1. Introduction
The maritime transportation sector plays a vital role in the global economy, facilitating over 80% of global trade, as estimated by the United Nations [
1]. This sector encompasses ships, ports, operating companies, and all infrastructure necessary for transporting goods and passengers via waterways. Given its critical importance, disruptions can lead to substantial financial losses and social ramifications. The 2017 Maersk cyberattack, for instance, resulted in damages amounting to nearly 300 million USD [
2], demonstrating the far-reaching consequences of cyber incidents. Beyond financial impacts, disruptions in maritime operations can have severe humanitarian consequences, particularly in regions where ships serve as the primary means of connectivity. A cyberattack compromising a rescue vessel, for example, could delay emergency response, potentially resulting in loss of life.
Despite the increasing integration of Information Technology (IT) and Operational Technology (OT) in the maritime sector, cybersecurity adoption has lagged behind compared to other industries. As Erbas et al. [
3] indicate, the interconnection and automation of ship subsystems introduce new cybersecurity threats, necessitating stronger cybersecurity frameworks. Onishchenko et al. [
4] emphasize that most modern ships lack dedicated cybersecurity specialists, structured incident response mechanisms, and robust encryption protocols, leaving them highly susceptible to sophisticated cyberattacks. The lifecycle of ships, typically spanning 25–30 years, inherently slows the implementation of new technological advancements and, more importantly, security best practices [
5]. While most cyberattacks, such as the Maersk incident, primarily target IT systems, the majority of systems onboard vessels are OT systems, which control the physical state of a ship. The International Maritime Organization (IMO) and related governmental agencies have begun addressing maritime cybersecurity, and significant gaps remain, particularly concerning vessels. The IMO adopted a resolution requiring cyber risks to be incorporated into safety management systems by 2021 [
6]. To further enhance the cyber resilience of ships, the International Association of Classification Societies (IACS) introduced requirements for cyber resilience of ships and on-board systems and equipment, which took effect for new ships on 1 January 2024 [
7,
8,
9]. While these initiatives reflect growing industry attention to maritime cybersecurity, research in this domain remains insufficient, necessitating further systematic investigation.
The maritime industry’s delayed adoption of cybersecurity measures, particularly in OT environments, leaves vessels highly susceptible to cyber threats. Unlike IT systems, which focus on data processing, communication, and administrative functions, OT systems control and monitor physical processes essential to ship operations, including navigation, propulsion, and power management. The integration of IT and OT has improved efficiency but has also introduced new cybersecurity vulnerabilities, as OT systems, which were originally designed for reliability and safety, often lack robust security mechanisms found in modern IT networks. The lack of systematic methodologies for identifying, modeling, and validating maritime cyber threats further exacerbates this challenge. To mitigate these risks, structured threat modeling approaches are necessary to account for real-world attack scenarios and their potential consequences. This study aims to answer the following research question: What are the possible attack scenarios against a ship?
To systematically explore maritime cyber threats, this study employs attack trees, a structured threat modeling methodology widely used in cybersecurity analysis. An attack tree is a hierarchical diagram that systematically represents potential cyberattack scenarios, with the main objective at the root and various attack paths branching out to show different ways an attacker could achieve that objective. Attack trees provide a structured approach for analyzing vulnerabilities, mapping attack sequences, and assessing potential impacts.
This study builds upon a comprehensive literature review to extract and analyze cyberattack scenarios in maritime operations. The findings from prior research form the foundation for constructing attack trees, ensuring that identified threats align with real-world cyber risks. By integrating these insights with expert validation, the study strengthens existing knowledge while developing structured cybersecurity threat models.
By synthesizing insights from both the literature and expert interviews, this research constructs attack trees that represent realistic cyber threats targeting ship systems. The final step involves validating these attack scenarios through expert evaluations to ensure their feasibility and relevance in real-world maritime operations.
Unlike previous studies that primarily document past incidents or present isolated vulnerabilities, this research takes a systematic approach to cyber threat modeling by integrating expert perspectives to enhance its validity and real-world application. In this study, experts are defined as professionals with significant experience in maritime operations, ship systems, and cybersecurity, including ship captains, technical consultants, cybersecurity officers, and researchers. A total of 10 experts participated in structured interviews, providing diverse insights on attack feasibility, system vulnerabilities, and real-world operational challenges. It contributes to maritime cybersecurity by combining literature review and expert interviews to develop structured attack trees that model cyberattack scenarios in a maritime context, ensuring alignment with industry realities through expert validation.
The subsequent sections of this paper outline the study’s comprehensive approach to exploring maritime cybersecurity threats.
Section 2 provides background on maritime systems and a review of relevant literature on cyber risk management in the maritime domain along with a brief summary of various systems of a ship.
Section 3 presents the details of the methodology, and how insights from the literature and expert interviews were gathered.
Section 4 presents the generated attack trees, categorizing scenarios by their goals.
Section 5 validates these scenarios with expert feedback, examining their feasibility and operational impact, while also discussing broader vulnerabilities and challenges. Finally,
Section 6 concludes with an analysis of findings, implications for the maritime industry, and recommendations for future research.
2. Background
This section provides foundational context on maritime cybersecurity, summarizing prior research and outlining the key shipboard systems relevant to cyber risk. The discussion first reviews existing studies on maritime cyber risk assessment methodologies and identified vulnerabilities, highlighting the evolving threat landscape. This is followed by an overview of critical ship systems, including navigation, communication, and OT networks, emphasizing their interdependencies and cybersecurity challenges. Together, these elements establish the groundwork for understanding maritime cyber risks and the necessity of structured threat modeling approaches.
2.1. Previous Work on Ship Systems’ Cybersecurity
Cyber risk management in the maritime domain has received increasing attention over recent years, particularly as the integration of digital technologies in ship systems has expanded. While risk studies and models exist in the literature, no work has utilized attack trees to systematically represent attack paths to ships. Instead, previous research has primarily focused on cyber risk assessment methods, threat models, and analyses of vulnerabilities, human factors, and legal frameworks, as we discuss in detail in this section with references to prior studies.
Awan and Al Ghamdi [
10] conducted an early review of 59 historical incidents involving ship OT, particularly the integrated bridge system. Similarly, Tam and Jones [
11] introduced the Maritime Cyber-Risk Assessment (MaCRA) framework, a cyber risk assessment approach tailored to operational risks in advanced maritime systems. These works have contributed foundational knowledge but are limited in their scope, as they do not systematically model attack scenarios or validate them with industry experts.
More recent studies have further explored cyber risk management methodologies. Sahay et al. [
12] compared three cyber risk assessment frameworks—System Theoretic Process Analysis (STPA-Sec), Spoofing, Tampering, Repudiation, Information disclosure, Denial of Service, Elevation of Privilege (STRIDE), and CORAS—applied to CyberShip systems. This comparative analysis emphasized the strengths and limitations of these methodologies for identifying vulnerabilities in maritime cyber-physical systems. Tatar et al. [
13] proposed the Cyber Risk Analysis Method for Maritime Transportation Systems (CRAMMTS), a survey-driven cybersecurity risk assessment model for the maritime transportation sector, incorporating input from maritime professionals to quantify risks at both tactical and strategic levels. These approaches address the growing need for structured frameworks for assessing cyber risks but remain focused on identifying risks rather than systematically modeling attack scenarios.
Several studies have examined specific vulnerabilities and system components in the maritime domain. Soner et al. [
14] conducted a risk sensitivity analysis of the Automatic Identification System (AIS), one of the most vulnerable ship systems [
15], integrating regulatory frameworks like the National Institute of Standards and Technology (NIST) to propose preventative measures. Tatar and Gheorghe [
16] provided a risk-based perspective. Similarly, Dimakopoulou and Rantos [
17] used the NIST Cybersecurity Framework to provide a comprehensive review of vulnerabilities in maritime operations, outlining research gaps and offering recommendations for improved practices.
A growing number of systematic literature reviews have analyzed different aspects of maritime cybersecurity. Larsen and Lund [
18] examined cyber risk perception within the maritime industry, highlighting industry concerns and the need for better risk assessment frameworks. Clavijo Mesa et al. [
19] conducted a systematic review of cyberattack impacts and defenses in maritime supply chains, categorizing common threats such as distributed denial-of-service (DDoS) attacks and malware, while also identifying emerging technologies for enhancing cybersecurity in Industry 4.0 contexts. While this review provides valuable perspectives on overarching challenges and defense mechanisms, it primarily focuses on summarizing known risks rather than systematically modeling specific attack scenarios. Bolbot et al. [
20] outlined key challenges and future research directions, identifying critical gaps in maritime cybersecurity. Ben Farah et al. [
21] enumerated various ship systems, their vulnerabilities, and possible cyber threats, emphasizing the complexity of securing modern vessels. Similarly, Erbas et al. [
3] identified significant challenges in maritime cybersecurity risk assessment, stressing the need for a standardized approach to securing shipboard systems. Although these studies provide valuable insights, they focus primarily on risk identification and assessment rather than systematically modeling attack scenarios.
Threat modeling is a crucial approach to understanding cyber risks, particularly in industrial control systems. Khalil et al. [
22] reviewed threat modeling approaches for industrial control systems, demonstrating how these models help defend networks by analyzing them from an attacker’s perspective. Additionally, Balogun et al. [
23] compared various attacker capabilities within industrial control systems, further illustrating the benefits of structured threat modeling methodologies [
23].
Table 1 presents a summary of existing systematic literature reviews.
Other works have explored human factors and legal issues in maritime cybersecurity. For example, Haugli-Sandvik et al. [
24] analyzed deck officers’ perceptions of cyber risks to IT and OT systems, emphasizing the importance of tailored risk communication and training programs. Meanwhile, Karim [
25] examined the evolving legal landscape in maritime cybersecurity, advocating for reform toward multidimensional cooperation with governmental and non-governmental actors.
While these studies provide valuable insights into cyber risk management, they largely focus on either high-level framework, individual system vulnerabilities, or broader organizational and legal challenges. A systematic approach using attack trees to map out potential attack paths and validate them with expert input remains absent in the literature. Although multiple cyber risk assessment methodologies exist, each has inherent limitations when applied to maritime cybersecurity. The following section compares key methodologies to justify the selection of attack trees in this study.
2.2. Comparison of Cyber Risk Assessment Approaches
Cyber risk assessment in maritime systems relies on various methodologies, each with strengths and limitations. Approaches such as STRIDE and attack graphs provide structured frameworks for evaluating threats but face challenges when applied to complex, interconnected shipboard systems. This study employs attack trees, a hierarchical modeling technique, to systematically analyze cyberattack scenarios while addressing the limitations of other models.
In this study, we utilized attack trees to model cyber threats and their operational impacts. Attack trees provide a systematic method for generating attack scenarios through nodes and operators and uniquely offer the flexibility to define attack steps using free-form text within the nodes [
22]. This feature allows us to integrate detailed operational information into our threat modeling.
Attack graphs, another threat modeling approach, identify attack paths within a target system [
26]. However, they are limited to predefined vulnerabilities or network access weaknesses, making them less adaptable for modeling dynamic maritime cyber threats. Thus, it is challenging to reflect all attack steps and operational facts in these graphs. As the graph node content contains specific vulnerabilities, the generalization of the results obtained from one specific target system to other systems is limited. This modeling alternative requires more specific information about the target system (e.g., OS vulnerabilities, network protocol vulnerabilities). It can be only applied during the design stage when such details can be identified, creating another applicability bottleneck in earlier stages (e.g., requirement analysis).
STRIDE, a widely-known threat modeling method developed by Microsoft [
27], starts with a structured system modeling instrument, a data flow diagram (DFD), and elicits threats for each DFD component. Although this model can provide a systematic approach to threat identification, it lacks notation to include detailed attack steps and operational data. Furthermore, it does not specify the dependencies among various threats. In contrast, such dependencies can be determined by tracing paths from any leaf node to the root in an attack tree.
2.3. Ship Systems
A ship is considered a system of systems, comprising a network of interconnected components. Modern ships rely on OT networks where various tasks can be automated to enhance efficiency by reducing workforce requirements. The systems enable control of numerous subsystems by a small number of people, ensuring functionality in various and often remote environments while the OT systems closely monitor the physical processes throughout the ship and automate safe and reliable operations. These characteristics also make them cyber-physical systems (CPS).
Figure 1 illustrates the key IT and OT systems that support ship operations, including those discussed in this section, such as navigation, operational control, and communication. While this paper focuses on specific ship systems that are relevant to cyber risk assessment, many other OT systems exist, including fire suppression, ballast water management, and dynamic positioning systems, which play essential roles in maritime safety and operational efficiency [
28].
2.3.1. Navigation Systems
Navigation systems are critical for ensuring a safe and efficient route for a vessel is followed. These systems include several interconnected technologies that provide the crew with real-time positional and environmental data.
ECDIS (Electronic Chart Display and Information System): ECDIS serves as the primary navigation tool for modern ships, replacing traditional paper charts with digital displays and integrating data from multiple sensors. Mandated by the IMO for larger vessels since 2009, ECDIS merges input from systems such as AIS [
29], Global Positioning System (GPS) [
29], radar [
29], gyroscopes [
30], and weather stations to provide comprehensive situational awareness [
31]. Redundancies, including backup ECDIS units, are standard to mitigate the risk of system failure. Despite its advantages, ECDIS poses cybersecurity risks, as updates to electronic charts are frequently performed via USB memory sticks [
32], potentially exposing the system to malicious software (Int1). Moreover, research by [
33] demonstrated that IEC61162-450-based ECDIS systems are susceptible to replay, injection, and modification attacks, allowing attackers to manipulate sensor data and compromise navigational integrity.
AIS: AIS operates by exchanging static and dynamic information about a vessel, such as its name, type, payload type, position, course, speed, and destination. Integrated AIS systems share data with ECDIS, while standalone setups include independent GPS sensors. AIS is essential for collision avoidance and situational awareness but is vulnerable to spoofing and data manipulation, which could lead to severe navigational hazards [
34].
Weather Data and Navigational Telex (NAVTEX): Navigation systems integrate data from onboard weather stations and NAVTEX, a radio-based system that transmits navigational warnings and weather forecasts. This information enables crews to adapt to changing environmental conditions and avoid potential hazards.
GPS: Shipborne GPS systems operate similarly to consumer devices but often incorporate Differential GPS (DGPS) technology to improve accuracy. DGPS stations of maritime authorities along coastal areas calibrate satellite data, ensuring precise positional information. However, GPS systems are vulnerable to signal jamming and spoofing, which can disrupt navigation [
35].
2.3.2. Ship OT Systems
OT systems form the backbone of a vessel’s physical operation, encompassing power management, steering, propulsion, and control systems.
Power Management System (PMS): The PMS oversees the generation and distribution of electricity onboard, ensuring sufficient power for thrusters and other systems. It dynamically adjusts generator output based on real-time power consumption and demand. For certain ships, such as electric-propelled ferries, the PMS directly interfaces with the propulsion system. However, the increased interconnectivity of modern shipboard PMSs has introduced cybersecurity risks. A cyberattack targeting these systems could lead to blackouts, propulsion loss, or even permanent damage to essential ship operations, posing significant safety concerns [
20].
Steering and Propulsion Systems: Thrusters are the primary means of propulsion and steering, receiving input from the ship’s wheel. Depending on the vessel, redundancy is often built into these systems, allowing for operation from multiple control points. These systems are critical for maintaining course and ensuring maneuverability. Vulnerabilities in the steering and propulsion network, especially those in the Electronic Control Unit (ECU), can compromise the vessel’s handling [
36].
Integrated Automation System (IAS): The IAS consolidates sensor input from various ship systems, including the PMS and navigation systems, into a centralized platform. It also manages alarm signals and reduces the load on navigation systems by transmitting relevant data to the Voyage Data Recorder (VDR) [
37]. Autopilot systems, which range from basic to highly sophisticated, rely on inputs from ECDIS, GPS, and other sensors to maintain or adjust the ship’s course automatically. Cyberattacks that compromise these systems may cause abrupt course deviations or impair vessel responsiveness [
38].
Autopilot Systems: Autopilot systems range from basic models that maintain speed and course to advanced tracking systems capable of following preplanned routes with speed adjustments. These systems receive input from ECDIS and integrate data from GPS and other sensors, offering operational efficiencies.
VDR: The VDR acts as the ship’s central logging system, recording commands, sensor inputs, and crew communications. While typically used only in the event of incidents, it provides invaluable data for investigations and safety assessments.
2.3.3. Communication Systems and Network Topology
Communication systems and network configurations play a vital role in ensuring the interoperability of ship systems and the secure exchange of data. Effective communication enables seamless interaction between navigation, operational, and external systems.
Ship Network Topology: Network topology onboard ships typically includes segregated OT, guest, and office networks, as recommended by industry guidelines such as the Baltic and International Maritime Council (BIMCO) cyber security standards. Virtual Local Area Networks (VLANs) and firewalls are used to maintain logical separation of traffic between these networks. Despite these measures, interviews (e.g., Int3, Int4) suggest that implementation varies significantly across the industry. Smaller vessels and operators often face resource constraints that limit their ability to implement robust segregation, while larger operators prioritize advanced network security.
Communication Infrastructure: Shipboard communication systems include satellite links, Very Small Aperture Terminal (VSAT) systems, VHF radios, and internal communication networks. These systems are essential for maintaining contact with port authorities, other vessels, and emergency services. However, vulnerabilities in these networks could allow unauthorized access to the OT network, enabling attackers to exploit connected systems.
Mitigating these vulnerabilities requires a layered security approach that addresses multiple attack vectors. Wang et al. [
39] propose a combination of physical, computational, and information-theoretic security measures to enhance network resilience and prevent unauthorized access to critical maritime systems. In a similar vein, Zeng et al. [
40] show that advanced encryption techniques can protect ship–shore communications from attacks aimed at manipulating data. Their findings feature the importance of integrating cryptographic security, network monitoring, and secure routing mechanisms to protect against eavesdropping and data manipulation attacks.
While the integration of these communication systems is critical for the efficient operation of modern ships, it also increases cybersecurity risks. A vulnerability in one system can propagate to others, making it essential to understand these interdependencies. Comprehensive threat models and effective mitigation strategies are therefore needed to ensure the overall security and resilience of maritime operations [
20,
41].
3. Methodology
This study employs a multi-phase methodology to systematically explore cyber attack scenarios against ship systems. The process begins with data collection, which integrates findings from a comprehensive literature review and unstructured expert interviews to establish foundational knowledge and generate potential attack scenarios. These scenarios are then synthesized into attack trees, a widely adopted threat modeling technique, to visually represent the various attack paths. In the final phase, the generated attack trees are validated through structured interviews with industry experts, ensuring their feasibility and relevance in real-world contexts (see
Figure 2).
3.1. Data Collection Phase
The first phase of the methodology focused on gathering foundational knowledge about the ship’s OT systems and potential cyberattack scenarios. This phase comprised two complementary approaches: a literature review and unstructured expert interviews.
3.1.1. Literature Review
The literature review aimed to consolidate existing knowledge on maritime cybersecurity, with a focus on cyber risk management, vulnerabilities in ship systems, and documented attack scenarios. The review process followed a structured approach to ensure a comprehensive and rigorous analysis of relevant academic publications, industry reports, and regulatory guidelines.
To identify relevant literature, keywords were divided into three groups:
General cybersecurity terms: “cyber”.
Attack-related terms: “attack”, “intrusion”, “exploit”, “vulnerability”, and “threat”.
Maritime-specific terms: “maritime”, “sea”, “ship”, “MTS”, “ECDIS”, “GPS”, “AIS”, “VDR”, “GMDSS”, and “PSMS”.
These search strings were applied in Web of Science to limit results to studies pertinent to maritime cybersecurity and attack-related topics.
Papers were included if they addressed vulnerabilities, exploits, attacks, human behavior, or practical examples related to maritime cybersecurity.
Papers were excluded if they:
Were unrelated to the maritime transportation system or offshore systems.
Were focused solely on autonomous ships.
Focused exclusively on frameworks, legislation, or other non-technical topics.
Were inaccessible through institutional resources or is not in English.
After initial screening, 58 articles were identified as most relevant.
Figure 3 presents the distribution of the articles over the years. The literature was analyzed to identify recurring themes, including common attack vectors, network components and architecture, systems’ vulnerabilities, and risk management practices. This process provided a baseline for understanding the current state of knowledge in maritime cybersecurity and informed the subsequent interview phase by revealing gaps in the literature.
3.1.2. Expert Interviews
To complement the findings from the literature review, expert interviews were conducted with professionals from the maritime industry, including ship operators, cybersecurity specialists, and OT engineers. These interviews provided valuable real-world insights into operational practices, cybersecurity challenges, and potential vulnerabilities that are not always explicitly documented in academic sources. Given the complexity of ship systems and their operational environments, expert knowledge was crucial in contextualizing technical aspects and understanding the data flow within a ship’s network.
A total of 13 interviews with 10 different experts were conducted. To mitigate potential biases, experts were selected from diverse backgrounds across different sectors of the maritime industry, ensuring a balanced perspective on cyber threats. Interviewees were selected based on their expertise in maritime operations, ship systems, and cybersecurity, ensuring a range of perspectives that covered both IT and OT domains. The group included ship captains, technical consultants, cybersecurity officers, and researchers, with experience levels ranging from early-career specialists to senior maritime professionals with decades of expertise.
The participants’ professional roles included:
Cybersecurity and IT specialists: Experts in maritime cybersecurity, including the Chief of Information Security at Port of Tallinn and IT infrastructure architects. Their insights were crucial in understanding ship network segmentation, vulnerabilities, and cyber risk management.
Maritime operators and captains: Cargo ship captains, second officers, and marine safety managers, who provided operational perspectives on how attacks might manifest in real-world scenarios and the crew’s ability to detect and respond to threats.
Technical consultants and researchers: Experts with backgrounds in ship engineering, automation systems, and remote maintenance. These professionals contributed to the assessment of the plausibility of technical attacks against ship systems.
Harbor pilots and regulatory advisors: A harbor pilot and head of shipping, along with an advisor from the Estonian Maritime Authority, contributed knowledge about navigation procedures, physical security, and interactions with port authorities.
The interviews were conducted in two phases: an initial exploratory phase and a structured validation phase.
The first phase consisted of five unstructured interviews aimed at gathering background information on ship operations, cybersecurity risks, and technological dependencies. These discussions were open-ended, allowing interviewees to share their experiences and expertise freely.
The second phase involved eight structured interviews that followed a specific set of questions designed to validate the attack scenarios developed in this study. Experts were presented with various cyberattack scenarios and asked to assess their feasibility, potential consequences, and mitigation strategies.
To protect the identities of the interviewees, all references to individual responses in this study are coded as Int1, Int2, etc. The coding ensures anonymization while maintaining the ability to attribute insights to different professional backgrounds.
Expert interviews serve as a widely recognized and rigorous method for validating cybersecurity research when direct testing is not feasible. Prior studies have successfully employed expert interviews as the sole validation method to assess cybersecurity models and frameworks [
42,
43]. Given the complexity of maritime cybersecurity and the impracticality of real-world testing on operational ship systems, this study adopts expert interviews as the validation method.
Appendix A provides the list of questions asked during the structured interviews phase, and
Table 2 summarizes expert input across research stages, detailing key insights from the literature review, attack tree development, and validation phases.
3.2. Attack Tree Methodology
Attack trees are a threat modeling technique used to systematically decompose, analyze, and represent potential attack scenarios. They provide a hierarchical structure where the root node represents the attacker’s primary goal, and the branches depict various sub-goals and actions required to achieve that goal. This structure allows for a clear and logical representation of the steps an adversary might take to compromise a system. The effectiveness of such methodologies depends on a structured classification of cyber risks. Recent research outlines that cyber risks in the maritime domain can be grouped based on attack vectors, affected systems, and potential cascading failures, making systematic threat modeling approaches even more valuable [
44].
Attack trees are used in this study for their versatility in representing attack scenarios concisely. They help identify vulnerabilities, assess risks, and support mitigation planning. Their visual structure also improves communication, making threats easier to understand, even for non-technical audiences.
The adoption of attack trees in cybersecurity is constantly evolving as a methodology. Its compatibility with other frameworks and tools allows the results to serve as inputs for future work. For example, MITRE ATT&CK Framework for Industrial Control Systems offers a comprehensive repository of adversary tactics and techniques that can be integrated into attack trees to enhance their relevance.
While attack graphs were considered as an alternative, they were ultimately deemed less suitable for this study. Lallie et al. [
26] found that attack graphs lack standardization, making their application more challenging and less consistent across different contexts. In contrast, attack trees provide a more structured and widely recognized approach, aligning well with the goals of this research.
4. Results: Attack Tree Generation
The primary contribution of this study is the development of attack trees that systematically represent potential cyberattacks against ship systems. These attack trees illustrate various attack paths, outlining vulnerabilities and the steps an attacker could take to compromise critical ship functions. They serve as a tool for analyzing possible scenarios that could result in significant operational, financial, or safety-related consequences. Furthermore, these scenarios can be utilized as inputs for risk assessments and for developing mitigation strategies.
The ultimate goal of the identified attack trees is to cause damage to the ship, which encompasses both monetary losses and safety impacts, including potential loss of life. Three major high-level goals were identified: crashing the ship, capsizing the ship, and immobilizing the ship. While all these goals result in physical consequences, the pathways to achieving them rely primarily on cyber means while possibly supplemented by physical actions. For example, gaining a foothold in a ship’s systems may require the attacker to physically access or be in close proximity to the targeted system.
Each goal is represented by a distinct attack tree, and a total of 20 high-level scenarios were identified across the three goals: 9 scenarios for crashing the ship, 4 for capsizing the ship, and 7 for immobilizing the ship. However, due to the separation of attack trees into distinct goals and the unification of common elements, such as loss of operational view or initial foothold acquisition, the actual number of potential attack paths is significantly larger. This modularity allows for flexibility in the analysis and adaptation of the attack trees to different contexts.
The attack trees focus exclusively on systems critical to the safe and effective operation of a modern ship. Auxiliary systems, such as entertainment systems on cruise ships, were intentionally excluded to maintain simplicity and generality. Similarly, while redundancy in critical systems (e.g., ECDIS or sensors) is standard practice in ship design, this analysis considers single points of failure to account for instances where redundancy may be improperly implemented, as suggested by findings from interviews (Int1) and prior studies [
30].
The attack trees were constructed using a structured approach based on insights from the literature review and expert interviews. Each branch represents a logical sequence of actions an attacker might take to achieve specific objectives.
The attack tree structure begins with a root node at the top, representing the main attack objective. This node is either an AND or OR node:
OR nodes are green, with a curved bottom edge, indicating that any of the child nodes can lead to the attack goal.
AND nodes are orange, with a flat bottom edge, meaning all child nodes must occur together for the attack to succeed.
Leaf nodes (rectangles at the bottom level) represent basic attack steps or preliminary actions that contribute to higher-level attack paths.
The attack tree structure is designed to be adaptable, meaning new attack scenarios or evolving threats can be incorporated into the model in the future. The current trees were constructed using expert interviews and literature analysis, but additional attack pathways can be added as new vulnerabilities are identified.
The following sections outline the common elements shared across the attack trees, such as infiltrating the network or compromising operational systems, and detail the high-level goals that define the attack scenarios.
4.1. Common Parts of the Attack Tree
The three high-level goals (i.e., crashing the ship, capsizing the ship, and immobilizing the ship) share several recurring components within their attack trees. These common parts represent critical stages or tactics that an attacker might employ regardless of the ultimate goal. By isolating these elements as standalone subtrees, the analysis avoids unnecessary repetition, simplifies interpretation, and facilitates adaptability for different scenarios. These subtrees also outline essential vulnerabilities and potential points of mitigation that are broadly applicable across attack scenarios.
The attack trees presented in this study are modular, with shared components reused across different branches. This modularity improves the clarity and manageability of the analysis, as any adjustments or refinements to these common elements need only be made in a single instance. While the study does not prioritize attacks based on their probability, these modular subtrees could serve as inputs for future research that incorporates probability analysis into risk assessments.
The following subsections detail the key common parts of the attack tree: infiltrating the network, taking control of ECDIS, loss of operational view, and evasion. These components collectively form the foundation for the more complex and goal-specific attack scenarios discussed in subsequent sections.
4.1.1. Infiltrating the Network
Infiltrating a ship’s internal network is a critical step for attackers aiming to compromise OT systems. This process involves exploiting vulnerabilities to gain an initial foothold, which can then be leveraged for further stages of the attack. The attack tree for this component identifies two major approaches: attaching a malicious device and exploiting external interfaces. The former relies on various techniques, such as physical access, social engineering, insider threats, and technical exploitation, as illustrated in the corresponding attack tree (Please see
Figure 4).
The most consistent and effective approach for network infiltration involves physically introducing a malicious device into the ship’s systems. This method allows attackers to bypass external network defenses and directly access critical infrastructure. The sub-goals for this approach include:
Physical Intrusion: An attacker could physically sneak onto the ship and place a malicious device in critical areas such as the bridge, control room, or communication hubs. This method, while challenging, is feasible under specific conditions. For instance, passenger ships provide opportunities for attackers to blend in with guests, although access to crew areas remains more difficult. Social engineering techniques, such as pretending to be a maintenance worker, could increase the likelihood of success. Once a device is connected to the ship’s network, it may enable remote command and control using Wi-Fi or 4G connectivity. For example, a Raspberry Pi device configured with malicious software could exploit guest Wi-Fi for external communication, reducing the risk of detection.
Insider Threat: Leveraging insider threats is another plausible method. Attackers could bribe or coerce a crew member, harbor pilot, or maintenance worker to install malicious hardware. This could involve smuggling the device onboard or directly attaching it to a vulnerable system. The insider threat approach is particularly concerning due to its ability to bypass traditional security protocols entirely.
Social Engineering: Attackers may use deception to gain access, such as impersonating a maintenance worker with scheduled tasks or pretending to be a visitor. Information for such impersonations could be obtained through spear-phishing campaigns or public sources like social media. For example, attackers could exploit knowledge of maintenance schedules or ship schematics to enhance their credibility.
Compromising Intermediate Devices: Maintenance laptops or removable media, such as USB drives used for routine operations (e.g., ECDIS updates), present another significant risk. Attackers could infect these devices with malware, which would then propagate to the ship’s network during maintenance activities. Real-world incidents demonstrate the feasibility of this approach; for instance, a compromised maintenance worker’s device once delayed a ship’s release from a dry dock due to malware propagation [
30,
45]. Additionally, routine updates to navigational systems, such as ECDIS charts via USB, create opportunities for attackers to introduce malware if proper security protocols are not followed.
External-facing interfaces provide another avenue for attackers to infiltrate the ship’s network. Vulnerabilities in VSAT, internet-connected systems, or other external interfaces can be exploited to gain unauthorized access. Specific examples include:
Default Configurations: Attackers may exploit the default configurations of VSAT equipment, which are often publicly available online. By correlating AIS data with VSAT models, attackers can identify vulnerabilities and gain access to the ship’s network [
46].
Outdated Systems: Many shipboard systems run older versions of operating systems, such as Windows, that are no longer supported with security updates. These systems present potential entry points for attackers, especially if the equipment is connected to the internet or if the attacker has already gained a foothold within the OT network [
30,
46,
47,
48,
49,
50].
External interfaces are particularly vulnerable due to their exposure to public networks, making them an attractive target for attackers aiming to bypass internal security measures. Once access is gained, attackers can exploit these entry points to manipulate operational data, such as GPS coordinates, or deploy malware to critical systems.
4.1.2. Taking Control of ECDIS
The ECDIS is a critical navigation tool used on modern ships. Its compromise could provide attackers with significant control over a vessel’s operations, enabling disruptions to navigation and posing severe safety risks. Attackers may employ various methods to take control of ECDIS, focusing on introducing malicious software or compromising the system’s update processes. The corresponding attack tree (See
Figure 5) outlines these pathways.
One of the primary methods to compromise ECDIS is to directly introduce a malicious device into the system. This involves physical access to the ship and executing a malware attack. An attacker physically connects a malicious device, such as a USB drive or other hardware, to the ECDIS terminal. This device could introduce malware designed to manipulate chart data, override system functionality, or disrupt navigation. For example, such a device could upload corrupted charts or alter coordinates displayed to the crew, potentially causing navigational errors.
Real-world incidents indicate the risks posed by such attacks, as removable media remains a frequent vector for malware. Ensuring secure procedures for connecting external devices to ECDIS is critical for mitigating this risk.
Another major pathway involves exploiting vulnerabilities in the ECDIS update process. As indicated by [
51], attackers can manipulate ECDIS and AIS through cyber mechanisms, even in air-gapped environments, by leveraging vulnerabilities in update processes and networked naval systems. Since ECDIS relies on regular chart updates, attackers can target this supply chain in two primary ways:
Compromising Chart Updates via the Internet: Many ECDIS setups rely on internet-based services for updating electronic charts. Attackers could intercept or compromise these updates, introducing malicious modifications to chart files. While some experts deem this attack vector unlikely due to the low prevalence of internet-connected ECDIS systems, it remains a potential risk, particularly in cases where outdated software or insecure connections are used.
Compromising Updates via
Removable Media: Removable media, such as a USB drive, is commonly used to transfer updates to ECDIS systems. Attackers could infect these devices with malware before they are connected to the system, allowing them to manipulate chart data or compromise system functionality. For instance, malware embedded in chart files could distort geographic information, mislead navigational decisions, or disrupt ECDIS operations entirely. Malware infections, particularly via external media and networked systems, are among the most significant threats to ECDIS security. Proper controls such as pre-scanning external devices, restricting USB access, and implementing cryptographic validation of updates can mitigate these risks [
52].
The modular nature of this pathway makes it particularly dangerous. A single compromised supply chain can impact multiple vessels, amplifying the attack’s potential consequences.
4.1.3. Loss of Operational View
Maintaining an operational view is critical to the safe and efficient operation of a ship. The operational view encompasses real-time data from navigation systems, propulsion feedback, and other key subsystems, enabling the crew to make informed decisions. A loss of operational view can lead to significant disruptions, increasing the risk of navigation errors, system failures, and accidents. Attackers seeking to achieve this can target specific systems or leverage environmental conditions to reduce the crew’s situational awareness.
The attack tree for loss of operational view (See
Figure 6) identifies several key methods: modifying sensor data, creating diversions, disabling ECDIS, hiding sensors by altering configuration files, and timing attacks with adverse weather events. Each of these methods can directly impact the crew’s ability to interpret critical data and respond effectively to emergencies.
Attackers can tamper with key sensors that feed data into navigation and operational systems. This includes GPS, radar, echo sounders, and propulsion sensors. As Wolsing et al. [
53] demonstrate, marine radar systems are particularly vulnerable to network attacks, which can introduce false echoes or distort navigational data, leading to incorrect situational awareness and increased collision risks. By altering sensor output, attackers can inject false data into the system, leading to incorrect conclusions about the ship’s position, heading, or operational state.
The sensor data can also be manipulated at the Terminal Processing Unit (TPU), which is a data converter that bridges sensors and the ship’s internal network. If compromised, the TPU could allow attackers to intercept, alter, or block sensor data, leading to incorrect situational awareness and impaired decision-making (Int5).
For instance, GPS spoofing could mislead the ECDIS into displaying incorrect location data, while tampering with propulsion sensors could obscure engine performance or fuel efficiency metrics. Longo et al. [
54] indicate that radar hijacking techniques can alter a ship’s perception of its surroundings, making navigation decisions based on false data particularly dangerous. Such interference directly compromises the operational view and increases the likelihood of errors in decision-making.
Rather than outright disabling systems, attackers could gradually introduce minor inconsistencies in sensor data to erode the crew’s confidence in the system. By doing so, the attacker creates a diversion, distracting the crew from the primary attack or delaying their response.
For example, in the hours or days leading up to an attack, an attacker might sporadically display invalid position data or propulsion feedback. The crew might dismiss these as sensor malfunctions, increasing their reliance on manual validation processes. Over time, this would elevate the crew’s workload, reducing their ability to respond effectively when the actual attack occurs. Studies have documented over-reliance on interface data and the challenges crews face in such scenarios [
55,
56].
The ECDIS is central to navigation and is a key target for attackers aiming to disable operational view. Research in the literature [
53,
57] presents how attackers can manipulate radar and ECDIS data streams to deceive crew members, rendering critical navigation tools unreliable or even useless. The attack tree identifies several methods to render ECDIS unusable:
Encrypting Critical Files: An attacker could deploy ransomware to encrypt essential ECDIS files, rendering the software inoperable. Without access to ECDIS, the crew would need to rely on manual navigation methods, significantly increasing the risk of errors [
58].
Hiding Sensors from ECDIS: By altering configuration files, attackers can hide critical sensors from ECDIS, effectively blinding the system. For example, the attacker could remove mappings between sensors and their respective data streams, preventing the crew from accessing real-time information about the ship’s environment.
Denial of Service (DoS) Attacks: Attackers could overload the ECDIS system with computation-heavy processes, consuming all available computational resources and leaving none for the system’s core functions [
55]. Alternatively, they could delete ECDIS’s underlying operating system or associated files, effectively disabling the entire system. Considering that ECDIS commonly runs on an outdated operating system [
59], this attack vector needs attention [
46,
47,
49].
Certain ship systems, including ECDIS, rely on configuration files to map sensors to their respective data sources. Attackers with sufficient access could corrupt or modify these files, causing the system to lose track of critical sensors. Without these mappings, the crew would be unable to restore operational view, resulting in a denial-of-service condition. This tactic is particularly insidious, as it can render even intact sensors functionally useless.
While weather events are outside an attacker’s control, they can significantly degrade visual means of maintaining an operational view. For example, stormy weather can obscure visual landmarks and reduce the crew’s ability to cross-check sensor data manually. Attackers might time their operations to coincide with such events, exacerbating the crew’s challenges and amplifying the impact of the attack. For instance, publicly available tools can provide attackers with real-time information about a vessel’s location and weather conditions at its destination, enabling precise timing of their operations. Although this study primarily focuses on cyber means, such timing considerations depend on the interplay between environmental and cyber factors.
4.1.4. Evasion
Evasion techniques are integral to many cyberattacks, allowing attackers to obscure their activities and avoid detection during or after an operation. In the maritime context, such actions typically involve tampering with systems that log critical events, preventing forensic analysis and complicating incident response. While evasion techniques in OS are widely known and applicable, this section focuses on a ship-specific example: compromising the VDR [
60].
The VDR functions as the primary logging system on a ship, recording critical data such as navigation commands, system changes, alarms, and communications. Disabling or corrupting the VDR effectively blinds investigators to malicious activities, erasing key evidence of the attack. The corresponding attack tree (See
Figure 7) outlines the primary method for achieving this:
To evade detection, an attacker could stop systems under their control from sending log data to the VDR or corrupting the VDR itself. This could be achieved through the following methods:
Although this article presents a ship-specific example, it is important to note that general evasion techniques used in OS environments, such as modifying system logs or disabling monitoring tools, could also be applied to shipboard systems.
Evasion tactics, particularly those targeting logging mechanisms like the VDR, are essential components of sophisticated cyberattacks. By compromising the integrity of logging systems, attackers can effectively hinder post-incident investigations and minimize the chances of detection during the operation.
4.2. Goals
This section presents the three primary goals of cyberattacks against ship systems: crashing the ship, capsizing the ship, and immobilizing the ship. Each goal is detailed in a separate attack tree, outlining specific pathways and scenarios attackers may exploit to achieve their objectives.
4.2.1. Primary Goal 1: Crashing the Ship
Crashing a ship is a highly destructive goal, capable of causing significant monetary loss, environmental damage, and potential loss of life. As Butchko et al. [
61] discuss, cyber-physical system vulnerabilities in surface ships can allow attackers to manipulate autopilot and navigation controls, increasing the risk of unintended collisions or groundings. Although it may not be as catastrophic as capsizing, crashing a ship can still lead to devastating consequences, as seen in incidents like the Costa Concordia disaster in 2012 [
62]. The attack tree for crashing a ship (See
Figure 8) identifies two primary approaches: colliding with an object and running aground.
One method to crash a ship involves setting it on a collision course with another vessel, iceberg, or floating object. Attackers can achieve this by ensuring two preliminary conditions at the same time: (1) manipulating the ship’s navigation systems to influence the course and (2) rendering commands to the thrusters and wheel inoperable for manual override. As research has demonstrated, internal cyberattacks targeting ship networks can manipulate key sensor data, tricking onboard systems into processing falsified information, thereby affecting navigational decision-making and automation [
63].
While these attacks primarily distort situational awareness, they can also serve as an entry point for deeper intrusions affecting the vessel’s steering and propulsion systems. Once access is gained, attackers can execute the following techniques to force a collision or grounding:
Set Ship on Course with Object: First, the attacker needs the means to change the course of the vessel, via either:
- ○
Sending Malicious Commands to Wheel or Thrusters: Attackers with control over the wheel or thrusters could directly send commands to steer the ship towards an object. This requires access to the ship’s OT network and precise knowledge of its planned route. Butchko et al. [
61] introduce a high-authority supervisory control mechanism that could mitigate such attacks by limiting actuator responses, preventing unsafe maneuvers from being executed even if a cyberattack compromises the control system.
- ○
Forcing Autopilot to Change Course: The autopilot system, particularly tracking autopilots capable of route adjustments, can be manipulated to alter the ship’s direction toward an obstacle. Longo et al. [
64] emphasize that targeted cyberattacks on the Steering Gear Control System (SGCS) can exploit maritime protocols, such as NMEA 0183, to introduce rogue control inputs, leading to unintended ship maneuvers. This could be accomplished through various approaches such as by tampering with inputs of GPS or route data in the ECDIS system., effectively deceiving the autopilot into making incorrect course adjustments.
Denial of Service of Wheel Commands and Thrusters: To ensure the success of a collision, attackers might execute a DoS attack on wheel commands or thrusters, preventing the crew or autopilot from altering the ship’s trajectory once it is on a collision course. This is a required step as a part of causing the ship to collide with an object.
Another method to crash the ship is running it aground. This involves steering it into a shallow area or shoreline, often by tricking the captain or autopilot into making incorrect navigational decisions. This method relies on either manipulating ECDIS or GPS systems:
Manipulated Charts in ECDIS: Attackers could introduce false data into electronic charts, such as incorrect depth readings or nonexistent obstacles. For example, charts could be altered to indicate safe waters where the depth is insufficient, leading the ship to ground itself. Another method could be adding a false object to the chart to compel the captain to steer around it, resulting in an unintentional grounding.
Inject Fake GPS Data: Attackers might use GPS spoofing to provide the ECDIS system with falsified location data. This could cause the captain or autopilot to make navigational corrections that steer the ship off course. Butchko et al. [
61] demonstrate how cyberattacks on ship autopilot systems can overwrite control signals, effectively steering the vessel off its intended route and into hazardous conditions. While GPS spoofing requires proximity to the ship, attackers could overcome this limitation by smuggling a GPS-spoofing device onboard the vessel.
Many of these attacks rely on manipulating the ship’s navigation systems or exploiting the trust placed in sensors and automated systems. For example, gradual modifications to GPS or chart data may go unnoticed by the crew until it is too late to take corrective action. Narrow canals or unfamiliar routes exacerbate the risks, as they limit the crew’s ability to rely on visual landmarks for navigation.
To maximize effectiveness, attackers may time these attacks to coincide with adverse weather conditions or periods of high workload for the crew. Additionally, integrating these attacks with denial-of-service techniques, such as disabling wheel commands, can further reduce the crew’s ability to respond effectively to impending collisions or groundings.
4.2.2. Primary Goal 2: Capsizing the Ship
Capsizing a ship involves destabilizing its physical balance to the point where it overturns. This type of attack focuses on manipulating the ship’s stability systems to align physical forces in one direction, ultimately causing the vessel to capsize. While not universally applicable due to differences in ship types and stability designs, such an attack is more likely to succeed in adverse weather conditions or with certain ship configurations, such as cargo or cruise ships.
The attack tree for capsizing (See
Figure 9) outlines the key preliminary conditions attackers need to meet.
Attackers aim to compromise the ship’s stability by taking control of key systems that govern balance and orientation. These include:
Control Ballast System: The ballast system is responsible for maintaining the ship’s balance by adjusting the distribution of water within its tanks. An attacker could manipulate the ballast pumps to shift water to one side of the ship, creating a tilt.
Control Thrusters: Engaging thrusters at maximum power in an extreme turn can amplify the tilt initiated by the ballast system, pushing the ship closer to capsizing.
Control Anti-Rolling System: For ships equipped with anti-rolling systems, attackers could counteract stabilization efforts. This would further exacerbate the ship’s imbalance and increase the likelihood of capsizing.
Exploit Weather Conditions: Timing the attack during rough seas maximizes its impact. Using data from gyroscope sensors, attackers could synchronize their actions with the natural tilt of the ship caused by waves, executing the attack at the peak of instability.
While the outlined pathways theoretically allow for capsizing, this attack faces several practical challenges. Ship designs incorporate centuries of engineering advancements to mitigate such risks, including physical security measures and manual overrides for electronic systems like ballast pumps. For example, ballast pumps are slow and often feature manual valves to prevent unauthorized electronic commands.
Moreover, successful execution depends heavily on external factors, such as severe weather conditions, which attackers cannot control but can exploit when present. These challenges limit the universality of this attack, making it more plausible in specific scenarios or with particular ship types.
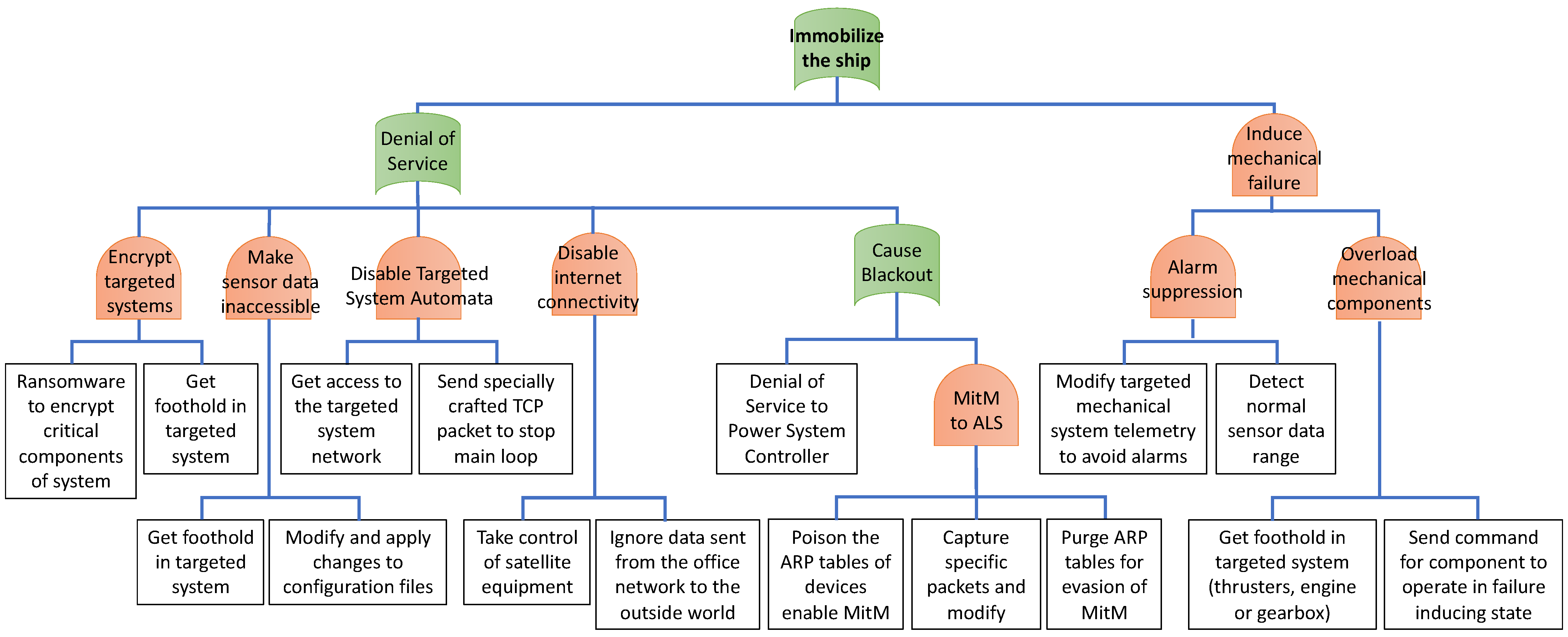
4.2.3. Primary Goal 3: Immobilizing the Ship
The goal of immobilizing a ship is to prevent it from continuing normal operations, leaving it stranded and potentially vulnerable to environmental conditions or further attacks. This can be achieved through two primary approaches: DoS attacks targeting critical systems or inducing mechanical failures [
55,
56]. Both methods leverage the ship’s dependency on automation and interconnected systems to create operational paralysis. The attack tree for immobilizing a ship (See
Figure 10) outlines these two main options.
DoS attacks focus on making critical systems unresponsive to crew input. These attacks, while not always permanent, can render a ship inoperable, especially if the crew lacks the necessary IT skills to resolve the issue. As demonstrated by [
65], ship power management systems and load-shedding controllers are highly vulnerable to cyber-based DoS attacks, which can disrupt power balance and trigger cascading failures in ship operations. Badr et al. [
66] further address how such attacks on Distributed Control Systems (DCS) can propagate across ship power networks, leading to voltage instabilities, generator overloads, and loss of propulsion capabilities. These vulnerabilities are particularly concerning for modern naval architectures that rely on real-time control and automation. The main pathways include:
Disable Control Automation: Sending crafted Transport Control Protocol (TCP) packets can disrupt control loops in key systems like thrusters or the PMS. This halts normal operations, requiring a manual restart of affected systems [
56]. In addition, researchers have demonstrated in a simulated environment that in some cases it is possible to write directly to the memory of the automata and ignore user commands [
56].
Deploy Ransomware: Critical files in control systems can be encrypted using ransomware, effectively locking operators out of essential functionality.
Modify Configuration Files: Attackers may alter configuration files, preventing the crew from accessing real-time ship status and causing confusion or delays in response.
Disable External Communications: By targeting the ship’s external communications, attackers can prevent required documentation from being sent to the destination port, leading to delays or operational standstills.
Cause Blackout: A blackout immobilizes the ship entirely by disrupting power supply systems. This can be achieved through:
- ○
DoS to Power System Controller: Overloading the Advanced Load-Shedding (ALS) controller with network traffic, rendering it unresponsive. Vu et al. [
65] present how targeted DoS attacks on the ALS controller can delay or prevent critical load-shedding processes, increasing the risk of total blackout in ship power systems. Additionally, research on all-electric ships (AES) has shown that failures in Integrated Power Systems (IPS) caused by cyberattacks can severely impair onboard operations, as IPS controls both propulsion and auxiliary systems, making it a prime target for attackers [
67].
- ○
Modify Sensor Data: Using a man-in-the-middle (MitM) attack to alter traffic between the ALS controller and its sensors, causing the system to miscalculate load distribution. Techniques may include poisoning Address Resolution Protocol (ARP) tables, capturing and modifying packets, and purging ARP tables to evade detection.
Mechanical failure targets the physical components of the ship, exploiting their operational limits to cause breakdowns. Key methods include:
Alarm Suppression: The attacker would need to modify the sensor data in a way that would not indicate to the crew that the engine is overloaded.
Overload Engine: Commands can be sent to force the engine or generators to operate beyond safe thresholds, leading to damage and eventual failure.
The impact of immobilizing a ship is magnified in challenging conditions, such as stormy or remote waters. A stranded ship in these environments faces increased risks, including potential sinking, loss of human life, and significant economic consequences. Furthermore, the timing of the attack is crucial to maximizing its effect, with poorly timed attacks being easier to mitigate.
Denial-of-service attacks rely on exploiting vulnerabilities in the ship’s IT and OT systems, often requiring prior access to the network. Mechanical failures, on the other hand, require precise manipulation of sensor data to prevent the crew from detecting abnormalities before damage occurs.
While some ships have physical fail-safes or manual overrides for systems like ballast pumps and thrusters, these defenses can be circumvented if attackers gain control of critical components. The complexity of modern ship systems, combined with the difficulty of detecting subtle manipulations, increases the potential severity of these attack scenarios.
5. Validation
The validation of the attack scenarios was conducted through structured interviews with 10 maritime professionals. The experts included captains, engineers, cybersecurity specialists, and operational managers, offering a diverse range of perspectives. These interviews assessed the feasibility, plausibility, and operational impacts of the proposed attack scenarios, providing a practical lens through which to evaluate theoretical constructs.
5.1. Validation of Attack Scenarios
The interviews systematically evaluated the 20 attack scenarios across the four main goals: gaining a foothold, crashing the ship, capsizing the ship, and immobilizing the ship. The feedback provided valuable insights into the technical feasibility, operational complexities, and real-world challenges associated with each scenario.
5.1.1. Gaining a Foothold
Experts unanimously agreed on the plausibility of gaining initial access to a ship’s network via physical means. Social engineering tactics, such as impersonating a maintenance worker, were deemed highly feasible. Int3 and Int7 emphasized the variability in port security, noting that smaller or less-regulated ports present a higher risk. Another key concern was the frequent use of removable media provided by port authorities, which Int7 indicated as a potential attack vector. Interviewees also agreed that a malicious device, if properly concealed, could go undetected for extended periods, especially in areas not frequently inspected by the crew.
5.1.2. Crashing the Ship
Manipulating the ship’s thrusters or autopilot systems to crash into an object or run aground was identified as the most likely scenario within this goal. Int1 and Int7 emphasized narrow waterways, ports, and areas with restricted maneuverability as prime targets due to limited crew response time. Scenarios involving GPS spoofing and malicious ECDIS charts were considered less likely, as they would require advanced expertise and proximity to the ship. However, the interviewees stressed the high levels of trust placed in ECDIS systems, which could be exploited by attackers. Denial-of-service attacks on wheel commands were also considered viable tactics to prevent crew intervention.
5.1.3. Capsizing the Ship
Capsizing was viewed as the least feasible of the three attack goals. Experts such as Int9 and Int10 noted that modern ships are designed with extensive fail-safes, making such an attack highly improbable. However, certain scenarios, such as manipulating anti-rolling systems or shifting improperly secured cargo, were considered plausible under extreme conditions. Int9 suggested that exploiting the anti-fire system to flood upper decks could amplify instability, though this would require significant oversight or negligence from the crew. Weather conditions were frequently cited as a potential enabler, with stormy seas increasing the likelihood of success.
5.1.4. Immobilizing the Ship
Disabling a ship’s communication systems emerged as a practical and impactful strategy for immobilization. Int7 pointed out that failing to transmit mandatory port documentation could delay the vessel and incur financial penalties. Disabling ECDIS systems or deploying ransomware to critical automation systems were also considered effective tactics. However, the scenario of inducing mechanical failure was viewed with skepticism. Int8 indicated that while manipulating engines or thrusters could theoretically immobilize a ship, the loud noises and vibrations associated with mechanical stress would alert the crew well before critical damage occurred. Interviewees also noted that immobilizing a ship during severe weather could compound the consequences, increasing risks to crew safety and vessel integrity.
5.2. Practical Challenges and Vulnerabilities
The interviews revealed a range of challenges and vulnerabilities in maritime operations, many of which extend beyond specific attack scenarios. Key insights are provided in this subsection.
System-Specific Weaknesses: ECDIS and AIS were repeatedly identified as high-risk systems due to their reliance on external data sources. AIS, in particular, lacks encryption, making it susceptible to data manipulation. Interviewees noted that these systems are often trusted implicitly by the crew, creating opportunities for exploitation.
Human Factors: Human error emerged as a critical vulnerability. Int7 shared an incident where a minor navigation error resulted in a 60-nautical-mile deviation. Similarly, interviewees noted that crew fatigue, especially during late-night shifts (e.g., between 02:00 and 04:00), reduces alertness and increases the likelihood of mistakes. Int3 emphasized that over-reliance on sensor and interface data further exacerbates this issue, as discrepancies may go unnoticed until it is too late.
Operational Contexts: The feasibility of attacks varies significantly depending on the ship’s operational environment. Narrow waterways, ports, and high-traffic areas were identified as high-risk zones due to limited maneuverability and reduced reaction times. Adverse weather conditions were also cited as a major complicating factor, both for attackers (e.g., reduced precision) and for the crew’s ability to respond effectively.
Ship-Type Variability: Interviewees indicated variances in cybersecurity measures between passenger and cargo ships. Passenger vessels tend to have more robust redundancy systems and better-maintained networks. Cargo ships, on the other hand, are often older and less secure, making them more vulnerable to attacks.
Network Segmentation and Security: Several interviewees, including Int5 and Int6, pointed out that network segmentation on ships is often inadequate. While VLANs and firewalls are commonly used, misconfigurations and human error undermine their effectiveness. Int5 also noted the absence of network access control in many ships, allowing unauthorized devices to communicate freely once connected.
Physical Security: Physical access to critical systems remains a significant concern. As Int7 and Int9 noted, many ports and ships lack strict access controls, making it relatively easy for attackers to gain physical proximity to critical systems. This is particularly true for smaller vessels and cargo ships, where budgets for security measures are often limited.
Motivational Challenges: Int2 raised an important point regarding the motivation of attackers. He argued that the resource-intensive nature of maritime cyberattacks, coupled with limited financial incentives, reduces their likelihood. Most attackers would find higher risk-to-reward ratios in other industries. However, he acknowledged that nation-state actors or ideologically motivated groups might still consider such attacks.
5.3. Summary of the Attack Scenarios
The structured validation of attack scenarios provided insight into their feasibility, attack paths, and potential consequences. Expert assessments highlighted the most and least plausible cyberattack strategies based on real-world operational constraints.
Table 3 summarizes the validated attack scenarios, reflecting expert evaluations of their feasibility and expected impact on maritime operations.
5.4. Limitations and Implications
The feedback from the interviews emphasize both the strengths and limitations of the proposed attack scenarios. While many were validated as plausible, their execution often relies on specific conditions, such as favorable weather or human error. Moreover, the interviews emphasized the critical role of human factors, operational contexts, and system-specific vulnerabilities in determining the success or failure of an attack.
The findings emphasize the importance of a layered approach to maritime cybersecurity. Technical defenses, such as improved network segmentation and encrypted communications, must be complemented by robust crew training and strict adherence to security protocols. The insights gained from these interviews also point to areas for future research, including the role of emerging technologies and the impact of regulatory frameworks on maritime cybersecurity.
6. Conclusions
This study identifies critical vulnerabilities and cyberattack scenarios in maritime operations, identifying 20 attack paths categorized under crashing, capsizing, and immobilizing a ship. By integrating an extensive literature review and expert interviews, it bridges theoretical knowledge with real-world operational insights. Among the identified attack types, crashing and immobilizing scenarios were deemed highly plausible, particularly in constrained environments like ports and narrow waterways. Capsizing, while theoretically possible under extreme conditions, was assessed as the least feasible attack due to modern ship designs and existing safety measures.
The key contribution of this research is the development of structured attack trees as a systematic approach for modeling cyber threats against ship systems. Unlike prior studies that primarily document past incidents or individual vulnerabilities, this study constructs attack scenarios using hierarchical models that capture complex attack paths. The attack trees not only help assess vulnerabilities and potential impacts but also serve as a structured tool for maritime cybersecurity risk assessments. By incorporating expert validation, the study ensures that its scenarios are grounded in operational realities, making the findings directly applicable to industry risk management and cybersecurity planning. The study also features the interplay between technological vulnerabilities and human factors, advocating for closer collaboration between IT professionals, operational staff, and maritime engineers.
These findings have significant implications for the maritime industry, emphasizing the urgent need for enhanced cybersecurity measures in navigation systems, operational technologies, and human decision-making processes. The increasing reliance on systems such as ECDIS and autopilot presents significant risks if compromised. Additionally, human factors, such as errors, oversights, and inadequate security awareness, can amplify cyberattack success. Strengthening network segmentation, enforcing strict removable media controls, and improving crew training are key measures to mitigate risks.
This research is conducted within the domain of maritime cybersecurity, aiming to enhance defensive capabilities rather than promote offensive operations. While it identifies vulnerabilities in ship systems, its primary objective is to improve cyber resilience and inform risk mitigation strategies. The study aligns with ethical cybersecurity research practices and complies with relevant national and international maritime cybersecurity standards and best practices.
The dual-use potential of cybersecurity research is acknowledged, and all necessary precautions have been taken to prevent misuse. The findings are intended solely for defensive applications, contributing to improved cybersecurity standards, regulatory compliance, and industry-wide awareness of cyber risks. This study adheres to relevant national and international laws governing cybersecurity research and aligns with ethical guidelines on responsible cybersecurity threat modeling. The authors emphasize that all methodologies and findings presented should only be used for ethical and lawful purposes to safeguard critical maritime infrastructure.
Despite its contributions, this research has limitations. The attack scenarios require adaptation to specific ship configurations and do not account for autonomous ships, which represent an emerging cybersecurity challenge. Additionally, the study does not quantify attack probabilities or impacts, leaving this aspect for future research. The homogeneous pool of expert interviewees may also limit the generalizability of some findings.
Future research should address these limitations by incorporating diverse perspectives from ship designers, engineers, and crews operating various vessel types, such as cruise liners or tankers. Autonomous ships, AI-driven navigation, and blockchain-based cargo management present new attack surfaces that warrant deeper investigation. Additionally, as cybersecurity frameworks evolve, future work could explore how attack trees can be integrated into these frameworks to enhance risk assessment methodologies and incident response planning. Scoring-based quantitative modeling and simulations would enhance the ability to assess the likelihood and consequences of attacks, translating findings into actionable cybersecurity strategies. As cyber threats evolve, the maritime sector must continuously adapt, integrating advanced security frameworks to protect critical operations from both traditional and emerging cyber risks.