A Security Analysis Method for Security Protocol Implementations Based on Message Construction
Abstract
1. Introduction
- (1)
- Do not have client-side implementations and server-side implementations.
- (2)
- Have both client-side implementations and server-side implementations.
- (3)
- Have the client-side implementations but not the server-side implementation.
- (4)
- Have the server-side implementations but not the client-side implementation.
- (1)
- Present the state-of-the-art security analysis method of security protocol implementations and point out that existing researchers have not taken into consideration the internal structures of cryptographic primitive implementations to analyze the security of security protocol implementations.
- (2)
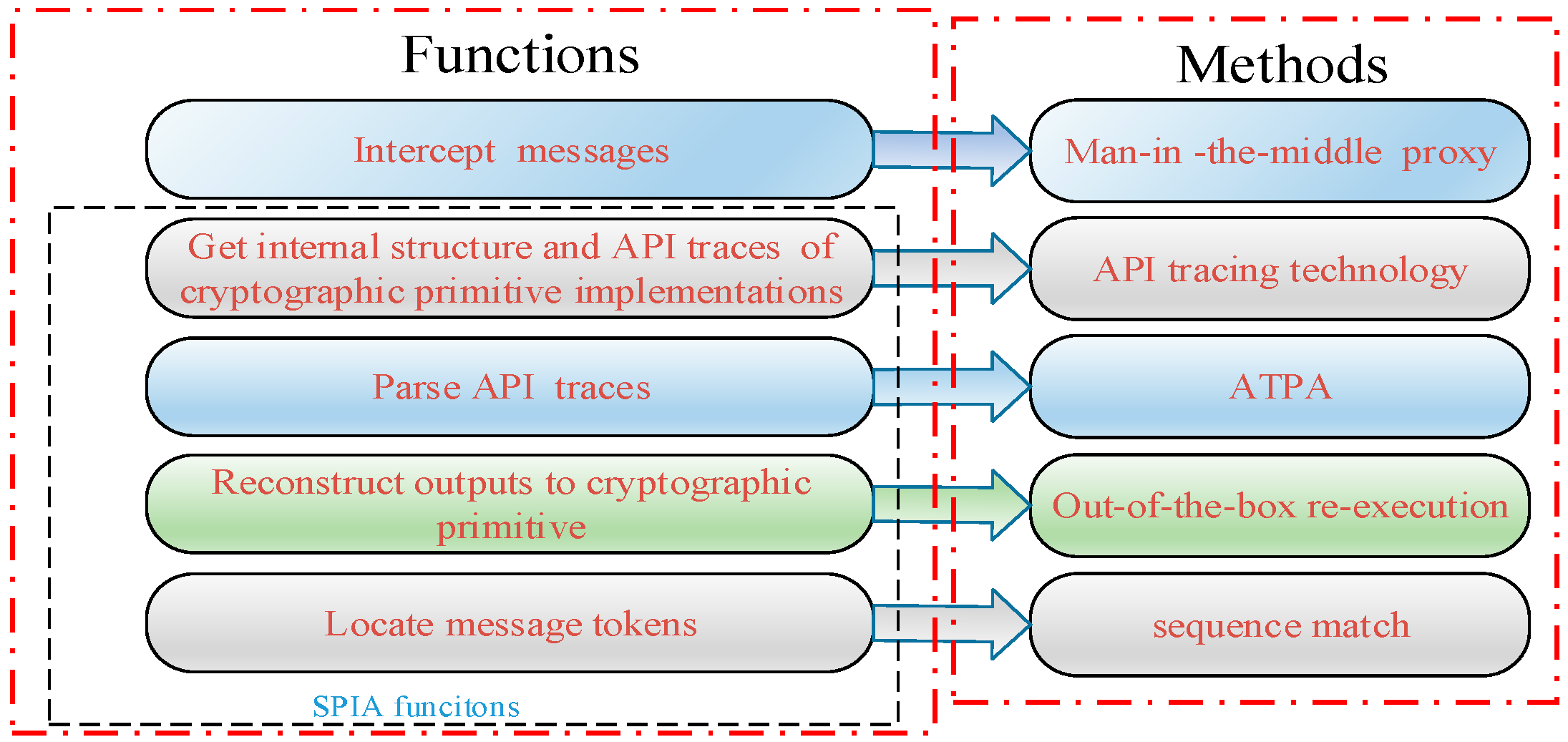
- Propose the Message Construction to Security Protocol Implementation (MCSPI) method, a message construction based on application programming interface (API) traces. At the beginning, it intercepts and parses messages between client and server. Then, it traces the cryptographic primitive functions in security protocol implementations with API tracing technology. Finally, it reconstructs outputs using out-of-the-box re-execution to replace the located tokens to generate the valid client messages.
- (3)
- Present the Security Analysis Scheme (SAS), a security analysis scheme that combines MCSPI and the corresponding server-side response message to generate an abstract model of the security protocol server.
- (4)
- Propose a security analysis method to evaluate the security of security protocol implementations on the basis of constructed client request messages generated by MCSPI, the corresponding server-side response message, and the server-side abstract model produced by SAS.
- (5)
- Implement the Security Protocol Implementation Analysis (SPIA) to test the RSAAuth system and Tencent QQ mail system version 2017. We found that RSAAuth has just user password verification at server-side, while Tencent QQ mail system version 2017 holds some other restrictions besides user password security verification.
2. Related Works
3. Solution
3.1. MCSPI
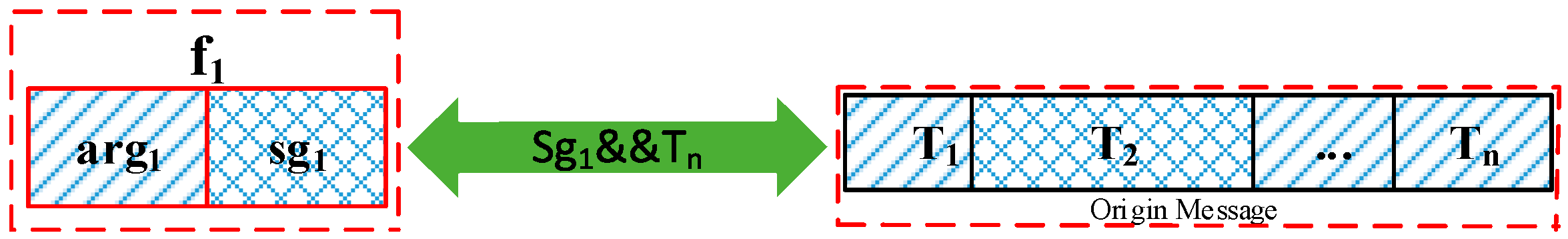
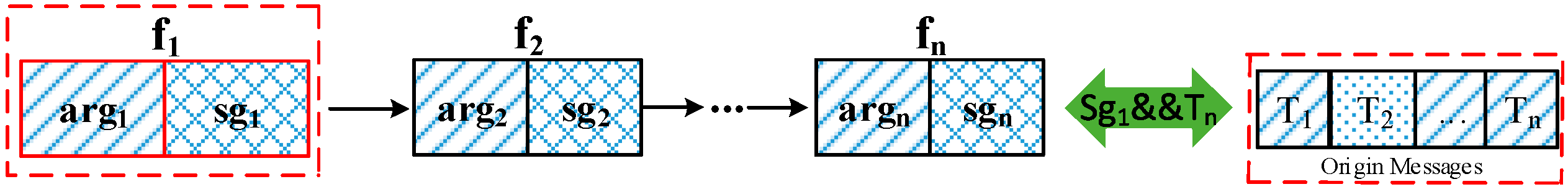
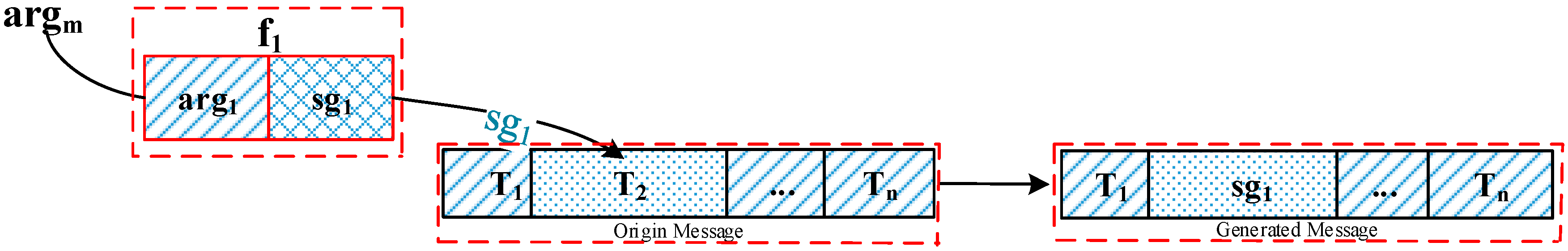
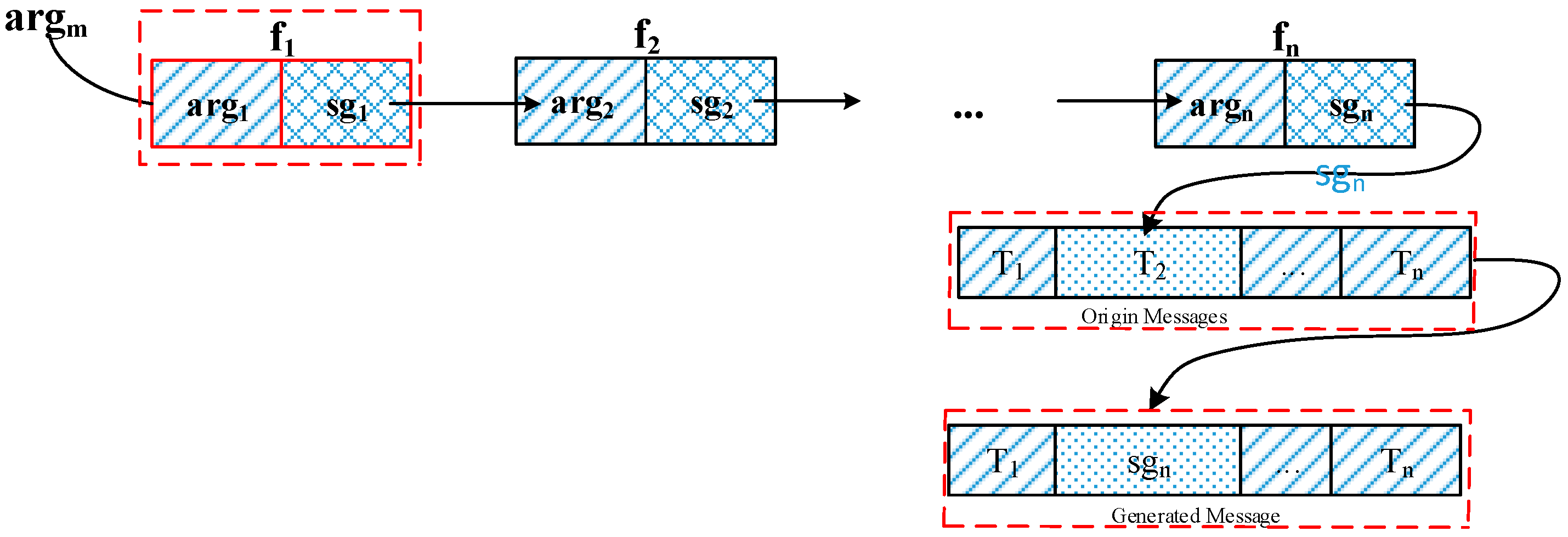
- (1)
- Substitute arg with argm.
- (2)
- Re-execute fun with argm to generate Sg, which is the constructed output to the traced functions. Sg is used to substitute Tn to generate the constructed messages.
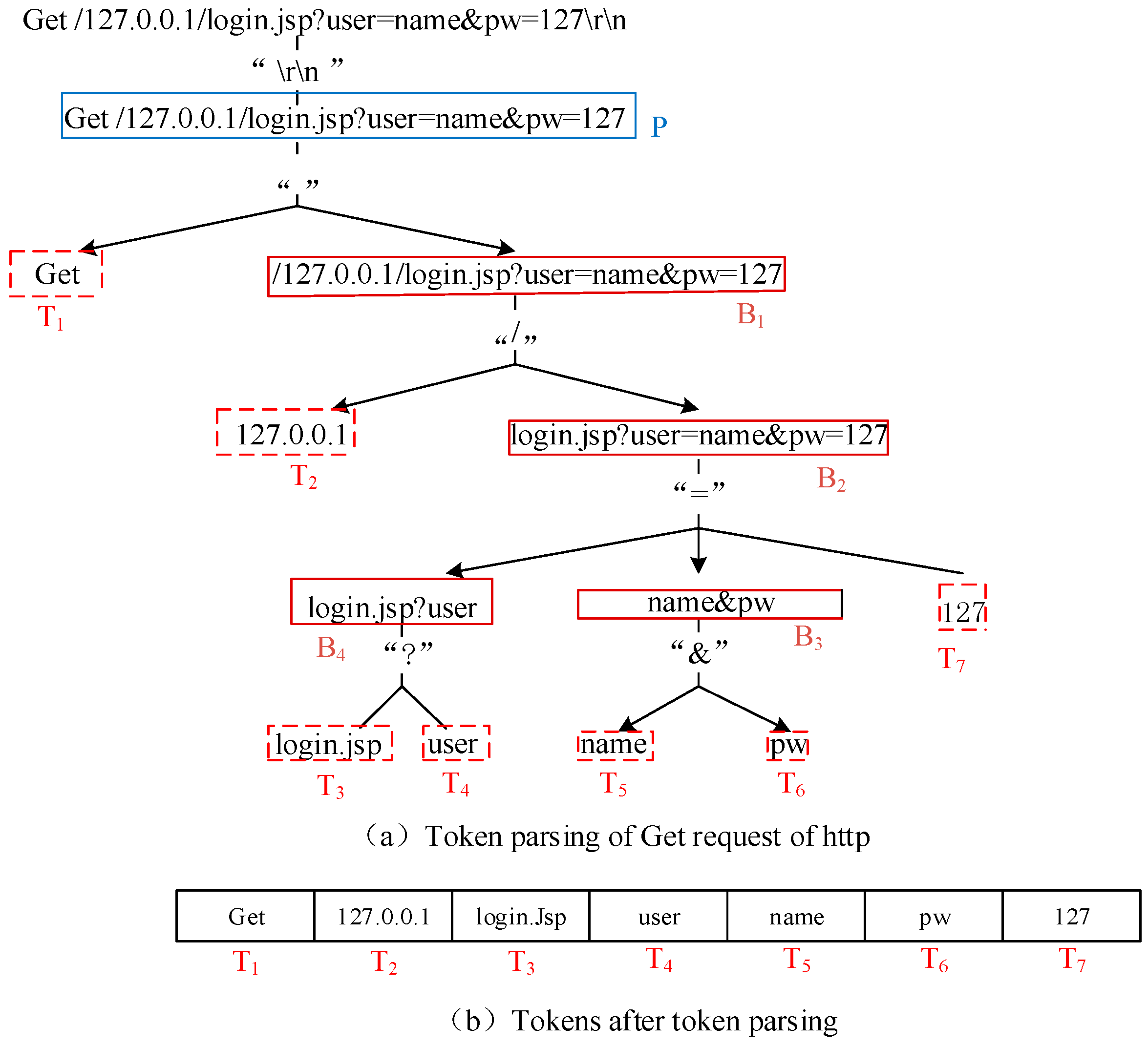
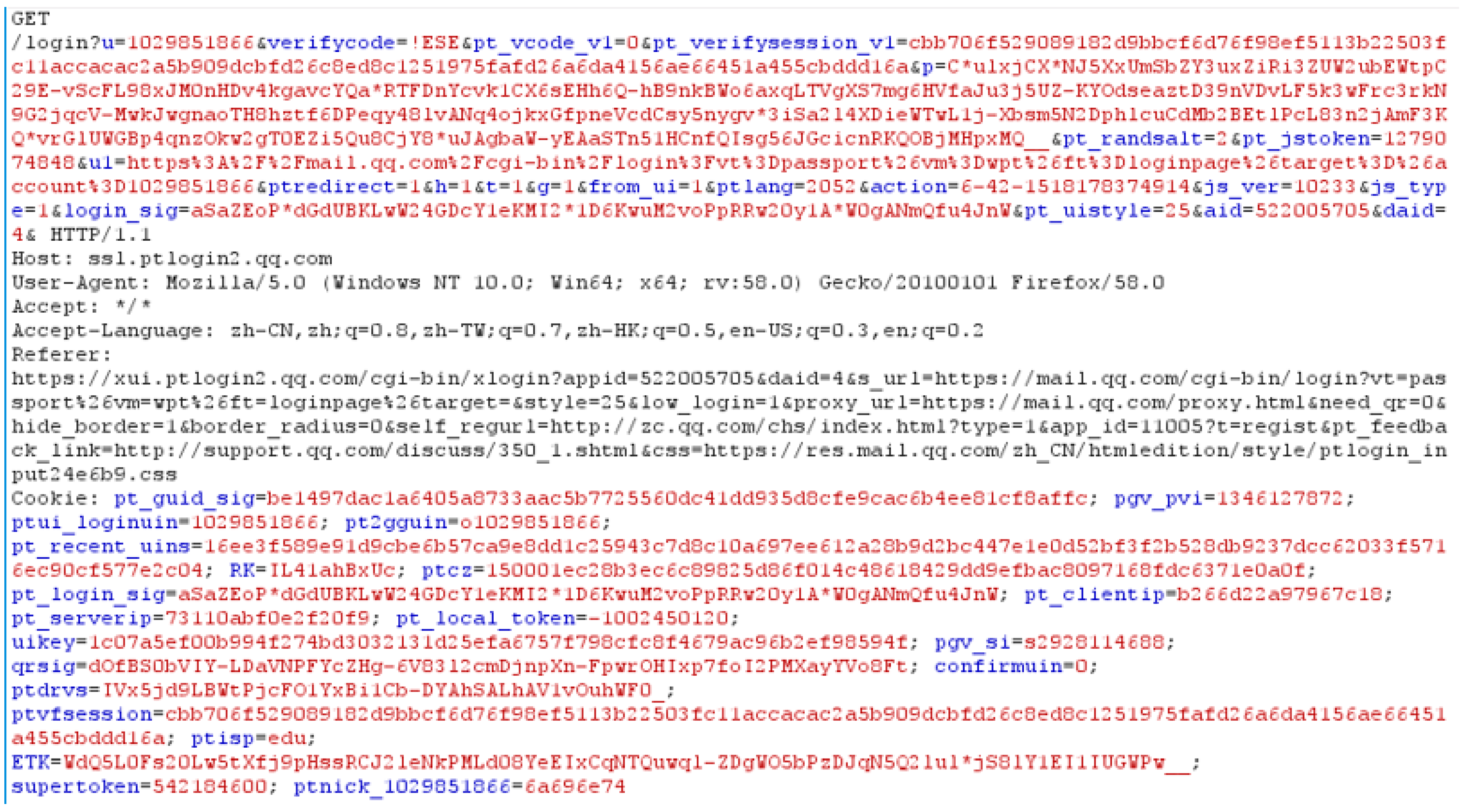
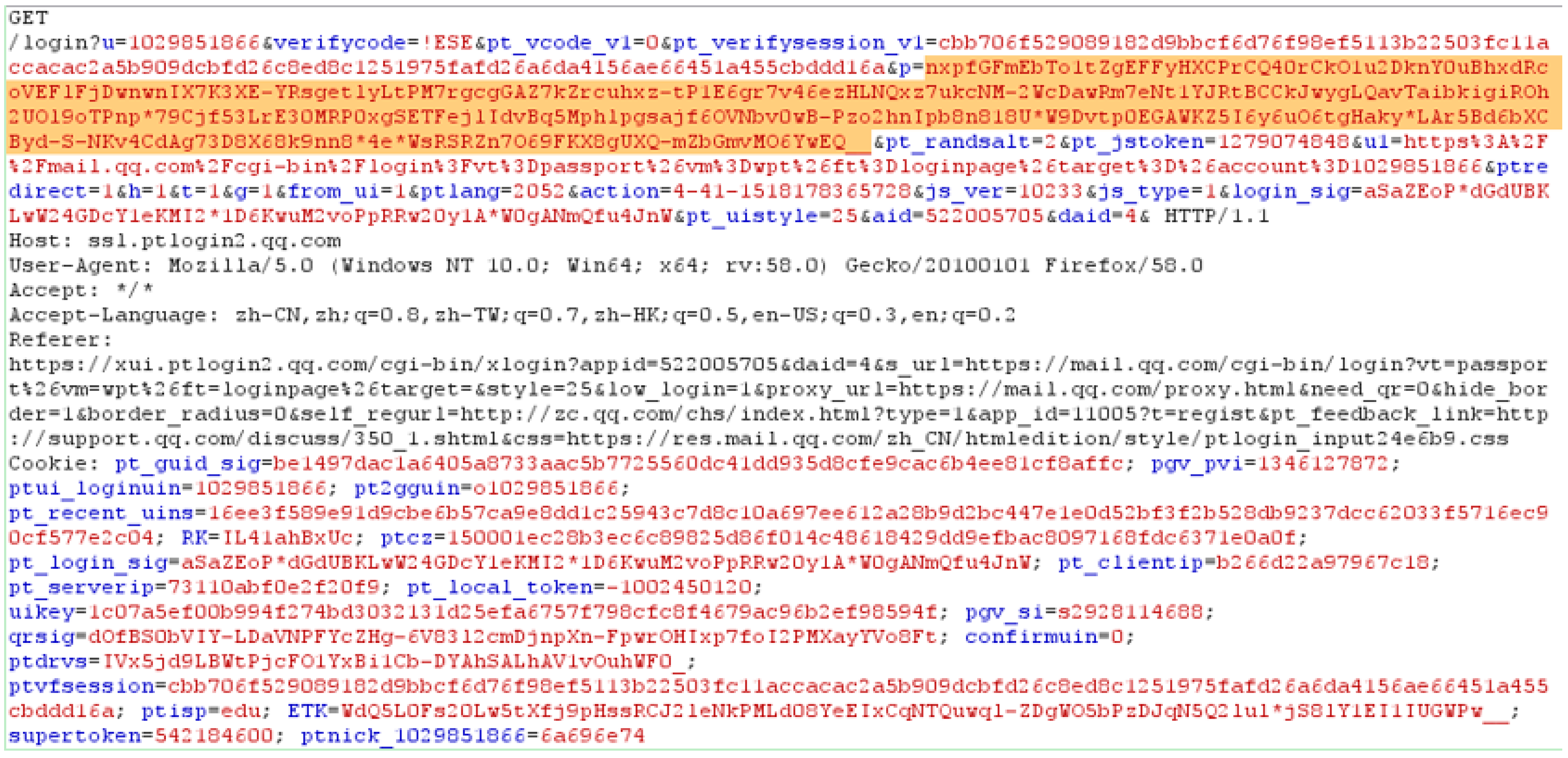
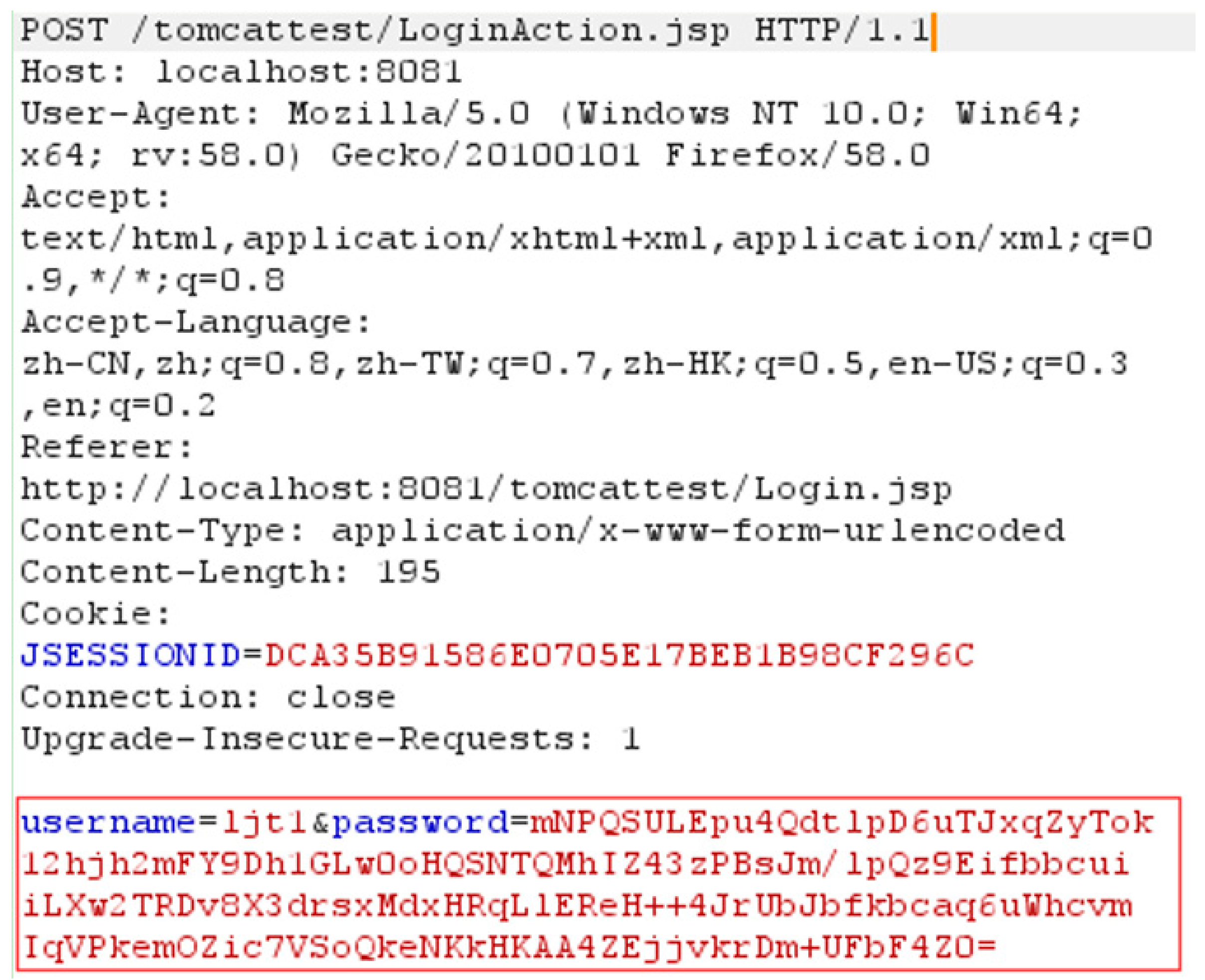
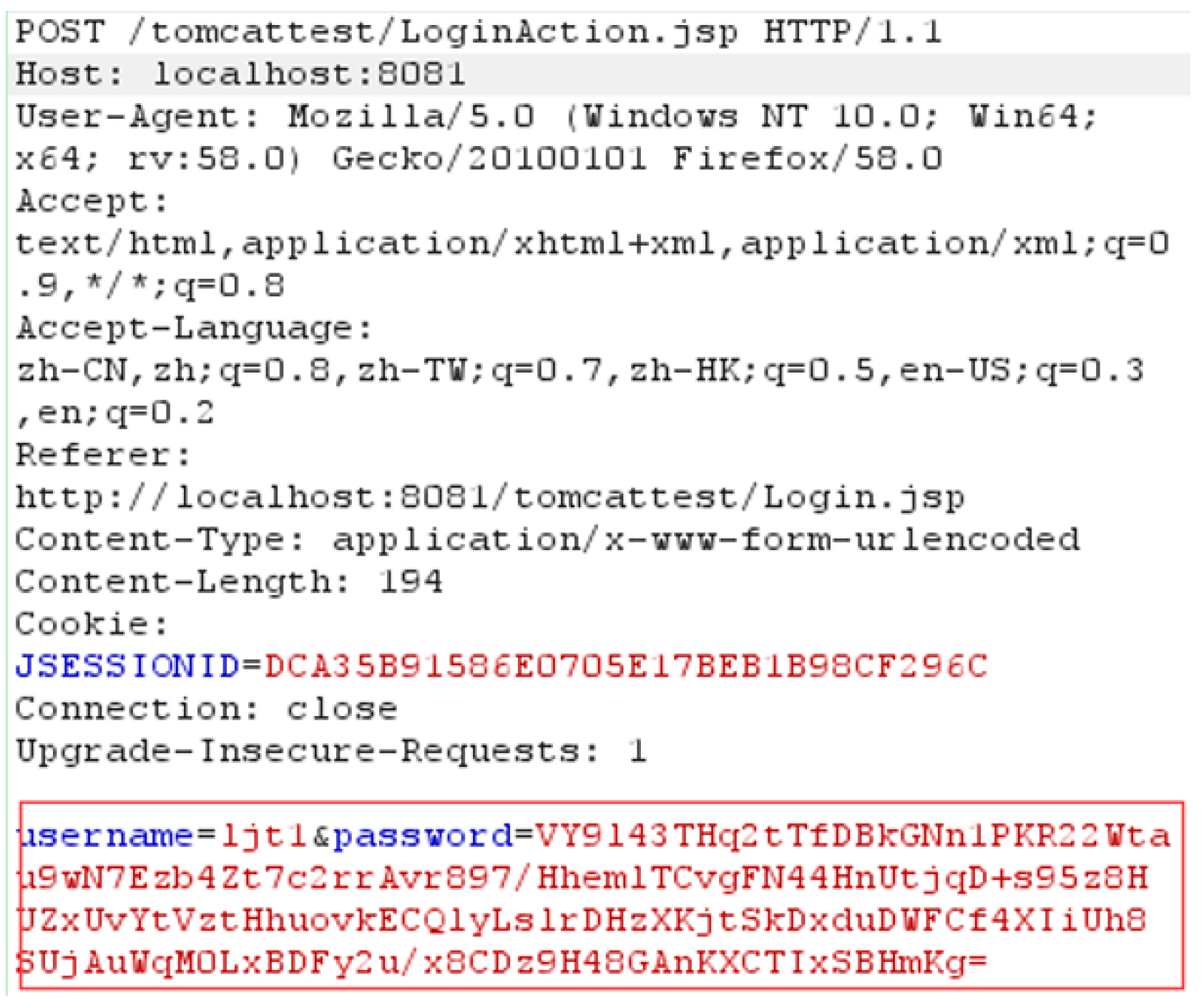
3.1.1. Intercept and Parse Message
- (1)
- Identify “\r\n” symbols to generate message piece P.
- (2)
- Parse message piece P through identifying space symbol “ ” to produce message token T1 and message block B1.
- (3)
- Parse B1 by identifying delimiter symbol “/” to generate message token T2 and message block B2.
- (4)
- Parse message block B2 through identifying message connecting symbol “=” to generate message blocks B3 and B4 and message token T7.
- (5)
- Parse B3 and B4 by identifying message connecting symbol “?” and “&” to produce message tokens T3–T6. Note that T3 cannot be parsed into “login” and “jsp”.
- (6)
- All of the message tokens T1–T7 in (b) in Figure 3 locate the message token(s) which would be replaced by matching with the original output of traced cryptographic functions.
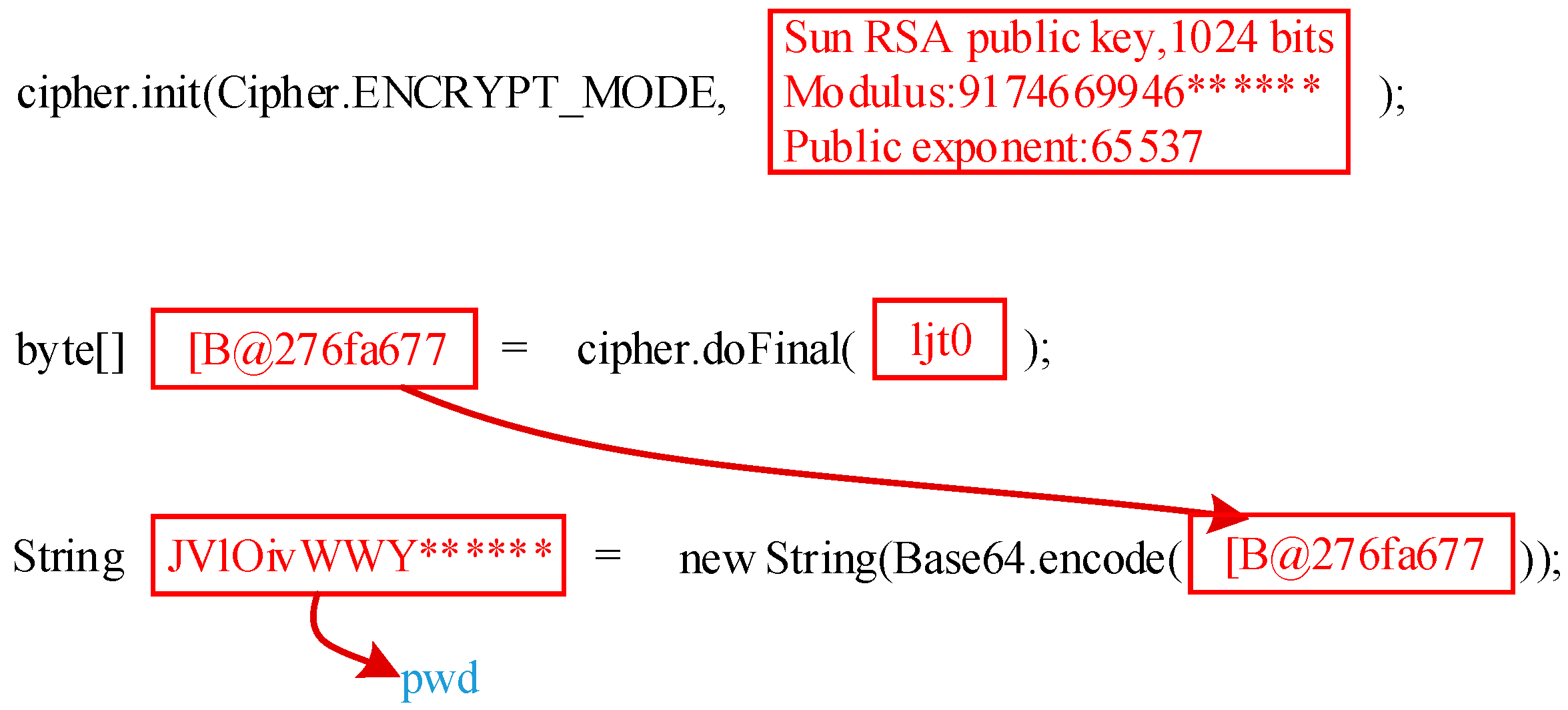
3.1.2. Get Internal Structure and Parse API Trace of Cryptographic Primitive Implementation
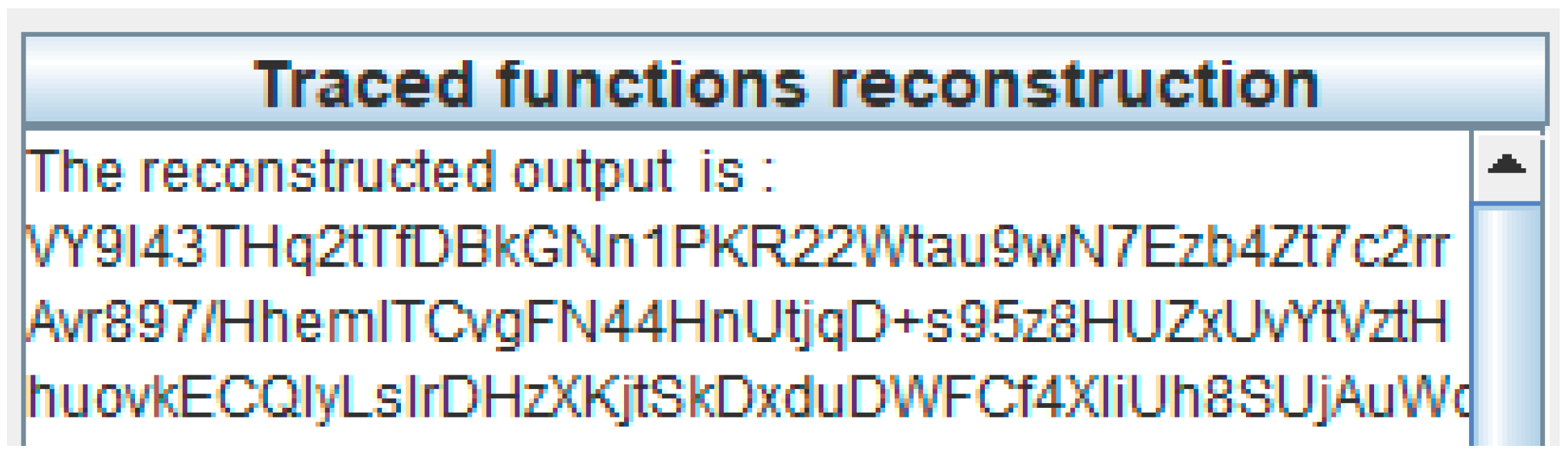
3.1.3. Reconstruct Outputs to Cryptographic Primitive Implementations
3.1.4. Location Message Tokens
3.1.5. Construct Message
3.2. SAS
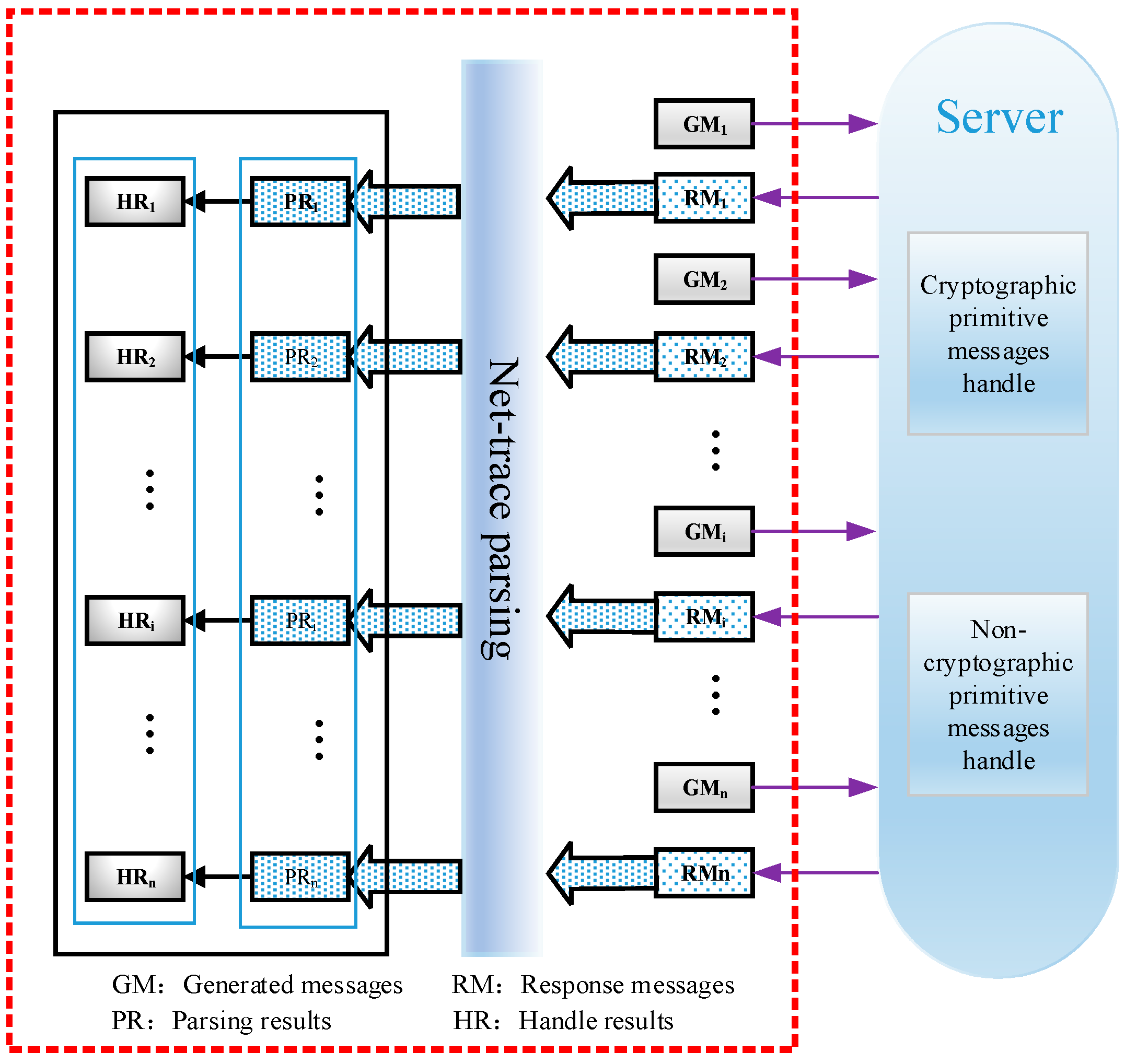
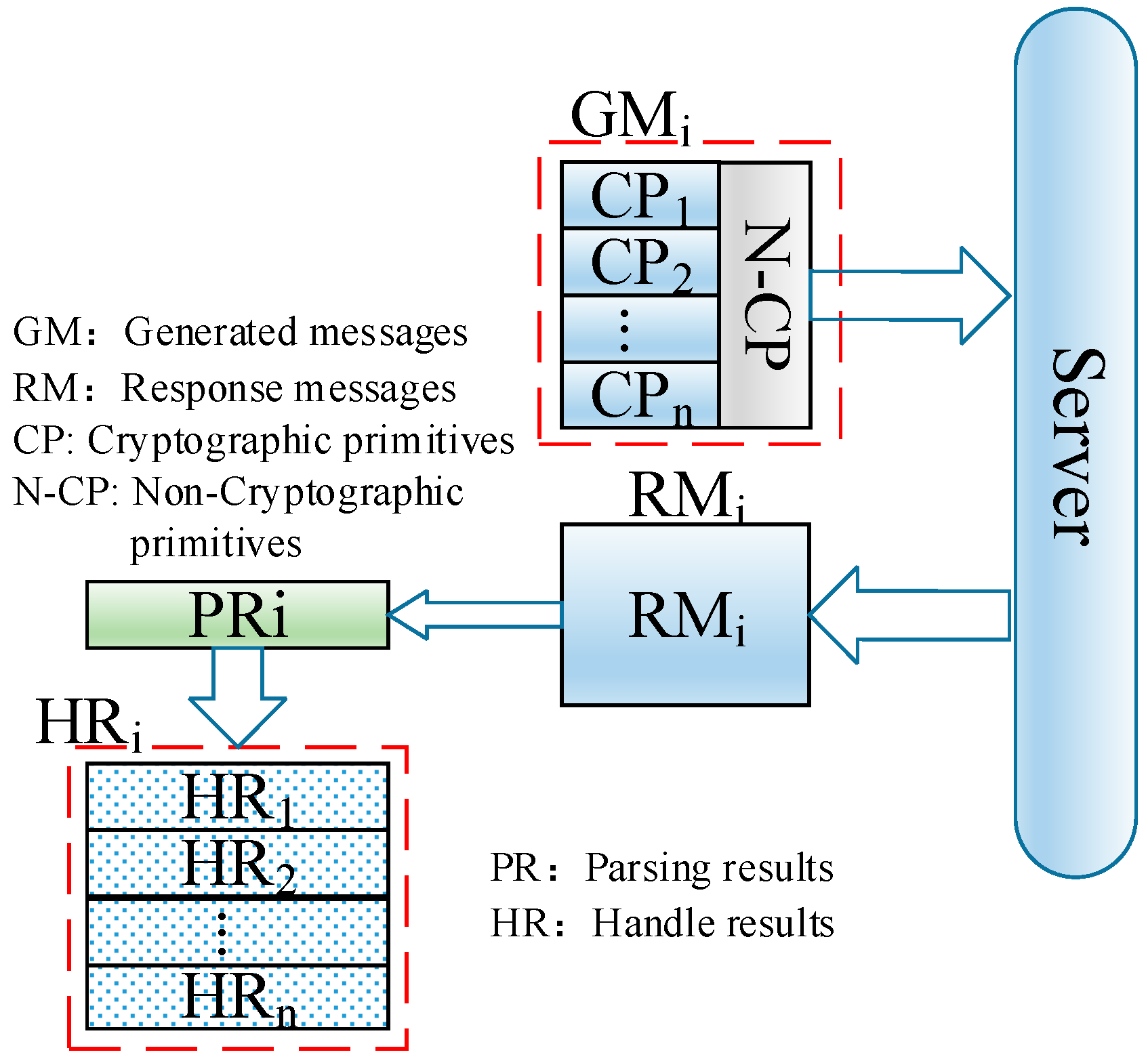
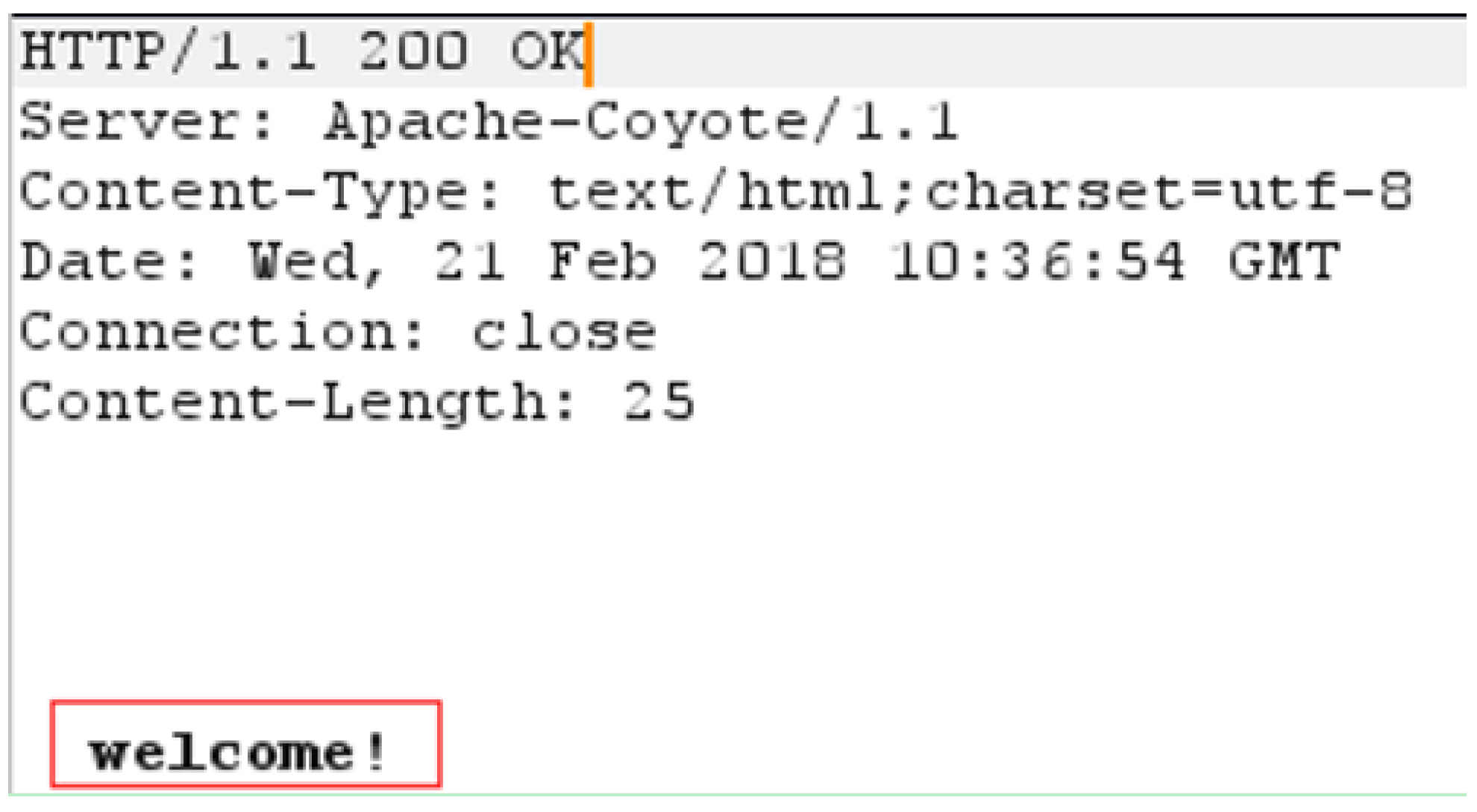
- (1)
- Send constructed request message GM1, which includes one cryptographic primitive, to the security protocol server.
- (2)
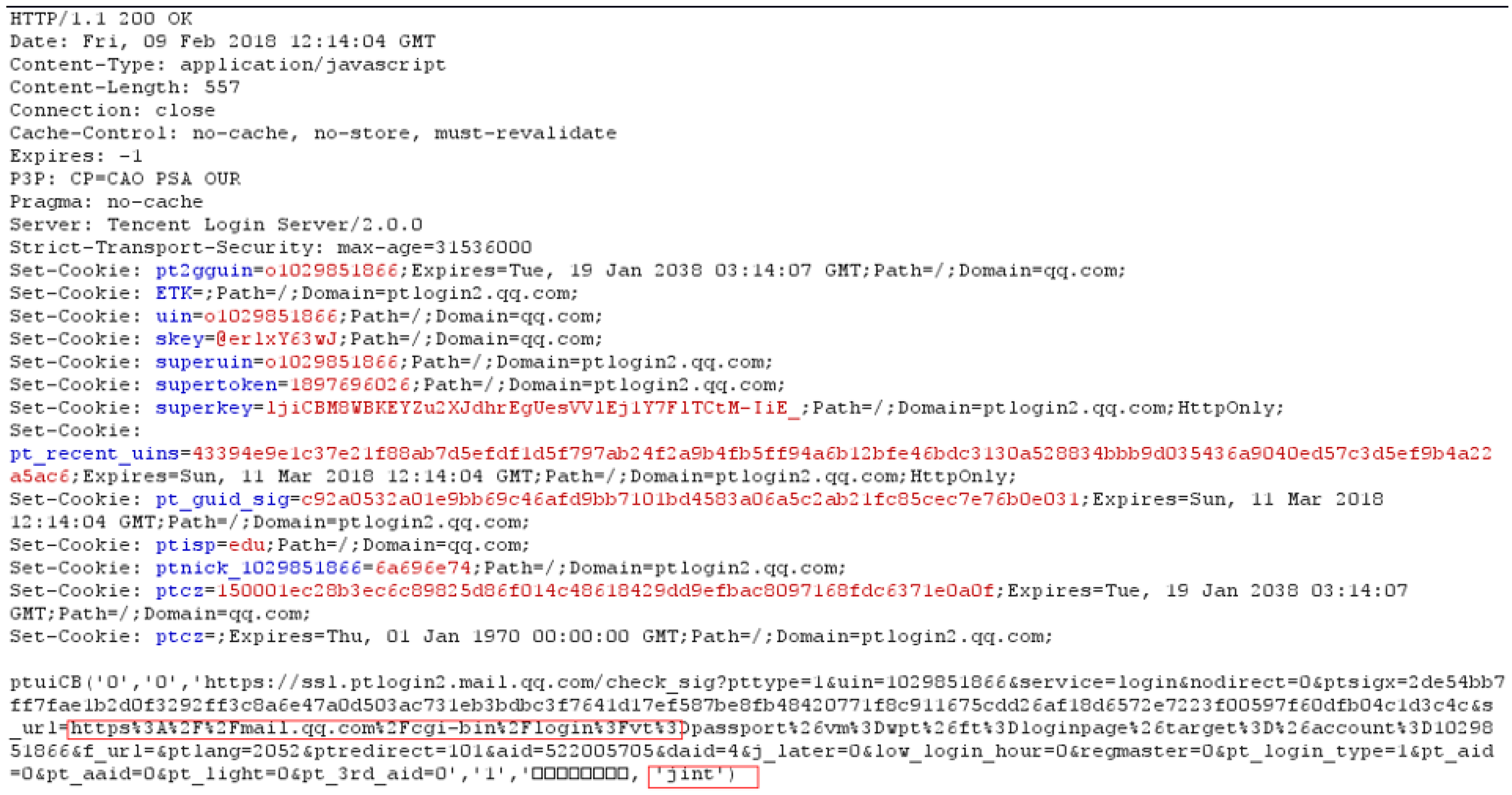
- Intercept response message RMi by MITM proxy and then parse it to produce the result PRi.
- (3)
- Extract HRi from PRi.
- (4)
- Repeat (1)–(4) until the end of the security protocol.
- (1)
- Send constructed message GMi that contains cryptographic primitives to the server.
- (2)
- Intercept RMi with the MITM proxy and parse RMi to generate parse action PRi.
- (3)
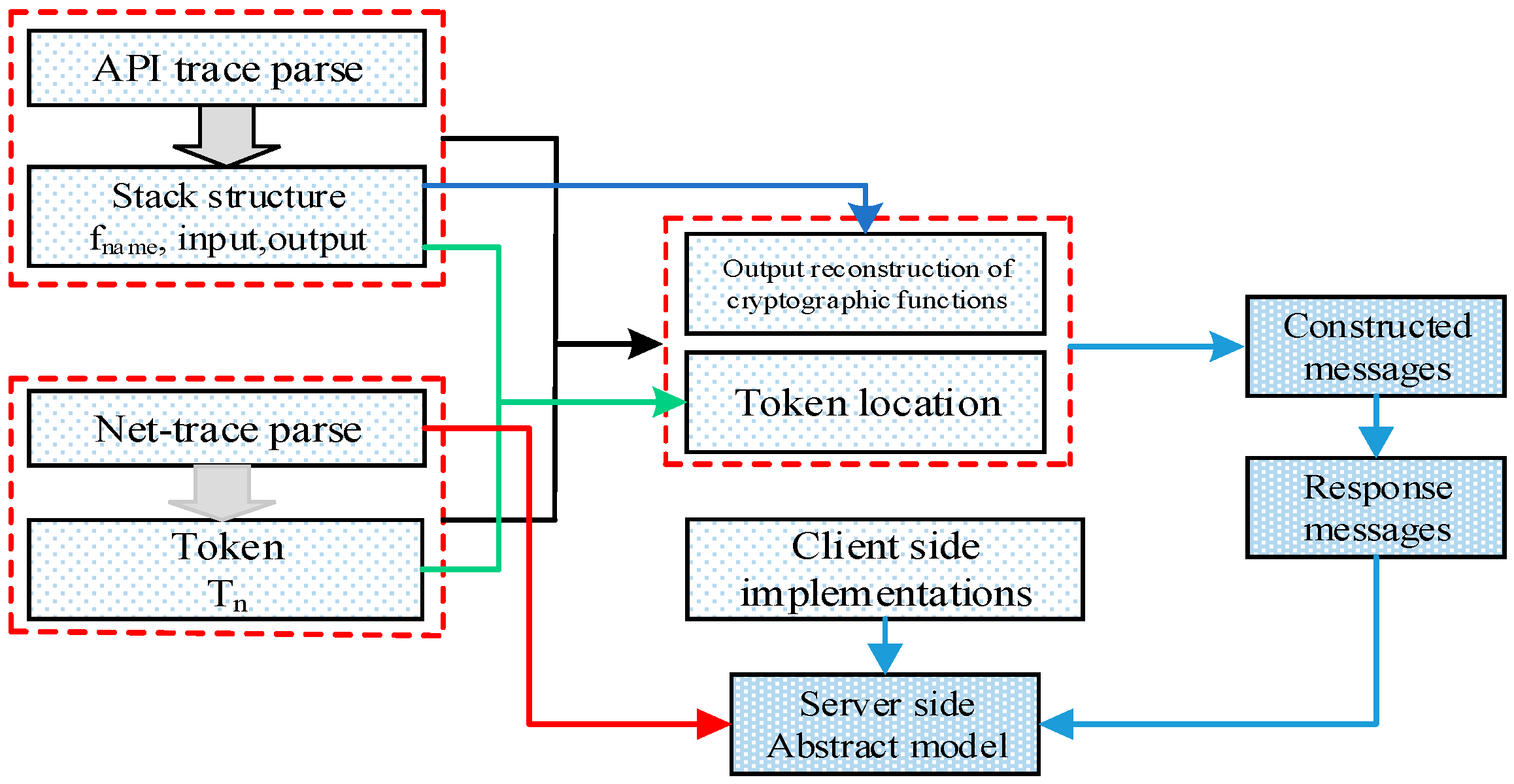
3.3. Security Analysis Method for Security Protocol Implementations Based on MCSPI and SAS
3.4. Discussion
- (1)
- The analysis objects are the message tokens that are the minimum compositions of protocol messages.
- (2)
- The internal structures (dependencies) of cryptographic primitive implementations in client-side implementations are used to locate and reconstruct the output of cryptographic primitive implementations, which is powerful for constructed valid request messages.
- (3)
- MCSPI can deal with both cryptographic and noncryptographic protocols.
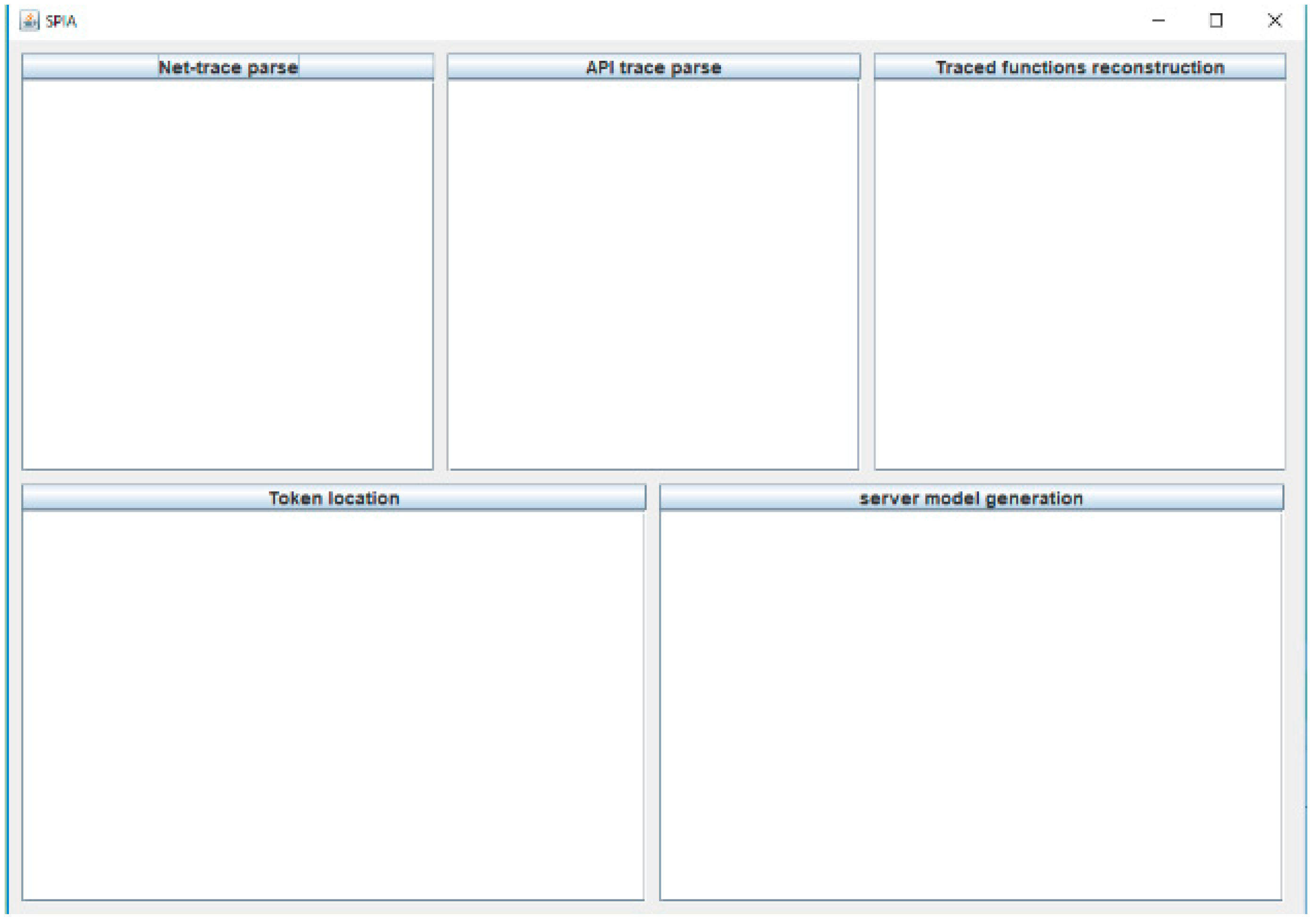
4. SPIA
4.1. Design
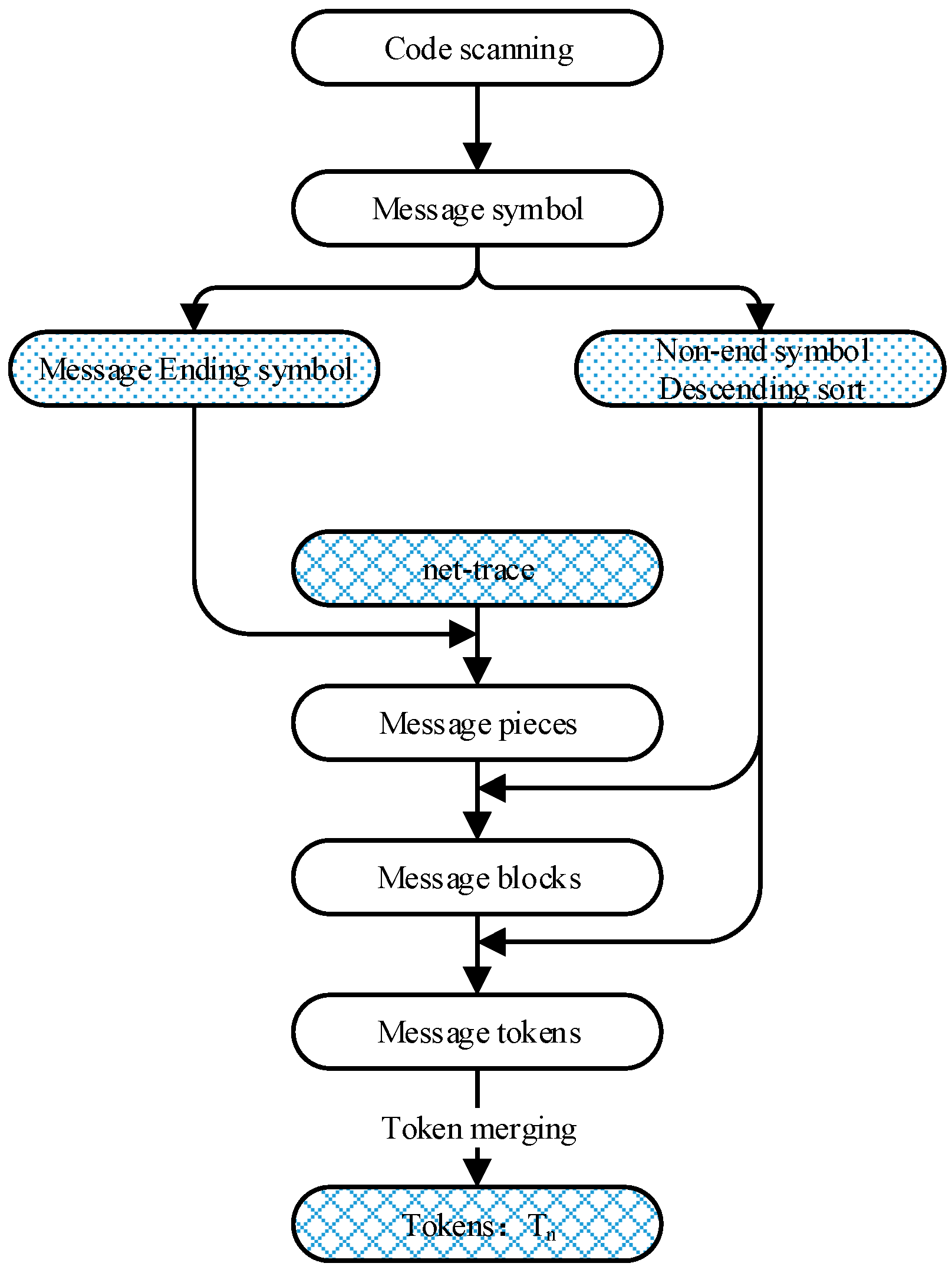
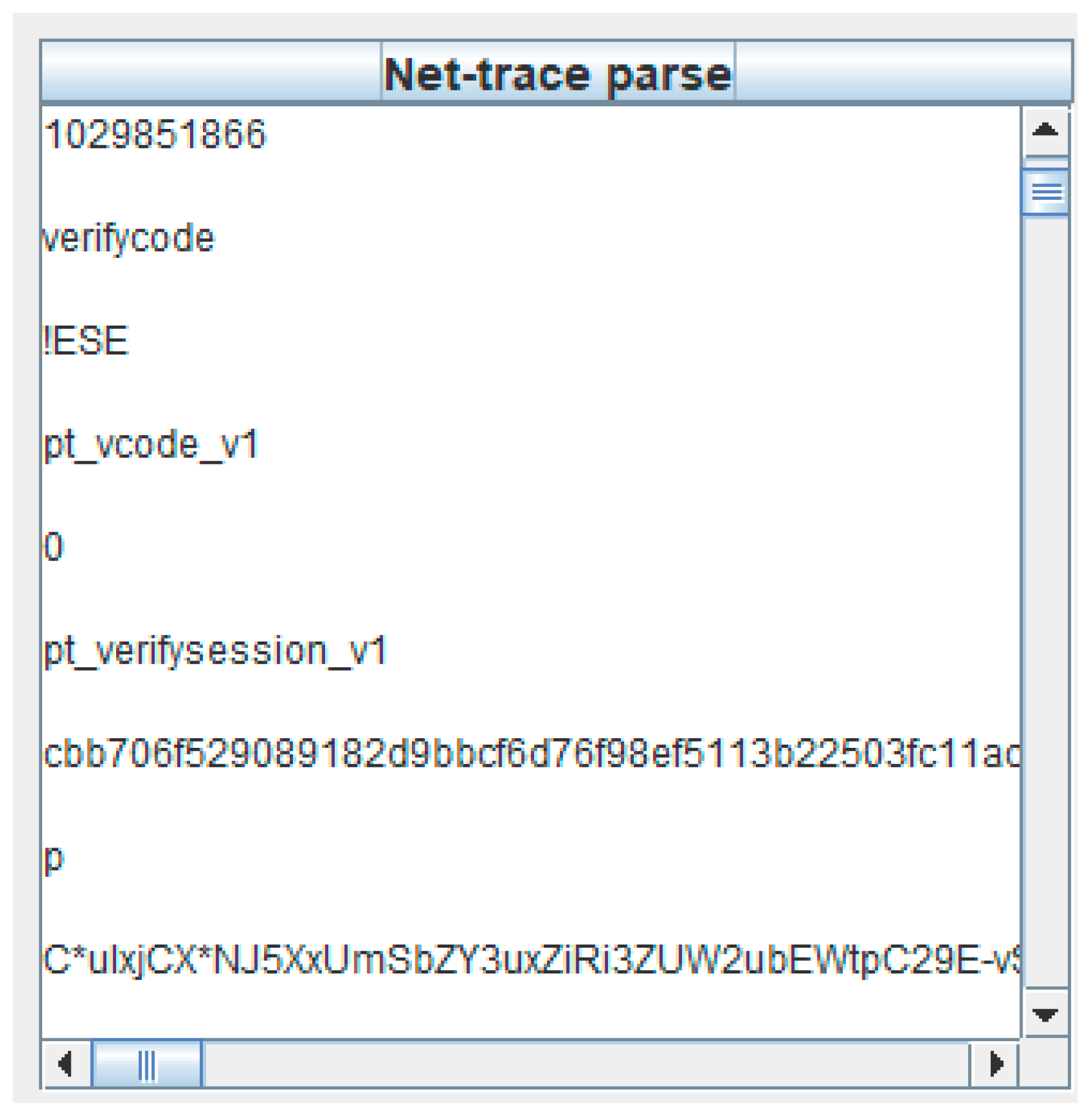
4.1.1. Net-Trace Parse Module
- (1)
- Scan client-side implementations to extract the message symbols and build the sets of message symbols.
- (2)
- Build a set of end symbols and a set of non-end symbols using extracted message symbols.
- (3)
- Sort the non-end symbols in the order of descendent frequency.
- (4)
- Get net-traces with MITM proxy.
- (5)
- Parse net-traces through identifying message symbols to generate message pieces, message blocks, and message tokens.
- (6)
- Generate message tokens Tn.
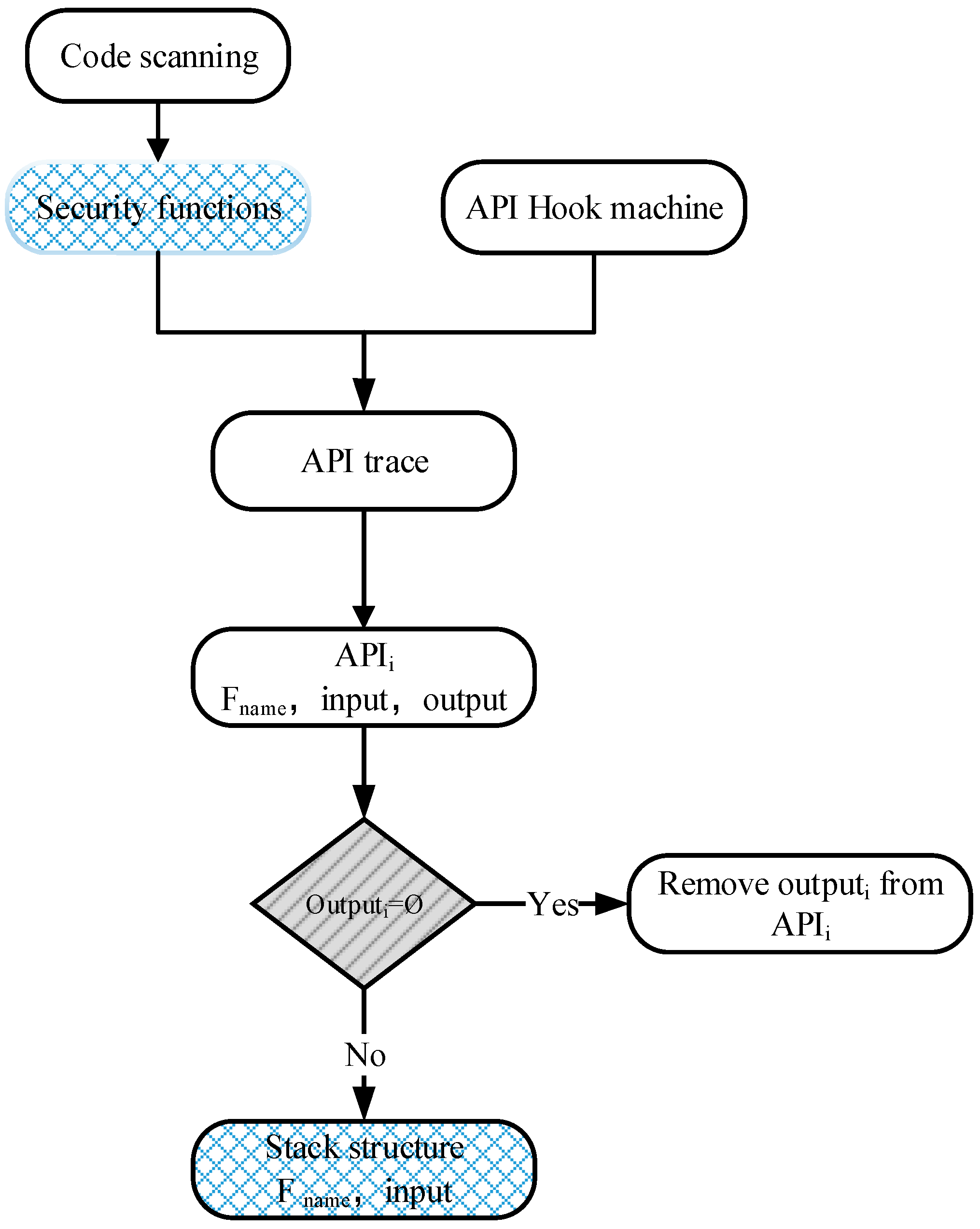
4.1.2. API Trace Parse Module
- (1)
- Scan the client-side implementations of security protocols and extract cryptographic primitive implementations.
- (2)
- Trace the extracted cryptographic primitive implementations through API tracing technology to generate the API traces stored in a local log file.
- (3)
- Get the API traces APIi from log file that contains the function name, arguments, and outputs of the traced cryptographic primitive implementations.
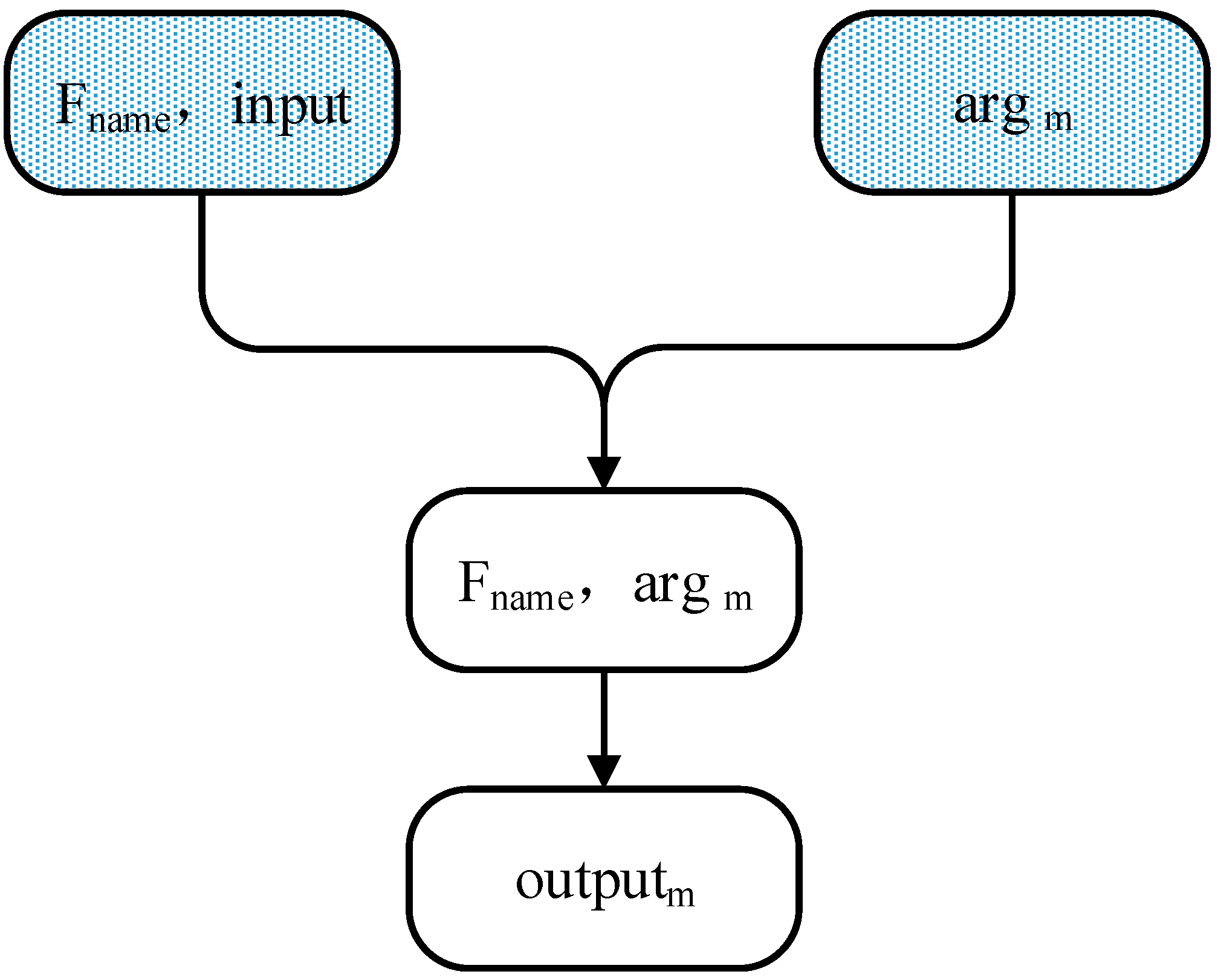
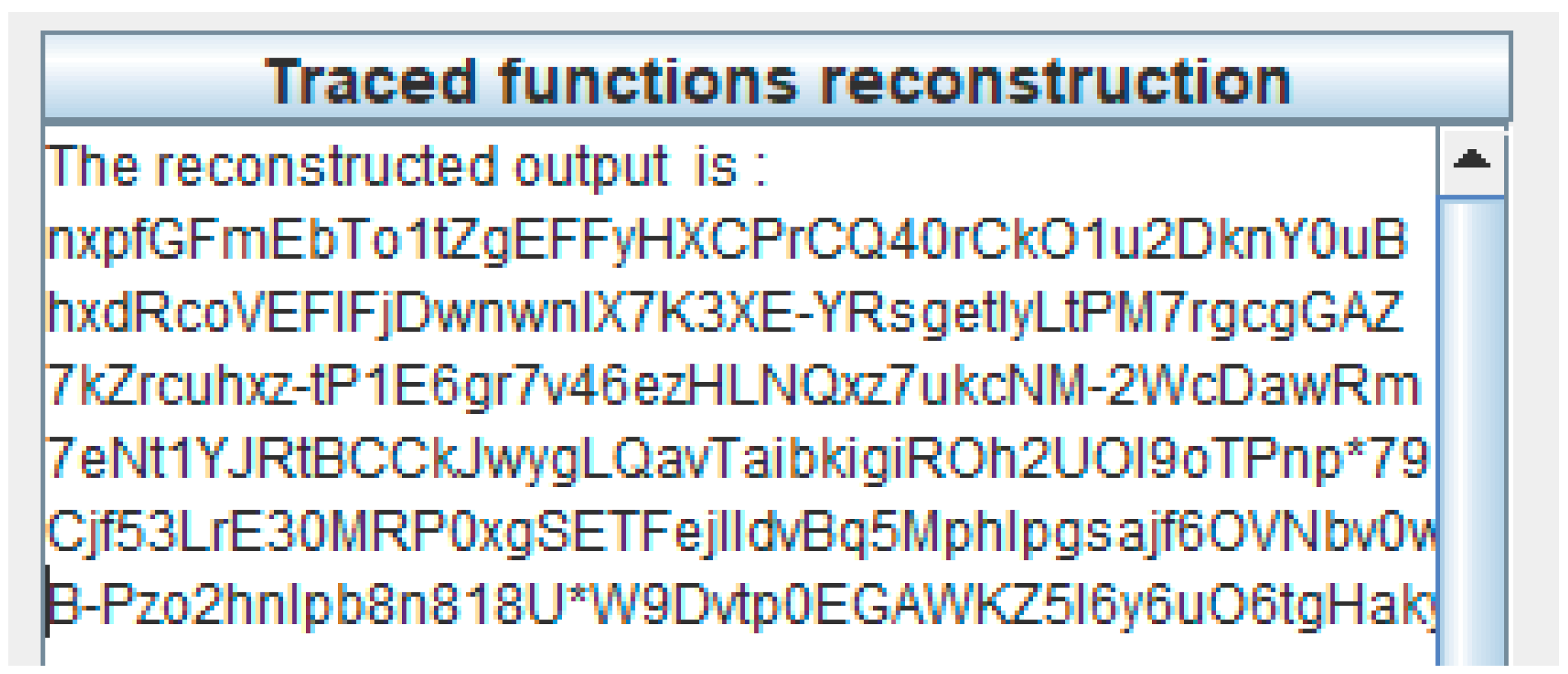
4.1.3. Function Reconstruction Module
- (1)
- Modify arguments stored in stack to produce modified argument argm.
- (2)
- Re-execute the traced cryptographic primitive implementation with argm to generate reconstructed outputs outputm.
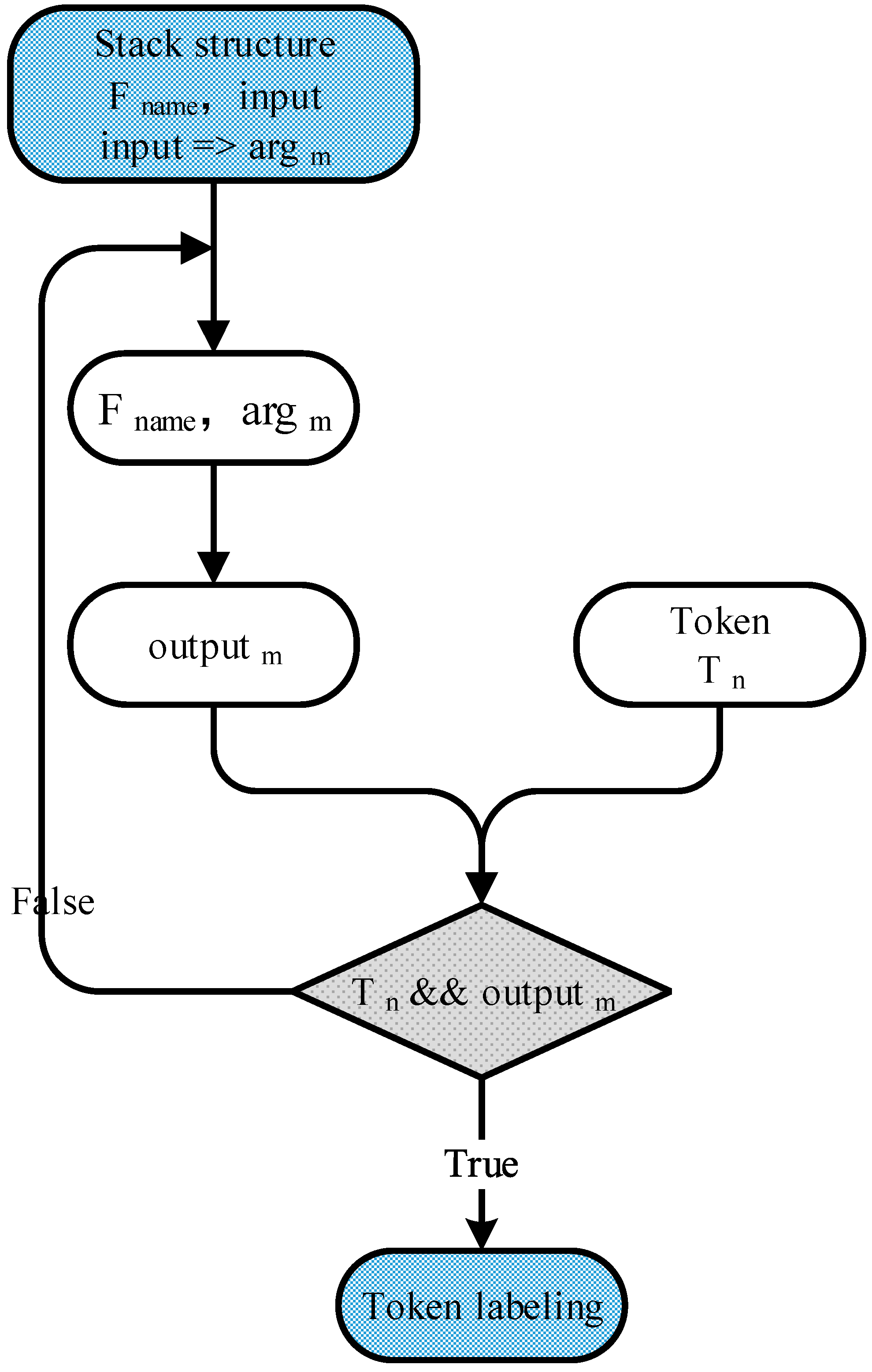
4.1.4. Token Location Module
- (1)
- Invoke the traced cryptographic primitive implementations from the data stored in the stack built by APTA, and modify the original arguments to generate the modified arguments argm.
- (2)
- Re-execute traced implementations to generate the reconstructed outputs outputm of cryptographic primitive implementations.
- (3)
- Locate and label message tokens through matching message tokens Tn with the output. If successfully matched, label the corresponding token.
4.1.5. Server Model Generation Module
4.2. Development
5. Evaluation
5.1. Case One: Tencent QQ Mail System Version 2017
5.2. Case Two: RSAAuth System
5.3. Discussion
6. Conclusions and Future Work
- (1)
- Universal methods or tools to extract, at a high automatic level, the security protocol implementations from web applications are necessary. The precondition of security analysis is to obtain security protocol implementations. However, the work is currently mainly performed by hand. Although there are some automatic methods for extracting security protocol implementations, these methods are not suitable for all security systems. Therefore, universal methods or tools that can extract the implementations of security protocols from web applications at a high automatic level are important.
- (2)
- So far, many client-side implementations have been obfuscated or encrypted to enhance the security of web security applications. Hence, handling encrypted or obfuscated client-side implementations is our core work in the future.
Author Contributions
Funding
Conflicts of Interest
References
- Zhang, H.G.; Han, W.B.; Lai, X.J.; Lin, D.D.; Ma, J.F.; Li, J.H. Survey on cyberspace security. Sci. Sin. Inf. 2016, 46, 125–164. [Google Scholar] [CrossRef]
- Meng, B.; Lu, J.T.; Wang, D.J.; He, X.D. A survey of security analysis of security protocol implementation. J. Shandong Univ. (Nat. Sci.) 2018, 53, 1–18. [Google Scholar] [CrossRef]
- Zhang, H.G.; Wu, F.S.; Wang, H.Z.; Wang, Z.Y. A Survey: Security Verification Analysis of Cryptographic Protocols Implementations on Real Code. Chin. J. Comput. 2018, 41, 288–308. [Google Scholar] [CrossRef]
- Meng, B.; Huang, C.T.; Yang, Y.T. Automatic Generation of Security Protocol Implementations Written in Java from Abstract Specifications Proved in the Computational Model. Int. J. Netw. Secur. 2017, 19, 138–153. [Google Scholar] [CrossRef]
- Narayan, J.; Shukla, S.K.; Clancy, T.C. A survey of automatic protocol reverse engineering tools. ACM Comput. Surv. 2016, 48, 40. [Google Scholar] [CrossRef]
- Ye, Q.Q.; Bai, G.D.; Wang, K.; Dong, S. Formal Analysis of a Single Sign-On Protocol Implementation for Android. In Proceedings of the 2015 20th International Conference on Engineering of Complex Computer Systems (ICECCS), Washington, DC, USA, 9–12 December 2015; pp. 9–12. [Google Scholar]
- Zuo, C.S.; Wang, W.B.; Wang, R.; Lin, Z.Q. Automatic Forgery of Cryptographically Consistent Messages to Identify Security Vulnerabilities in Mobile Services. In Proceedings of the Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 21–24 February 2016; 17p. [Google Scholar]
- Bai, G.D.; Lei, J.; Meng, G.Z.; Venkatraman, S.S.; Saiena, P.; Sun, J.; Li, Y.; Dong, S. AUTHSCAN: Automatic Extraction of Web Authentication Protocols from Implementations. In Proceedings of the 20th Annual Network & Distributed System Security Symposium (NDSS), San Diego, USA, 24–27 February 2013; 20p. [Google Scholar]
- Kobeissi, N.; Bhargavan, K.; Blanchet, B. Automated Verification for Secure Messaging Protocols and Their Implementations: A Symbolic and Computational Approach. In Proceedings of the 2017 IEEE European Symposium on Security and Privacy (EuroS&P), Paris, France, 26–28 April 2017; 16p. [Google Scholar]
- Jürjens, J. Automated Security Verification for Crypto Protocol Implementations: Verifying the Jessie Project. Electron. Notes Theor. Comput. Sci. 2005, 250, 123–136. [Google Scholar] [CrossRef]
- Dupressoir, F.; Gordon, A.D.; Jürjens, J. Guiding a General-Purpose C Verifier to Prove Cryptographic Protocols. In Proceedings of the 24th IEEE Computer Security Foundations Symposium, Cernay-la-Ville, France, 27–29 June 2011; pp. 3–17. [Google Scholar]
- Bhargavan, K.; Fournet, C.; Gordon, A.D. Modular verification of security protocol code by typing. In Proceedings of the 37th Annual ACM SIGPLAN-SIGACT Symposium on Principles of Programming Languages, Madrid, Span, 17–23 January 2010; pp. 445–456. [Google Scholar]
- Backes, M.; Maffei, M.; Unruh, D. Computationally sound verification of source code. In Proceedings of the 17th ACM Conference on Computer and communications security (CCS), Chicago, IL, USA, 4–8 October 2010; pp. 387–398. [Google Scholar]
- Swamy, A.; Chen, C.; Fournet, C. Secure distributed programming with value-dependent types. ACM Sigplan Not. 2011, 46, 266–278. [Google Scholar] [CrossRef]
- Swamy, N.; Hriţcu, C.; Keller, C.; Strub, P.-Y.; Rastogi, A.; Delignat-Lavaud, A.; Bhargavan, K.; Fournet, C. Semantic Purity and Effects Reunited in F*. In Proceedings of the 20th ACM SIGPLAN International Conference on Functional Programming, Vancouver, BC, Canada, 31 August–2 September 2015; 12p. [Google Scholar]
- Swamy, N.; Kohlweiss, M.; Zinzindohoue, J.K.; Zanella-Béguelin, S. Dependent Types and multi-monadic effects in F*. In Proceedings of the 43rd annual ACM SIGPLAN-SIGACT Symposium on Principles of Programming Languages (POPL), St. Petersburg, FL, USA, 20–22 January 2016; pp. 256–270. [Google Scholar]
- Lin, Z.Q.; Liang, X.X.; Xu, D.Y.; Zhang, X.Y. Automatic Protocol Format Reverse Engineering through Context-Aware Monitored Execution. In Proceedings of the 15th Symposium on Network and Distributed System Security (NDSS), San Diego, CA, USA, 24–27 February 2008; 17p. [Google Scholar]
- Cui, W.D.; Peinado, M.; Chen, K.; Wang, H.; Briz, L.I. Tupni: Automatic reverse engineering of input formats. In Proceedings of the 15th ACM Conference on Computer and Communications Security (CCS), Alexandria, VA, USA, 27–31 October 2008; pp. 391–402. [Google Scholar]
- Caballero, J.; Poosankam, P.; Kreibich, C.; Song, D. Dispatcher: Enabling active botnet infiltration using automatic protocol reverse-engineering. In Proceedings of the 16th ACM Conference on Computer and Communications Security (CCS), Chicago, IL, USA, 9–13 November 2009; pp. 621–634. [Google Scholar]
- Shi, X.L.; Zhu, F.Y.; Liu, L.; Lin, W. Method of Encrypted Protocol Reverse Engineering. Appl. Res. Comput. 2015, 32, 214–217. [Google Scholar] [CrossRef]
- Zhu, Y.N.; Han, J.H.; Yuan, L.; Gu, W.; Fan, Y.D. Protocol Ciphertext Field Identification by Entropy Estimating. J. Electron. Inf. Technol. 2016, 38, 1865–1871. [Google Scholar] [CrossRef]
- Protocol Information Project. Available online: httpwww.4tphi.net/~awalters/PI/PI.html. (accessed on 13 April 2018).
- Cui, W.D.; Kannan, J.K.; Wang, H. Discover: Automatic protocol reverse engineering from network trace. In Proceedings of the 16th USENIX Security Symposium on USENIX Security Symposium, USENIX Association, Berkeley, CA, USA, 6–10 August 2007. [Google Scholar]
- Wang, Y.P.; Meng, J. Biprominer: Automatic mining of binary protocol features. In Proceedings of the 12th International Conference on Parallel and Distributed Computing, Applications and Technologies (PDCAT), Gwangju, Korea, 20–22 October 2011; pp. 179–184. [Google Scholar]
- Wang, Y.P.; Yun, X.C.; Shafiq, M.; Wang, L.Y. A semantics aware approach to automated reverse engineering unknown protocols. In Proceedings of the 20th IEEE International Conference on Network Protocols (ICNP), Austin, TX, USA, 30 October–2 November 2012; 10p. [Google Scholar]
- Bermudeza, I.; Tongaonkar, A.; Iliofotou, M.; Mellia, M.; Munafò, M.M. Towards automatic protocol field inference. Comput. Commun. 2016, 84, 40–51. [Google Scholar] [CrossRef]
- Luo, J.Z.; Yu, S.Z. Position-based automatic reverse engineering of network protocols. J. Netw. Comput. Appl. 2013, 36, 1070–1077. [Google Scholar] [CrossRef]
- Yun, X.C.; Wang, Y.P.; Zhang, Y.Z.; Zhou, Y. A semantics-aware approach to the automated network protocol identification. IEEE/ACM Trans. Network. 2016, 24, 583–595. [Google Scholar] [CrossRef]
- Tao, S.Y.; Yu, H.G.; Li, Q. Bit-oriented format extraction approach for automatic binary protocol reverse engineering. IET Commun. 2016, 10, 709–716. [Google Scholar] [CrossRef]
- Bhargavan, K.; Fournet, C.; Gordon, A.D.; Tse, S. Verified interoperable implementations of security protocols. ACM Trans. Program. Lang. Syst. 2008, 31, 5. [Google Scholar] [CrossRef]
- Bhargavan, K.; Fournet, C.; Corin, R.; Zalinescu, E. Cryptographically verified implementations for TLS. In Proceedings of the 15th ACM Conference on Computer and Communications Security (CCS), Alexandria, VA, USA, 27–31 October 2008; pp. 459–468. [Google Scholar]
- Aizatulin, M.; Gordon, A.D.; Jürjens, J. Extracting and verifying cryptographic models from C protocol code by symbolic execution. In Proceedings of the 18th ACM Conference on Computer and Communications Security (CCS), Chicago, IL, USA, 17–21 October 2011; pp. 331–340. [Google Scholar]
- Li, Z.M.; Meng, B.; Wang, D.J.; Chen, W. Mechanized Verification of Cryptographic Security of Cryptographic Security Protocol Implementation in JAVA through Model Extraction in the Computational Model. J. Softw. Eng. 2015, 9, 1–32. [Google Scholar] [CrossRef]
- Avinash, S.; Alessandro, A.; Roberto, C.; Compaagna, L. Attack Patterns for Black-Box Security Testing of Multi-Party Web Applications. In Proceedings of the Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 21–24 February 2016; 15p. [Google Scholar]
- Giancarlo, P.; Constantin, T.; Eric, B.; Rossow, C. jÄk: Using Dynamic Analysis to Crawl and Test Modern Web Applications. In Proceedings of the International Workshop on Recent Advances in Intrusion Detection Reseach in Attacks, Instructions and Defense (LNCS), Kyoto, Japan, 2–4 November 2015; pp. 295–316. [Google Scholar]
- Deedleman, S.B.; Wunsch, C.D. A general method applicable to the search for similarities in the amino acid sequence of two proteins. J. Mol. Biol. 1970, 48, 443–453. [Google Scholar] [CrossRef]
- Burp Suite Scanner. Available online: https://portswigger.net/burp (accessed on 15 January 2018).
- QQ Mail Login. Available online: https://mail.qq.com/ (accessed on 12 January 2018).
- Cui, W.; Paxson, V.; Weaver, N.; Katz, R.H. Protocol-independent adaptive replay of application dialog. In Proceedings of the Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 21–24 February 2016. [Google Scholar]
- Ahn, L.; Von Blum, M.; Hopper, N.J.; Langford, J. Captcha: Using hard ai problems for security. In Proceedings of the International Conference on the Advances in Cryptology—EUROCRYPT, Warsaw, Poland, 4–8 May 2003; pp. 294–311. [Google Scholar]











| Environment | Tools | Languages |
|---|---|---|
| Windows 10, ×64 bit | Eclipse 3.7, Java JDK1.7, 64 bit | Java, Java Script |
| Systems | Client-Side Implementations | Server Abstract Model | Results |
|---|---|---|---|
| QQ mail | p -> salt -> 3 times MD5 > rsaencrypt -> p′ | p -> decrypt -> verifyMD5 | Less vulnerable |
| RSAAuth | Pwd -> rsaencrypt -> base64encode -> M | M -> crypt -> decode | Vulnerable |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lu, J.; Yao, L.; He, X.; Huang, C.; Wang, D.; Meng, B. A Security Analysis Method for Security Protocol Implementations Based on Message Construction. Appl. Sci. 2018, 8, 2543. https://doi.org/10.3390/app8122543
Lu J, Yao L, He X, Huang C, Wang D, Meng B. A Security Analysis Method for Security Protocol Implementations Based on Message Construction. Applied Sciences. 2018; 8(12):2543. https://doi.org/10.3390/app8122543
Chicago/Turabian StyleLu, Jintian, Lili Yao, Xudong He, Chintser Huang, Dejun Wang, and Bo Meng. 2018. "A Security Analysis Method for Security Protocol Implementations Based on Message Construction" Applied Sciences 8, no. 12: 2543. https://doi.org/10.3390/app8122543
APA StyleLu, J., Yao, L., He, X., Huang, C., Wang, D., & Meng, B. (2018). A Security Analysis Method for Security Protocol Implementations Based on Message Construction. Applied Sciences, 8(12), 2543. https://doi.org/10.3390/app8122543





