ZONE-Based Multi-Access Edge Computing Scheme for User Device Mobility Management
Abstract
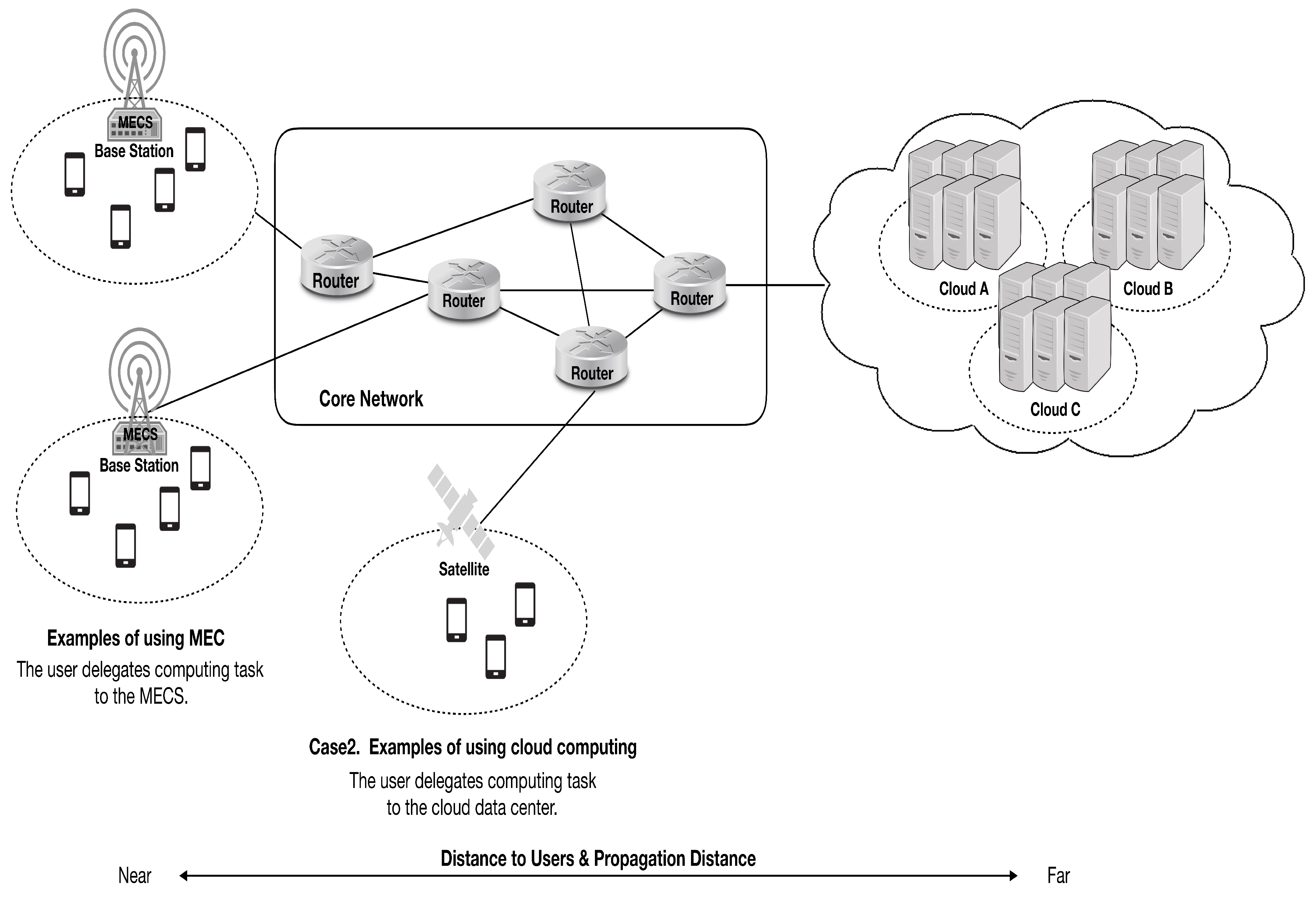
1. Introduction
2. Related Works
3. Proposed Zone-Based MEC Architecture for User Device Mobility Management
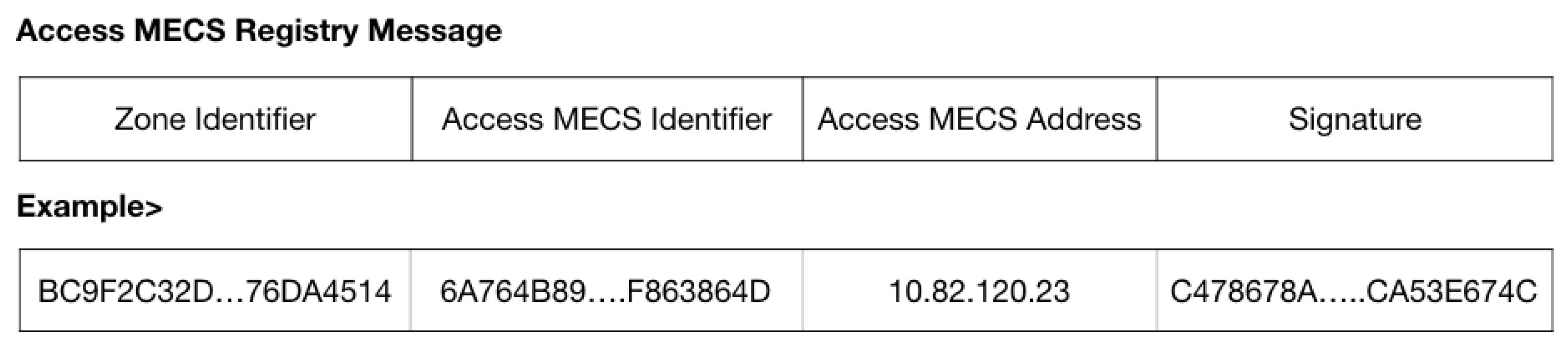
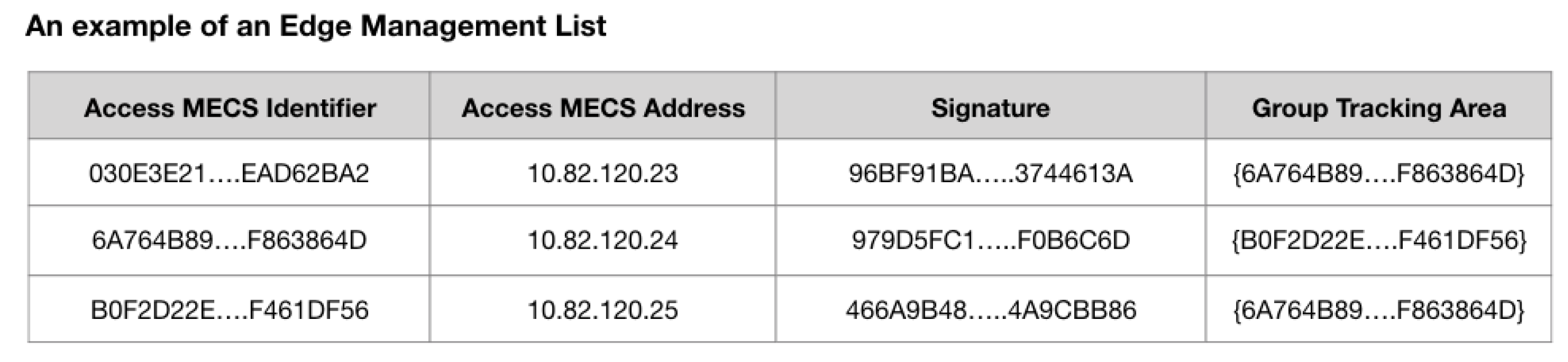
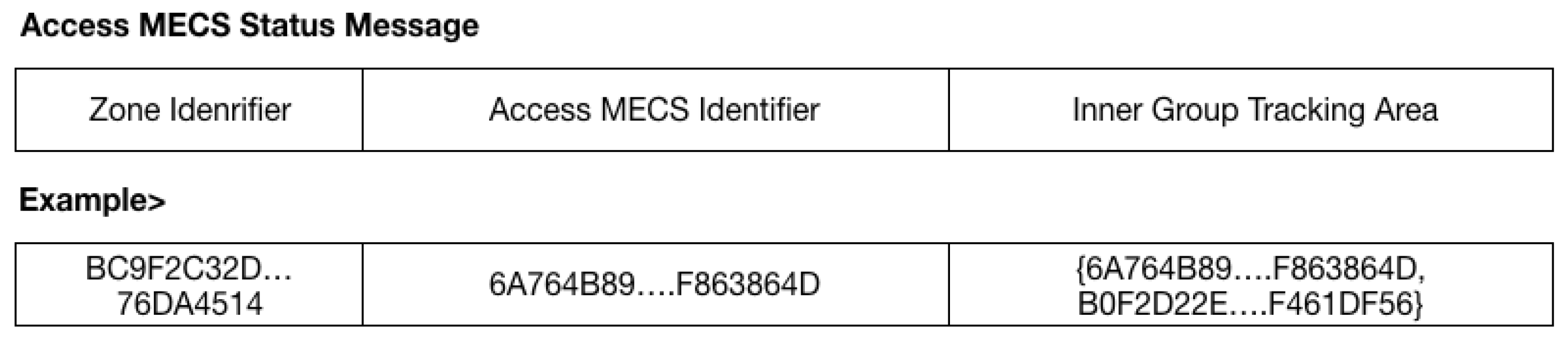
3.1. A Scheme to Support User Mobility Management within the Zone
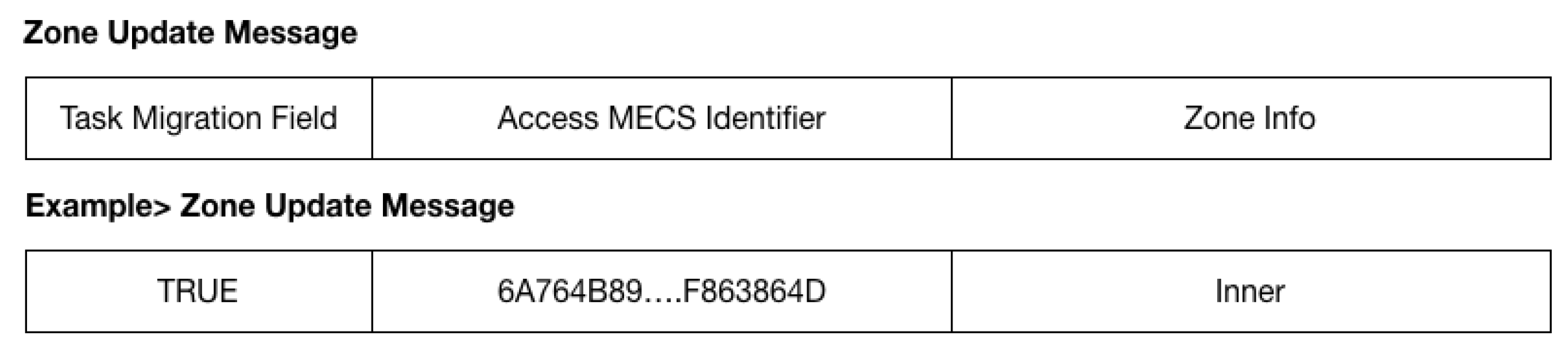
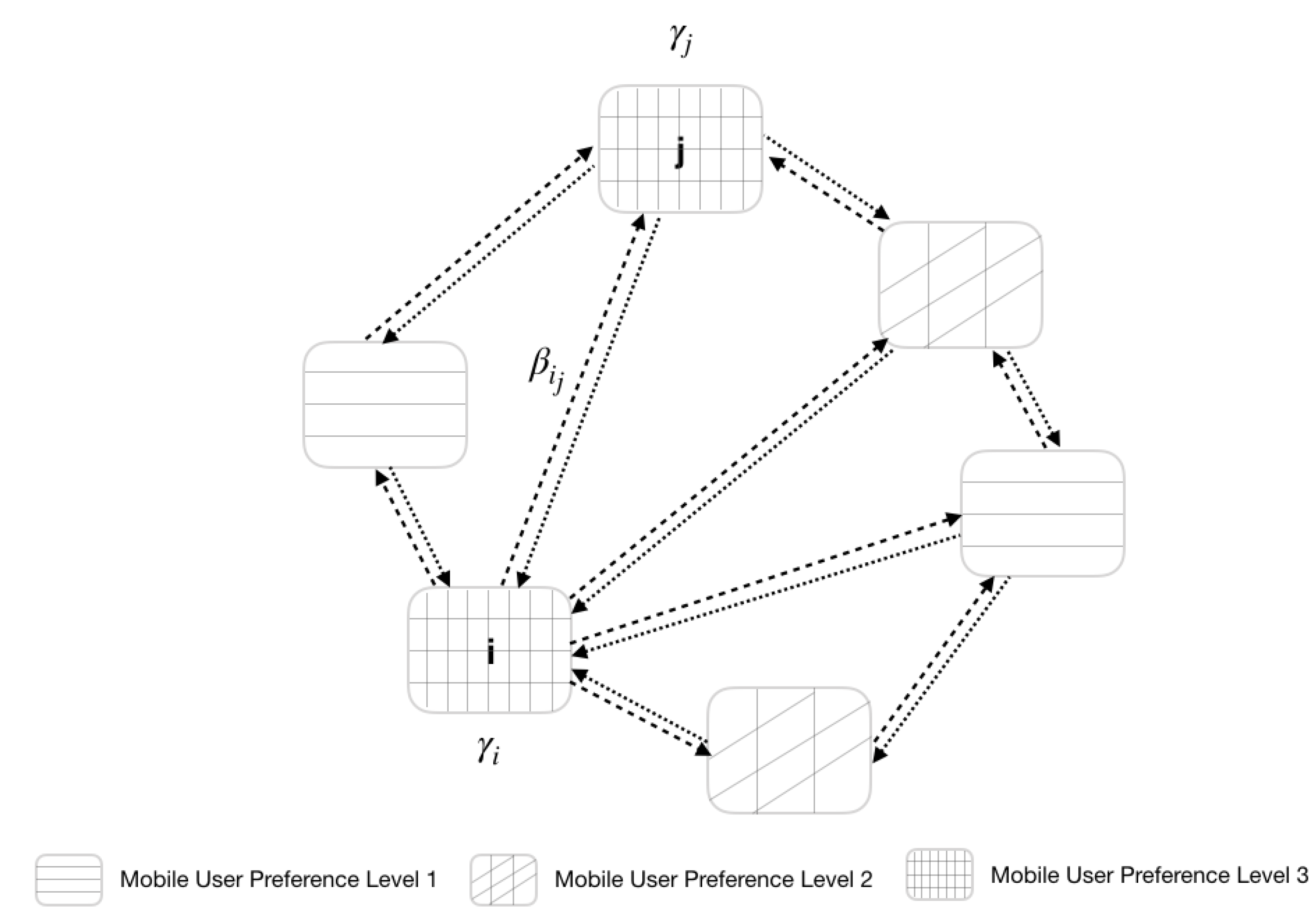
3.2. A Scheme to Support User Mobility Management between the Zones
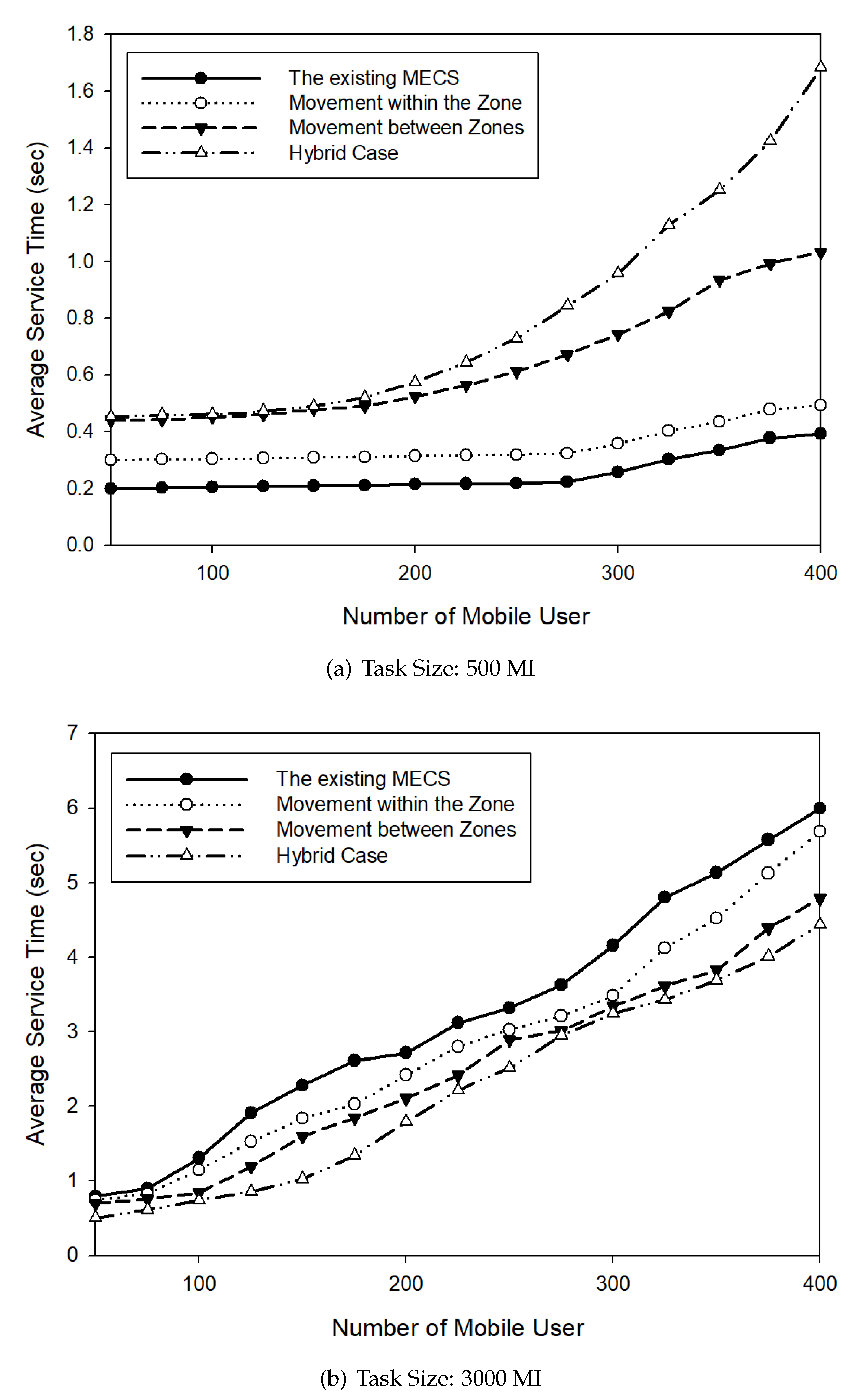
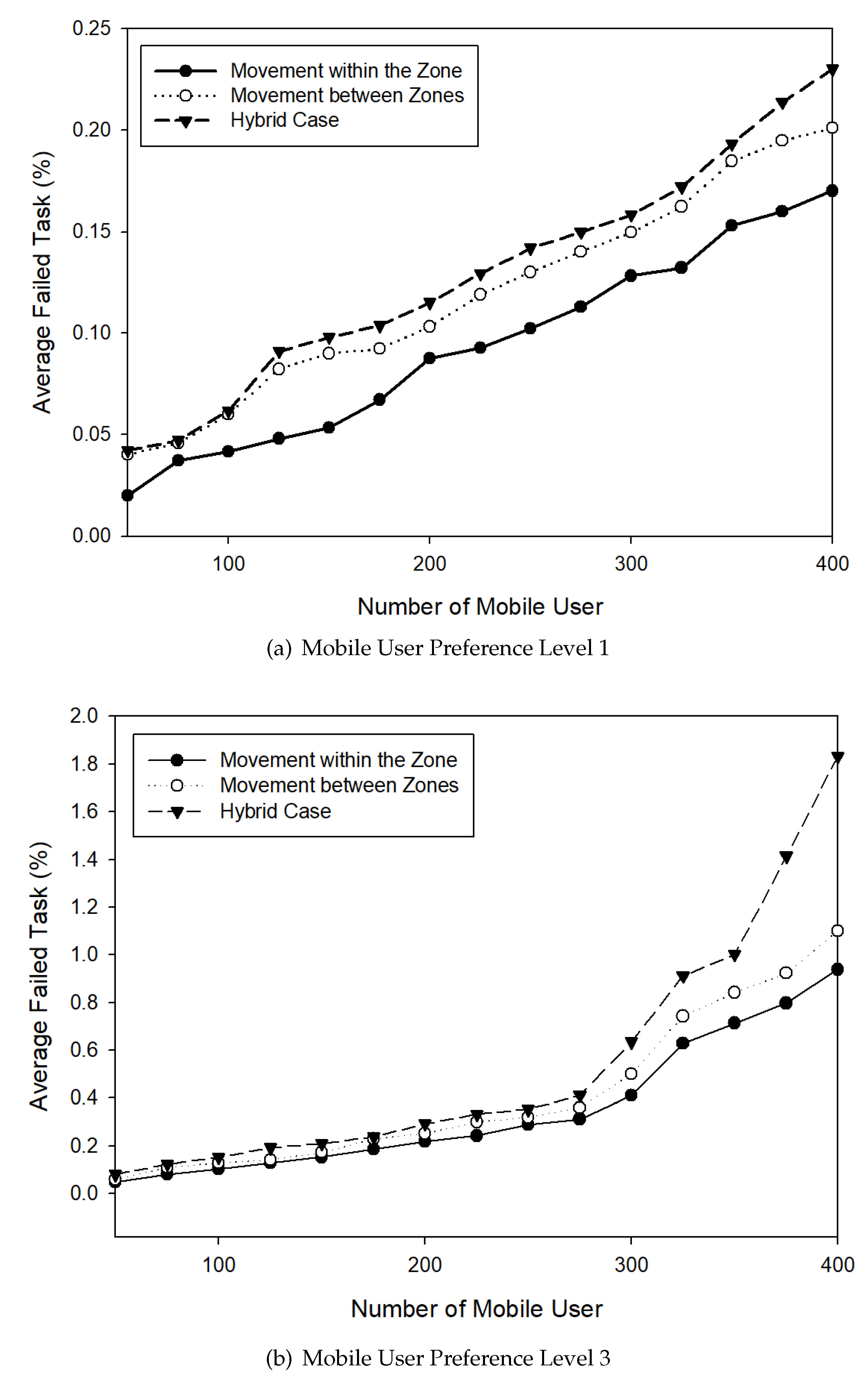
4. Performance Evaluations
5. Open Issues and Challenges
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| MEC | Multi-Access Edge Computing |
| MECS | Multi-Access Edge Computing Server |
| IoT | Internet of Things |
| ML | Machine Learning |
| AR | Augmented Reality |
| GCP | Google Cloud Platform |
| EC2 | Amazon Elastic Compute Cloud |
| UHD | Ultra-High Definition |
| ETSI | The European Telecommunications Standard Institute |
| RAN | Radio Access Network |
| vMSG | virtualized Mobility Support Gateway |
| QoS | Quality of Service |
| MPTCP | MultiPath TCP |
| EMO | Edge Management Orchestra |
| ZMO | Zone Management Orchestra |
| AMR | Access MECS Registry |
| UUID | Universally Unique Identifier |
| SHA | Secure Hash Algorithm |
| EML | Edge Management List |
| AMS | Access MECS Status |
| ZU | Zone Update |
| ZML | Zone Management List |
| MI | Million Instructions |
| MIPS | Million Instructions Per Second |
| AI | Artificial Intelligence |
References
- Baydin, A.G.; Pearlmutter, B.A.; Radul, A.A.; Siskind, J.M. Automatic differentiation in machine learning: A survey. J. Marchine Learn. Res. 2018, 18, 1–43. [Google Scholar]
- Zhao, R.; Yan, R.; Chen, Z.; Mao, K.; Wang, P.; Gao, R.X. Deep learning and its applications to machine health monitoring. Mech. Syst. Signal Process. 2019, 115, 213–237. [Google Scholar] [CrossRef]
- Ye, H.; Liang, L.; Li, G.Y.; Kim, J.; Lu, L.; Wu, M. Machine learning for vehicular networks: Recent advances and application examples. IEEE Veh. Technol. Mag. 2018, 13, 94–101. [Google Scholar] [CrossRef]
- Palmarini, R.; Erkoyuncu, J.A.; Roy, R.; Torabmostaedi, H. A systematic review of augmented reality applications in maintenance. Robot. Comput.-Integr. Manuf. 2018, 49, 215–228. [Google Scholar] [CrossRef]
- Lee, J.; Lee, J. Preallocated duplicate name prefix detection mechanism using naming pool in CCN based mobile IoT networks. Mob. Inf. Syst. 2016, 2016. [Google Scholar] [CrossRef]
- Tom Dieck, M.C.; Jung, T. A theoretical model of mobile augmented reality acceptance in urban heritage tourism. Curr. Issues Tour. 2018, 21, 154–174. [Google Scholar] [CrossRef]
- Fraga-Lamas, P.; Fernández-Caramés, T.M.; Blanco-Novoa, Ó.; Vilar-Montesinos, M.A. A review on industrial augmented reality systems for the industry 4.0 shipyard. IEEE Access 2018, 6, 13358–13375. [Google Scholar] [CrossRef]
- Yao, L.; Ge, Z. Deep learning of semisupervised process data with hierarchical extreme learning machine and soft sensor application. IEEE Trans. Ind. Electron. 2018, 65, 1490–1498. [Google Scholar] [CrossRef]
- Komura, D.; Ishikawa, S. Machine learning methods for histopathological image analysis. Comput. Struct. Biotechnol. J. 2018, 16, 34–42. [Google Scholar] [CrossRef]
- Ostermann, S.; Iosup, A.; Yigitbasi, N.; Prodan, R.; Fahringer, T.; Epema, D. A performance analysis of EC2 cloud computing services for scientific computing. In Proceedings of the International Conference on Cloud Computing, Munich, Germany, 19–21 October 2009; pp. 115–131. [Google Scholar]
- Challita, S.; Zalila, F.; Gourdin, C.; Merle, P. A Precise Model for Google Cloud Platform. In Proceedings of the 018 IEEE International Conference on Cloud Engineering (IC2E), Orlando, FL, USA, 17–20 April 2018; Volume 10, pp. 177–183. [Google Scholar]
- Peng, H.G.; Wang, J.Q. A Multicriteria Group Decision-Making Method Based on the Normal Cloud Model With Zadeh’sZ-Numbers. IEEE Trans. Fuzzy Syst. 2018, 26, 3246–3260. [Google Scholar] [CrossRef]
- Stergiou, C.; Psannis, K.E.; Kim, B.G.; Gupta, B. Secure integration of IoT and cloud computing. Future Gener. Comput. Syst. 2018, 78, 964–975. [Google Scholar] [CrossRef]
- Rosário, D.; Schimuneck, M.; Camargo, J.; Nobre, J.; Both, C.; Rochol, J.; Gerla, M.T. Service migration from cloud to multi-tier fog nodes for multimedia dissemination with QoE support. Sensors 2018, 18, 329. [Google Scholar] [CrossRef] [PubMed]
- Benkacem, I.; Taleb, T.; Bagaa, M.; Flinck, H. Optimal VNFs placement in CDN slicing over multi-cloud environment. IEEE J. Sel. Areas Commun. 2018, 36, 616–627. [Google Scholar] [CrossRef]
- Jacobson, V.; Smetters, D.K.; Thornton, J.D.; Plass, M.F.; Briggs, N.H.; Braynard, R.L. Networking named content. In Proceedings of the 5th International Conference on Emerging Networking Experiments and Technologies, Rome, Italy, 1–4 December 2009; pp. 1–12. [Google Scholar]
- Lee, J.; Lee, J. Pre-allocated duplicate name prefix detection mechanism using naming-pool in mobile content-centric network. In Proceedings of the 2015 Seventh International Conference on Ubiquitous and Future Networks, Sapporo, Japan, 7–10 July 2015; pp. 115–117. [Google Scholar]
- Oueida, S.; Kotb, Y.; Aloqaily, M.; Jararweh, Y.; Baker, T. An Edge Computing Based Smart Healthcare Framework for Resource Management. Sensors 2018, 18, 4307. [Google Scholar] [CrossRef] [PubMed]
- Mao, Y.; Zhang, J.; Letaief, K.B. Dynamic computation offloading for mobile-edge computing with energy harvesting devices. IEEE J. Sel. Areas Commun. 2016, 34, 3590–3605. [Google Scholar] [CrossRef]
- Mach, P.; Becvar, Z. Mobile edge computing: A survey on architecture and computation offloading. IEEE Internet Things J. 2018, 5, 450–465. [Google Scholar] [CrossRef]
- Li, H.; Shou, G.; Hu, Y.; Guo, Z. Mobile edge computing: Progress and challenges. In Proceedings of the 2016 4th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud), Oxford, UK, 29 March–1 April 2016. [Google Scholar]
- Lee, J.; Lee, J. Hierarchical Mobile Edge Computing Architecture Based on Context Awareness. Appl. Sci. 2018, 8, 1160. [Google Scholar] [CrossRef]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog computing and its role in the internet of things. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing, Helsinki, Finland, 17 August 2012; pp. 13–16. [Google Scholar]
- Mahmud, R.; Kotagiri, R.; Buyya, R. Fog computing: A taxonomy, survey and future directions. In In Internet of Everything; Springer: Singapore, 2018; pp. 103–130. [Google Scholar]
- Hu, Y.C.; Patel, M.; Sabella, D.; Sprecher, N.; Young, V. Mobile Edge Computing—A Key Technology towards 5G; ETSI White Paper; European Telecommunications Standards Institute: Valbonne, France, 2015; Volume 11, pp. 1–16. [Google Scholar]
- Kondo, T.; Isawaki, K.; Maeda, K. Development and Evaluation of the MEC Platform Supporting the Edge Instance Mobility. In Proceedings of the 2018 IEEE 42nd Annual Computer Software and Applications Conference, Tokyo, Japan, 23–27 July 2018; Volume 2, pp. 193–198. [Google Scholar]
- Ojima, T.; Fujii, T. Resource management for mobile edge computing using user mobility prediction. In Proceedings of the 2018 International Conference on Information Networking (ICOIN), Chiang Mai, Thailand, 10–12 January 2018; pp. 718–720. [Google Scholar]
- Al Ridhawi, I.; Aloqaily, M.; Kotb, Y.; Al Ridhawi, Y.; Jararweh, Y. A collaborative mobile edge computing and user solution for service composition in 5G systems. Trans. Emerg. Telecommun. Technol. 2018, 29, e3446. [Google Scholar] [CrossRef]
- Aloqaily, M.; Al Ridhawi, I.; Salameh, H.B.; Jararweh, Y. Data and service management in densely crowded environments: Challenges, opportunities, and recent developments. IEEE Commun. Mag. 2019, 57, 81–87. [Google Scholar] [CrossRef]
- Balasubramanian, V.; Aloqaily, M.; Zaman, F.; Jararweh, Y. Exploring Computing at the Edge: A Multi-Interface System Architecture Enabled Mobile Device Cloud. In Proceedings of the IEEE 7th International Conference on Cloud Networking (CloudNet), Tokyo, Japan, 22–24 October 2018; pp. 1–4. [Google Scholar]
- Calheiros, R.N.; Ranjan, R.; Beloglazov, A.; De Rose, C.A.; Buyya, R. CloudSim: A Toolkit for Modeling and Simulation of Cloud Computing Environments and Evaluation of Resource Provisioning Algorithms. Softw. Pract. Exper. 2011, 41, 23–50. [Google Scholar] [CrossRef]
- Sonmez, C.; Ozgovde, A.; Ersoy, C. EdgeCloudSim: An environment for performance evaluation of edge computing systems. Trans. Emerg. Telecommun. Technol. 2018, 29, e3493. [Google Scholar] [CrossRef]
- Lee, J.; Lee, J. Mobile Edge Computing based Charging Infrastructure considering Electric Vehicle Charging Efficiency. J. Korea Acad.-Ind. Coop. Soc. 2017, 18, 669–674. [Google Scholar]
- Ribeiro, A.; Sofia, R. A survey on mobility models for wireless networks. SITI 2011, 10, 142–149. [Google Scholar]
- Lee, J.; Lee, J. Efficient Mobile Content-Centric Networking Using Fast Duplicate Name Prefix Detection Mechanism. Contemp. Eng. Sci. 2014, 7, 1345–1353. [Google Scholar] [CrossRef][Green Version]
- Boettiger, C. An introduction to Docker for reproducible research. ACM SIGOPS Oper. Syst. Rev. 2015, 49, 71–79. [Google Scholar] [CrossRef]
- Al Ridhawi, I.; Aloqaily, M.; Kantarci, B.; Jararweh, Y.; Mouftah, H.T. A continuous diversified vehicular cloud service availability framework for smart cities. Comput. Netw. 2018, 145, 207–218. [Google Scholar] [CrossRef]
- Huang, C.M.; Chiang, M.S.; Dao, D.T.; Su, W.L.; Xu, S.; Zhou, H. V2V data offloading for cellular network based on the software defined network (SDN) inside mobile edge computing (MEC) architecture. IEEE Access 2018, 6, 17741–17755. [Google Scholar] [CrossRef]
- Otoum, S.; Kantarci, B.; Mouftah, H.T. On the Feasibility of Deep Learning in Sensor Network Intrusion Detection. IEEE Netw. Lett. 2019. [Google Scholar] [CrossRef]
- Otoum, S.; Kantarci, B.; Mouftah, H. Adaptively supervised and intrusion-aware data aggregation for wireless sensor clusters in critical infrastructures. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]


| Parameter | Value |
|---|---|
| User Mobility Model | Nomadic Mobility Model |
| Number of Mobile User | 50–400 |
| Number of Mobile User Preference Level | 3 |
| Probability of Selecting a Mobile User Preference Level | equal (1/3) |
| Number of access MECS per Place | 1 |
| VM Processor Speed (MIPS) per access MECS | 1000 |
| Average Task Size (MI) | 2000 |
| WLAN Bandwidth (Mbps) | 300 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, J.; Kim, D.; Lee, J. ZONE-Based Multi-Access Edge Computing Scheme for User Device Mobility Management. Appl. Sci. 2019, 9, 2308. https://doi.org/10.3390/app9112308
Lee J, Kim D, Lee J. ZONE-Based Multi-Access Edge Computing Scheme for User Device Mobility Management. Applied Sciences. 2019; 9(11):2308. https://doi.org/10.3390/app9112308
Chicago/Turabian StyleLee, Juyong, Daeyoub Kim, and Jihoon Lee. 2019. "ZONE-Based Multi-Access Edge Computing Scheme for User Device Mobility Management" Applied Sciences 9, no. 11: 2308. https://doi.org/10.3390/app9112308
APA StyleLee, J., Kim, D., & Lee, J. (2019). ZONE-Based Multi-Access Edge Computing Scheme for User Device Mobility Management. Applied Sciences, 9(11), 2308. https://doi.org/10.3390/app9112308







