A Cloud Image Data Protection Algorithm with Multilevel Encryption Scheme and Automated- Selection Mechanism
Abstract
:1. Introduction
2. Materials and Methods
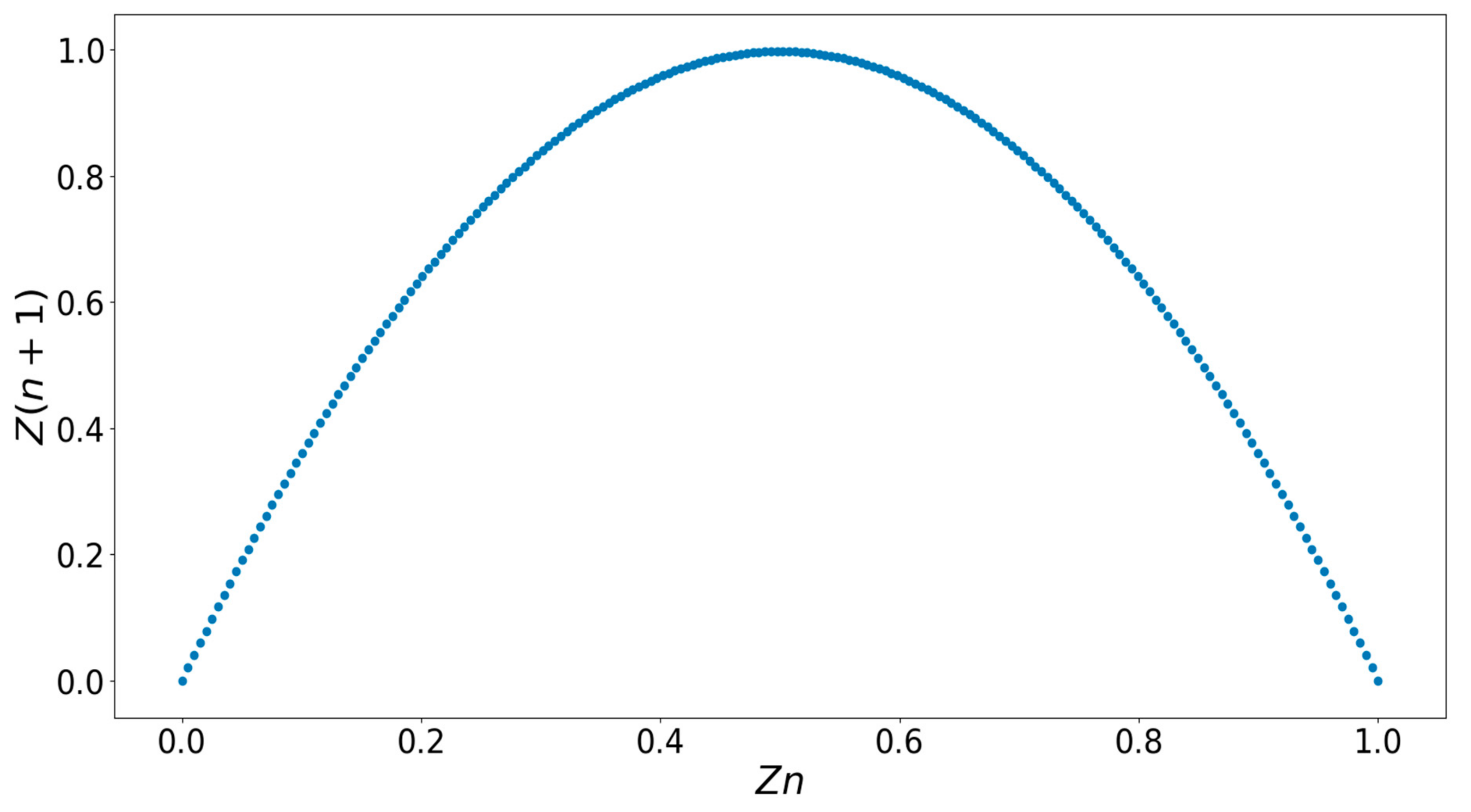
- (1)
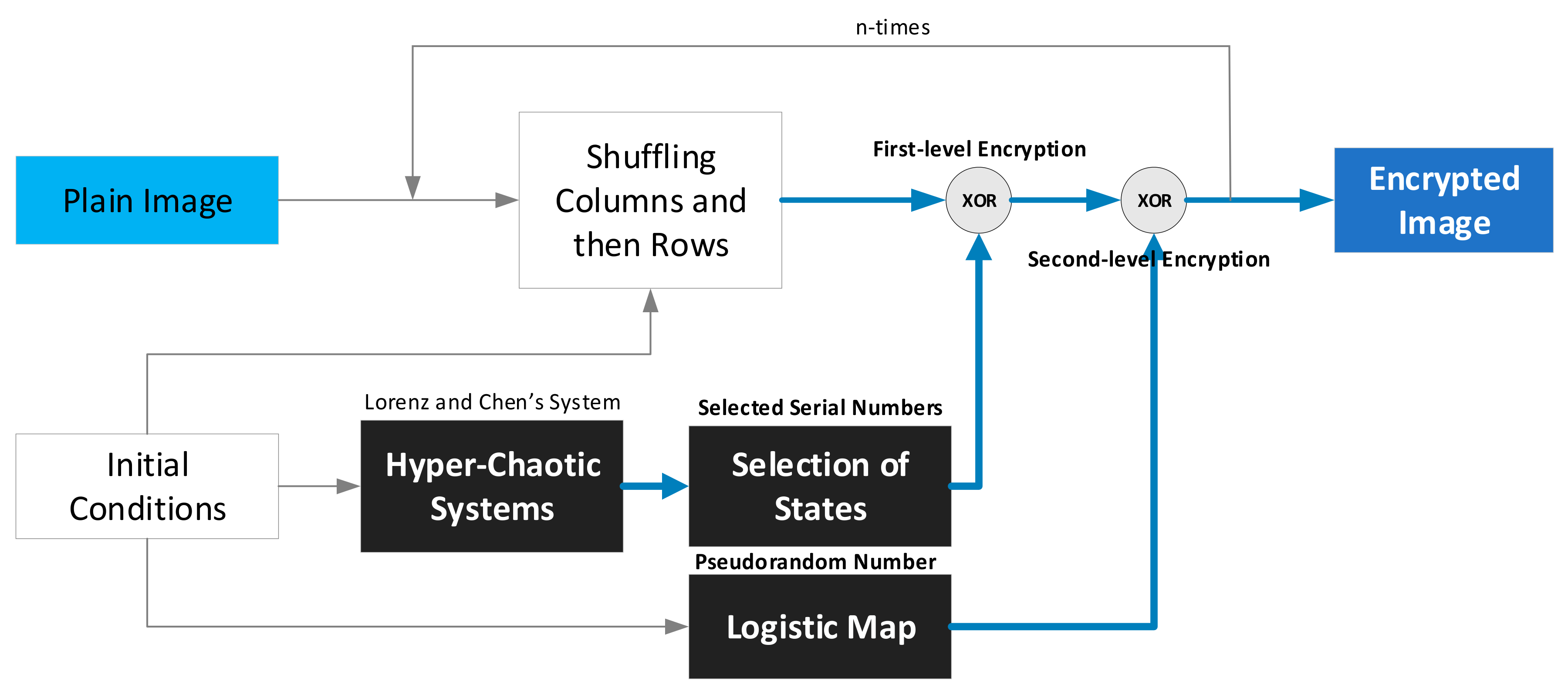
- In the confusion process, an appropriate slide window size is selected (M × N), which divides the original plain image into several subplain images. After this step, each subplain image can be handled through the confusion and diffusion stages until the whole plain image has been encrypted. Therefore, the first process is the confusion stage, Sub-section where a moving-window shuffling process at the bit level is developed mainly to destroy the correlations of adjacent pixels within the window size.
- (2)
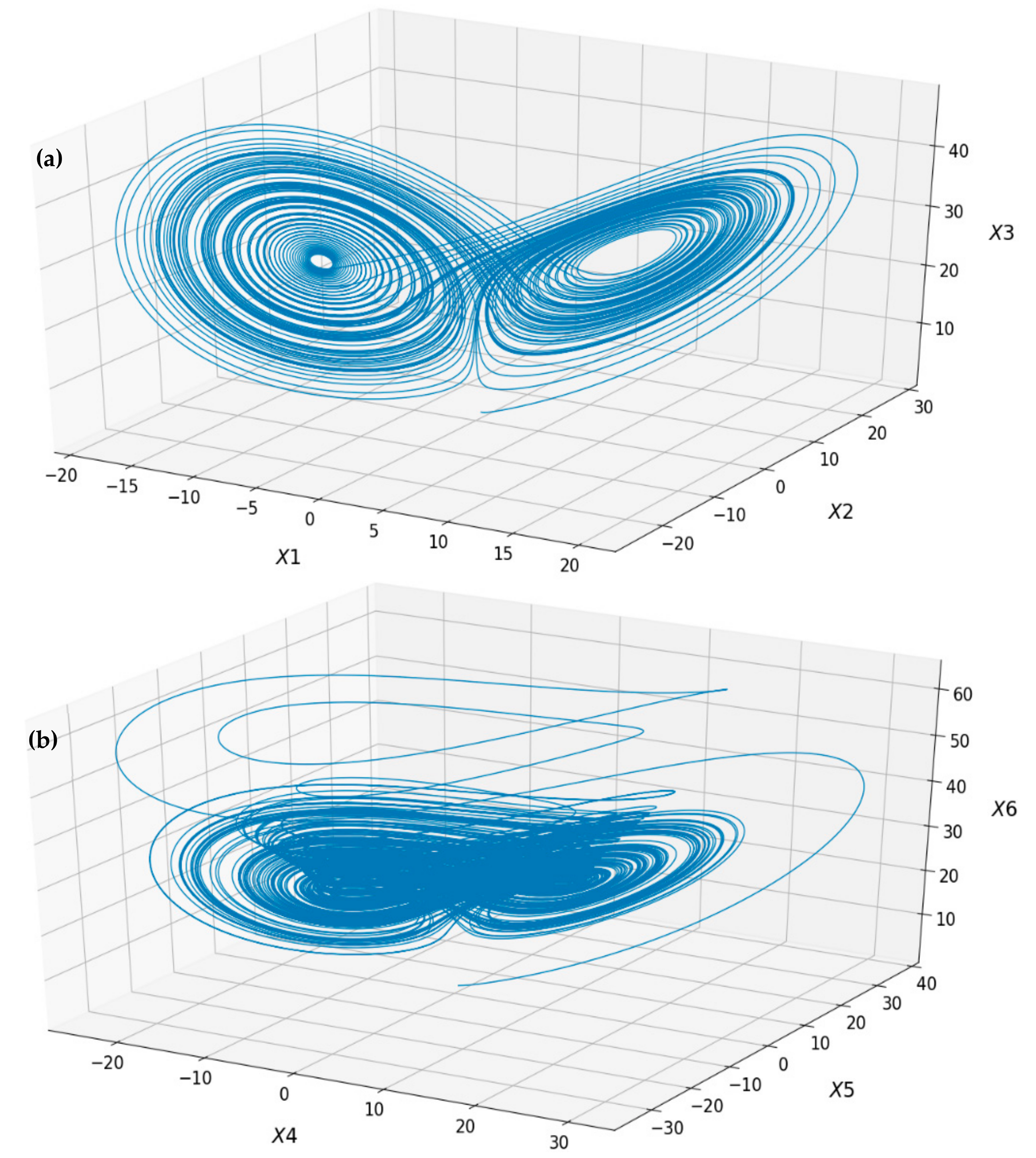
- The second stageSub-section, is the diffusion stage. It uses the same window size as the one assigned in the Sub-section where a multilevel encryption process is administered. Two hyperchaotic systems and a logistic map are applied to cipher the image content twice for more security.
2.1. Confusion Stage—Moving-Window Shuffling Process
- (1)
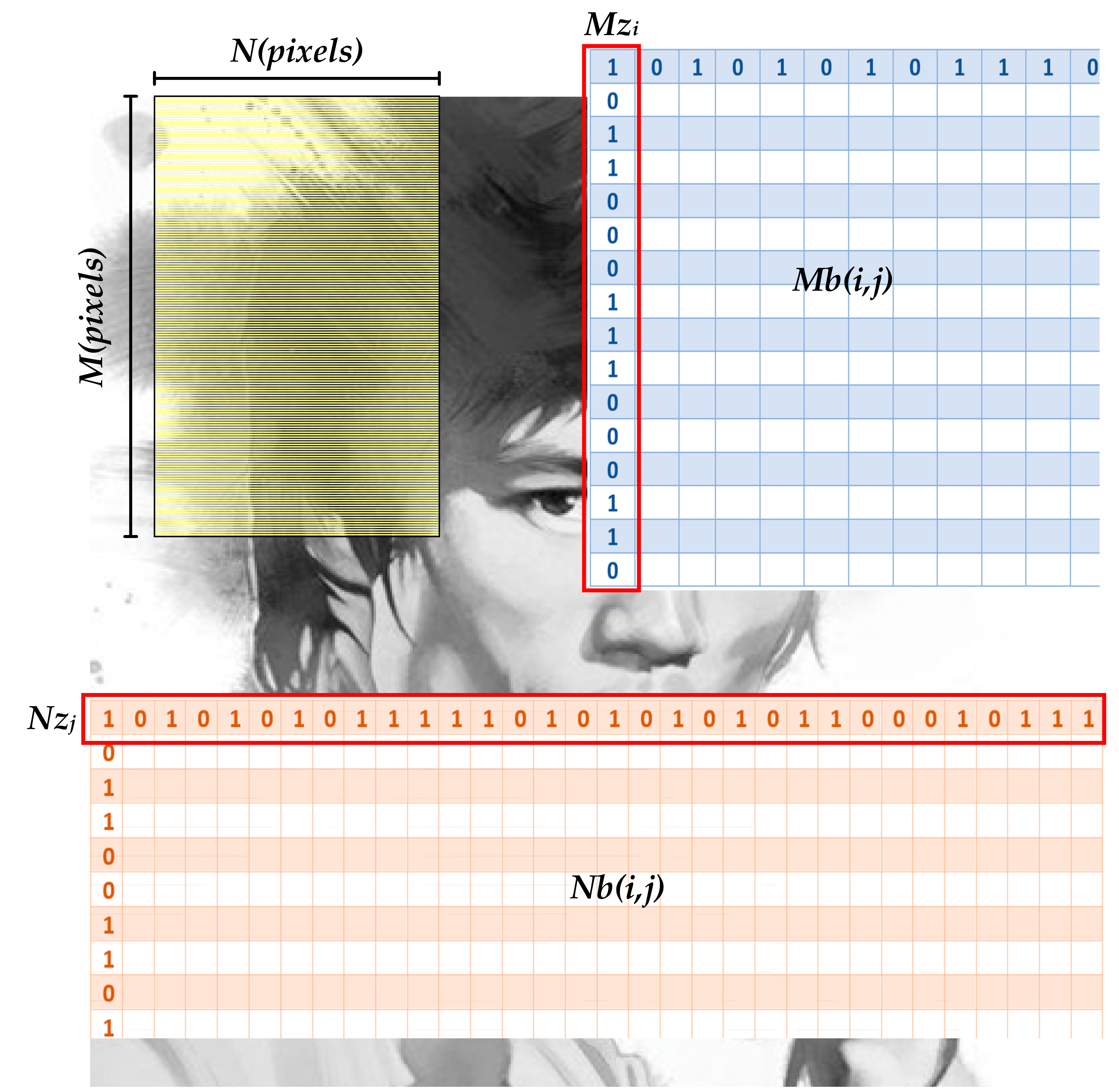
- For the shuffling process in the row direction, Equation (2) was applied to further convert the state value of the first logistic map in Equation (1) to a new position in each iteration:where zn is the state of the logistic map; Mzi(j) ϵ [1, M] is the new position for each binary number; and j = 1, 2, …, M describes the numbers of elements in each row direction. Mzi is a row vector representing the new position vector where i = 1, 2, …, N × 8 refers to the total number of row vectors. As a result, this repetitive process generates a new position matrix Mb(i,j), which is described in Equation (3). Following the new position matrix Mb to operate the shuffling process in the row direction, a completely new subimage at the bit level can be obtained. The complete flowchart is given in Figure 4.
- (2)
- For the shuffling process in the column direction, Equation (4) was applied to further convert the state value of the first logistic map in Equation (1) to a new column position:where Nzj(i) ϵ [1, N × 8] is the new position for each binary number and i = 1, 2, …, N × 8 denotes the number of elements in each column direction. Nzj is a column vector representing the new position vector and j = 1, 2, …, M refers to the total number of column vectors. As a consequence, this repetitive process generates a new position matrix, Nb(i,j), which is described in Equation (5). Following the new position matrix Nb, to further finish the shuffling process in the column direction, a completely new bit-level subimage is gained.
2.2. Diffusion Stage—Multilevel Encryption Scheme
2.3. Decryption Process
3. Experimental Results and Discussion
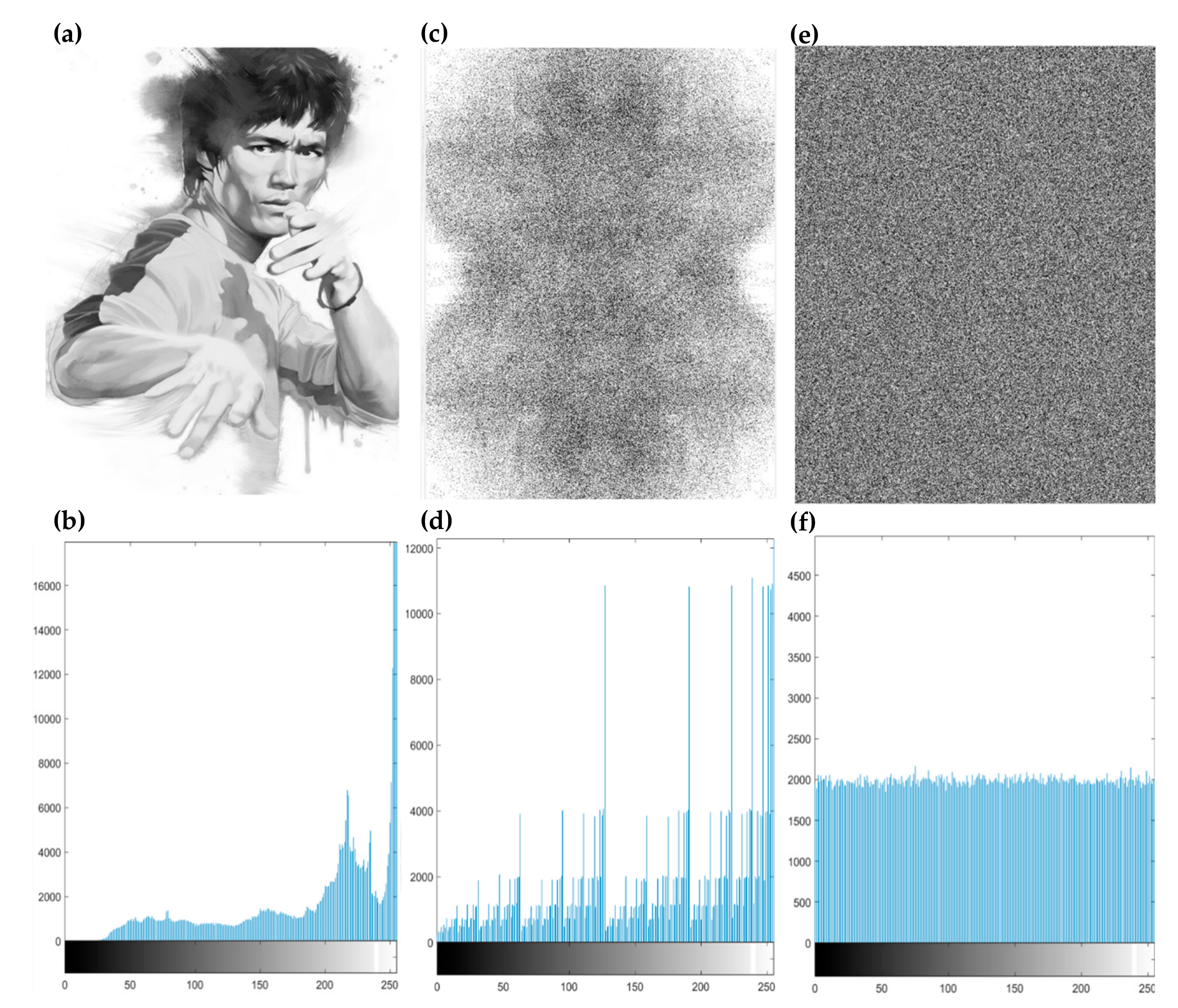
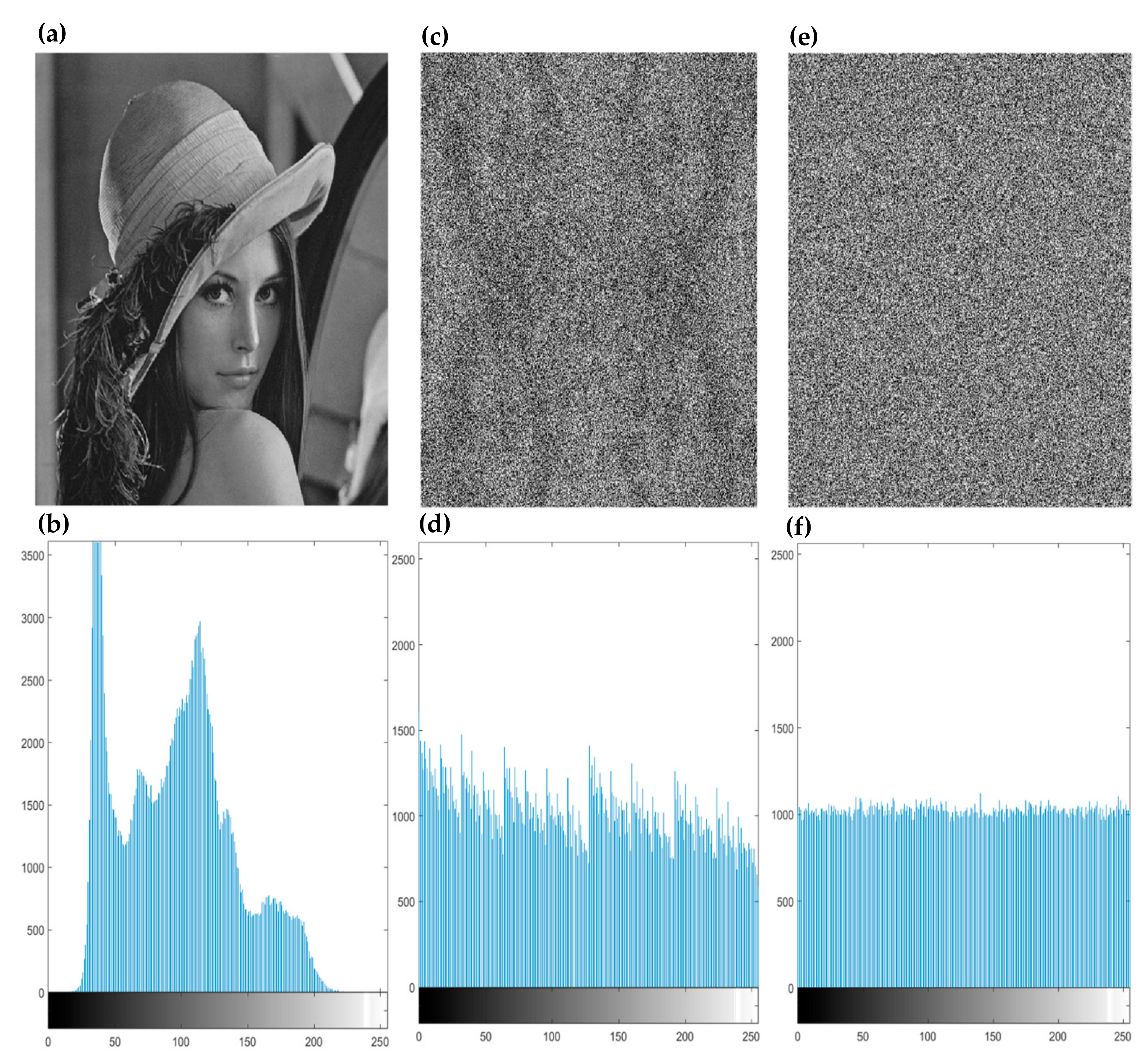
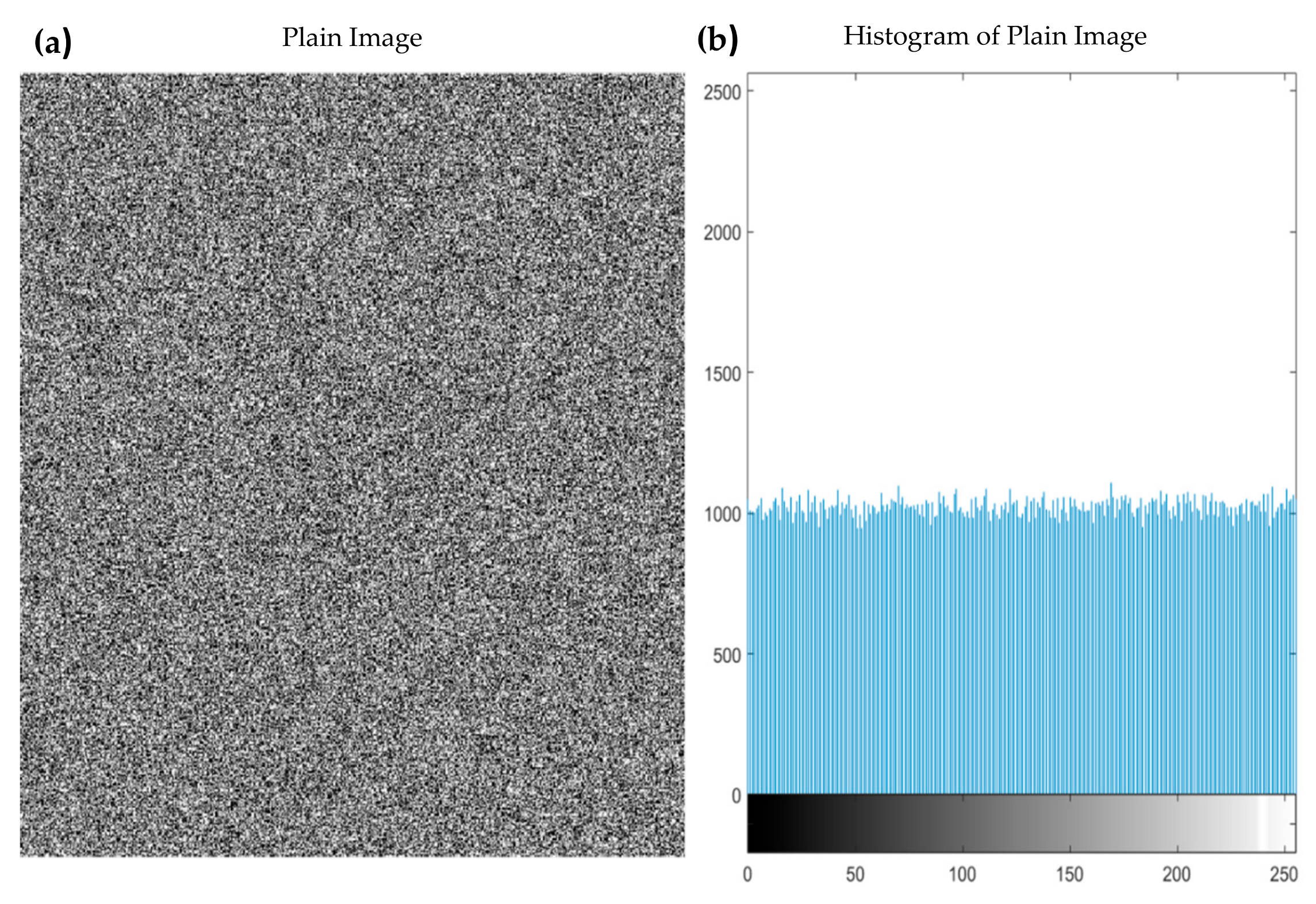
3.1. Experimental Analysis
3.2. Security Analysis
3.2.1. Key Space Analysis
3.2.2. Key-Sensitivity Test
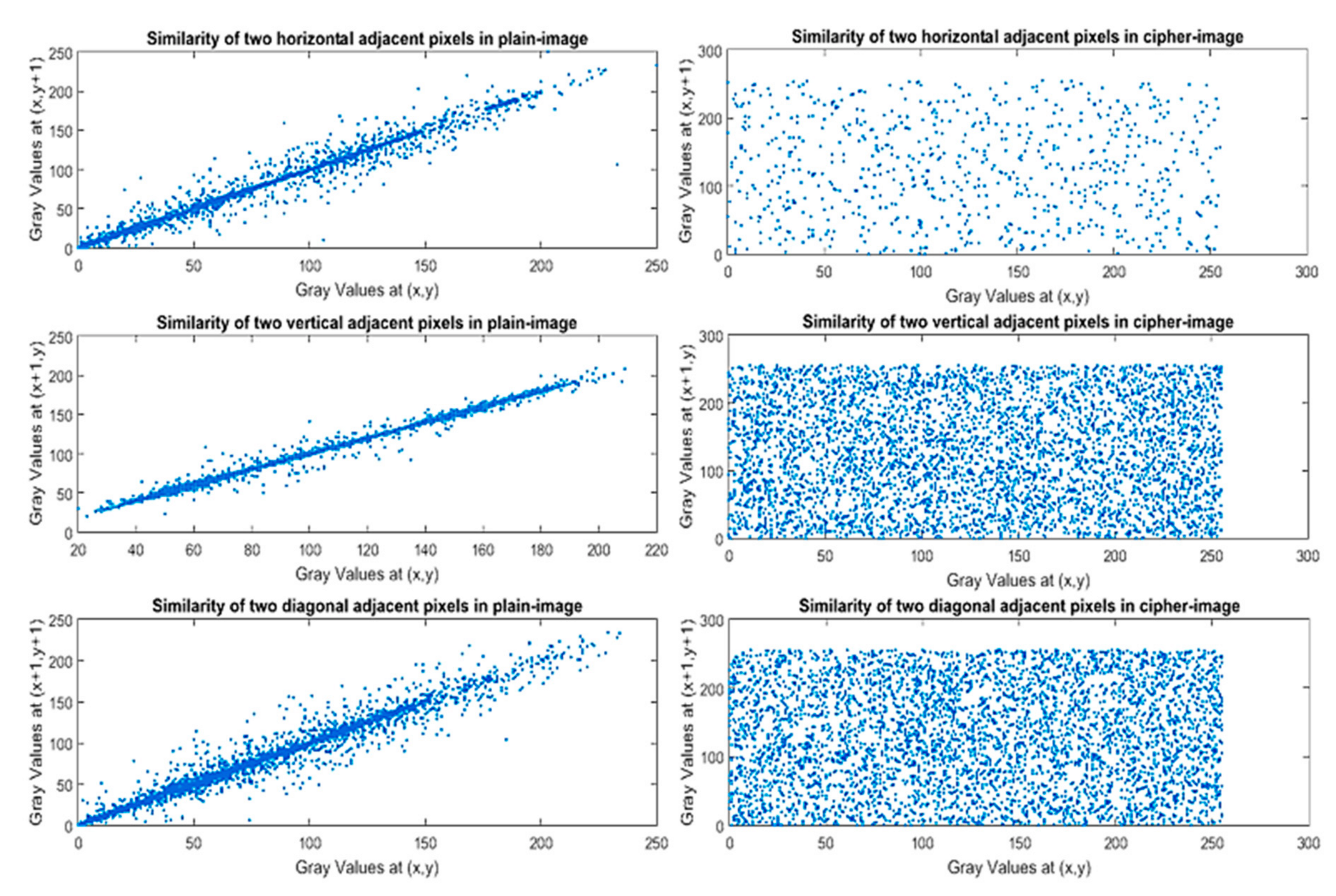
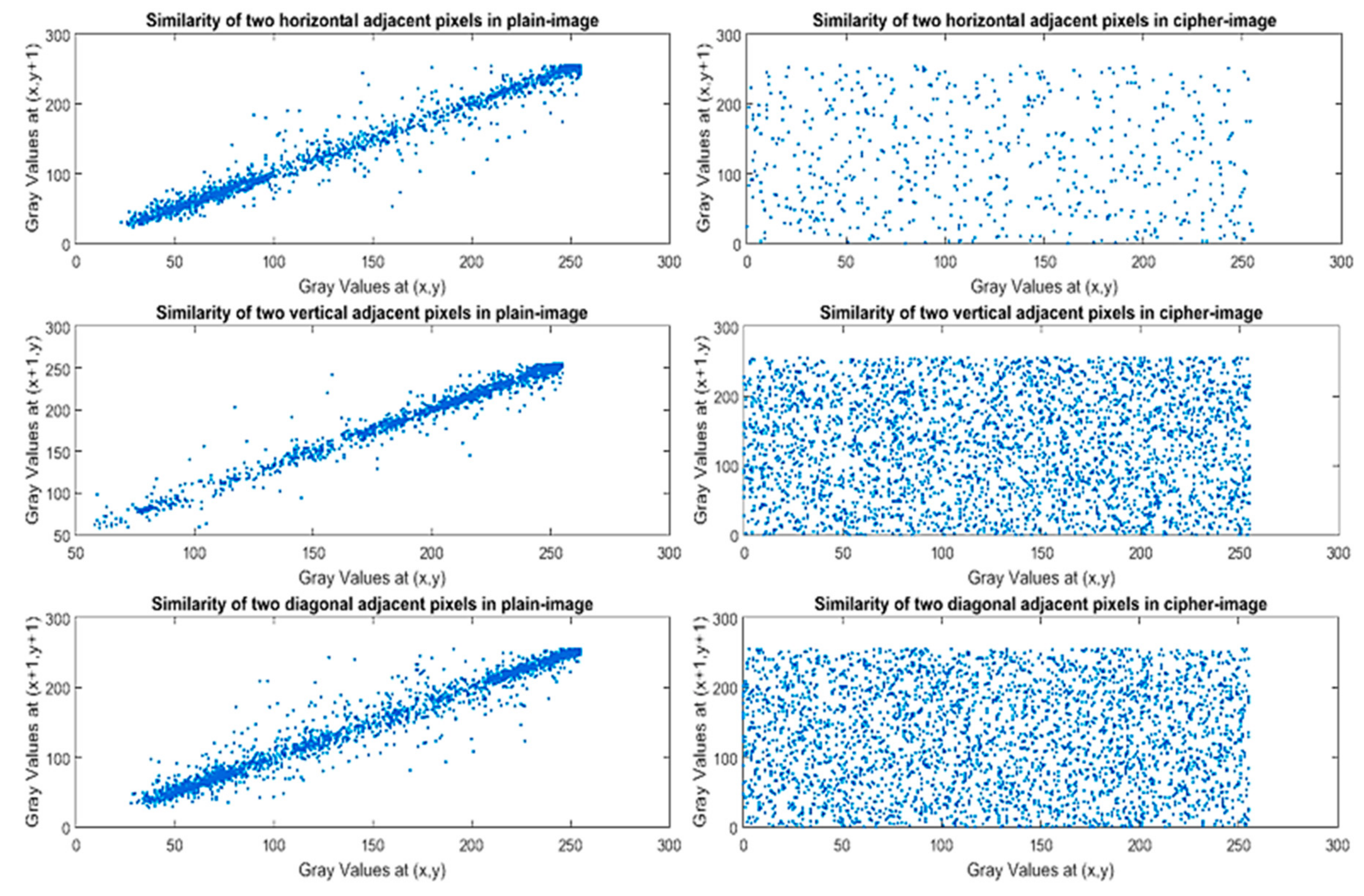
3.2.3. Correlation Analysis of Two Adjacent Pixels
3.2.4. Information Entropy Analysis
4. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Li, X.; Meng, X.; Yang, X.; Yin, Y.; Wang, Y.; Peng, X.; He, W.; Dong, G.; Chen, H. Multiple-image encryption based on compressive ghost imaging and coordinate sampling. IEEE Photonics J. 2016, 8, 1–11. [Google Scholar] [CrossRef]
- Chen, W. Optical multiple-image encryption using three-dimensional space. IEEE Photonics J. 2016, 8, 1–8. [Google Scholar] [CrossRef]
- Yao, S.; Chen, L.; Chang, G.; He, B. A new optical encryption system for image transformation. Opt. Laser Technol. 2017, 97, 234–241. [Google Scholar] [CrossRef]
- Liu, J.; Bai, T.; Shen, X.; Dou, S.; Lin, C.; Cai, J. Parallel encryption for multi-channel images based on an optical joint transform correlator. Opt. Commun. 2017, 396, 174–184. [Google Scholar] [CrossRef]
- Dalhoum, A.; Latif, A.; Mahafzah, B.A.; Awwad, A.A.; Aldhamari, I.; Ortega, A.; Alfonseca, M. Digital image scrambling using 2D cellular automata. IEEE Multimed. 2012, 19, 28–36. [Google Scholar] [CrossRef]
- Niyat, A.Y.; Hei, R.M.H.; Jahan, M.V. Chaos-based image encryption using a hybrid cellular automata and a DNA sequence. In Proceedings of the 2015 International Congress on Technology, Communication and Knowledge (ICTCK) 2015, Mashhad, Iran, 11–12 November 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 247–252. [Google Scholar]
- Wei, R.; Li, X.; Wang, Q.-H. Double color image encryption scheme based on off-axis holography and maximum length cellular automata. Optik 2017, 145, 407–417. [Google Scholar] [CrossRef]
- Enayatifar, R.; Abdullah, A.H.; Isnin, I.F. Chaos-based image encryption using a hybrid genetic algorithm and a DNA sequence. Opt. Lasers Eng. 2014, 56, 83–93. [Google Scholar] [CrossRef]
- Wang, X.-Y.; Zhang, Y.-Q.; Bao, X.-M. A novel chaotic image encryption scheme using DNA sequence operations. Opt. Lasers Eng. 2015, 73, 53–61. [Google Scholar] [CrossRef]
- Al-Mashhadi, H.M.; Abduljaleel, I.Q. Color image encryption using chaotic maps, triangular scrambling, with DNA sequences. In Proceedings of the 2017 International Conference on Current Research in Computer Science and Information Technology (ICCIT) 2017, Slemani, Iraq, 26–27 April 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 93–98. [Google Scholar]
- Liu, H.; Wang, X. Image encryption using DNA complementary rule and chaotic maps. Appl. Soft Comput. 2012, 12, 1457–1466. [Google Scholar] [CrossRef]
- Niu, Y.; Zhang, X.; Han, F. Image encryption algorithm based on hyperchaotic maps and nucleotide sequences database. Comput. Intel. Neurosc. 2017, 2017, 1–9. [Google Scholar] [CrossRef]
- Chen, Y.Y.; Hsia, C.H.; Chi, K.Y.; Chen, B.Y. High-quality and high-capacity data hiding based on absolute moment block truncation coding. J. Internet Technol. 2019, 20, 1–10. [Google Scholar]
- Yun-Peng, Z.; Wei, L.; Shui-Ping, C.; Zheng-Jun, Z.; Xuan, N.; Wei-di, D. Digital image encryption algorithm based on chaos and improved DES. In Proceedings of the 2009 IEEE International Conference on Systems, Man and Cy bernetics 2009, San Antonio, TX, USA, 11–14 October 2009; IEEE: Piscataway, NJ, USA, 2009; pp. 474–479. [Google Scholar]
- Gong-bin, Q.; Qing-feng, J.; Shui-sheng, Q. A new image encryption scheme based on DES algorithm and Chua’s circuit. In Proceedings of the 2009 IEEE International Workshop on Imaging Systems and Techniques 2009, Shenzhen, China, 11–12 May 2009; IEEE: Piscataway, NJ, USA, 2009; pp. 168–172. [Google Scholar]
- Chen, Y.Y.; Hsia, C.H.; Jhong, S.Y.; Lin, H.J. Data hiding method for AMBTC compressed images. J. Ambient Intell. Humanized Comput. 2018, 1–9. [Google Scholar] [CrossRef]
- Zhang, Y. Test and Verification of AES Used for Image Encryption. 3D Res. 2018, 9, 3. [Google Scholar] [CrossRef]
- Dey, S.; Ayyar, S.S.; Subin, S.; Asis, P.A. Sd-ies: An advanced image encryption standard application of different cryptographic modules in a new image encryption system. In Proceedings of the 2013 7th International Conference on Intelligent Systems and Control (ISCO) 2013, Coimbatore, India, 4–5 January 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 285–289. [Google Scholar]
- Zeghid, M.; Machhout, M.; Khriji, L.; Baganne, A.; Tourki, R. A modified AES based algorithm for image encryption. Int. J. Comput. Sci. Eng. 2007, 1, 70–75. [Google Scholar]
- Toughi, S.; Fathi, M.H.; Sekhavat, Y.A. An image encryption scheme based on elliptic curve pseudo random and advanced encryption system. Signal Process. 2017, 141, 217–227. [Google Scholar] [CrossRef]
- Bora, S.; Sen, P.; Pradhan, C. Novel color image encryption technique using Blowfish and Cross Chaos map. In Proceedings of the 2015 International Conference on Communications and Signal Processing (ICCSP) 2015, Melmaruvathur, India, 2–4 April 2015; IEEE: Piscataway, NJ, USA, 2015; Volume 2015, pp. 0879–0883. [Google Scholar]
- Matthews, R. On the derivation of a “chaotic” encryption algorithm. Cryptologia 1989, 13, 29–42. [Google Scholar] [CrossRef]
- Fridrich, J. Symmetric Ciphers Based on Two-Dimensional Chaotic Maps. Int. J. Bifurc. Chaos 1998, 08, 1259–1284. [Google Scholar] [CrossRef]
- Chen, G.; Mao, Y.; Chui, C.K. A symmetric image encryption scheme based on 3D chaotic cat maps. Chaos Solitons Fractals 2004, 21, 749–761. [Google Scholar] [CrossRef]
- Tang, Y.; Wang, Z.; Fang, J.-A. Image encryption using chaotic coupled map lattices with time-varying delays. Commun. Nonlinear Sci. Numer. Simul. 2010, 15, 2456–2468. [Google Scholar] [CrossRef]
- Wang, Y.; Wong, K.-W.; Liao, X.; Chen, G. A new chaos-based fast image encryption algorithm. Appl. Soft Comput. 2011, 11, 514–522. [Google Scholar] [CrossRef]
- Wang, X.; Zhao, J.; Liu, H. A new image encryption algorithm based on chaos. Opt. Commun. 2012, 285, 562–566. [Google Scholar] [CrossRef]
- Seyedzadeh, S.M.; Norouzi, B.; Mosavi, M.R.; Mirzakuchaki, S. A novel color image encryption algorithm based on spatial permutation and quantum chaotic map. Nonlinear Dyn. 2015, 81, 511–529. [Google Scholar] [CrossRef]
- Chen, J.-X.; Zhu, Z.-L.; Fu, C.; Yu, H. A fast image encryption scheme with a novel pixel swapping-based confusion approach. Nonlinear Dyn. 2014, 77, 1191–1207. [Google Scholar] [CrossRef]
- Xiao, D.; Liao, X.; Wei, P. Analysis and improvement of a chaos-based image encryption algorithm. Chaos Solitons Fractals 2009, 40, 2191–2199. [Google Scholar] [CrossRef]
- Norouzi, B.; Mirzakuchaki, S. Breaking a novel image encryption scheme based on an improper fractional order chaotic system. Multimed. Tools Appl. 2015, 76, 1817–1826. [Google Scholar] [CrossRef]
- Wang, X.; Guoxiang, H. Cryptanalysis on a novel image encryption method based on total shuffling scheme. Opt. Commun. 2011, 284, 5804–5807. [Google Scholar] [CrossRef]
- Liu, H.; Wang, X. Color image encryption based on one-time keys and robust chaotic maps. Comput. Math. Appl. 2010, 59, 3320–3327. [Google Scholar] [CrossRef]
- Wang, X.; Teng, L.; Qin, X. A novel colour image encryption algorithm based on chaos. Signal Process. 2012, 92, 1101–1108. [Google Scholar] [CrossRef]
- Zhang, Y.-Q.; Wang, X.-Y. A new image encryption algorithm based on non-adjacent coupled map lattices. Appl. Soft Comput. 2015, 26, 10–20. [Google Scholar] [CrossRef]
- Gao, T.; Chen, Z. A new image encryption algorithm based on hyperchaos. Phys. Lett. A 2008, 372, 394–400. [Google Scholar] [CrossRef]
- Rhouma, R.; Belghith, S. Cryptanalysis of a new image encryption algorithm based on hyperchaos. Phys. Lett. A 2008, 372, 5973–5978. [Google Scholar] [CrossRef]
- Zhang, Q.; Guo, L.; Wei, X. A novel image fusion encryption algorithm based on DNA sequence operation and hyperchaotic system. Optik Int. J. Light Electron. Opt. 2013, 124, 3596–3600. [Google Scholar] [CrossRef]
- Wang, X.; Zhang, H.-L. A novel image encryption algorithm based on genetic recombination and hyperchaotic systems. Nonlinear Dyn. 2016, 83, 333–346. [Google Scholar] [CrossRef]
- Wang, H.Y.; Lin, H.J.; Gao, X.Y.; Cheng, W.H.; Chen, Y.Y. Reversible AMBTC-based data hiding with security improvement by chaotic encryption. IEEE Access 2019, 7, 38337–38347. [Google Scholar] [CrossRef]
- Huang, X.; Ye, G. An image encryption algorithm based on hyperchaos and dna sequence. Multimed. Tools Appl. 2014, 72, 57–70. [Google Scholar]
- Wang, X.; Qian, W. A fast image encryption algorithm based on only blocks in cipher text. Chin. Phys. B 2014, 23, 030503. [Google Scholar] [CrossRef]
- Li, Y.; Wang, C.; Chen, H. A hyperchaos-based image encryption algorithm using pixel-level permutation and bit-level permutation. Opt. Lasers Eng. 2017, 90, 238–246. [Google Scholar] [CrossRef]
- Wang, X.; Liu, L.; Zhang, Y. A novel chaotic block image encryption algorithm based on dynamic random growth technique. Opt. Lasers Eng. 2015, 66, 10–18. [Google Scholar] [CrossRef]



| Serial Number | Combination of States | Serial Number | Combination of States |
|---|---|---|---|
| 0 | 8 | ||
| 1 | 9 | ||
| 2 | 10 | ||
| 3 | 11 | ||
| 4 | 12 | ||
| 5 | 13 | ||
| 6 | 14 | ||
| 7 |
| x1= 0.00001661846822 | x2= 0.00001810482068 |
| x3= 0.00015043192106 | x4= 0.00024400694444 |
| x5= 0.00002680017881 | x6= 0.00001304826999 |
| l0= 0.00000415544568 | y0= 0.00000174644423 |
| x1 = 0.00001661846822 | x1 = 0.00001810482068 |
| x3 = 0.00015043192106 | x4 = 0.00024400694444 |
| x5 = 0.00002680017881 | x6 = 0.0000130482699 |
| l0 = 0.00000415544538 | y0 = 0.00000174644423 |
| Model | Bruce Lee Image (849 × 600) | Lena Image (512 × 512) | ||
|---|---|---|---|---|
| Plain Image | Ciphered Image | Plain Image | Ciphered Image | |
| Horizontal | 0.990870 | −0.012164 | 0.967504 | 0.005335 |
| Vertical | 0.990991 | −0.011759 | 0.973323 | −0.016496 |
| Diagonal | 0.987203 | 0.017524 | 0.958654 | 0.052681 |
| Correlation Coefficient Values | ||
|---|---|---|
| Wonder Woman (2880 × 1800) | Horizontal | 0.025846 |
| Vertical | 0.0166156 | |
| Diagonal | 0.001811 | |
| Lena image (256 × 256) | Horizontal | 0.033227 |
| Vertical | 0.022104 | |
| Diagonal | −0.032824 | |
| [41] | Horizontal | −0.0796392 |
| Vertical | 0.0166156 | |
| Diagonal | 0.0032779 | |
| [42] | Horizontal | 0.0014 |
| Vertical | 0.0171 | |
| Diagonal | 0.0054 | |
| [43] | Horizontal | −0.0015 |
| Vertical | −0.0032 | |
| Diagonal | 0.0008 | |
| [44] | Horizontal | 0.0019064 |
| Vertical | 0.0038175 | |
| Diagonal | −0.0019482 | |
| Bruce Lee Image (849 × 600) | Lena Image (512 × 512) | ||
|---|---|---|---|
| Plain Image | Ciphered Image | Plain Image | Ciphered Image |
| 6.425890 | 7.999634 | 7.235559 | 7.999362 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, S.-Y.; Benalcázar Hernández, M.A.; Tam, L.-M.; Chen, C.-S. A Cloud Image Data Protection Algorithm with Multilevel Encryption Scheme and Automated- Selection Mechanism. Appl. Sci. 2019, 9, 5146. https://doi.org/10.3390/app9235146
Li S-Y, Benalcázar Hernández MA, Tam L-M, Chen C-S. A Cloud Image Data Protection Algorithm with Multilevel Encryption Scheme and Automated- Selection Mechanism. Applied Sciences. 2019; 9(23):5146. https://doi.org/10.3390/app9235146
Chicago/Turabian StyleLi, Shih-Yu, Miguel Angel Benalcázar Hernández, Lap-Mou Tam, and Chin-Sheng Chen. 2019. "A Cloud Image Data Protection Algorithm with Multilevel Encryption Scheme and Automated- Selection Mechanism" Applied Sciences 9, no. 23: 5146. https://doi.org/10.3390/app9235146
APA StyleLi, S.-Y., Benalcázar Hernández, M. A., Tam, L.-M., & Chen, C.-S. (2019). A Cloud Image Data Protection Algorithm with Multilevel Encryption Scheme and Automated- Selection Mechanism. Applied Sciences, 9(23), 5146. https://doi.org/10.3390/app9235146






