Distributed Dynamic Cluster-Head Selection and Clustering for Massive IoT Access in 5G Networks
Abstract
1. Introduction
- Massive IoT devices access will generate a large number of collisions and especially the congestion of random access, which will seriously reduce the access success probability and result in a system overload.
- IoT devices transmit small amounts of data requiring more than 20 handshakes to establish a data connection with the base station (BS) in LTE-M [3], which leads to high signaling overhead and results in low Resource Utilization.
- We analyze the communication process combined with the channel resources including random access and data transmission under the existing network system structure developed by 3GPP. The energy efficiency of the system is then modeled based on the analysis.
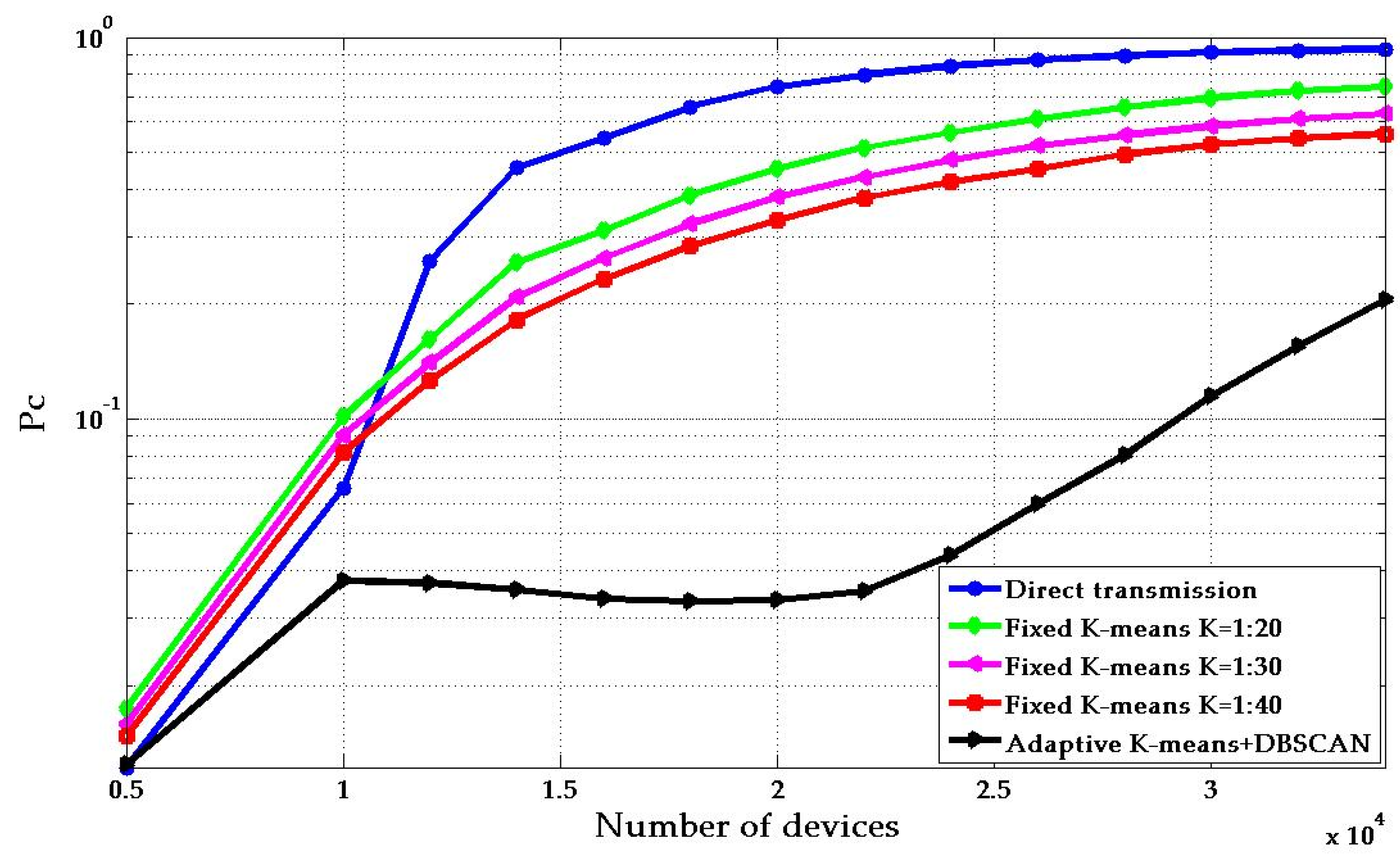
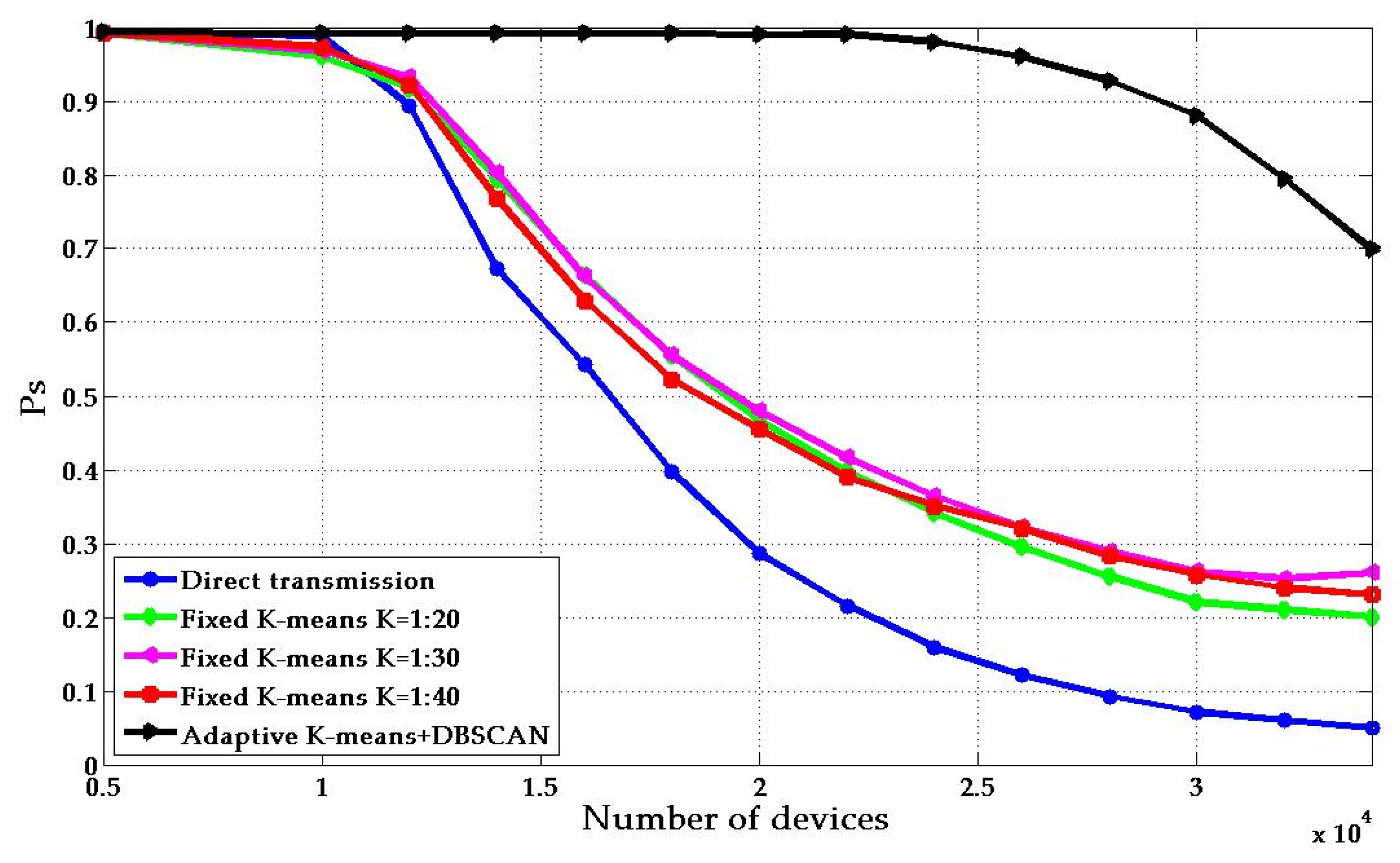
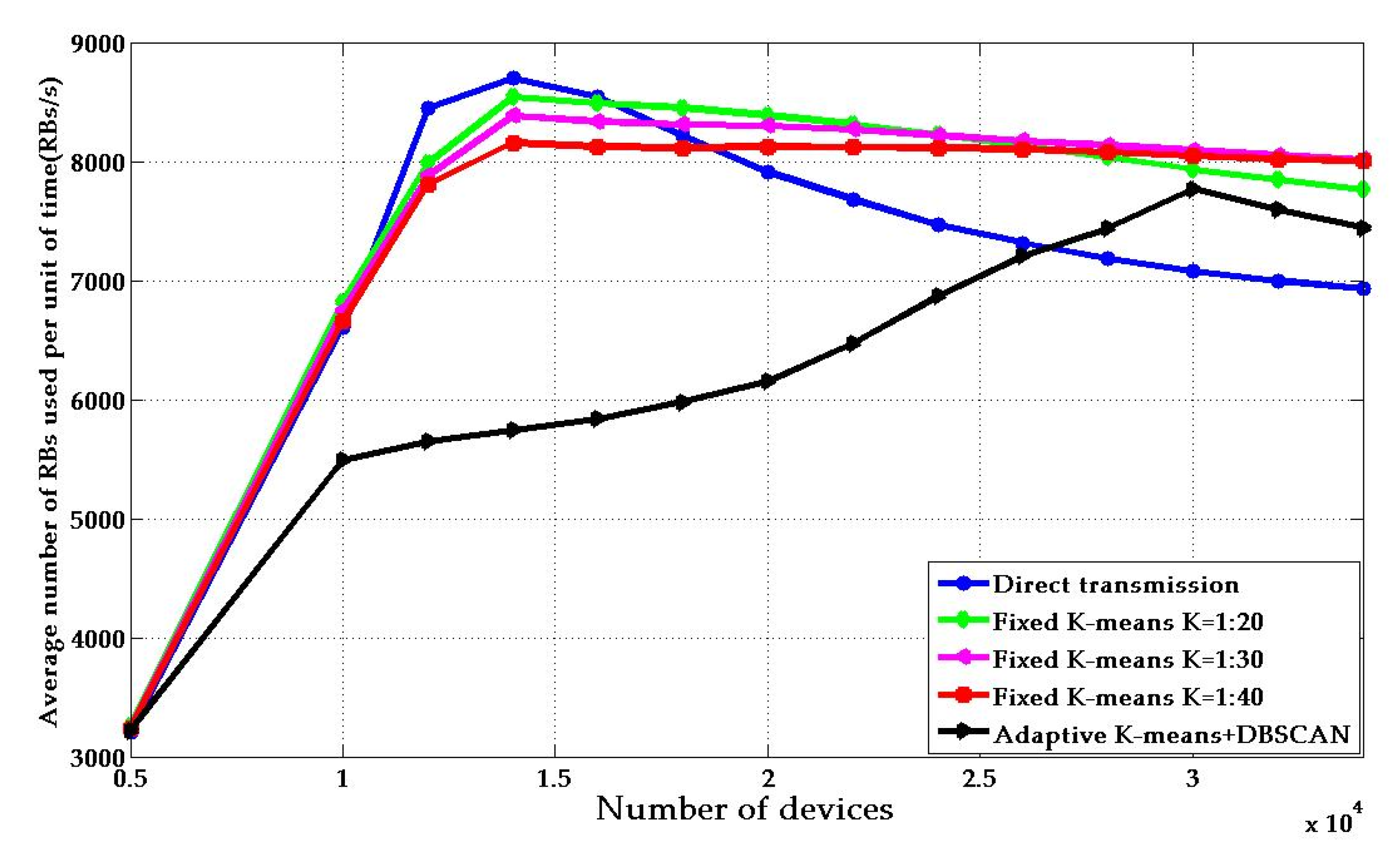
- We use a noise-based density-based method to pre-separate clusters, obtain the required number of cluster heads and initial positions according to the distribution of devices in the region, and solve the actual process access problem of excessive energy consumption in the cluster head. In the optimization of system energy efficiency, an adaptive energy efficiency optimization algorithm based on the distributed idea is proposed. Compared with the existing K-means algorithm, the simulation results show that the proposed algorithm can significantly improve the system energy efficiency and throughput.
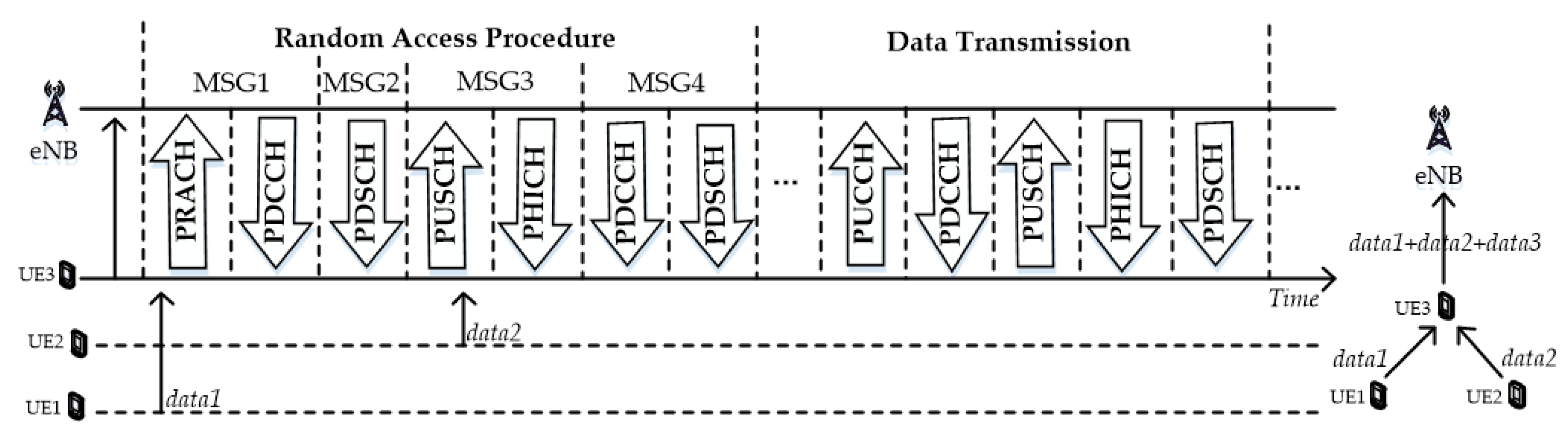
2. Description of Random Access and Data Aggregation
- Establishing an RRC-connected contention-based random access procedure
- Establishing an RRC-connected data transmission
- Releasing an RRC connection
- If the UE receives a response containing an RA-preamble identifier which is the same as the identifier contained in the transmitted random access preamble, the response is successful, and the RA-preamble identifier is used for uplink transmission.
- If the UE does not receive a response within the random access window or fails to verify the response, the response fails.
3. System Model
3.1. Energy Consumption Analysis
3.2. Algorithm Design
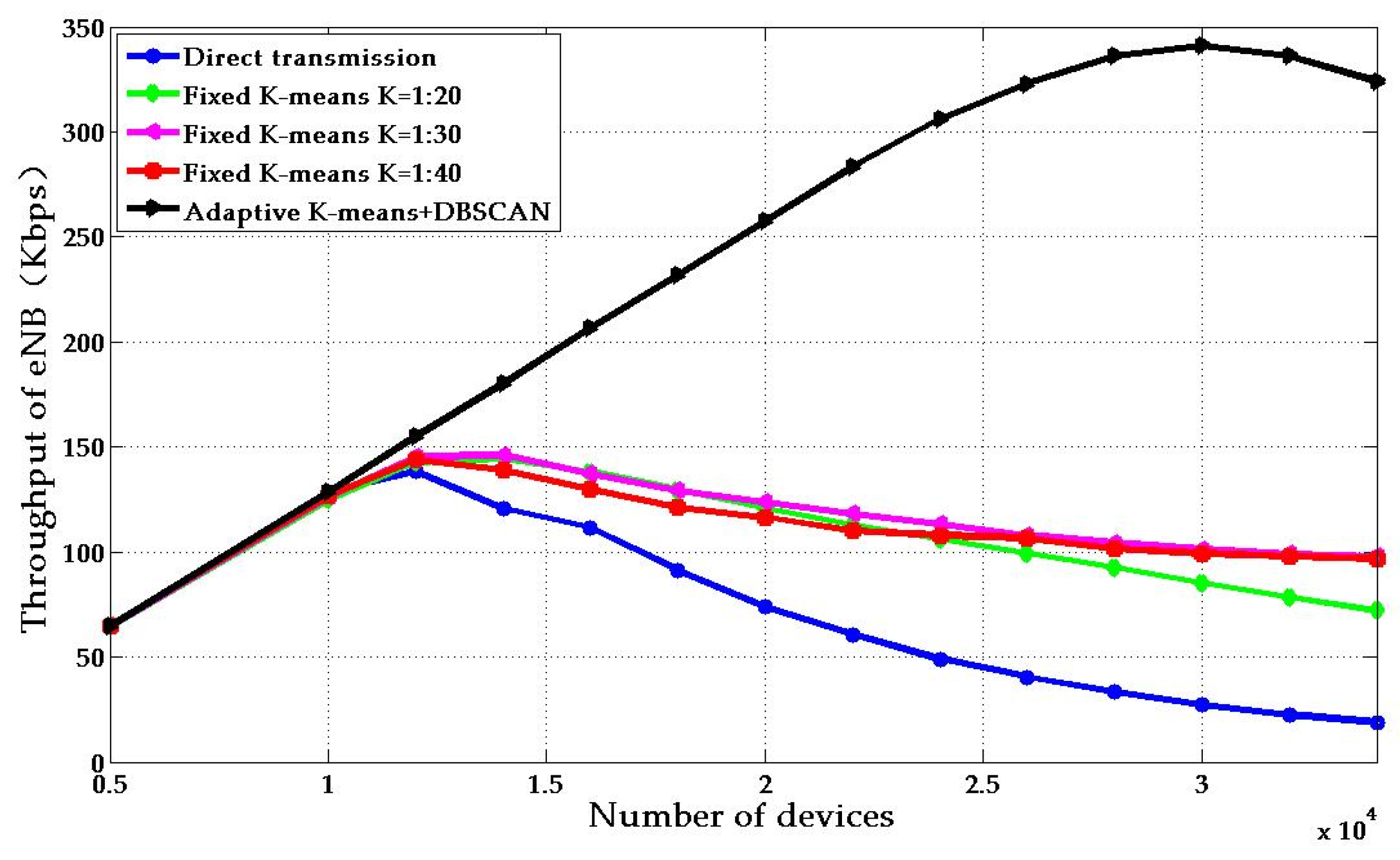
4. Numerical Results
4.1. Platform Analysis
4.2. Parameters
5. Conclusions
Author Contributions
Acknowledgments
Conflicts of Interest
Abbreviations
| IoT | Internet of thing |
| MAC | Media Access Control |
| OFDMA | Orthogonal Frequency-Division Multiple Access |
| LPWAN | Low-Power Wide-Area Network |
| 3GPP | 3rd Generation Partner Project |
| BS | Base Station |
| LEACH | Low-Energy Adaptive Clustering Hierarchy |
| D2D | Device-to-Device |
| MTC | Machine-Type Communications |
| RAN | Radio Access Network |
| CSMA/CA | Carrier Sense Multiple Access/Collision Avoidance |
| RRC | Radio Resource Control |
| PRACH | Physical Random Access Channel |
| C-RNTI | Cell Radio Network Temporary ID |
| PDSCH | Physical Downlink Shared Channel |
| PDCCH | Physical Downlink Control Channel |
| PHICH | Physical HARQ Indication Channel |
| RA | Random Access |
| PUSCH | Physical Uplink Shared Channel) |
| CCCH | Common Control Channel |
| PDU | Packet Data Unit |
| LAN | Local Area Networks |
| RB | Resource Block |
References
- Cisco Systems, Inc. Cisco Visual Networking Index: Global Mobile Data Traffic Forecast Update, 2016–2021 White Pape. Available online: https://www.cisco.com/c/en/us/solutions/collateral/service-provider/visual-networking-index-vni/mobile-white-paper-c11-520862.html (accessed on 28 March 2017).
- Lazarescu, M.T. Design of a WSN Platform for Long-Term Environmental Monitoring for IoT Applications. IEEE J. Emerg. Sel. Top. Circuits Syst. 2013, 3, 45–54. [Google Scholar] [CrossRef]
- Madueño, G.C.; Nielsen, J.J.; Kim, D.M.; Pratas, N.K.; Stefanović, Č.; Popovski, P. Assessment of LTE Wireless Access for Monitoring of Energy Distribution in the Smart Grid. IEEE J. Sel. Areas Commun. 2016, 34, 675–688. [Google Scholar] [CrossRef]
- 3GPP TR 37.868. Technical Specification Group Radio Access Network: Study on RAN Improvements for Machine-type. In 3rd Generation Partnership Project; 3GPP: Valbonne, France, September 2011. [Google Scholar]
- Lien, S.Y.; Liau, T.H.; Kao, C.Y. Cooperative Access Class Barring for Machine-to-Machine Communications. IEEE Trans. Wirel. Commun. 2012, 11, 27–32. [Google Scholar] [CrossRef]
- ZTE. R2-104662: MTC Simulation Results with Specific Solutions, 3GPP, TSG RAN WG2 Meeting 71; ZTE: Shenzhen, China, August 2010. [Google Scholar]
- Lien, S.Y.; Chen, K.C.; Lin, Y. Toward ubiquitous massive accesses in 3GPP machine-to-machine communications. IEEE. Commun. Mag. 2011, 49, 66–74. [Google Scholar] [CrossRef]
- Heinzelman, W.R.; Chandrakasan, A.; Balakrishnan, H. Energy-efficient communication protocol for wireless microsensor networks. In Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, Maui, HI, USA, 10 January 2000. [Google Scholar]
- Gangwar, B.; Bhosale, J.D.; Gangwar, N. An energy optimized path selection and dynamic Cluster head selection for Wireless Mesh Network. In Proceedings of the International Conference on Trends in Electronics and Informatics (ICEI), Tirunelveli, India, 11–12 May 2017. [Google Scholar]
- John, A.; Rajput, A.; Babu, K.V. Dynamic cluster head selection in wireless sensor network for Internet of Things applications. In Proceedings of the International Conference on Innovations in Electrical, Electronics, Instrumentation and Media Technology (ICEEIMT), Coimbatore, India, 3–4 February 2017. [Google Scholar]
- Mohapatra, A.D.; Sahoo, M.N.; Sangaiah, A.K. Distributed fault diagnosis with dynamic cluster-head and energy efficient dissemination model for smart city. Sustain. Cities Soc. 2018, 43, 624–634. [Google Scholar] [CrossRef]
- Jia, D.; Zhu, H.; Zou, S.; Hu, P. Dynamic Cluster Head Selection Method for Wireless Sensor Network. IEEE Sens. J. 2016, 15, 2746–2754. [Google Scholar] [CrossRef]
- Kalantari, M.; Ekbatanifard, G. An energy-aware dynamic cluster head selection mechanism for wireless sensor networks. In Proceedings of the IEEE International Systems Conference (SysCon), Montreal, QC, Canada, 1–8 April 2017. [Google Scholar]
- Song, Q.; Nuaymi, L.; Lagrange, X. Survey of radio resource management issues and proposals for energy-efficient cellular networks that will cover billions of machines. EURASIP J. Wirel. Commun. Netw. 2016, 1, 140. [Google Scholar] [CrossRef]
- Kim, R.Y. Snoop based group communication scheme in cellular Machine-to-Machine communications. In Proceedings of the IEEE International Conference on Information and Communication Technology Convergence (ICCT), Jeju, Korea, 17–19 November 2010. [Google Scholar]
- Tsiropoulou, E.E.; Mitsis, G.; Papavassiliou, S. Interest-aware energy collection & resource management in machine to machine communications. Ad Hoc Netw. 2018, 68, 48–57. [Google Scholar]
- Tsiropoulou, E.E.; Paruchuri, S.T.; Baras, J.S. Interest, energy and physical-aware coalition formation and resource allocation in smart IoT applications. In Proceedings of the 51st Annual Conference on Information Sciences and Systems (CISS), Baltimore, MD, USA, 1–6 April 2017. [Google Scholar]
- Katsinis, G.; Tsiropoulou, E.E.; Papavassiliou, S. Joint Resource Block and Power Allocation for Interference Management in Device to Device Underlay Cellular Networks: A Game Theoretic Approach. Mob. Netw. Appl. 2017, 22, 539–551. [Google Scholar] [CrossRef]
- Tu, C.Y.; Ho, C.Y.; Huang, C.Y. Energy-Efficient Algorithms and Evaluations for Massive Access Management in Cellular Based Machine to Machine Communications. In Proceedings of the IEEE Vehicular Technology Conference (VTC Fall), San Francisco, CA, USA, 5–8 September 2011. [Google Scholar]
- Ho, C.Y.; Huang, C.Y. Energy-Saving Massive Access Control and Resource Allocation Schemes for M2M Communications in OFDMA Cellular Networks. IEEE Wirel. Commun. Lett. 2012, 3, 209–212. [Google Scholar] [CrossRef]
- Azari, A.; Miao, G. Energy-efficient MAC for cellular-based M2M communications. In Proceedings of the 2nd IEEE Global Conference on Signal and Information Processing, Atlanta, GA, USA, 3–5 December 2014; pp. 128–132. [Google Scholar]
- Guan, Z.; Li, J.; Wu, L.; Zhang, Y.; Wu, J.; Du, X. Achieving Efficient and Secure Data Acquisition for Cloud-supported Internet of Things in Smart Grid. IEEE Int. Things J. 2017, 4, 1934–1944. [Google Scholar] [CrossRef]
- Du, X.; Guizani, M.; Xiao, Y.; Chen, H.H. A Routing-Driven Elliptic Curve Cryptography based Key Management Scheme for Heterogeneous Sensor Networks. IEEE Trans. Wirel. Commun. 2009, 8, 1223–1229. [Google Scholar] [CrossRef]
- Cheng, Y.; Fu, X.; Du, X.; Luo, B.; Guizani, M. A lightweight live memory forensic approach based on hardware virtualization. Inf. Sci. 2017, 379, 23–41. [Google Scholar] [CrossRef]
- Hasan, M.; Hossain, E.; Niyato, D. Random access for machine-to-machine communication in LTE-advanced networks: Issues and approaches. IEEE Commun. Mag. 2013, 51, 86–93. [Google Scholar] [CrossRef]
- Dawaliby, S.; Bradai, A.; Pousset, Y. In depth performance evaluation of LTE-M for M2M communications. In Proceedings of the IEEE International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), New York, NY, USA, 1–8 May 2016. [Google Scholar]
- Zhang, X.; Wang, Y.; Wang, R. Group-based joint signaling and data resource allocation in MTC-underlaid cellular networks. Sci. China Inf. Sci. 2017, 60, 304. [Google Scholar] [CrossRef]
- Kim, D.M.; Sorensen, R.B.; Mahmood, K.O.; Osterbo, N.; Zanella, A.; Popovski, P. Data Aggregation and Packet Bundling of Uplink Small Packets for Monitoring Applications in LTE. IEEE Netw. 2017, 31, 32–38. [Google Scholar] [CrossRef]
- Dhillon, H.S.; Huang, H.C.; Viswanathan, H.; Valenzuela, R.A. On resource allocation for machine-to-machine (M2M) communications in cellular networks. In Proceedings of the 2012 IEEE Globecom Workshops (GLOBECOM), Anaheim, CA, USA, 3–7 December 2012. [Google Scholar]
- Polyanskiy, Y.; Poor, H.V.; Verdu, S. Channel Coding Rate in the Finite Blocklength Regime. IEEE Trans. Inf. Theory 2010, 56, 2307–2359. [Google Scholar] [CrossRef]
- Wei, C.H.; Bianchi, G.; Cheng, R.G. Modeling and Analysis of Random Access Channels With Bursty Arrivals in OFDMA Wireless Networks. IEEE Trans. Wirel. Commun. 2015, 14, 1940–1953. [Google Scholar] [CrossRef]
- Petrioli, C.; Nati, M.; Casari, P. ALBA-R: Load-Balancing Geographic Routing Around Connectivity Holes in Wireless Sensor Networks. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 529–539. [Google Scholar] [CrossRef]
- Ferdouse, L.; Anpalagan, A.; Misra, S. Congestion and overload control techniques in massive M2M systems: A survey. Trans. Emerg. Telecommun. Technol. 2017, 28, 21–37. [Google Scholar] [CrossRef]
- Rico-Alvarino, A.; Vajapeyam, M.; Xu, H. An overview of 3GPP enhancements on machine to machine communications. IEEE Commun. Mag. 2016, 54, 14–21. [Google Scholar] [CrossRef]
- Stefanovic, C.; Popovski, P. ALOHA Random Access that Operates as a Rateless Code. IEEE Trans. Commun. 2013, 61, 4653–4662. [Google Scholar] [CrossRef]
- Yang, X.; Venkata, K.R.; Bo, S.; Du, X.; Fei, H.; Michael, G. A survey of key management schemes in wireless sensor networks. Comput. Commun. 2007, 30, 2314–2341. [Google Scholar]
- Du, X.; Chen, H.H. Security in Wireless Sensor Networks. IEEE Wirel. Commun. Mag. 2008, 15, 60–66. [Google Scholar]
- Du, X.; Xiao, Y.; Guizani, M.; Chen, H.H. An effective key management scheme for heterogeneous sensor networks. Ad Hoc Netw. 2007, 5, 24–34. [Google Scholar] [CrossRef]
- Zhao, Y.; Huang, L.; Chi, T.Y. Capacity analysis for multiple-input multiple-output relay system in a low-rank line-of-sight environment. IET Commun. 2012, 6, 668–675. [Google Scholar] [CrossRef]
- Andrade, T.P.C.d.; Astudillo, C.A.; Sekijima, L.R.; da Fonseca, N.L.S. The Random Access Procedure in Long Term Evolution Networks for the Internet of Things. IEEE Commun. Mag. 2017, 55, 124–131. [Google Scholar] [CrossRef]


| Parameter | Notation |
|---|---|
| Bandwidth | |
| Channel gain | |
| Normal Device | |
| The cluster set | |
| The cluster head of the cluster | |
| Number of devices in the cell | |
| The transmission power of the Machine Type Communications (MTC) device | |
| The transmission power of the cluster header device on Resource Block (RB) | |
| The number of bits of the device data packet | |
| The total amount of data received by the cluster header device in the cluster and transmitted by the RB | |
| The link data rates of the device and the cluster header device | |
| The link data rates of the cluster header device and the base station | |
| The total energy consumption |
| Algorithm 1. Adaptive K-means Algorithm |
| 1: Input: ( is arbitrarily small) |
| 2: Mark all objects in data set as unprocessed |
| 3: for (each object in data set ) do |
| 4: if ( is clustered or marked as noise) |
| 5: continue; |
| 6: else if () |
| 7: Mark object as the border point; |
| 8: else |
| 9: Mark object as the core point, Create a cluster , Add all the object s in the to , ; |
| 10: for (Unprocessed object in the ) |
| 11: if () |
| 12: Add all the Objects in the which do not belong to any cluster to ; |
| 13: end for |
| 14: end if |
| 15: end if |
| 16: end for |
| 17: Get the position of the center of the initial cluster ; |
| 18: Calculate by the formula (7); |
| 19: Calculate by the formula (8), mark as ; |
| 20: if () |
| 21: , the new value mark as ; |
| 22: if () |
| 23: return step 26; |
| 24: else |
| 25: return step 18; |
| 26: if () |
| 27: move the object out of the cluster , , ; |
| 28: else |
| 29: end the algorithm; |
| 30: end if |
| 31: end if |
| 32: end if |
| 33: Output , |
| Parameter | Value |
|---|---|
| Traffic distribution parameter | |
| Cell radius | 1000 m |
| Number of devices | Variation (5000–30000) |
| Number of aggregation devices | Variation (depends on the algorithm) |
| Group arrival rate of the device | 1/10 |
| Grouping model | Periodic reporting of business models |
| PHY parameter | |
| Working frequency | 900 MHz |
| Transmit power of the base station | 30 dBm |
| Transmit power of the device | 23 dBm |
| The power density of thermal noise | −121.45 dBm/Hz |
| Target bit error rate of AMC | |
| MAC parameter | |
| Number of preambles | 54 |
| Backoff time | 20 subframe |
| Maximum number of retransmissions | 10 |
| System parameter | |
| System bandwidth | 1.4 MHz |
| Simulation time | subframe (10 s) |
| Algorithm parameter | |
| The maximum number of devices that trigger the algorithm | 27 |
| Maximum cluster radius | 300 m |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhao, Y.; Liu, K.; Xu, X.; Yang, H.; Huang, L. Distributed Dynamic Cluster-Head Selection and Clustering for Massive IoT Access in 5G Networks. Appl. Sci. 2019, 9, 132. https://doi.org/10.3390/app9010132
Zhao Y, Liu K, Xu X, Yang H, Huang L. Distributed Dynamic Cluster-Head Selection and Clustering for Massive IoT Access in 5G Networks. Applied Sciences. 2019; 9(1):132. https://doi.org/10.3390/app9010132
Chicago/Turabian StyleZhao, Yifeng, Kai Liu, Xueting Xu, Huayu Yang, and Lianfen Huang. 2019. "Distributed Dynamic Cluster-Head Selection and Clustering for Massive IoT Access in 5G Networks" Applied Sciences 9, no. 1: 132. https://doi.org/10.3390/app9010132
APA StyleZhao, Y., Liu, K., Xu, X., Yang, H., & Huang, L. (2019). Distributed Dynamic Cluster-Head Selection and Clustering for Massive IoT Access in 5G Networks. Applied Sciences, 9(1), 132. https://doi.org/10.3390/app9010132





