A VM-Based Detection Framework against Remote Code Execution Attacks for Closed Source Network Devices
Abstract
:1. Introduction
2. Related Work
3. Design Goals
- Universality: The system should succeed in detecting any kind of remote code execution attacks causing modifications in the target’s memory.
- Generality: The system should support various platforms with diversity in vendors and operating systems.
- Runtime support: Any intrusion attempts to the target device should be detected immediately to mitigate the attacks in time.
- Availability: The system should work correctly while not affecting the internal states of the target device as well as its network configuration.
4. VM-Based Intrusion Detection Mechanism
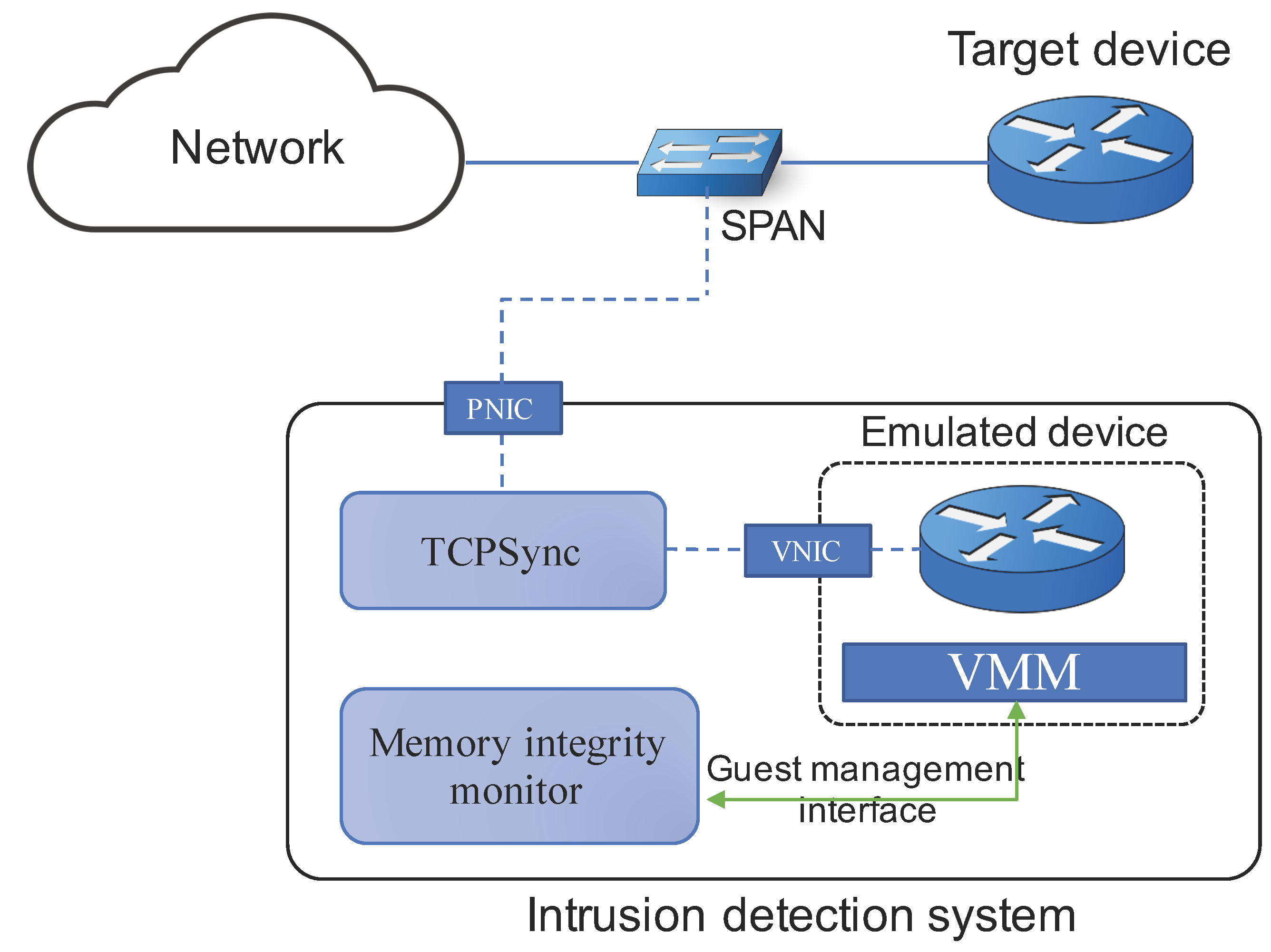
4.1. System Architecture
- Emulated device: It is a VM instance that emulates the target device. We require the VM to run the same binary image as the target’s firmware. All mirrored packets from the target device, being passed through a physical network interface (PNIC) of the host system, TCPSync, and a virtualized network interface (VNIC) in order, are then injected into the emulated device. Due to the agreement of the firmware image and the traffic mirroring, internal states of the emulated device will conform to the target device.
- TCPSync: It is a software module, running outside the emulated device that forwards all received packets from a PNIC, transforming some packets if necessary, to a VNIC attached to the emulated device. The main work of this module is to conduct transparent conversion of certain packet flows through connection-oriented protocols such as TCP. Details on TCPSync will be presented in the next section.
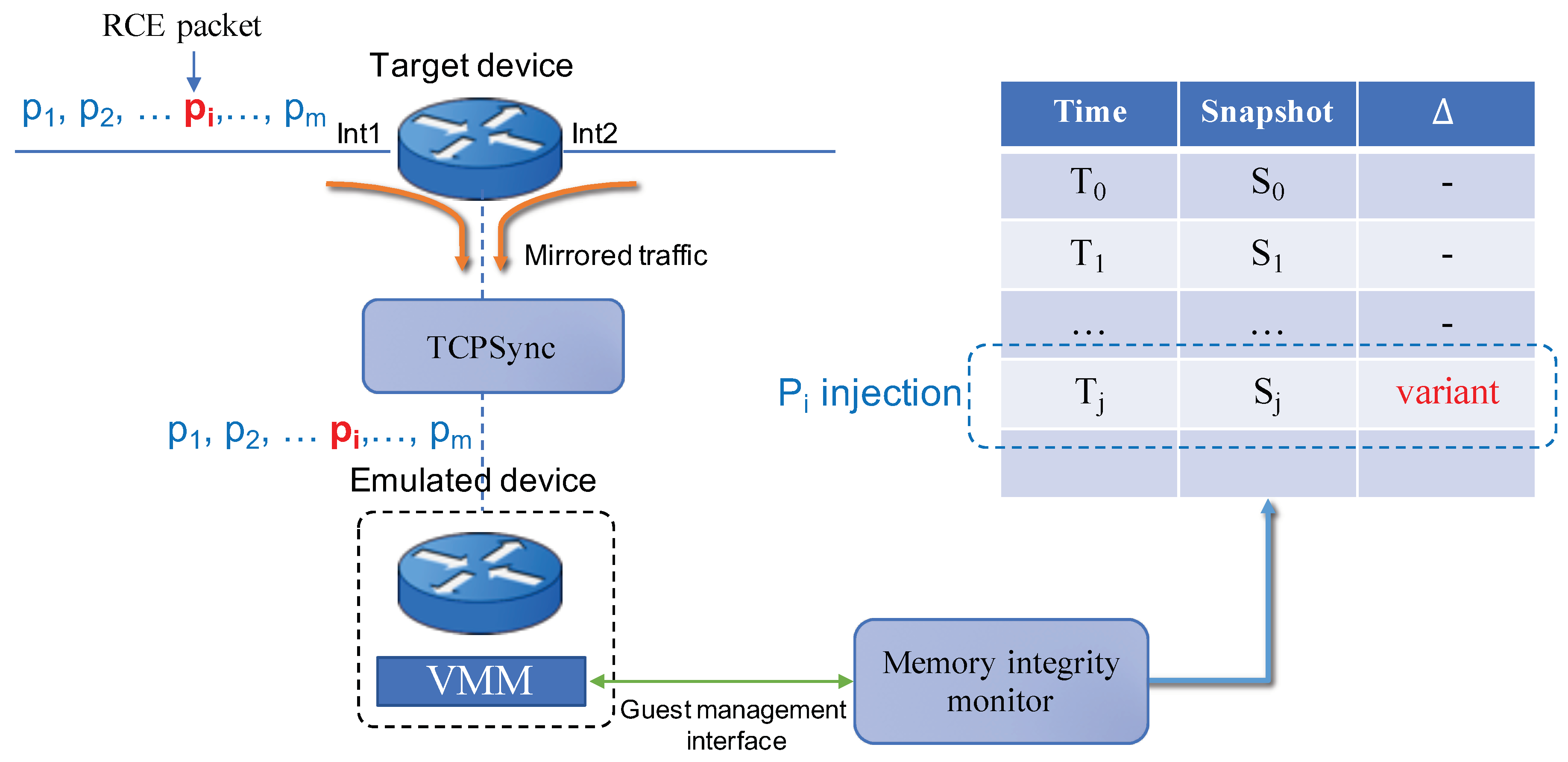
- Memory integrity monitor: It is a software module that aims to monitor the internal state of the VM. It has an interaction with the emulated device through a guest management interface, which is provided by a virtual machine manager (VMM). By using an introspection library (e.g., Libvmi [20]) or a debugger such as GDB, it periodically obtains snapshots of the VM’s memory and the corresponding hash value, from which it checks whether the integrity has been broken.
4.2. System Components
4.2.1. Memory Integrity Monitor
4.2.2. TCPSync
5. Experiment and Evaluation
5.1. Experiment
5.2. Discussion on Detection Performance
5.3. Evaluation
6. Conclusions and Future Work
Funding
Conflicts of Interest
References
- Veeraraghavan, M.; Sato, T.; Buchanan, M.; Rahimi, R.; Okamoto, S.; Yamanaka, N. Network function virtualization: A survey. IEICE Trans. Commun. 2017, E100B. [Google Scholar] [CrossRef]
- Joshi, K.; Benson, T. Network Function Virtualization. IEEE Internet Compu. 2016, 20, 7–9. [Google Scholar] [CrossRef]
- Vilalta, R.; Muñoz, R.; Mayoral, A.; Casellas, R.; Martínez, R.; López, V.; López, D. Transport Network Function Virtualization. J. Lightwave Technol. 2015, 33, 1557–1564. [Google Scholar] [CrossRef]
- Li, Y.; Chen, M. Software-defined network function virtualization: A survey. IEEE Access 2015, 3, 2542–2553. [Google Scholar] [CrossRef]
- Martins, J.; Ahmed, M.; Raiciu, C.; Olteanu, V.; Honda, M.; Huici, R.; Felipe, B. ClickOS and the Art of Network Function Virtualization. In Proceedings of the 11th USENIX Symposium on Networked Systems Design and Implementation (NSDI 14), Boston, MA, USA, 2–4 April 2014; pp. 459–473. [Google Scholar]
- Egi, N.; Greenhalgh, A.; Handley, M.; Iannaccone, G.; Manesh, M.; Mathy, L.; Ratnasamy, S. Improved forwarding architecture and resource management for multi-core software routers. In Proceedings of the NPC 2009—6th International Conference on Network and Parallel Computing, Gold Coast, QLD, Australia, 19–21 October 2009; pp. 117–124. [Google Scholar] [CrossRef]
- Scott-Hayward, S.; Natarajan, S.; Sezer, S. Survey of Security in Software Defined Networks. Surv. Tutor. 2016, 18, 623–654. [Google Scholar] [CrossRef]
- Yin, Z.; Caesar, M.; Zhou, Y. Towards Understanding Bugs in Open Source Router Software. ACM SIGCOMM Comput. Commun. Rev. 2010, 40, 35–40. [Google Scholar] [CrossRef]
- Prieto, L.P.; Rodríguez-Triana, M.J.; Kusmin, M.; Laanpere, M. Don’t Trust Your Router: Detecting Compromised Routers. CEUR Workshop Proc. 2017, 1828, 53–59. [Google Scholar] [CrossRef]
- Hau, B.; Lee, T.; Homan, J. SYNful Knock—A Cisco Router Implant. Fire Eye Threat Res. Adv. Malware 2015. Available online: https://www.fireeye.com/blog/threat-research/2015/09/synful_knock_-_acis.html (accessed on 28 March 2019).
- Li, F.; Zhang, L.; Chen, D. Vulnerability mining of Cisco router based on fuzzing. In Proceedings of the 2014 2nd International Conference on Systems and Informatics, ICSAI 2014, Shanghai, China, 15–17 November 2014; pp. 649–653. [Google Scholar] [CrossRef]
- Sang-Hoon, C.; Ki-Woong, P. Mem-Shot: Design and Implementation of API-Trigger Driven Memory Dump System for Obfuscated Malware Analysis. J. Korean Soc. Comput. 2016; 12, 23–32. [Google Scholar]
- Patil, R.; Modi, C. A Novel Approach to Detect Extraneous Network Traffic from the Compromised Router. In Proceedings of the 3rd International Conference on Recent Advances in Information Technology (RAIT), Dhanbad, India, 3–5 March 2016. [Google Scholar]
- Mizrak, A.T.; Savage, S.; Marzullo, K. Detecting compromised routers via packet forwardåing behavior. IEEE Netw. 2008, 22, 34–39. [Google Scholar] [CrossRef]
- Cui, A.; Stolfo, S.J. Defending Embedded Systems with Software Symbiotes. Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics). 6961 LNCS. 2011, pp. 358–377. Available online: https://doi.org/10.1007/978-3-642-23644-0_19 (accessed on 27 March 2019).
- Cui, A.; Kataria, J.; Stolfo, S.J. From prey to hunter. In Proceedings of the 27th Annual Computer Security Applications Conference on—ACSAC’11, Orlando, FL, USA, 5–9 December 2011; p. 393. [Google Scholar] [CrossRef]
- Desai, V.; Natarajan, S.; Wolf, T. Packet forwarding misbehavior detection in next-generation networks. In Proceedings of the IEEE International Conference on Communications, Ottawa, ON, Canada, 10–15 June 2012; pp. 846–851. [Google Scholar] [CrossRef]
- Le, F.; Lee, S.; Wong, T.; Kim, H.S.; Newcomb, D. Detecting network-wide and router-specific misconfigurations through data mining. IEEE/ACM Trans. Netw. 2009, 17, 66–79. [Google Scholar] [CrossRef]
- Le, F.; Lee, S.; Wong, T.; Kim, H.; Newcomb, D. Minerals: Using Data Mining to Detect Router Misconfigurations. In Proceedings of the 2006 SIGCOMM Workshop on Mining Network Data, Pisa, Italy, 11–15 September 2006; pp. 293–298. [Google Scholar] [CrossRef]
- LibVMI-Project. Libvmi, a Virtual Machine Introspection Library. 2018. Available online: http://libvmi.com/ (accessed on 27 March 2019).
- Cisco PSIRT. Multiple Vulnerabilities in the IOS FTP Server; Technical Report; 2007. [Google Scholar]
- Cisco PSIRT. Crafted IP Option Vulnerability in Cisco IOS; Technical Report; 2007. [Google Scholar]



© 2019 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shin, Y. A VM-Based Detection Framework against Remote Code Execution Attacks for Closed Source Network Devices. Appl. Sci. 2019, 9, 1294. https://doi.org/10.3390/app9071294
Shin Y. A VM-Based Detection Framework against Remote Code Execution Attacks for Closed Source Network Devices. Applied Sciences. 2019; 9(7):1294. https://doi.org/10.3390/app9071294
Chicago/Turabian StyleShin, Youngjoo. 2019. "A VM-Based Detection Framework against Remote Code Execution Attacks for Closed Source Network Devices" Applied Sciences 9, no. 7: 1294. https://doi.org/10.3390/app9071294
APA StyleShin, Y. (2019). A VM-Based Detection Framework against Remote Code Execution Attacks for Closed Source Network Devices. Applied Sciences, 9(7), 1294. https://doi.org/10.3390/app9071294



