Joint Trajectory and Communication Design for Buffer-Aided Multi-UAV Relaying Networks
Abstract
1. Introduction
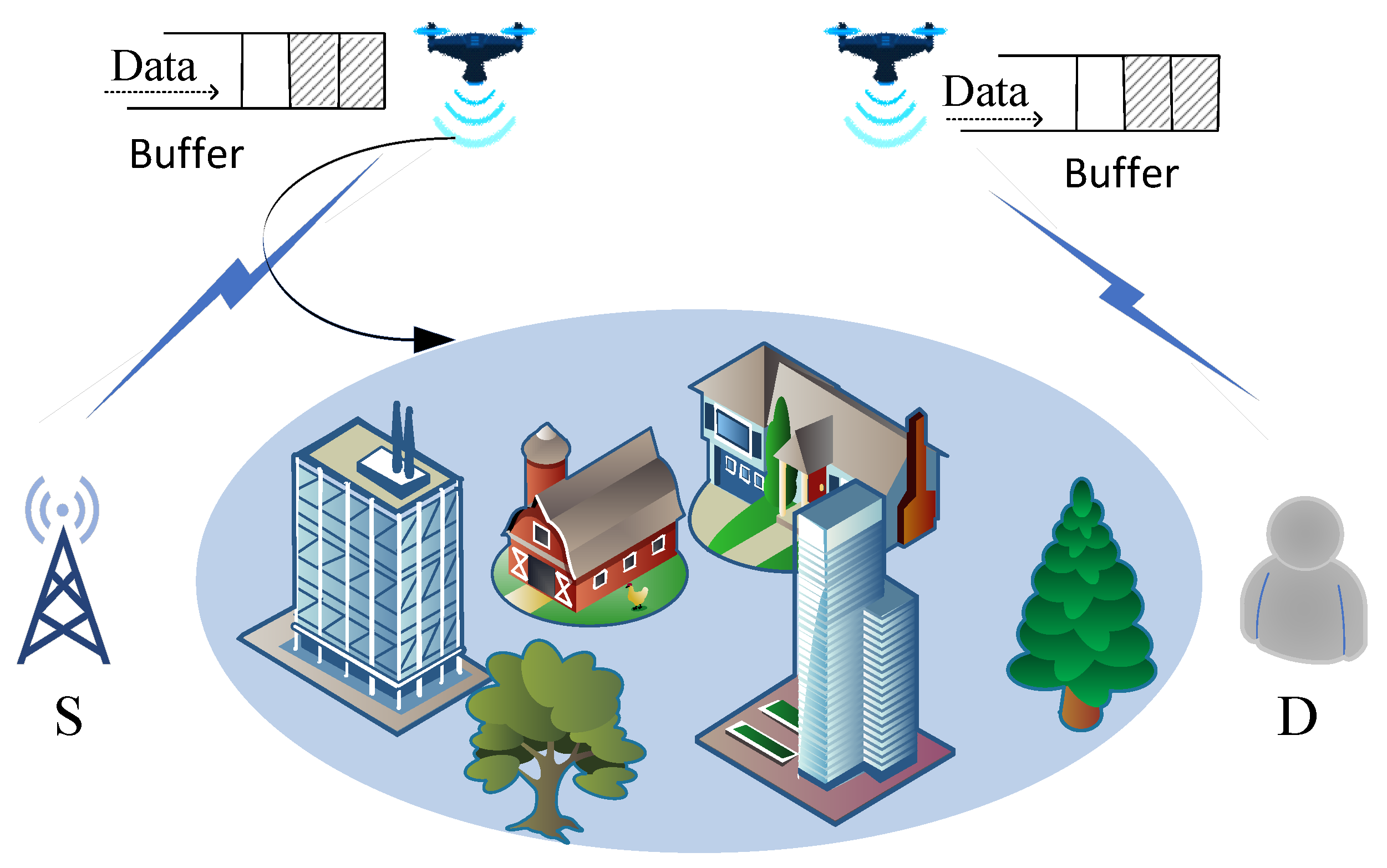
2. System Model and Problem Formulation
2.1. System Model
2.2. Problem Formulation
3. The Proposed Algorithm
3.1. Sub-Problem 1: Optimizing Relay Selection and UAV Power Control of a Given UAV Trajectory
3.2. Sub-Problem 2: Optimizing the UAV Trajectory a Given Relay Selection and Power Control
3.3. Overall Algorithm and Convergence
| Algorithm 1 Proposed joint relay selection, power allocation, and trajectory optimization algorithm. |
|
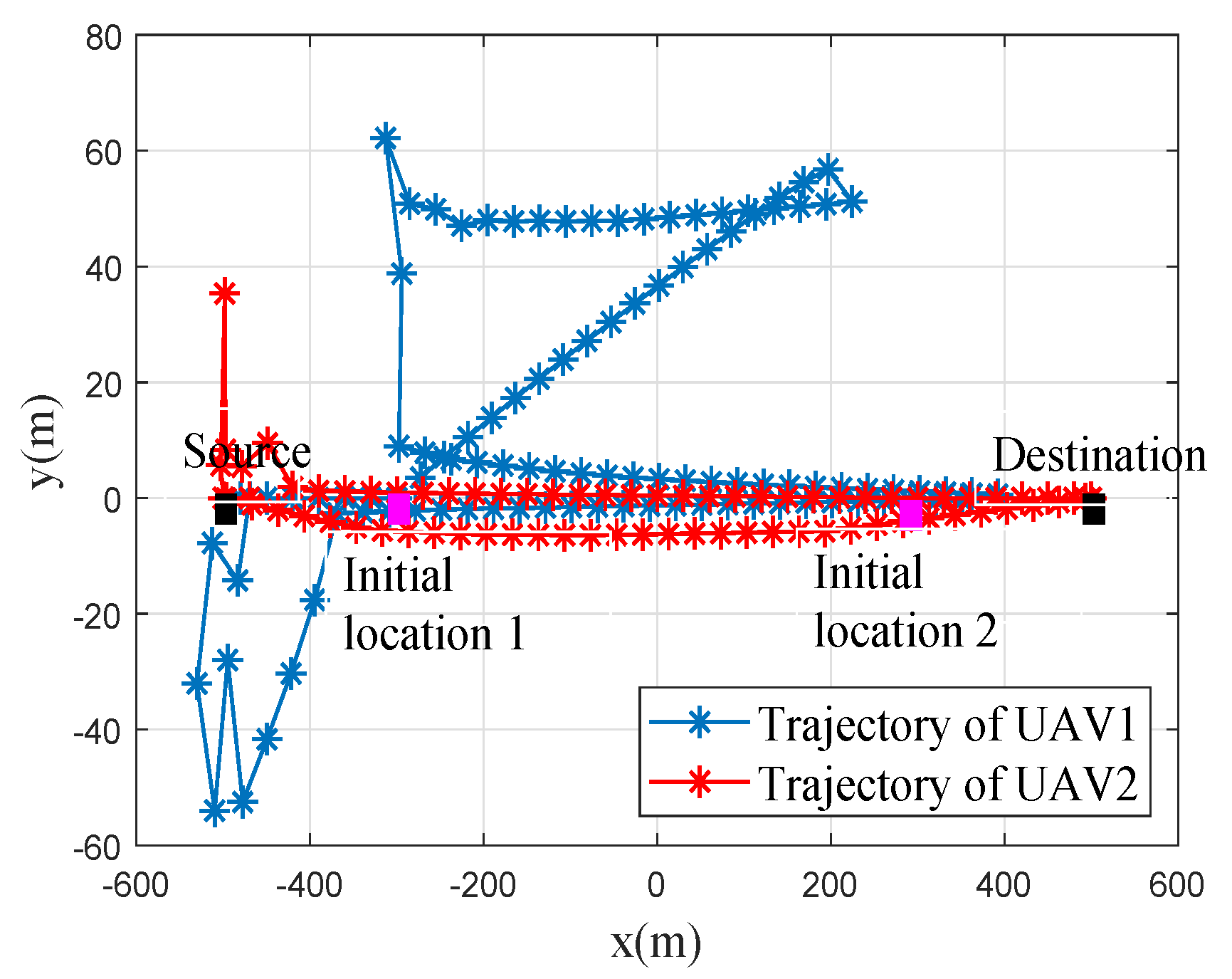
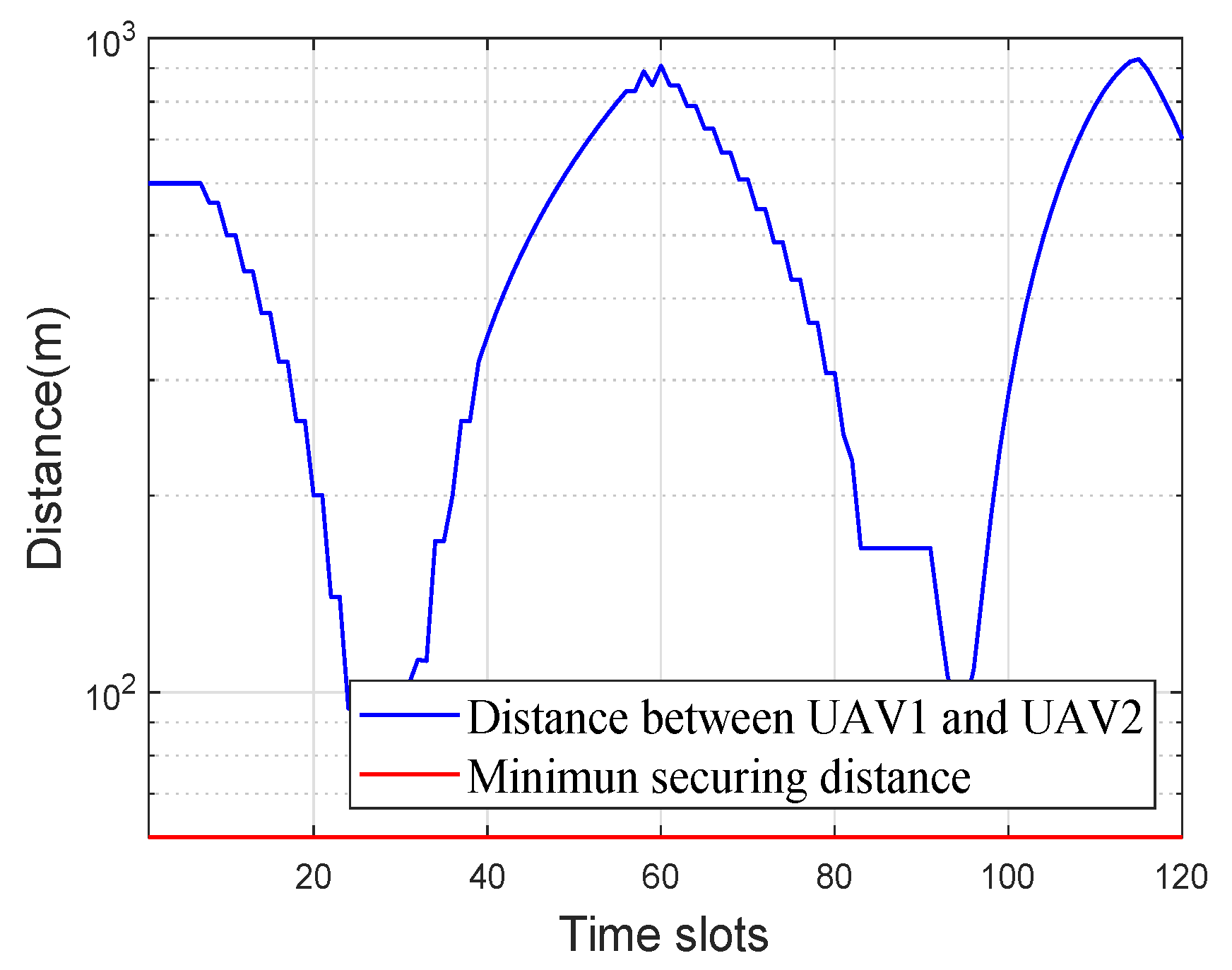
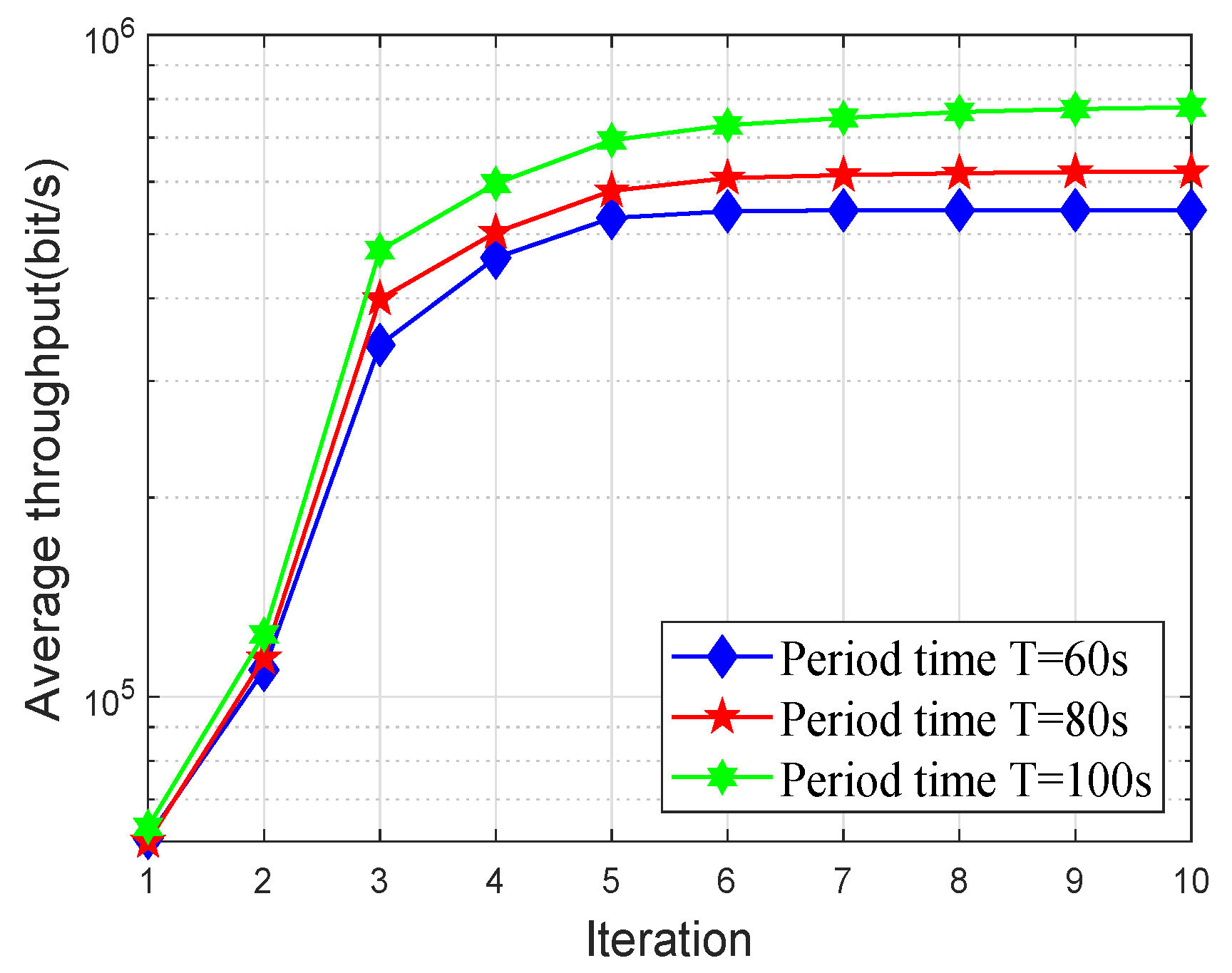
4. Numerical Results
- No optimization: According to the CSI and buffer state, the system decided which UAV stored the data from the source and which UAV served the destination. The transmit power of UAVs W. A circular flight trajectory with radius of m and the center of the flight trajectory above the middle of S and D were considered.
- Only the relay selection and transmit power optimized: For a given trajectory, we only optimized the relay selection and transmit power via the proposed algorithm.
- Only the trajectory optimized: For given relay selection and transmit power, we only optimized the trajectories via the proposed algorithm.
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Lyu, J.; Zeng, Y.; Zhang, R.; Lim, T.J. Placement Optimization of UAV-Mounted Mobile Base Stations. IEEE Commun. Lett. 2016, 21, 604–607. [Google Scholar] [CrossRef]
- Zeng, Y.; Zhang, R.; Lim, T.J. Throughput maximization for UAV-enabled mobile relaying systems. IEEE Trans. Commun. 2016, 64, 4983–4996. [Google Scholar] [CrossRef]
- Gupta, L.; Jain, R.; Vaszkun, G. Survey of important issues in UAV communication networks. IEEE Commun. Surv. Tutor. 2016, 18, 1123–1152. [Google Scholar] [CrossRef]
- Chen, M.C.; Pai, H.H.; Kung, H.T.; Dario, V. Maximizing throughput of UAV-relaying networks with the load-carry-and-deliver paradigm. In Proceedings of the IEEE Wireless Communications Networking Conference (WCNC), Kowloon, China, 11–15 March 2007; pp. 4417–4424. [Google Scholar]
- Zeng, Y.; Zhang, R.; Lim, T.J. Energy Minimization for Wireless Communication with Rotary-Wing UAV. IEEE Trans. Wirel. Commun. 2019, 18, 2329–2345. [Google Scholar] [CrossRef]
- Zhang, G.; Yan, H.; Zeng, Y.; Cui, M.; Liu, Y. Trajectory optimization and power allocation for multi-hop UAV relaying communications. IEEE Access 2018, 6, 48566–48576. [Google Scholar] [CrossRef]
- Nosratinia, A.; Hunter, T.E.; Hedayat, A. Cooperative communication in wireless networks. IEEE Commun. Surv. Tutor. 2014, 42, 74–80. [Google Scholar] [CrossRef]
- Nomikos, N.; Charalambous, T.; Vouyioukas, D.; Wichman, R.; Karagiannidis, G.K. Power Adaptation in Buffer-Aided Full-Duplex Relay Networks With Statistical CSI. IEEE Trans. Veh. Technol. 2018, 67, 7846–7850. [Google Scholar] [CrossRef]
- Mohammadmahdi, M.; Fernando, R.; Kwangcheng, C.; Sofie, P. Ultra reliable UAV communication using altitude and cooperation diversity. IEEE Trans. Commun. 2017, 66, 330–344. [Google Scholar]
- Li, Y.; Yang, D.; Xu, Y.; Xiao, L.; Chen, H. Throughput Maximization for UAV-Enabled Relaying in Wireless Powered Communication Networks. Sensors 2019, 19, 2989. [Google Scholar] [CrossRef]
- Li, A.; Wu, Q.; Zhang, R. UAV-enabled cooperative jamming for improving secrecy of ground wiretap channel. IEEE Wirel. Commun. Lett. 2018, 8, 181–184. [Google Scholar] [CrossRef]
- Hoon, L.; Subin, E.; Junhee, P.; Inkyu, L. UAV aided secure communications with cooperative jamming. IEEE Trans. Veh. Technol. 2018, 67, 9385–9392. [Google Scholar]
- Zhong, C.; Yao, J.; Xu, J. Secure UAV communication with cooperative jamming and trajectory control. IEEE Commun. Lett. 2018, 23, 286–289. [Google Scholar] [CrossRef]
- Wang, Q.; Chen, Z.; Mei, W.; Fang, J. Improving physical layer security using UAV-enabled mobile relaying. IEEE Wirel. Commun. Lett. 2017, 6, 310–313. [Google Scholar] [CrossRef]
- Shen, L.; Wang, N.; Ji, X.; Mu, X.; Cai, L. Iterative Trajectory Optimization for Physical-Layer Secure Buffer-Aided UAV Mobile Relaying. Sensors 2019, 19, 3442. [Google Scholar] [CrossRef] [PubMed]
- Juhyung, L.; Kihong, P.; Mohamedslim, A.; Youngchai, K. On the Throughput of Mixed FSO/RF UAV-Enabled Mobile Relaying Systems with a Buffer Constraint. In Proceedings of the IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019. [Google Scholar]
- Jaroslav, H.; Pavel, P. Elevation Dependent Shadowing Model for Mobile Communications via High Altitude Platforms in Built-Up Areas. IEEE Trans. Antennas Propag. 2008, 56, 1078–1084. [Google Scholar]
- Liu, L.; Zhang, S.; Zhang, R. CoMP in the Sky: UAV Placement and Movement Optimization for Multi-User Communications. IEEE Trans. Commun. 2019, 18, 3192–3207. [Google Scholar] [CrossRef]
- You, C.; Zhang, R. 3D Trajectory Optimization in Rician Fading for UAV-Enabled Data Harvesting. IEEE Trans. Wirel. Commun. 2019, 6, 74648–74659. [Google Scholar] [CrossRef]
- Hong, M.; Razaviyayn, M.; Luo, Z.; Pang, J. A Unified Algorithmic Framework for Block-Structured Optimization Involving Big Data: With applications in machine learning and signal processing. IEEE Signal Process. Mag. 2015, 33, 57–77. [Google Scholar] [CrossRef]
- Khuwaja, A.; Chen, Y.; Zhao, N.; Alouini, M.S.; Dobbins, P. A survey of channel modeling for UAV communications. IEEE Commun. Surv. Tutor. 2018, 20, 280–2821. [Google Scholar] [CrossRef]
- Xu, Y.; Xiao, L.; Yang, D.; Wu, Q.; Cuthbert, L. Throughput Maximization in Multi-UAV Enabled Communication Systems with Difference Consideration. IEEE Access 2018, 6, 55291–55301. [Google Scholar] [CrossRef]
- Boyd, S.; Vandenberghe, L. Convex Optimization; Cambridge University Press: Cambridge, UK, 2004. [Google Scholar]
- Grant, M.; Boyd, S. CVX: MATLAB Software for Disciplined Convex Programming. 2016. Available online: http://cvxr.com/cvx (accessed on 3 November 2019).
- Zhang, G.; Wu, Q.; Cui, M.; Zhang, R. Securing UAV Communications via Joint Trajectory and Power Control. IEEE Trans. Wirel. Commun. 2019, 18, 1376–1389. [Google Scholar] [CrossRef]
- Wu, Q.; Zeng, Y.; Zhang, R. Joint trajectory and communication design for multi-UAV enabled wireless networks. IEEE Trans. Wirel. Commun. 2018, 17, 2109–2121. [Google Scholar] [CrossRef]
- Wang, H.; Ren, G.; Chen, J.; Ding, G.; Yang, Y. Unmanned aerial vehicle aided communications: Joint transmit power and trajectory optimization. IEEE Wirel. Commun. Lett. 2018, 7, 522–525. [Google Scholar] [CrossRef]
- Wang, H.; Wang, J.; Ding, G.; Chen, J.; Li, Y.; Han, Z. Spectrum sharing planning for full-duplex UAV relaying systems with underlaid D2D communications. IEEE J. Sel. Areas Commun. 2018, 36, 1986–1999. [Google Scholar] [CrossRef]

© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cao, D.; Yang, W.; Xu, G. Joint Trajectory and Communication Design for Buffer-Aided Multi-UAV Relaying Networks. Appl. Sci. 2019, 9, 5524. https://doi.org/10.3390/app9245524
Cao D, Yang W, Xu G. Joint Trajectory and Communication Design for Buffer-Aided Multi-UAV Relaying Networks. Applied Sciences. 2019; 9(24):5524. https://doi.org/10.3390/app9245524
Chicago/Turabian StyleCao, Dongju, Wendong Yang, and Gangyi Xu. 2019. "Joint Trajectory and Communication Design for Buffer-Aided Multi-UAV Relaying Networks" Applied Sciences 9, no. 24: 5524. https://doi.org/10.3390/app9245524
APA StyleCao, D., Yang, W., & Xu, G. (2019). Joint Trajectory and Communication Design for Buffer-Aided Multi-UAV Relaying Networks. Applied Sciences, 9(24), 5524. https://doi.org/10.3390/app9245524




