Anomaly Detection in Maritime AIS Tracks: A Review of Recent Approaches
Abstract
1. Introduction
2. The Automatic Identification System
2.1. Background, Regulations, and Requirements
2.2. Data Format of AIS Messages
2.3. AIS-Based Surveillance
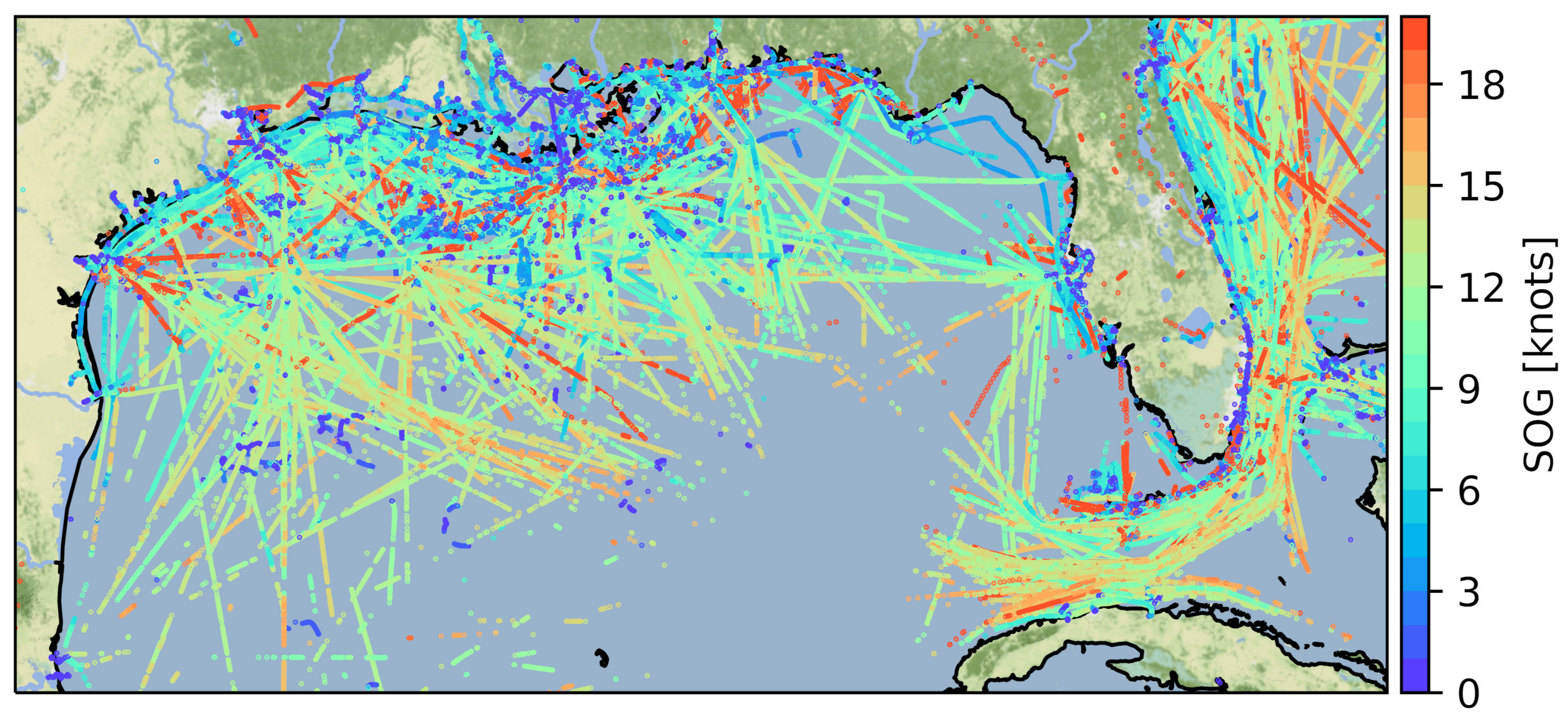
2.4. Available Datasets
3. AIS Anomaly Detection
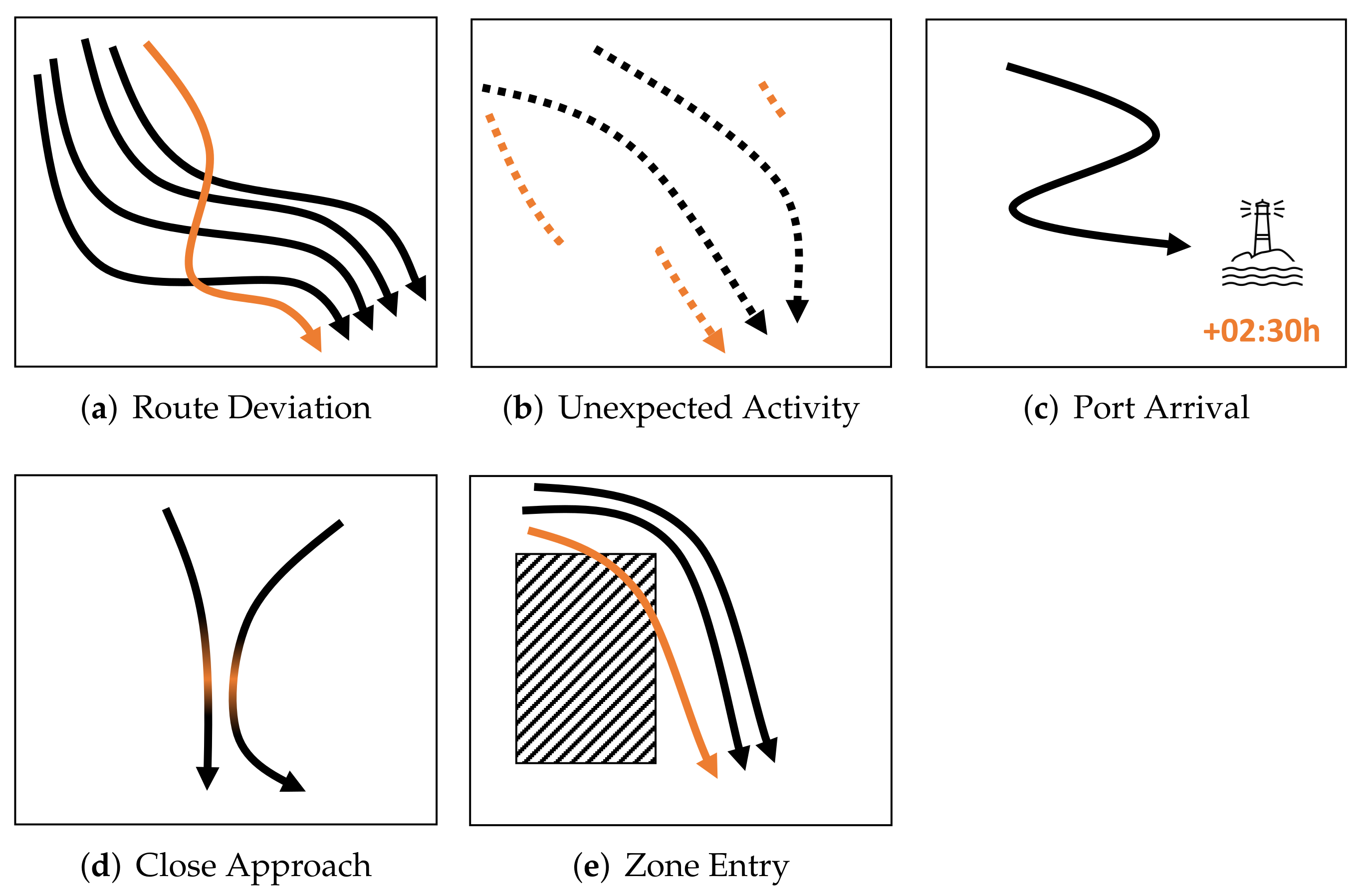
3.1. Anomalous AIS Behaviors
3.2. Applications of AIS-Based Anomaly Detection
| Route Deviation | Unexpected | Port Arrival | Close Approach | Zone Entry | ||
|---|---|---|---|---|---|---|
| Applications | Monitoring criminal activities | |||||
| • drug trade/smuggling [27,36] | ✓ | ✓ | ✓ | ✓ | ||
| • piracy [38] | ✓ | ✓ | ✓ | ✓ | ||
| • cloak the vessels’ identities [27] | ✓ | ✓ | ✓ | |||
| Support for safety activities | ||||||
| • collision risks [39,40] | ✓ | ✓ | ✓ | |||
| • Search and rescue (SAR) [41] | ✓ | ✓ | ✓ | |||
| • traffic monitoring [42] | ✓ | ✓ | ||||
| Environmental monitoring | ||||||
| • (over)fishing [8] | ✓ | ✓ | ✓ | |||
| • illegal fishing [37,43] | ✓ |
4. Classification of AIS Track Anomaly Detection Approaches
4.1. Related Work
4.2. Survey Methodology
4.3. Methods for AIS Anomaly Detection
4.4. Anomaly Types Addressed by Research
4.5. Detection Features
4.6. Scope of Detection Methods
4.7. Evaluation Datasets and Ground Truth
5. Discussion
5.1. Limitations of Recent Approaches
5.2. Privacy Considerations
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| AIS | Automatic identification system |
| AtoN | Aids to navigation |
| COG | Course over ground |
| COTS | Commercial off-the-shelf |
| DST | Destination |
| EMSA | European Maritime Safety Authority |
| GNSS | Global navigation satellite system |
| GPS | Global positioning system |
| HE | Heading |
| IMO | International Maritime Organization |
| MMSI | Maritime mobile service identity |
| PO | Position |
| ROT | Rate of turn |
| S-AIS | Satellite-based AIS |
| SAR | Search and rescue |
| SOG | Speed over ground |
| SOLAS | Safety of life at sea |
| STA | Status |
| TDMA | Time-division multiple access |
| VHF | Very high frequency |
| VTS | Vessel traffic service |
References
- International Transport Forum. ITF Transport Outlook 2021; Economic Cooperation and Development (OECD) Publishing: Paris, France, 2021. [Google Scholar] [CrossRef]
- International Maritime Organization (IMO). Resolution MSC. 74 (69) Adoption of New and Amended Performance Standards; IMO: London, UK, 1998. [Google Scholar]
- International Maritime Organization (IMO). SOLAS Chapter V—1/7/02 Safety of Navigation; IMO: London, UK, 2002. [Google Scholar]
- International Maritime Organization (IMO). Resolution A.1106(29) Revised Guidelines for the Onboard Operational Use of Shipborn Automatic Identification Systems (AIS); IMO: London, UK, 2015. [Google Scholar]
- Fournier, M.; Casey Hilliard, R.; Rezaee, S.; Pelot, R. Past, present, and future of the satellite-based automatic identification system: Areas of applications (2004–2016). WMU J. Marit. Aff. 2018, 17, 311–345. [Google Scholar] [CrossRef]
- Liu, D.; Wang, X.; Cai, Y.; Liu, Z.; Liu, Z.J. A Novel Framework of Real-Time Regional Collision Risk Prediction Based on the RNN Approach. J. Mar. Sci. Eng. 2020, 8, 224. [Google Scholar] [CrossRef]
- Zhen, R.; Riveiro, M.; Jin, Y. A novel analytic framework of real-time multi-vessel collision risk assessment for maritime traffic surveillance. Ocean Eng. 2017, 145, 492–501. [Google Scholar] [CrossRef]
- Natale, F.; Gibin, M.; Alessandrini, A.; Vespe, M.; Paulrud, A. Mapping Fishing Effort through AIS Data. PLoS ONE 2015, 10, e0130746. [Google Scholar] [CrossRef] [PubMed]
- MarineTraffic. Vessels Database. 2021. Available online: https://www.marinetraffic.com/en/data (accessed on 29 December 2021).
- Ferlansyah, N.; Suharjito, S. A Systematic Literature Review of Vessel Anomaly Behavior Detection Methods Based on Automatic Identification System (AIS) and another Sensor Fusion. Adv. Sci. Technol. Eng. Syst. J. 2020, 5, 287–292. [Google Scholar] [CrossRef]
- Martineau, E.; Roy, J. Maritime Anomaly Detection: Domain Introduction and Review of Selected Literature; Technical Report; Defence Research and Development Canada—Valcartier, Technical Memorandum TM2010-460; Defence Research and Development Canada: Ottawa, ON, Canada, 2011. [Google Scholar]
- Riveiro, M.; Pallotta, G.; Vespe, M. Maritime anomaly detection: A review. WIREs Data Min. Knowl. Discov. 2018, 8, e1266. [Google Scholar] [CrossRef]
- Sidibé, A.; Shu, G. Study of Automatic Anomalous Behaviour Detection Techniques for Maritime Vessels. J. Navig. 2017, 70, 847–858. [Google Scholar] [CrossRef]
- Tu, E.; Zhang, G.; Rachmawati, L.; Rajabally, E.; Huang, G.B. Exploiting AIS Data for Intelligent Maritime Navigation: A Comprehensive Survey From Data to Methodology. IEEE Trans. Intell. Transp. Syst. 2018, 19, 1559–1582. [Google Scholar] [CrossRef]
- Zissis, D.; Chatzikokolakis, K.; Spiliopoulos, G.; Vodas, M. A Distributed Spatial Method for Modeling Maritime Routes. IEEE Access 2020, 8, 47556–47568. [Google Scholar] [CrossRef]
- Cutlip, K. AIS for Safety and Tracking: A Brief History. 2017. Available online: https://globalfishingwatch.org/data/ais-for-safety-and-tracking-a-brief-history/ (accessed on 29 December 2021).
- Committee on Maritime Advanced Information Systems. Vessel Navigation and Traffic Services for Safe and Efficient Ports and Waterways: Interim Report; National Academies Press: Washington, DC, USA, 1996. [Google Scholar] [CrossRef]
- ITU-R. Recommendation M.1371-5 (02/2014)—Technical Characteristics for a Universal Shipborne Automatic Identification System Using Time Division Multiple Access in the VHF Maritime Mobile Band—M Series Mobile, Radiodetermination, Amateur and Related Satellite Services. Technical Report, International Telecommunication Union (ITU). 2014. Available online: https://www.itu.int/rec/R-REC-M.1371-5-201402-I/en (accessed on 29 December 2021).
- Harchowdhury, A.; Sarkar, B.K.; Bandyopadhyay, K.; Bhattacharya, A. Generalized mechanism of SOTDMA and probability of reception for satellite-based AIS. In Proceedings of the 2012 5th International Conference on Computers and Devices for Communication (CODEC), Kolkata, India, 17–19 December 2012; pp. 1–4. [Google Scholar] [CrossRef]
- Mazzarella, F.; Vespe, M.; Alessandrini, A.; Tarchi, D.; Aulicino, G.; Vollero, A. A novel anomaly detection approach to identify intentional AIS on-off switching. Expert Syst. Appl. 2017, 78, 110–123. [Google Scholar] [CrossRef]
- Vesecky, J.F.; Laws, K.E.; Paduan, J.D. Using HF surface wave radar and the ship Automatic Identification System (AIS) to monitor coastal vessels. In Proceedings of the IEEE 2009 IEEE International Geoscience and Remote Sensing Symposium, Cape Town, South Africa, 12–17 July 2009; Volume 3, pp. 761–764. [Google Scholar] [CrossRef]
- Cervera, M.A.; Ginesi, A. On the performance analysis of a satellite-based AIS system. In Proceedings of the 2008 10th International Workshop on Signal Processing for Space Communications (SPSC), Rhodes, Greece, 6–8 October 2008; pp. 1–8. [Google Scholar] [CrossRef]
- Metcalfe, K.; Bréheret, N.; Chauvet, E.; Collins, T.; Curran, B.K.; Parnell, R.J.; Turner, R.A.; Witt, M.J.; Godley, B.J. Using satellite AIS to improve our understanding of shipping and fill gaps in ocean observation data to support marine spatial planning. J. Appl. Ecol. 2018, 55, 1834–1845. [Google Scholar] [CrossRef]
- Nguyen, D.; Vadaine, R.; Hajduch, G.; Garello, R.; Fablet, R. A Multi-Task Deep Learning Architecture for Maritime Surveillance Using AIS Data Streams. In Proceedings of the 2018 IEEE 5th International Conference on Data Science and Advanced Analytics (DSAA), Turin, Italy, 1–3 October 2018; pp. 331–340. [Google Scholar] [CrossRef]
- Goudossis, A.; Katsikas, S.K. Towards a secure automatic identification system (AIS). J. Mar. Sci. Technol. 2019, 24, 410–423. [Google Scholar] [CrossRef]
- Kessler, G.C. Protected AIS: A Demonstration of Capability Scheme to Provide Authentication and Message Integrity. Trans. Nav. Int. J. Mar. Navig. Saf. Sea Transp. 2020, 14, 279–286. [Google Scholar] [CrossRef]
- Balduzzi, M.; Pasta, A.; Wilhoit, K. A security evaluation of AIS automated identification system. In Proceedings of the 30th Annual Computer Security Applications Conference (ACSAC), New Orleans, LA, USA, 8–12 December 2014; pp. 436–445. [Google Scholar] [CrossRef]
- Department of Homeland Security. Small Vessel Security Strategy. 2008. Available online: https://www.dhs.gov/sites/default/files/publications/small-vessel-security-strategy.pdf (accessed on 29 December 2021).
- Yang, D.; Wu, L.; Wang, S.; Jia, H.; Li, K.X. How big data enriches maritime research—A critical review of Automatic Identification System (AIS) data applications. Transp. Rev. 2019, 39, 755–773. [Google Scholar] [CrossRef]
- Schwehr, K.D.; McGillivary, P.A. Marine Ship Automatic Identification System (AIS) for Enhanced Coastal Security Capabilities: An Oil Spill Tracking Application. In Proceedings of the OCEANS 2007, Vancouver, BC, Canada, 29 September–4 October 2007; pp. 1–9. [Google Scholar] [CrossRef]
- European Maritime Safety Agency (EMSA). Procedures for requesting EMSA data from maritime applications. Marit. Data Req. Proced. 2018. Available online: http://www.emsa.europa.eu/publications/data-request-procedure/download/5120/2076/23.html (accessed on 29 December 2021).
- Laxhammar, R. Anomaly detection for sea surveillance. In Proceedings of the 2008 11th International Conference on Information Fusion Fusion, Cologne, Germany, 30 June–3 July 2008; pp. 1–8. [Google Scholar]
- Lane, R.O.; Nevell, D.A.; Hayward, S.D.; Beaney, T.W. Maritime anomaly detection and threat assessment. In Proceedings of the 2010 13th International Conference on Information Fusion, Edinburgh, UK, 26–29 July 2010; pp. 1–8. [Google Scholar] [CrossRef]
- Iphar, C.; Ray, C.; Napoli, A. Uses and Misuses of the Automatic Identification System. In Proceedings of the OCEANS 2019, Marseille, France, 17–20 June 2019; pp. 1–10. [Google Scholar] [CrossRef]
- Androjna, A.; Perkovič, M.; Pavic, I.; Mišković, J. AIS Data Vulnerability Indicated by a Spoofing Case-Study. Appl. Sci. 2021, 11, 5015. [Google Scholar] [CrossRef]
- Kowalska, K.; Peel, L. Maritime anomaly detection using Gaussian Process active learning. In Proceedings of the 2012 15th International Conference on Information Fusion, Singapore, 9–12 July 2012; pp. 1164–1171. [Google Scholar]
- Singh, S.K.; Heymann, F. Machine Learning-Assisted Anomaly Detection in Maritime Navigation using AIS Data. In Proceedings of the IEEE/ION Position, Location and Navigation Symposium (PLANS), Portland, OR, USA, 20–23 April 2020; pp. 832–838. [Google Scholar] [CrossRef]
- Rong, H.; Teixeira, A.P.; Guedes Soares, C. Data mining approach to shipping route characterization and anomaly detection based on AIS data. Ocean Eng. 2020, 198, 106936. [Google Scholar] [CrossRef]
- Vespe, M.; Visentini, I.; Bryan, K.; Braca, P. Unsupervised learning of maritime traffic patterns for anomaly detection. In Proceedings of the 9th IET Data Fusion Target Tracking Conference (DF&TT): Algorithms Applications, London, UK, 16–17 May 2012; pp. 1–5. [Google Scholar] [CrossRef]
- Fang, Z.; Yu, H.; Ke, R.; Shaw, S.L.; Peng, G. Automatic Identification System-Based Approach for Assessing the Near-Miss Collision Risk Dynamics of Ships in Ports. IEEE Trans. Intell. Transp. Syst. 2019, 20, 534–543. [Google Scholar] [CrossRef]
- Varlamis, I.; Tserpes, K.; Sardianos, C. Detecting Search and Rescue Missions from AIS Data. In Proceedings of the 2018 IEEE 34th International Conference on Data Engineering Workshops (ICDEW), Paris, France, 16–20 April 2018; 2018; pp. 60–65, ISSN 2473-3490. [Google Scholar] [CrossRef]
- Gao, M.; Shi, G.; Li, S. Online Prediction of Ship Behavior with Automatic Identification System Sensor Data Using Bidirectional Long Short-Term Memory Recurrent Neural Network. Sensors 2018, 18, 4211. [Google Scholar] [CrossRef]
- Ford, J.H.; Peel, D.; Kroodsma, D.; Hardesty, B.D.; Rosebrock, U.; Wilcox, C. Detecting suspicious activities at sea based on anomalies in Automatic Identification Systems transmissions. PLoS ONE 2018, 13, e0201640. [Google Scholar] [CrossRef]
- Pauly, D.; Zeller, D. Catch reconstructions reveal that global marine fisheries catches are higher than reported and declining. Nat. Commun. 2016, 7, 10244. [Google Scholar] [CrossRef]
- Guillarme, N.L.; Lerouvreur, X. Unsupervised extraction of knowledge from S-AIS data for maritime situational awareness. In Proceedings of the 16th International Conference on Information Fusion, Istanbul, Turkey, 9–12 July 2013; pp. 2025–2032. [Google Scholar]
- Wang, X.; Liu, X.; Liu, B.; de Souza, E.N.; Matwin, S. Vessel route anomaly detection with Hadoop MapReduce. In Proceedings of the IEEE International Conference on Big Data (Big Data), Washington, DC, USA, 27–30 October 2014; pp. 25–30. [Google Scholar] [CrossRef]
- Liu, B.; Souza, E.N.d.; Matwin, S.; Sydow, M. Knowledge-based clustering of ship trajectories using density-based approach. In Proceedings of the IEEE International Conference on Big Data (Big Data), Washington, DC, USA, 27–30 October 2014; pp. 603–608. [Google Scholar] [CrossRef]
- Radon, A.N.; Wang, K.; Glässer, U.; Wehn, H.; Westwell-Roper, A. Contextual verification for false alarm reduction in maritime anomaly detection. In Proceedings of the IEEE International Conference on Big Data (Big Data), Santa Clara, CA, USA, 29 October–1 November 2015; pp. 1123–1133. [Google Scholar] [CrossRef]
- Fu, P.; Wang, H.; Liu, K.; Hu, X.; Zhang, H. Finding Abnormal Vessel Trajectories Using Feature Learning. IEEE Access 2017, 5, 7898–7909. [Google Scholar] [CrossRef]
- Goodarzi, M.; Shaabani, M. Maritime Traffic Anomaly Detection from Spatio-Temporal AIS Data. In Proceedings of the 2nd of International Conference on Management and Fuzzy Systems (ICMFS Series), Eyvanekey, Iran, 29 November 2018; pp. 1–9. [Google Scholar]
- Riveiro, M.; Johansson, F.; Falkman, G.; Ziemke, T. Supporting maritime situation awareness using self organizing maps and gaussian mixture models. Front. Artif. Intell. Appl. 2008, 173, 84. [Google Scholar]
- Ristic, B.; La Scala, B.; Morelande, M.; Gordon, N. Statistical analysis of motion patterns in AIS Data: Anomaly detection and motion prediction. In Proceedings of the 11th International Conference on Information Fusion (FUSION), Cologne, Germany, 30 June–3 July 2008; pp. 1–7. [Google Scholar]
- Laxhammar, R.; Falkman, G. Conformal Prediction for Distribution-Independent Anomaly Detection in Streaming Vessel Data. In Proceedings of the 1st International Workshop on Novel Data Stream Pattern Mining Techniques (StreamKDD), Washington, DC, USA, 25 July 2010; pp. 47–55. [Google Scholar] [CrossRef]
- Laxhammar, R.; Falkman, G.; Sviestins, E. Anomaly detection in sea traffic - A comparison of the Gaussian Mixture Model and the Kernel Density Estimator. In Proceedings of the 12th International Conference on Information Fusion (FUSION), Seattle, WA, USA, 6–9 July 2009; pp. 756–763. [Google Scholar]
- Smith, J.; Nouretdinov, I.; Craddock, R.; Offer, C.; Gammerman, A. Anomaly Detection of Trajectories with Kernel Density Estimation by Conformal Prediction. In Artificial Intelligence Applications and Innovations (AIAI); Springer: Heidelberg, Germany, 2014; pp. 271–280. [Google Scholar] [CrossRef]
- Anneken, M.; Fischer, Y.; Beyerer, J. Evaluation and comparison of anomaly detection algorithms in annotated datasets from the maritime domain. In Proceedings of the SAI Intelligent Systems Conference (IntelliSys), London, UK, 10–11 November 2015; pp. 169–178. [Google Scholar] [CrossRef]
- Rhodes, B.J.; Garagic, D.; Dankert, J.R.; Stolzar, L.H.; Zandipour, M.; Seibert, M.; Bomberger, N.A. Anomaly Detection & Behavior Prediction: Higher-Level Fusion Based on Computational Neuroscientific Principles; IntechOpen Limited: London, UK, 2009. [Google Scholar]
- Venskus, J.; Treigys, P.; Bernatavičienė, J.; Tamulevičius, G.; Medvedev, V. Real-Time Maritime Traffic Anomaly Detection Based on Sensors and History Data Embedding. Sensors 2019, 19, 3782. [Google Scholar] [CrossRef]
- Nguyen, D.; Vadaine, R.; Hajduch, G.; Garello, R.; Fablet, R. GeoTrackNet–A Maritime Anomaly Detector Using Probabilistic Neural Network Representation of AIS Tracks and A Contrario Detection. IEEE Trans. Intell. Transp. Syst. 2021, 1–13. [Google Scholar] [CrossRef]
- Osekowska, E.; Johnson, H.; Carlsson, B. Grid Size Optimization for Potential Field based Maritime Anomaly Detection. Transp. Res. Procedia 2014, 3, 720–729. [Google Scholar] [CrossRef][Green Version]
- Soleimani, B.H.; Souza, E.N.D.; Hilliard, C.; Matwin, S. Anomaly detection in maritime data based on geometrical analysis of trajectories. In Proceedings of the 18th International Conference on Information Fusion (FUSION), Washington, DC, USA, 6–9 July 2015; pp. 1100–1105. [Google Scholar]
- Venskus, J.; Kurmis, M.; Andziulis, A.; Lukošius, Z.; Voznak, M.; Bykovas, D. Self-learning adaptive algorithm for maritime traffic abnormal movement detection based on virtual pheromone method. In Proceedings of the International Symposium on Performance Evaluation of Computer and Telecommunication Systems (SPECTS), Chicago, IL, USA, 26–29 July 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Guo, S.; Mou, J.; Chen, L.; Chen, P. An Anomaly Detection Method for AIS Trajectory Based on Kinematic Interpolation. J. Mar. Sci. Eng. 2021, 9, 609. [Google Scholar] [CrossRef]
- Katsilieris, F.; Braca, P.; Coraluppi, S. Detection of malicious AIS position spoofing by exploiting radar information. In Proceedings of the 16th International Conference on Information Fusion (FUSION), Istanbul, Turkey, 9–12 July 2013; pp. 1196–1203. [Google Scholar]
- Keane, K.R. Detecting Motion Anomalies. In Proceedings of the 8th ACM SIGSPATIAL Workshop on GeoStreaming (IWGS), Redondo Beach, CA, USA, 7 November 2017; pp. 21–28. [Google Scholar] [CrossRef]
- d’Afflisio, E.; Braca, P.; Millefiori, L.M.; Willett, P. Maritime Anomaly Detection Based on Mean-Reverting Stochastic Processes Applied to a Real-World Scenario. In Proceedings of the 21st International Conference on Information Fusion (FUSION), Cambridge, UK, 10–13 July 2018; pp. 1171–1177. [Google Scholar] [CrossRef]
- de Vries, G.K.D.; van Someren, M. Machine learning for vessel trajectories using compression, alignments and domain knowledge. Expert Syst. Appl. 2012, 39, 13426–13439. [Google Scholar] [CrossRef]
- Handayani, D.O.D.; Sediono, W.; Shah, A. Anomaly Detection in Vessel Tracking Using Support Vector Machines (SVMs). In Proceedings of the International Conference on Advanced Computer Science Applications and Technologies (ACSAT), Kuching, Malaysia, 22–24 December 2013; pp. 213–217. [Google Scholar] [CrossRef]
- Zhen, R.; Jin, Y.; Hu, Q.; Shao, Z.; Nikitakos, N. Maritime Anomaly Detection within Coastal Waters Based on Vessel Trajectory Clustering and Naïve Bayes Classifier. J. Navig. 2017, 70, 648–670. [Google Scholar] [CrossRef]
- Pallotta, G.; Vespe, M.; Bryan, K. Vessel Pattern Knowledge Discovery from AIS Data: A Framework for Anomaly Detection and Route Prediction. Entropy 2013, 15, 2218–2245. [Google Scholar] [CrossRef]
- Pallotta, G.; Vespe, M.; Bryan, K. Traffic knowledge discovery from AIS data. In Proceedings of the 16th International Conference on Information Fusion (FUSION), Istanbul, Turkey, 9–12 July 2013; pp. 1996–2003. [Google Scholar]
- Kazemi, S.; Abghari, S.; Lavesson, N.; Johnson, H.; Ryman, P. Open data for anomaly detection in maritime surveillance. Expert Syst. Appl. 2013, 40, 5719–5729. [Google Scholar] [CrossRef]
- Lei, P.R. A framework for anomaly detection in maritime trajectory behavior. Knowl. Inf. Syst. Vol. 2016, 47, 189–214. [Google Scholar] [CrossRef]
- Johansson, F.; Falkman, G. Detection of vessel anomalies—A Bayesian network approach. In Proceedings of the 3rd International Conference on Intelligent Sensors, Sensor Networks and Information (ISSNIP), Melbourne, VIC, Australia, 3–6 December 2007; pp. 395–400. [Google Scholar] [CrossRef]
- Mascaro, S.; Korb, K.B.; Nicholson, A.E. Learning Abnormal Vessel Behaviour from AIS Data with Bayesian Networks at Two Time Scales. Technical Report, 2010/4, Bayesian Intelligence. 2010. Available online: https://bayesian-intelligence.com/publications/TR2010_4_AbnormalVesselBehaviour.pdf (accessed on 29 December 2021).
- Mascaro, S.; Nicholso, A.E.; Korb, K.B. Anomaly detection in vessel tracks using Bayesian networks. Int. J. Approx. Reason. 2014, 55, 84–98. [Google Scholar] [CrossRef]
- Zor, C.; Kittler, J. Maritime anomaly detection in ferry tracks. In Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), New Orleans, LA, USA, 5–9 March 2017; pp. 2647–2651. [Google Scholar] [CrossRef]
- McAbee, A.; Scrofani, J.; Tummala, M.; Garren, D.; McEachen, J. Traffic pattern detection using the Hough transformation for anomaly detection to improve maritime domain awareness. In Proceedings of the 17th International Conference on Information Fusion (FUSION), Salamanca, Spain, 7–10 July 2014; pp. 1–6. [Google Scholar]
- Wu, Y.; Patterson, A.; Santos, R.; Vijaykumar, N. Topology Preserving Mapping for Maritime Anomaly Detection. In Proceedings of the International Conference on Computational Science and Its Applications (ICCSA), Guimarães, Portugal, 30 June–3 July 2014. [Google Scholar] [CrossRef]
- Terroso-Saenz, F.; Valdes-Vela, M.; Skarmeta-Gomez, A.F. A complex event processing approach to detect abnormal behaviours in the marine environment. Inf. Syst. Front. 2016, 18, 765–780. [Google Scholar] [CrossRef]
- Kong, Z.; Jones, A.; Belta, C. Temporal Logics for Learning and Detection of Anomalous Behavior. IEEE Trans. Autom. Control 2017, 62, 1210–1222. [Google Scholar] [CrossRef]
- Roy, J. Anomaly detection in the maritime domain. In Optics and Photonics in Global Homeland Security IV; Halvorson, C.S., Lehrfeld, D., Saito, T.T., Eds.; International Society for Optics and Photonics, SPIE Defense and Security Symposium: Orlando, FL, USA, 2008; Volume 6945, pp. 180–193. [Google Scholar] [CrossRef]
- Alessandrini, A.; Mazzarella, F.; Vespe, M. Estimated Time of Arrival Using Historical Vessel Tracking Data. IEEE Trans. Intell. Transp. Syst. 2019, 20, 7–15. [Google Scholar] [CrossRef]
- Chen, X.; Ling, J.; Yang, Y.; Zheng, H.; Xiong, P.; Postolache, O.; Xiong, Y. Ship trajectory reconstruction from AIS sensory data via data quality control and prediction. Math. Probl. Eng. 2020, 2020, 7191296. [Google Scholar] [CrossRef]
- Willems, N.; Van De Wetering, H.; Van Wijk, J.J. Visualization of vessel movements. Comput. Graph. Forum 2009, 28, 959–966. [Google Scholar] [CrossRef]
- Khraisat, A.; Gondal, I.; Vamplew, P.; Kamruzzaman, J. Survey of intrusion detection systems: Techniques, datasets and challenges. Cybersecurity 2019, 2, 1–22. [Google Scholar] [CrossRef]
- Mao, S.; Tu, E.; Zhang, G.; Rachmawati, L.; Rajabally, E.; Huang, G.B. An Automatic Identification System (AIS) Database for Maritime Trajectory Prediction and Data Mining. In Proceedings of the International Conference of Extreme Learning Machine (ELM), Singapore, Yatai, China, 4–7 October 2017; pp. 241–257. [Google Scholar] [CrossRef]
- Harati-Mokhtari, A.; Wall, A.; Brookes, P.; Wang, J. Automatic Identification System (AIS): A human factors approach. J. Navig. 2007, 60, 373–389. [Google Scholar] [CrossRef]
- Mondal, K.; Banerjee, T.; Panja, A. Autonomous Underwater Vehicles: Recent Developments and Future Prospects. Int. J. Res. Appl. Sci. Eng. Technol. 2019, 7, 215–222. [Google Scholar] [CrossRef]
- Kavallieratos, G.; Katsikas, S.; Gkioulos, V. Modelling Shipping 4.0: A Reference Architecture for the Cyber-Enabled Ship. In Proceedings of the Asian Conference on Intelligent Information and Database Systems (ACIIDS), Phuket, Thailand, 23–26 March 2020; pp. 202–217. [Google Scholar] [CrossRef]
- Golz, M.; Boeck, F.; Ritz, S.; Holbach, G.; Richter, N.; Haselberger, P.; Wehner, W.; Schiemann, M.; Rentzow, E.; Müller, T.; et al. MUM - Large Modifiable Underwater Mother Ship: Requirements and Application Scenarios. In Proceedings of the 2018 OCEANS - MTS/IEEE Kobe Techno-Oceans (OTO), Kobe, Japan, 28–31 May 2018; pp. 1–9. [Google Scholar] [CrossRef]
- Serra-Sogas, N.; O’Hara, P.D.; Pearce, K.; Smallshaw, L.; Canessa, R. Using aerial surveys to fill gaps in AIS vessel traffic data to inform threat assessments, vessel management and planning. Mar. Policy 2021, 133, 104765. [Google Scholar] [CrossRef]
- nex. Spying on the Seven Seas with AIS. 2013. Available online: https://blog.rapid7.com/2013/04/29/spying-on-the-seven-seas-with-ais/ (accessed on 29 December 2021).
- International Maritime Organization (IMO). Report Of The Maritime Safety Committee On Its Seventy-Ninth Session, Agenda item 23 (15 December 2004). MSC 79/23; IMO: London, UK, 2004. [Google Scholar]
- European Data Protection Supervisor. Opinion of the European Data Protection Supervisor on the Commission Implementing Regulation (EU) No 404/2011. Off. J. Eur. Union 2012, C 37/1, 5. [Google Scholar]
- epic.org. EPIC v. USCG – Nationwide Automatic Identification System. Available online: https://epic.org/documents/epic-v-uscg-nationwide-automatic-identification-system/ (accessed on 29 December 2021).
- Aziz, A.; Tedeschi, P.; Sciancalepore, S.; Pietro, R.D. SecureAIS - Securing Pairwise Vessels Communications. In Proceedings of the IEEE Conf. on Communications and Network Security (CNS), Avignon, France, 29 June–1 July 2020; pp. 1–9. [Google Scholar] [CrossRef]

| Type | Data |
|---|---|
| Static | • MMSI number |
| • Call sign & call name | |
| • Length & beam | |
| • Ship type | |
| • Antenna location (aft/bow; port/starboard) | |
| Dynamic | • Ship position (PO), accuracy, and integrity |
| • Time in UTC | |
| • Course over ground (COG) | |
| • Speed over ground (SOG) | |
| • Heading (HE) | |
| • Rate of turn (ROT) | |
| • Navigational status, e.g., at anchor (STA) | |
| Voyage related | • Draught |
| • Hazardous cargo (type) | |
| • Destination (DST), and estimated time of arrival | |
| Safety related | • Text messages |
| Method | Publication | Anomaly | Features (Section 4.5) | Scope (Section 4.6) | Dataset (Section 4.7) | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| (Section 4.3) | Authors | Year | (Section 4.4) | PO | COG | SOG | HE | DST | Type | STA | EXT | Region | Vessel | Time | Type | Ground Truth |
| DBSCAN | Guillarme and Lerouvreur [45] | 2013 | R | ● | ● | ● | ○ | ○ | ○ | ○ | ○ | ● | ○ | ● | priv | ○ |
| Wang et al. [46] | 2014 | R | ● | ○ | ● | ● | ○ | ○ | ○ | ○ | ● | ○ | ○ | - | ● | |
| Liu et al. [47] | 2014 | R | ● | ● | ● | ○ | ○ | ○ | ○ | ● | ● | ○ | ● | priv | ○ | |
| Radon et al. [48] | 2015 | R | ● | ● | ● | ○ | ● | ○ | ○ | ○ | ● | ○ | ● | pub | ● | |
| Fu et al. [49] | 2017 | R | ● | ● | ● | ○ | ● | ● | ○ | ○ | ● | ○ | ● | priv | ○ | |
| Goodarzi and Shaabani [50] | 2019 | R | ● | ● | ● | ○ | ○ | ○ | ○ | ○ | ● | ○ | ○ | priv | ○ | |
| Gaussian Mixture Model and Kernel Density Estimation | Riveiro et al. [51] | 2008 | R | ● | ○ | ● | ● | ○ | ○ | ○ | ○ | ● | ● | ● | synth | ◐ |
| Laxhammar [32] | 2008 | R | ● | ○ | ● | ○ | ○ | ○ | ○ | ○ | ● | ○ | ○ | priv | ○ | |
| Ristic et al. [52] | 2008 | R | ● | ○ | ● | ○ | ○ | ○ | ○ | ○ | ● | ○ | ● | self | ○ | |
| Laxhammer et al. [53,54] | 2010 | R | ● | ○ | ● | ○ | ○ | ● | ○ | ○ | ● | ○ | ○ | pub | ◐ | |
| Smith et al. [55] | 2014 | R | ● | ○ | ● | ○ | ○ | ○ | ○ | ○ | ● | ● | ● | self | ○ | |
| Anneken et al. [56] | 2015 | R | ● | ○ | ● | ● | ○ | ○ | ○ | ○ | ● | ● | ● | priv | ● | |
| Neural Network | Rhodes et al. [57] | 2009 | R | ● | ● | ● | ○ | ○ | ○ | ○ | ○ | ● | ○ | ○ | priv | ○ |
| Nguyen et al. [24] | 2018 | R | ● | ● | ● | ○ | ○ | ○ | ○ | ○ | ● | ○ | ● | pub | ◐ | |
| Venskus et al. [58] | 2019 | R | ● | ○ | ● | ● | ○ | ○ | ○ | ● | ● | ● | ○ | priv | ○ | |
| Singh and Heymann [37] | 2020 | U | ● | ● | ● | ○ | ○ | ○ | ○ | ○ | ○ | ● | ● | self | ● | |
| Nguyen et al. [59] | 2021 | R | ● | ● | ● | ○ | ○ | ○ | ○ | ○ | ● | ● | ● | priv | ◐ | |
| Geometry | Osekowska et al. [60] | 2014 | U | ● | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ● | ○ | ● | - | - |
| Soleimani et al. [61] | 2015 | R | ● | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ● | ○ | priv | ● | |
| Venskus et al. [62] | 2015 | R | ● | ○ | ○ | ○ | ○ | ○ | ○ | ● | ○ | ● | ● | priv | ○ | |
| Zissis et al. [15] | 2020 | R | ● | ○ | ○ | ○ | ● | ○ | ○ | ○ | ● | ● | ○ | pub | ● | |
| Guo et al. [63] | 2021 | R | ● | ● | ● | ● | ○ | ○ | ○ | ○ | ○ | ● | ● | pub | ○ | |
| Stochastic | Katsilieris et al. [64] | 2013 | R Z | ● | ○ | ○ | ○ | ○ | ○ | ○ | ● | ○ | ○ | ○ | priv | ○ |
| Keane [65] | 2017 | R | ● | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ● | ○ | ○ | priv | ○ | |
| Ford et al. [43] | 2018 | U | ● | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ● | ○ | ● | priv | ◐ | |
| d’Afflisio et al. [66] | 2018 | U | ● | ○ | ● | ○ | ○ | ○ | ○ | ○ | ○ | ● | ● | - | ● | |
| Rong et al. [38] | 2020 | R | ● | ○ | ● | ● | ● | ● | ○ | ○ | ● | ○ | ● | - | ○ | |
| Machine-Learning & Clustering | Vespe et al. [39] | 2012 | R Z | ● | ● | ● | ○ | ○ | ○ | ● | ○ | ● | ○ | ● | priv | ○ |
| de Vries and van Someren [67] | 2012 | R | ● | ○ | ○ | ○ | ○ | ○ | ○ | ● | ● | ○ | ● | self | ○ | |
| Handayani et al. [68] | 2013 | R | ● | ● | ● | ● | ○ | ○ | ● | ○ | ● | ○ | ● | pub | ○ | |
| Zhen et al. [69] | 2017 | R | ● | ● | ● | ○ | ○ | ○ | ○ | ○ | ● | ○ | ● | priv | ○ | |
| Frameworks | Pallota et al. [70,71] | 2013 | R | ● | ● | ● | ○ | ○ | ○ | ● | ○ | ● | ○ | ● | priv | ○ |
| Kazemi et al. [72] | 2013 | P | ● | ○ | ● | ● | ● | ● | ● | ● | ● | ● | ● | pub | ● | |
| Lei [73] | 2016 | R | ● | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ● | ○ | ● | self | ◐ | |
| Lane et al. [33] | 2010 | R U P C Z | ● | ○ | ● | ● | ● | ○ | ○ | ○ | ● | ● | ○ | - | - | |
| Bayesian Network | Johansson and Falkman [74] | 2007 | R | ● | ○ | ● | ● | ○ | ● | ○ | ○ | ● | ● | ○ | synth | ○ |
| Mascaro et al. [75] | 2010 | R | ● | ● | ● | ● | ○ | ● | ○ | ● | ● | ○ | ● | priv | ◐ | |
| Mascaro et al. [76] | 2014 | R C | ● | ● | ● | ● | ○ | ● | ○ | ● | ● | ○ | ● | priv | ◐ | |
| Gaussian Process | Kowalska and Peel [36] | 2007 | R C | ● | ○ | ● | ● | ○ | ● | ○ | ○ | ● | ○ | ● | priv | ◐ |
| Zor and Kittler [77] | 2017 | R P | ● | ○ | ● | ● | ● | ○ | ○ | ○ | ● | ● | ● | priv | ○ | |
| Miscellaneous | McAbee et al. [78] | 2014 | R | ● | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ● | ○ | ○ | self | ◐ |
| Wu et al. [79] | 2014 | U | ● | ○ | ● | ○ | ○ | ○ | ○ | ○ | ● | ○ | ● | self | ○ | |
| Terroso-Saenz et al. [80] | 2016 | R C | ● | ○ | ● | ○ | ○ | ○ | ○ | ● | ● | ● | ● | pub | ◐ | |
| Kong et al. [81] | 2017 | R | ● | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ● | ○ | ● | priv | ○ | |
| Vessel Type | |||
|---|---|---|---|
| Specific (●) | Independent (○) | ||
| Region | constrained (●) | 11 | 27 |
| independent (○) | 5 | 1 | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wolsing, K.; Roepert, L.; Bauer, J.; Wehrle, K. Anomaly Detection in Maritime AIS Tracks: A Review of Recent Approaches. J. Mar. Sci. Eng. 2022, 10, 112. https://doi.org/10.3390/jmse10010112
Wolsing K, Roepert L, Bauer J, Wehrle K. Anomaly Detection in Maritime AIS Tracks: A Review of Recent Approaches. Journal of Marine Science and Engineering. 2022; 10(1):112. https://doi.org/10.3390/jmse10010112
Chicago/Turabian StyleWolsing, Konrad, Linus Roepert, Jan Bauer, and Klaus Wehrle. 2022. "Anomaly Detection in Maritime AIS Tracks: A Review of Recent Approaches" Journal of Marine Science and Engineering 10, no. 1: 112. https://doi.org/10.3390/jmse10010112
APA StyleWolsing, K., Roepert, L., Bauer, J., & Wehrle, K. (2022). Anomaly Detection in Maritime AIS Tracks: A Review of Recent Approaches. Journal of Marine Science and Engineering, 10(1), 112. https://doi.org/10.3390/jmse10010112





