Review of the D2D Trusted Cooperative Mechanism in Mobile Edge Computing
Abstract
1. Introduction
2. Concept and Architecture of the MEC Trusted Cooperative Mechanism
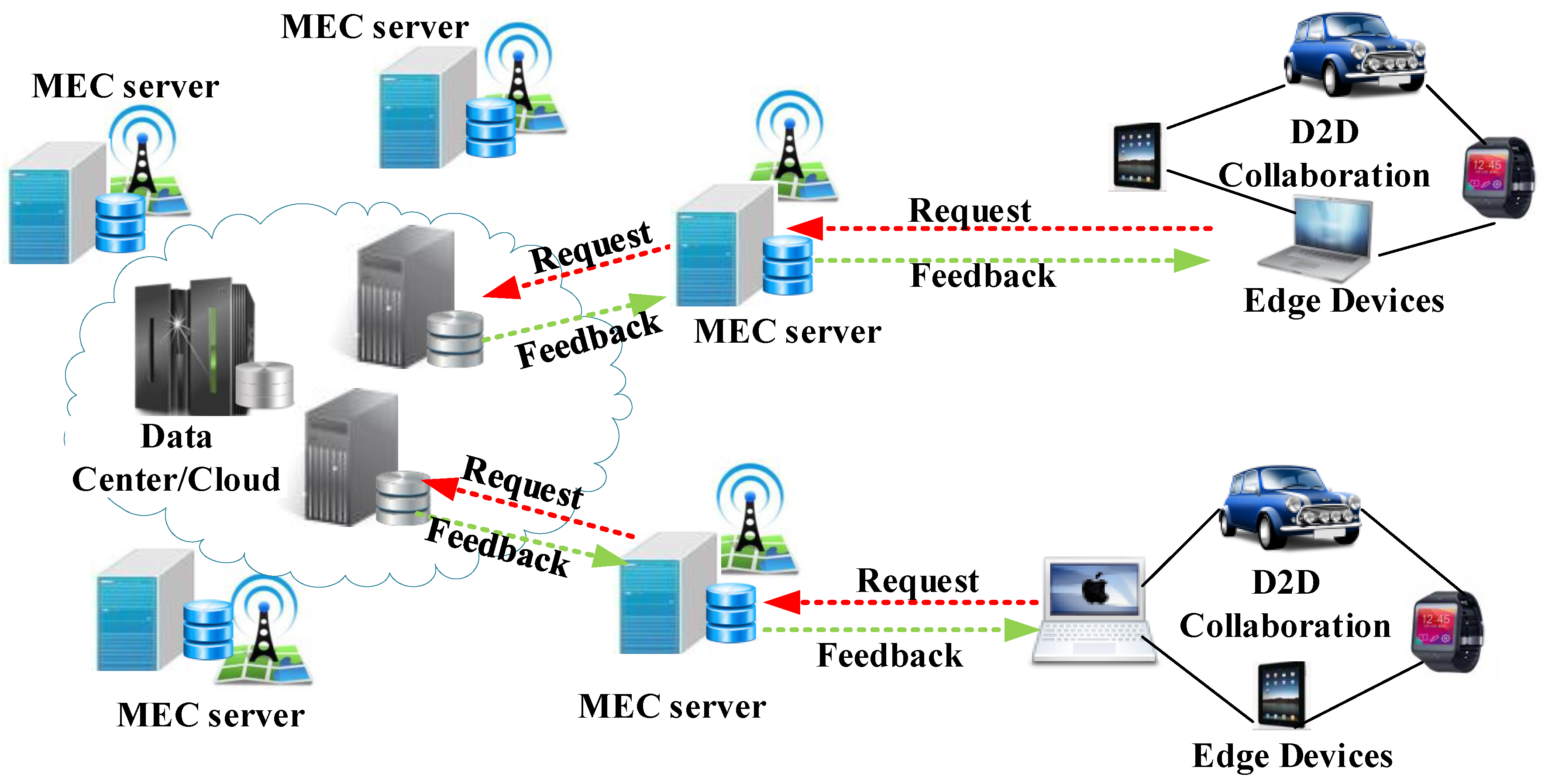
2.1. Mobile Edge Computing Architecture and Applications
2.2. D2D Trusted Cooperative Mechanism in MEC
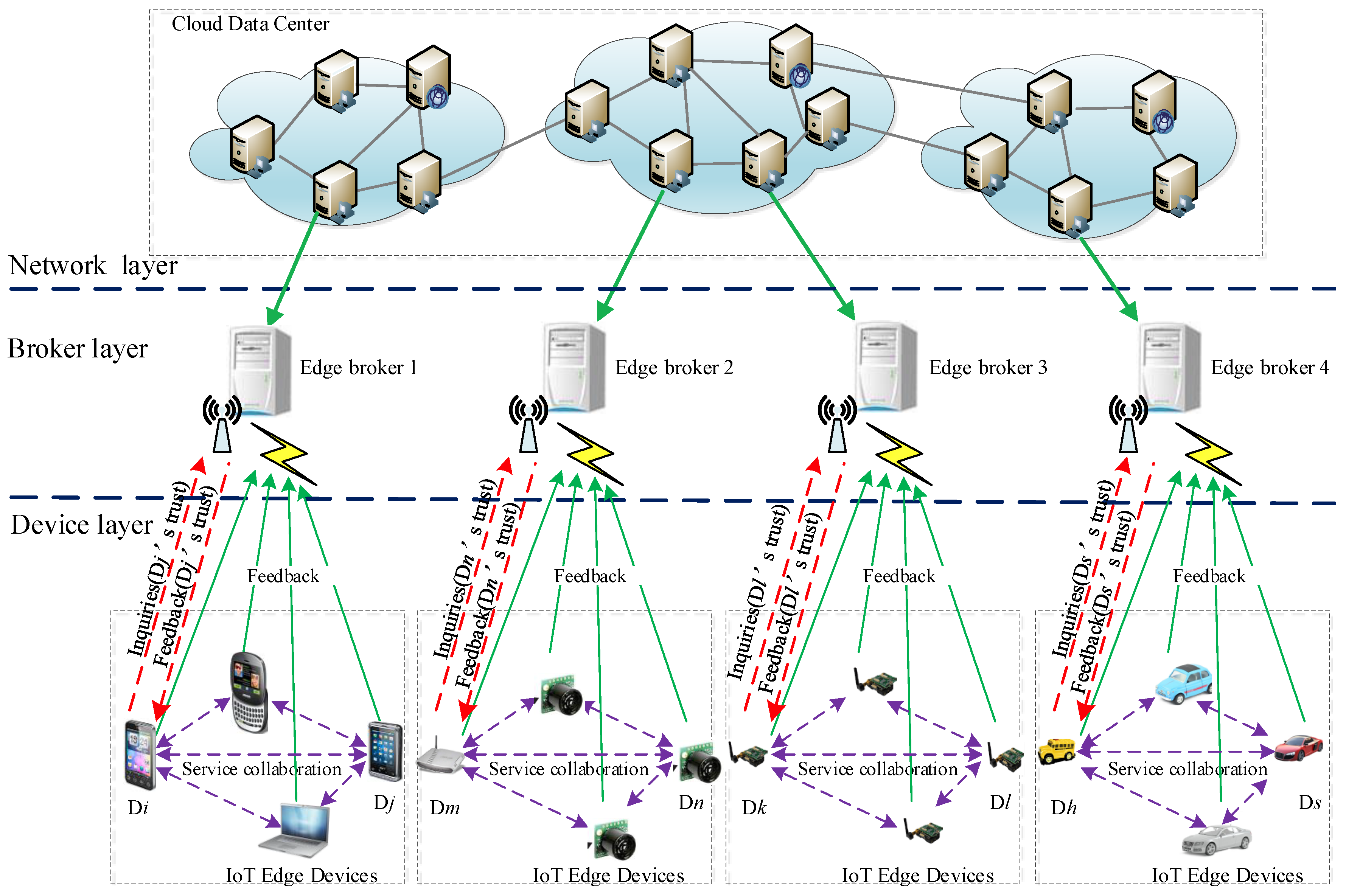
- The network layer is supported by the traditional cloud computing platform. The central server that hosts the master database is located within a professionally-managed cloud data center. Cloud computing promises more power, safer data, and easier access to the information and tools needed for successful implementation in any industry or organization compared with the alternatives. In this condition, we can assume that the cloud data center is reliable and always available, while attacks and other risks to the central server are beyond the scope of this work.
- The broker layer is used to monitor the service behavior of devices and aggregate the feedback from these devices. In an open edge computing environment, a large number of undependable (or malicious) devices and feedback from these undependable devices may yield incorrect evaluation results. However, the limited work at present mainly focuses on a reliable feedback mechanism for an edge computing environment. Hence, we extend traditional feedback mechanisms such that feedback can come not only from devices, but also from brokers, thus effectively reducing networking risk and improving system reliability. More importantly, different from traditional feedback aggregation mechanisms, the trust aggregate calculation based on feedback information is entirely derived from brokers. This approach can reduce the energy costs of devices and render the proposed trust mechanism a lightweight scheme from the perspective of client energy cost.
- The device layer consists of various edge devices. In the process of service coordination, multiple participating devices communicate with the brokers through the Internet via WiFi or cellular access points. The devices are divided into different domains based on their location, and each domain is managed by a broker. In the area of wireless computer networking, the broker is derived from the BS. A radio receiver/transmitter serves as the hub of the local wireless network, and it may also serve as the gateway between a wired network and the wireless network. The device layer typically consists of a low-power transmitter and wireless router. After completing a service collaboration, both devices will submit mutual evaluation information to the broker. Before the collaborative service of the two devices, a device will send a request message to its broker to ensure the trustworthiness of the collaborator.
2.3. Classification of the Trusted Cooperative Mechanism
2.4. Trusted Edge Computing Network Control Structure
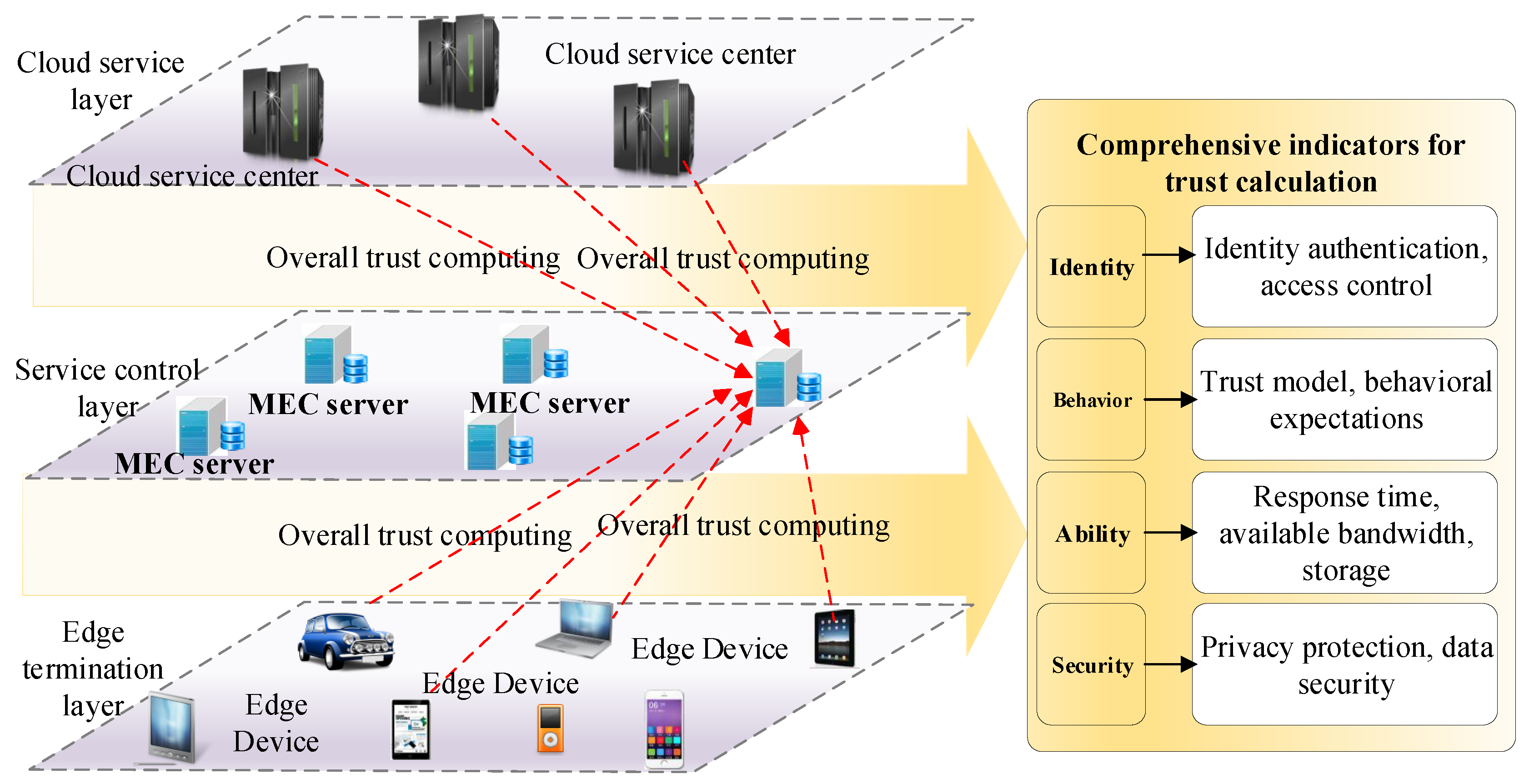
- Trust of identity: This indicator is mainly used to confirm the uniqueness of an entity and decide whether the entity can be authorized. The main considerations are identity authentication, access control, common technologies for authentication, authorization, encryption, data hiding, digital signature, public-key certificate, and access control policy.
- Trust of behavior: The entity’s historical behavior record and current behavior characteristics are used to judge the entity’s trust and behavioral expectation dynamically, and the access and service authority are given according to the trust of the entity, which is undeniable and authoritative. In different network environments, the trust evaluation model of an entity’s behavior is extremely extensive. Obtaining the trust value of the entity through direct evaluation and indirect evaluation and performing an aggregation algorithm calculation are therefore proposed.
- The capability of trust: This indicator refers to the ability and reliability of the entity’s response time, available bandwidth, storage space, computing power, and mission execution success rate. In the field of trusted computing, previous types of trusted computer systems were based entirely on the assumption that hardware devices and network communications were secure and reliable. However, in actual large-scale edge computing network environments, hardware devices or network communications are highly likely to be unstable and unreliable during the interaction process. The trust of the edge devices is perceived and monitored in a trusted computer system. Moreover, dynamic measurement is a necessary indicator.
- Security of MEC: This indicator comprehensively considers the security credibility of entities from the aspects of privacy protection, data security, and sharing security. In large-scale MEC network environments, users do not want their privacy, personal data, personal behavior characteristics, and other information to be mastered by the server or the cloud. After processing the user information, the mobile edge device extracts the necessary information and uploads the result to the cloud server, which greatly enhances the privacy protection of the user, ensures data security, and guarantees shared security. Therefore, the trust evaluation of the security of the edge devices in terms of privacy protection, data security, and sharing security is also an important indicator.
3. Existing Trusted Cooperative Relation Models
3.1. Trusted Cooperative Relation Model Based on Social Trust
3.2. Trusted Cooperative Relation Model Based on Authentication Techniques
3.3. Trusted Cooperative Relation Model Based on Intrusion Detection
3.4. Comparison of Trusted Cooperative Relation Models for MEC
4. Conclusions and Future Directions
- Trusted MEC application and deployment: We can combine trust management with incentive mechanisms to encourage collaboration across devices. Implementing and evaluating our proposed trust calculation mechanism on various edge computing systems, such as distributed file sharing, is an important direction of future research.
- Overall trust adaptive computing: We should fully consider the weight distribution issue in the fused computation of direct trust and feedback trust. The implementation of convergence and the accurate, rapid, objective, and dynamic computing of overall trust evaluation and prediction are also important directions of future research.
- Trusted data acquisition and storage: The main tasks of trusted data collection include identity data, behavior data, security data, and capability data. The efficient data collection mechanism for calculating direct trust and feedback is a basic task for deploying trusted MEC applications.
- Trust analysis and calculation: Trust analysis and calculation include three core tasks: direct trust calculation, feedback trust calculation, and overall trust fusion calculation. By adopting an effective adaptive machine learning algorithm, we can accurately calculate and predict direct trust, feedback trust, and overall trust. According to the result of the trust calculation, the related mobile node can perform access control authorization.
- Seamless integration of trusted collaboration mechanisms with existing mobile IoT systems: The mobility of the mobile IoT environment and the characteristics of nodes belonging to different management domains can be combined. In this manner, a high-trust network collaborative management framework based on identity trust and behavior trust can be achieved by the domain. Moreover, the trustworthy behavior between domains can be fed back and monitored, and complex management is established. The network environment and the various external interferences can then achieve stability and adaptive reliability in the MEC network.
Funding
Acknowledgments
Conflicts of Interest
References
- Mach, P.; Becvar, Z. Mobile edge computing: A survey on architecture and computation offloading. IEEE Commun. Surv. Tutor. 2017, 19, 1628–1656. [Google Scholar] [CrossRef]
- Mao, Y.; Zhang, J.; Letaief, K.B. Dynamic computation offloading for mobile-edge computing with energy harvesting devices. IEEE J. Sel. Areas Commun. 2016, 34, 3590–3605. [Google Scholar] [CrossRef]
- Abbas, N.; Zhang, Y.; Taherkordi, A.; Skeie, T. Mobile edge computing: A survey. IEEE Internet Things J. 2017, 5, 450–465. [Google Scholar] [CrossRef]
- Tran, T.X.; Hajisami, A.; Pandey, P.; Pompili, D. Collaborative mobile edge computing in 5G networks: New paradigms, scenarios, and challenges. arXiv 2016, arXiv:1612.03184. [Google Scholar] [CrossRef]
- Hu, Y.C.; Patel, M.; Sabella, D.; Sprecher, N.; Young, V. Mobile edge computing—A key technology towards 5G. ETSI White Pap. 2015, 11, 1–16. [Google Scholar]
- Rimal, B.P.; Van, D.P.; Maier, M. Mobile edge computing empowered fiber-wireless access networks in the 5G era. IEEE Commun. Mag. 2017, 55, 192–200. [Google Scholar] [CrossRef]
- Yu, Y. Mobile edge computing towards 5G: Vision, recent progress, and open challenges. China Commun. 2016, 13, 89–99. [Google Scholar] [CrossRef]
- Fajardo, J.O.; Liberal, F.; Giannoulakis, I.; Kafetzakis, E.; Pii, V.; Trajkovska, I.; Bohnert, T.M.; Goratti, L.; Riggio, R.; Lloreda, J.O. Introducing mobile edge computing capabilities through distributed 5G cloud enabled small cells. Mob. Netw. Appl. 2016, 21, 564–574. [Google Scholar] [CrossRef]
- Wang, S.; Zhao, Y.; Xu, J.; Yuan, J.; Hsu, C.H. Edge server placement in mobile edge computing. J. Parallel Distrib. Comput. 2019, 127, 160–168. [Google Scholar] [CrossRef]
- Bellavista, P.; Belli, D.; Chessa, S.; Foschini, L. A Social-Driven Edge Computing Architecture for Mobile Crowd Sensing Management. IEEE Commun. Mag. 2019, 57, 68–73. [Google Scholar] [CrossRef]
- Cui, Q.; Gong, Z.; Ni, W.; Hou, Y.; Chen, X.; Tao, X.; Zhang, P. Stochastic Online Learning for Mobile Edge Computing: Learning from Changes. IEEE Commun. Mag. 2019, 57, 63–69. [Google Scholar] [CrossRef]
- Zhang, F.; Liu, G.; Zhao, B.; Fu, X.; Yahyapour, R. Reducing the network overhead of user mobility–induced virtual machine migration in mobile edge computing. Softw. Pract. Exp. 2019, 49, 673–693. [Google Scholar] [CrossRef]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge computing: Vision and challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Mao, Y.; You, C.; Zhang, J.; Huang, K.; Letaief, K.B. A Survey on Mobile Edge Computing: The Communication Perspective. IEEE Commun. Surv. Tutor. 2017, 19, 2322–2358. [Google Scholar] [CrossRef]
- Ahmed, E.; Akhunzada, A.; Whaiduzzaman, M.; Gani, A.; Ab Hamid, S.H.; Buyya, R. Network-centric performance analysis of runtime application migration in mobile cloud computing. Simul. Model. Pract. Theory 2015, 50, 42–56. [Google Scholar] [CrossRef]
- Pace, P.; Aloi, G.; Gravina, R.; Caliciuri, G.; Fortino, G.; Liotta, A. An Edge-based Architecture to Support Efficient Applications for Healthcare Industry 4.0. IEEE Trans. Ind. Inform. 2018, 15, 481–489. [Google Scholar] [CrossRef]
- Wazir, Z.; Ejaz, A.; Saqib, H.; Ibrar, Y.; Arif, A. Edge computing: A survey. Future Gener. Comput. Syst. 2019, 97, 219–235. [Google Scholar]
- Habak, K.; Zegura, E.W.; Ammar, M.; Harras, K.A. Workload management for dynamic mobile device clusters in edge femtoclouds. In Proceedings of the Second ACM/IEEE Symposium on Edge Computing, San Jose/Fremont, CA, USA, 12–14 October 2017; pp. 1–14. [Google Scholar]
- Habak, K.; Ammar, M.; Harras, K.A.; Zegura, E. Femto Clouds: Leveraging Mobile Devices to Provide Cloud Service at the Edge. In Proceedings of the 2015 IEEE 8th International Conference on Cloud Computing, New York, NY, USA, 27 June–2 July 2015. [Google Scholar]
- He, Y.; Yu, F.R.; Zhao, N.; Yin, H. Secure Social Networks in 5G Systems with Mobile Edge Computing, Caching, and Device-to-Device Communications. IEEE Wirel. Commun. 2018, 25, 103–109. [Google Scholar] [CrossRef]
- Yuan, J.; Li, X. A multi-source feedback based trust calculation mechanism for edge computing. In Proceedings of the IEEE INFOCOM 2018—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Honolulu, HI, USA, 15–19 April 2018; pp. 819–824. [Google Scholar]
- Mtibaa, A.; Harras, K.; Alnuweiri, H. Friend or Foe Detecting and Isolating Malicious Nodes in Mobile Edge Computing Platforms. In Proceedings of the IEEE 7th International Conference on Cloud Computing Technology & Science, Vancouver, BC, Canada, 30 November–3 December 2015. [Google Scholar]
- Vassilakis, V.; Chochliouros, I.P.; Spiliopoulou, A.S.; Sfakianakis, E.; Belesioti, M.; Bompetsis, N.; Wilson, M. Security analysis of mobile edge computing in virtualized small cell networks. In Proceedings of the IFIP International Conference on Artificial Intelligence Applications and Innovations, Thessaloniki, Greece, 16–18 September 2016; Springer: Cham, Switzerland, 2016; pp. 653–665. [Google Scholar]
- He, D.; Chan, S.; Guizani, M. Security in the internet of things supported by mobile edge computing. IEEE Commun. Mag. 2018, 56, 56–61. [Google Scholar] [CrossRef]
- Stojmenovic, I.; Wen, S.; Huang, X.; Luan, H. An overview of fog computing and its security issues. Concurr. Comput. Pract. Exp. 2016, 28, 2991–3005. [Google Scholar] [CrossRef]
- Liu, H.; Zhang, Y.; Yang, T. Blockchain-enabled security in electric vehicles cloud and edge computing. IEEE Netw. 2018, 32, 78–83. [Google Scholar] [CrossRef]
- Mollah, M.B.; Azad, M.A.K.; Vasilakos, A. Security and privacy challenges in mobile cloud computing: Survey and way ahead. J. Netw. Comput. Appl. 2017, 84, 38–54. [Google Scholar] [CrossRef]
- Huang, X.; Yu, R.; Kang, J.; Zhang, Y. Distributed reputation management for secure and efficient vehicular edge computing and networks. IEEE Access 2017, 5, 25408–25420. [Google Scholar] [CrossRef]
- Roman, R.; Lopez, J.; Mambo, M. Mobile edge computing, Fog et al.: A survey and analysis of security threats and challenges. Future Gener. Comput. Syst. 2016, 78, 680–698. [Google Scholar] [CrossRef]
- Azzedin, F.; Ridha, A. Feedback behavior and its role in trust assessment for peer-to-peer systems. Telecommun. Syst. 2010, 44, 253–266. [Google Scholar] [CrossRef]
- Li, X.; Ma, H.; Zhou, F.; Gui, X. Service Operator-Aware Trust Scheme for Resource Matchmaking across Multiple Clouds. IEEE Trans. Parallel Distrib. Syst. 2015, 26, 1419–1429. [Google Scholar] [CrossRef]
- Li, X.; Ma, H.; Zhou, F.; Gui, X. T-Broker: A Trust-Aware Service Brokering Scheme for Multiple Cloud Collaborative Services. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1402–1415. [Google Scholar]
- Li, X.; Yuan, J.; Ma, H.; Yao, W. Fast and Parallel Trust Computing Scheme Based on Big Data Analysis for Collaboration Cloud Service. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1917–1931. [Google Scholar] [CrossRef]
- Yuan, J.; Li, X. A Reliable and Lightweight Trust Computing Mechanism for IoT Edge Devices Based on Multi-Source Feedback Information Fusion. IEEE Access 2018, 6, 23626–23638. [Google Scholar] [CrossRef]
- Yuan, J.; Li, X. A Broker-Guided Trust Calculation Model for Mobile Devices of D2D Communications. In Proceedings of the 2018 IEEE Symposium on Computers and Communications (ISCC), Natal, Brazil, 25–28 June 2018; pp. 1–6. [Google Scholar]
- Li, J.; Li, X.; Gao, Y.; Yuan, J.; Fang, B. Dynamic Trustworthiness Overlapping Community Discovery in Mobile Internet of Things. IEEE Access 2018, 6, 74579–74597. [Google Scholar] [CrossRef]
- Li, X.; Zhou, F.; Yang, X. A multi-dimensional trust evaluation model for large-scale P2P computing. J. Parallel Distrib. Comput. 2011, 71, 837–847. [Google Scholar] [CrossRef]
- Li, X.Y.; Gui, X.L. Research on dynamic trust model for large scale distributed environment. J. Softw. 2007, 18, 1510–1521. [Google Scholar] [CrossRef]
- Li, X.; Zhou, F.; Yang, X. Scalable feedback aggregating (SFA) overlay for large-scale P2P trust management. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 1944–1957. [Google Scholar] [CrossRef]
- Sicari, S.; Rizzardi, A.; Grieco, L.A.; Coen-Porisini, A. Security, privacy and trust in Internet of Things: The road ahead. Comput. Netw. 2015, 76, 146–164. [Google Scholar] [CrossRef]
- Lu, Z.; Qu, G.; Liu, Z. A survey on recent advances in vehicular network security, trust, and privacy. IEEE Trans. Intell. Transp. Syst. 2018, 20, 760–776. [Google Scholar] [CrossRef]
- Tang, J.; Ibrahim, M.; Chakrabarty, K.; Karri, R. Security and Trust, Secure and Trustworthy Cyberphysical Microfluidic Biochips; Springer: Cham, Switzerland, 2020; pp. 19–49, Unpublished. [Google Scholar]
- Jain, A.K.; Tokekar, V.; Shrivastava, S. Security Enhancement in MANETs Using Fuzzy-Based Trust Computation Against Black Hole Attacks. In Information and Communication Technology; Springer: Singapore, 2018; pp. 39–47. [Google Scholar]
- Paul, A.B.; Biswas, S.; Nandi, S.; Chakraborty, S. MATEM: A unified framework based on trust and MCDM for assuring security, reliability and QoS in DTN routing. J. Netw. Comput. Appl. 2018, 104, 1–20. [Google Scholar] [CrossRef]
- Tewari, A.; Gupta, B.B. Security, privacy and trust of different layers in Internet-of-Things (IoTs) framework. Future Gener. Comput. Syst. 2018, in press. [Google Scholar] [CrossRef]
- Peccoud, J.; Gallegos, J.E.; Murch, R.; Buchholz, W.G.; Raman, S. Cyberbiosecurity: From naive trust to risk awareness. Trends Biotechnol. 2018, 36, 4–7. [Google Scholar] [CrossRef]
- Palattella, M.R.; Dohler, M.; Grieco, A.; Rizzo, G.; Torsner, J.; Engel, T.; Ladid, L. Internet of Things in the 5G Era: Enablers, Architecture and Business Models. IEEE J. Sel. Areas Commun. 2016, 34, 510–527. [Google Scholar] [CrossRef]
- Wang, S.; Zhang, X.; Zhang, Y.; Wang, L.; Yang, J.; Wang, W. A Survey on Mobile Edge Networks: Convergence of Computing, Caching and Communications. IEEE Access 2017, 5, 6757–6779. [Google Scholar] [CrossRef]
- Nathan, C. What Is Multi-access Edge Computing? 2017. Available online: https://www.rcrwireless.com/20170707/wireless/what-is-mobile-edge-computing-tag27 (accessed on 21 May 2019).
- Rani, V.U.; Sundaram, K.S. Review of Trust Models in Wireless Sensor Networks. Int. Sch. Sci. Res. Innov. 2014, 8, 371–377. [Google Scholar]
- Echeverra, S.; Klinedinst, D.; Williams, K.; Lewis, G.A. Establishing Trusted Identities in Disconnected edge environment. In Proceedings of the 2016 IEEE/ACM Symposium on Edge Computing (SEC), Washington, DC, USA, 27–28 October 2016. [Google Scholar]
- Cui, J.; Wei, L.; Zhang, J.; Xu, Y.; Zhong, H. An Efficient Message-Authentication Scheme Based on Edge Computing for Vehicular Ad Hoc Networks. IEEE Trans. Intell. Transp. Syst. 2018, 20, 1621–1632. [Google Scholar] [CrossRef]
- Goh, S.T.; Pang, H.H.; Deng, R.H.; Bao, F. Three Architectures for Trusted Data Dissemination in Edge Computing. Data Knowl. Eng. 2006, 58, 381–409. [Google Scholar] [CrossRef]
- Kozik, R.; Chora, M.; Ficco, M.; Palmieri, F. A scalable distributed machine learning approach for attack detection in edge computing environments. J. Parallel Distrib. Comput. 2018, 119, 18–26. [Google Scholar] [CrossRef]
| Trusted Cooperative Relation Model | Basics | Network Latency | Calculation Efficiency |
|---|---|---|---|
| Ying et al. [20] | Social Trust | Medium | Low |
| Habak et al. [18] | Social Trust | Low | Medium |
| Yuan et al. [34] | Social Trust | Low | High |
| Huang et al. [28] | Reputation | Low | Medium |
| Echeverria et al. [51] | Authentication | Medium | High |
| Cui et al. [52] | Authentication | Low | Medium |
| Goh et al. [53] | Authentication | Medium | High |
| Mtibaa et al. [22] | Intrusion Detection | Low | Medium |
| Kozik et al. [54] | Intrusion Detection | High | Low |
| Trusted Cooperative Relation Model | Reliability | Scalability | Memory Usage |
| Ying et al. [20] | High | High | High |
| Habak et al. [18] | Medium | Medium | Medium |
| Yuan et al. [34] | High | High | High |
| Huang et al. [28] | Medium | Medium | Medium |
| Echeverria et al. [51] | High | High | High |
| Cui et al. [52] | Medium | Medium | Medium |
| Goh et al. [53] | High | High | High |
| Mtibaa et al. [22] | Medium | Medium | Medium |
| Kozik et al. [54] | High | High | High |
| Trusted Cooperative Relation Model | Basics | Trust Calculation Executor |
|---|---|---|
| Ying et al. [20] | Social Trust | BSs |
| Habak et al. [18] | Social Trust | Edge Servers |
| Yuan et al. [34] | Social Trust | Edge Brokers |
| Huang et al. [28] | Reputation | Edge Servers |
| Echeverria et al. [51] | Authentication | Edge Servers |
| Cui et al. [52] | Authentication | Edge Servers |
| Goh et al. [53] | Authentication | Trusted Central DBMS |
| Mtibaa et al. [22] | Intrusion Detection | Edge Servers |
| Kozik et al. [54] | Intrusion Detection | Edge Clouds |
| Trusted Cooperative Relation Model | Edge Service Provider | Architecture |
| Ying et al. [20] | BSs and Edge Devices | Hybrid |
| Habak et al. [18] | Edge Servers | Hybrid |
| Yuan et al. [34] | Edge Brokers and Edge Devices | Hybrid |
| Huang et al. [28] | Edge Servers | Semi-centralized |
| Echeverria et al. [51] | Edge Servers | Semi-centralized |
| Cui et al. [52] | Edge Servers | Semi-Centralized |
| Goh et al. [53] | Edge Servers | Centralized |
| Mtibaa et al. [22] | Edge Servers and Edge Devices | Hybrid |
| Kozik et al. [54] | Edge Clouds | Semi-centralized |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yuan, J.; Li, E.; Kang, C.; Chang, F.; Li, X. Review of the D2D Trusted Cooperative Mechanism in Mobile Edge Computing. Information 2019, 10, 259. https://doi.org/10.3390/info10080259
Yuan J, Li E, Kang C, Chang F, Li X. Review of the D2D Trusted Cooperative Mechanism in Mobile Edge Computing. Information. 2019; 10(8):259. https://doi.org/10.3390/info10080259
Chicago/Turabian StyleYuan, Jie, Erxia Li, Chaoqun Kang, Fangyuan Chang, and Xiaoyong Li. 2019. "Review of the D2D Trusted Cooperative Mechanism in Mobile Edge Computing" Information 10, no. 8: 259. https://doi.org/10.3390/info10080259
APA StyleYuan, J., Li, E., Kang, C., Chang, F., & Li, X. (2019). Review of the D2D Trusted Cooperative Mechanism in Mobile Edge Computing. Information, 10(8), 259. https://doi.org/10.3390/info10080259





