Remote-Sensing Image Encryption Algorithm Using the Advanced Encryption Standard
Abstract
1. Introduction
2. Theoretical Principle
2.1. AES
2.2. Chaotic System
2.3. Secure Hash Algorithm
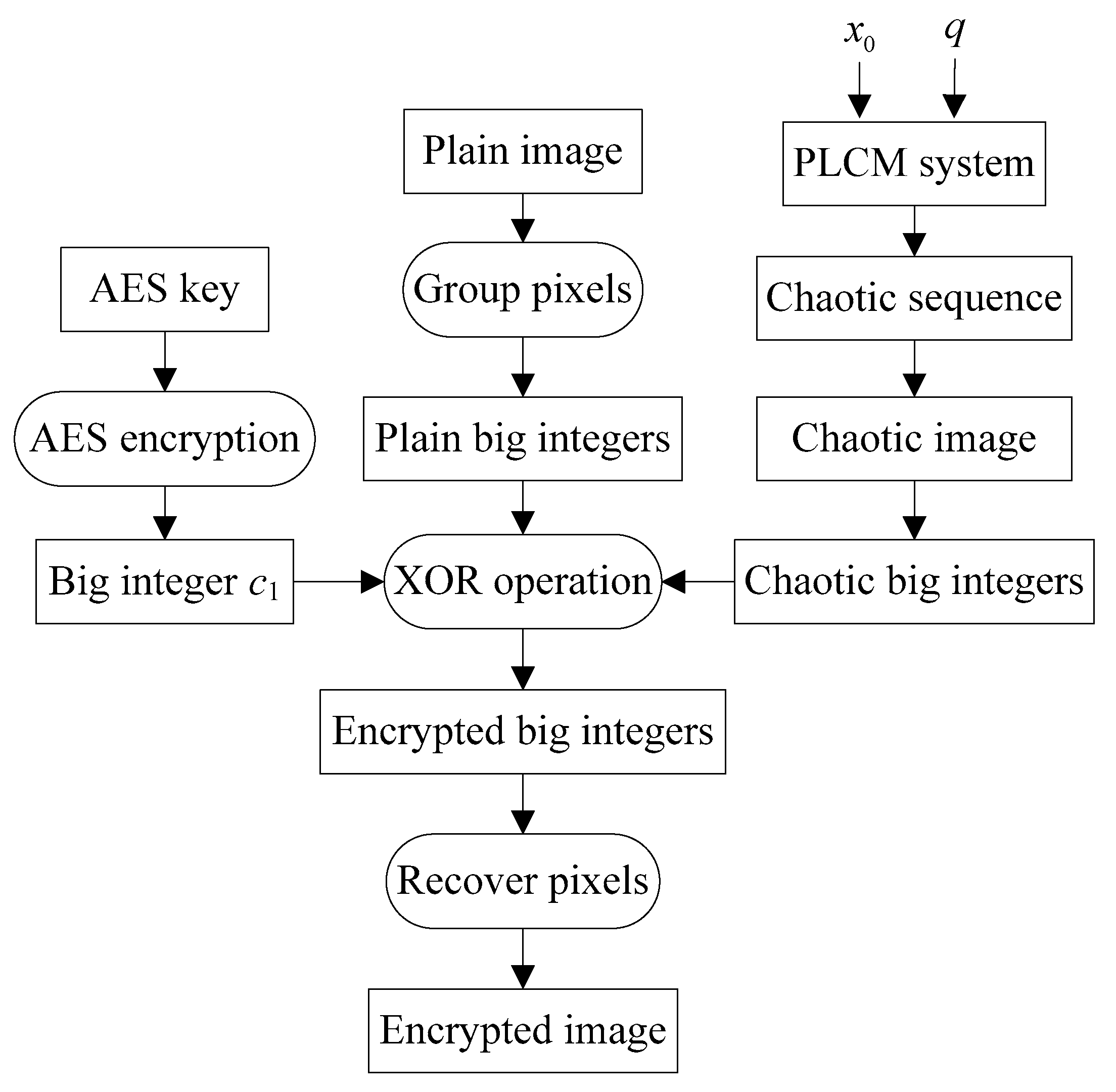
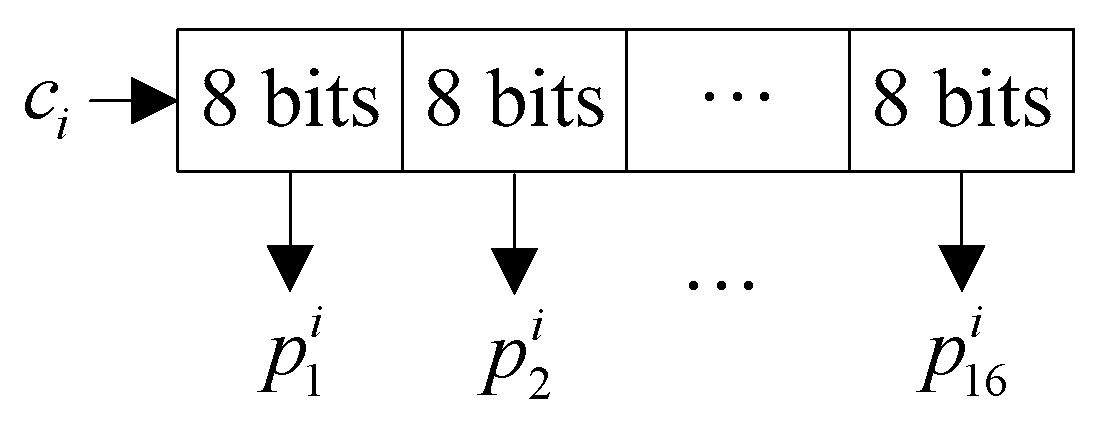
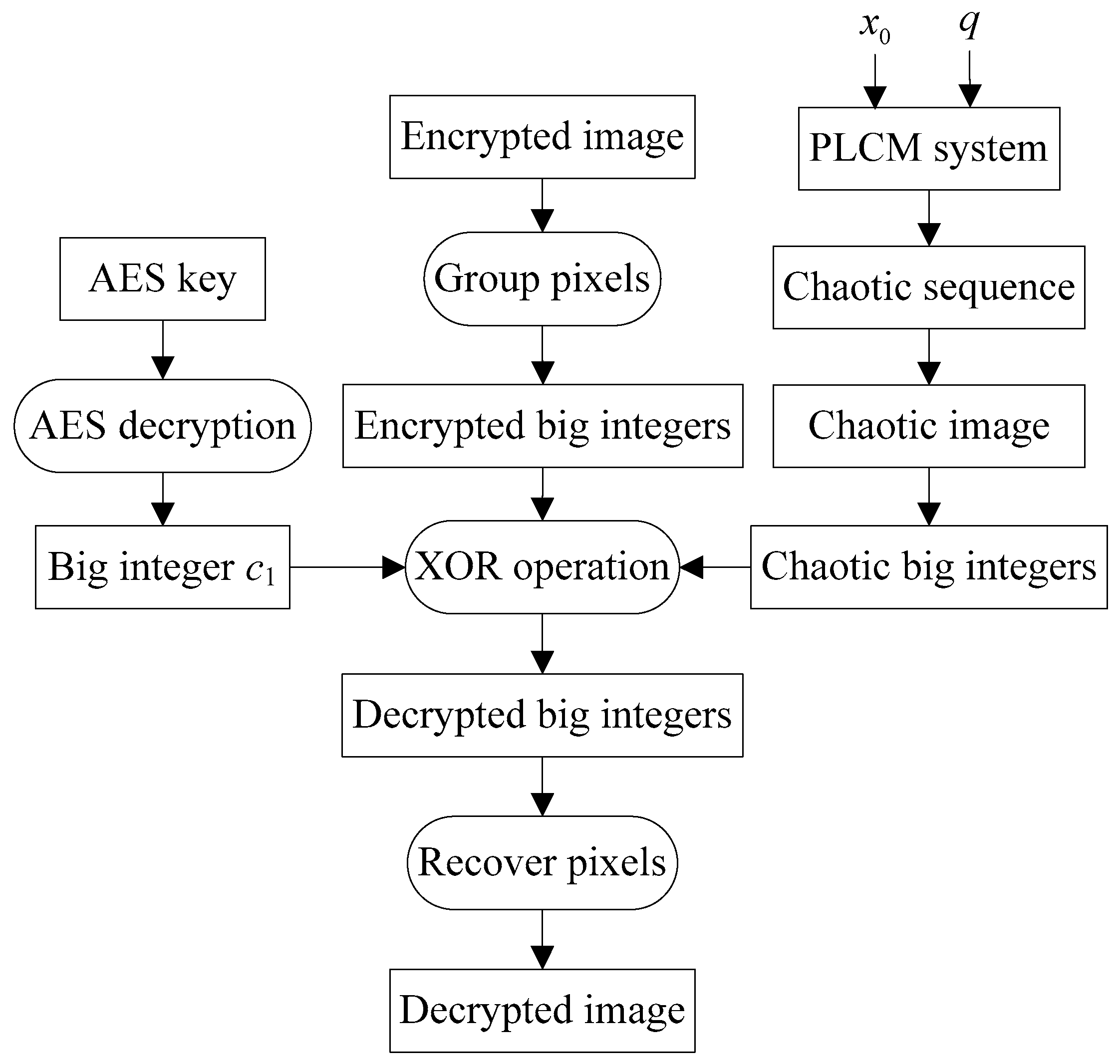
3. Proposed Image Encryption Algorithm
3.1. Sender’s Encryption Process
3.2. Recipient’s Decryption Process
4. Existing Similar Algorithms
4.1. Zhang’s Algorithm
4.2. Kalubandi’s Algorithm
4.3. Hraoui’s Algorithm
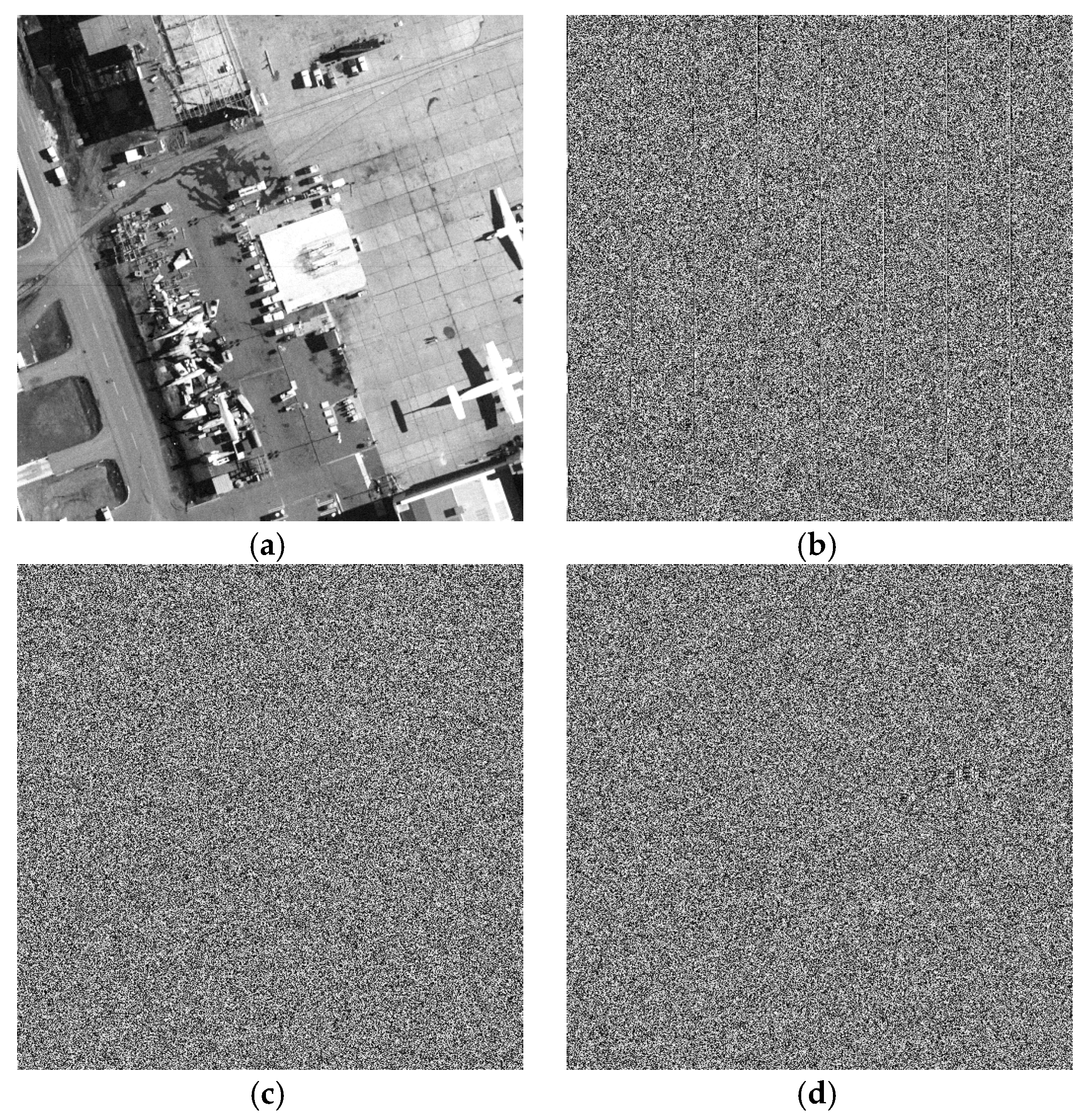
5. Experiments
6. Algorithm Analyses
6.1. Key Space Analysis
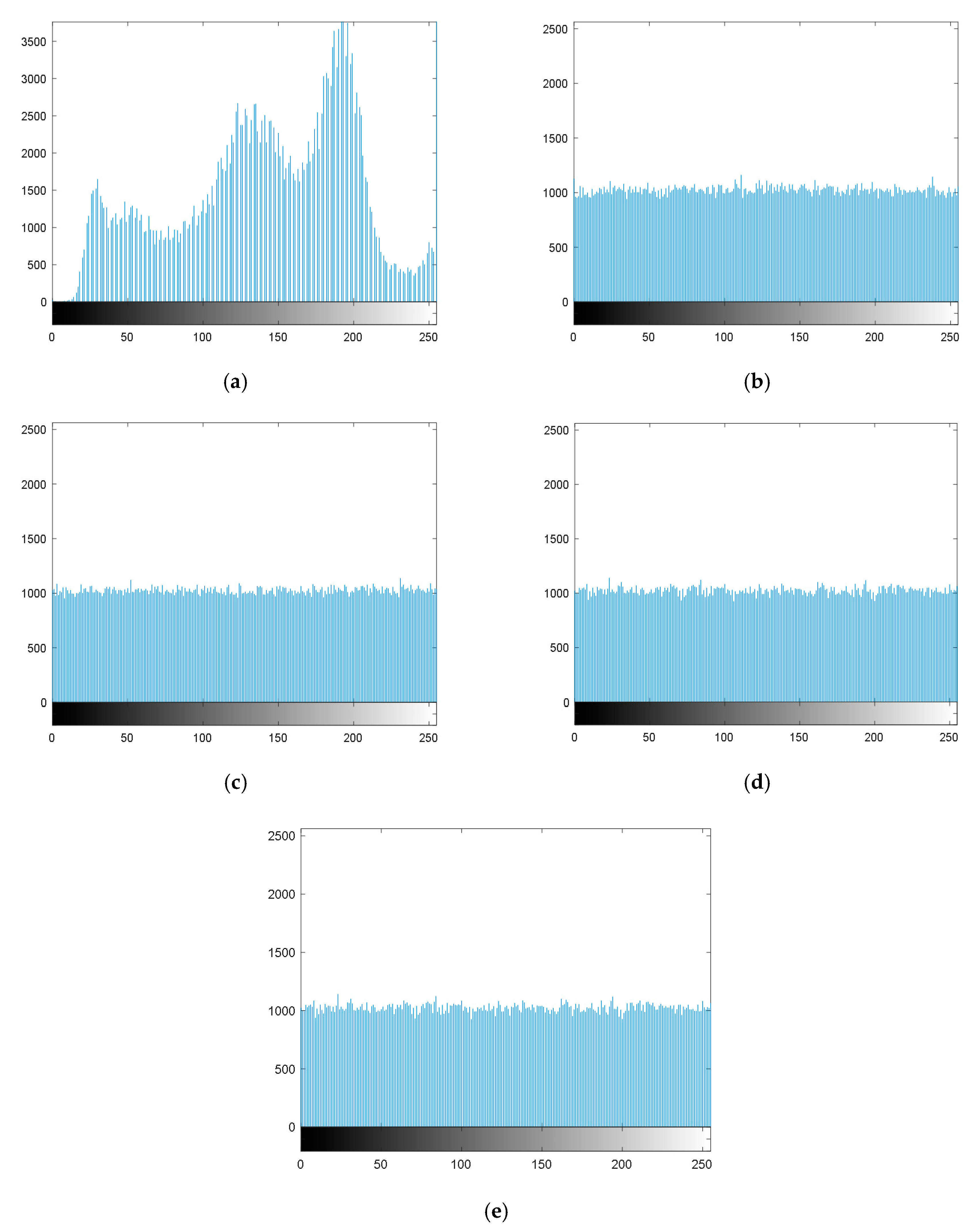
6.2. Histogram Analysis
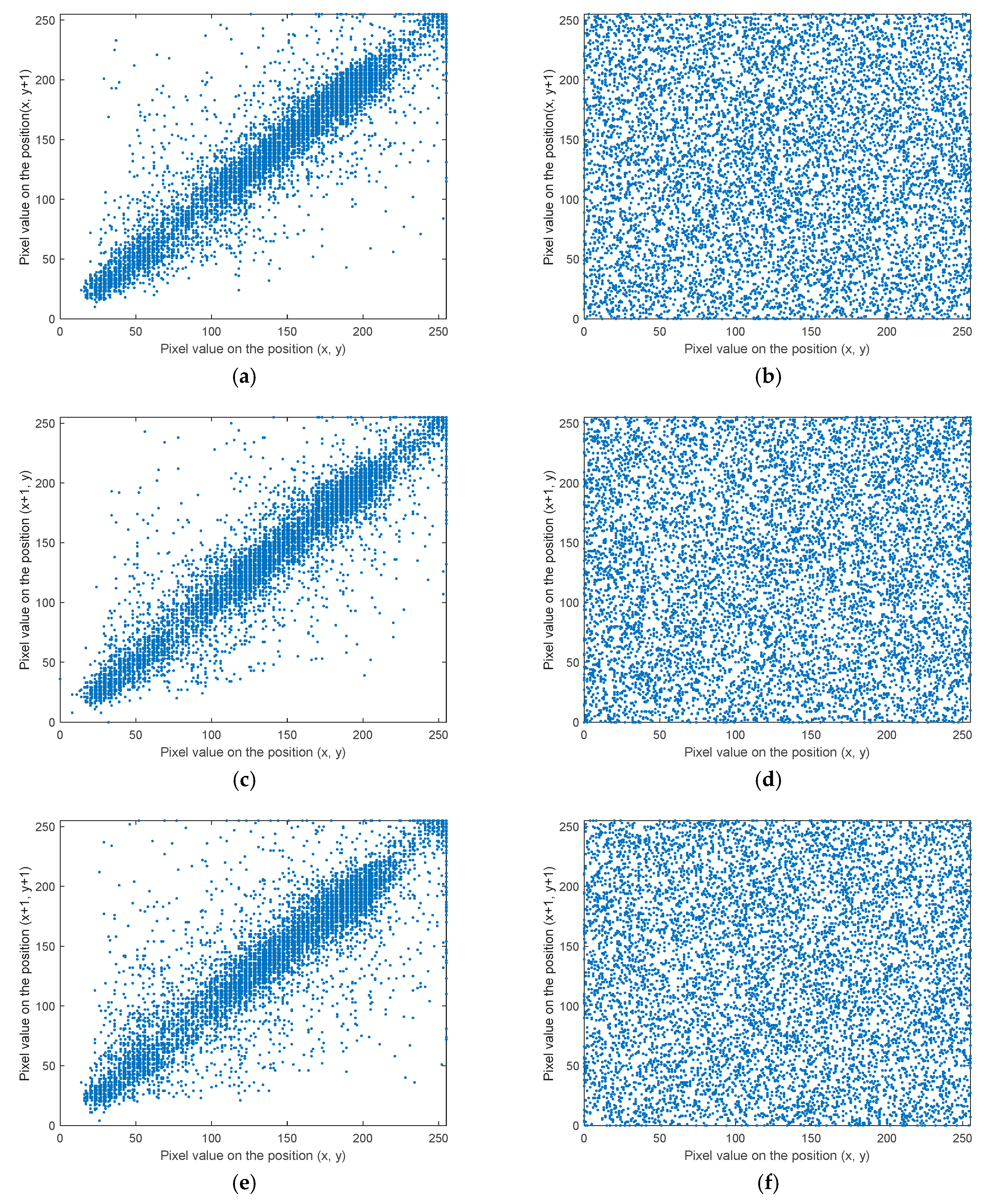
6.3. Correlation Analysis
6.4. Differential Attack Analysis
6.5. Information Entropy Analysis
6.6. Encryption Efficiency Analysis
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Huang, X.; Ye, G. An image encryption algorithm based on hyper-chaos and DNA sequence. Multimed. Tools Appl. 2014, 72, 57–70. [Google Scholar] [CrossRef]
- Chai, X.; Zheng, X.; Gan, Z.; Han, D.; Chen, Y. An image encryption algorithm based on chaotic system and compressive sensing. Signal Process. 2018, 148, 124–144. [Google Scholar] [CrossRef]
- Lan, R.; He, J.; Wang, S.; Gu, T.; Luo, X. Integrated chaotic systems for image encryption. Signal Process. 2018, 147, 133–145. [Google Scholar] [CrossRef]
- Parvaz, R.; Zarebnia, M. A combination chaotic system and application in color image encryption. Opt. Laser Technol. 2018, 101, 30–41. [Google Scholar] [CrossRef]
- Teng, L.; Wang, X.; Meng, J. A chaotic color image encryption using integrated bit-level permutation. Multimed. Tools Appl. 2018, 77, 6883–6896. [Google Scholar] [CrossRef]
- Liu, L.; Hao, S.; Lin, J.; Wang, Z.; Hu, X.; Miao, S. Image block encryption algorithm based on chaotic maps. IET Signal Process. 2018, 12, 22–30. [Google Scholar] [CrossRef]
- Pak, C.; Huang, L. A new color image encryption using combination of the 1D chaotic map. Signal Process. 2017, 138, 129–137. [Google Scholar] [CrossRef]
- Ran, Q.; Wang, L.; Ma, J.; Tan, L.; Yu, S. A quantum color image encryption scheme based on coupled hyper-chaotic Lorenz system with three impulse injections. Quantum Inf. Process. 2018, 17, 1–30. [Google Scholar] [CrossRef]
- Gong, L.; Deng, C.; Pan, S.; Zhou, N. Image compression-encryption algorithms by combining hyper-chaotic system with discrete fractional random transform. Opt. Laser Technol. 2018, 103, 48–58. [Google Scholar] [CrossRef]
- Zhang, J.; Hou, D.; Ren, H. Image encryption algorithm based on dynamic DNA coding and Chen’s hyperchaotic system. Math. Probl. Eng. 2016, 2016, 1–11. [Google Scholar] [CrossRef]
- Zhu, H.; Zhang, X.; Yu, H.; Zhao, C.; Zhu, Z. An image encryption algorithm based on compound homogeneous hyper-chaotic system. Nonlinear Dyn. 2017, 89, 61–79. [Google Scholar] [CrossRef]
- Zhang, X.; Nie, W.; Ma, Y.; Tian, Q. Cryptanalysis and improvement of an image encryption algorithm based on hyper-chaotic system and dynamic S-box. Multimed. Tools Appl. 2017, 76, 15641–15659. [Google Scholar] [CrossRef]
- Kaur, M.; Kumar, V. Efficient image encryption method based on improved Lorenz chaotic system. Electron. Lett. 2018, 54, 562–563. [Google Scholar] [CrossRef]
- Hua, Z.; Jin, F.; Xu, B.; Huang, H. 2D Logistic-Sine-coupling map for image encryption. Signal Process. 2018, 149, 148–161. [Google Scholar] [CrossRef]
- Zhang, Y.; Li, X.; Hou, W. A fast image encryption scheme based on AES. In Proceedings of the 2nd International Conference on Image, Vision and Computing (ICIVC), Chengdu, China, 2–4 June 2017; pp. 624–628. [Google Scholar]
- Daemen, J.; Rijmen, V. The Design of Rijndael: AES-The Advanced Encryption Standard; Springer: Heidelberg, Germany, 2013. [Google Scholar]
- Wang, X.; Xu, D. A novel image encryption scheme based on Brownian motion and PWLCM chaotic system. Nonlinear Dyn. 2015, 75, 345–353. [Google Scholar] [CrossRef]
- Guesmi, R.; Farah, M.A.B.; Kachouri, A.; Samet, M. A novel chaos-based image encryption using DNA sequence operation and Secure Hash Algorithm SHA-2. Nonlinear Dyn. 2015, 83, 1123–1136. [Google Scholar] [CrossRef]
- Kalubandi, V.K.P.; Vaddi, H.; Ramineni, V.; Loganathan, A. A novel image encryption algorithm using AES and visual cryptography. In Proceedings of the 2nd International Conference on Next Generation Computing Technologies (NGCT), Dehradun, India, 14–16 October 2016; pp. 808–813. [Google Scholar]
- Hraoui, S.; Gmira, F.; Jarar, A.O.; Satori, K.; Saaidi, A. Benchmarking AES and chaos based logistic map for image encryption. In Proceedings of the IEEE/ACS International Conference on Computer Systems and Applications (AICCSA), Ifrane, Morocco, 27–30 May 2013; pp. 1–4. [Google Scholar]
- Chai, X.; Chen, Y.; Broyde, L. A novel chaos-based image encryption algorithm using DNA sequence operations. Opt. Lasers Eng. 2017, 88, 197–213. [Google Scholar] [CrossRef]
- Belazi, A.; El-Latif, A.A.A.; Belghith, S. A novel image encryption scheme based on substitution-permutation network and chaos. Signal Process. 2016, 128, 155–170. [Google Scholar] [CrossRef]
- Tang, Z.; Zhang, X.; Lan, W. Efficient image encryption with block shuffling and chaotic map. Multimed. Tools Appl. 2015, 74, 5429–5448. [Google Scholar] [CrossRef]
- Wikipedia, The Free Encyclopedia: Base64. Available online: https://en.wikipedia.org/wiki/Base64 (accessed on 21 August 2018).

| Key Length | Block Size | Rounds |
|---|---|---|
| 128 | 128 | 10 |
| 192 | 128 | 12 |
| 256 | 128 | 14 |
| Variables | Values |
|---|---|
| K | B40608C3183BC9E3D9933DE8B4DB1366FA970574CD8C12D8D9AD0E7DCF37C0FE |
| x0 | 0.960784313725490 |
| q | 0.150980392156863 |
| K1 | 84AAC 12F54AB666ECFC2A83C676908C8BBC381B1F11EF5B2B433F3962493F52C |
| K2 | 1D7EB543FF740AA264768900CCD5120B787F41AE0F84B16941D6D7D58736B2F2 |
| K3 | 453CFC8A74A14B81F983F9294B817FCE3611DA5014041B1DD7175BEC79F94F1E |
| K4 | CA9A7C77EA9A03627B40A335FEC53098 |
| Directions | Horizontal | Vertical | Diagonal |
|---|---|---|---|
| Plain image | 0.9402 | 0.9423 | 0.9032 |
| The proposed algorithm | −0.0047 | 0.0025 | 0.0014 |
| Zhang’s algorithm | −0.0039 | 0.0022 | −0.0020 |
| Kalubandi’s algorithm | −0.0012 | 0.0007 | 0.0034 |
| Hraoui’s algorithm | −0.0026 | −0.0009 | 0.0007 |
| Algorithms | NPCR | UACI |
|---|---|---|
| The proposed algorithm | 99.62% | 33.38% |
| Zhang’s algorithm | 99.36% | 33.14% |
| Kalubandi’s algorithm | 0 | 0 |
| Hraoui’s algorithm | 0 | 0 |
| Algorithms | Entropy |
|---|---|
| The proposed algorithm | 7.9991 |
| Zhang’s algorithm | 7.9994 |
| Kalubandi’s algorithm | 7.9994 |
| Hraoui’s algorithm | 7.9991 |
| Algorithms | AES Encryption Times |
|---|---|
| Zhang’s algorithm | 16,384 |
| Kalubandi’s algorithm | 21,846 |
| Hraoui’s algorithm | 16,384 |
| The proposed algorithm | 1 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, X.; Wang, X. Remote-Sensing Image Encryption Algorithm Using the Advanced Encryption Standard. Appl. Sci. 2018, 8, 1540. https://doi.org/10.3390/app8091540
Zhang X, Wang X. Remote-Sensing Image Encryption Algorithm Using the Advanced Encryption Standard. Applied Sciences. 2018; 8(9):1540. https://doi.org/10.3390/app8091540
Chicago/Turabian StyleZhang, Xiaoqiang, and Xuesong Wang. 2018. "Remote-Sensing Image Encryption Algorithm Using the Advanced Encryption Standard" Applied Sciences 8, no. 9: 1540. https://doi.org/10.3390/app8091540
APA StyleZhang, X., & Wang, X. (2018). Remote-Sensing Image Encryption Algorithm Using the Advanced Encryption Standard. Applied Sciences, 8(9), 1540. https://doi.org/10.3390/app8091540






