Information Security Risk Propagation Model Based on the SEIR Infectious Disease Model for Smart Grid
Abstract
:1. Introduction
2. Related Work
2.1. Risk Assessment
2.2. Infectious Disease Model
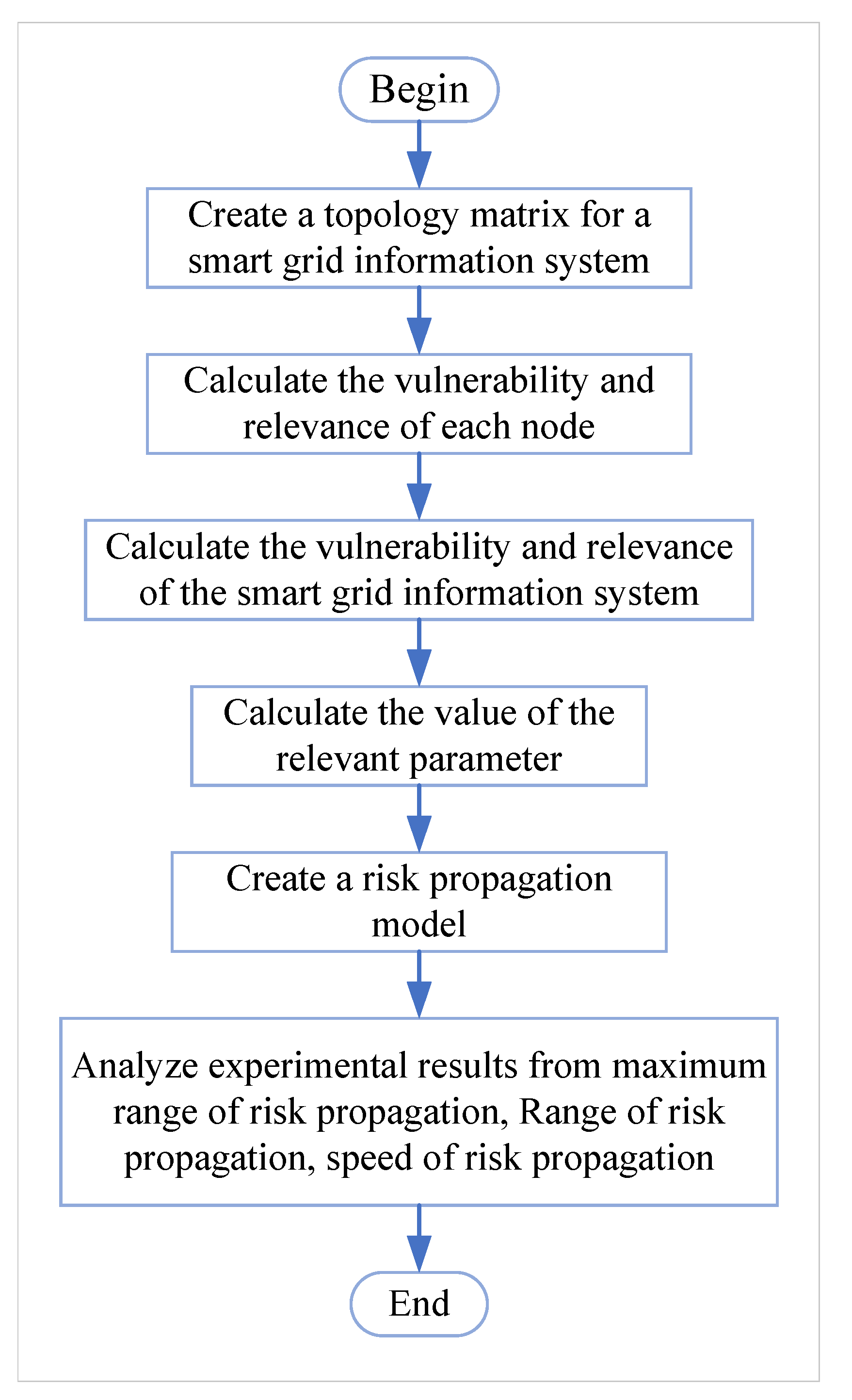
3. Information Security Risk Propagation Model Based on SEIR Infectious Disease Model for Smart Grids
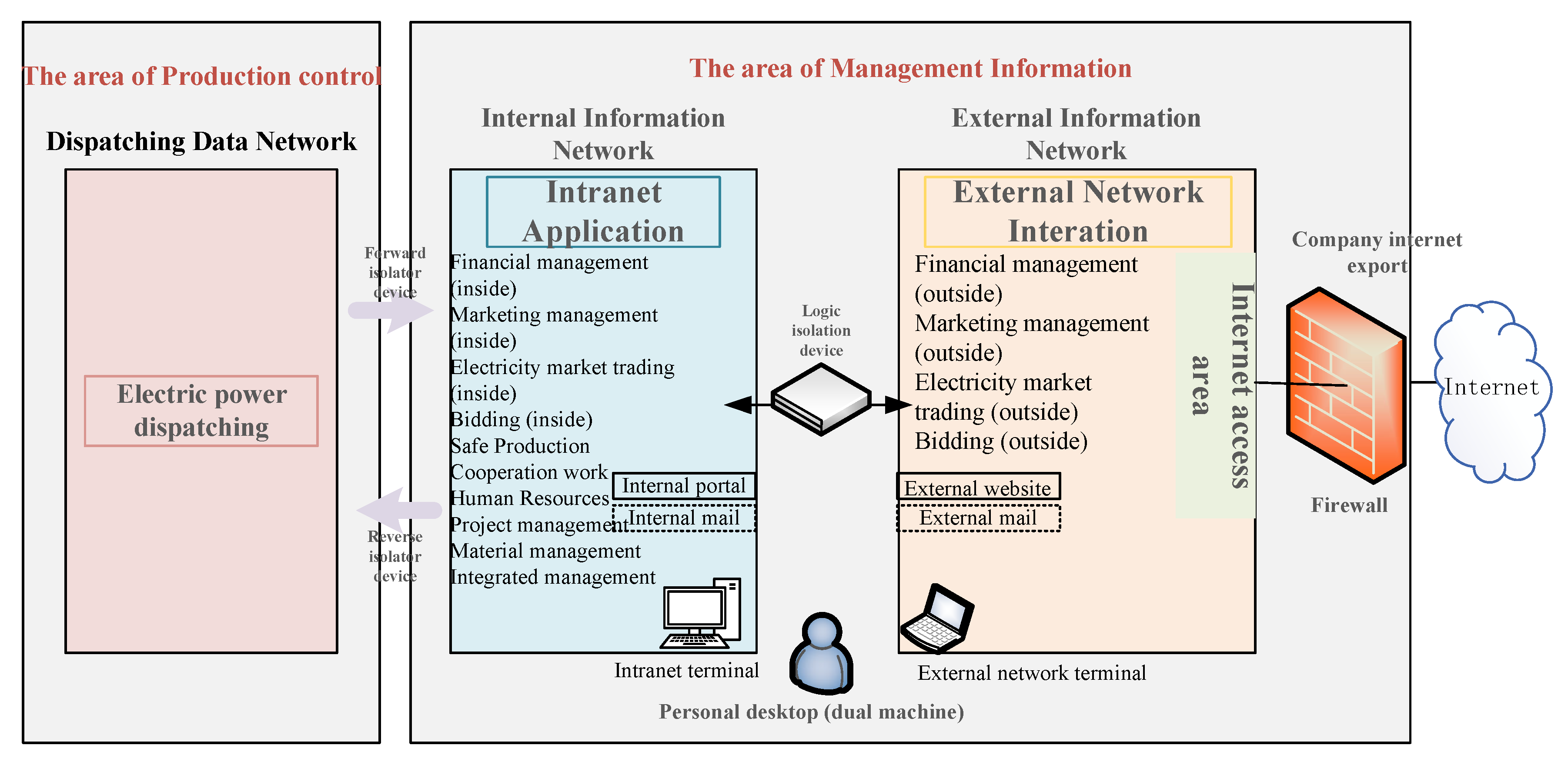
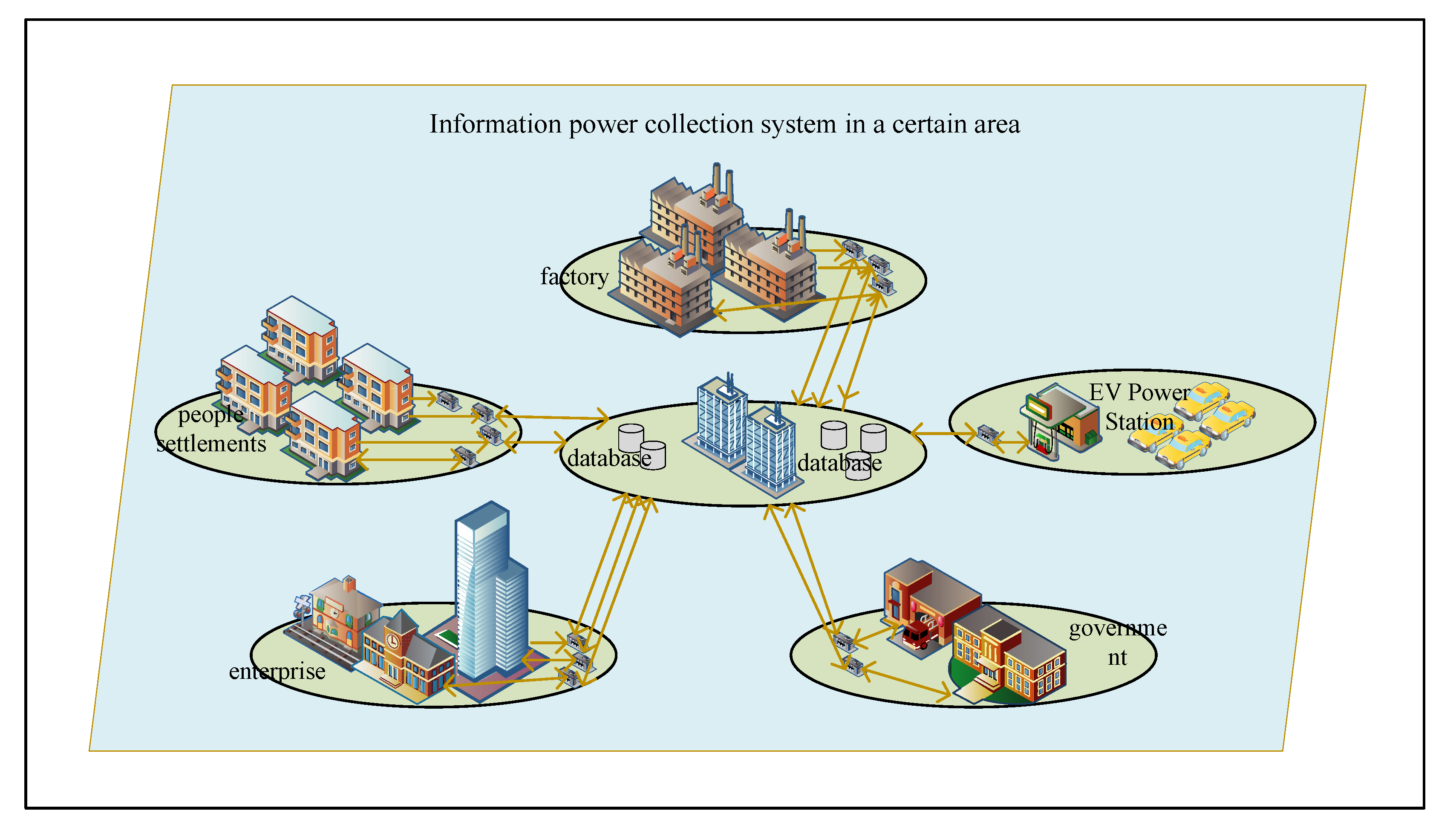
3.1. Information Security Risk Propagation Method for a Smart Grid
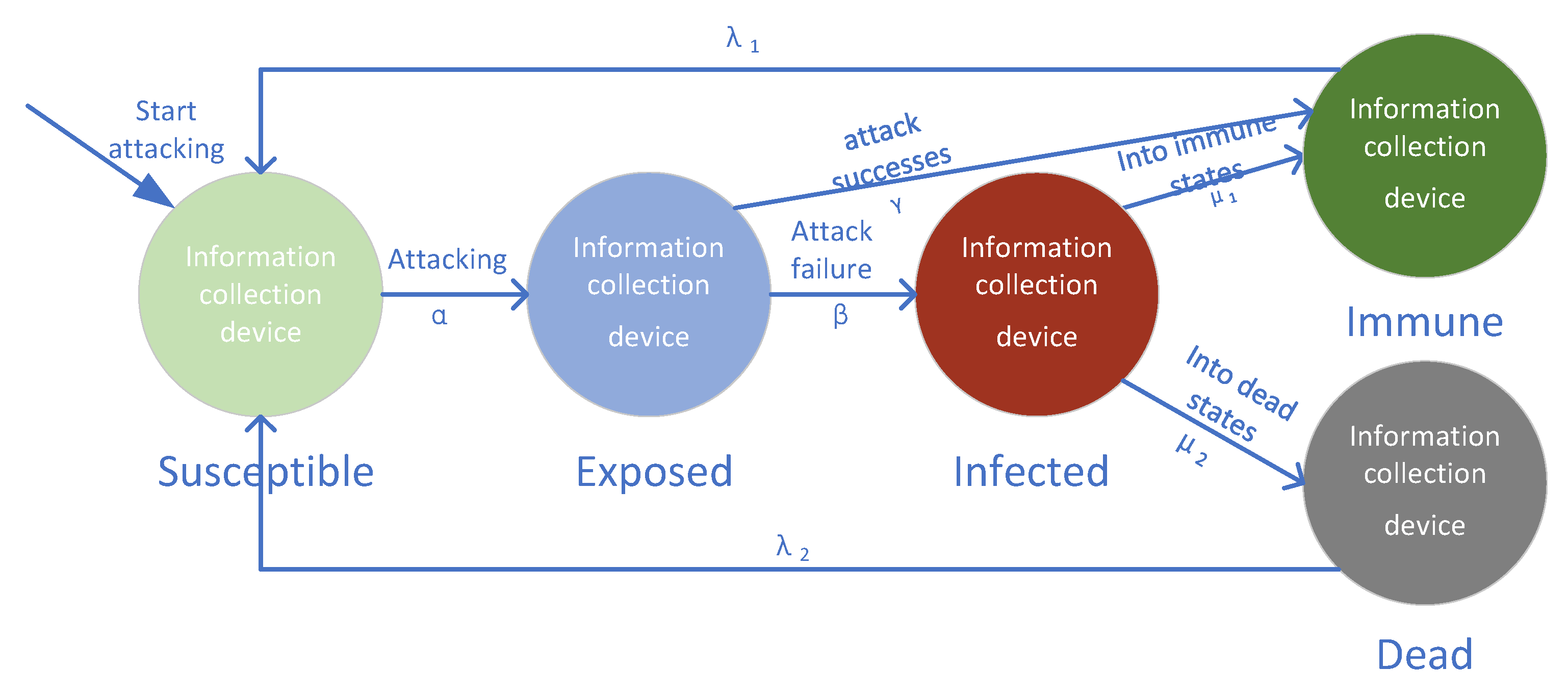
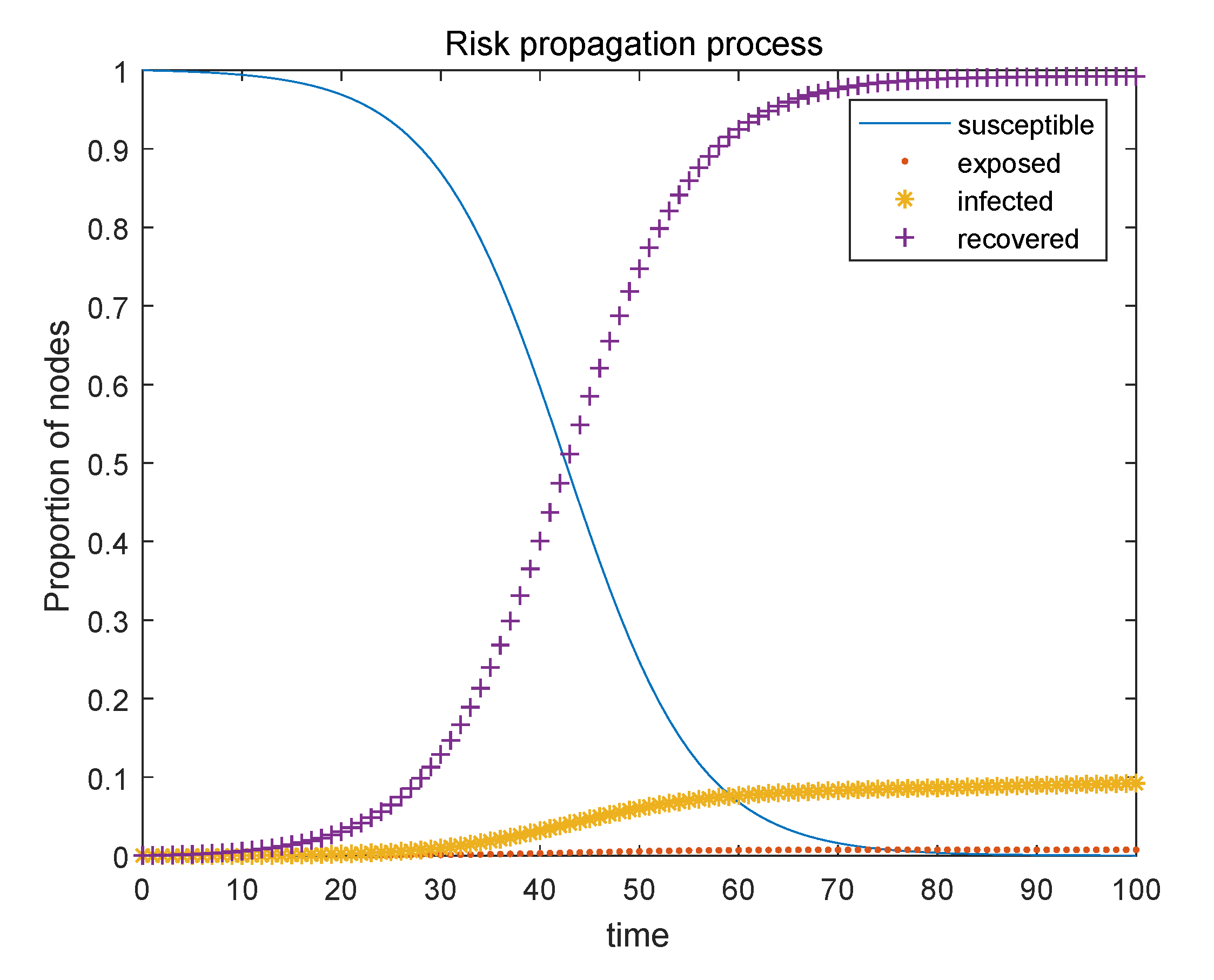
3.2. SEIR Infectious Disease Model
3.3. ISRP-SEIRIDM
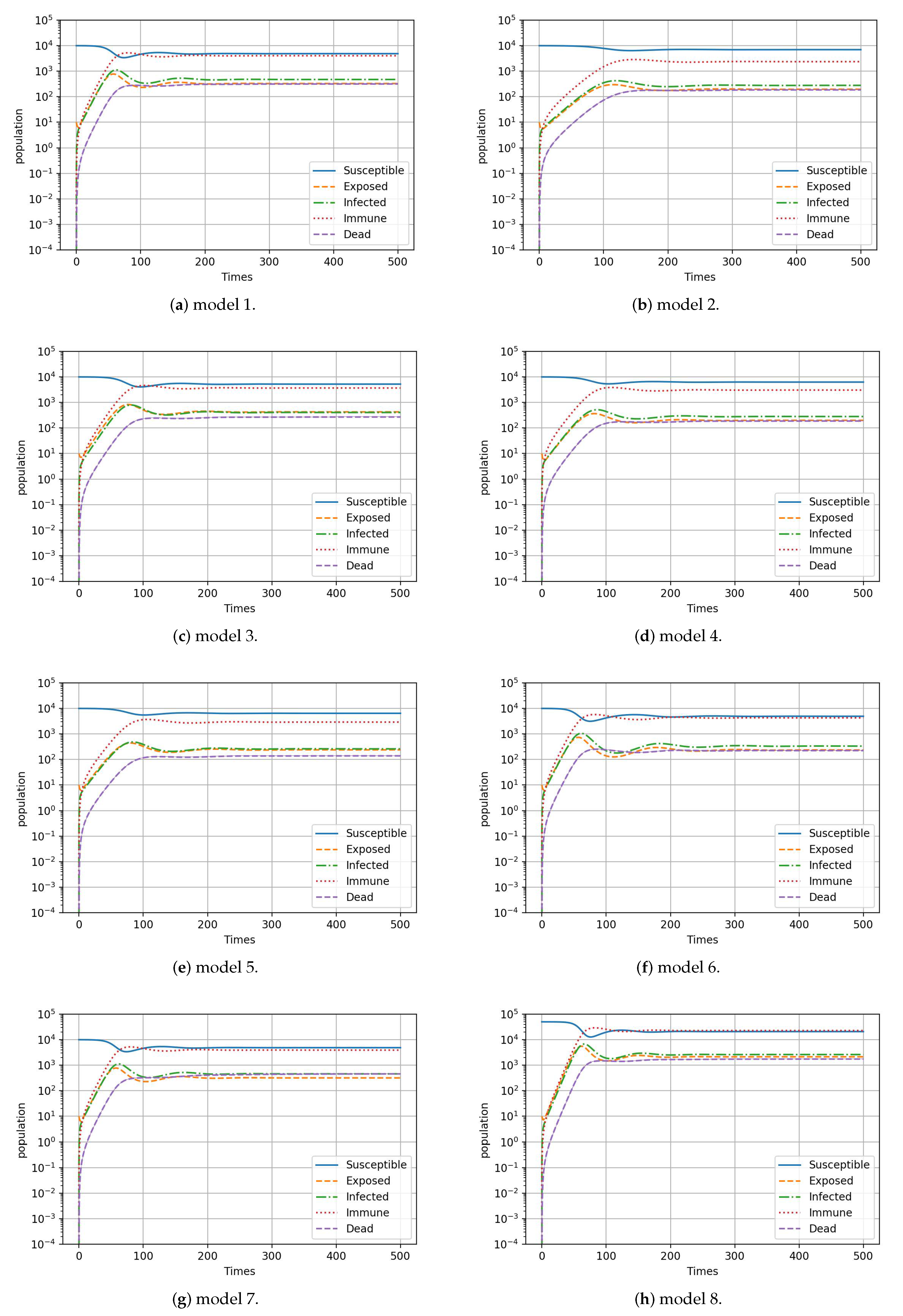
4. Experimental Analysis
4.1. Experimental Environment
4.2. Experimental Data
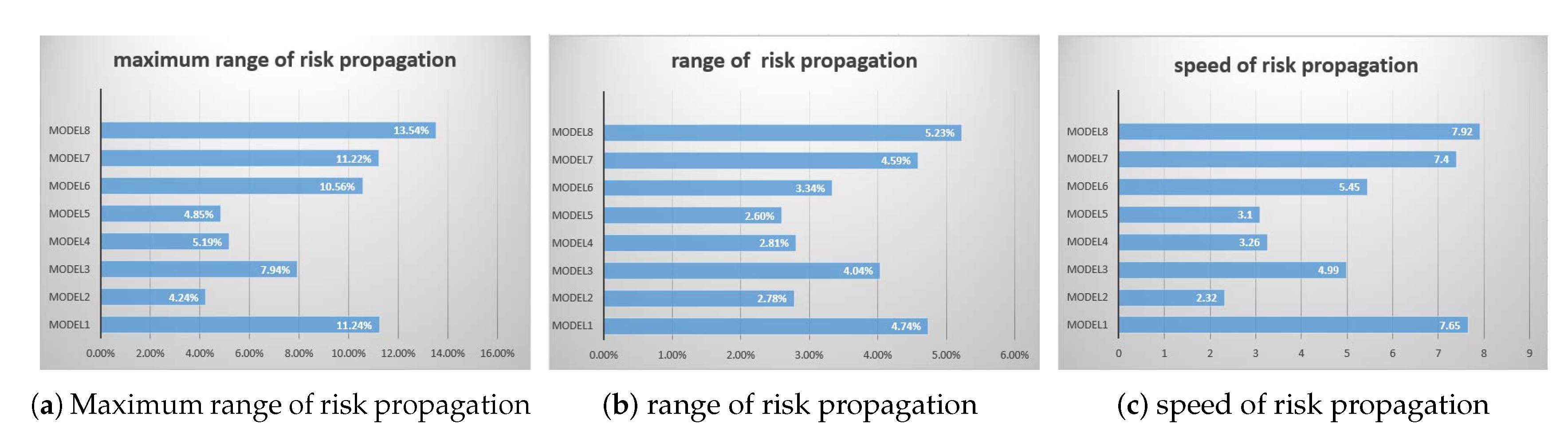
4.3. Evaluation Index
4.4. Experimental Analysis
5. Conclusions
Author Contributions
Acknowledgments
Conflicts of Interest
References
- Gungor, V.C.; Sahin, D.; Kocak, T.; Ergut, S.; Buccella, C.; Cecati, C.; Hancke, G.P. Smart grid technologies: Communication technologies and standards. IEEE Trans. Ind. Inform. 2011, 7, 529–539. [Google Scholar] [CrossRef]
- McDaniel, P.; McLaughlin, S. Security and privacy challenges in the smart grid. IEEE Secur. Priv. 2009, 7, 75–77. [Google Scholar] [CrossRef]
- Aloul, F.; Al-Ali, A.; Al-Dalky, R.; Al-Mardini, M.; El-Hajj, W. Smart grid security: Threats, vulnerabilities and solutions. Int. J. Smart Grid Clean Energy 2012, 1, 1–6. [Google Scholar] [CrossRef]
- Case, D.U. Analysis of the Cyber Attack on the Ukrainian Power Grid; Electricity Information Sharing and Analysis Center (E-ISAC): Washington, DC, USA, 2016. [Google Scholar]
- Li, Z.W.; Tong, W.M.; Jin, X.J. Construction of cyber security defense hierarchy and cyber security testing system of smart grid: Thinking and enlightenment for network attack events to national power grid of Ukraine and Israel. Autom. Electr. Power Syst. 2016, 40, 147–151. [Google Scholar]
- Vaz, R. Venezuela’s power grid disabled by cyber attack. Green Left Weekly, 15 March 2019; 15. [Google Scholar]
- Depuru, S.S.S.R.; Wang, L.; Devabhaktuni, V.; Gudi, N. Smart meters for power grid—Challenges, issues, advantages and status. In Proceedings of the 2011 IEEE/PES Power Systems Conference and Exposition, Phoenix, AZ, USA, 20–23 March 2011; pp. 1–7. [Google Scholar]
- Amin, S.M.; Wollenberg, B.F. Toward a smart grid: Power delivery for the 21st century. IEEE Power Energy Mag. 2005, 3, 34–41. [Google Scholar] [CrossRef]
- Wang, W.; Lu, Z. Cyber security in the smart grid: Survey and challenges. Comput. Netw. 2013, 57, 1344–1371. [Google Scholar] [CrossRef]
- Delgado-Gomes, V.; Martins, J.F.; Lima, C.; Borza, P.N. Smart grid security issues. In Proceedings of the 2015 9th International Conference on Compatibility and Power Electronics (CPE), Costa da Caparica, Portugal, 24–26 June 2015; pp. 534–538. [Google Scholar]
- Falahati, B.; Fu, Y.; Wu, L. Reliability assessment of smart grid considering direct cyber-power interdependencies. IEEE Trans. Smart Grid 2012, 3, 1515–1524. [Google Scholar] [CrossRef]
- Sridhar, S.; Hahn, A.; Govindarasu, M. Cyber–physical system security for the electric power grid. Proc. IEEE 2012, 100, 210–224. [Google Scholar] [CrossRef]
- Varaiya, P.P.; Wu, F.F.; Bialek, J.W. Smart operation of smart grid: Risk-limiting dispatch. Proc. IEEE 2011, 99, 40–57. [Google Scholar] [CrossRef]
- Marsadek, M.; Mohamed, A.; Norpiah, Z. Risk of static security assessment of a power system using non-sequential monte carlo simulation. J. Appl. Sci. 2011, 11, 300–307. [Google Scholar] [CrossRef]
- Habash, R.W.; Groza, V.; Krewski, D.; Paoli, G. A risk assessment framework for the smart grid. In Proceedings of the 2013 IEEE Electrical Power & Energy Conference, Halifax, NS, Canada, 21–23 August 2013; pp. 1–6. [Google Scholar]
- Zhao, T.; Lu, D.; Wang, D.; Zeng, Y.; Liu, Y. A risk assessment approach for power system based on a comprehensive fault probabilistic model. In Proceedings of the 2015 5th International Conference on Electric Utility Deregulation and Restructuring and Power Technologies (DRPT), Changsha, China, 26–29 November 2015; pp. 574–577. [Google Scholar]
- Peng, P.; Liu, S.; Mi, C.; Tao, J. A study on the assessment of power system security risk based on gray clustering and maximum entropy theory. In Proceedings of the 2016 IEEE International Conference on Systems, Man, and Cybernetics (SMC), Budapest, Hungary, 9–12 October 2016; pp. 3002–3007. [Google Scholar]
- Li, Z.; Xu, G.A.; Ban, X.F.; Zhang, Y.; Hu, Z.M. Complex information system security risk propagation research based on cellular automata. Acta Phys. Sin. Chin. Ed. 2013, 62. [Google Scholar] [CrossRef]
- Kosut, O.; Jia, L.; Thomas, R.J.; Tong, L. Malicious data attacks on smart grid state estimation: Attack strategies and countermeasures. In Proceedings of the 2010 First IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 220–225. [Google Scholar]
- Kermack, W.O.; McKendrick, A.G. Contributions to the mathematical theory of epidemics. III.—Further studies of the problem of endemicity. Proc. R. Soc. Lond. Ser. A 1933, 141, 94–122. [Google Scholar] [CrossRef]
- Lu, D.; Liu, Y.; Zeng, Y. Risk assessment of power grid considering the reliability of the information system. In Proceedings of the 2016 IEEE International Conference on Smart Grid Communications (SmartGridComm), Sydney, Australia, 6–9 November 2016; pp. 723–728. [Google Scholar]
- Ghanbari, R.; Jalili, M.; Yu, X. Discovering the structure of cascade propagation in power grids. In Proceedings of the 2018 IEEE International Conference on Industrial Electronics for Sustainable Energy Systems (IESES), Hamilton, New Zealand, 31 January–2 February 2018; pp. 272–276. [Google Scholar]
- Dey, P.; Mehra, R.; Kazi, F.; Wagh, S.; Singh, N.M. Impact of topology on the propagation of cascading failure in power grid. IEEE Trans. Smart Grid 2016, 7, 1970–1978. [Google Scholar] [CrossRef]
- De Jong, M.; Papaefthymiou, G.; Palensky, P. A framework for incorporation of infeed uncertainty in power system risk-based security assessment. IEEE Trans. Power Syst. 2018, 33, 613–621. [Google Scholar] [CrossRef]
- Ding, M.; Xiao, Y.; Zhang, J.; He, J. Risk assessment model of power grid cascading failures based on fault chain and dynamic fault tree. Proc. CSEE 2015, 35, 821–829. [Google Scholar]
- Yan, F.; Wang, Y.; Yin, X.; Li, J.; Yang, W.; Xu, B.; Jian, C. Research on the security risk assessment system for regional complex power grid. In Proceedings of the 2015 5th International Conference on Electric Utility Deregulation and Restructuring and Power Technologies (DRPT), Changsha, China, 26–29 November 2015; pp. 1–4. [Google Scholar]
- Kermack, W.O.; McKendrick, A.G. A contribution to the mathematical theory of epidemics. Proc. R. Soc. Lond. Ser. A 1927, 115, 700–721. [Google Scholar] [CrossRef] [Green Version]
- Kermack, W.O.; McKendrick, A.G. Contributions to the mathematical theory of epidemics. II.—The problem of endemicity. Proc. R. Soc. Lond. Ser. A 1932, 138, 55–83. [Google Scholar] [CrossRef]
- Jyothi, S.; Vorugunti, C.S. Epidemic model based evaluation of malware propagation in Twitter. In Proceedings of the 2017 9th International Conference on Communication Systems and Networks (COMSNETS), Bangalore, India, 4–8 January 2017; pp. 407–408. [Google Scholar]
- Chen, F.; Chen, T. Research on Public Opinion Emergencies Evolution: Based on the Perspective of Opinion Leaders Guiding Role. Inf. Doc. Serv. 2015, 36, 23–28. [Google Scholar]
- Gardner, M.T.; Beard, C.; Medhi, D. Using SEIRS Epidemic Models for IoT Botnets Attacks. In Proceedings of the 13th International Conference on DRCN 2017-Design of Reliable Communication Networks, Munich, Germany, 8–10 March 2017; pp. 1–8. [Google Scholar]
- Chen, P.Y.; Cheng, S.M.; Hsu, H.Y. Analysis of information delivery dynamics in cognitive sensor networks using epidemic models. IEEE Internet Things J. 2018, 5, 2333–2342. [Google Scholar] [CrossRef]
- Romero-L, M.; Gallego, L. Analysis of voltage sags propagation in distribution grids using a SI epidemic model. In Proceedings of the 2017 IEEE Workshop on Power Electronics and Power Quality Applications (PEPQA), Bogota, Colombia, 31 May–2 June 2017; pp. 1–6. [Google Scholar]
- Wu, Q.; Zhang, D.; Liu, D.; Liu, F.; Ling, X.B.; Li, Z. Disturbance propagation in power system based on an epidemic model. In Proceedings of the 2017 IEEE Conference on Energy Internet and Energy System Integration (EI2), Beijing, China, 26–28 November 2017; pp. 1–6. [Google Scholar]
- Cisotto, G.; Badia, L. Cyber security of smart grids modeled through epidemic models in cellular automata. In Proceedings of the 2016 IEEE 17th International Symposium on a World of Wireless, Mobile and Multimedia Networks (WOWMoM), Coimbra, Portugal, 21–24 June 2016; pp. 1–6. [Google Scholar]
- Tian, C.; Wang, Y.; Zhou, Y.; Wang, J. Composite power system risk assessment and weak links identification considering cascading failures. In Proceedings of the 2015 5th International Conference on Electric Utility Deregulation and Restructuring and Power Technologies (DRPT), Changsha, China, 26–29 November 2015; pp. 543–548. [Google Scholar]
| Parameters | Description |
|---|---|
| Probability of transitioning from a susceptible state to a exposed state | |
| Probability of transitioning from a exposed state to a infected state | |
| Probability of transitioning from a exposed state to a immune state | |
| Probability of transitioning from a infected state to a immune state | |
| Probability of transitioning from a infected state to a dead state | |
| Probability of transitioning from a immune state to a susceptible state | |
| Probability of transitioning from a dead state to a susceptible state |
| Model | N | |||||||
|---|---|---|---|---|---|---|---|---|
| 1 | 0.52 | 0.317 | 0.05 | 0.22 | 0.010 | 0.03 | 0.015 | 10,000 |
| 2 | 0.37 | 0.317 | 0.05 | 0.22 | 0.010 | 0.03 | 0.015 | 10,000 |
| 3 | 0.52 | 0.210 | 0.05 | 0.22 | 0.010 | 0.03 | 0.015 | 10,000 |
| 4 | 0.52 | 0.317 | 0.15 | 0.22 | 0.010 | 0.03 | 0.015 | 10,000 |
| 5 | 0.52 | 0.317 | 0.05 | 0.29 | 0.008 | 0.03 | 0.015 | 10,000 |
| 6 | 0.52 | 0.317 | 0.05 | 0.22 | 0.010 | 0.02 | 0.015 | 10,000 |
| 7 | 0.52 | 0.317 | 0.05 | 0.22 | 0.010 | 0.03 | 0.010 | 10,000 |
| 8 | 0.62 | 0.268 | 0.05 | 0.22 | 0.010 | 0.03 | 0.015 | 50,000 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhu, B.; Deng, S.; Xu, Y.; Yuan, X.; Zhang, Z. Information Security Risk Propagation Model Based on the SEIR Infectious Disease Model for Smart Grid. Information 2019, 10, 323. https://doi.org/10.3390/info10100323
Zhu B, Deng S, Xu Y, Yuan X, Zhang Z. Information Security Risk Propagation Model Based on the SEIR Infectious Disease Model for Smart Grid. Information. 2019; 10(10):323. https://doi.org/10.3390/info10100323
Chicago/Turabian StyleZhu, Boyu, Song Deng, Yunan Xu, Xinya Yuan, and Zi Zhang. 2019. "Information Security Risk Propagation Model Based on the SEIR Infectious Disease Model for Smart Grid" Information 10, no. 10: 323. https://doi.org/10.3390/info10100323




