Improving Cybersafety Maturity of South African Schools
Abstract
1. Introduction
2. Cybersafety for Schools
3. Methodology and Data-Gathering Method
4. Data Analysis
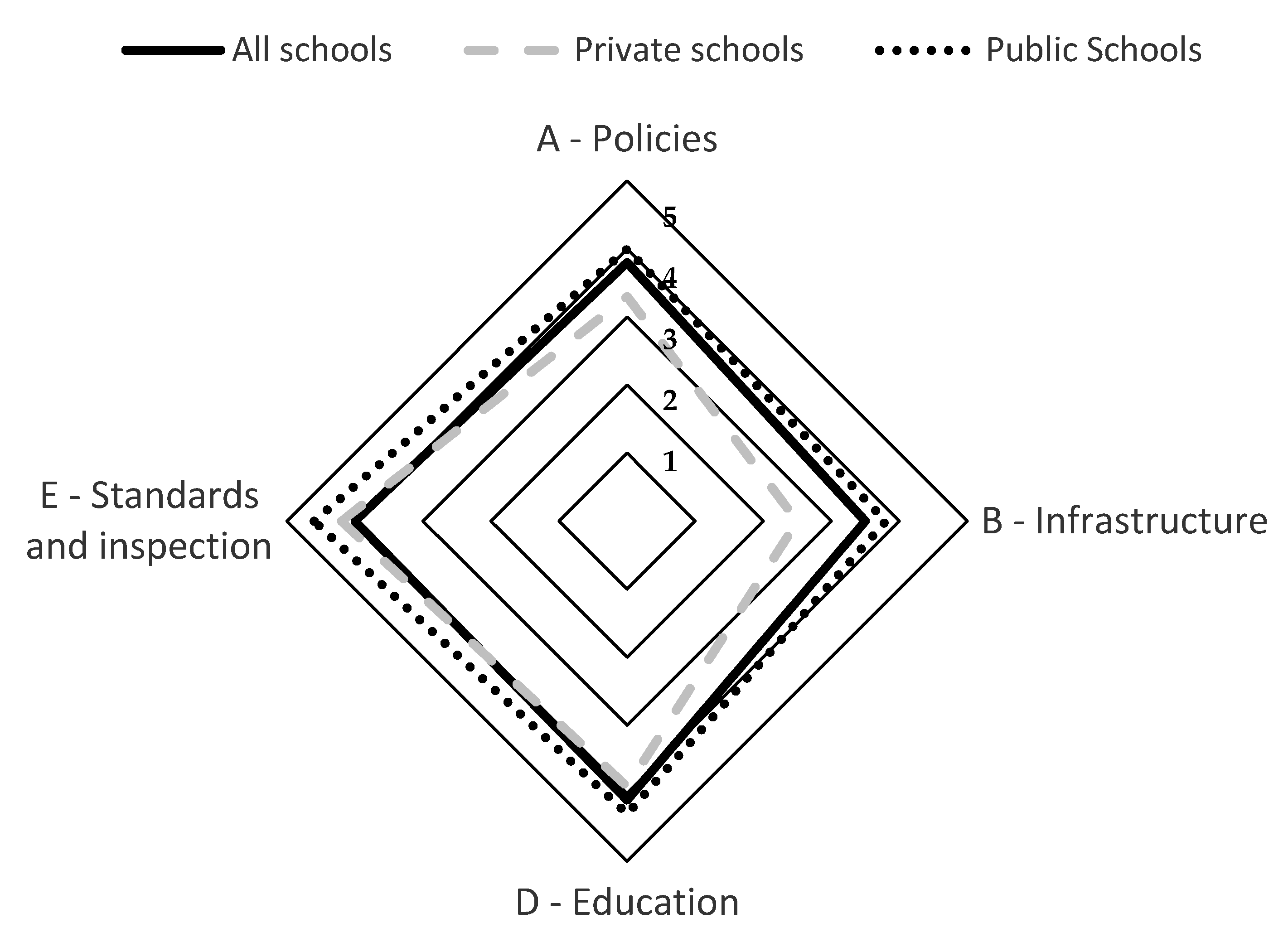
4.1. Element A: Policies and Leadership
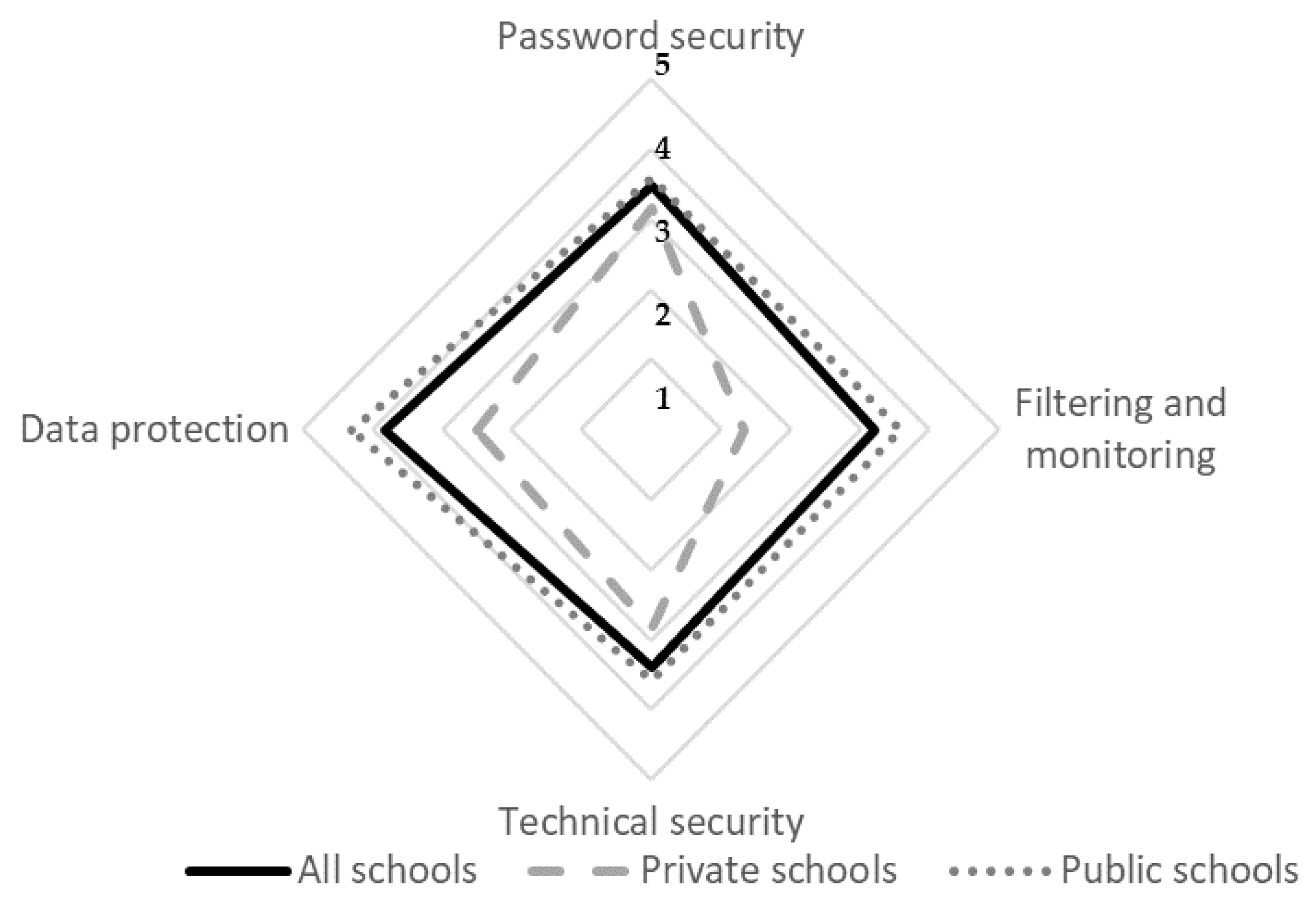
4.2. Element B: Infrastructure
4.3. Element C: Education
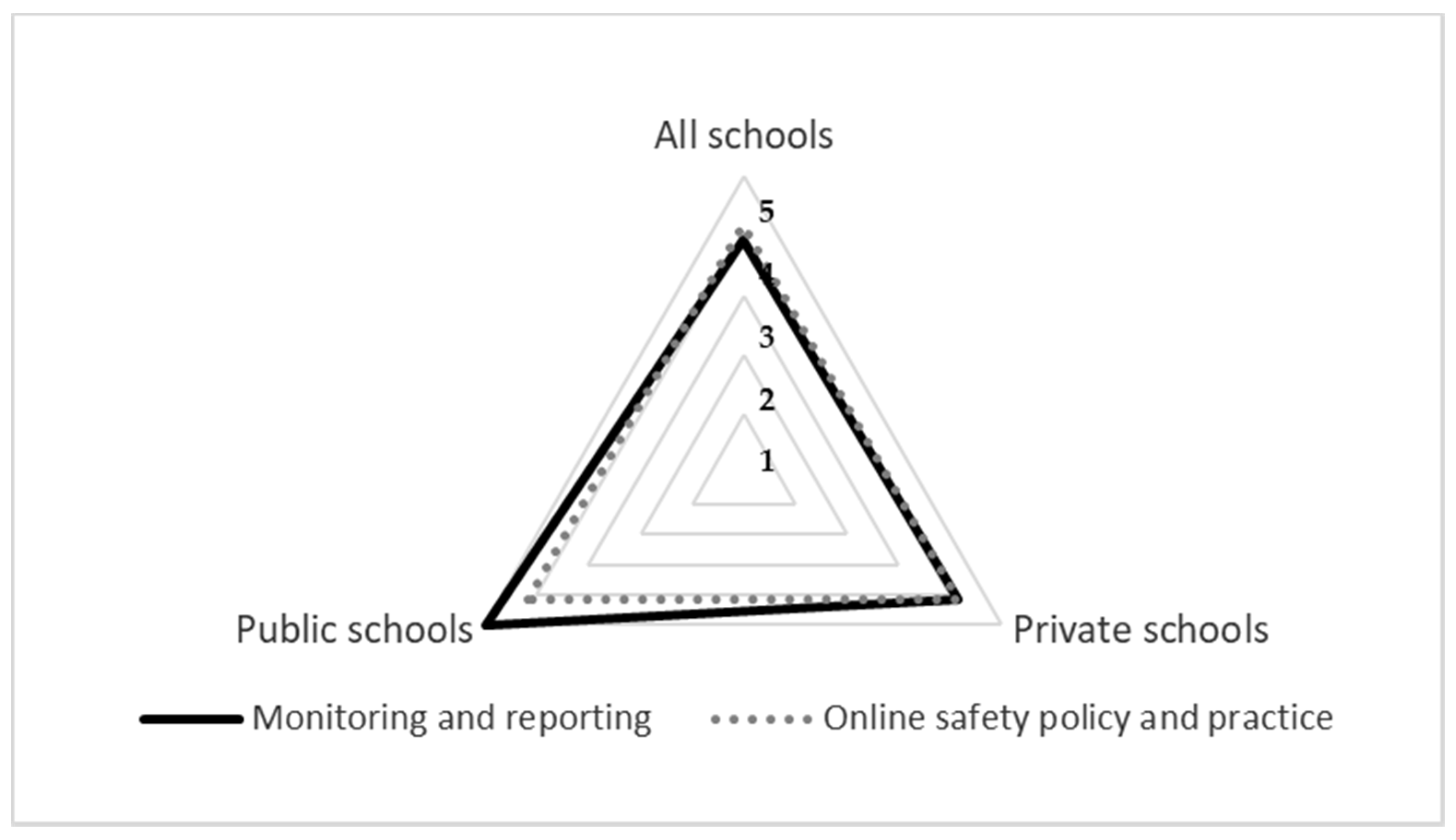
4.4. Element D: Standards and Inspection
4.5. Discussion of Overall Findings
- Filtering and monitoring (3.2)
- Acceptable-use policies (3.3)
- Technical security (3.4)
- Staff training (4.3)
- Parental engagement (4.3)
- Online safety (4.4)
- Data protection (4.3)
- cybersafety knowledge and skills [34]
- motivation to establish and grow a cybersafety culture [28]
- leadership to ensure that the necessary cybersafety measures are in place
- commitment by parents/guardians to become involved in cybersafety education
- participation by learners [37]
- training opportunities for school teachers [28]
- school material (e.g., curriculum) [27]
- cybersafety policies and procedures at the government level [27]
- a monitoring and reporting system [40]
- social support for cyber victims in schools [41]
- planning documents
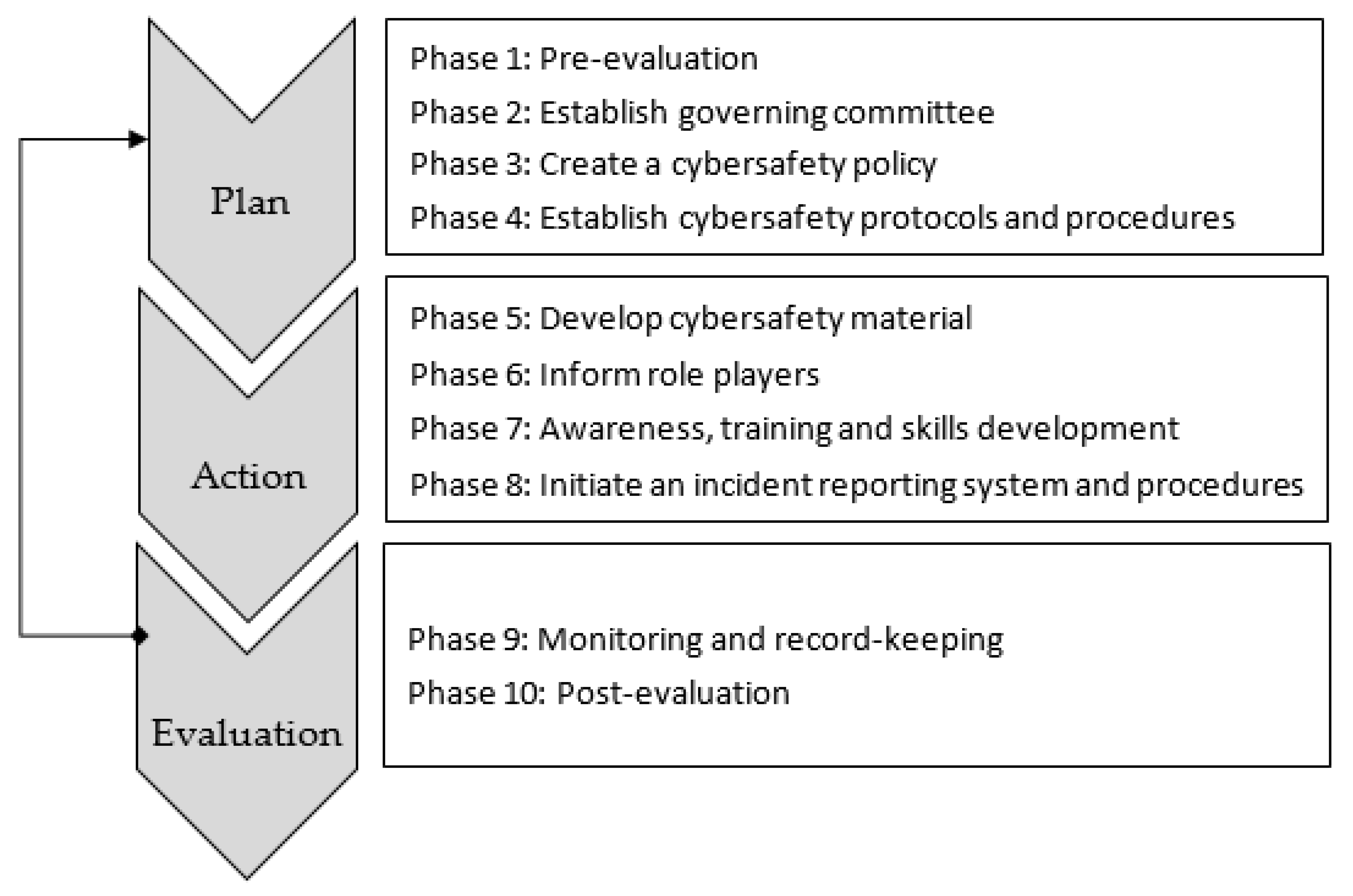
5. Proposed Cybersafety Maturity Guidelines for South Africa
6. Conclusions
Funding
Conflicts of Interest
References
- Barbosa, J. How to Educate to Build an Effective Cyber Resilient Society. Int. J. Cyber Res. Educ. 2020, 2, 55–72. [Google Scholar] [CrossRef]
- Randa, R. The in fluence of the cyber-social environment on fear of victimization: Cyberbullying and school. Secur. J. 2013, 26, 331–348. [Google Scholar] [CrossRef]
- Alotaib, F. Evaluation and Enhancement of Public Cyber Security Awareness; Unversity of Plymouth: Plymouth, UK, 2019. [Google Scholar]
- De Lange, M. Guidelines to Establish an e-Safety Awareness in South Africa; Nelson Mandela Metropolitan University: Port Elizabeth, South Africa, 2012. [Google Scholar]
- International Telecommunication Union. Global Cybersecurity Index (GCI) 2017. ITU-D Global, 2017. Available online: https://www.itu.int/dms_pub/itu-d/opb/str/D-STR-GCI.01-2017-PDF-E.pdf (accessed on 2 September 2020).
- Castilla, J.E.M.; Pursiainen, C. Cyberspace Effects on Civil Society. The Ultimate Game-Changer or Not? J. Civ. Soc. 2019, 15, 392–411. [Google Scholar] [CrossRef]
- Wright, M.F. Adolescents’ cyber aggression perpetration and cyber victimization: The longitudinal associations with school functioning. Soc. Psychol. Educ. 2015, 18, 653–666. [Google Scholar] [CrossRef]
- Rahman, A.; Malaysia, N.A.; Sairi, M.T.U.K.; Zizi, I.K.; Khalid, F. The Importance of Cybersecurity Education in School. Int. J. Inf. Educ. Technol. 2020, 10, 378–382. [Google Scholar] [CrossRef]
- DePaolis, K.; Williford, A. The Nature and Prevalence of Cyber Victimization among Elementary School Children. Child Youth Care Forum 2014, 44, 377–393. [Google Scholar] [CrossRef]
- De Barros, M.J.Z.; Lazarek, H. A Cyber Safety Model for Schools in Mozambique. In Proceedings of the 4th International Conference on Information Systems Security and Privacy, Funchal, Portugal, 22–24 January 2018; Scitepress: Setúbal, Portugal, 2018; pp. 251–258. [Google Scholar]
- Shariff, S.; Hoff, D.L. Cyber bullying: Clarifying Legal Boundaries for School Supervision in Cyberspace. Int. J. Cyber Criminol. 2007, 1, 76–118. [Google Scholar]
- Pencheva, D.; Hallett, J.; Rashid, A. Bringing Cyber to School: Integrating Cybersecurity into Secondary School Education. IEEE Secur. Priv. Mag. 2020, 18, 68–74. [Google Scholar] [CrossRef]
- Abawajy, J.H. User preference of cyber security awareness delivery methods. Behav. Inf. Technol. 2012, 33, 237–248. [Google Scholar] [CrossRef]
- Dlamini, Z.; Modise, M. Cyber Security Awareness Initiatives in South Africa: A Synergy Approach. In Proceedings of the 7th International Conference on Information Warfare and Security, Seattle, DC, USA, 22–23 March 2012; pp. 98–107. [Google Scholar]
- Smith, C. Cyber Security, Safety and Ethics Education; Utica College, ProQuest Publishing: Emeryville, CA, USA, 2018. [Google Scholar]
- Kritzinger, E. Cultivating a cyber-safety culture among school learners in South Africa cultivating a cybersafety culture. Afr. Educ. Rev. 2017, 14, 22–41. [Google Scholar] [CrossRef]
- Antoniadou, N.; Kokkinos, C. Cyber and school bullying: Same or different phenomena? Aggress. Violent Behav. 2015, 25, 363–372. [Google Scholar] [CrossRef]
- Gonzales, R.H. Social Media as a Channel and its Implications on Cyber Bullying. In Proceedings of the DLSU Research Congress, Manila, PH, USA, 20–22 June 2006; pp. 1–7. [Google Scholar]
- Von Solms, S.; Von Solms, R. Towards Cyber Safety Education in Primary Schools in Africa. In Proceedings of the Eighth International Symposium on Human Aspects of Information Security & Assurance (HAISA 2014), Plymouth, UK, 8–9 July 2014; pp. 185–197. [Google Scholar]
- Peterson, J.; Densley, J. Cyber violence: What do we know and where do we go from here? Aggress. Violent Behav. 2017, 34, 193–200. [Google Scholar] [CrossRef]
- Edwards, S.; Nolan, A.; Henderson, M.; Mantilla, A.; Plowman, L.; Skouteris, H. Young children’ s everyday concepts of the internet: A platform for cyber-safety education in the early years. Br. J. Educ. Technol. 2018, 49, 45–55. [Google Scholar] [CrossRef]
- Zwilling, M.; Lesjak, D.; Natek, S.; Phusavat, K.; Anussornnitisarn, P. How to Deal with the Awareness of Cyber Hazards and Security in (Higher) Education? Thriving on Future Education, Industry, Business and Society. In Proceedings of the MakeLearn and TIIM International Conference, Piran, Slovenia, 15–17 May 2019; pp. 433–439. [Google Scholar]
- Kritzinger, E.; Bada, M.; Nurse, J. A study into the cybersecurity awareness initiatives for school learners in South Africa and the UK. In Proceedings of the WISE 10 (IFIP), Shangai, China, 8–10 November 2017; pp. 1–11. [Google Scholar]
- Pelletier, R.; Handal, B.; Khalil, J.; Francis, T. Cyberbyllying-when does a school authority’s liabilty in tort end? West. Aust. Jurist. 2015, 6, 93–121. [Google Scholar]
- Srivastava, J.S. Cyber Crime: Kids as Soft Targets. Int. J. Innov. Comput. Sci. Eng. 2017, 4, 31–36. [Google Scholar]
- Miles, D. Youth Protection. In Proceedings of the Cybersecurity Summit (WCS), London, UK, 1–2 June 2011; pp. 1–3. [Google Scholar]
- Kortjan, N.; Von Solms, R. A conceptual framework for cyber security awareness and education in SA. S. Afr. Comput. J. 2014, 52, 29–41. [Google Scholar] [CrossRef]
- Govender, I.; Skea, B. Teachers’ Understanding of E-Safety: An Exploratory Case in KZN South Africa. Electron. J. Inf. Syst. Dev. Ctries. 2015, 70, 1–17. [Google Scholar] [CrossRef]
- Cilliers, L.; Chinyamurindi, W.T. Perceptions of cyber bullying in primary and secondary schools among student teachers in the Eastern Cape Province of South Africa. Electron. J. Inf. Syst. Dev. Ctries. 2020, e12131. [Google Scholar] [CrossRef]
- Scholtz, D.; Kritzinger, E.; Botha, A. Underpinning Knowledge and Skills for Educators to Enhance Cyber Safety Awareness in South African Schools. Bioinform. Res. Appl. 2019, 11937, 278–290. [Google Scholar] [CrossRef]
- Kempen, A. The 4th Industrial Revolution. Servamus 2019, 112, 10–12. [Google Scholar]
- Vishwanath, A.; Neo, L.S.; Goh, P.; Lee, S.; Khader, M.; Ong, G.; Chin, J. Cyber hygiene: The concept, its measure, and its initial tests. Decis. Support. Syst. 2020, 128, 113160. [Google Scholar] [CrossRef]
- Von Solms, R.; Von Solms, S. Cyber Safety Education in Developing Countries. In Proceedings of the 9th International Multi-Conference on Society, Cybernetics and Informatics, Proceedings (IMSCI 2015), George, South Africa, 11–12 December 2015; pp. 173–178. [Google Scholar]
- De Lange, M.; Von Solms, R. An e-Safety Educational Framework in South Africa. In Proceedings of the Southern Africa Telecommunication Networks and Applications Conference (SATNAC), George, South Africa, 2–5 September 2012. [Google Scholar]
- Mashiane, T.; Dlamini, Z.; Mahlangu, T. A rollout strategy for cybersecurity awareness campaigns. In Proceedings of the 14th International Conference on Cyber Warfare and Security (ICCWS 2019), Stellenbosch, South Africa, 28 February–1 March 2019; pp. 243–250. [Google Scholar]
- Grobler, M.; Flowerday, S.; Von Solms, R.; Venter, H. Cyber Awareness Initiatives in South Africa: A National Perspective. In Proceedings of the First IFIP TC9/TC11 South African Cyber Security Awareness Workshop (SACSAW) 2011, Gaborone, Botswana, 12 May 2011; pp. 32–41. [Google Scholar]
- UNICEF. Your People’s Navigation of Online Risks 2012. Available online: http://goo.gl/hqaXJ9 (accessed on 10 March 2014).
- Grobler, M.; Dlamini, Z. Global Cyber Trends a South African Reality. In Proceedings of the IST-Africa 2012 Conference, Dar es Salaam, Dar es Salaam, Tanzania, 9–11 May 2012; pp. 1–8. [Google Scholar]
- Kyobe, M.E.; Mimbi, L.; Nembandona, P.; Mtshazi, S. Mobile Bullying Among Rural South African Students: Examining the Applicability of Existing Theories. Afr. J. Inf. Syst. 2018, 10, 1. [Google Scholar]
- Odora, R.J. The Nature and Prevalence of Cyber Bullying Behaviors among South African High School Learners. Int. J. Educ. Sci. 2015, 10, 399–409. [Google Scholar] [CrossRef][Green Version]
- Sonhera, N.; Kritzinger, E.; Loock, M. Cyber Threat Incident Handling Procedure for South African Schools. In Proceedings of the Ninth International Symposium on Human Aspects of Information Security & Assurance (HAISA 2015), Lesvos, Greece, 1–3 July 2015; pp. 215–232. [Google Scholar]
- Bada, M.; Von Solms, B.; Agrafiotis, I. Reviewing National Cybersecurity Awareness in Africa: An Empirical Study. In Proceedings of the Third International Conference on Cyber-Technologies and Cyber-Systems, CYBER 2018, Athens, Greece, 18–22 November 2018; pp. 78–83. [Google Scholar]
- Vogel, R. Closing the Cybersecurity Skills Gap. Salus. J. 2016, 4, 32–46. [Google Scholar]
- Kritzinger, E. Short-term initiatives for enhancing cyber-safety within South African schools. S. Afr. Comput. J. 2016, 28, 1–17. [Google Scholar] [CrossRef]


| Element A: Policy and Leadership | ||
| Strand 1: Responsibility | ||
| A1.1. | Online safety group | This aspect describes how the school manages its online safety strategy involving a group with wide-ranging representation. |
| A1.2. | Online safety responsibilities | This aspect describes the roles of those responsible for the school’s online safety strategy. |
| A1.3. | Governors | This aspect describes the online safety accountabilities of the school’s Board of Directors, and how the school ensures this influences policy. |
| Strand 2: Policies | ||
| A2.1. | Policy development | This aspect describes the process of establishing an effective online safety policy involving the stakeholders and their responsibilities, consultation, communication, review and impact. |
| A2.2. | Policy scope | This aspect considers policy content, its breadth in terms of technology and expectations around behaviour, and its relevance to current social trends and educational developments. |
| A2.3. | Acceptable use | This aspect considers how the school communicates its expectations regarding acceptable use of technology and the steps towards successfully implementing these expectations within the school. |
| A2.4. | Self-evaluation | This aspect describes how the online safety self-evaluation process builds upon and aligns with other self-evaluation mechanisms. |
| A2.5. | Whole school | This aspect describes how the online safety policy is consistent with school expectations in other relevant policies/safeguarding practices and vice versa (e.g., behaviour, anti-bullying and preventative action plans). |
| A2.6. | Managing unacceptable use | This aspect considers the actions the school may take and the strategies it employs in response to misuse. There is evidence that responsible use is acknowledged through celebration and reward. |
| A2.7. | Reporting | This aspect describes the routes and mechanisms the school provides for its community to report abuse and misuse. |
| Strand 3: Communications and communications technology | ||
| A3.1. | Mobile technology | This aspect considers the benefits and challenges of mobile technologies, and their use in a school environment and beyond. |
| A3.2. | Social media | This aspect covers the use of social media in and by the school and where appropriate, beyond the school. It considers how the school can educate all users about the responsible use of social media. |
| A3.3. | Digital and video images | This aspect describes how the school manages the use and publication of digital and video images in relation to the requirements of the data protection act. |
| A3.4. | Public online communications | This aspect describes how the school manages its public-facing online communications in both managing risk, and disseminating online safety advice, information and practice. |
| A3.5. | Professional standards | This aspect describes how staff’s use of technology complies with both school policy and professional standards. |
| Element B: Infrastructure | ||
| Strand 1: Passwords | ||
| B1.1. | Password security | This aspect covers the ability of the school to ensure the security of its systems and data through good password policy and practice. |
| Strand 2: Services | ||
| B2.1. | Filtering and monitoring | This aspect describes how the online safety policy is consistent with school expectations in other relevant policies/safeguarding practices. |
| B2.2. | Technical security | This aspect describes the ability of the school to understand and ensure reasonable duty of care regarding the technical and physical security of administrative and curriculum networks. |
| B2.3. | Data protection | This aspect describes the ability of the school to be compliant with the current Protection of Personal Information Act. Note this section was adapted to the POPI Act within South Africa (No 4 of 2013). |
| Element C: Education | ||
| Strand 1: Children and young people | ||
| C1.1. | Online safety education | This aspect describes how the school builds resilience in its learners/students through an effective online safety education program. |
| C1.2. | Digitalliteracy | This aspect describes how the school develops the ability of young people to find, evaluate, use, share and create digital content in a way that minimises risk and promotes positive outcomes. |
| C1.3. | Contribution of young people | This aspect describes how the school maximises the potential of young people’s knowledge and skills in shaping an online safety strategy for the school. |
| Strand 2: Staff | ||
| C2.1. | Staff training | This aspect describes the effectiveness of the school’s online safety development programme for staff, and how it prepares and empowers staff to educate and to intervene in issues when they arise. |
| Strand 3: Governors | ||
| C3.1. | Governor education | This aspect describes the school’s provision of online safety education for governors (Board of Directors) to support them in the execution of their roles. |
| Strand 4: Parents and carers | ||
| C4.1. | Parental engagement | This aspect describes how the school educates and informs parents and carers on issues relating to online safety, including support in establishing effective online safety strategies for the family. |
| Strand 5: Community | ||
| C5.1. | Community engagement | This aspect describes how the school communicates and shares best practices with the wider community, including local people, agencies and organisations. |
| Element D: Standards and inspection | ||
| Strand 1: Monitoring | ||
| D1.1. | Monitoring and reporting safety incidents | This aspect covers the school’s effectiveness in monitoring and recording online safety incidents, including its response to such incidents and how the online safety strategy is informed. |
| D1.2. | Online safety policy and practices | This aspect covers the effectiveness of the school’s online safety strategy, the evidence used to evaluate impact, and how such evidence shapes developments in policy and practice. |
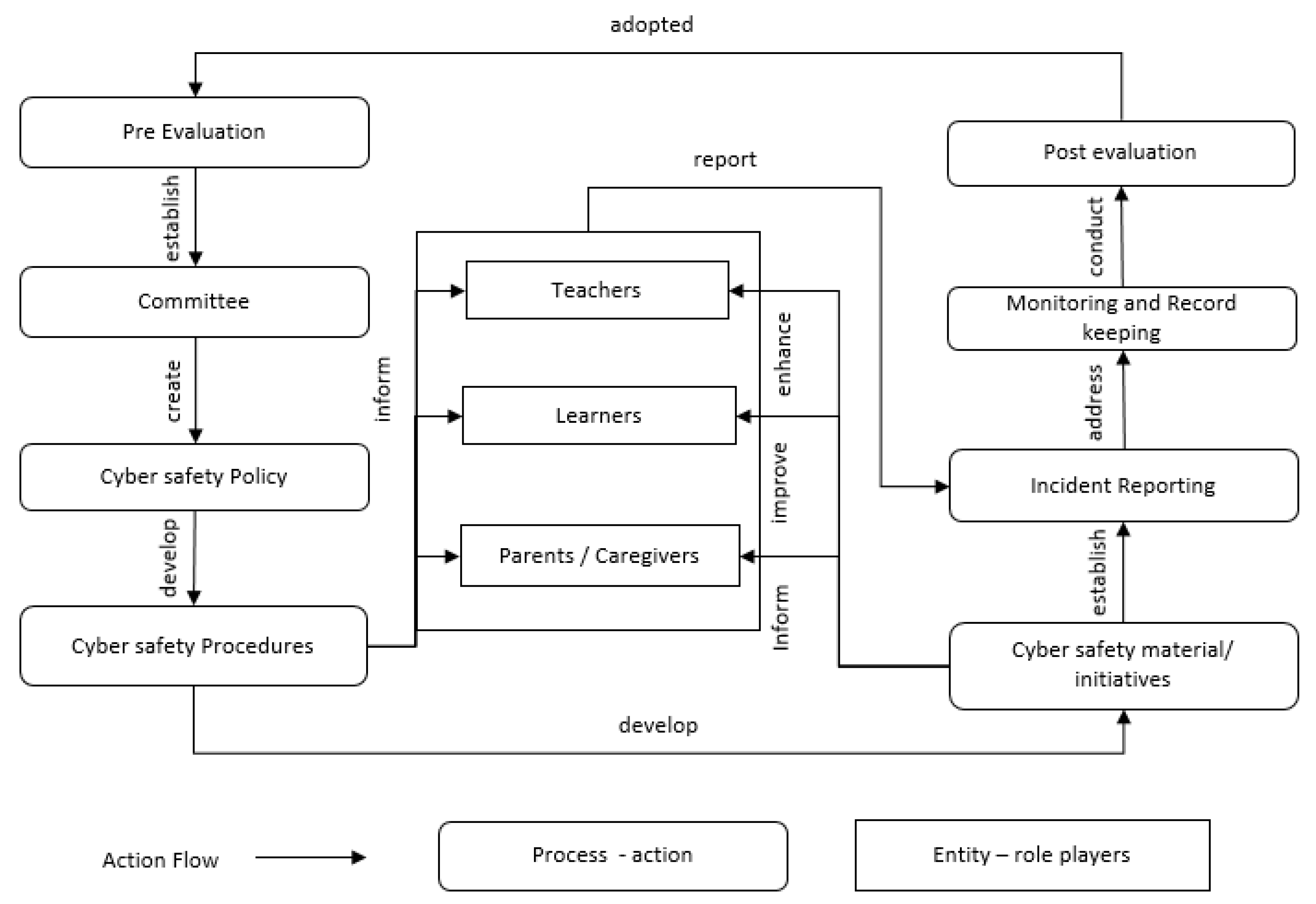
| Phase 1: Pre-Evaluation | |
| 1.1. | Delineate existing/prior knowledge and skills of learners and teachers |
| 1.2. | Identify funding and resources available for cybersafety activities |
| 1.3. | Determine teachers’ and learners’ access to technology |
| 1.4. | Determine current cybersafety culture within the school |
| 1.5. | Evaluate existing cybersafety material |
| Phase 2: Establish Governing Committee | |
| 2.1. | Establish the cybersafety committee (part of the ICT committee) |
| 2.2. | Identify the school’s responsiveness towards cybersafety |
| 2.3. | Establish management protocols and governance procedures |
| 2.4. | Assign management committee responsibilities |
| 2.5. | Initiate a consultation process with representatives from the Department of Education |
| 2.6. | Consult with legal representation |
| 2.7. | Identify risk factors for risk register |
| 2.8. | Identify success indicators |
| Phase 3: Create a Cybersafety Policy | |
| 3.1. | Design a cybersafety policy/acceptable-use policy (AUP) (or adapt existing document) |
| 3.2. | Create protocol for supporting structure related to cyber incidents |
| Phase 4: Establish Cybersafety Protocols and Procedures to Support Policy | |
| 4.1. | Infrastructure |
| 4.2. | Education (awareness, training and skills development) |
| 4.3. | Implementation process |
| 4.4. | Reporting |
| 4.5. | Monitoring and measuring |
| 4.6. | Pre-evaluation |
| Phase 5: Develop Cybersafety Material | |
| 5.1. | Identify role players and their responsibility for developing material |
| 5.2. | Initiate consultation process with designing team |
| 5.3. | Identify training programs for teachers |
| Phase 6: Inform Role Players | |
| 6.1. | Consultation process with external role players |
| 6.2. | Consultation process with teachers |
| 6.3. | Consultation process with parents |
| 6.4. | Consultation process with learners |
| Phase 7: Awareness, Training and Skills Development | |
| 7.1. | Increase knowledge and skills of teacher |
| 7.2. | Improve awareness of learner |
| 7.3. | Advise parents and care givers |
| Phase 8: Incident-Reporting System and Procedures | |
| 8.1. | Implement reporting system and procedures |
| 8.2. | Inform all role players of process regarding the reporting of incidents |
| Phase 9: Monitoring and Record-Keeping | |
| 9.1. | Implement monitoring process |
| 9.2. | Implement record-keeping process |
| 9.3. | Identify the audit process of monitoring and record-keeping |
| 9.4. | Establish reported process |
| Phase 10: Post-Evaluation | |
| 10.1. | Evaluate/measure success indicators |
| 10.2. | Revise policies |
© 2020 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kritzinger, E. Improving Cybersafety Maturity of South African Schools. Information 2020, 11, 471. https://doi.org/10.3390/info11100471
Kritzinger E. Improving Cybersafety Maturity of South African Schools. Information. 2020; 11(10):471. https://doi.org/10.3390/info11100471
Chicago/Turabian StyleKritzinger, Elmarie. 2020. "Improving Cybersafety Maturity of South African Schools" Information 11, no. 10: 471. https://doi.org/10.3390/info11100471
APA StyleKritzinger, E. (2020). Improving Cybersafety Maturity of South African Schools. Information, 11(10), 471. https://doi.org/10.3390/info11100471





