Defeat Your Enemy Hiding behind Public WiFi: WiGuard Can Protect Your Sensitive Information from CSI-Based Attack †
Abstract
:1. Introduction
- In order to interfere with the attacker’s received CSI measurements, the channel spacing between the safe wireless transmitter and the target public AP should be one, and it can interfere with the target public AP to the greatest extent.
- In order not to interfere with the other normal public APs, the distance between the safe wireless transmitter and the normal public APs should be more than 4 m, and the longer the distance is, the smaller the impact will be on the normal public APs.
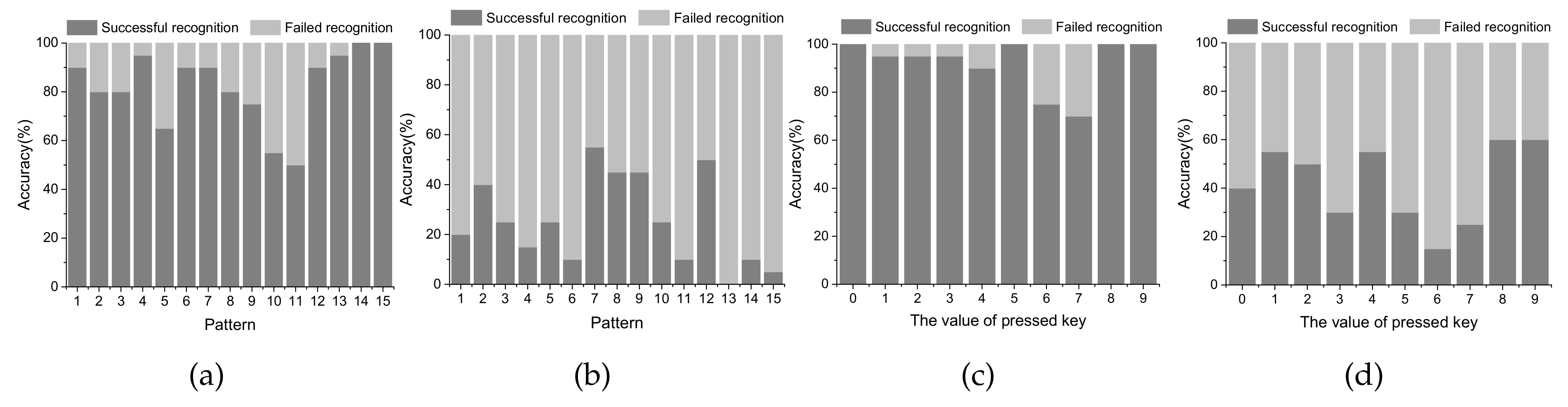
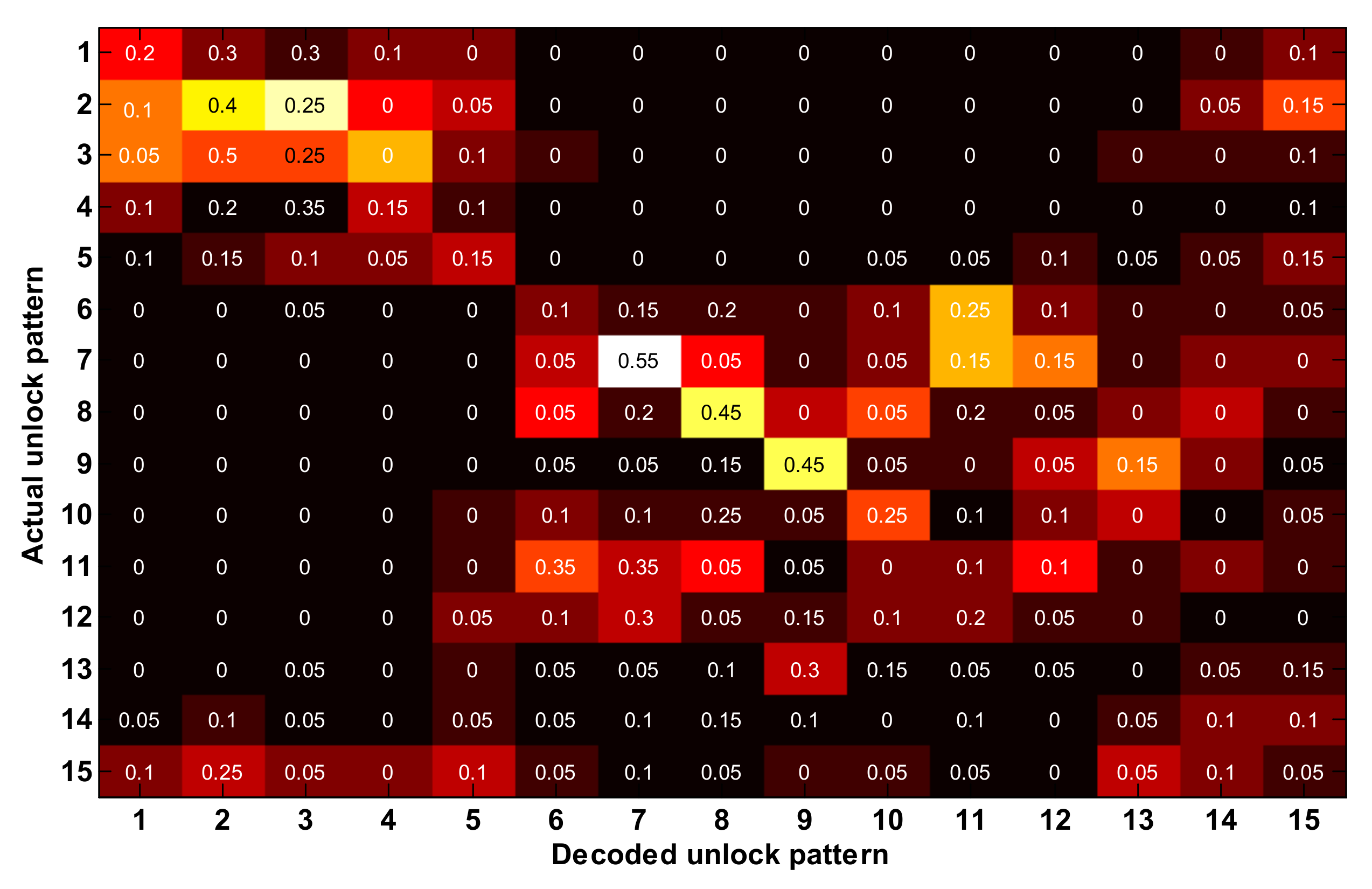
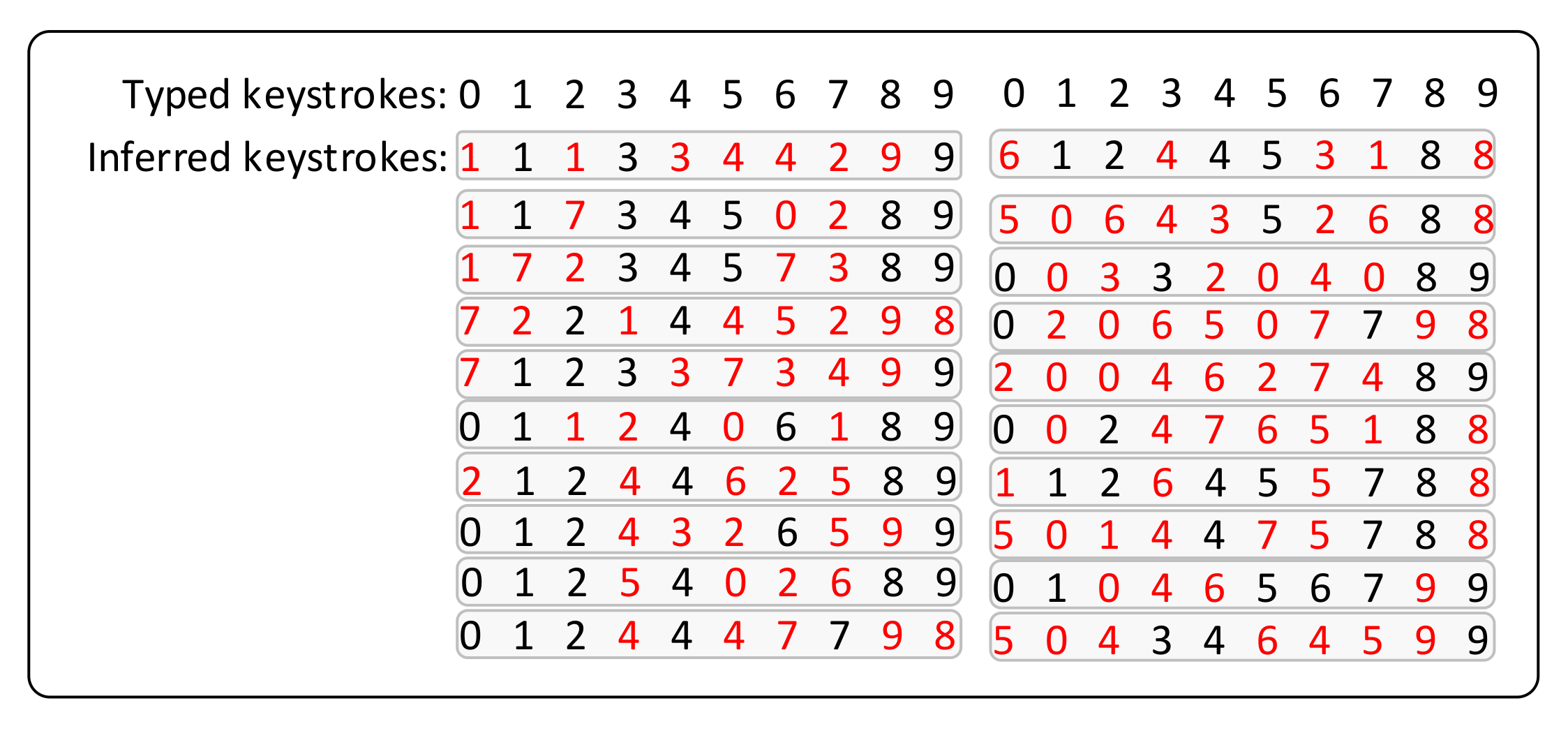
- The paper demonstrates that channel interference can defeat the CSI-based attack by recovering the unlock patterns for the smart phone and the keyboards of the PC. The attacker can achieve an accuracy of 82.33% and 92% respectively for patterns and keyboards when there exists no channel interference; and with channel interference, the recovery accuracy is respectively 21.67% and 42%.
- It analyzes the essence of the CSI-based attack and introduces a protection system to defeat it. To the best of our knowledge, we are the first to propose solutions for such an attack.
- It presents a channel interference protection system that exploits channel interference to defeat CSI-based attack. As a result, the design delivers a good protective effect, and the success rate of CSI-based attack decreases dramatically.
- It is a working system, and we have evaluated it in a real-word environment. The results demonstrate that the system does not influence the normal network service.
2. Related Work
2.1. CSI-Based Input Sensitive Information Recognition
2.2. Channel Interference
2.2.1. Interference between 802.11 Networks and Other Networks That Work on 2.4 GHz
- Interference mechanism/interference principle:Some research works focused on the interference mechanism/interference principle and tried to analyze the possible causes of interference appearing between different communication systems. For example, Yuan et al. [27] divided the interference between WiFi and ZigBee into four cases and analyzed whether there exists channel interference in these four cases. The study of the interference mechanism/interference principle will lay the foundation for the following two types of research works.
- Interference avoidance:The scheduling problem of spectrum resources is the essence of interference avoidance, and the core problem is how to allocate the spectrum resources in different communication systems to transmit data. Tytgat et al. [28] and Shi et al. [29] achieved interference avoidance between WiFi and ZigBee communication systems. Lee et al. [30] proposed a collaborative approach and a non-collaborative approach to solve the interference avoidance.
- Interference coexistence:When the spectrum resources are used, there will exist interference. How to make different communication systems coexist is a challenge. Yan et al. [31] achieved the coexistence of interference between WiFi and ZigBee, and Almeida et al. [32] achieved the coexistence of interference between WiFi and LTE.
2.2.2. Channel Interference in 802.11 Networks
3. Background
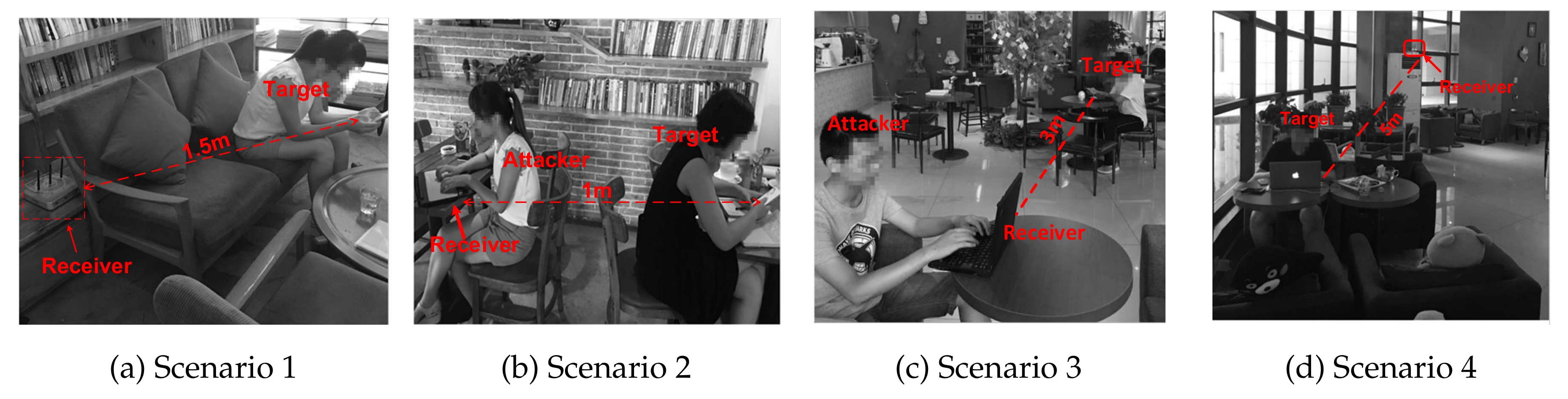
3.1. Threat Model
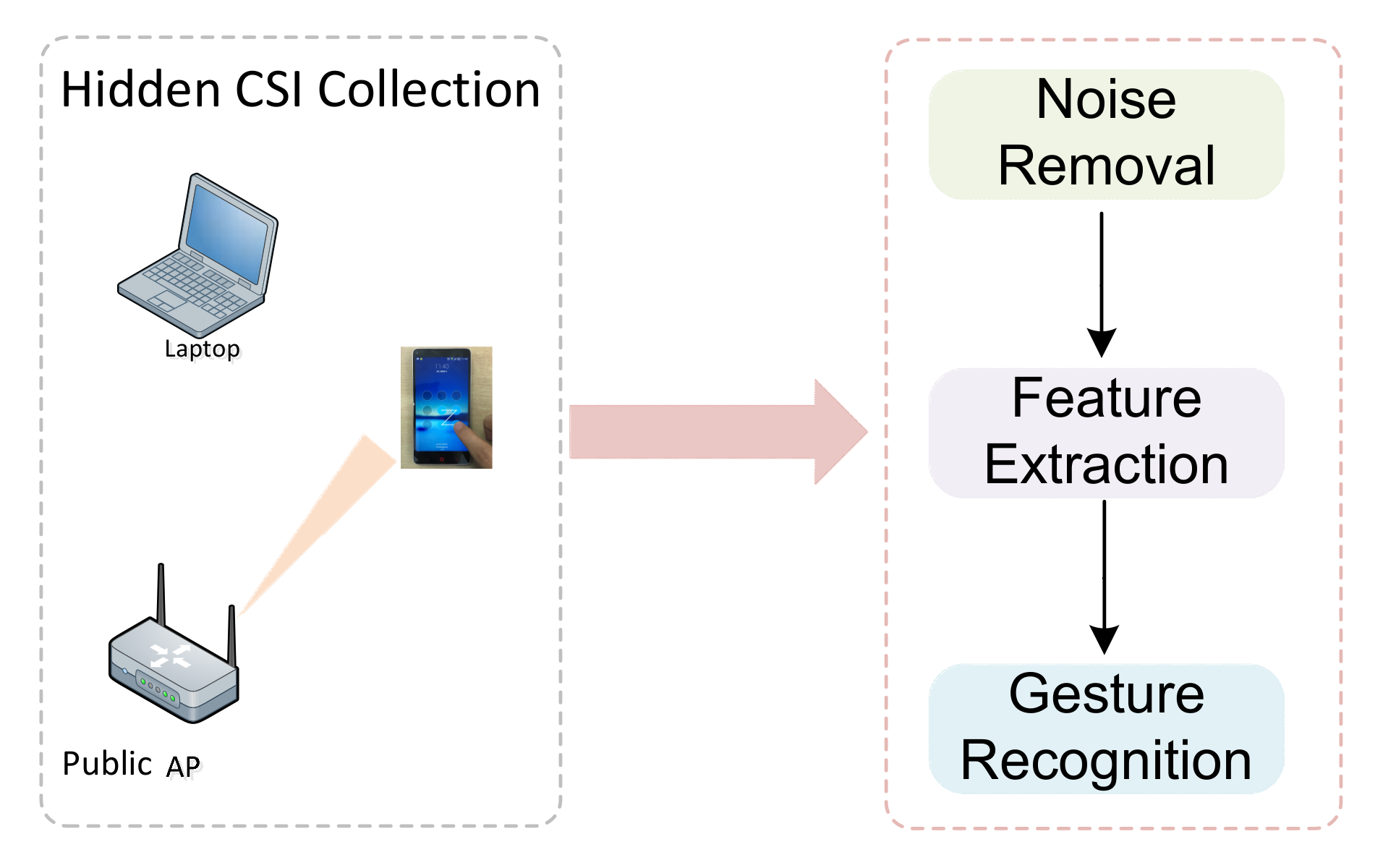
3.2. CSI-Based Attack
3.2.1. Overview of CSI
3.2.2. CSI-Based Input Sensitive Information Recovery Model
3.2.3. Requirements for CSI-Based Attack
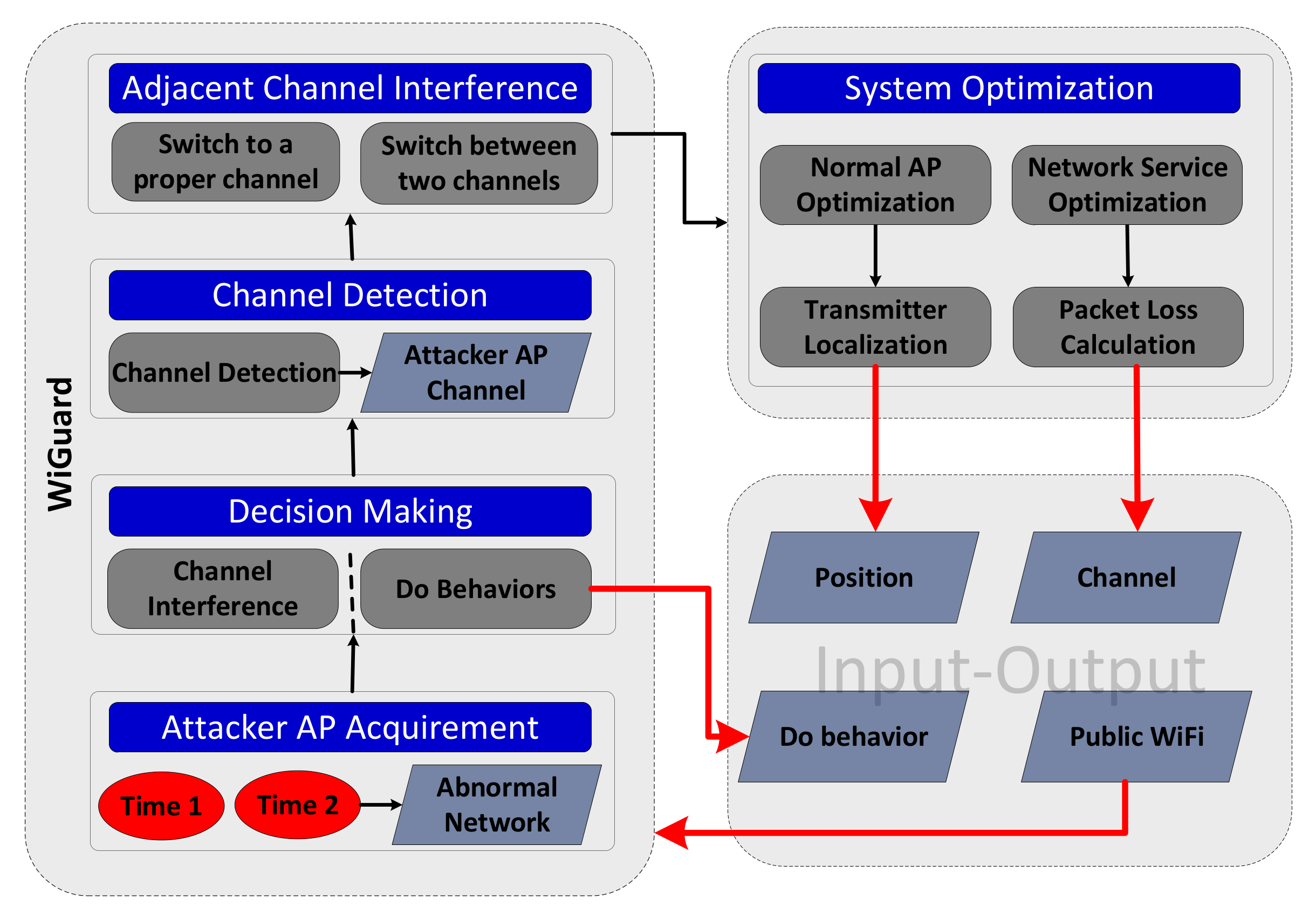
4. WiGuard Overview
4.1. Channel Interference
4.2. System Overview
5. ICMP-Based Attacker AP Detection
5.1. Attacker AP Characteristics
5.2. Attacker AP Detection
6. Adjacent Channel Interference
6.1. Safe Wireless Transmitter
6.2. Channel Switch
7. System Performance Optimization
7.1. System Optimization Model
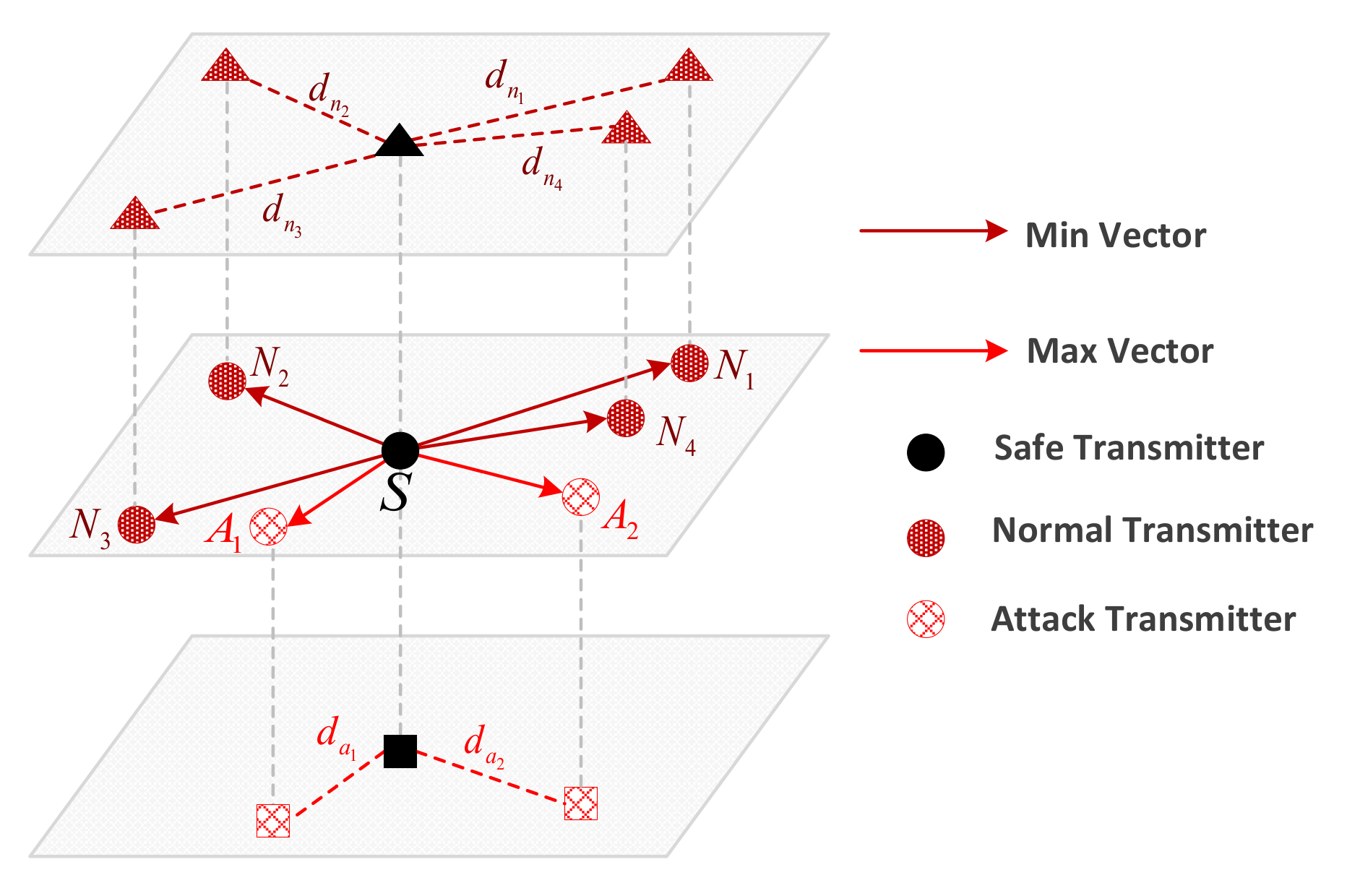
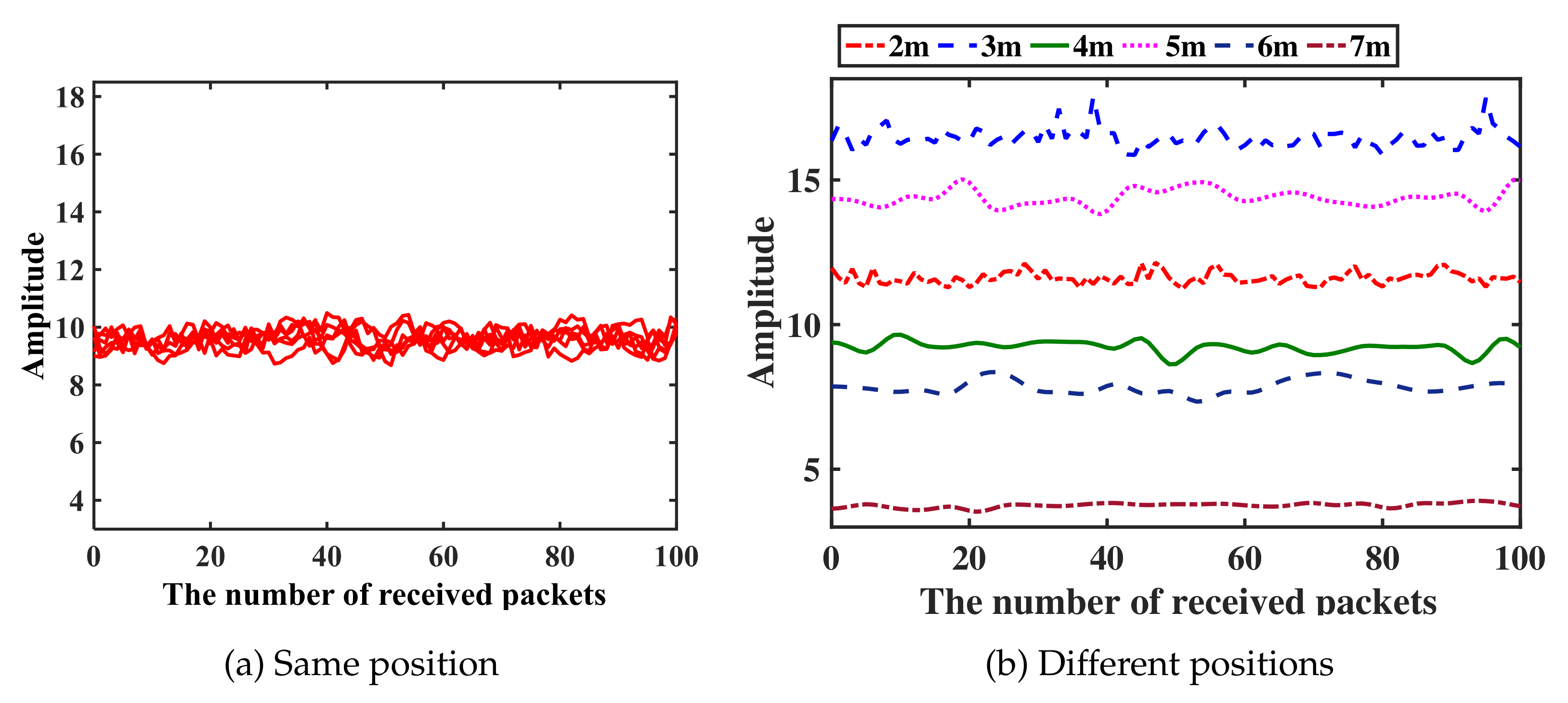
7.2. CSI-Based Localization for Wireless Transmitters
7.2.1. Noise Removal Using DWT
7.2.2. Dimension Reduction Using PCA
7.2.3. Location Using DTW and SVM
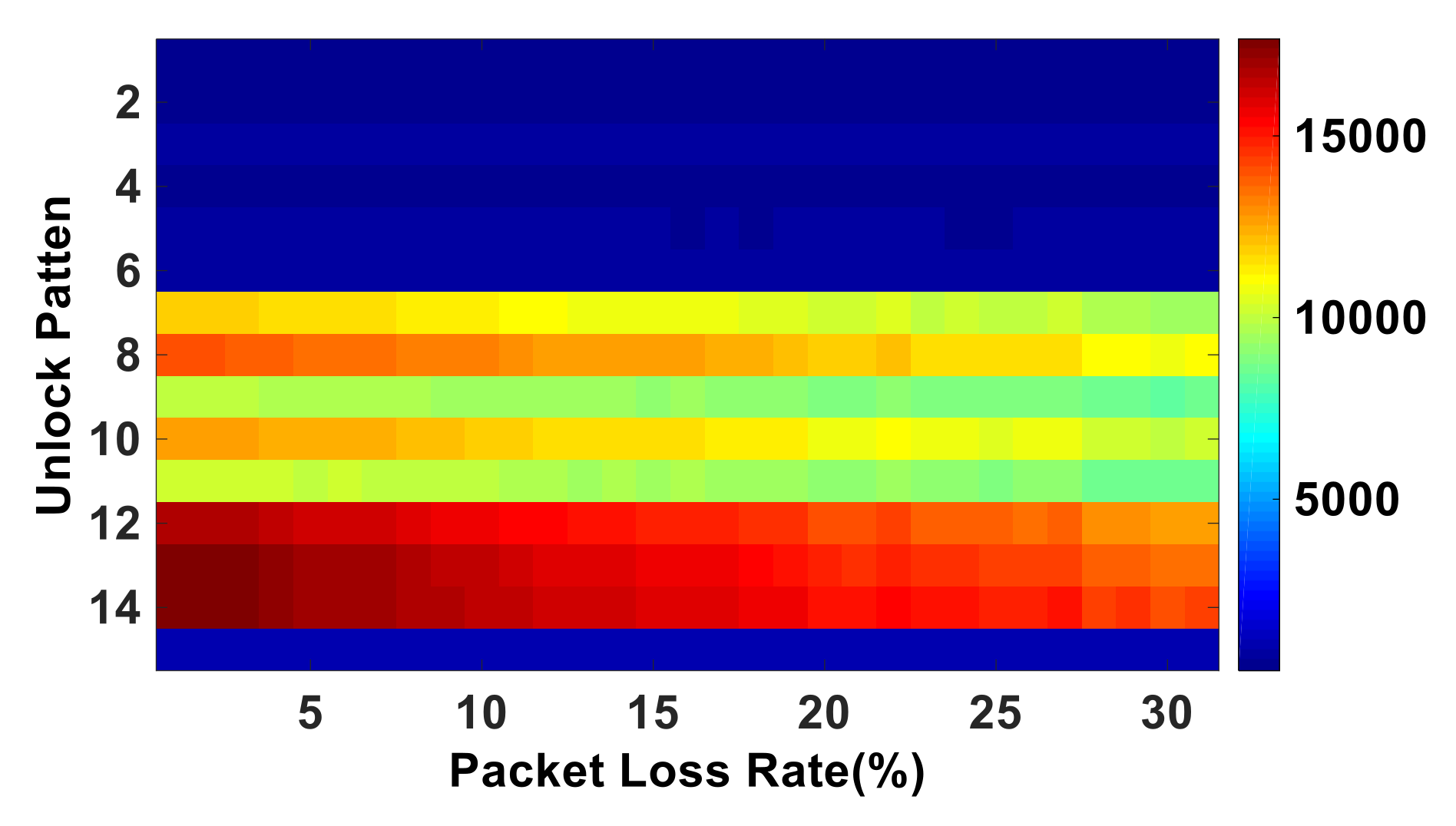
7.3. Packet Loss Rate Calculation
7.3.1. Packet Loss Rate (QoS)
7.3.2. Packet Loss Rate (CSI)
8. Implementation
8.1. Experimental Setup
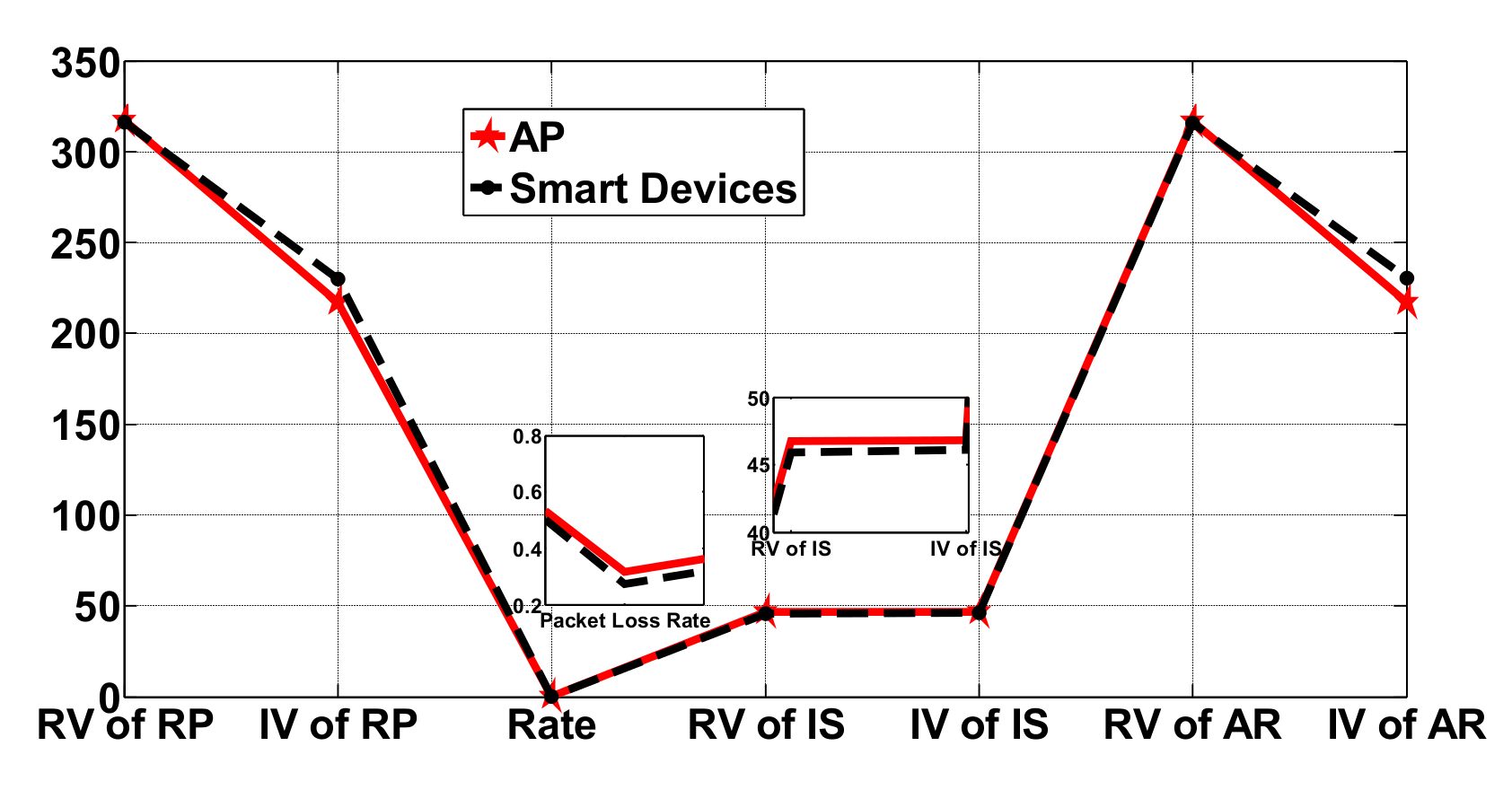
8.2. Parameters for Interference Evaluation
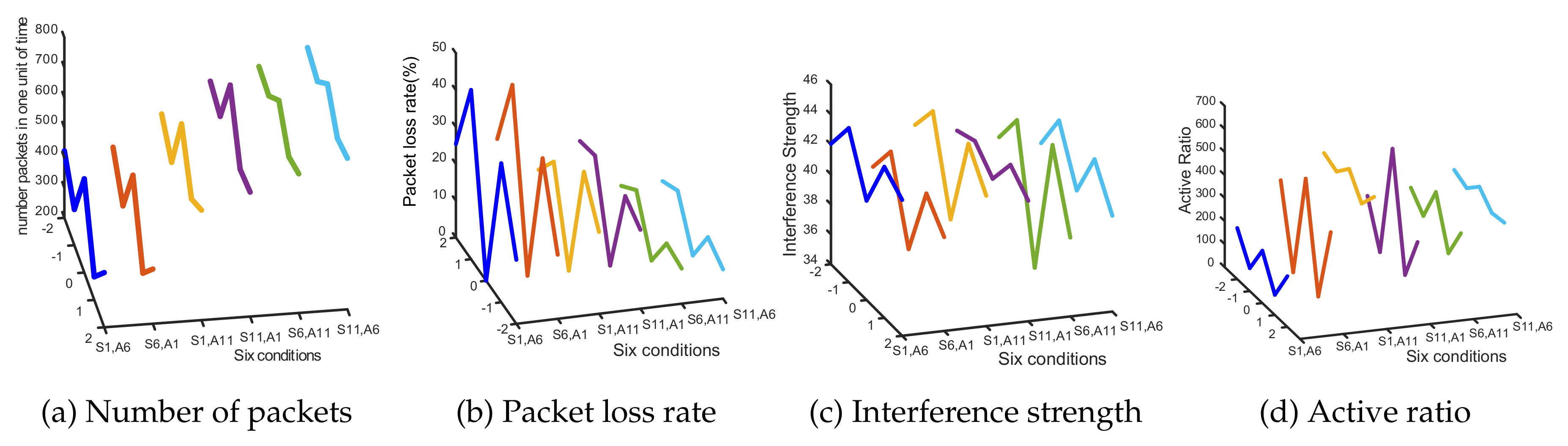
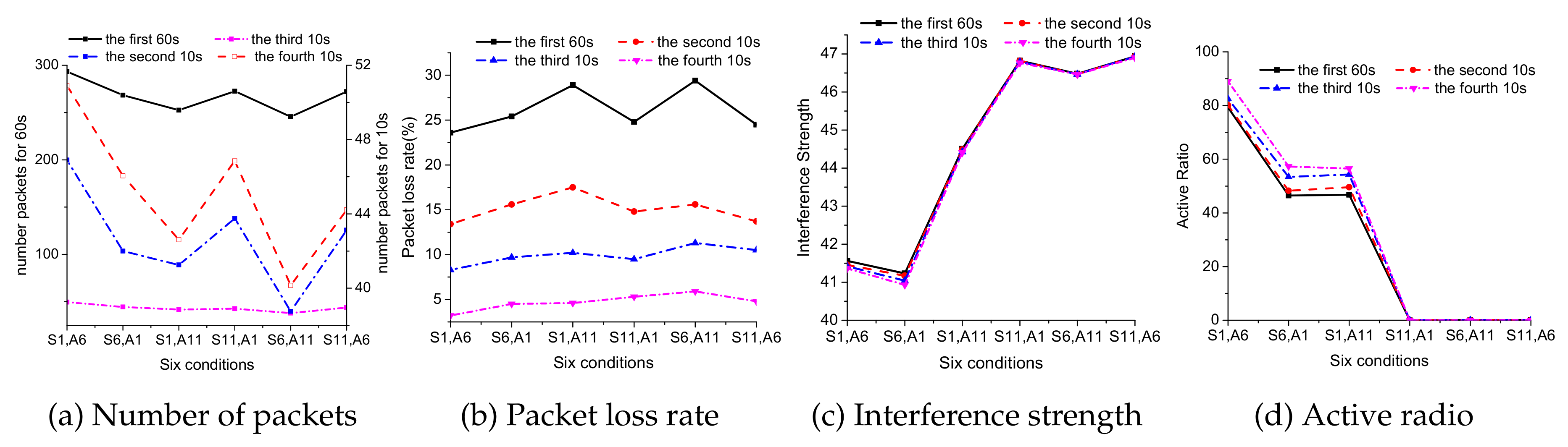
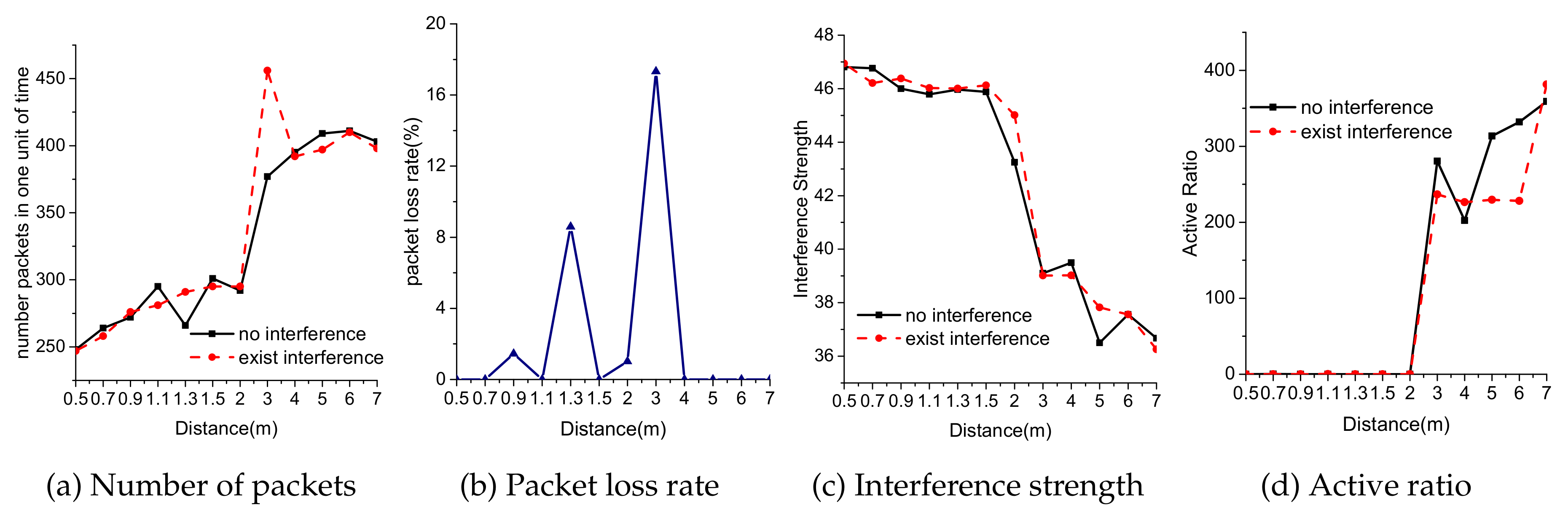
- The number of received packets:The parameters are obtained by actual experiments. What we have obtained is a sequence of CSI measurements, and the length of the sequence is the number of received packets.
- Packet loss rate:In the above equation, represents the reference number of received packets, and the packets are obtained when the safe wireless transmitter and target public APs work on different channels and there exists no channel interference between them. represents the interference number of received packets, and the packets are obtained when the safe wireless transmitter and the target public APs work on adjacent channels and there will exist adjacent channel interference between them. We assume that when the safe wireless transmitter and the target AP work on different channels and there exist no channel interference between them, the packet loss rate is zero.
- Interference strength:In the above equation, represents the RSSI value of the i-th packet from which the noise has been removed, and represents the reference number of the received packets. The value of represents the interference strength between the safe wireless transmitter and the target public AP; when the value of is greater, the interference strength between the safe wireless transmitter and the target public APs is stronger.
- Active ratio:In the above equation, represents the RSSI value of the i-th packet and represents the noise value of the i-th packets; when the value of is greater, the noise contained in the received packets is lower, and the channel interference between the safe wireless transmitter and the target public APs will be weaker.
9. Evaluation
9.1. Channel Interference on Public APs that the Attacker Leverages
9.1.1. Channel
9.1.2. Time
9.1.3. Different Wireless Transmitters
9.2. Channel Interference on Normal Public Wireless Transmitters
9.3. Case Study
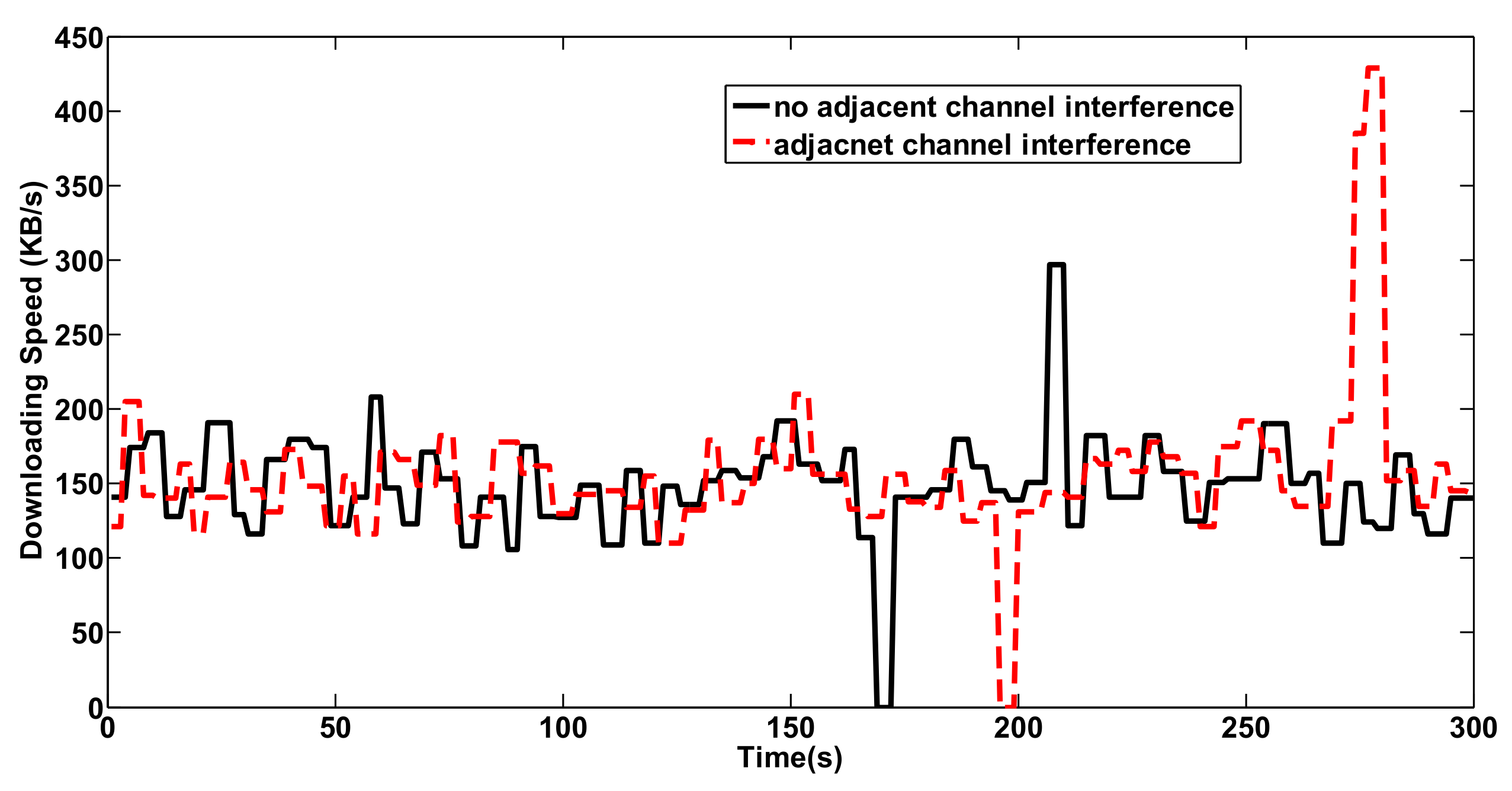
9.4. Channel Interference on the Network Service
10. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Abbreviations
| CSI | channel state information |
| PIN | personal identification number |
| AP | access point |
| COTS | commercial off-the-shelf |
| NIC | network interface controller |
| MIMO | multiple input multiple output |
| ICMP | Internet control messages protocol |
| PC | personal computer |
| USB | Universal Serial Bus |
| PCA | principal component analysis |
| DTW | dynamic time warping |
| KNN | k-nearest neighbor |
| NB | naive Bayesian |
| TCP | transmission control protocol |
| UDP | user datagram protocol |
| QoS | quality of service |
| RSS | received signal strength |
| SVM | support vector machine |
| OFDM | orthogonal frequency division multiplexing |
| RSSI | received signal strength indicator |
References
- Zhang, J.; Tang, Z.; Li, R.; Chen, X.; Gong, X.Q.; Fang, D.; Wang, Z. Protect Sensitive Information against Channel State Information Based Attacks. In Proceedings of the 2017 IEEE International Conference on Computational Science and Engineering, Guangzhou, China, 21–24 July 2017; pp. 203–210. [Google Scholar]
- William, R. Trumble. In Shorter Oxford English Dictionary, 6th ed.; Oxford University Press: Oxford, UK, 2007. [Google Scholar]
- Zhang, Y.; Xia, P.; Luo, J.; Ling, Z.; Liu, B.; Fu, X. Fingerprint attack against touch-enabled devices. In Proceedings of the ACM Workshop on Security and Privacy in Smartphones and Mobile Devices, Raleigh, NC, USA, 19 October 2012; pp. 57–68. [Google Scholar]
- Shukla, D.; Kumar, R.; Serwadda, A.; Phoha, V.V. Beware, Your Hands Reveal Your Secrets! In Proceedings of the ACM Sigsac Conference on Computer and Communications Security, Scottsdale, AZ, USA, 3–7 November 2014; pp. 904–917. [Google Scholar]
- Ali, K.; Liu, A.X.; Wang, W.; Shahzad, M. Keystroke recognition using wifi signals. In Proceedings of the 21st Annual International Conference on Mobile Computing and Networking, ACM, Paris, France, 7–11 September 2015; pp. 90–102. [Google Scholar]
- Zhang, J.; Zheng, X.; Tang, Z. Privacy Leakage in Mobile Sensing: Your Unlock Passwords Can Be Leaked through Wireless Hotspot Functionality. Mob. Inf. Syst. 2016, 2016. [Google Scholar] [CrossRef]
- Li, M.; Meng, Y.; Liu, J.; Zhu, H.; Liang, X.; Liu, Y.; Ruan, N. When CSI Meets Public WiFi: Inferring Your Mobile Phone Password via WiFi Signals. In Proceedings of the ACM Sigsac Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 1068–1079. [Google Scholar]
- Wang, G.; Zou, Y.; Zhou, Z. We can hear you with Wi-Fi! In Proceedings of the 20th Annual International Conference on Mobile Computing and Networking, Maui, HI, USA, 7–11 September 2014; pp. 593–604. [Google Scholar]
- Rouf, I.; Mustafa, H.; Xu, M. Neighborhood watch: Security and privacy analysis of automatic meter reading systems. ACM Conf. Comput. Commun. Secur. 2012, 462–473. [Google Scholar] [CrossRef]
- Wikipedia. Denial-Of-Service Attack. Available online: https://en.wikipedia.org/wiki/Denial-of-service_attack/ (accessed on 10 August 2016).
- Qiao, Y.; Zhang, O.; Zhou, W.; Srinivasan, K.; Arora, A. PhyCloak: Obfuscating sensing from communication signals. In Proceedings of the Usenix Conference on Networked Systems Design and Implementation, Santa Clara, CA, USA, 16–18 March 2016. [Google Scholar]
- Xu, R.; Shi, G.; Luo, J. Muzi: Multi-channel zigbee networks for avoiding wifi interference. In Proceedings of the 2011 International Conference on Internet of Things and 4th International Conference on Cyber, Physical and Social Computing, Dalian, China, 19–22 October 2011; pp. 323–329. [Google Scholar]
- Villegas, E.G.; Lopez-Aguilera, E.; Vidal, R. Effect of adjacent-channel interference in IEEE 802.11 WLANs. In Proceedings of the CrownCom 2007 2nd International Conference on Cognitive Radio Oriented Wireless Networks and Communications, Orlando, FL, USA, 1–3 August 2007; pp. 118–125. [Google Scholar]
- Mishra, A.; Banerjee, S.; Arbaugh, W. Weighted coloring based channel assignment for WLANs. ACM SIGMOBILE Mob. Comput. Commun. Rev. 2005, 9, 19–31. [Google Scholar] [CrossRef]
- Lee, Y.; Kim, K.; Choi, Y. Optimization of AP placement and channel assignment in wireless LANs. In Proceedings of the LCN 2002. 27th Annual IEEE Conference on Local Computer Networks, Tampa, FL, USA, 6–8 November 2002; pp. 831–836. [Google Scholar]
- Akl, R.; Arepally, A. Dynamic channel assignment in IEEE 802.11 networks. In Proceedings of the PORTABLE07 International Conference on Portable Information Devices, Orlando, FL, USA, 25–29 May 2007; pp. 1–5. [Google Scholar]
- Akella, A.; Judd, G.; Seshan, S. Self-management in chaotic wireless deployments. Wirel. Netw. 2007, 13, 737–755. [Google Scholar] [CrossRef]
- Cordeschi, N.; Amendola, D.; Shojafar, M.; Baccarelli, E. Distributed and adaptive resource management in Cloud-assisted Cognitive Radio Vehicular Networks with hard reliability guarantees. Veh. Commun. 2015, 2, 1–12. [Google Scholar] [CrossRef]
- Zahra, P.; Kang-Cheng, C.; Chia-Mu, Y.; Mauro, C. RARE: Defeating Side Channels based on Data-Deduplication in Cloud Storage. In Proceedings of the International Conference on Computer Communications: Cloud Computing Systems, Networks, and Applications (INFOCOM CCSNA), Honolulu, HI, USA, 15–19 April 2018; pp. 1–6. [Google Scholar]
- Nosrat-Makouei, B.; Andrews, J.G.; Heath, R.W. MIMO Interference Alignment Over Correlated Channels With Imperfect CSI. IEEE Trans. Signa Process. 2011, 59, 2783–2794. [Google Scholar] [CrossRef]
- Nauryzbayev, G.; Seilov, S. Impact of antenna correlation and imperfect csi on interference alignment in compound MIMO BC. In Proceedings of the International Conference on Information and Communication Technology Convergence, Jeju, Korea, 19–21 October 2016; pp. 544–548. [Google Scholar]
- Chen, X.; Yuen, C. On Interference Alignment With Imperfect CSI: Characterizations of Outage Probability, Ergodic Rate and SER. IEEE Trans. Veh. Technol. 2016, 65, 47–58. [Google Scholar] [CrossRef]
- Yu, H. A Review on Interference Alignment in Multiuser Interference Channels. Wirel. Pers. Commun. 2015, 83, 1751–1764. [Google Scholar] [CrossRef]
- Lau, V.K.N.; Rao, X.; Ruan, L. CSI Feedback Reduction for Mimo Interference Alignment. IEEE Trans. Signa Process. 2015, 61, 4428–4437. [Google Scholar]
- Zhang, J.; Lei, X.; Shi, J.; De, L. Simulation study and performance analysis on Zigbee system with CCI. In Proceedings of the Wireless and Optical Communication Conference, Chengdu, China, 21–23 May 2016; pp. 1–4. [Google Scholar]
- Backes, F.; Vacon, G.; Callahan, P.; Hawe, W.R.; Durand, R. Program for Adjusting Channel Interference between Access Points in a Wireless Network. U.S. Patent US7774013A1, 10 August 2010. [Google Scholar]
- Yuan, W.; Wang, X.; Linnartz, J.-P.M.G. A Coexistence Model of IEEE 802.15.4 and IEEE 802.11b/g. In Proceedings of the 2007 14th IEEE Symposium on Communications and Vehicular Technology in the Benelux, Delft, The Netherlands, 15 November 2007; pp. 1–5. [Google Scholar]
- Tytgat, L.; Yaron, O.; Pollin, S. Analysis and experimental verification of frequency-based interference avoidance mechanisms in IEEE 802.15. 4. Netw. IEEE/ACM Trans. 2015, 23, 369–382. [Google Scholar] [CrossRef]
- Shi, G.; Xu, R.; Shu, Y. Exploiting temporal and spatial variation for WiFi interference avoidance in ZigBee networks. Int. J. Sens. Netw. 2015, 18, 204–216. [Google Scholar] [CrossRef]
- Lee, L.; Kang, G.; Zhang, X. An interference avoidance strategy for zigbee based WeHealth monitoring system. In Proceedings of the IEEE, International Conference on E-Health Networking, Applications and Services, Beijing, China, 10–13 October 2012; pp. 68–72. [Google Scholar]
- Yan, Y.; Yang, P.; Li, X.Y. Wizbee: Wise zigbee coexistence via interference cancellation with single antenna. Mob. Comput. IEEE Trans. 2015, 14, 2590–2603. [Google Scholar] [CrossRef]
- Almeida, E.; Cavalcante, A.M.; Paiva, R.C.D. Enabling LTE/WiFi coexistence by LTE blank subframe allocation. In Proceedings of the 2013 IEEE International Conference on Communications (ICC), Budapest, Hungary, 9–13 June 2013; pp. 5083–5088. [Google Scholar]
- Zubow, A.; Sombrutzki, R. Adjacent channel interference in IEEE 802.11n. In Proceedings of the 2012 IEEE Wireless Communications and Networking Conference (WCNC), Shanghai, China, 1–4 April 2012; pp. 1163–1168. [Google Scholar]
- Tan, W.L.; Bialkowski, K.; Portmann, M. Evaluating Adjacent Channel Interference in IEEE 802.11 Networks. In Proceedings of the IEEE Vehicular Technology Conference, Taipei, Taiwan, 16–19 May 2010; pp. 1–5. [Google Scholar]
- Xiao, J.; Wu, K.; Yi, Y. Pilot: Passive device-free indoor localization using channel state information. In Proceedings of the 2013 IEEE 33rd International Conference on Distributed Computing Systems (ICDCS), Philadelphia, PA, USA, 8–11 July 2013; pp. 236–245. [Google Scholar]
- Abdel-Nasser, H.; Samir, R.; Sabek, I.; Youssef, M. MonoPHY: Mono-stream-based device-free WLAN localization via physical layer information. In Proceedings of the Wireless Communications and Networking Conference (WCNC), Shanghai, China, 7–10 April 2013; pp. 4546–4551. [Google Scholar]
- Draft, W.G. Telecommunications and Information Exchange Between Systems-LAN/MAN Specific Requirements-Part 11: Wireless Medium Access Control (MAC) and Physical Layer (PHY) Specification: Specification for Radio Resource Measurement; IEEE Stdandard: Piscataway, NJ, USA, 2003. [Google Scholar]
- Angelakis, V.; Papadakis, S.; Siris, V.A.; Traganitis, A. Adjacent channel interference in 802.11a is harmful: Testbed validation of a simple quantification model. Commun. Mag. IEEE 2011, 49, 160–166. [Google Scholar] [CrossRef]
- Chieochan, S.; Hossain, E.; Diamond, J. Channel assignment schemes for infrastructure-based 802.11 WLANs: A survey. IEEE Commun. Surv. Tutor. 2010, 12, 124–136. [Google Scholar] [CrossRef]
- Sin, T.W.; Halim, M.N.; Naredula, J.R.; Fang, M.H.; Payne, K. Quality of Transmission across Packet-Based Networks. U.S. Patent US20020051464A1, 2 May 2002. [Google Scholar]
- Abdelnasser, H.; Youssef, M.; Harras, K.A. Wigest: A ubiquitous wifi-based gesture recognition system. In Proceedings of the 2015 IEEE Conference on Computer Communications (INFOCOM), Kowloon, Hong Kong, China, 26 April–1 May 2015; pp. 1472–1480. [Google Scholar]
- Wang, J.; Xie, B.; Fang, D.; Chen, X.; Liu, C.; Xing, T.; Nie, W. Accurate Device-Free Localization with Little Human Cost. In Proceedings of the 1st International Workshop on Experiences with the Design and Implementation of Smart Objects, Paris, France, 7 September 2015; pp. 55–60. [Google Scholar]
- Chang, C.C.; Lin, C.J. LIBSVM: A library for support vector machines. ACM Trans. Intell. Syst. Technol. 2011, 2, 1–27. [Google Scholar] [CrossRef]
- Wang, W.; Liu, A.X.; Shahzad, M. Gait recognition using wifi signals. In Proceedings of the ACM International Joint Conference on Pervasive and Ubiquitous Computing, Heidelberg, Germany, 12–16 September 2016; pp. 363–373. [Google Scholar]
- Borella, M.S.; Swider, D.; Uludag, S.; Brewster, G.B. Internet Packet Loss: Measurement and Implications for End-to-End QoS. In Proceedings of the International Conference on Parallel Processing Workshops, Minneapolis, MN, USA, 14 August 1998; pp. 3–12. [Google Scholar]
- Zhao, L.; Fan, C. Enhancement of QoS differentiation over IEEE 802.11 WLAN. Commun. Lett. IEEE 2004, 8, 494–496. [Google Scholar] [CrossRef]
- Halperin, D.; Hu, W.; Sheth, A.; Wetherall, D. Linux 802.11n CSI Tool. Available online: http://dhalperi.github.io/linux-80211n-csitool/ (accessed on 20 March 2017).
- Zhang, Z.L.; Chen, H.M.; Huang, T.P. A channel allocation scheme to mitigate Wifi interference for wireless sensor networks. Jisuanji Xuebao (Chin. J. Comput.) 2012, 35, 504–517. [Google Scholar] [CrossRef]
- H3C, The Leader in Digital Solution. H3C Corp. Available online: http://www.h3c.com.hk (accessed on 10 April 2017.).
- Uellenbeck, S.; Dürmuth, M.; Wolf, C.; Holz, T. Quantifying the security of graphical passwords: The case of android unlock patterns. In Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013; pp. 161–172. [Google Scholar]

© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, J.; Li, M.; Tang, Z.; Gong, X.; Wang, W.; Fang, D.; Wang, Z. Defeat Your Enemy Hiding behind Public WiFi: WiGuard Can Protect Your Sensitive Information from CSI-Based Attack. Appl. Sci. 2018, 8, 515. https://doi.org/10.3390/app8040515
Zhang J, Li M, Tang Z, Gong X, Wang W, Fang D, Wang Z. Defeat Your Enemy Hiding behind Public WiFi: WiGuard Can Protect Your Sensitive Information from CSI-Based Attack. Applied Sciences. 2018; 8(4):515. https://doi.org/10.3390/app8040515
Chicago/Turabian StyleZhang, Jie, Meng Li, Zhanyong Tang, Xiaoqing Gong, Wei Wang, Dingyi Fang, and Zheng Wang. 2018. "Defeat Your Enemy Hiding behind Public WiFi: WiGuard Can Protect Your Sensitive Information from CSI-Based Attack" Applied Sciences 8, no. 4: 515. https://doi.org/10.3390/app8040515
APA StyleZhang, J., Li, M., Tang, Z., Gong, X., Wang, W., Fang, D., & Wang, Z. (2018). Defeat Your Enemy Hiding behind Public WiFi: WiGuard Can Protect Your Sensitive Information from CSI-Based Attack. Applied Sciences, 8(4), 515. https://doi.org/10.3390/app8040515





