Vector Map Random Encryption Algorithm Based on Multi-Scale Simplification and Gaussian Distribution
Abstract
1. Introduction
2. Related Works
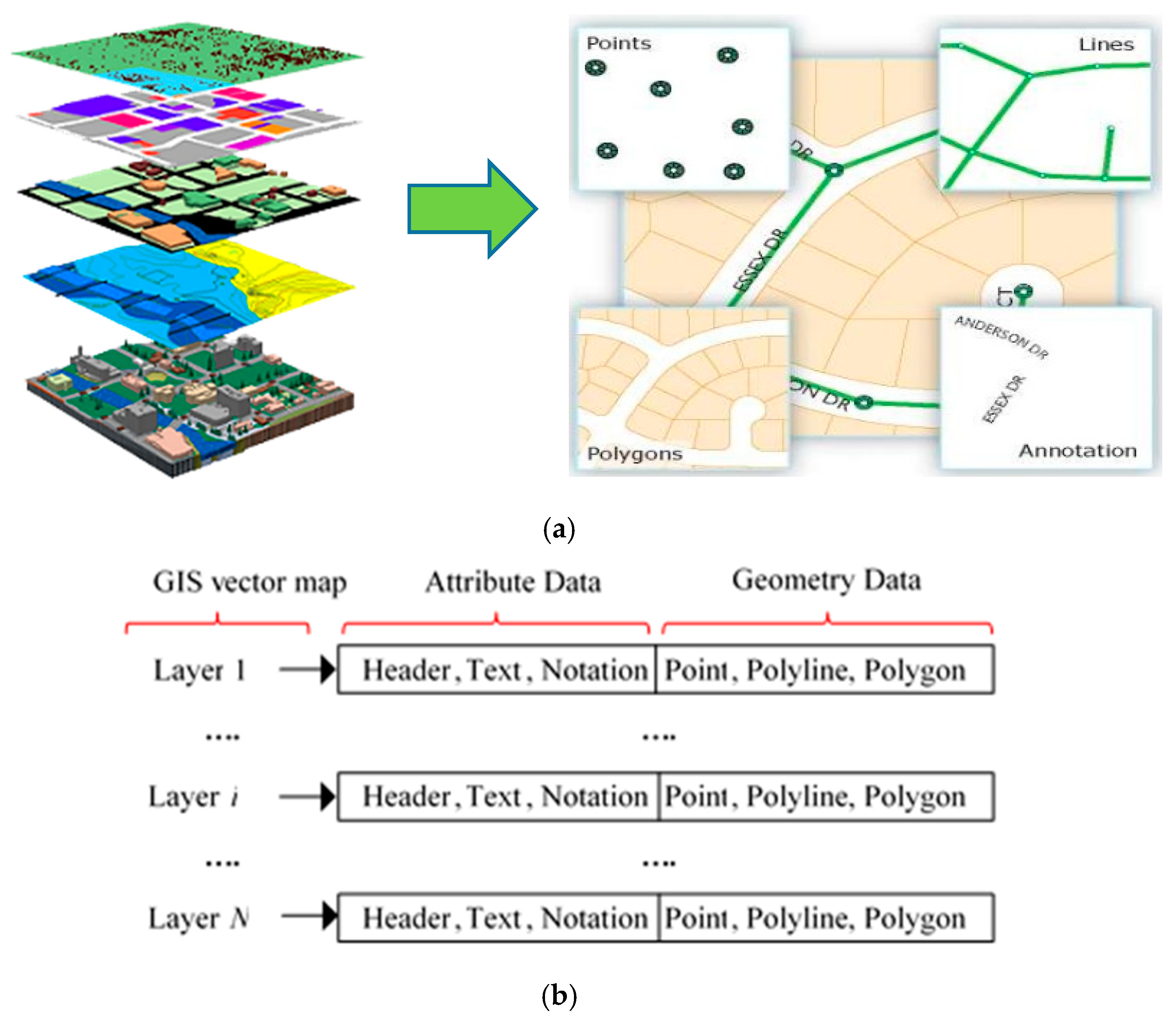
2.1. Vector Map Data Security
2.2. Vector Map Data-Based Encryption
3. The Proposed Method
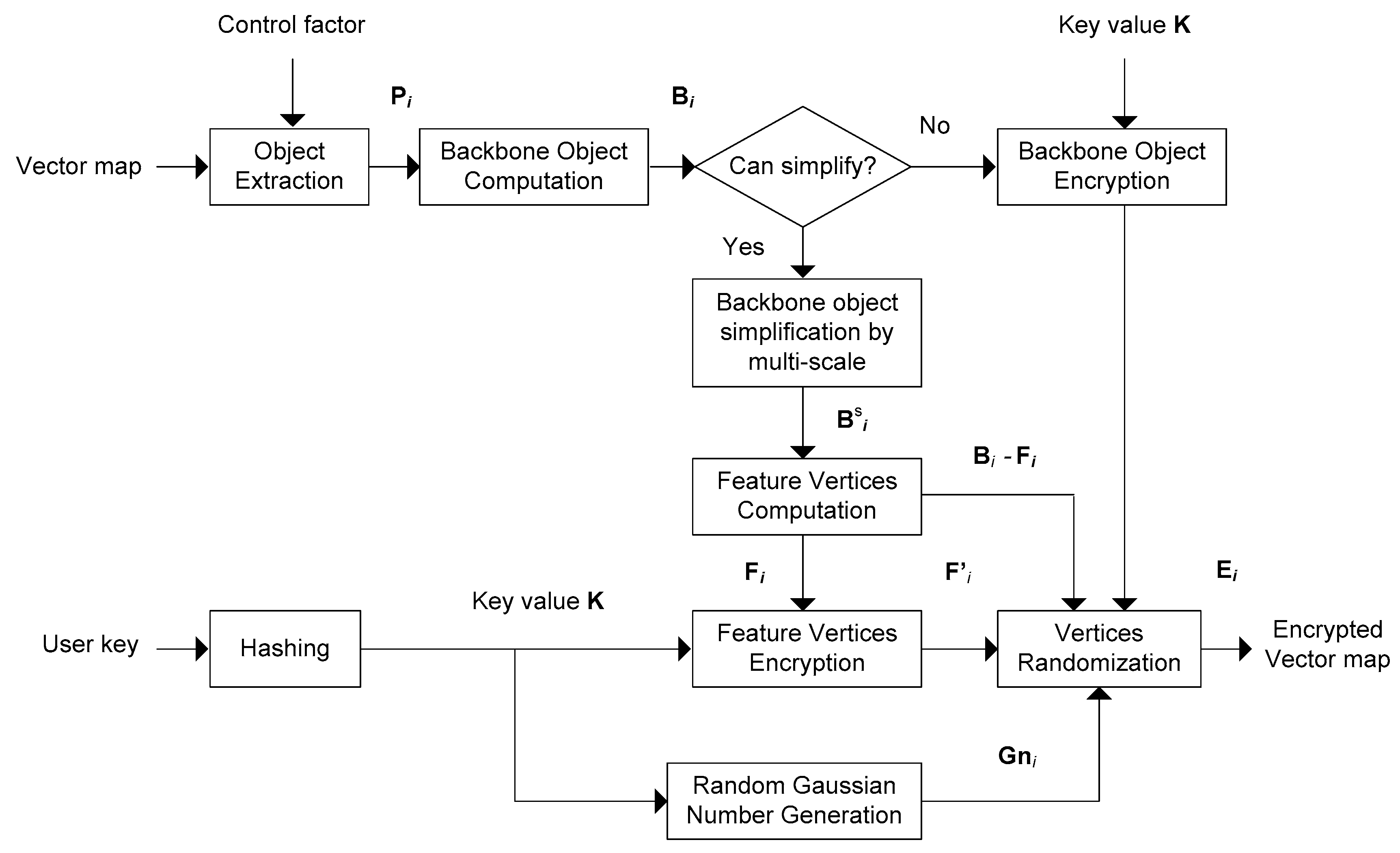
3.1. Overview
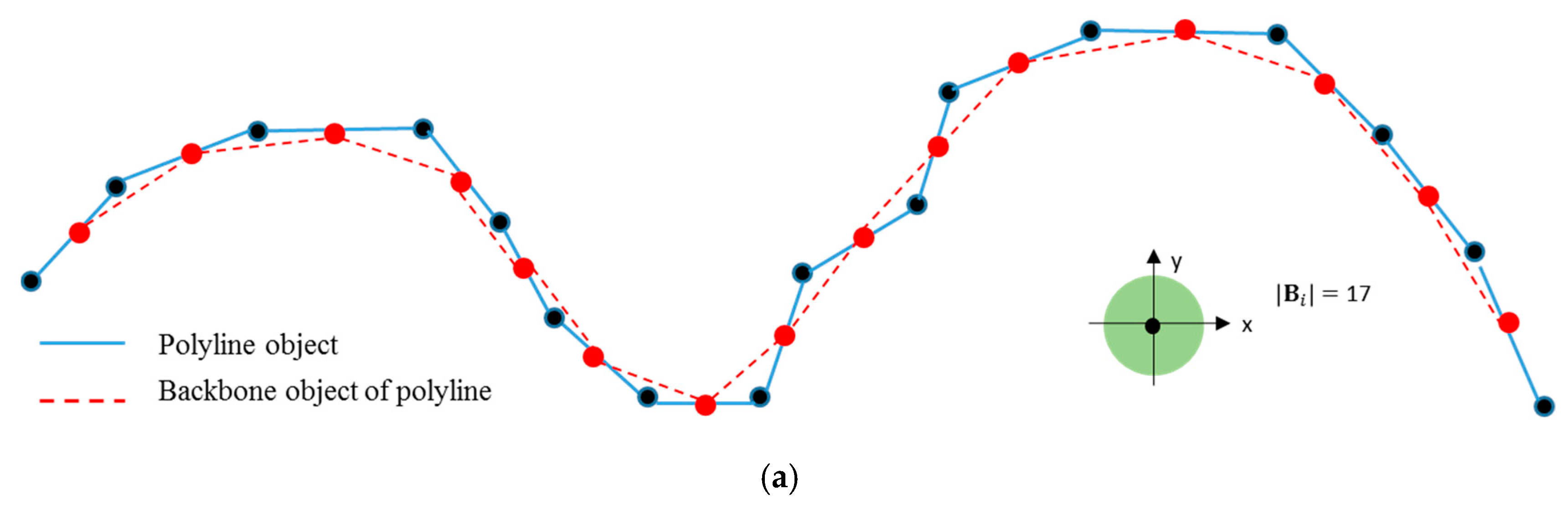
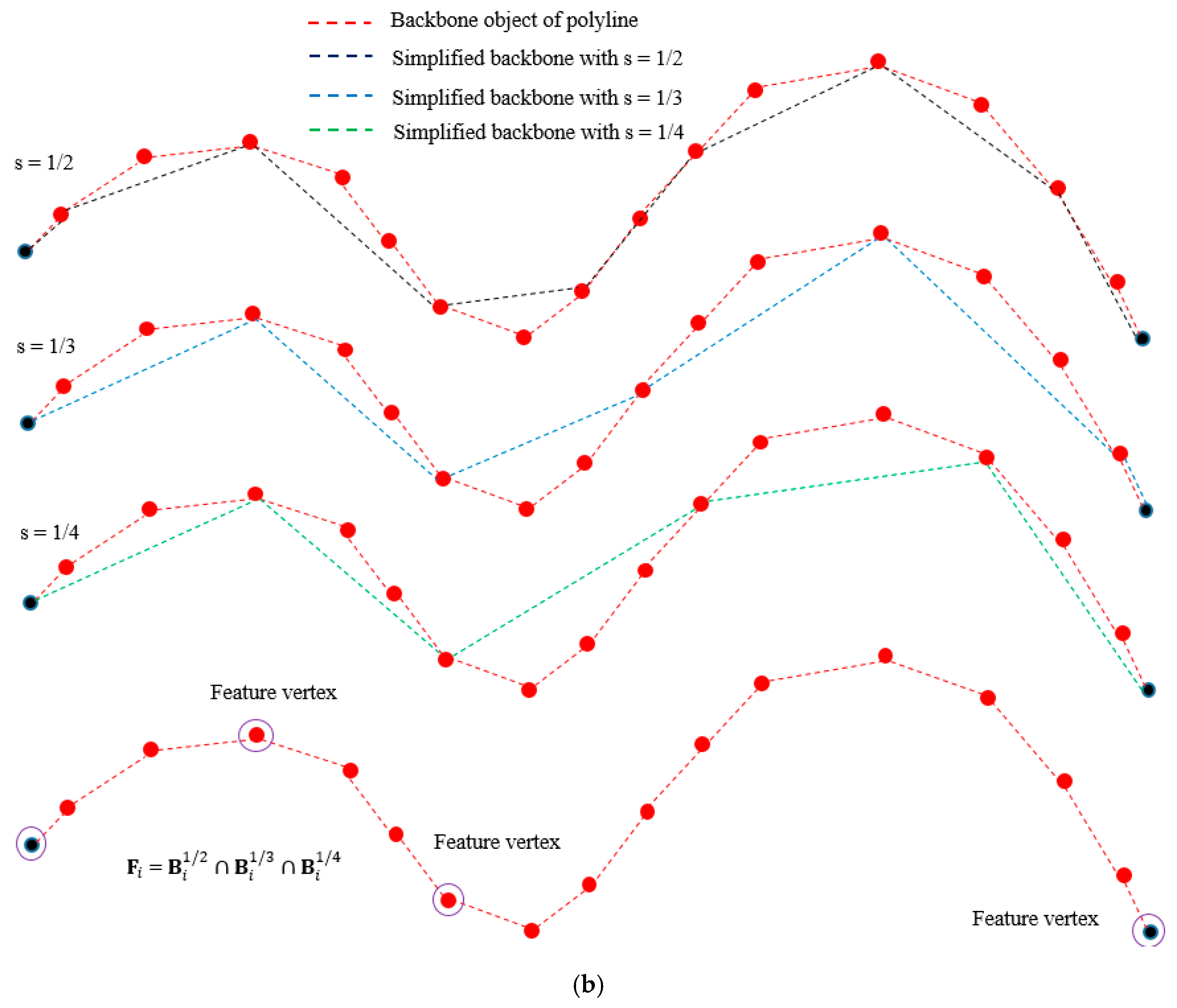
3.2. Backbone Object Simplification and Feature Vertices Computation
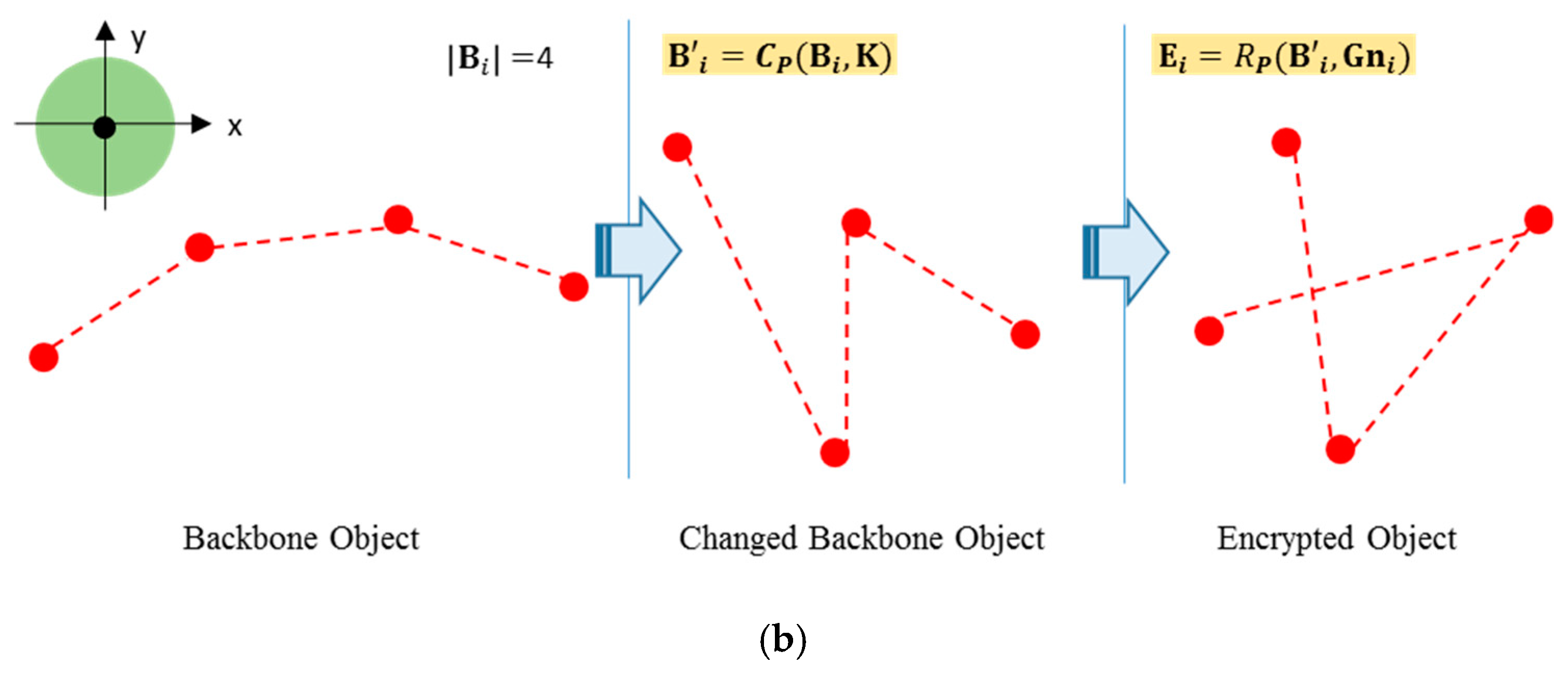
3.3. Random Encryption
3.4. Decryption Process
4. Experimental Results and Analysis
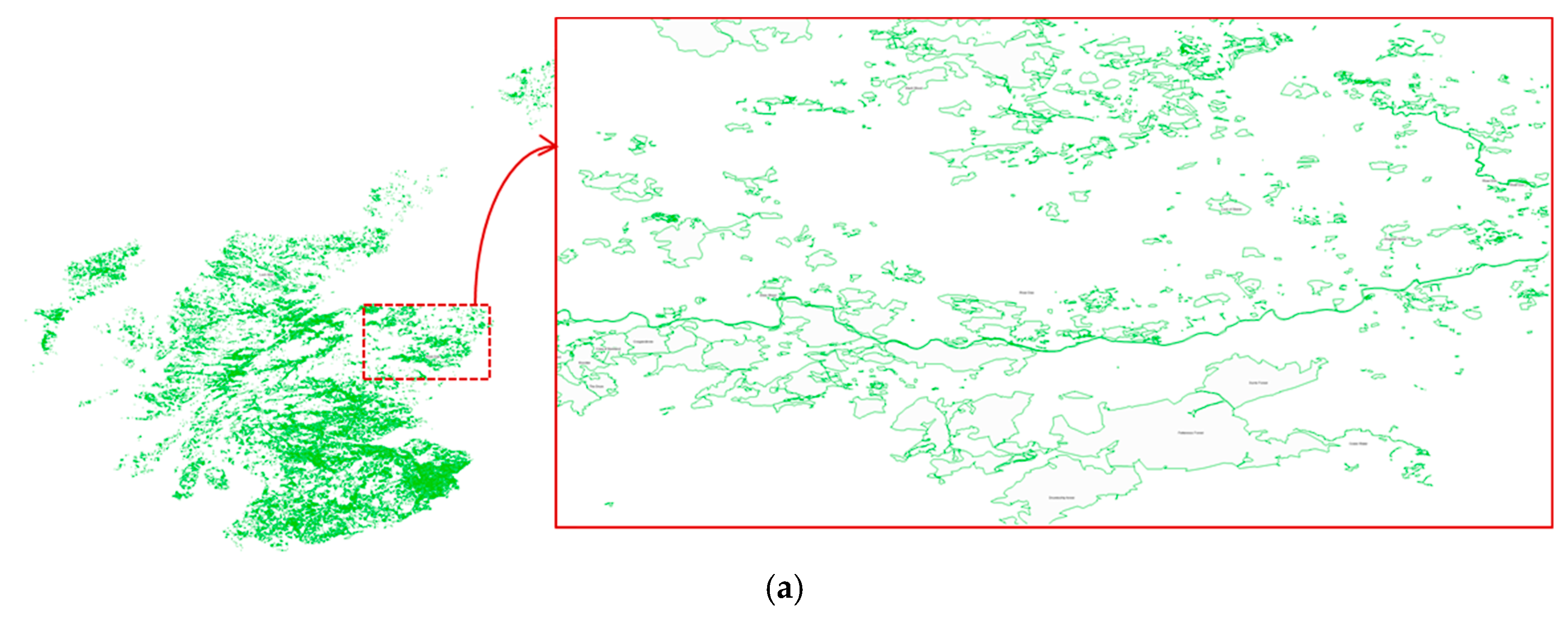
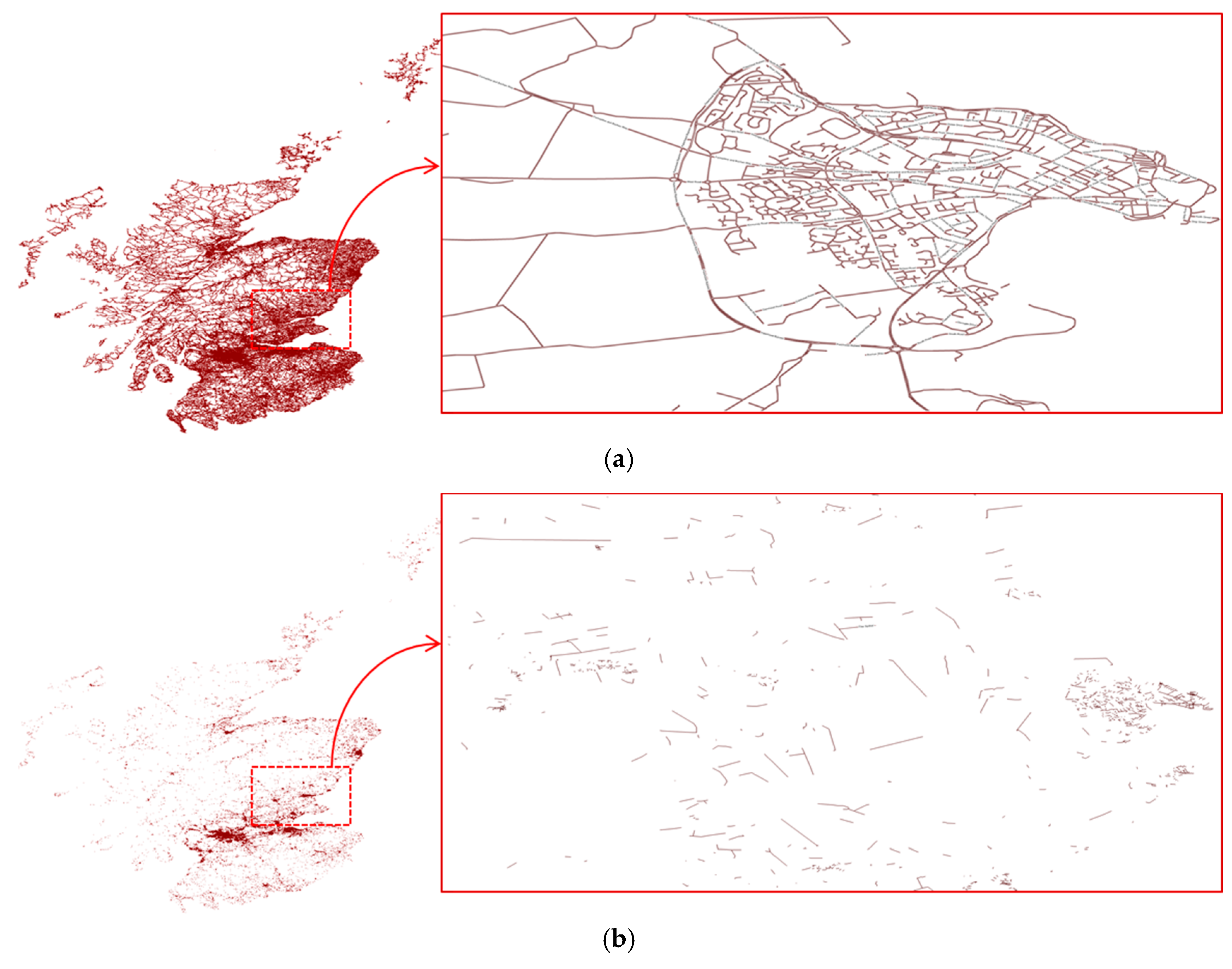
4.1. Visualization Experiments
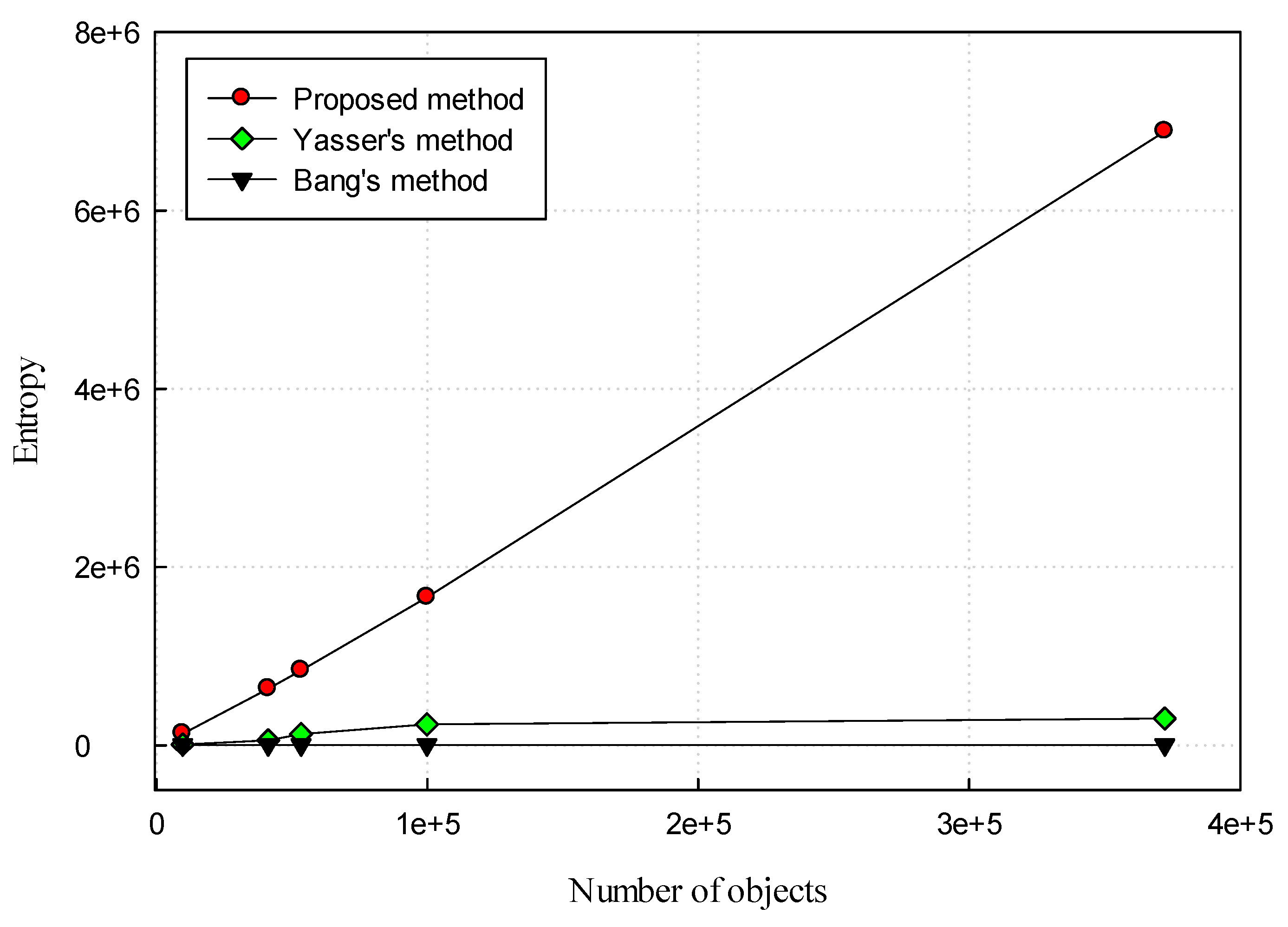
4.2. Security Evaluation
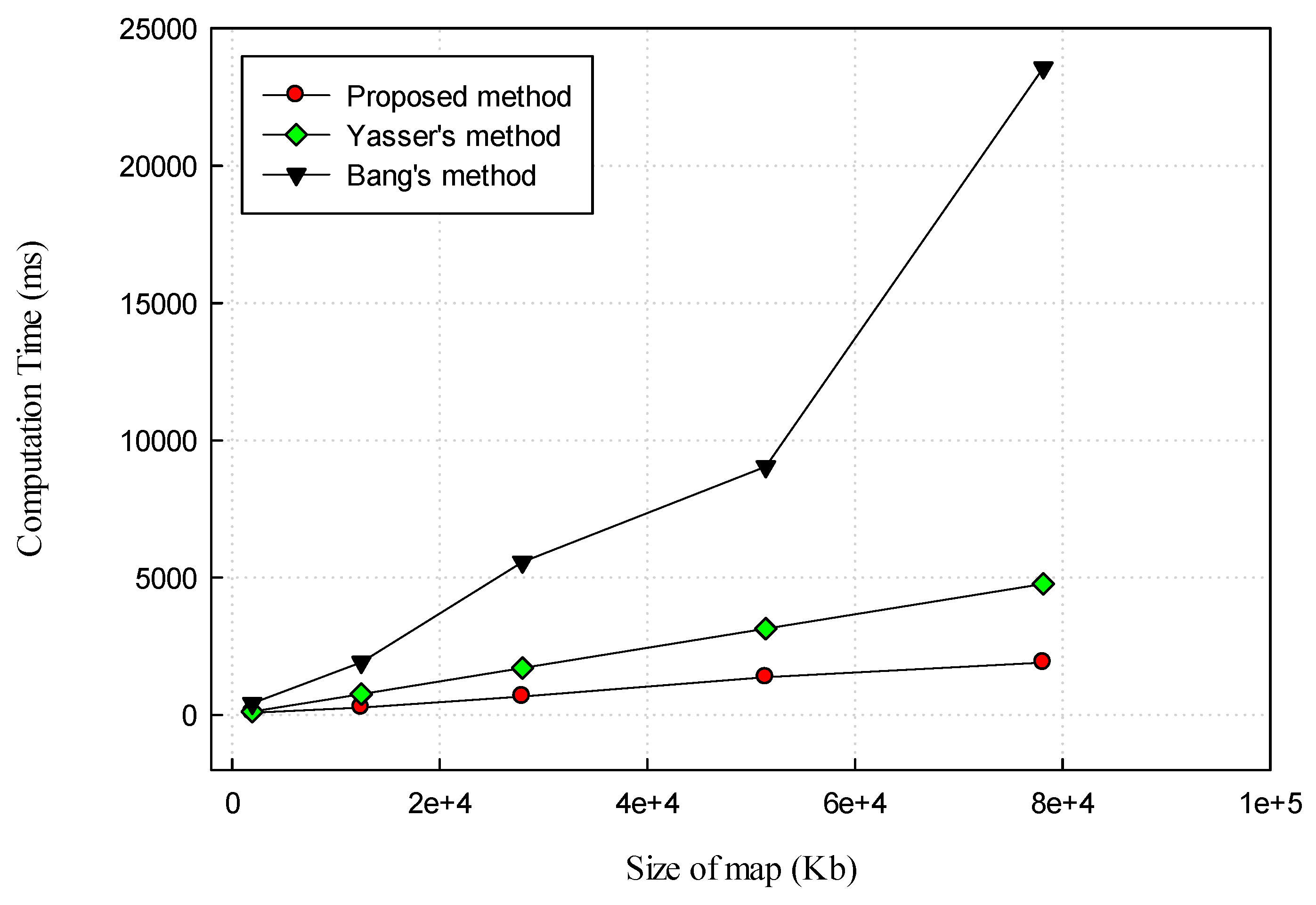
4.3. Computation Time
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- What Is Geographic Information Systems (GIS)? Available online: https://gisgeography.com/what-gis-geographic-information-systems/ (accessed on 30 October 2019).
- Wang, C.; Peng, Z.; Peng, Y.; Yu, L.; Wang, J.; Zhao, Q. Watermarking geographical data on spatial topological relations. Multimed. Tools Appl. 2012, 57, 67–69. [Google Scholar] [CrossRef]
- Lee, S.H.; Kwon, K.R. Vector watermarking scheme for GIS vector map management. Multimed. Tools Appl. 2013, 63, 757–790. [Google Scholar] [CrossRef]
- Ohbuchi, R.; Ueda, H.; Endoh, S. Robust watermarking of vector digital maps. In Proceedings of the IEEE International Conference on Multimedia and Expo, Lausanne, Switzerland, 26–29 August 2002; pp. 577–580. [Google Scholar]
- Chena, S.C.; Wang, X.; Rishea, N.; Weiss, M.A. A web-based spatial data access system using semantic R-trees. J. Inf. Sci. 2003, 167, 41–61. [Google Scholar] [CrossRef]
- Bertino, E.; Damiani, M.L. A Controlled Access to Spatial Data on Web. In Proceedings of the 7th Conference on Geographic Information Science, Heraklion, Greece, 12–13 November 2004; pp. 369–377. [Google Scholar]
- Rybalov, N.B.; Zhukovsky, O.I. Access to the Spatial Data in the Web-Oriented GIS. In Proceedings of the Siberian Conference on Control and Communications, Tomsk, Russia, 20–21 April 2007; pp. 104–107. [Google Scholar]
- Bertino, E.; Thuraisingham, B.; Gertz, M.; Damiani, M.L. Security and privacy for geospatial data: Concepts and research directions. In Proceedings of the International Workshop on Security and Privacy in GIS and LBS, Irvine, CA, USA, 4 November 2008; pp. 6–19. [Google Scholar]
- Fuguang, M.; Yong, G.; Menglong, Y.; Fuchun, X.; Ding, L. The fine-grained security access control of spatial data. In Proceedings of the 18th International Conference on Geo-informatics, Beijing, China, 18–20 June 2010; pp. 1–4. [Google Scholar]
- Wu, F.; Cui, W.; Chen, H. A Compound Chaos-Based Encryption Algorithm for Vector Geographic Data under Network Circumstance. In Proceedings of the Cardholder Information Security Program, Hainan, China, 27–30 May 2008; pp. 254–258. [Google Scholar]
- Li, G. Research of Key Technologies on Encrypting Vector Spatial Data in Oracle Spatial. In Proceedings of the International Conference on Industrial Electronics and Computer Science, Wuhan, China, 25–26 December 2010; pp. 1–4. [Google Scholar]
- Yasser, D.; Elghafar, I.A.; Tammam, A. Protecting GIS Data Using Cryptography and Digital Watermarking. Int. J. Comput. Sci. Netw. Secur. 2010, 10, 75–84. [Google Scholar]
- Jang, B.J.; Lee, S.H.; Kwon, K.R. Perceptual Encryption with Compression for Secure Vector Map Data Processing. J. Digit. Signal Process. 2014, 25, 224–243. [Google Scholar] [CrossRef]
- Bang, N.V.; Lim, S.H.; Moon, K.S.; Lee, S.H.; Kwon, K.R. Selective Encryption Scheme for Vector Map Data using Chaotic Map. J. Korea Multimed. Soc. 2015, 18, 818–826. [Google Scholar] [CrossRef]
- RSA Laboratories. Password-Based Cryptography Standard; RSA Security LLC: Bedford, MA, USA, 2006. [Google Scholar]
- Maria, I.R. Gaussian Probability Density Functions: Properties and Error Characterization; Institute for Systems and Robotics: Lisbon, Portugal, 2004. [Google Scholar]
- Gaussian Distribution. Available online: http://hyperphysics.phy-astr.gsu.edu/hbase/Math/gaufcn.html (accessed on 30 October 2019).
- United Kingdom Shapefile. Available online: https://www.igismap.com/united-kingdom-shapefile-download/ (accessed on 30 October 2019).
- White Paper: ESRI Shape-File Technical Description; Environmental Systems Research Institute: Redlands, CA, USA, 1998.
- Open GIS Geography Markup Language (GML) Encoding Standard. Available online: https://www.opengeospatial.org/standards/security (accessed on 30 October 2019).
- Mapinfor. Available online: http://www.pbinsight.com/welcome/mapinfo/ (accessed on 30 October 2019).

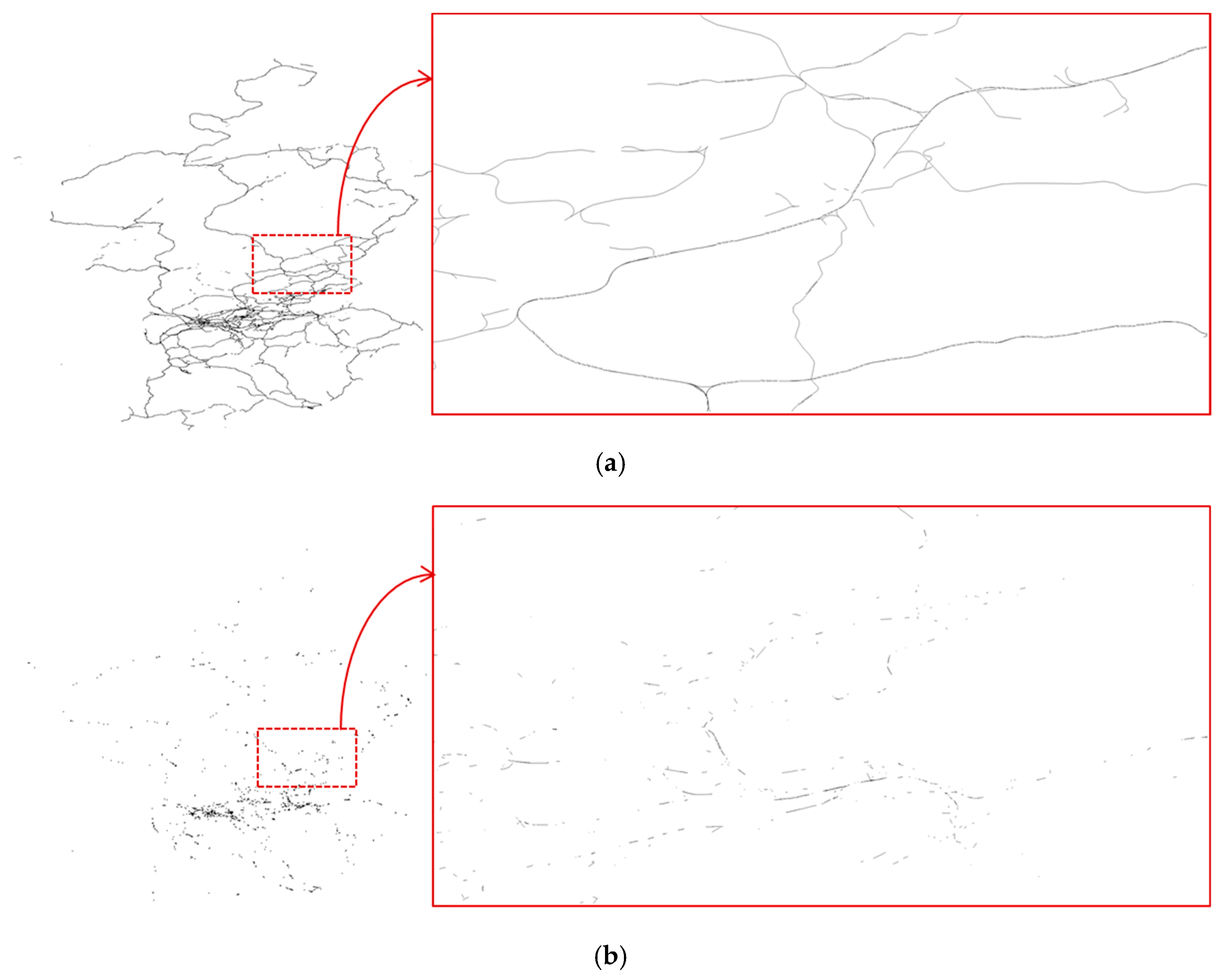
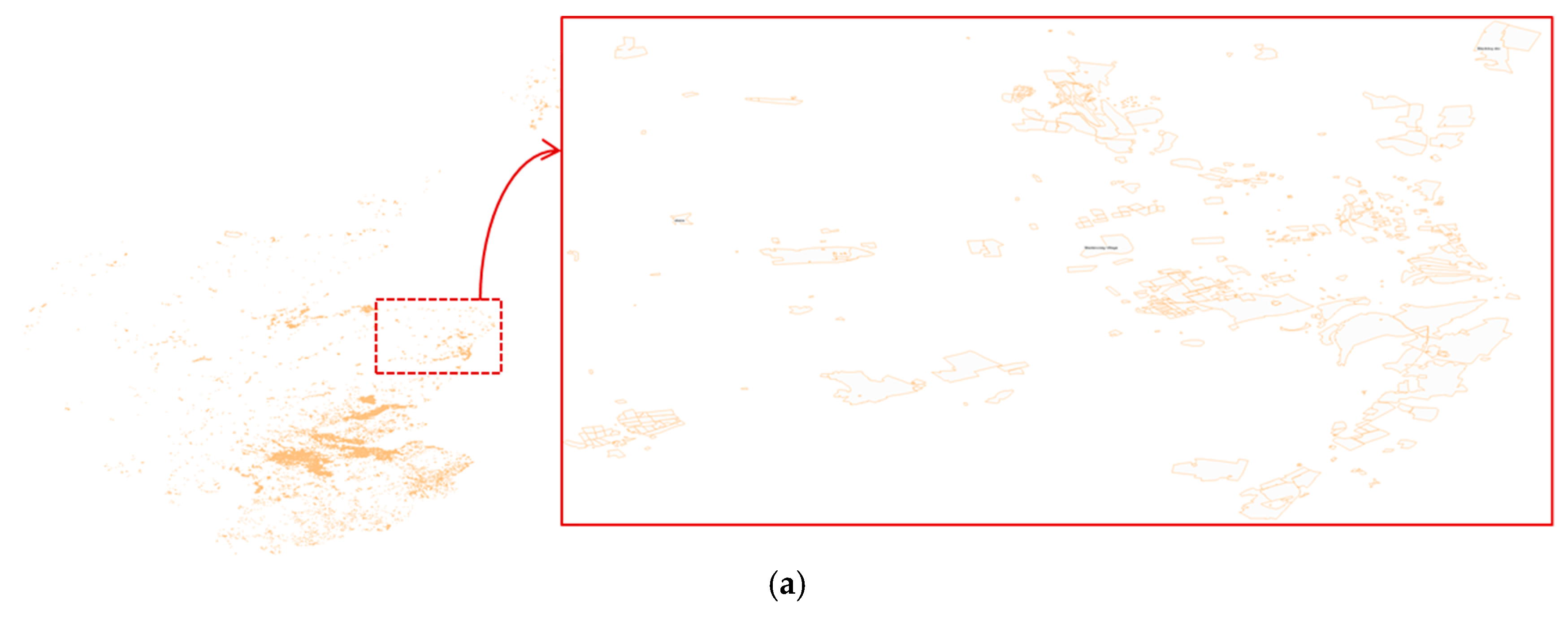

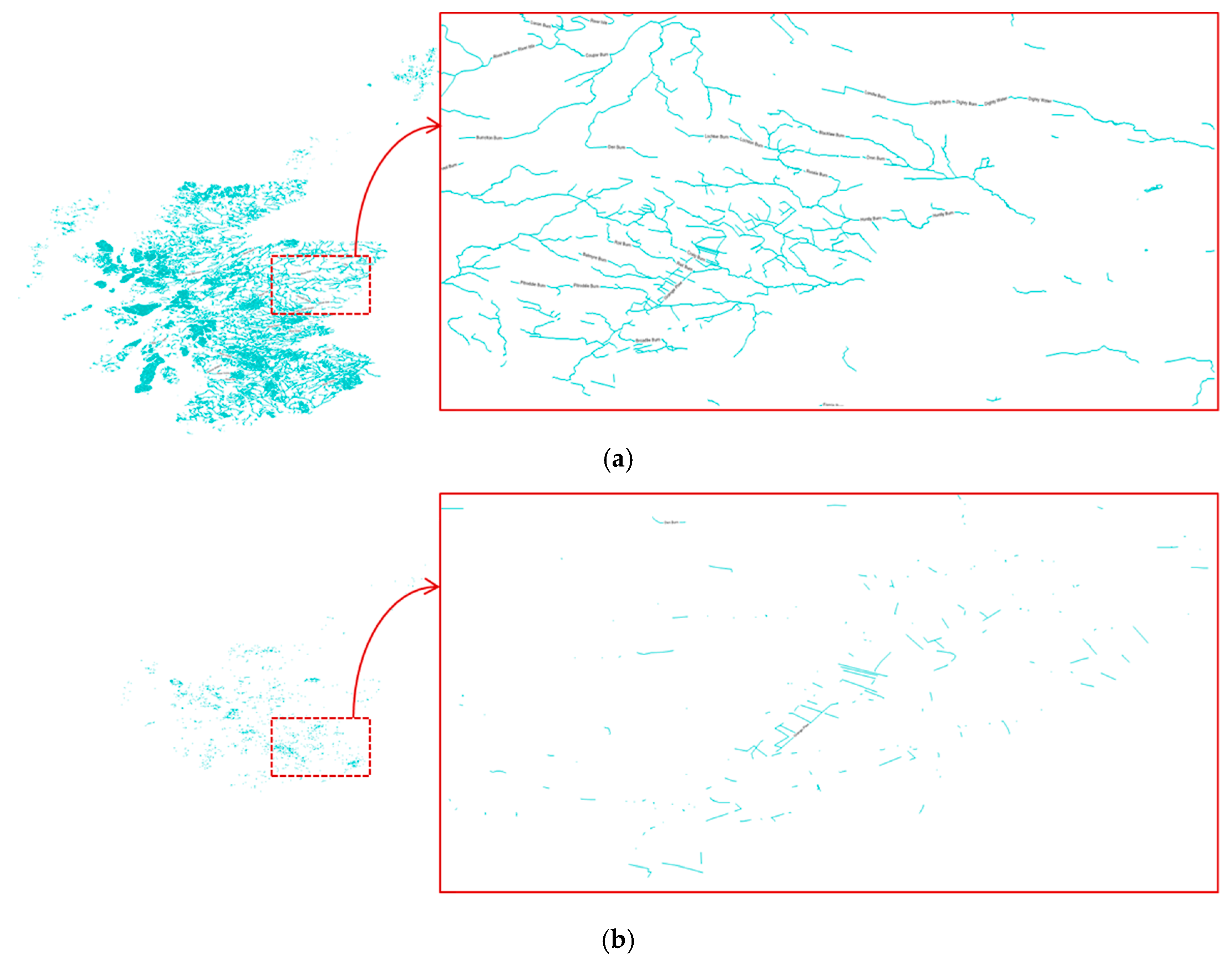

| Scotland Maps | Size (Kb) | # Objects | Computation Time (ms) | Entropy (dB) |
|---|---|---|---|---|
| Railway | 1951 | 9724 | 77 | 128,817 |
| Land-use | 12,452 | 41,242 | 263 | 632,315 |
| Waterway | 27,954 | 53,389 | 668 | 838,434 |
| Nature | 51,417 | 99,835 | 1367 | 1,657,985 |
| Road | 78,136 | 372,138 | 1896 | 6,886,591 |
| Scotland Maps | # Objects | Entropy (dB) | ||
|---|---|---|---|---|
| Our Method | Yasser’s Method | Bang’s Method | ||
| Railway | 9724 | 128,817 | 9216 | 4608 |
| Land-use | 41,242 | 632,315 | 55,296 | 4608 |
| Waterway | 53,389 | 838,434 | 124,416 | 4608 |
| Nature | 99,835 | 1,657,985 | 235,008 | 4608 |
| Road | 372,138 | 6,886,591 | 299,520 | 4608 |
| Scotland Maps | Size (Kb) | Computation Time (ms) | ||
|---|---|---|---|---|
| Our Method | Yasser’s Method | Bang’s Method | ||
| Railway | 1951 | 77 | 117 | 416 |
| Land-use | 12,452 | 263 | 759 | 1916 |
| Waterway | 27,954 | 668 | 1705 | 5564 |
| Nature | 51,417 | 1367 | 3136 | 9036 |
| Road | 78,136 | 1896 | 4766 | 23,563 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pham, G.N.; Ngo, S.T.; Bui, A.N.; Tran, D.V.; Lee, S.-H.; Kwon, K.-R. Vector Map Random Encryption Algorithm Based on Multi-Scale Simplification and Gaussian Distribution. Appl. Sci. 2019, 9, 4889. https://doi.org/10.3390/app9224889
Pham GN, Ngo ST, Bui AN, Tran DV, Lee S-H, Kwon K-R. Vector Map Random Encryption Algorithm Based on Multi-Scale Simplification and Gaussian Distribution. Applied Sciences. 2019; 9(22):4889. https://doi.org/10.3390/app9224889
Chicago/Turabian StylePham, Giao N., Son T. Ngo, Anh N. Bui, Dinh V. Tran, Suk-Hwan Lee, and Ki-Ryong Kwon. 2019. "Vector Map Random Encryption Algorithm Based on Multi-Scale Simplification and Gaussian Distribution" Applied Sciences 9, no. 22: 4889. https://doi.org/10.3390/app9224889
APA StylePham, G. N., Ngo, S. T., Bui, A. N., Tran, D. V., Lee, S.-H., & Kwon, K.-R. (2019). Vector Map Random Encryption Algorithm Based on Multi-Scale Simplification and Gaussian Distribution. Applied Sciences, 9(22), 4889. https://doi.org/10.3390/app9224889





