Nonlinear-Finite-Time-Extended-State-Observer-Based Command Filtered Control for Unmanned Surface Vessels with Rotatable Thrusters Under False Data Injection Attacks
Abstract
1. Introduction
- (1)
- A novel scheme is proposed for USVs equipped with rotatable thrusters that are affected by FDIAs in a network environment. Compared with the methods in [4,5,6,7], the scheme improves the information interaction processes in the kinematic and dynamic loops by introducing command filtering to obtain the derivative of the generated virtual control quantity using a backstepping design. This method improves the system’s dynamic response in complex network environments and can effectively address the potential threat of FDIAs.
- (2)
- A novel nonlinear finite-time extended state observer (NFTESO) is designed. In contrast to the methods in [9,12,13], the NFTESO effectively blocks cyberattacks on the kinematic loop by reconstructing pose information. Moreover, the system extends the methods of [15,17] by using an NFTESO to reconstruct various uncertain dynamics, including for FDIAs, to ensure concise controller expression and effectively suppress complex uncertain dynamics.
- (3)
- The proposed control scheme is concise and integrates event triggering mechanisms with high-frequency gain at the control end. Compared with the methods in [8,19,20], the approach achieves lower communication bandwidth occupancy and can better suppress interference due to cyberattacks on the vessel control system. This is achieved by periodically adjusting the transmission of control signals, thus optimizing control performance, while maintaining a concise controller structure.
2. System Modeling and Problem Analysis
2.1. Problem Formulation
2.2. Preliminaries
2.3. Thruster Dynamics
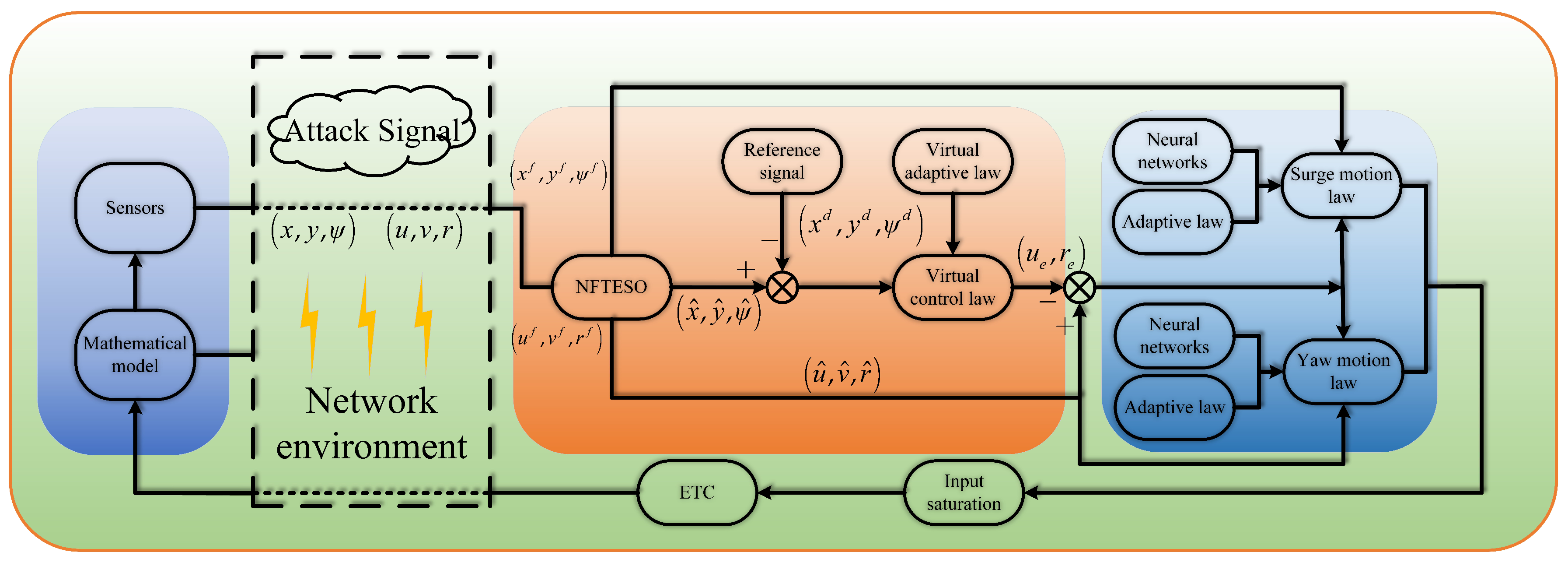
3. Trajectory-Tracking Controller Implementation
3.1. Design of NFTESO
3.2. Design of Tracking Control Law and Stability Analysis
- (1)
- The actual trajectory of the vessel can follow the reference trajectory , and the trajectory tracking errors and converge to a compact set , within finite time.
- (2)
- All signals in the closed-loop tracking system remain bounded.
- (3)
- Under the event triggering mechanisms (34) and (35), Zeno behavior can be avoided.
- (1)
- From (43), we obtain the following:If , thenAccording to Lemma 1, can stabilize within the residual set within finite time and with a settling time ofwhere is the initial value of .From (36), we can deduce that ; that is,
- (2)
- From (44), we obtain , which indicates that is bounded. Next, (36) indicates that , , , , , , , , , , , and are all bounded. According to assumptions 3 and 5, we can conclude that x, , y, , and are bounded. Because , , and are bounded, is bounded. According to assumption 5 and the boundedness of and , we can conclude that and are bounded. Then, the boundedness of and can be derived from the boundedness of , , , and . Furthermore, because , , and are bounded, it follows that and are bounded. According to assumption 4 and the boundedness of and , we conclude that u, v and r are bounded and further deduce that is bounded. The boundedness of can then be derived from the boundedness of and . Considering the properties of and and the boundedness of , and , we can conclude that and are bounded. According to Assumption 2 and the boundedness of and , the terms and are bounded. Furthermore, the control laws and must be bounded. It follows that every signal in the closed-loop tracking system is bounded.
- (3)
- According to the event triggering mechanisms (34) and (35), and are constant values within the time interval . Differentiating the measurement error yields the following:
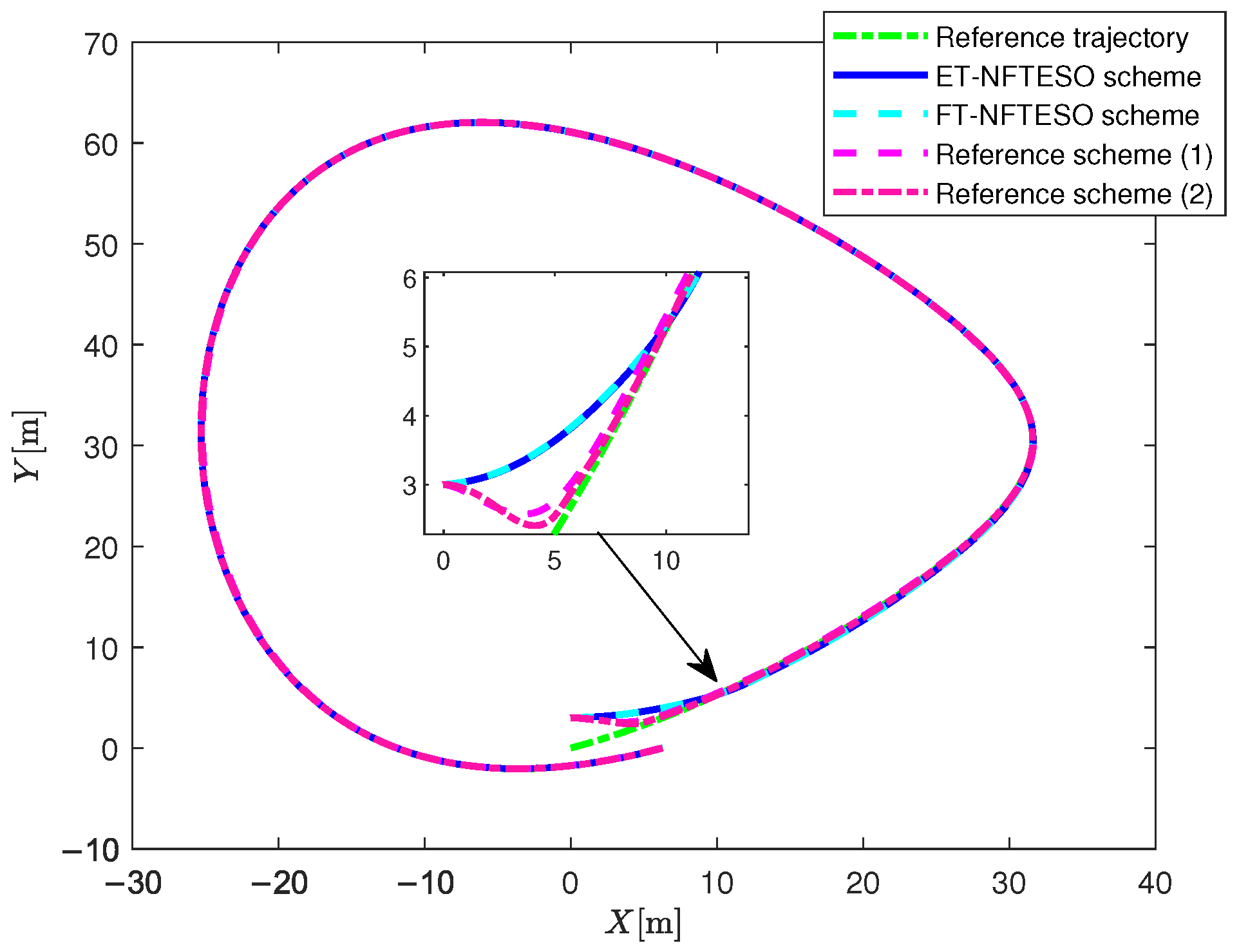
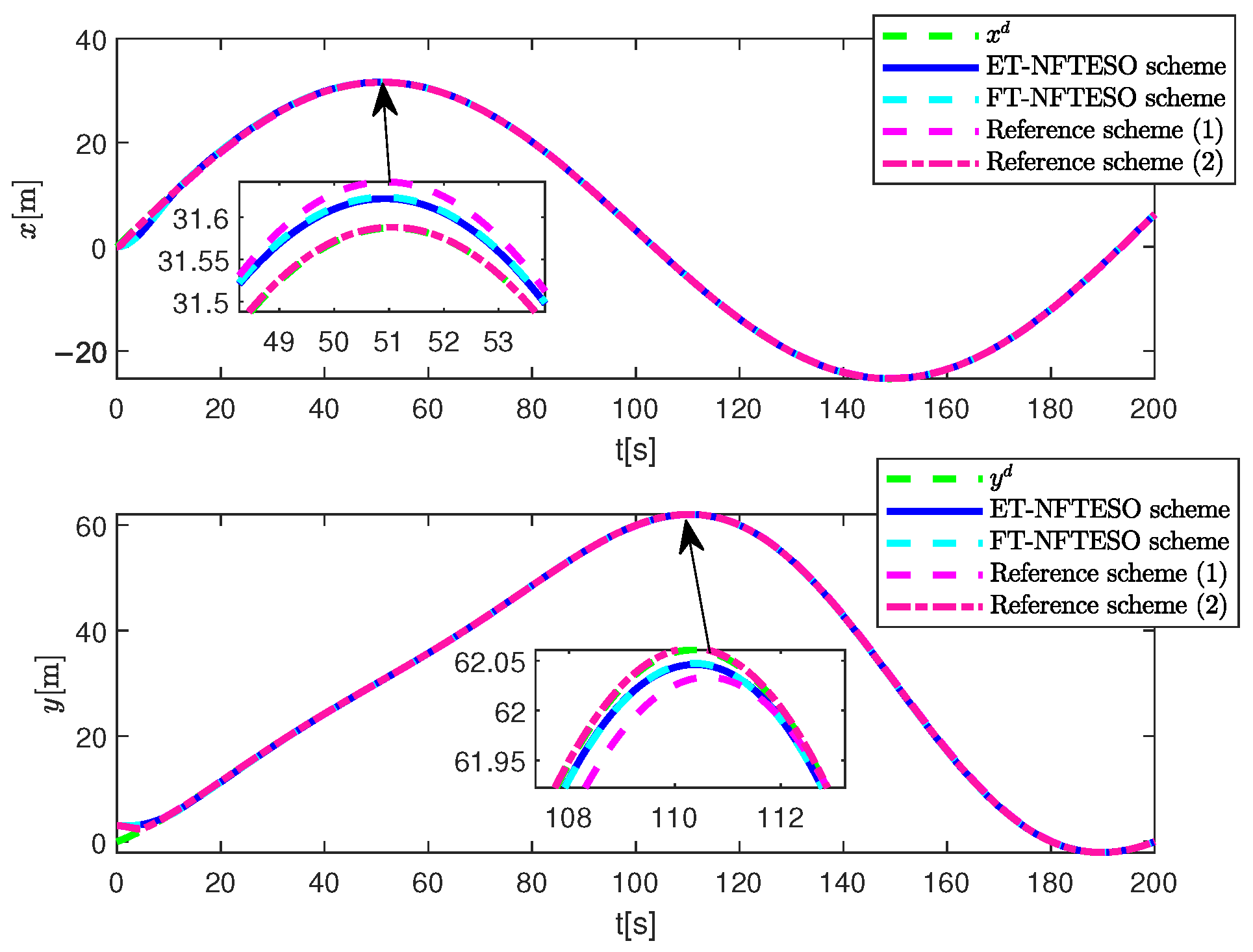
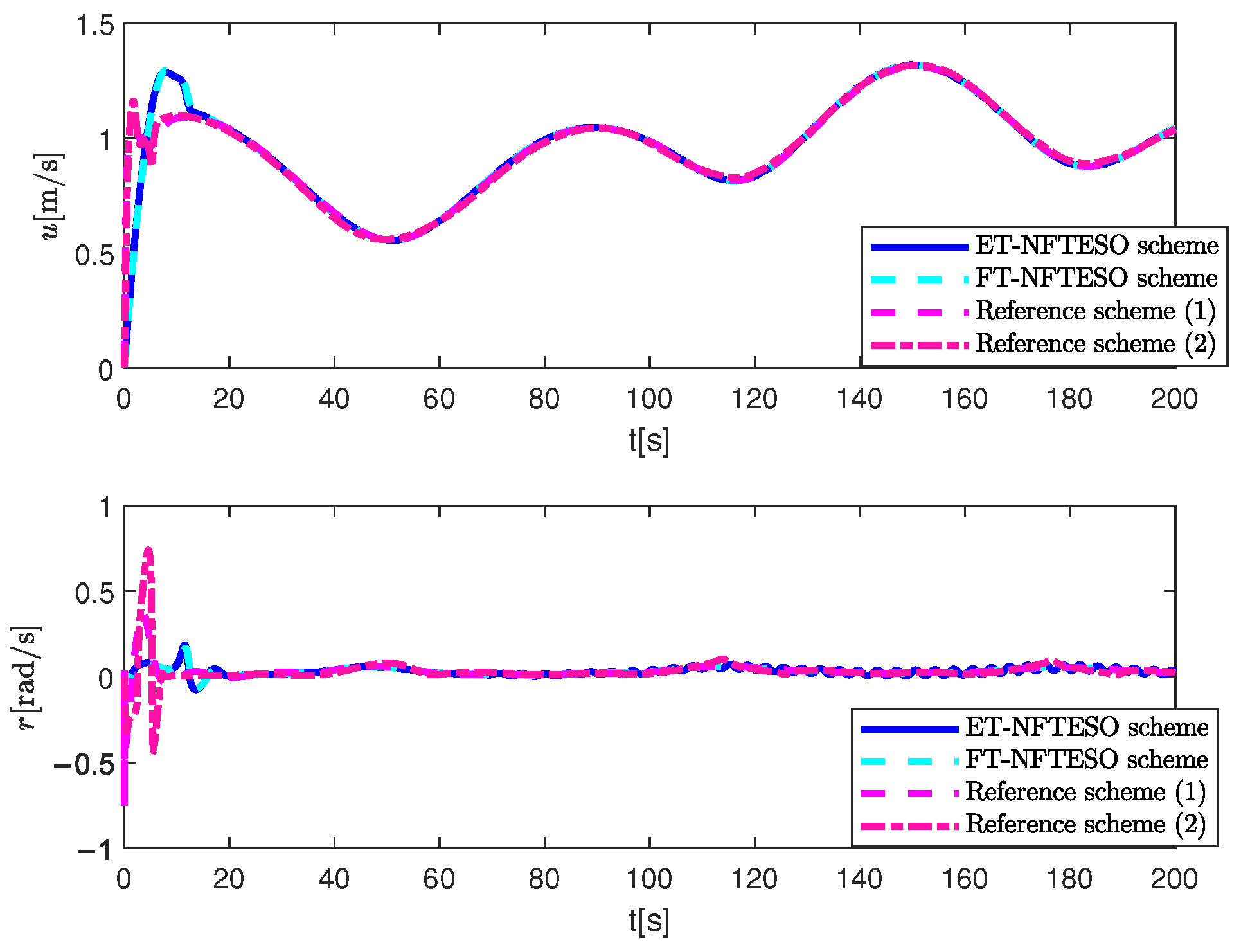
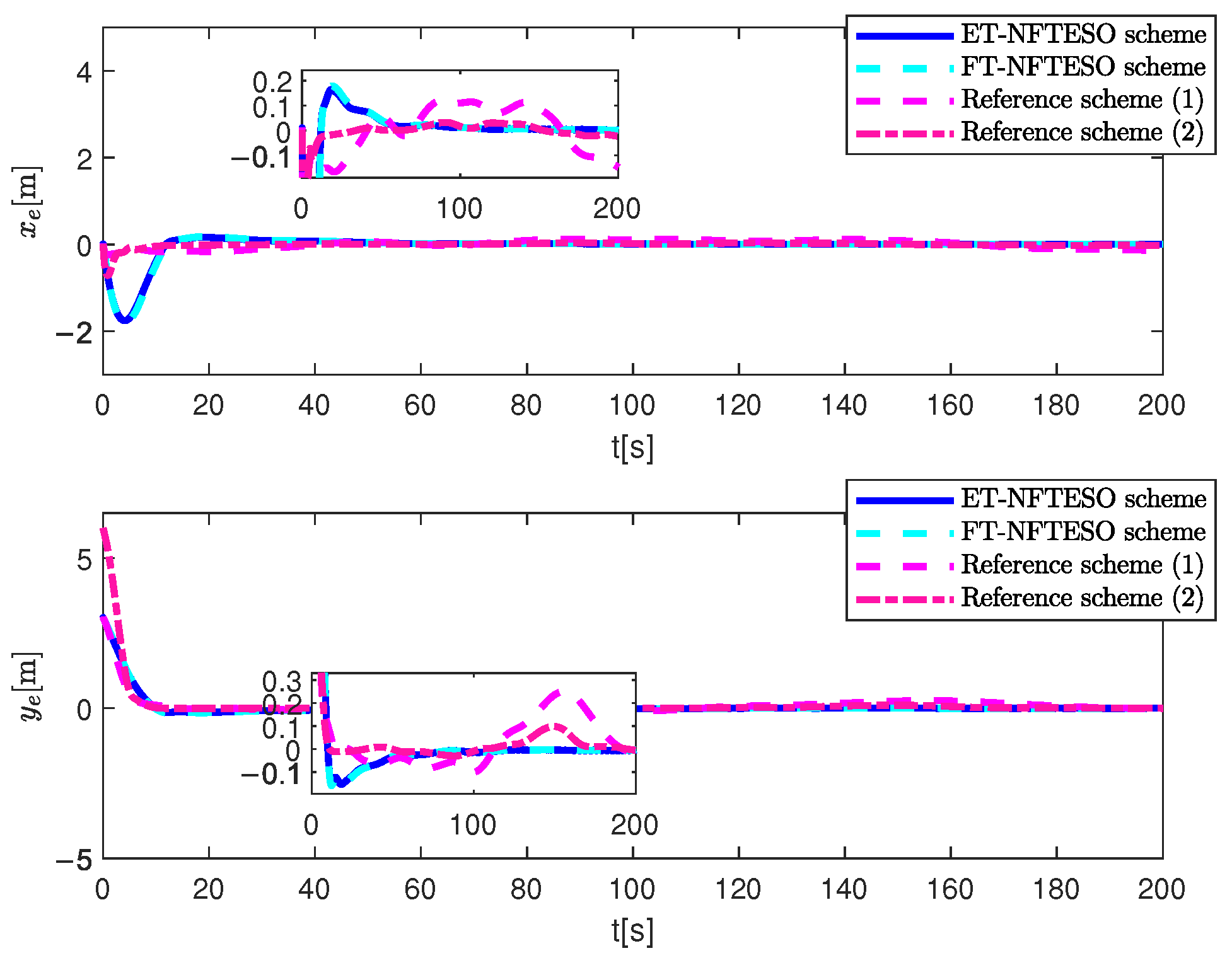
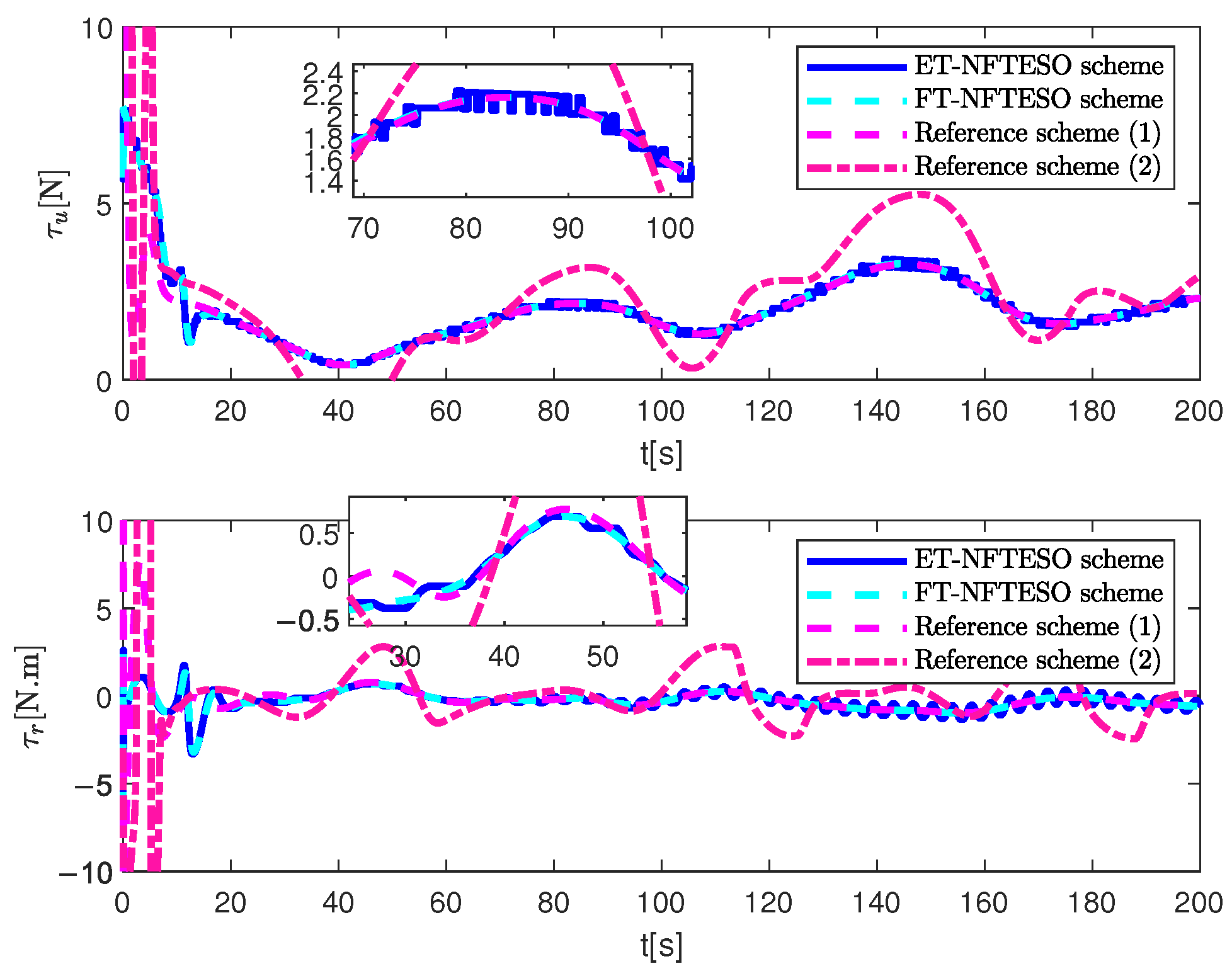
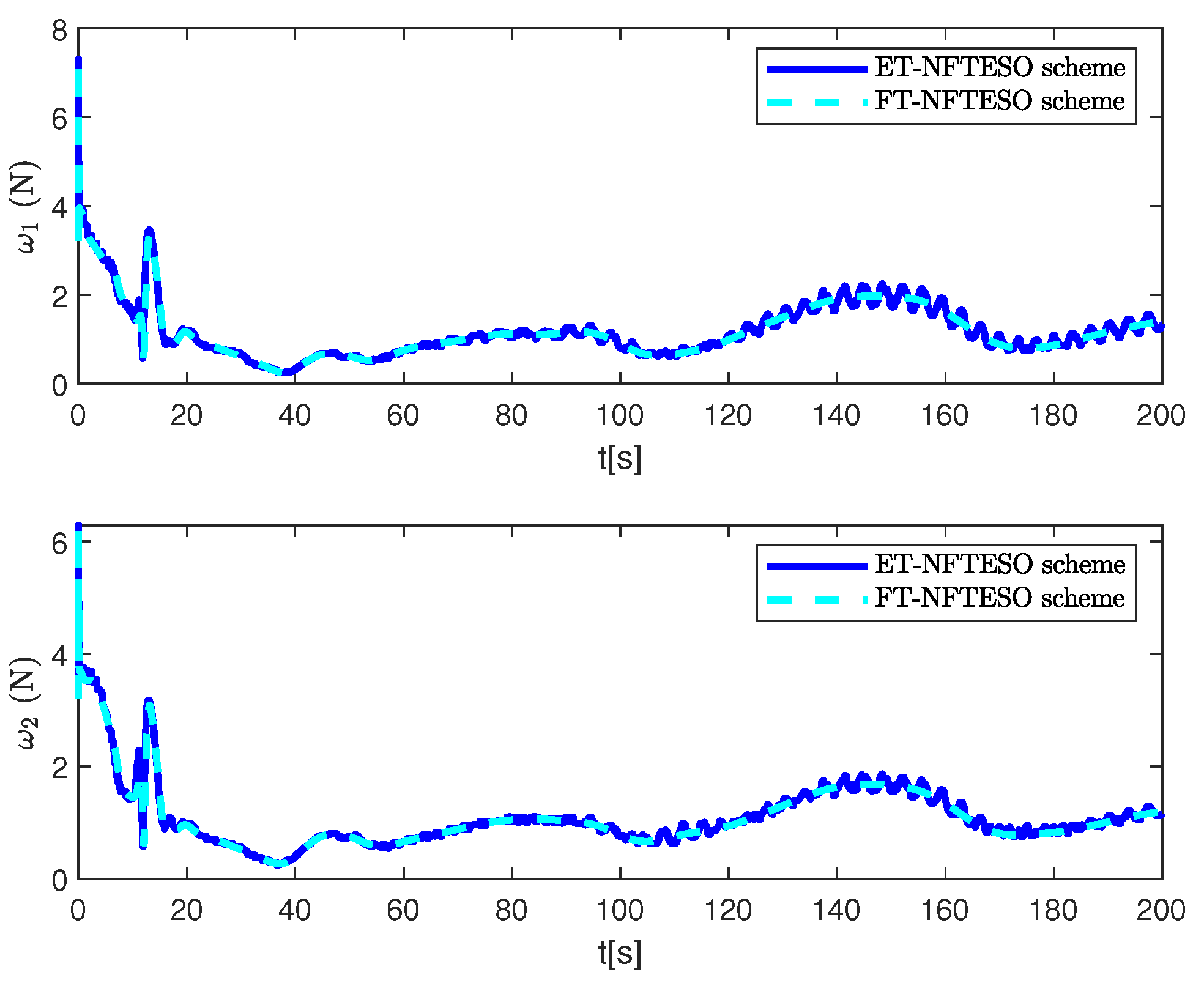
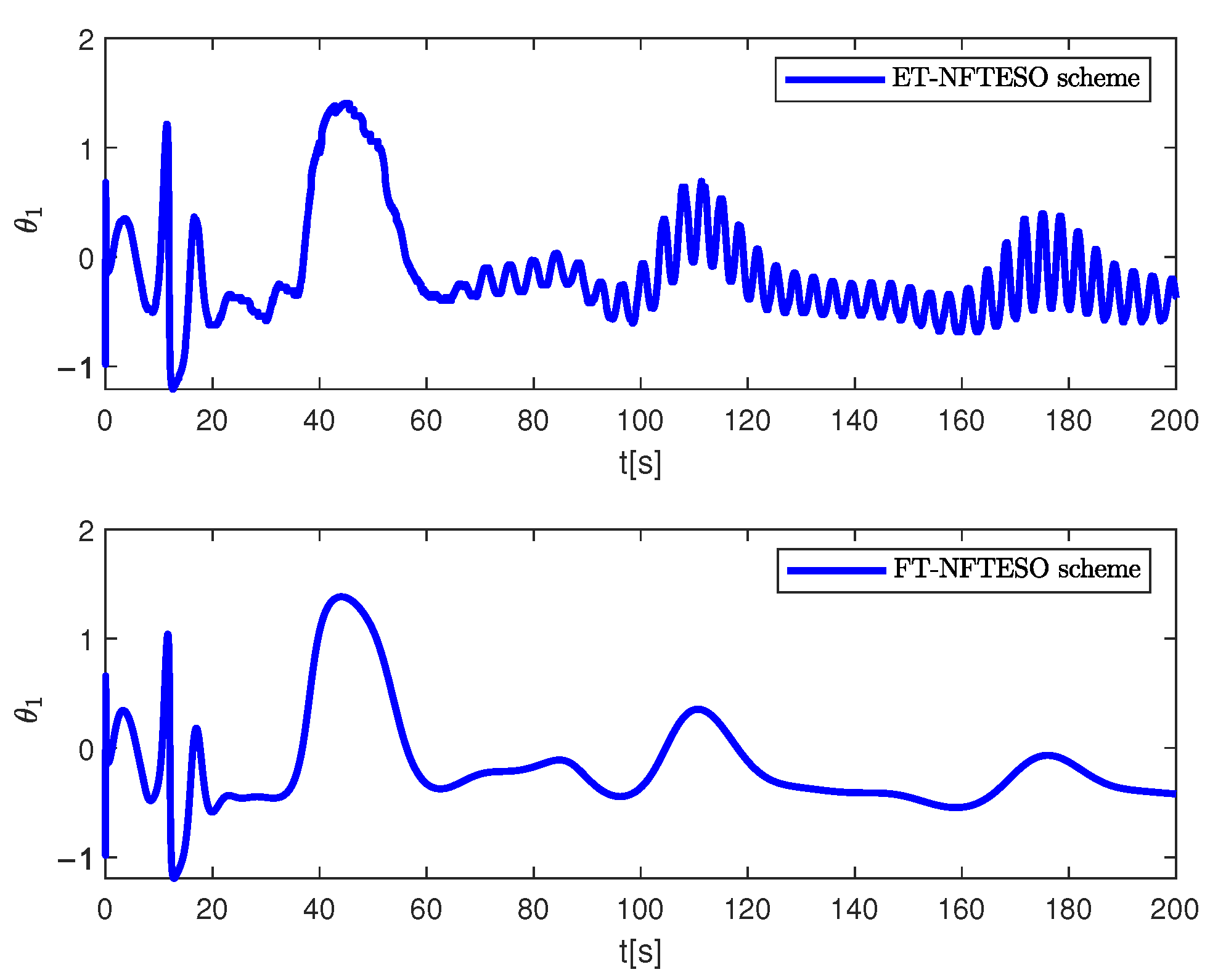
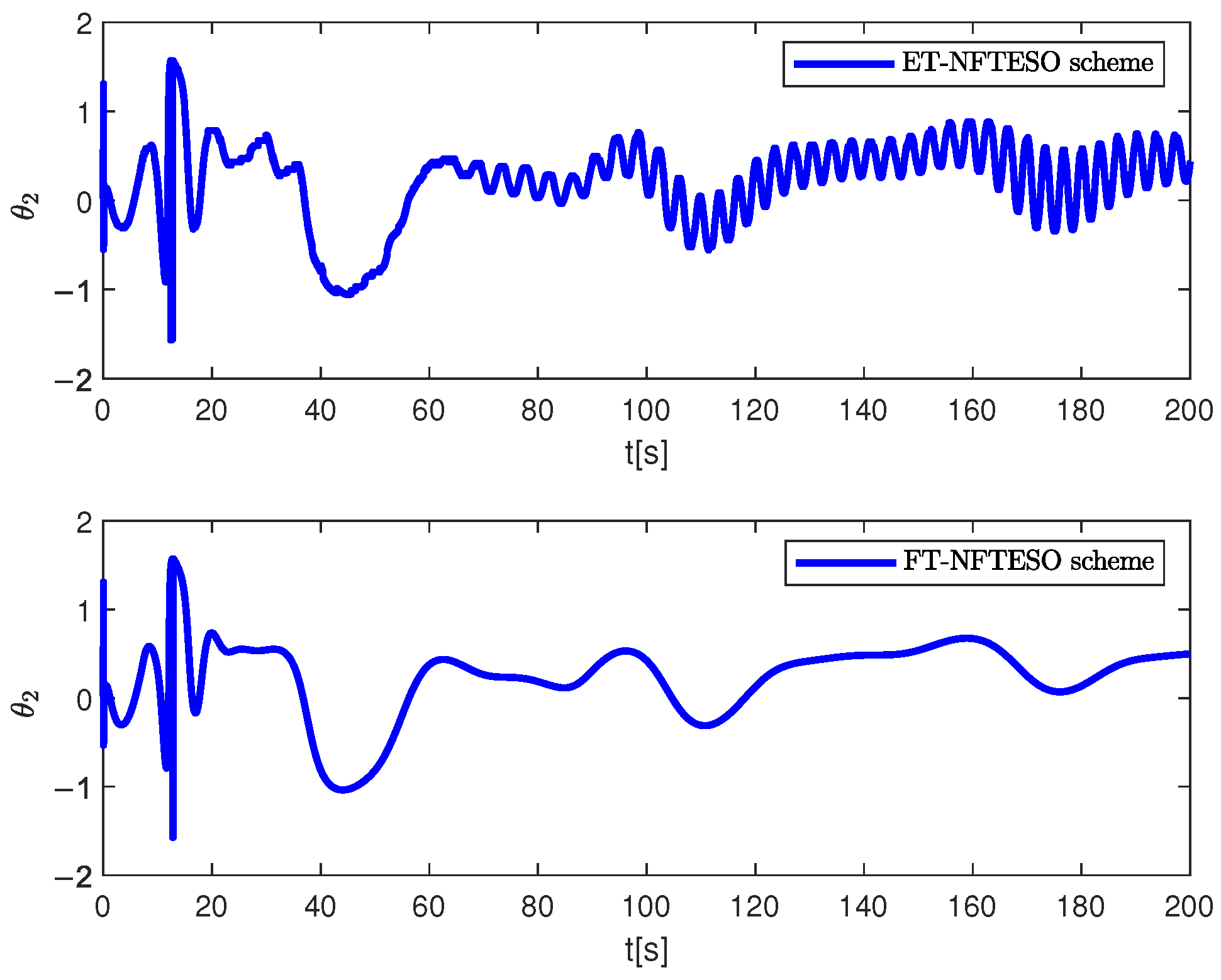
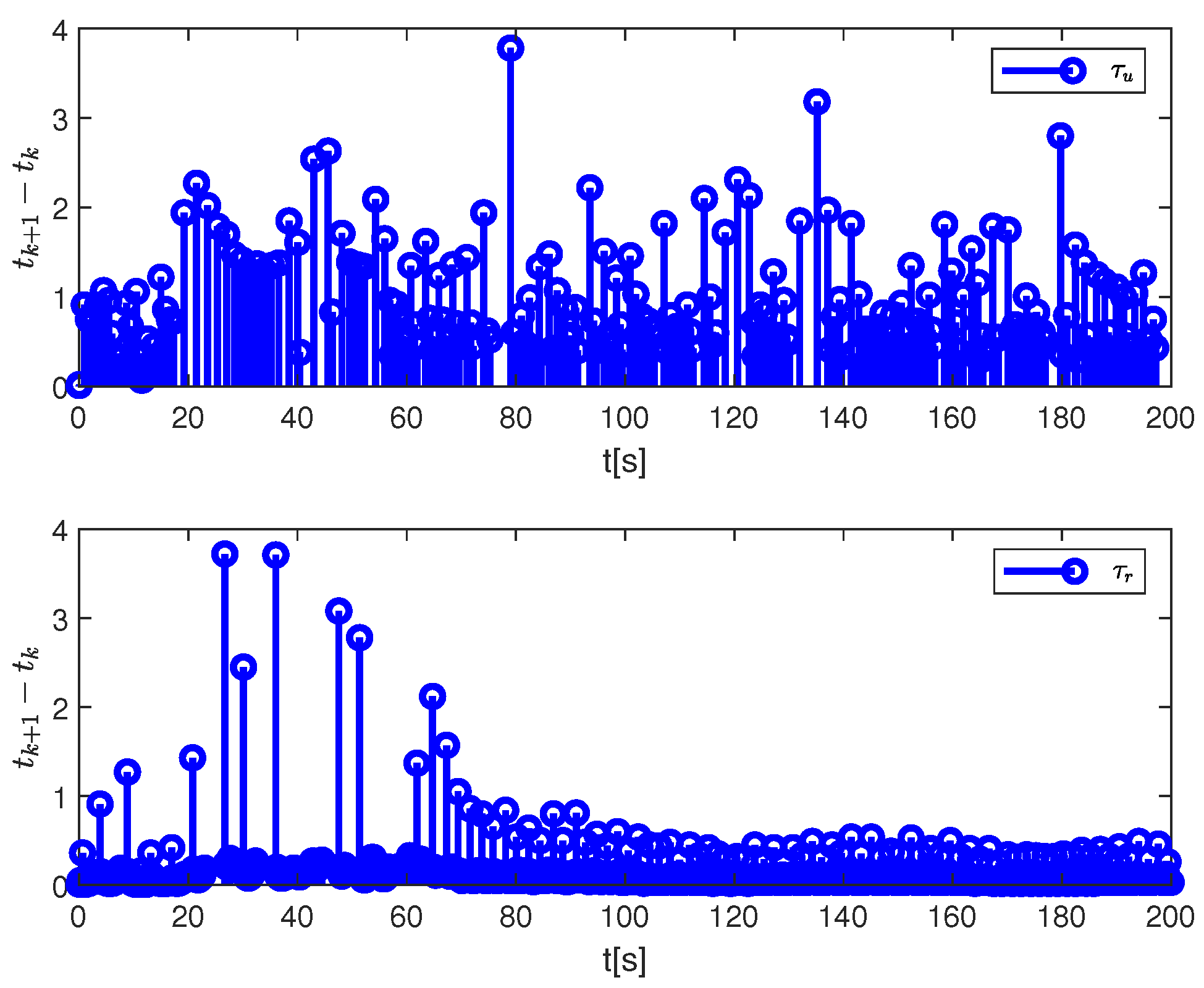
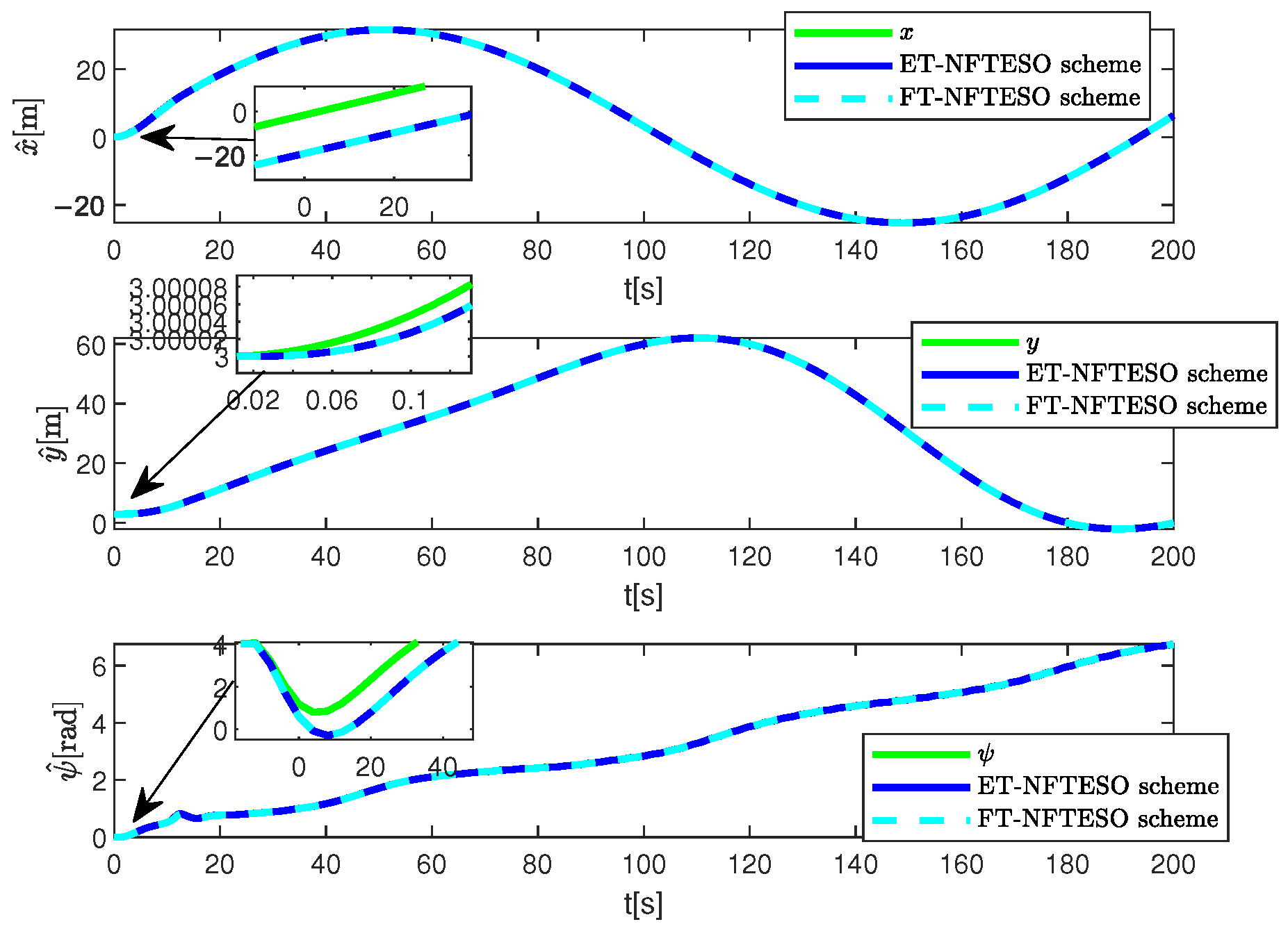
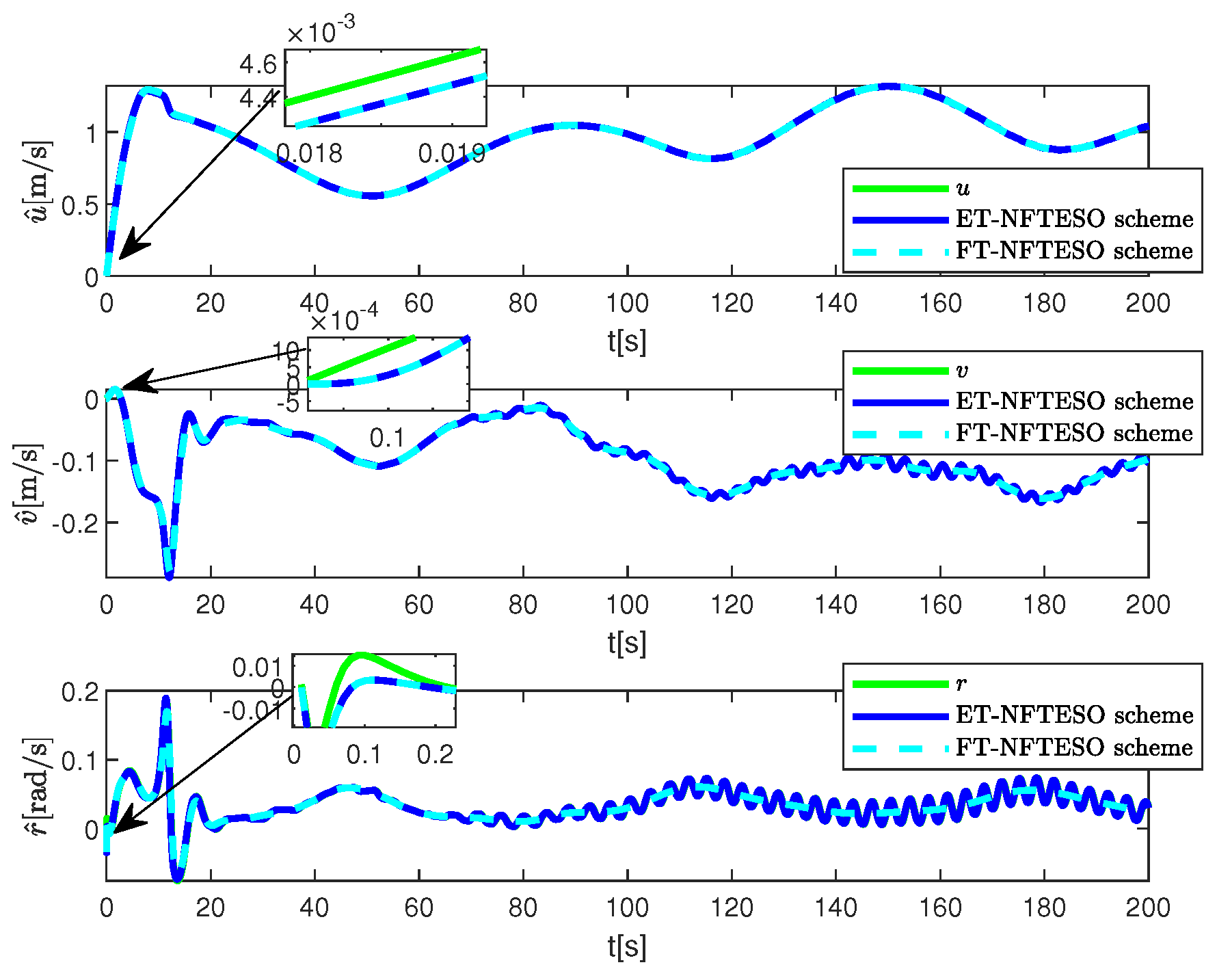
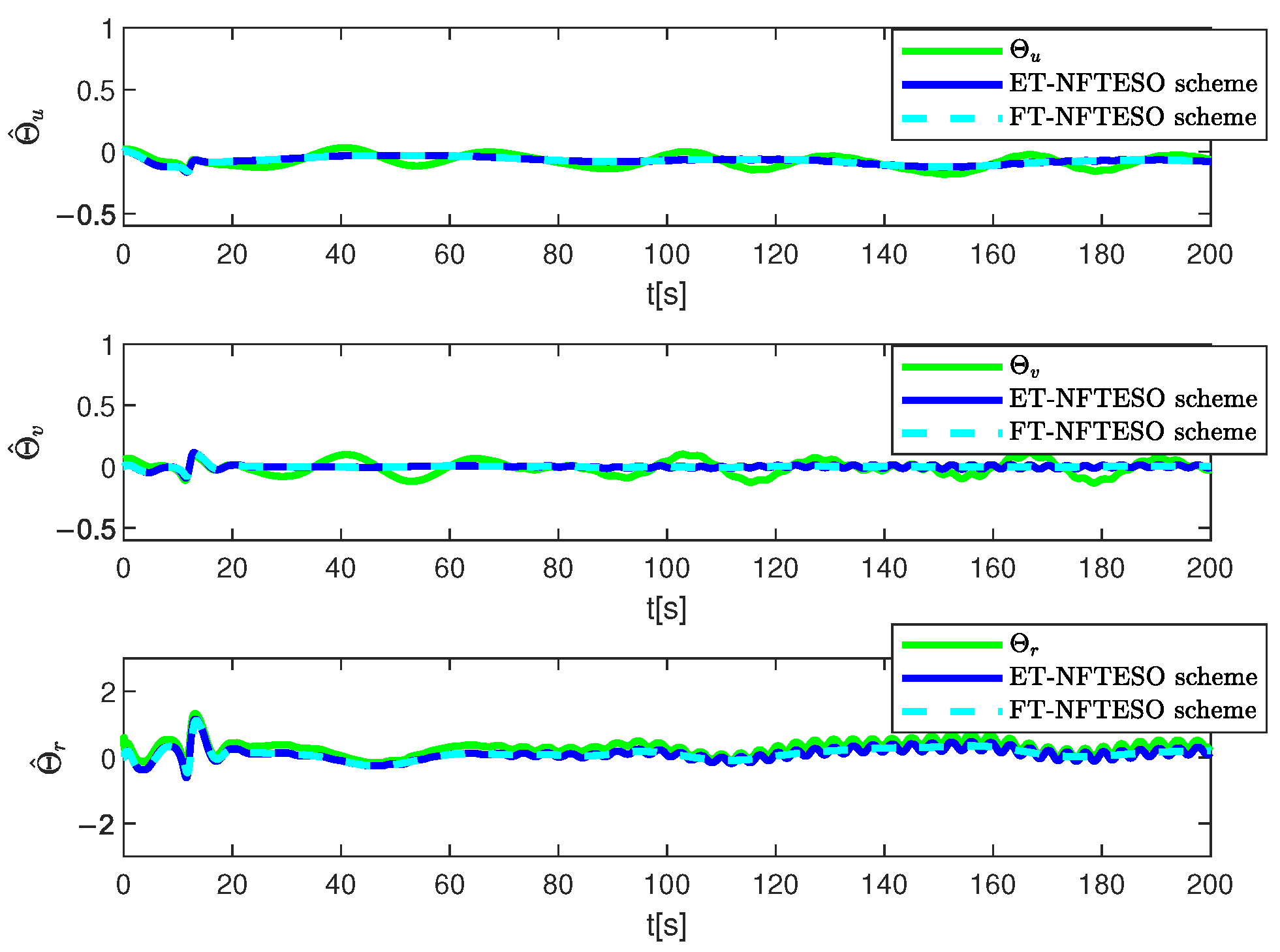
4. Simulation Results and Discussion
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Wu, C.; Zhu, G.B.; Lu, J.S. Indirect adaptive neural tracking control of USVs under injection and deception attacks. Ocean. Eng. 2023, 270, 113641. [Google Scholar] [CrossRef]
- Karimi, M.H.R.; Lu, Y.Y. Guidance and control methodologies for marine vehicles: A survey. Control Eng. Pract. 2021, 111, 104785. [Google Scholar] [CrossRef]
- Wang, N.; Zhang, Y.H.; Ahn, C.K.; Xu, Q.Y. Autonomous Pilot of Unmanned Surface Vehicles: Bridging Path Planning and Tracking. IEEE Trans. Veh. Technol. 2022, 71, 2358–2374. [Google Scholar] [CrossRef]
- Lu, Y.; Su, R.; Zhang, C.X.; Qiao, L. Event-Triggered Adaptive Formation Keeping and Interception Scheme for Autonomous Surface Vehicles Under Malicious Attacks. IEEE Trans. Ind. Inform. 2022, 18, 3947–3957. [Google Scholar] [CrossRef]
- Jiang, C.Y.; Zhang, G.Q.; Huang, C.F.; Zhang, W.J. Memory-based event-triggered path-following control for a USV in the presence of DoS attack. Ocean. Eng. 2024, 310, 118627. [Google Scholar] [CrossRef]
- Xie, X.H.; Hu, S.L.; Liu, Y.G.; Li, Q.X. Resilient Adaptive Event-Triggered H8 Fuzzy Filtering for Cyber-Physical Systems Under Stochastic-Sampling and Denial-of-Service Attacks. IEEE Trans. Fuzzy Syst. 2023, 31, 278–292. [Google Scholar] [CrossRef]
- Luo, P.; Wu, D.F.; Yamashita, A.S.; Feng, N.; Yang, Y. Observer-based fixed-time dynamic surface tracking control for autonomous surface vehicles under actuator constraints and denial-of-service attacks. Appl. Math. Comput. 2024, 465, 128403. [Google Scholar] [CrossRef]
- Du, X.; Wu, F.Y.; Lian, J. Secure Control of Networked Control Systems Under Replay Attacks: A Switching-Like Approach. Int. J. Robust Nonlinear Control 2025, 35, 3317–3328. [Google Scholar] [CrossRef]
- Huang, J.S.; Zhao, L.; Wang, Q.G. Adaptive control of a class of strict feedback nonlinear systems under replay attacks. ISA Trans. 2020, 107, 134–142. [Google Scholar] [CrossRef]
- Meng, X.F.; Zhang, G.C.; Han, B.; Zhang, B. Fault-tolerant control of underactuated unmanned surface vessels in presence of deception and injection attacks. Trans. Inst. Meas. Control 2024, 47, 1672–1685. [Google Scholar] [CrossRef]
- Chen, L.P.; Sun, M.H.; Wang, L. Practical Finite-Time Event-Triggered Control of Underactuated Surface Vessels in Presence of False Data Injection Attacks. Pol. Marit. Res. 2024, 31, 114–126. [Google Scholar] [CrossRef]
- Xu, Z.Y.; Zhu, G.B.; Xu, Y.; Ding, L. Periodic event-triggered adaptive neural control of USVs under replay attacks. Ocean. Eng. 2024, 306, 118022. [Google Scholar] [CrossRef]
- Meng, X.; Zhang, G.; Han, B. Nonlinear decoration-driven adaptive neural finite-time control for USVs with two rotatable thrusters under false data injection attacks and input saturation. ISA Trans. 2025, 158, 97–109. [Google Scholar] [CrossRef]
- Liu, Z.P.; Gong, Q.T.; Hu, X. Dynamic event-triggered adaptive neural prescribed performance control for dynamic positioning of vessels under input time-delay. Ocean. Eng. 2025, 322, 120503. [Google Scholar] [CrossRef]
- Zhang, L.; Zhang, S.Z.; Du, Z.; Li, H.; Gan, L.X.; Li, X.B. Adaptive trajectory tracking of the unmanned surface vessel based on improved AC-MPC method. Ocean. Eng. 2025, 322, 120455. [Google Scholar] [CrossRef]
- Dong, S.; Shen, Z.P.; Zhou, L.; Yu, H.M.; Zhu, G.B. Nonlinear feedback-based event-triggered output-feedback control for marine surface vehicles under deferred output constraints. Appl. Math. Comput. 2023, 454, 128084. [Google Scholar] [CrossRef]
- Ma, Y.; Zhu, G.B.; Li, Z.X. Error-Driven-Based Nonlinear Feedback Recursive Design for Adaptive NN Trajectory Tracking Control of Surface Ships with Input Saturation. IEEE Intell. Transp. Syst. Mag. 2019, 11, 17–28. [Google Scholar] [CrossRef]
- Dang, Y.K.; Huang, Y.; Shen, X.Y.; Zhu, D.Q.; Chu, Z.Z. Incremental Sparse Gaussian Process-Based Model Predictive Control for Trajectory Tracking of Unmanned Underwater Vehicles. IEEE Robot. Autom. Lett. 2025, 10, 2327–2334. [Google Scholar] [CrossRef]
- Tang, Y.J.; Chen, L.Y.; Mou, J.M.; Chen, P.F.; Huang, Y.M.; Zhou, Y. Robust Model Predictive Control for Ship Collision Avoidance Under Multiple Uncertainties. IEEE Trans. Transp. Electrif. 2024, 10, 10374–10387. [Google Scholar] [CrossRef]
- Yao, Q.J.; Li, Q.; Jahanshahi, H. Fixed-time adaptive neural control for output-constrained trajectory tracking of unknown marine surface vehicle. Int. J. Control 2025, 1–13. [Google Scholar] [CrossRef]
- Zhu, G.B.; Ma, Y.; Hu, S.L. Event-Triggered Adaptive PID Fault-Tolerant Control of Underactuated ASVs Under Saturation Constraint. IEEE Trans. Syst. Man-Cybern.-Syst. 2023, 53, 4922–4933. [Google Scholar] [CrossRef]
- Zhang, Q.; Ding, Z.Y.; Zhang, M.J. Adaptive Self-Regulation PID Control of Course-Keeping for Ships. Pol. Marit. Res. 2020, 27, 39–45. [Google Scholar] [CrossRef]
- Meng, X.F.; Zhang, G.C.; Han, B.; Liu, X.M. Multiport event-triggered finite-time PID control for underactuated unmanned surface vessels under cyber attacks. Proc. Inst. Mech. Eng. Part I-J. Syst. Control Eng. 2024, 2024, 09596518241273856. [Google Scholar] [CrossRef]
- Deng, Y.J.; Zhang, X.K.; Im, N.; Zhang, G.Q.; Zhang, Q. Model-Based Event-Triggered Tracking Control of Underactuated Surface Vessels With Minimum Learning Parameters. IEEE Trans. Neural Netw. Learn. Syst. 2020, 31, 4001–4014. [Google Scholar] [CrossRef] [PubMed]
- Zhang, Q.; Zhu, G.B.; Hu, X.; Yang, R.M. Adaptive neural network auto-berthing control of marine ships. Ocean. Eng. 2019, 177, 40–48. [Google Scholar] [CrossRef]
- Zhang, K.; Huang, L.W.; He, Y.X.; Wang, B.; Chen, J.H.; Tian, Y.F.; Zhao, X.Y. A real-time multi-ship collision avoidance decision-making system for autonomous ships considering ship motion uncertainty. Ocean. Eng. 2023, 278, 114205. [Google Scholar] [CrossRef]
- Han, X.; Zhang, X.K. Tracking control of ship at sea based on MPC with virtual ship bunch under Frenet frame. Ocean. Eng. 2022, 247, 110737. [Google Scholar] [CrossRef]
- Yu, S.L.; Lu, J.S.; Zhu, G.B.; Yang, S.J. Event-triggered finite-time tracking control of underactuated MSVs based on neural network disturbance observer. Ocean. Eng. 2022, 253, 111169. [Google Scholar] [CrossRef]
- Meng, X.F.; Zhang, G.C.; Han, B. Fault-tolerant control of underactuated MSVs based on neural finite-time disturbance observer: An Event-triggered Mechanism. J. Frankl.-Inst.-Eng. Appl. Math. 2024, 361, 106603. [Google Scholar] [CrossRef]
- Fossen, T.I. Handbook of Marine Craft Hydrodynamics and Motion Control; Wiley: New York, NY, USA, 2011. [Google Scholar]
- Wen, C.Y.; Zhou, J.; Liu, Z.T.; Su, H.Y. Robust Adaptive Control of Uncertain Nonlinear Systems in the Presence of Input Saturation and External Disturbance. IEEE Trans. Autom. Control 2011, 56, 1672–1678. [Google Scholar] [CrossRef]
- Wang, F.; Chen, B.; Liu, X.P.; Lin, C. Finite-Time Adaptive Fuzzy Tracking Control Design for Nonlinear Systems. IEEE Trans. Fuzzy Syst. 2018, 26, 1207–1216. [Google Scholar] [CrossRef]
- Yu, S.H.; Yu, X.H.; Shirinzadeh, B.; Man, Z.H. Continuous finite-time control for robotic manipulators with terminal sliding mode. Automatica 2005, 41, 1957–1964. [Google Scholar] [CrossRef]
- Kurdila, A.J.; Narcowich, F.J.; Ward, J.D. Persistency of excitation in identification using radial basis function approximants. SIAM J. Control Optim. 1995, 33, 625–642. [Google Scholar] [CrossRef]
- Wang, C.L.; Lin, Y. Decentralized adaptive tracking control for a class of interconnected nonlinear time-varying systems. Automatica 2015, 54, 16–24. [Google Scholar] [CrossRef]
- Polycarpou, M.M.; Weaver, S.E. Stable adaptive neural control of nonlinear systems. In Proceedings of the 1995 American Control Conference—ACC’95, Seattle, WA, USA, 21–23 June 1995; Volume 1, pp. 847–851. [Google Scholar]
- Reyhanoglu, M. Exponential stabilization of an underactuated autonomous surface vessel. Automatica 1997, 33, 2249–2254. [Google Scholar] [CrossRef]
- Kadiyam, J.; Parashar, A.; Mohan, S.; Deshmukh, D. Actuator fault-tolerant control study of an underwater robot with four rotatable thrusters. Ocean Eng. 2020, 197, 106929. [Google Scholar] [CrossRef]
- Park, B.S.; Kwon, J.W.; Kim, H. Neural network-based output feedback control for reference tracking of underactuated surface vessels. Automatica 2017, 77, 353–359. [Google Scholar] [CrossRef]
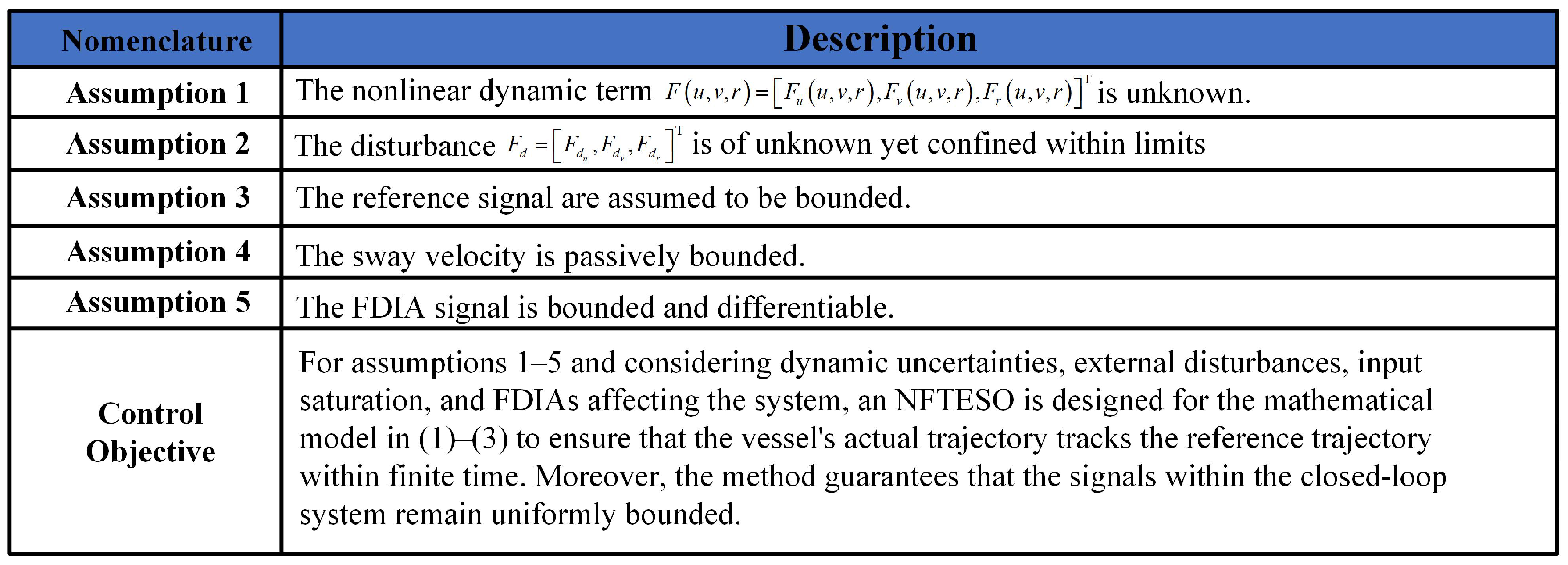
| Nomenclature | Description |
|---|---|
| The USV’s position and heading in the inertial coordinate system. | |
| The surge velocity u, sway velocity v, and yaw velocity r. | |
| Unknown environmental disturbances. | |
| Nonlinear dynamic term. | |
| The control input vector constrained by input saturation. |
| Parameters | Value | Parameters | Value | Parameters | Value |
|---|---|---|---|---|---|
| 0.1 | |||||
| 0.15 | 0.1 | 0.2 | |||
| 0.05 | 0.2 | 0.1 | |||
| 0.4 | 0.05 | 0.01 | |||
| 0.01 | 0.1 | 0.01 | |||
| 0.01 | 0.1 | 100 | |||
| 1 | 100 | 1 | |||
| 0.05 | 0.05 | 200 | |||
| 0.0025 | 100 | 0.005 | |||
| 0.1 | 1 | 0.01 | |||
| 1 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, M.; Zhang, G.; Meng, X. Nonlinear-Finite-Time-Extended-State-Observer-Based Command Filtered Control for Unmanned Surface Vessels with Rotatable Thrusters Under False Data Injection Attacks. J. Mar. Sci. Eng. 2025, 13, 1838. https://doi.org/10.3390/jmse13101838
Chen M, Zhang G, Meng X. Nonlinear-Finite-Time-Extended-State-Observer-Based Command Filtered Control for Unmanned Surface Vessels with Rotatable Thrusters Under False Data Injection Attacks. Journal of Marine Science and Engineering. 2025; 13(10):1838. https://doi.org/10.3390/jmse13101838
Chicago/Turabian StyleChen, Mengwei, Guichen Zhang, and Xiangfei Meng. 2025. "Nonlinear-Finite-Time-Extended-State-Observer-Based Command Filtered Control for Unmanned Surface Vessels with Rotatable Thrusters Under False Data Injection Attacks" Journal of Marine Science and Engineering 13, no. 10: 1838. https://doi.org/10.3390/jmse13101838
APA StyleChen, M., Zhang, G., & Meng, X. (2025). Nonlinear-Finite-Time-Extended-State-Observer-Based Command Filtered Control for Unmanned Surface Vessels with Rotatable Thrusters Under False Data Injection Attacks. Journal of Marine Science and Engineering, 13(10), 1838. https://doi.org/10.3390/jmse13101838






