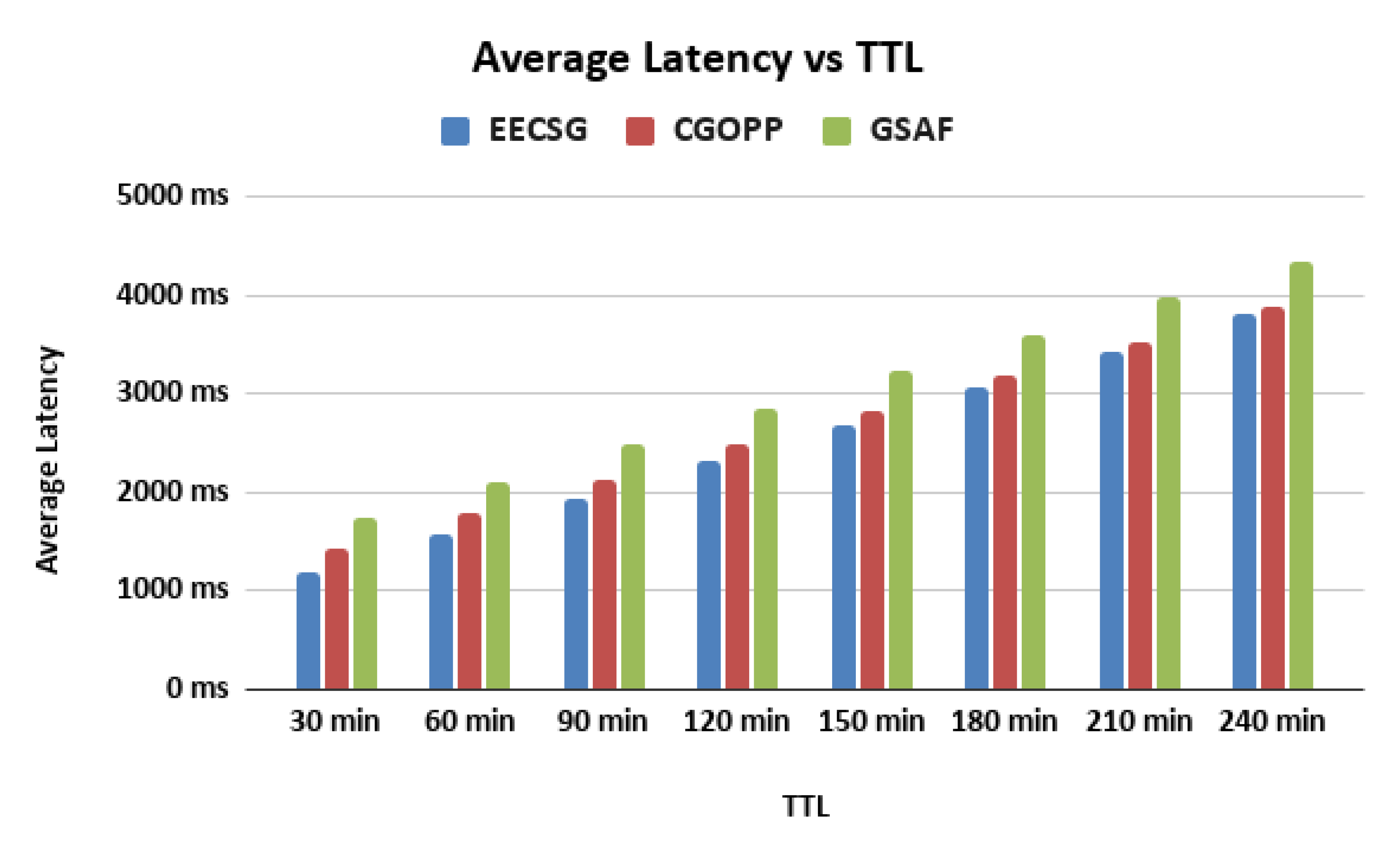
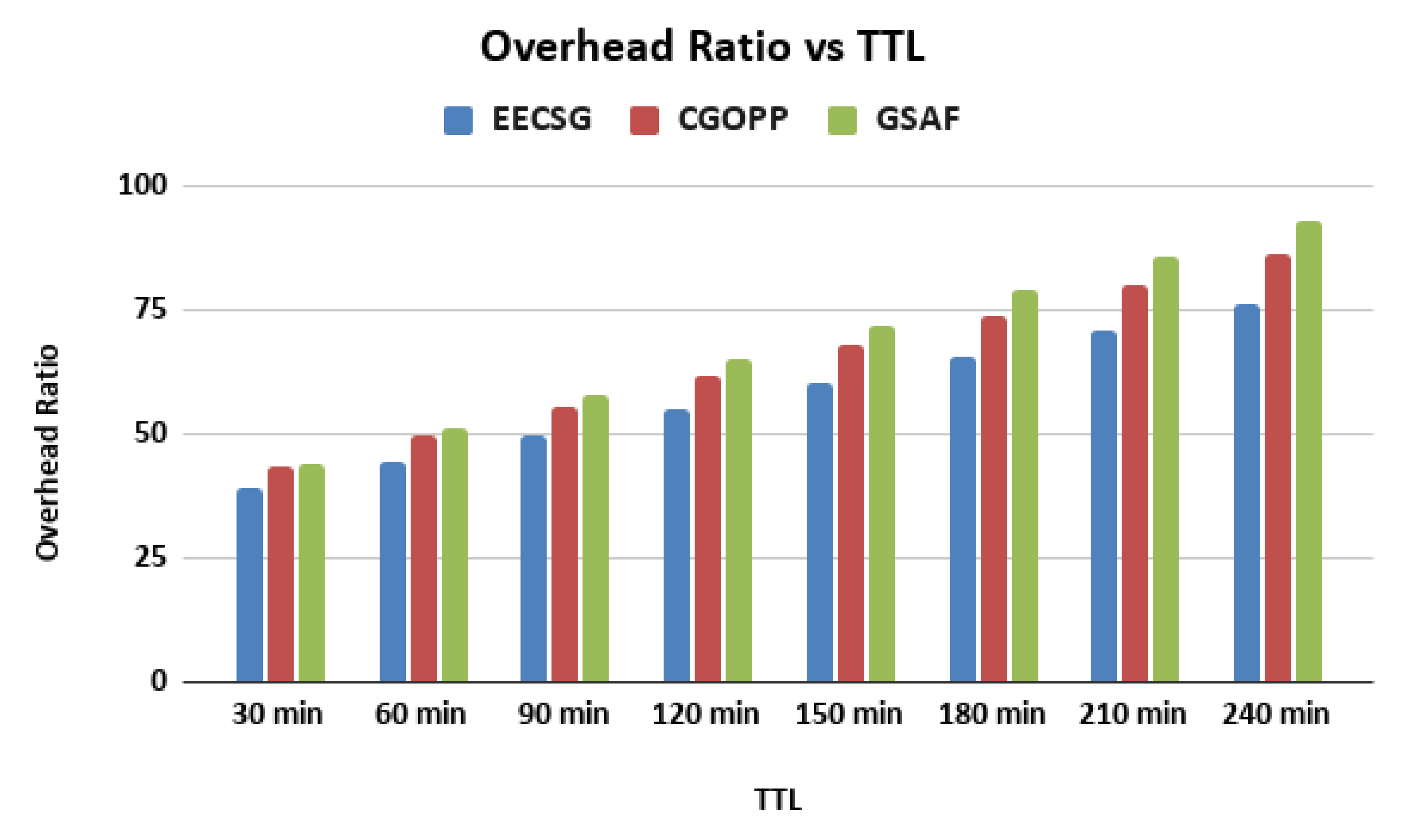
5.3. Varying the TTL
6. Simulation Results Using Real Data Mobility Traces
7. Conclusions and Future Works
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| EECSG | Energy Efficient Check-and-Spray Geocasting |
| OppNets | Opportunistic Networks |
| GSAF | Efficient and flexible Geocasting for opportunistic networks |
| CGOPP | Centrality-Based Geocasting for OPPortunistic networks |
| TTL | Time-to-Live |
References
- Lilien, L.; Kamal, Z.H.; Bhuse, V.; Gupta, A. Opportunistic networks: The concept and research. In Challenges in Privacy and Security. In Proceedings of the Workshop on Research Challenges in Security and Privacy for Mobile and Wireless Networks (WSPWN 2006), Miami, FL, USA, 15–16 March 2006. [Google Scholar]
- Jacqueline, H.; Lauren, G.; Yang, S. A survey of social-based routing protocols in Delay Tolerant Networks. In Proceedings of the International Conference on Computing, Networking and Communications (ICNC), Silicon Valley, CA, USA, 26–29 January 2017; pp. 788–792. [Google Scholar]
- Abali, A.M.; Ithnin, N.B.; Ebibio, T.A.; Dawood, M.; Gadzama, W.A. A Survey of Geocast Routing Protocols in Opportunistic Networks. In Proceedings of the International Conference of Reliable Information and Communication Technology, Johor, Malaysia, 22–23 September 2019; pp. 683–694. [Google Scholar]
- Wakeman, I.; Naicken, S.; Rimmer, J.; Chalmers, D.; Fisher, C. The fans united will always be connected: Building a practical DTN in a football stadium. In Proceedings of the International Conference on Ad Hoc Networks, San Remo, Italy, 1–2 September 2013; pp. 162–177. [Google Scholar]
- Lu, S.; Liu, Y. Geoopp: Geocasting for opportunistic networks. In Proceedings of the 2014 IEEE Wireless Communications and Networking Conference (WCNC), Istanbul, Turkey, 6–9 April 2014; pp. 2582–2587. [Google Scholar]
- Lu, S.; Liu, Y.; Liu, Y.; Kumar, M. Loop: A location based routing scheme for opportunistic networks. In Proceedings of the 2012 IEEE 9th International Conference on Mobile Ad-Hoc and Sensor Systems (MASS 2012), Las Vegas, NV, USA, 8–11 October 2012; pp. 118–126. [Google Scholar]
- Ott, J.; Hyytiä, E.; Lassila, P.; Vaegs, T.; Kangasharju, J. Floating content: Information sharing in urban areas. In Proceedings of the 2011 IEEE International Conference on Pervasive Computing and Communications (PerCom), Washington, DC, USA, 21–25 March 2011; pp. 136–146. [Google Scholar]
- Ma, Y.; Jamalipour, A. Opportunistic geocast in disruption-tolerant networks. In Proceedings of the 2011 IEEE Global Telecommunications Conference-GLOBECOM 2011, Houston, TX, USA, 5–9 December 2011; pp. 1–5. [Google Scholar]
- Rajaei, A.; Chalmers, D.; Wakeman, I.; Parisis, G. GSAF: Efficient and flexible geocasting for opportunistic networks. In Proceedings of the 2016 IEEE 17th International Symposium on A World of Wireless, Mobile and Multimedia Networks (WoWMoM), Coimbra, Portugal, 21–24 June 2016; pp. 1–9. [Google Scholar]
- Singh, J.; Dhurandher, S.K.; Woungang, I.; Takizawa, M. Centrality Based Geocasting for Opportunistic Networks. In Proceedings of the International Conference on Advanced Information Networking and Applications, Matsue, Japan, 27–29 March 2019; pp. 702–712. [Google Scholar]
- Dhurandher, S.K.; Singh, J.; Woungang, I.; Takizawa, M.; Gupta, G.; Kumar, R. Fuzzy Geocasting in Opportunistic Networks. In Proceedings of the International Conference on Broadband and Wireless Computing, Communication and Applications, Antwerp, Belgium, 7–9 November 2019; pp. 279–292. [Google Scholar]
- Haines, E. Point in Polygon Strategies. In Graphics Gems; Academic Press: San Diego, CA, USA, 1994; Volume 4, pp. 24–46. ISBN 978-0-12-336155-4. [Google Scholar]
- Keränen, A.; Ott, J.; Kärkkäinen, T. The ONE simulator for DTN protocol evaluation. In Proceedings of the 2nd international Conference on Simulation Tools and Techniques, Rome, Italy, 2–6 March 2009; pp. 1–10. [Google Scholar]
- Crawdad Haggle Dataset. Available online: https://crawdad.org/uoi/haggle/20160828/one (accessed on 14 August 2020).
- Khalid, K.; Woungang, I.; Dhurandher, S.K.; Barolli, L.; Carvalho, G.H.; Takizawa, M. An energy-efficient routing protocol for infrastructure-less opportunistic networks. In Proceedings of the 2016 10th International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing (IMIS), Fukuoka, Japan, 6–8 July 2016; pp. 237–244. [Google Scholar]









Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khalid, K.; Woungang, I.; Dhurandher, S.K.; Singh, J.; J. P. C. Rodrigues, J. Energy-Efficient Check-and-Spray Geocast Routing Protocol for Opportunistic Networks. Information 2020, 11, 504. https://doi.org/10.3390/info11110504
Khalid K, Woungang I, Dhurandher SK, Singh J, J. P. C. Rodrigues J. Energy-Efficient Check-and-Spray Geocast Routing Protocol for Opportunistic Networks. Information. 2020; 11(11):504. https://doi.org/10.3390/info11110504
Chicago/Turabian StyleKhalid, Khuram, Isaac Woungang, Sanjay Kumar Dhurandher, Jagdeep Singh, and Joel J. P. C. Rodrigues. 2020. "Energy-Efficient Check-and-Spray Geocast Routing Protocol for Opportunistic Networks" Information 11, no. 11: 504. https://doi.org/10.3390/info11110504
APA StyleKhalid, K., Woungang, I., Dhurandher, S. K., Singh, J., & J. P. C. Rodrigues, J. (2020). Energy-Efficient Check-and-Spray Geocast Routing Protocol for Opportunistic Networks. Information, 11(11), 504. https://doi.org/10.3390/info11110504






