Abstract
With the growing integration of digital technologies on modern vessels, ranging from satellite links and mobile networks to onboard Wi-Fi, the exposure of maritime systems to cyber threats has become a pressing concern. Wireless networks on ships, although essential for operations and crew welfare, often lack sufficient protection and are frequently overlooked in broader cybersecurity strategies. This article explores vulnerabilities linked to Man-in-the-Middle attacks and rogue access points, particularly in port areas where attackers may exploit signal range and proximity. A simulation carried out in a public setting near the Port of Rijeka demonstrated how standard crew devices could be lured into connecting to a counterfeit Wi-Fi network, resulting in traffic interception and potential data leaks. Although practical limitations, such as signal attenuation and distance, reduce the feasibility of such intrusions at sea, the risk remains significant while in port. Insecure configurations and common user behaviors were identified as key enablers. The article outlines a series of countermeasures aligned with international guidelines ranging from segmentation and encryption to crew training and intrusion detection. Addressing these wireless vulnerabilities is essential for building resilience and ensuring that digital transformation efforts in the maritime sector do not come at the expense of security.
1. Introduction
The maritime industry is undergoing rapid digital transformation, as information technology (IT) and operational technology (OT) converge to enhance efficiency, safety, and operational continuity at sea. Modern vessels are no longer isolated systems but are integral parts of a complex and interconnected digital infrastructure. Connectivity is maintained through various communication channels, including satellite broadband, coastal cellular networks, and widely adopted onboard Wi-Fi systems [1,2,3,4]. This continuous connectivity supports numerous operational functions, from navigation data exchange and cargo management to crew welfare applications. However, it also significantly broadens the attack surface, exposing ships to an evolving spectrum of cyber risks [4,5,6].
Recent maritime cybersecurity reports highlight a notable increase in targeted cyber activities, with monitoring centers detecting intrusion attempts on over 1800 vessels in the first half of 2024 alone. These trends clearly challenge the outdated belief that physical isolation at sea provides inherent security. Instead, the integration of digital technologies into core shipboard systems such as navigation, propulsion, and maintenance has introduced new vulnerabilities that adversaries actively seek to exploit [6,7,8].
Among the most vulnerable vectors are onboard wireless networks, which are often implemented with insufficient protections. These Wi-Fi systems facilitate critical crew communications and support operational workflows but are frequently configured with weak security controls. Attackers positioned within signal range, whether near the vessel while docked, aboard adjacent ships, or sometimes even onboard, can deploy techniques such as rogue access points and Man-in-the-Middle (MitM) attacks. By replicating legitimate network identifiers (SSIDs), attackers can coerce devices to automatically connect, granting them access to sensitive data streams, including login credentials and private communications [9,10,11,12,13,14].
Wireless network compromises do not remain isolated issues but often serve as footholds for deeper intrusions into the ship’s broader IT and OT environments. Weak VLAN segmentation and insufficient isolation between crew and operational domains create opportunities for attackers to gain visibility into safety-critical systems such as Electronic Chart Display and Information Systems (ECDISs), voyage planning terminals, or bridge navigation controls. Such lateral movements can theoretically result in unauthorized course changes, interference with helm controls, or extraction of sensitive voyage data [15,16,17,18]. Although this simulation did not encompass such escalations, prior case studies confirm the feasibility of these attack vectors under inadequate security conditions.
In response to these rising threats, international regulatory bodies have introduced frameworks aimed at bolstering maritime cybersecurity. Since its adoption in 2021, the International Maritime Organization’s Resolution MSC.428(98) has mandated that vessels incorporate cyber risk management as a key part of their Safety Management Systems [2]. Furthermore, guidelines issued by BIMCO and the International Chamber of Shipping highlight the importance of considering onboard wireless networks as inherently untrusted, recommending their strict separation from critical operational and control systems [3]. Despite these clear directives, implementation varies widely across fleets. Field audits continue to uncover misconfigurations such as crew-installed routers with weak passwords and poor network segmentation, underscoring the ongoing challenge of aligning practice with policy [10,19].
Several factors contribute to this implementation gap. Many vessels operate on legacy platforms incompatible with contemporary security protocols, while others face shortages of qualified IT personnel. These challenges are often worsened during long voyages where immediate technical assistance is unavailable onboard. Even when awareness exists, inconsistent infrastructure and varying levels of crew cybersecurity training often lead to overlooked vulnerabilities and unaddressed risks [8,18].
To empirically investigate these challenges, we conducted a controlled simulation near the Port of Rijeka, employing the Wi-Fi Pineapple Mark VII to replicate an external adversary launching rogue AP and MitM attacks. This real-world experiment, conducted from a publicly accessible location, provided an authentic assessment of vulnerability exposure and evaluated the efficacy of potential countermeasures [14,15].
The results emphasize the urgent need to enhance shipboard wireless security through measures such as network segmentation, strong encryption protocols, continuous crew training in cybersecurity best practices, and deployment of wireless intrusion detection systems. As digital technologies become further embedded in maritime operations, securing wireless communications is not simply a technical necessity but a fundamental part of building comprehensive cyber resilience, essential for maintaining both operational stability and the overall security of the maritime industry.
2. Background
Among the diverse cybersecurity challenges faced by modern vessels, the threat posed by rogue APs and their role in enabling MitM attacks stands out as one of the most pressing. As shipboard Wi-Fi networks become increasingly integrated into daily operations and crew welfare services, they also introduce critical vulnerabilities that can be exploited from both within and near the vessel [6,8,9,20]. These threats are not hypothetical; they are consistently observed during penetration testing and are well documented in cybersecurity advisories for the maritime sector [10,19,21].
A rogue AP, often referred to as an evil twin, is a malicious wireless access point designed to impersonate a legitimate shipboard Wi-Fi network. By mimicking the SSID and encryption settings of the real network, attackers can trick user devices, especially those set to auto-connect, into associating with the rogue AP [12,13,14]. This opens the door for a MitM attack, where all data between the user and the internet is routed through the attacker’s device. While some attacks simply eavesdrop on traffic, others manipulate it in real-time, injecting malicious payloads or altering transmitted data [11,13,14]. These tactics are alarmingly effective in maritime settings, particularly when vessels are in port and exposed to adjacent public spaces such as terminals and docks. A simplified overview of passive and active interception is illustrated in Figure 1.
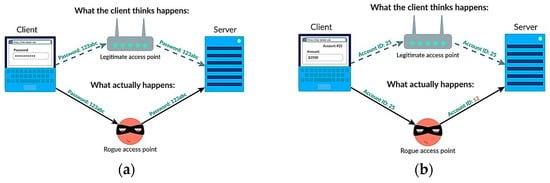
Figure 1.
Rogue AP exploitation scenarios: (a) passive interception; (b) active interception. Reproduced from [22], used under Khan Academy’s content usage policy.
Once an attacker achieves a MitM position, a range of data interception techniques becomes available. In passive interception, the rogue AP silently relays all communications, capturing sensitive data such as login credentials, email content, or session cookies, especially if the victim is using unencrypted services like HTTP or outdated mobile apps [14,23]. In active MitM scenarios, attackers may manipulate traffic in transit, inject malicious scripts, or redirect users to fake login portals. Techniques such as SSL stripping exploit situations where user devices initiate connections over HTTP or fail to enforce HTTPS redirects. In such cases, a rogue AP can intercept and relay traffic while downgrading the encryption, particularly if the targeted services lack HSTS (HTTP Strict Transport Security) headers or proper certificate pinning. This vulnerability is more pronounced in older mobile applications, legacy web interfaces, or poorly configured captive portals often used on ships for crew access. Devices that do not validate digital certificates rigorously may accept spoofed credentials, allowing attackers to present deceptive login pages or extract session data from unencrypted requests [14,24]. Modern mobile operating systems, including iOS and Android, typically display warnings when a known SSID is broadcast with weaker security settings, such as the absence of WPA2/3 encryption. In this simulation, automatic connections were observed only from devices that either had no prior configuration for the legitimate SSID or were manually connected by users during routine maintenance activities. No attempt was made to bypass OS-level protections or simulate forced reconnection scenarios. These constraints limited the scope of the attack to devices with permissive settings or inattentive user behavior, a factor consistent with known real-world vulnerabilities in port environments.
Smartphones, laptops, and tablets carried by crew often attempt to reconnect to known Wi-Fi networks without prompting the user, especially if the auto-connect feature is enabled. This behavior is common across both Android and iOS devices. An attacker can exploit this by replicating the ship’s Wi-Fi SSID and broadcasting it with a stronger signal, increasing the chances that nearby devices will automatically connect. In practice, this kind of setup is simple to execute from a parked van near the quay, inside the port terminal, or even from another ship moored nearby. Deauthentication packets can also be used to forcibly disconnect devices from the real network, prompting reconnection through the attacker’s AP [12,14].
Beyond rogue AP exploitation, wireless environments aboard ships face secondary risks. Signal jamming, for instance, can interrupt Wi-Fi-based CCTV or communication systems using cheap multi-band jammers. No wireless traffic associated with CCTV systems was directly observed during the test. The mention of potential impact on Wi-Fi-based CCTV refers to general risk scenarios applicable to vessels where such systems operate on unsecured or poorly segmented networks. While some vessels use wireless cameras for flexibility during maintenance or retrofits, this remains an assumption in the present study and should be interpreted accordingly. Similarly, passive sniffing of broadcast packets remains a realistic threat where encryption is weak or improperly configured. Weak or misconfigured Wi-Fi security, in this case, includes examples like open networks, outdated protocols (e.g., WEP), missing WPA protection, unchanged factory passwords, or setups where network traffic is not properly segmented.
Various wireless security protocols define how devices authenticate and manage encryption keys. Common Authentication and Key Management (AKM) modes include Open (no authentication), Pre-Shared Key (PSK), and 802.1X with Extensible Authentication Protocol (EAP). Modern configurations such as WPA2-PSK, WPA3-SAE, and WPA2-PSK/WPA3-SAE mixed mode offer strong security when properly implemented. In contrast, WEP and early WPA-PSK setups are considered obsolete due to known cryptographic weaknesses. Transitional modes, such as WPA-PSK/WPA2-PSK, provide compatibility but may degrade overall protection. Some networks use Opportunistic Wireless Encryption (OWE) or remain fully open, both of which should be avoided aboard vessels.
The choice of AKM mode plays a critical role in determining a network’s resistance to common attack vectors such as brute-force decryption, credential harvesting, and unauthorized access. In maritime settings, where physical access control is often limited during port stays, misconfigured AKM can leave onboard devices vulnerable to trivial compromise. Against this background, the specific setup used in the simulation can be better understood. For the purpose of this test, the rogue access point used no encryption at all, similar to what can be seen in older or hastily configured onboard networks. Only broadcast traffic, DHCP messages, and other unencrypted metadata were collected passively. No login credentials were captured, and encrypted data was left untouched.
Ships using WPA2-PSK with default or predictable passwords are especially vulnerable. Predictable Wi-Fi passwords, such as vessel names, default SSIDs, or short numeric sequences, can be vulnerable to dictionary and brute-force attacks. Legacy encryption schemes like WEP are especially susceptible to rapid key recovery due to weak initialization vectors. Even WPA2-PSK networks, when using simple or commonly reused passphrases, can be compromised using offline dictionary attacks combined with precomputed hash lists (rainbow tables). These techniques are widely available in standard penetration testing toolkits and can be executed without persistent access once a handshake is captured. These risks are amplified by inconsistent network hygiene and the use of unauthorized IoT devices such as crew-installed smart plugs or routers that bypass centralized controls. Wi-Fi jammers, for instance, can disable communications across 2.4 GHz and 5 GHz bands, disrupting CCTV feeds or crew messaging apps, potentially as a prelude to physical intrusion [25]. Passive packet sniffing using tools like Wireshark can expose sensitive data when ships employ weak encryption or unpatched services like FTP or Telnet [26]. Even WPA2 networks are at risk when using predictable passwords or legacy ciphers such as TKIP [27].
Much of this vulnerability stems from poor configuration hygiene. Studies and field audits have identified the persistent use of default router credentials, unpatched firmware, and inadequate network segmentation between crew, passenger, and operational domains [6,8,16,18,28]. This creates lateral movement opportunities, allowing attackers to pivot from compromised crew networks into OT systems controlling cargo or navigation.
To address these risks, maritime regulators and classification societies have published a range of guidelines. The IMO’s MSC-FAL.1/Circ.3 and Resolution MSC.428(98) stress the need to embed cyber risk management into Safety Management Systems [1,2]. The BIMCO/ICS guidelines further recommend treating all wireless networks as “uncontrolled” and strictly isolating them from core control networks [3]. Classification societies such as ClassNK have incorporated “secure-by-design” principles into cyber certification schemes, requiring WLAN architecture audits and formal risk assessment of wireless segments [29].
A growing number of shipowners are deploying Wireless Intrusion Detection Systems (WIDSs) to monitor for rogue APs and Wi-Fi anomalies. Open-source tools like Kismet can detect unknown SSIDs, sudden spikes in deauthentication frames, or unrecognized client behavior [14,30]. However, effective use of these technologies requires trained personnel, consistent monitoring, and integration with broader security operations, which are factors that are not always present aboard commercial fleets [6,8,18].
Finally, industry frameworks like the NIST Cybersecurity Framework (CSF) and ISO/IEC 27001 provide reference models for structuring wireless security controls under a risk-based approach [31,32]. These models advocate for robust asset identification, access control, incident response capabilities, and continuous monitoring, elements particularly critical in the high-stakes maritime environment.
In this context, rogue AP and MitM attacks are treated not merely as hypothetical threats but as practical entry points that merit empirical examination under realistic maritime conditions. This rationale guided the controlled simulation described in the following section, which evaluates how such attacks may unfold in practice and what countermeasures prove most effective.
The threat model adopted in this study assumes a passive external attacker operating within RF range during ship berthing. No physical access to the vessel is presumed, and the primary attack vectors include rogue AP deployment and MitM interception of crew devices that auto-connect to familiar SSIDs. Key vulnerabilities include insufficient SSID validation, weak encryption settings, and a lack of WIDS aboard. This model reflects a practical, low-complexity threat scenario based on recent maritime audits and aligns with real-world attacker behavior in port environments. While more sophisticated attack paths (e.g., persistent device compromise or physical breach) were not simulated, the selected model realistically captures the most accessible risk surface in everyday operations.
Building on this threat model, the following section details the tools, techniques, and methodology used to simulate wireless compromise in a realistic port-side setting, providing insight into the feasibility and impact of such attacks.
3. Tools and Methodology
As outlined earlier, wireless networks aboard ships, particularly those used by crew and passengers, represent a critical cyber risk surface that is often insufficiently protected. Given their proximity to public infrastructure while in port and the widespread use of devices configured to auto-connect to familiar networks, shipboard Wi-Fi becomes an accessible attack vector for even moderately skilled adversaries. To evaluate this threat in practice, the authors conducted a real-world simulation of wireless compromise using an “outside-in” penetration testing methodology. The goal was to determine how easily a rogue AP and MitM attack could be executed under realistic port conditions and how devices onboard might respond to such an intrusion.
Although this study focused on a single toolset, maritime wireless security broadly involves various technologies aimed at auditing, analyzing, or defending against such threats. Among the most established is Wireshark (Wireshark Foundation, Wilmington, DE, USA), a network protocol analyzer capable of capturing and decoding data packets in real time [26,33]. Operating at the data link, network, transport, and application layers, Wireshark can reveal everything from MAC address behavior to cleartext HTTP traffic, DNS lookups, and authentication handshakes. In a maritime security context, Wireshark is particularly useful for verifying whether sensitive information such as login credentials or shipboard device identifiers is exposed during normal communication. Its ability to parse captured traffic into readable streams provides both visibility into network behavior and a forensic record for later analysis.
Another valuable tool is Kismet (Open-source project, Kismet Wireless), an open-source wireless monitoring system that passively scans the radio frequency spectrum to detect anomalous activity [30,34]. Unlike active scanners, Kismet does not transmit packets; instead, it listens for beacon frames, probe requests, and other control packets to identify rogue APs, client misassociations, and channel saturation. It can detect signs of attack patterns such as deauthentication bursts, commonly used in evil twin scenarios, and notify operators of duplicate SSIDs or unknown BSSIDs operating within the same area. In environments such as ports or terminals, where multiple networks coexist, Kismet provides essential visibility into RF noise, unauthorized wireless devices, and potential interference that could indicate an ongoing or planned intrusion.
A third commonly used framework is the Aircrack-ng suite (Open-source project, Aircrack-ng.org), a set of utilities for auditing Wi-Fi encryption and testing the resilience of passwords [24,35]. Its process generally involves capturing the WPA2 handshake as a client connects to a target AP, then performing offline dictionary or brute-force attacks to determine whether the passphrase can be cracked. This toolset includes airodump-ng for packet capture, aireplay-ng for injecting deauth frames, and aircrack-ng itself for key recovery. Although not used in this study, Aircrack-ng remains relevant as a benchmark for evaluating the practical strength of wireless security configurations, particularly in cases where ship networks employ weak or predictable credentials.
In this particular test, the authors chose to focus exclusively on the Wi-Fi Pineapple Mark VII (Hak5 LLC, Sacramento, CA, USA) due to its portability, intuitive interface, and integrated capabilities for wireless deception and MitM traffic routing. However, unlike traditional surveys or tool-centered demonstrations, this study’s methodological contribution lies in its scenario-specific execution. The tools referenced were not tested in abstraction but integrated into a tightly controlled and replicable penetration testing workflow shaped by the constraints of a real-world port environment. Each operational choice, from equipment positioning and antenna selection to SSID emulation, signal control, and capture parameters, was governed by the maritime context in which the test occurred. For example, RF output was deliberately adjusted to avoid spillover beyond the immediate test zone and to remain within expected port-safe emission levels, thereby minimizing unintended interference.
While the Wi-Fi Pineapple Mark VII has been used in earlier audits and security demonstrations, its application in this study was purpose-driven and context-specific. The device was configured to replicate a live SSID broadcasted by the vessel’s crew network, identified through passive scanning. The interface was used solely to observe unencrypted metadata in real time, such as MAC addresses, DNS requests, and SSID probes, while deliberately excluding actions like credential collection, session hijacking, or deep packet inspection, in strict adherence to ethical research protocols. Importantly, all configurations reflected an assumed attacker profile operating without physical access, insider knowledge, or privileged hardware, thus simulating a low-complexity, high-plausibility threat model relevant to most public berthing scenarios.
Moreover, the testing sequence from rogue AP broadcast to downstream relay and interaction logging was designed to match behavioral patterns common among maritime crew, including auto-connect settings, routine maintenance usage, and unsegmented access. This level of procedural granularity differentiates the experiment from generic lab tests or tool capability lists. Rather than merely validating what tools can do, the study demonstrates how specific techniques may unfold in situ under live port constraints, constrained by space, time, and visibility.
This selective and controlled integration of a known auditing tool into a maritime-focused simulation forms the methodological core of the study. By adapting the configuration to reflect real-world safety constraints and operational nuances, the approach offers practical insights into onboard wireless vulnerabilities. It also provides a reproducible and ethically sound testing model for future assessments across other vessel types and port conditions. The purpose was to illustrate how theoretical wireless threats may translate into practical exposures aboard modern vessels, rather than to showcase any particular tool or tactic. In this way, the study contributes practical, context-driven insights that go beyond tool enumeration and directly inform maritime cybersecurity posture.
Prior to presenting the technical configuration, we outline the methodological rationale for limiting the test to a single vessel. While the simulation focused on a single vessel and test instance, this was an intentional methodological constraint aimed at replicating a realistic but ethically bounded attacker scenario. The test was not designed to generalize findings across all maritime environments but to explore feasibility within a constrained, real-world setting. The simulation’s value lies in its operational realism rather than statistical breadth. Future research will expand this work with structured baselines, repeated trials, and comparative testing across vessel types and port conditions.
To support these insights, we describe below the technical deployment and operational behavior of the selected tool during the live simulation. It is a purpose-built auditing device equipped with dual antennas and a Linux-based firmware that supports SSID cloning, client deauthentication, packet forwarding, and credential phishing, which are all controlled through a browser-based dashboard [12,23,36,37].
The test was conducted at the Port of Rijeka, a commercial harbor with a mix of industrial and passenger traffic. The observation point had a direct view of the vessel’s upper deck, which allowed us to maintain a strong signal for the duration of the test. The equipment was positioned in a public seating area where the use of laptops and mobile devices is typical, enabling us to conduct the simulation without drawing attention. This setup enabled seamless impersonation of the vessel’s crew network, drawing in devices that automatically reconnected based on previously stored SSIDs. On the day of the test, weather conditions were stable with minimal interference, which contributed to consistent signal quality and reliable data collection throughout the simulation.
The rogue AP was left open initially (no encryption) to attract any auto-connecting devices and then configured to mimic WPA2 settings for additional testing. To simulate the attacker’s tactics, the deauthentication feature was activated, causing connected devices to momentarily lose contact with the ship’s legitimate Wi-Fi network. No WPA2 passphrases, user credentials, or encrypted payloads were captured, decrypted, or brute-forced during this assessment. The test was limited to passive observation of network metadata and unauthenticated HTTP traffic. All activities were conducted in accordance with ethical research principles, and no intrusive techniques such as password cracking, credential harvesting, or decryption attempts were employed.
Shortly after, multiple client devices, such as phones and laptops, automatically connected to the spoofed AP and started transmitting data through it. Because the rogue AP maintained upstream connectivity via a secondary Wi-Fi source, the victims’ devices experienced no obvious interruption, reinforcing the deceptive nature of the attack. The Pineapple logged unencrypted HTTP requests, DNS queries, and basic metadata such as device MAC addresses and SSIDs probed. Although HTTPS traffic remained encrypted, metadata such as domain names and DNS requests were visible, providing clues about online habits and platforms in use. However, no attempt was made to profile user activity, infer personal identities, or categorize browsing behavior. These aspects were deliberately excluded due to ethical boundaries and privacy considerations, in line with the non-intrusive scope of the simulation.
For demonstration purposes, we also activated a basic login portal through the Pineapple interface, a typical social engineering technique to assess whether users might engage with a fake authentication page. Although no user credentials were submitted during this limited deployment, the successful delivery of the portal confirmed the viability of social engineering tactics in maritime Wi-Fi environments, especially where users are accustomed to captive login screens.
As shown in Figure 2, the Pineapple Mark VII was connected to a laptop set up near the dock. The ship was within direct visual range, and the device interface displayed live connections, confirming that such an attack can be performed without physical access to the vessel.

Figure 2.
Wi-Fi Pineapple Mark VII setup for wireless testing near a vessel in Rijeka.
Throughout the test, all activities were carried out with careful attention to ethical standards and operational safety. At no point was there any attempt to alter, disrupt, or exploit any systems or data. The simulation was restricted to monitoring unencrypted traffic and basic network metadata, ensuring that privacy and system integrity remained fully protected.
The testing device was positioned in a public seating area located approximately 35 m from the midsection of the vessel’s starboard side, with a clear line of sight to the upper deck. Although no formal map was generated for the experiment, the attacker’s vantage point aligned roughly amidships, without specific targeting of bow or stern zones. The estimated standoff distance ranged from 30 to 50 m, depending on device elevation and antenna alignment. Due to operational constraints and the informal nature of the port setting, precise coordinate mapping was not conducted. Future assessments may benefit from formal geospatial mapping to support replication, spatial analysis, and comparative evaluation across different vessel types and port settings. This limitation should be considered when interpreting signal propagation and device visibility in other maritime environments.
The vessel involved in the simulation was a privately owned motor yacht docked at the Port of Rijeka. As the test was conducted entirely from a public area without physical access to the vessel, observations were based solely on passive wireless activity and visible external layout. Devices observed connecting to the rogue access point included smartphones and laptops, which were consistent with typical crew or maintenance usage profiles. Network traffic captured during the simulation did not indicate the presence of navigation systems, CCTV feeds, or other operational technologies. Due to the external nature of the assessment and ethical boundaries observed throughout the experiment, direct insight into the spatial distribution of devices across specific yacht zones (such as cabins, the bridge, or service compartments) was not feasible. These limitations should be considered when assessing the generalizability of the findings.
The duration of the test was intentionally limited, and transmission strength was carefully adjusted to avoid interfering with nearby vessels or normal port operations.
In real-world port environments, attacks such as deauthentication could disrupt time-sensitive communications between crew and shore-based personnel. This may delay coordination during cargo operations, mooring, or refueling. If wireless networks supporting CCTV, access control, or crew logistics systems are affected, the resulting service interruptions may reduce situational awareness or operational safety, particularly during docking, boarding, or emergency procedures.
This type of assessment reflects a broader pattern seen across the maritime sector. Based on similar assessments on other commercial vessels, it is evident that wireless threats, particularly those involving rogue access points, remain largely unaddressed in operational practice. The simplicity and affordability of the tools used in such compromises only underscore the urgency of the issue.
In many cases, shipboard networks do not include wireless intrusion detection systems, and segmentation between crew and operational domains is inconsistently applied. Without proactive RF monitoring, defined password policies, or adequate crew training, intrusions like the one demonstrated can occur without drawing attention.
Recognizing these risks through controlled evaluations allows ship operators, port authorities, and classification societies to better understand their exposure and refine the safeguards they rely on. The insights gathered through this methodology provide a foundation for improving shipboard network protection and reinforcing broader cybersecurity strategies.
4. Results and Discussion
The test conducted near the Port of Rijeka clearly showed how easily shipboard wireless networks can be exposed when basic security precautions are missing. Despite relying on relatively simple tools and a modest setup, the operation succeeded in demonstrating the vulnerabilities that can arise in real-world maritime environments, particularly when vessels are docked and within range of public infrastructure.
By replicating the SSID of an active shipboard Wi-Fi network, the rogue AP deployed in this test attracted multiple crew devices, including smartphones and laptops, in a short amount of time. Most of these devices were set to auto-connect, and many lacked the safeguards necessary to verify whether the network they were joining was legitimate [12,14]. Both unencrypted and WPA2-like configurations were used during testing, and connections occurred even in the absence of encryption, suggesting widespread issues in device configuration and user awareness, consistent with earlier assessments in similar maritime contexts [6,10,19].
A brief activation of a fake login page through the Evil Portal module illustrated the feasibility of social engineering tactics in this setting. Given that users aboard ships are often accustomed to captive portals, even a modestly convincing imitation could trick someone into submitting sensitive credentials [7,20]. Although no real credentials were harvested in this ethical simulation, the Wi-Fi Pineapple Mark VII collected metadata such as DNS queries, HTTP requests, MAC addresses, and SSID probe requests. While individually limited, such data, especially when combined with session cookies or unsecured tokens, can provide a foothold for attackers and potentially enable further compromise of online services [4,8,38,39,40,41].
The vessel involved in this simulation was a private yacht, but the available documentation did not confirm whether it was subject to SOLAS classification or the requirements outlined in IMO Resolution MSC.428(98). Regardless of this uncertainty, the vulnerabilities observed, particularly around weak wireless authentication, poor segmentation, and the ease of device compromise, are directly relevant to SOLAS-compliant vessels exceeding 500 gross tonnage. Under MSC.428(98), such ships must incorporate cyber risk management into their safety management systems, including technical controls, operational procedures, and crew training. As the attack vector demonstrated in this study aligns with the kinds of risks this resolution aims to mitigate, the findings underscore the urgency of extending wireless threat defenses across both regulated and non-regulated vessel types.
Perhaps most concerning was the complete lack of detection during the attack. At no point was the rogue AP challenged, flagged, or disabled. This suggests an absence of WIDS or even basic monitoring, despite international regulatory frameworks like IMO’s Resolution MSC.428(98) or the NIST Cybersecurity Framework, which recommend such systems as part of risk-based defenses [2,3,31,42]. Without these mechanisms in place, ships remain vulnerable to unauthorized wireless access and data interception. Although WIDS/WIPS technologies such as Kismet or commercial equivalents were not deployed in this simulation, their absence and the complete lack of detection during the attack highlight the urgent need for their evaluation in future maritime environments.
Due to scope and ethical constraints, this study focused on exposure in an unmonitored setting. However, the assessment of WIDS/WIPS effectiveness aboard vessels is planned as a dedicated line of future work, enabling a more comprehensive practical validation of defensive capabilities under real-world port conditions.
From a technical standpoint, the Wi-Fi Pineapple Mark VII maintained a stable signal at a range of roughly 30 to 50 m, thanks to clear line-of-sight positioning. To better frame the technical conditions under which the attack occurred, we note the following parameters. The duration of the experiment was approximately 55 min, divided into a 15 min reconnaissance phase and 40 min of active rogue AP deployment. Transmission power on the Wi-Fi Pineapple was set to its default level (18 dBm), and signal strength was adjusted to remain within expected port-safe emission levels [23,37]. These parameters were selected to reflect real-world attacker constraints while ensuring ethical and non-intrusive execution of the test.
It should be noted, however, that this single 55 min simulation was limited by practical and ethical constraints typical for live testing in active port environments. The study did not include repeated trials or controlled variations in environmental factors such as weather, radio frequency interference, or time-of-day effects, nor were detailed performance metrics like packet loss, connection stability, or signal-to-noise ratios recorded. These limitations mean the findings are indicative rather than definitive, highlighting the need for further comprehensive studies under varied conditions.
Despite these limitations, the experiment provides valuable insights into the practical challenges and risks involved. While such proximity would be harder to achieve in open waters, port settings provide attackers with ample opportunities, whether from shore, adjacent berths, or even nearby cafés [14,37]. More advanced equipment, such as directional antennas, could significantly extend this range, especially if used from small watercraft or hidden on nearby infrastructure.
Still, practical limitations must be considered; most shipboard devices operate under IEEE 802.11 standards such as 802.11n and 802.11ac, which, while theoretically supporting ranges of up to 180 m, are heavily affected by the ship’s metal structures [43]. These conditions degrade signal strength and stability, meaning attackers would need close proximity and direct line-of-sight to maintain a reliable connection [8,28,37,44]. Despite these physical constraints, the controlled simulation still demonstrated that under typical port conditions, wireless compromise remains not only plausible but also operationally effective.
As shown in Figure 3, the rogue AP captured multiple device connections along with associated traffic metadata. Logs included repeated requests to common services, visible hostnames, and device fingerprints, offering a useful glimpse into user patterns and potential entry points.
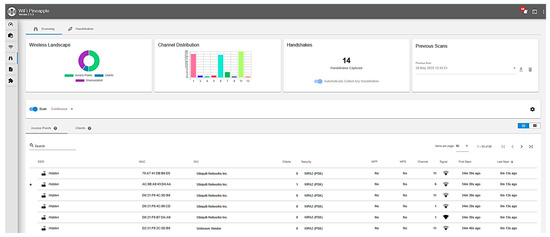
Figure 3.
Captured traffic and connection logs from rogue access point during simulation.
To better represent the scope of wireless activity during the simulation, Figure 4 presents key metrics collected by the rogue access point. The data includes SSID probe requests and client device associations, reflecting discovery and automatic connection behavior by nearby devices. A total of nine devices associated with the rogue AP and more than 20 SSID probes were detected. Additionally, 14 WPA2 handshakes were passively captured, without any attempt at decryption or credential harvesting. The device also logged approximately 95 DNS queries and 110 unsecured HTTP requests. While modest in absolute terms, these figures offer a compelling snapshot of the metadata exposure that can occur in under one hour of port-side operation using a rogue access point.
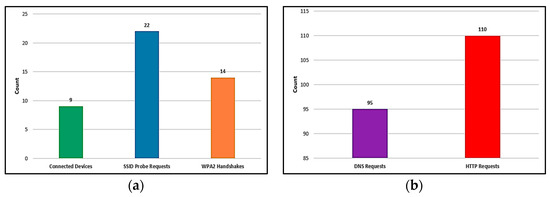
Figure 4.
Logged wireless activity metrics from the rogue access point: (a) network-layer wireless activity; (b) application-layer metadata.
Although limited in scope, this dataset illustrates how easily and passively wireless metadata can be captured, even under minimal conditions. The intent here was not to claim statistical generalizability but to show that meaningful insights can emerge from short-duration, real-world simulations. Future studies applying structured test plans and broader vessel sampling could offer stronger empirical grounding.
These values, though limited in duration and scope, are indicative of persistent vulnerabilities found across the maritime sector. Even brief rogue AP deployments can yield a meaningful volume of device associations and metadata, suggesting that real-world attackers, particularly those with longer access windows or enhanced equipment, could harvest significantly more information. The automatic behavior of crew devices, coupled with insufficient verification mechanisms, confirms how routine operational habits can translate into measurable security exposure. Importantly, this reinforces that wireless metadata leakage is not only a theoretical concern but a quantifiable risk that merits active mitigation within cyber risk management strategies.
While the tools used in this assessment did not capture the encryption configurations of surrounding networks, this limitation is acknowledged. Nonetheless, previous studies indicate that many maritime systems continue to operate legacy wireless technologies due to prolonged hardware use and limited modernization. These conditions may result in the persistence of insecure configurations, such as WEP-based access points, particularly on vessels not subject to regular IT lifecycle updates [45].
Although encryption standards like WPA2 and WPA3 are mentioned in the context of broader security practices, their technical robustness was not the focus of this study. The intention was not to conduct formal cryptographic testing or evaluate the comparative strength of encryption protocols but to demonstrate how wireless exposure can occur in realistic conditions, primarily due to misconfigurations, automatic connection behaviors, and the absence of monitoring tools. More detailed benchmarking of specific wireless security setups is recognized as a valuable direction for future, controlled testing environments.
The simulation highlighted the susceptibility of shipboard Wi-Fi networks and showed that exploitation could be achieved with minimal technical effort. The absence of network segmentation, monitoring tools, or access control policies makes such intrusions almost trivial to execute.
5. Recommendations and Future Work
To address the vulnerabilities observed, international regulatory frameworks such as those issued by the IMO and supported by BIMCO stress the need for a defense-in-depth strategy that incorporates both technical solutions and operational protocols. Technically, ships are advised to implement encryption protocols such as WPA2 or WPA3, maintain segmented wireless networks through VLANs and firewalls, and routinely update credentials, all of which are standard expectations under modern maritime cybersecurity frameworks [3,31].
While WPA2 remains a common standard aboard many vessels, it is not without weaknesses. One notable example is the KRACK attack, which exploits vulnerabilities in the WPA2 4-way handshake to intercept or manipulate traffic. Mitigating this risk typically requires firmware updates that implement protections against key reuse. In cases where older access points and client devices do not support such updates, mitigation may depend on replacing outdated hardware or installing open-source firmware like OpenWRT, which offers WPA2 countermeasures for compatible equipment [46].
These recommendations are deliberately framed within practical constraints, recognizing the varied capabilities of maritime operators. While high-assurance configurations such as WPA3 Enterprise with certificate-based authentication are ideal, even incremental upgrades, such as enforcing complex WPA2 passphrases, disabling legacy modes, and applying vendor firmware updates, can offer substantial protection in port environments where exposure risk is highest.
To support these implementation considerations, the following overview outlines the relative strengths and weaknesses of common wireless encryption protocols observed in maritime settings. Various wireless encryption protocols offer differing levels of protection, and their presence aboard vessels reflects both technological diversity and uneven security practices. Older standards such as WEP and WPA-PSK are now considered insecure, susceptible to rapid key recovery and brute-force attacks. In contrast, WPA2-PSK and WPA3-SAE represent more secure options, offering stronger encryption and resilience against common threats like dictionary attacks and key reinstallation exploits. Transitional configurations such as WPA2-PSK/WPA3-SAE mixed mode allow broader compatibility but may inherit the weaker properties of the older standard if not carefully managed. In port environments, it is not uncommon to encounter open or poorly secured networks, such as those operating in OWE (Opportunistic Wireless Encryption) mode or lacking encryption entirely, especially on non-commercial or privately configured systems. From a security standpoint, any configuration that does not enforce modern WPA2 or WPA3 standards should be considered a liability in maritime deployments.
Encryption protocols and firmware upgrades alone are not sufficient; vessels must also implement physical and operational measures to contain signal propagation and reduce exposure risks. Adjusting how antennas are positioned and reducing the strength of the wireless signal can help ensure that connectivity stays within the limits of the ship. For instance, a high-gain directional antenna such as a 14 dBi Yagi can increase the effective range by approximately 150% to 300% under favorable conditions. In practical terms, this means that the 30–50 m range observed in the simulation could be extended to around 75–125 m, or even up to 200 m in optimal scenarios, particularly when deployed from a nearby vessel, elevated platform, or shore-based location [47,48]. At the same time, it is important to keep an updated list of all wireless equipment onboard, set clear guidelines for its use, and routinely check the network setup to help maintain a secure and stable connection environment.
These measures are not exclusive to large vessels or organizations with extensive IT budgets. Smaller commercial ships can and should take foundational steps such as disabling guest network access, changing wireless credentials following crew rotations, and leveraging portable wireless intrusion detection tools for occasional checks. Even minimal, well-targeted investments can significantly reduce the likelihood of unauthorized access.
While only the Wi-Fi Pineapple was used in this simulation, it is important to consider what a determined attacker could accomplish with additional tools such as Aircrack-ng for password cracking, SSLStrip for HTTPS downgrades, or even malware injection kits [24,35]. Conversely, detection tools like Kismet or Wireshark, though not used here, could help uncover anomalies such as rogue APs, SSID duplication, or suspicious traffic patterns [26,30].
Preventive strategies must integrate these technical foundations with clear policies and user training to ensure consistent application and oversight. In addition to these technical measures, it is equally important to carry out routine checks, use wireless intrusion detection tools where possible, and ensure crew members receive basic cybersecurity training [49,50,51]. Even relatively small steps, like avoiding shared passwords or limiting which devices can access the network, can improve overall resilience [52].
The findings from this test highlight just how urgent it is for ship operators to shift toward a more preventive approach. Weaknesses in wireless setups are not just minor technical flaws; they can serve as the first link in a much larger chain of compromise [53]. In a sector where safety and uninterrupted operations are critical, securing the wireless layer deserves the same attention as any other core system, not just for data integrity, but for the continued safety and operability of the entire vessel.
However, the scope of this simulation was subject to practical constraints that warrant acknowledgment. This study was carried out in a single-port environment at the Port of Rijeka, centered on one vessel that was accessible from a public location. The decision to focus on a single setting was shaped by logistical limitations, safety concerns, and the requirement to maintain ethical oversight during the experiment. While the findings offer a plausible representation of wireless vulnerabilities under typical port-side conditions, they should not be assumed to reflect all vessel types or operational environments. Future research involving multiple ports, vessel categories, and use-case scenarios is recommended to assess the consistency and broader relevance of the patterns observed here. This simulation did not involve credential harvesting or decryption attempts, which were deliberately limited to visible metadata.
To place the findings of this experiment into a broader context, a comparative overview of related studies is included in Appendix A. It highlights research addressing Wi-Fi vulnerabilities, rogue access points, and cybersecurity threats in maritime and adjacent sectors. Although many of these works focus on theoretical analysis or lab-based simulations, relatively few document live testing under real port conditions with operational vessels. This study stands apart in that regard, using a practical “outside-in” approach involving common penetration tools, such as the Wi-Fi Pineapple Mark VII and Evil Portal under realistic, controlled constraints. The simulation required no physical access, relying solely on standard auto-connect behavior and attacker proximity.
Compared to earlier literature that often omits field conditions or emphasizes conceptual threats, the approach here yielded actionable data rooted in operational maritime infrastructure. Metadata, including MAC addresses, DNS queries, and unsecured HTTP traffic, was collected non-invasively, confirming that even short-term rogue access deployments can produce meaningful insights into potential vulnerabilities. The absence of any detection or response during the test further illustrates how current shipboard systems may lack essential monitoring capabilities, such as WIDS. As summarized in the comparative table, this work contributes by bridging the gap between theoretical modeling and hands-on, ethically conducted field testing. The outcomes support the argument for strengthening shipboard wireless security, especially in high-exposure environments such as port berths.
Proactive and Reactive Controls for Securing Onboard Wireless Networks
Building on the previous recommendations, it is clear that managing wireless network security aboard vessels requires a balanced approach combining both proactive and reactive measures. Proactive controls aim to reduce vulnerabilities before incidents occur, while reactive controls ensure effective response if an issue arises.
Proactive controls focus on technical and organizational steps that make unauthorized access more difficult. Some key measures include the following:
- Implementation and regular updating of modern security protocols such as WPA3. Ensuring proper configuration and strong password policies is crucial to prevent unauthorized access. Without this, even the best hardware can be compromised.
- Segmentation of network domains through VLANs and firewall rules. This limits the ability of attackers to move laterally between different systems onboard, containing potential damage.
- Deployment and maintenance of WIDS/WIPS. These systems help monitor networks in real time, alerting operators to suspicious activity like rogue access points before they can cause harm.
- Continuous monitoring of the RF spectrum. Timely detection of unauthorized wireless devices or anomalous signals is essential, especially in high-risk port environments.
- Ongoing training for crew and IT personnel. Recognizing suspicious network behavior and proper use of wireless infrastructure greatly reduces human error and enhances overall security.
- Clear policies governing wireless network usage. Including change management and configuration monitoring helps maintain a consistent and secure environment.
On the other hand, reactive controls are equally important, as they focus on how the vessel responds to incidents:
- Immediate identification and isolation of compromised devices. This includes disabling rogue APs and changing affected credentials to contain damage quickly.
- Thorough forensic analysis of network logs. Understanding the scope and method of an attack informs future defenses and helps prevent recurrence.
- Notification of relevant authorities and ship management. Compliance with international regulations and internal protocols ensures coordinated and effective incident handling.
- Revising and strengthening security measures post-incident. Lessons learned should lead to policy updates and enhanced training programs.
- Regular security audits and attack simulations. These continuous improvement activities keep defenses sharp and prepare the crew for real-world threats.
In practice, a balanced combination of these proactive and reactive controls, supported by continuous monitoring and awareness among crew members, is vital. This holistic strategy aligns well with international frameworks like IMO MSC.428(98), BIMCO guidelines, and the NIST Cybersecurity Framework, all advocating for integrated maritime cybersecurity risk management.
6. Conclusions
Wireless networks have increasingly become central aboard modern vessels, evolving from optional amenities into essential components of operational routines. They support everything from internal communication and logistics coordination to personal connectivity for crew and passengers. As their role becomes more deeply embedded in shipboard operations, assessing the extent of their security exposure has become increasingly important.
The simulation suggests that wireless intrusion is not merely a theoretical possibility but a realistic risk under typical port-side conditions. Using accessible tools and a constrained setup, the study demonstrated that unauthorized access is alarmingly achievable, fueled by devices auto-connecting to familiar SSIDs, transmission of unencrypted data, and the total absence of real-time detection mechanisms. In practice, these vulnerabilities are sometimes underestimated, especially when safeguards are seen as static solutions rather than part of a continuously evolving defense strategy.
Addressing this exposure demands a shift in how wireless security is conceptualized at sea. Segmentation of wireless networks, consistent application of modern encryption protocols, enforcement of authentication policies, and the deployment of detection systems such as WIDS/WIPS must become standard practice. This comprehensive approach should be complemented by periodic audits, up-to-date access policies, and integration of wireless considerations into broader cybersecurity frameworks.
Technology alone cannot account for the unpredictable dynamics of real-world maritime operations. The ability of crew members to notice unusual patterns, question unexpected changes, and respond to ambiguous situations remains vital. To support this, training must extend beyond formal instruction, including practical drills, scenario-based exercises, and clear escalation procedures. Cybersecurity must therefore be embraced not only as an infrastructure requirement but also as a cultural imperative onboard.
Looking ahead, the wireless footprint aboard vessels is poised to grow significantly. The proliferation of IoT-enabled cargo monitoring, remote diagnostics, and digital navigation aids will increase connectivity layers, introducing both operational benefits and expanded risks. Maintaining a stable and secure wireless environment will require continuous attention and timely adjustments. While emerging security tools offer promising capabilities, many existing safeguards remain effective when consistently applied, updated, and supported by sound operational judgment.
Ultimately, securing the wireless layer must be viewed as a core element of a vessel’s safety framework. Treating wireless access as a convenience disconnected from critical functions is no longer acceptable. Its compromise can disrupt operations, jeopardize privacy, and open pathways to broader system infiltration. In a sector where even minor oversights may have serious consequences, integrating wireless security into everyday maritime practice is a necessity.
While these arguments emphasize long-term priorities, the immediate findings of this study also merit reflection. The simulation was intentionally limited to a single vessel and port-side setting to reflect a plausible, ethically constrained real-world scenario. The goal was not broad generalization but to demonstrate how wireless compromise can occur in typical maritime contexts. The results, though narrow in scope, highlight vulnerability patterns unlikely to be isolated. Future research involving different vessel classes, multiple port environments, repeated scenarios, and consistent testing protocols is needed to better understand the prevalence and impact of these vulnerabilities.
Author Contributions
Conceptualization, M.V.; investigation, J.Ć., I.P., and A.C.; methodology, M.V., J.Ć., I.P., and A.C.; supervision, M.V.; writing—original draft, J.Ć., I.P., and A.C.; writing—review and editing, M.V. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded under the project line ZIP UNIRI of the University of Rijeka for the research project “Cyber security, resilience and sustainability in the maritime industry” (UNIRI-ZIP-2103-17-22).
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| AKM | Authentication and Key Management |
| AP | Access Point |
| DNS | Domain Name System |
| EAP | Extensible Authentication Protocol |
| ECDIS | Electronic Chart Display and Information Systems |
| FTP | File Transfer Protocol |
| HSTS | HTTP Strict Transport Security |
| HTTP | Hypertext Transfer Protocol |
| HTTPS | Hypertext Transfer Protocol Secure |
| IoT | Internet of Things |
| IT | Information Technology |
| KRACK | Key Reinstallation Attack |
| MAC | Media Access Control |
| MitM | Man-in-the-Middle |
| OT | Operational Technology |
| OWE | Opportunistic Wireless Encryption |
| PSK | Pre-shared Key |
| RF | Radio Frequency |
| SSID | Service Set Identifier |
| VLAN | Virtual Local Area Network |
| WEP | Wired Equivalent Privacy |
| WIDS | Wireless Intrusion Detection System |
| WIPS | Wireless Intrusion Prevention System |
| WPA2 | Wi-Fi Protected Access 2 |
| WPA3 | Wi-Fi Protected Access 3 |
Appendix A
To provide context for the results of this simulation and underscore its distinct contribution, the following table presents a comparison of academic studies that examine Wi-Fi-related cybersecurity threats in maritime and adjacent domains. While many of these works focus on theoretical frameworks or controlled lab settings, few report on in situ experiments conducted aboard operational vessels. This comparison highlights how the present study addresses that gap by offering empirical insights derived from a realistic, real-world attack scenario.

Table A1.
Comparative overview of related experimental studies in maritime Wi-Fi security.
Table A1.
Comparative overview of related experimental studies in maritime Wi-Fi security.
| Study/Source | Research Objective | Methodology | Environment | Tools/Techniques | Key Findings | Limitations |
|---|---|---|---|---|---|---|
| Hearne & Hearne (2020) [10] | Review of penetration tests on ships | Multiple case summaries | Commercial fleet in the UK/EU | Wireshark, manual inspection | Common issues: weak SSIDs, default passwords, poor segmentation | Limited methodological detail |
| Oruc et al. (2025) [16] | Security assessment of integrated navigation systems | Technical analysis and simulation | Simulators and real-world systems | ECDIS forensics, network scanning | Vulnerability through IT/OT convergence | Does not focus on Wi-Fi attacks |
| Kavallieratos et al. (2019) [18] | Cyberattacks against autonomous ships | Theoretical attack models | Lab conditions | MitM, spoofing simulations | Potential for remote command takeover | No real-world Wi-Fi evaluation |
| Carranza et al. (2018) [35] | Tool benchmarking for Wi-Fi penetration | Experimental testing | Lab and semi-field settings | Aircrack-ng, Wireshark, Pineapple | Compared tools for effectiveness | No maritime context |
| Li et al. (2024) [38] | Review of the maritime cyber threat landscape | Systematic literature review | Global commercial perspective | Threat taxonomy, incident classification | Wi-Fi threats noted as rising vector | No empirical demonstrations |
| Cantelli-Forti et al. (2023) [39] | Data exfiltration in maritime/underwater scenarios | Simulated intrusion and analysis | Maritime network models | Sniffing, metadata analysis | Potential leakage via insecure wireless channels | Lacks live vessel experimentation |
| Meucci et al. (2023) [40] | AI-based deception of maritime sensors | Simulations using GANs | Surveillance and imaging systems | Adversarial input simulation | Highlighted risks to visual-based systems | Not focused on communication layers |
| Cantelli-Forti et al. (2019) [41] | Digital forensics in vessel operations | Case study review | Marine transport systems | Log analysis, incident reconstruction | Emphasized the importance of wireless integrity | No specific Wi-Fi attack study |
| Beyah & Venkataraman (2011) [42] | Detection of rogue APs | Taxonomy of detection methods | Technical scenarios | Signal analysis, management frames | Identified MitM mitigation techniques | Pre-maritime relevance |
| This study (present work) | Assessment of shipboard Wi-Fi vulnerabilities | Live simulation of MitM and rogue AP | Rijeka port, real vessel | Wi-Fi Pineapple, Evil Portal | Multiple devices connected, metadata captured | Ethically constrained, single ship |
Note: This selection includes works from maritime and adjacent domains that address Wi-Fi vulnerabilities. While not exhaustive, the comparison emphasizes that relatively few studies involve live wireless assessments conducted in actual maritime contexts. The present work contributes uniquely by replicating a plausible port-side attack scenario and documenting its execution under realistic operational constraints.
References
- The Facilitation Committee; Maritime Safety Committee; The Maritime Safety Committee; The Facilitation Committee. Guidelines on Maritime Cyber Risk Management. 2025. Available online: https://wwwcdn.imo.org/localresources/en/OurWork/Facilitation/FAL%20related%20nonmandatory%20documents/MSC-FAL.1-Circ.3-Rev.3.pdf (accessed on 15 April 2025).
- Maritime Safety Committee. Resolution MSC.428(98). Maritime Cyber Risk Management In Safety Management Systems. 2017. Available online: https://wwwcdn.imo.org/localresources/en/OurWork/Security/Documents/Resolution%20MSC.428(98).pdf (accessed on 15 April 2025).
- BIMCO; CSA; DCSA; ICS; INTERCARGO; InterManager; INTERTANKO; IUMI; OCIMF; WSC; et al. The Guidelines on Cyber Security Onboard Ships. Available online: https://www.ics-shipping.org/wp-content/uploads/2021/02/2021-Cyber-Security-Guidelines.pdf (accessed on 15 April 2025).
- Karim, M.S. Maritime cybersecurity and the IMO legal instruments: Sluggish response to an escalating threat? Mar. Policy 2022, 143, 105138. [Google Scholar] [CrossRef]
- SAFETY4SEA. Guidelines on Maritime Cyber Risk Management. SAFETY4SEA, 15 February 2018. Available online: https://staging.safety4sea.com/main/guidelines-on-maritime-cyber-risk-management/ (accessed on 15 April 2025).
- Kanwal, K.; Shi, W.; Kontovas, C.; Yang, Z.; Chang, C.H. Maritime cybersecurity: Are onboard systems ready? Marit. Policy Manag. 2024, 51, 484–502. [Google Scholar] [CrossRef] [PubMed]
- Marine Log Staff. Marlink: Maritime Cyber Threats up Sharply in 2024. Marine Log, 14 October 2024. Available online: https://www.marinelog.com/news/marlink-maritime-cyber-threats-up-sharply-in-2024/ (accessed on 15 April 2025).
- Akpan, F.; Bendiab, G.; Shiaeles, S.; Karamperidis, S.; Michaloliakos, M. Cybersecurity challenges in the maritime sector. Network 2022, 2, 123–138. [Google Scholar] [CrossRef]
- Ship Universe. The Ultimate Maritime Cybersecurity FAQ. Available online: https://www.shipuniverse.com/the-ultimate-maritime-cybersecurity-faq/ (accessed on 15 April 2025).
- Hearne, N.; Hearne, N. Pen Testing Ships. A Year in Review. Pen Test Partner, 20 February 2020. Available online: https://www.pentestpartners.com/security-blog/pen-testing-ships-a-year-in-review/ (accessed on 15 April 2025).
- Vanhoef, M.; Piessens, F. Key reinstallation attacks: Forcing nonce reuse in WPA2. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; pp. 1313–1328. [Google Scholar]
- Vaishnavi. Wi-Fi PineApple Explained | How Hackers Use This Powerful Gadget for Wireless Hacking, Man-in-the-Middle Attacks, and Penetration Testing. WebAsha Technologies, 12 April 2025. Available online: https://www.webasha.com/blog/wi-fi-pineapple-explained-how-hackers-use-this-powerful-gadget-for-wireless-hacking-man-in-the-middle-attacks-and-penetration-testing (accessed on 20 April 2025).
- Vanhoef, M. Fragment and forge: Breaking {Wi-Fi} through frame aggregation and fragmentation. In Proceedings of the 30th USENIX Security Symposium (USENIX Security 21), Vancouver, BC, Canada, 11–13 August 2021; pp. 161–178. [Google Scholar]
- Okta Inc. Evil Twin Attack: Fake WiFi Access Point Vulnerabilities. Available online: https://www.okta.com/identity-101/evil-twin-attack/ (accessed on 20 April 2025).
- Hatteland Technology AS. Common Cyber-Security Vulnerabilities in Ships. Available online: https://www.hattelandtechnology.com/blog/cyber-security-vulnerabilities-on-board-ships (accessed on 20 April 2025).
- Oruc, A.; Kavallieratos, G.; Gkioulos, V.; Katsikas, S. Perspectives on the Cybersecurity of the Integrated Navigation System. J. Mar. Sci. Eng. 2025, 13, 1087. [Google Scholar] [CrossRef]
- Kavallieratos, G.; Diamantopoulou, V.; Katsikas, S.K. Shipping 4.0: Security requirements for the cyber-enabled ship. IEEE Trans. Ind. Inform. 2020, 16, 6617–6625. [Google Scholar] [CrossRef]
- Kavallieratos, G.; Katsikas, S.; Gkioulos, V. Cyber-attacks against the autonomous ship. In Computer Security: ESORICS 2018 International Workshops, CyberICPS 2018 and SECPRE 2018, Barcelona, Spain, 6–7 September 2018, Revised Selected Papers; Springer International Publishing: Cham, Switzerland, 2019; pp. 20–36. [Google Scholar]
- SAFETY4SEA. 6 Common Cyber Risks Affecting Maritime Industry. SAFETY4SEA, 4 December 2019. Available online: https://safety4sea.com/cm-6-common-cyber-risks-affecting-maritime-industry/ (accessed on 20 April 2025).
- Marlink Group. Marlink Security Operations Centre Report Shows Continued Evolution of Maritime Cyber Threats. Marlink | Managed Service Provider | Possibility Enablers. Available online: https://marlink.com/news/news-resources/marlink-security-operations-centre-report-shows-continued-evolution-of-maritime-cyber-threats/ (accessed on 25 April 2025).
- U.S. Coast Guard; U.S. Department of Homeland Security. Navigation and Vessel Inspection Circular (NVIC) 01–20 Guidelines for Addressing Cyber Risks at Maritime Transportation Security Act (MTSA) Regulated Facilities. 26 February 2020. Available online: https://www.dco.uscg.mil/Portals/9/DCO%20Documents/5p/5ps/NVIC/2020/NVIC_01-20_CyberRisk_dtd_2020-02-26.pdf?ver=2020-03-19-071814-023 (accessed on 25 April 2025).
- Khan Academy. Available online: https://www.khanacademy.org/computing/computers-and-internet/xcae6f4a7ff015e7d:online-data-security/xcae6f4a7ff015e7d:cyber-attacks/a/rogue-access-points-mitm-attacks (accessed on 25 April 2025).
- WiFi PineApple Mark VII | WiFi PineApple Mark VII. Available online: https://docs.hak5.org/wifi-pineapple (accessed on 25 April 2025).
- Aircrack-ng. Available online: https://www.aircrack-ng.org/doku.php?id=aircrack-ng (accessed on 25 April 2025).
- Editor. Jamming—It’s Not Just for GPS Anymore! RNTF, 21 October 2021. Available online: https://rntfnd.org/2021/01/06/jamming-its-not-just-for-gps-anymore/ (accessed on 25 April 2025).
- Jmporup. What Is Wireshark? What This Essential Troubleshooting Tool Does and How to Use It. CSO Online, 17 September 2018. Available online: https://www.csoonline.com/article/566309/what-is-wireshark-what-this-essential-troubleshooting-tool-does-and-how-to-use-it.html (accessed on 2 May 2025).
- Ship Universe. 2025 Maritime Cybersecurity Regulations: A Simplified Breakdown. Available online: https://www.shipuniverse.com/2025-maritime-cybersecurity-regulations-a-simplified-breakdown/ (accessed on 2 May 2025).
- Bothur, D.; Zheng, G.; Valli, C. A Critical Analysis of Security Vulnerabilities and Countermeasures in a Smart Ship System; Edith Cowan University: Joondalup, Australia, 2017. [Google Scholar]
- Nippon Kaiji Kyokai. Guidelines for Designing Cyber Security Onboard Ships. 2020. Available online: https://www.nextdeal.gr/sites/default/files/sitefiles_2020-07/guidelines_for_designing_cyber_security_onboard_ships.pdf (accessed on 2 May 2025).
- Kismet Wireless. Kismet. 9 August 2022. Available online: https://www.kismetwireless.net/docs/readme/intro/kismet/ (accessed on 2 May 2025).
- National Institute of Standards and Technology. Framework for Improving Critical Infrastructure Cybersecurity. 2018. Available online: https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf (accessed on 2 May 2025).
- ISO/IEC 27001:2022; Information Security, Cybersecurity and Privacy Protection—Information Security Management Systems—Requirements. ISO: Geneva, Switzerland, 2022. Available online: https://www.iso.org/standard/27001 (accessed on 2 May 2025).
- Avada. Acronis Ransomware Protection: The Ultimate Guide to Safeguarding Your Data in 2025. KingsGuard, 30 January 2025. Available online: https://kings-guard.com/how-is-wireshark-used-in-cybersecurity/ (accessed on 2 May 2025).
- Kismet | CISA. Cybersecurity and Infrastructure Security Agency CISA. Available online: https://www.cisa.gov/resources-tools/services/kismet (accessed on 2 May 2025).
- Carranza, A.; Mayorga, D.; DeCusatis, C.; Rahemi, H. Comparison of wireless network penetration testing tools on desktops and raspberry Pi platforms. In Proceedings of the 16th LACCEI International Multi-Conference for Engineering, Education and Technology, Lima, Peru, 18–20 July 2018; pp. 1–5. [Google Scholar]
- Hautzinger, D. The Wifi Pineapple-The Forbidden Fruit of Networking. In Proceedings of the Summer Interdisciplinary Research Symposium, Valparaiso, IN, USA, 7–12 July 2021; Available online: https://scholar.valpo.edu/sires/102/ (accessed on 2 May 2025).
- Witemyre, S.J.; Abegaz, T.T.; Payne, B.R.; Mady, A. Hijacking Wireless Communications Using WiFi Pineapple NANO as a Rogue Access Point. In Proceedings of the 2018 KSU Proceedings on Cybersecurity Education, Research and Practice (CCERP), Kennesaw, GA, USA, 29 October 2018; Available online: https://digitalcommons.kennesaw.edu/ccerp/2018/practice/5/ (accessed on 2 May 2025).
- Li, M.; Zhou, J.; Chattopadhyay, S.; Goh, M. Maritime Cybersecurity: A Comprehensive Review. arXiv 2024, arXiv:2409.11417. [Google Scholar]
- Cantelli-Forti, A.; Colajanni, M.; Russo, S. Penetrating the silence: Data exfiltration in maritime and underwater scenarios. In Proceedings of the 2023 IEEE 48th Conference on Local Computer Networks (LCN), Daytona Beach, FL, USA, 2–5 October 2023; pp. 1–6. [Google Scholar]
- Meucci, G.; Karahoda, B.; Oveis, A.H.; Mancuso, F.; Jajaga, E.; Cantelli-Forti, A. Naval cybersecurity in the age of ai: Deceptive isar images generation with gans. In Proceedings of the 2023 IEEE 48th Conference on Local Computer Networks (LCN), Daytona Beach, FL, USA, 2–5 October 2023; pp. 1–6. [Google Scholar]
- Cantelli-Forti, A.; Colajanni, M. Digital forensics in vessel transportation systems. In Foundations and Practice of Security, 12th International Symposium, FPS 2019, Toulouse, France, 5–7 November 2019, Revised Selected Papers; Springer International Publishing: Cham, Switzerland, 2019; pp. 354–362. [Google Scholar]
- Beyah, R.; Venkataraman, A. Rogue-access-point detection: Challenges, solutions, and future directions. IEEE Secur. Priv. 2011, 9, 56–61. [Google Scholar] [CrossRef]
- IEEE SA. IEEE Standards Association. Available online: https://standards.ieee.org/ieee/802.11/7028/ (accessed on 2 May 2025).
- Jana, S.; Kasera, S.K. On fast and accurate detection of unauthorized wireless access points using clock skews. In Proceedings of the 14th ACM international conference on Mobile computing and networking, San Francisco, CA, USA, 14–19 September 2008; pp. 104–115. [Google Scholar]
- Cantelli-Forti, A.; Longo, G.; Oveis, A.H.; Russo, E. Insights from field experience: Digital forensics of event and voyage data recorders in transportation systems accident investigation. Int. J. Inf. Secur. 2025, 24, 1–19. [Google Scholar] [CrossRef]
- Alhamry, M.; Elmedany, W. Exploring Wi-Fi WPA2 KRACK vulnerability: A review paper. In Proceedings of the 2022 International Conference on Data Analytics for Business and Industry (ICDABI), Virtual, 25–26 October 2022; pp. 766–772. [Google Scholar]
- Friis, H.T. A note on a simple transmission formula. Proc. IRE 1946, 34, 254–256. [Google Scholar] [CrossRef]
- Rademacher, M.; Jonas, K. Interference of Simulated IEEE 802.11 Links with Directional Antennas; IEEE: Piscataway, NJ, USA, 2017; pp. 27–32. [Google Scholar]
- Chupkemi, D.C.; Mersinas, K. Challenges in Maritime Cybersecurity Training and Compliance. J. Mar. Sci. Eng. 2024, 12, 1844. [Google Scholar] [CrossRef]
- Erstad, E.; Ostnes, R.; Lund, M.S. An operational approach to maritime cyber resilience. Int. J. Mar. Navig. Saf. Sea Transp. 2021, 15, 27–34. [Google Scholar] [CrossRef]
- Raimondi, M.; Longo, G.; Merlo, A.; Armando, A.; Russo, E. Training the maritime security operations centre teams. In Proceedings of the 2022 IEEE International Conference on Cyber Security and Resilience (CSR), Virtual, 27–29 July 2022; pp. 388–393. [Google Scholar]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Gritzalis, S. Intrusion detection in 802.11 networks: Empirical evaluation of threats and a public dataset. IEEE Commun. Surv. Tutor. 2015, 18, 184–208. [Google Scholar] [CrossRef]
- Horowitz, B.M. Cyberattack-resilient cyberphysical systems. IEEE Secur. Priv. 2020, 18, 55–60. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).