Interpolating Spline Curve-Based Perceptual Encryption for 3D Printing Models
Abstract
:1. Introduction
2. Related Works
2.1. 3D Model Security
2.2. 3D Triangle Mesh-Based Encryption
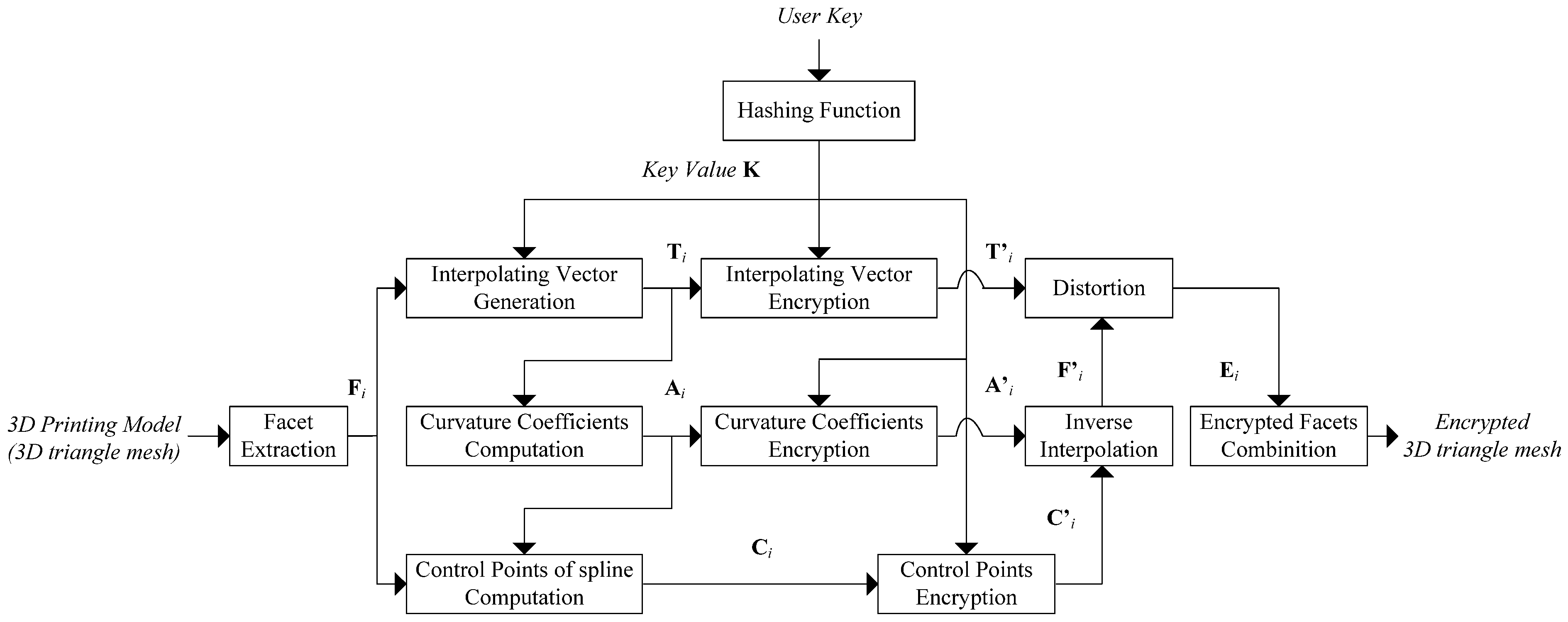
3. The Proposed Algorithm
3.1. Overview
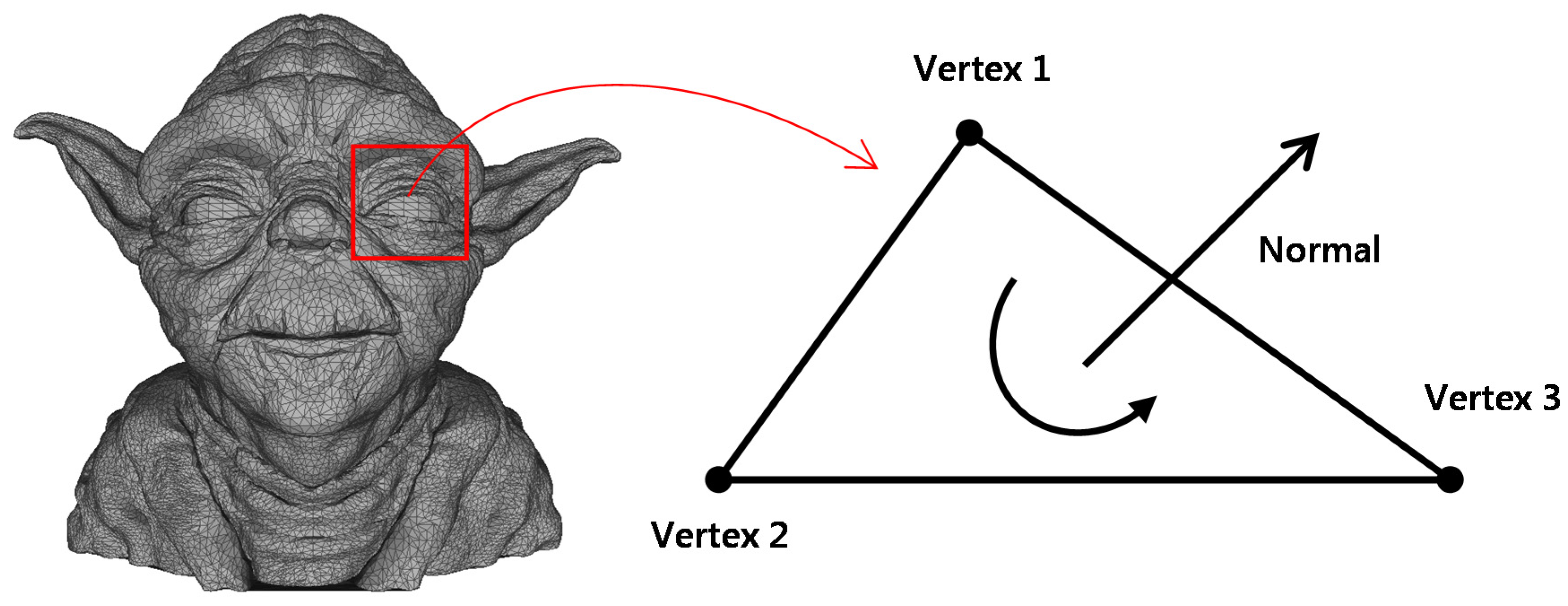
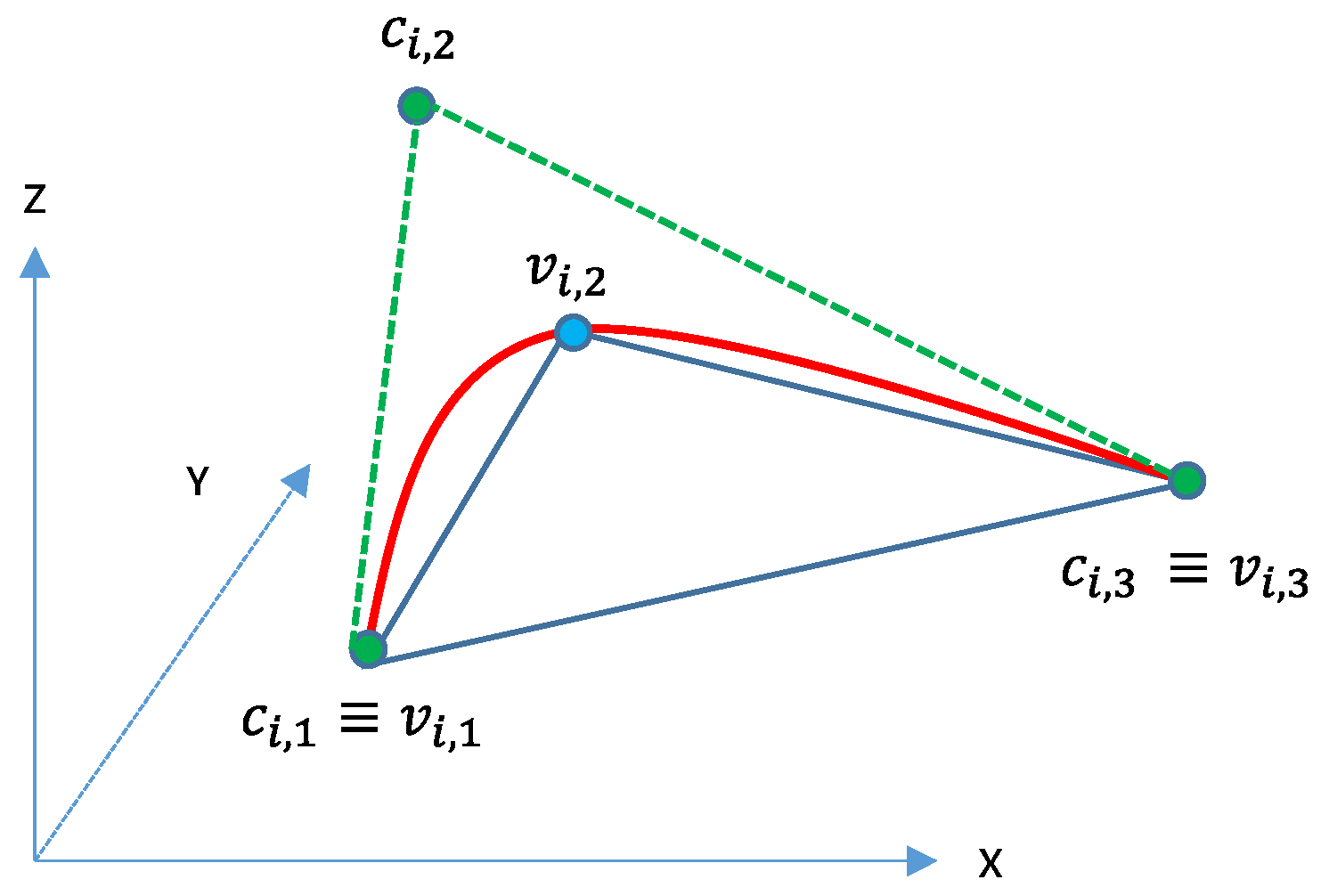
3.2. Features of the Interpolating Spline Curve in 3D Space
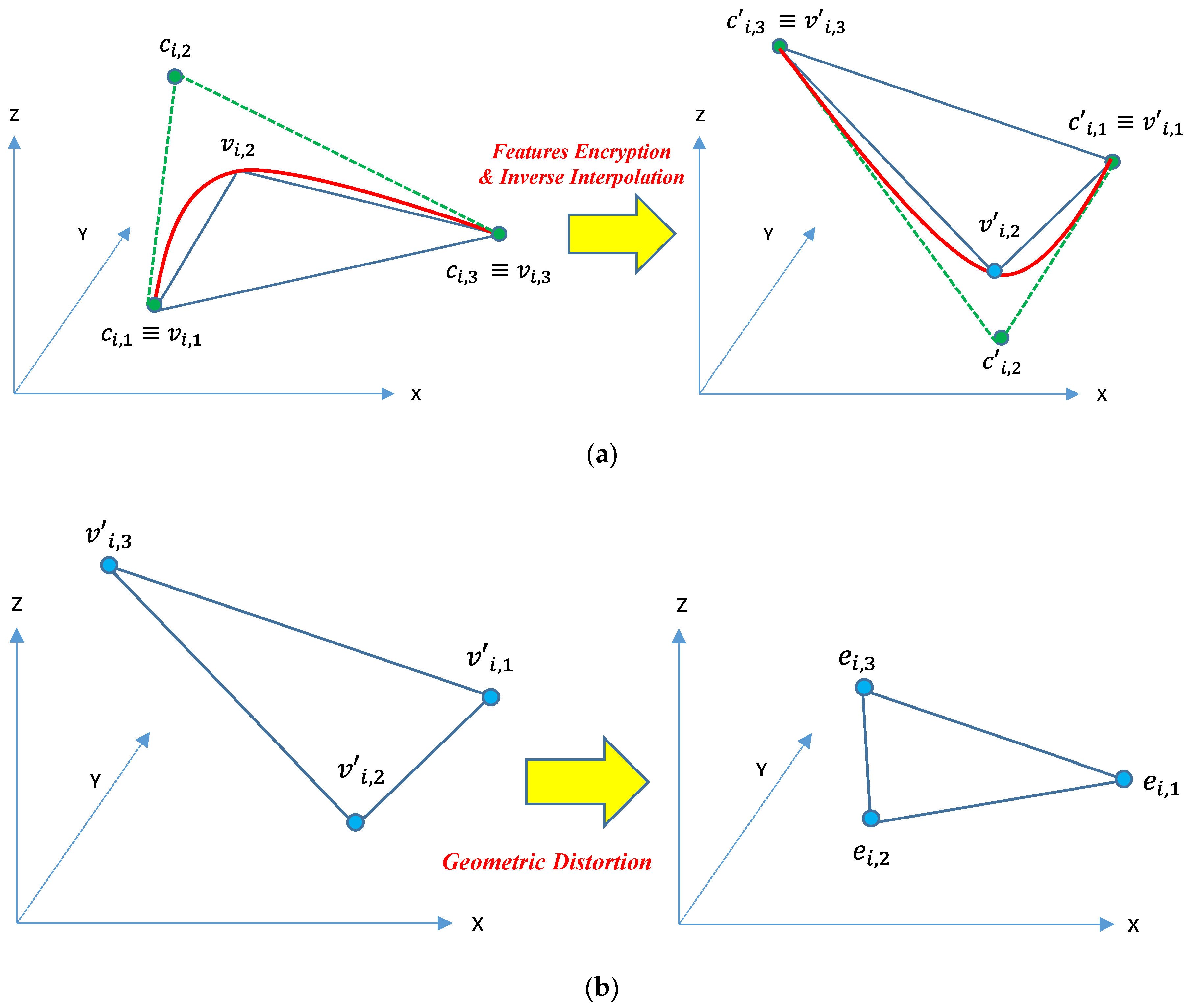
3.3. Features of Interpolating Spline Curve Encryption
3.4. Decryption Process
4. Experimental Results, Analysis, and Evaluation
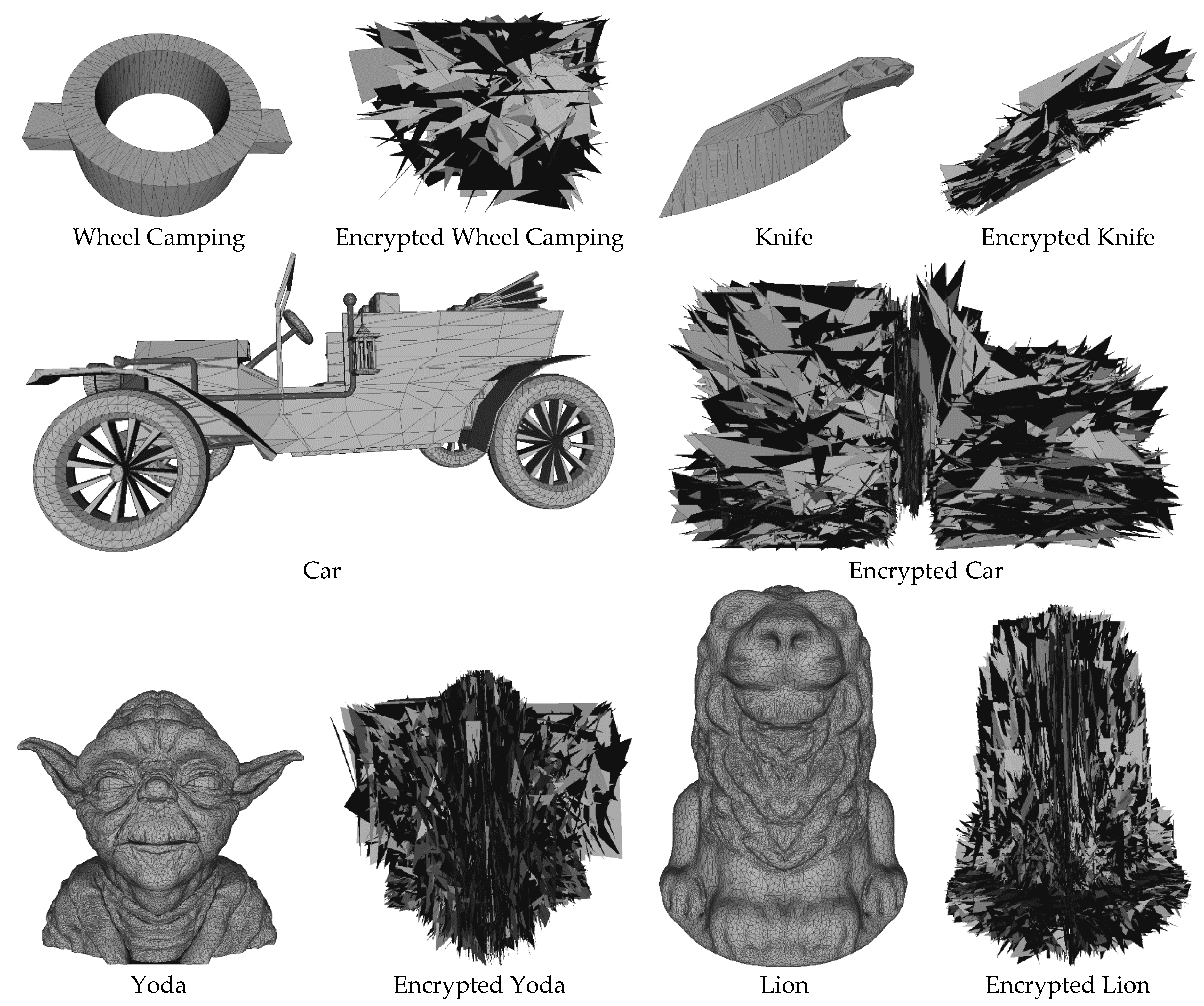
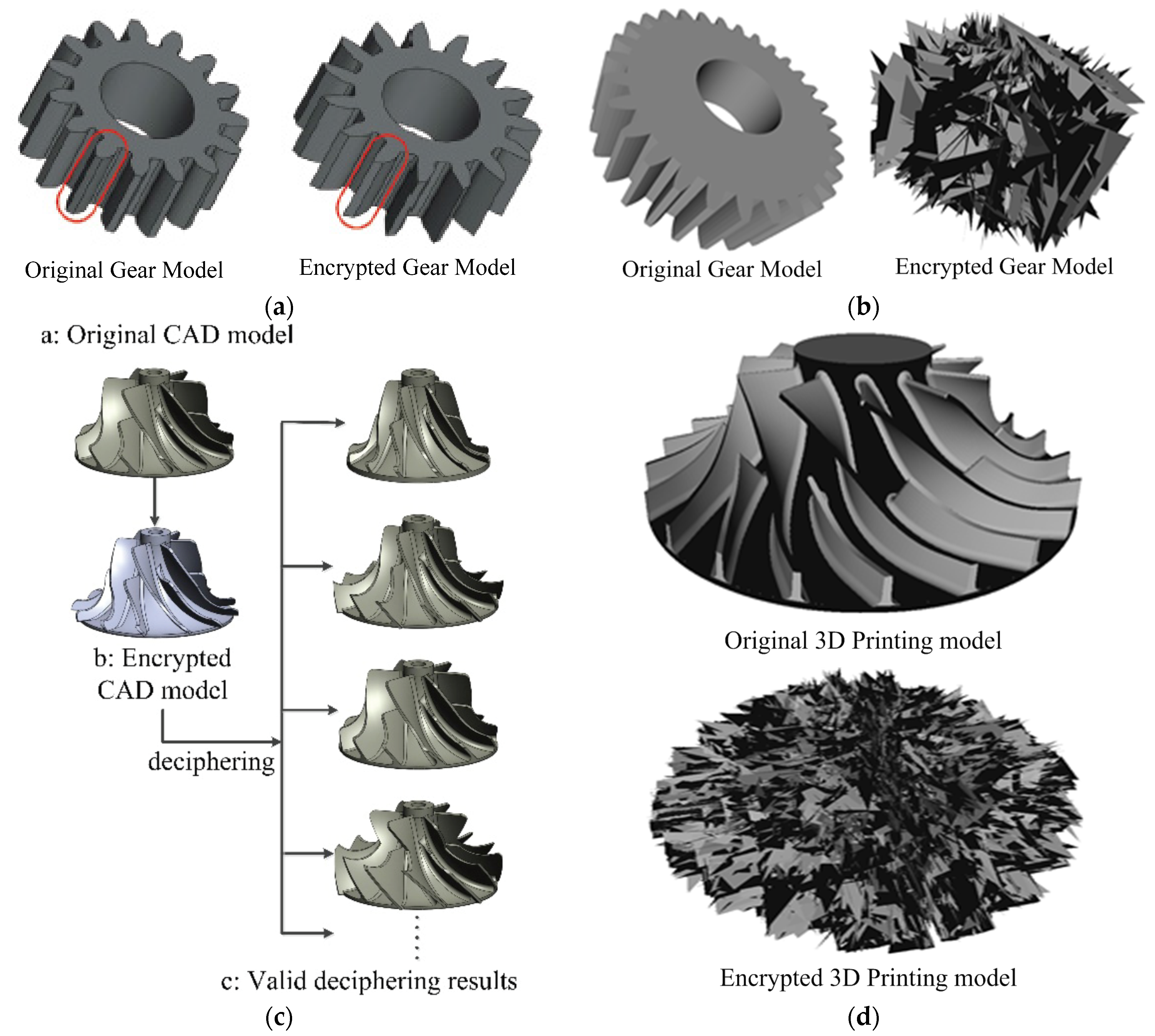
4.1. Visualization Experiments
4.2. Security Evaluation
4.3. Computation Time and Analysis
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- United States Government Accountability Office. 3D Printing Opportunities, Challenges, and Policy Implications of Additive Manufacturing; DIANE Publishing Company: Collingdale, PA, USA, 2015.
- 3D Systems Circle Rock Hill. White Paper: How 3D Printing Works, The Vision, Innovation and Technologies behind Inkjet 3D Printing; 333 Three D Systems Circle: Rock Hill, SC, USA, 2012. [Google Scholar]
- Ho, J.U.; Kim, D.G.; Choi, S.H.; Lee, H.K. 3D Print-Scan Resilient Watermarking Using a Histogram-Based Circular Shift Coding Structure. In Proceedings of the 3rd ACM Workshop on Information Hiding and Multimedia Security, Portland, OR, USA, 17–19 June 2015; pp. 115–121. [Google Scholar]
- Yamazaki, S.; Satoshi, K.; Masaaki, M. Extracting Watermark from 3D Prints. In Proceedings of the 22nd International Conference on Pattern Recognition, Stockholm, Sweden, 24–28 August 2014; pp. 4576–4581. [Google Scholar]
- Suzuki, M.; Piyarat, S.; Kazutake, U.; Hiroshi, U.; Takashima, Y. Copyright Protection for 3D Printing by Embedding Information inside Real Fabricated Objects. In Proceedings of the 10th International Conference on Computer Vision Theory and Applications, Berlin, Germany, 11–14 March 2015; pp. 180–185. [Google Scholar]
- Tan, X.H. A 3D Model Asymmetric Watermarking Algorithm Based on Optimization Statistics. J. Theor. Appl. Inf. Technol. 2011, 51, 175–181. Available online: http://www.jatit.org/volumes/Vol51No2/2Vol51No2.pdf (accessed on 3 February 2018).
- Ramya, P.; Nalini, D. A New Watermarking For 3D Models Based On Integral Invariants. Int. J. Innov. Res. Comput. Commun. Eng. 2013, 1, 190–192. Available online: https://www.ijircce.com/upload/2013/april/8_A%20New.pdf (accessed on 3 February 2018).
- Esam, E.; Ben, A. Secret Sharing Approaches for 3D Object Encryption. Expert Syst. Appl. 2011, 38, 13906–13911. [Google Scholar] [CrossRef]
- Marc, E.; Maetz, Y.; Gwenael, D. Geometry-preserving Encryption for 3D Meshes. In Proceedings of the Conference: Compression at Representation Signal Audio, Le Creusot, France, 28–29 November 2013; pp. 7–12. [Google Scholar]
- Cai, X.T.; He, F.Z.; Li, W.D.; Li, X.X.; Wu, Y.Q. Encryption Based Partial Sharing of CAD models. Integr. Comput.-Aided Eng. 2015, 22, 243–260. [Google Scholar] [CrossRef]
- Cai, X.T.; Li, W.D.; He, F.Z.; Li, X.X. Customized Encryption of Computer Aided Design Models for Collaboration in Cloud Manufacturing Environment. J. Manuf. Sci. Eng. 2015, 137, 1–10. [Google Scholar] [CrossRef]
- Cai, X.T.; He, F.Z.; Li, W.D.; Li, X.X.; Wu, Y.Q. Parametric and Adaptive Encryption of Feature-Based Computer-Aided Design Models for Cloud-based Collaboration. Integr. Comput.-Aided Eng. 2017, 24, 129–142. [Google Scholar] [CrossRef]
- STL Format in 3D Printing. Available online: https://all3dp.com/what-is-stl-file-format-extension-3d-printing/ (accessed on 3 February 2018).
- The Virtual Reality Modeling Language. Available online: http://www.cacr.caltech.edu/~slombey/asci/vrml/ (accessed on 3 February 2018).
- Shene, C.K. Michigan Technological University. Introduction to Computing With Geometry Notes. Available online: http://pages.mtu.edu/~shene/COURSES/cs3621/NOTES/ (accessed on 3 February 2018).
- Lyche, T.; Morken, K. Spline Methods Draft; Dept. Informatics Centre of Mathematics for Applications, University of Oslo: Oslo, Norway, 2008. [Google Scholar]
- RSA Lab. Password-Based Cryptography Standard; RSA Lab.: Bedford, MA, USA, 2006. [Google Scholar]
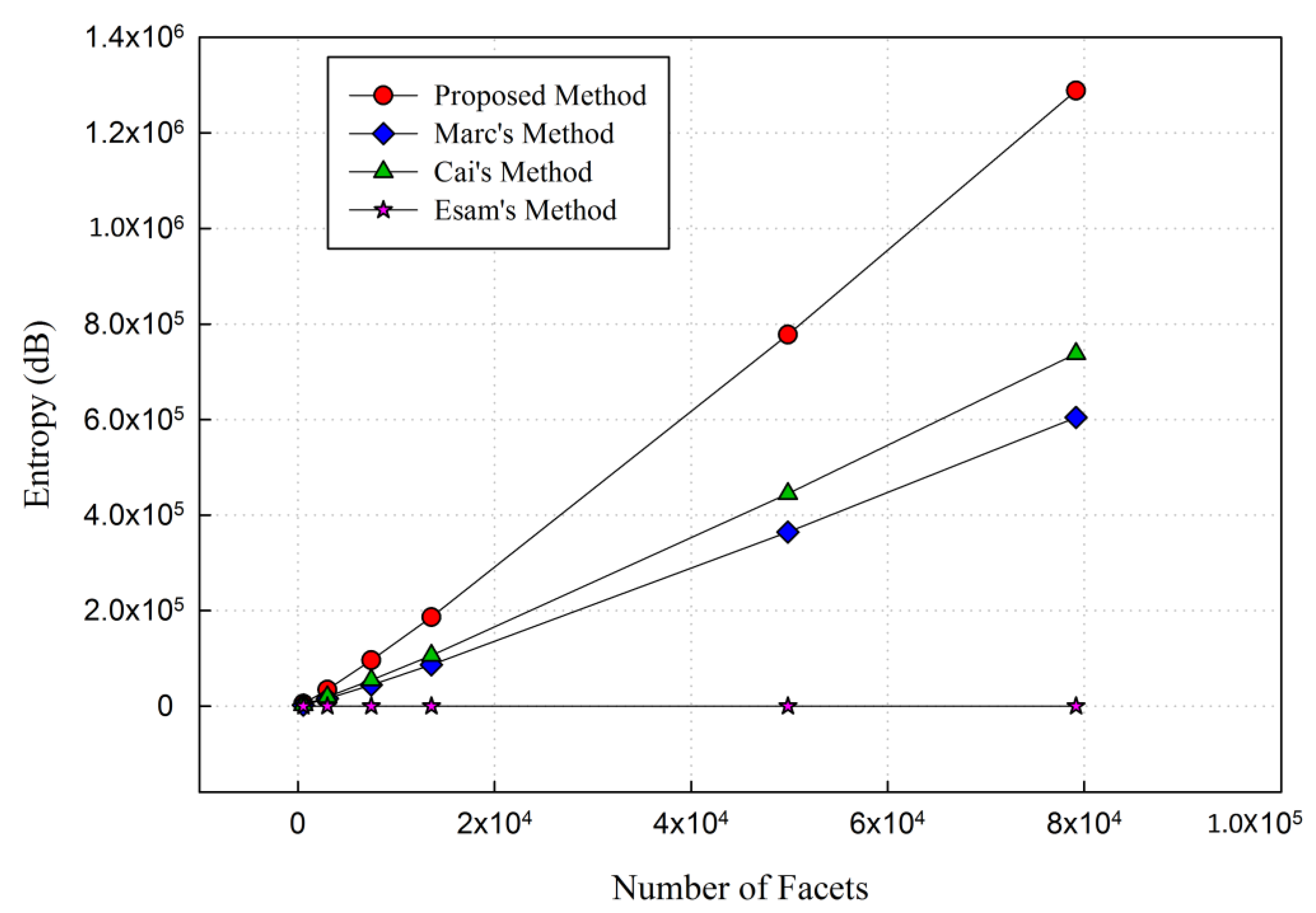
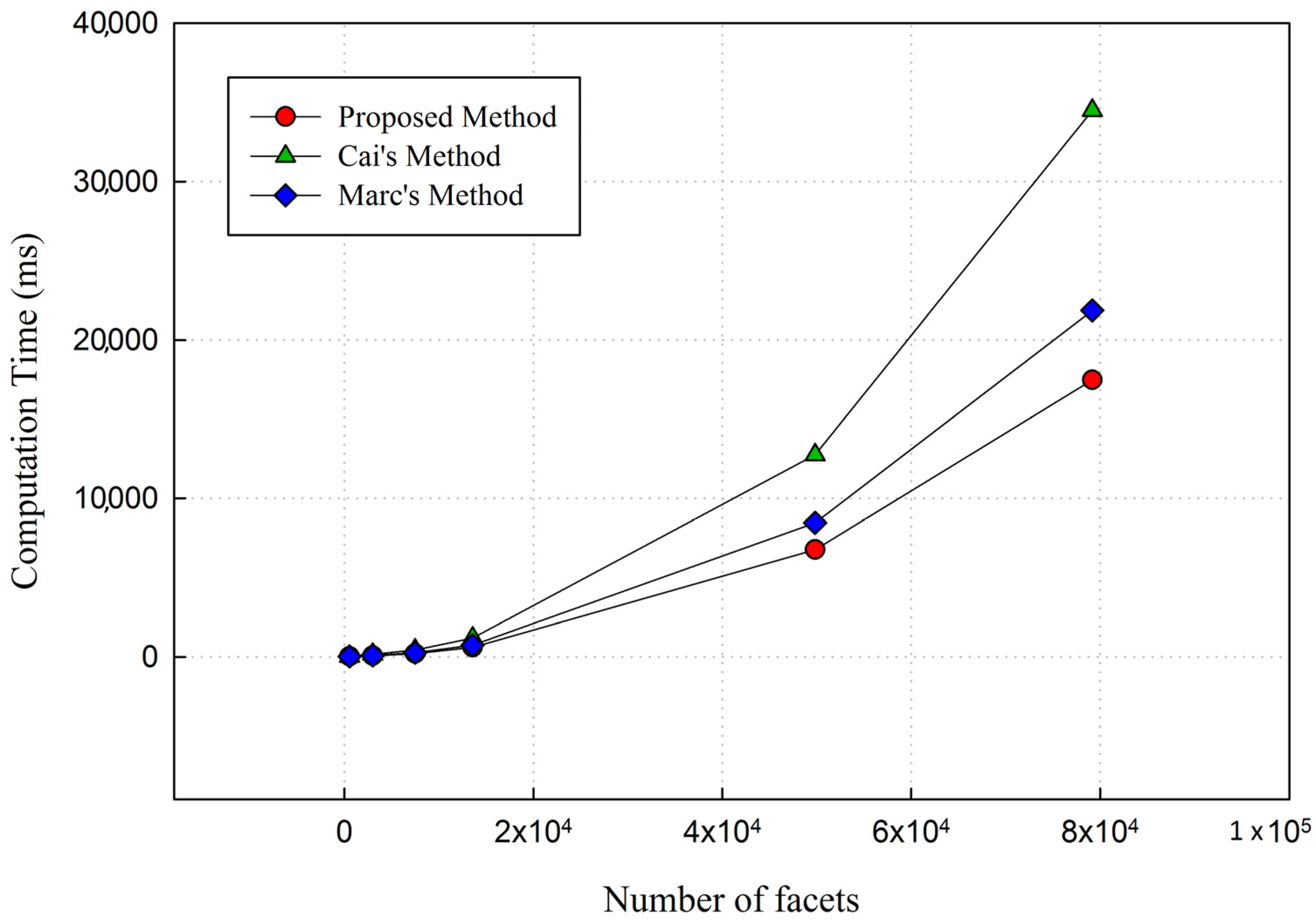
| Name | # Facets | Entropy (dB) | Computation Time (ms) | |||
|---|---|---|---|---|---|---|
| Proposed Method | Cai’s Method | Marc’s Method | Esam’s Method | |||
| Wheel Camping | 544 | 4981 | 2754 | 2218 | 8.0 | 17.5 |
| Knife | 1176 | 12,032 | 6705 | 5430 | 8.0 | 29 |
| Aperture Face | 2026 | 22,292 | 12,485 | 10,137 | 8.0 | 46 |
| Flower | 2986 | 34,508 | 19,390 | 15,766 | 8.0 | 72 |
| Gun | 3961 | 47,378 | 26,681 | 21,714 | 8.0 | 90 |
| Castle | 7466 | 96,096 | 54,362 | 44,322 | 8.0 | 209 |
| Batman | 13,566 | 186,268 | 105,767 | 86,360 | 8.0 | 591 |
| Rabbit | 21,056 | 302,443 | 172,161 | 140,704 | 8.0 | 1312 |
| Moto-bike | 22,034 | 317,932 | 181,022 | 147,959 | 8.0 | 1421 |
| Car | 32,426 | 485,937 | 277,229 | 226,767 | 8.0 | 2951 |
| Yoda | 49,844 | 777,860 | 44,4681 | 364,021 | 8.0 | 6763 |
| Lion | 79,162 | 1,288,203 | 737,923 | 604,535 | 8.0 | 17,486 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pham, G.N.; Lee, S.-H.; Kwon, K.-R. Interpolating Spline Curve-Based Perceptual Encryption for 3D Printing Models. Appl. Sci. 2018, 8, 242. https://doi.org/10.3390/app8020242
Pham GN, Lee S-H, Kwon K-R. Interpolating Spline Curve-Based Perceptual Encryption for 3D Printing Models. Applied Sciences. 2018; 8(2):242. https://doi.org/10.3390/app8020242
Chicago/Turabian StylePham, Giao N., Suk-Hwan Lee, and Ki-Ryong Kwon. 2018. "Interpolating Spline Curve-Based Perceptual Encryption for 3D Printing Models" Applied Sciences 8, no. 2: 242. https://doi.org/10.3390/app8020242
APA StylePham, G. N., Lee, S.-H., & Kwon, K.-R. (2018). Interpolating Spline Curve-Based Perceptual Encryption for 3D Printing Models. Applied Sciences, 8(2), 242. https://doi.org/10.3390/app8020242





