2.1. General Context
In a general case of entanglement distribution, Alice and Bob usually have quantum channels connecting them to Charlie, another node in the network. We refer to Charlie as a third party, who might actually represent a laboratory that generates maximally entangled pairs and then sends each particle to Alice and Bob, thus having successfully provided them with shared entanglement. Nevertheless, problems arise when considering practical situations of entanglement distribution. Although one ebit constitutes a perfect, noiseless transmission channel for Alice and Bob [
10], the entangled pair is still distributed via noisy quantum channels, hence its purity is altered and our parties will eventually share a non-maximally entangled state (less than 1 ebit). By executing the teleportation protocol with such a resource, perfect reconstruction of the original qubit cannot be accomplished.
A major result that overcomes these limitations is the process of
entanglement purification [
2,
10], which is possible via local operations. The purpose of purification protocols is to
concentrate the entanglement of a certain number of entangled pairs to obtain a higher amount of entanglement for a smaller number of pairs. Given sufficient partially-entangled pairs shared by Alice and Bob, under LOCC, they can obtain a pair with entanglement close to 1 ebit in order to teleport a qubit with satisfactory fidelity. Entanglement concentration using nonlinear optics is presented in [
11].
Even though entanglement can be concentrated, this process is successful under a minimum fidelity condition for the initial pairs, which cannot be met beyond certain distances [
10,
12]. It is reasonable to assume that distances between such arbitrary nodes as those represented by Alice and Bob are significant enough to make this process rather infeasible. This led to the emergence of
quantum repeaters [
12], devices that use
entanglement swapping [
13,
14,
15] and purification in order to propagate entanglement in shorter segments (node to node), until source and destination are linked by an almost maximally entangled pair. Thus, quantum repeaters are key elements in the framework of a quantum network and they have been considered in various entanglement distribution schemes. The phenomenon of entanglement swapping for continuous variables is discussed in [
16]. A quantum key distribution scheme involving entanglement swapping is proposed in [
17], while a quantum conferencing scheme for secure communication between several users is developed in [
18].
An entanglement distribution scheme was recently proposed as an optimal routing protocol that ensures the greatest entanglement distribution rate between two arbitrary nodes in a quantum network [
19]. It operates on a graph model of the network, while taking into account physical challenges such as the stochastic nature of entanglement generation, imperfect Bell measurement and short coherence time
of memories in quantum repeaters. Given multiple possible routes between two nodes, the protocol finds the optimal one according to a route metric. The optimality of the path provides the highest average number of successfully established entangled pairs between two nodes in unit time, considering the coherence time interval
. Through numerical simulations, the underlying algorithm of the protocol was proven to outperform classical graph algorithms (Dijkstra, Bellman–Ford) used in conventional routing.
Two other previously proposed routing schemes are referred to as
quantum relay and
EPR-pair bridging [
20] (maximally entangled pairs of particles are also called EPR-pairs). Considering Alice and Bob do not share entangled pairs with each other, but rather each of them does with another node Charlie, then a quantum relay method achieves teleportation of a qubit from Alice to Bob in two steps: Alice teleports first to Charlie, followed by him teleporting to Bob. By extension, an arbitrary number of intermediate nodes can exist between Alice and Bob, with entangled pairs set up between adjacent stations. This hop-by-hop “forwarding” mechanism exhibits an obvious lack of security and privacy [
20], as the initial quantum information passes through all the nodes before finally reaching its intended destination. EPR-pair bridging addresses this problem by implementing a swapping scheme that provides Alice and Bob with a shared entangled pair. A Bell measurement performed by Charlie on his qubits and a subsequent transmission of classical information will establish entanglement as a particular Bell state between qubits held by Alice and Bob. Using this method based on entanglement swapping, direct teleportation is realized between source and destination. A quantum routing protocol was considered as a combination of quantum relay and EPR-pair bridging mechanisms, without necessary time synchronization between nodes, as a faster completion of operations at source or at the intermediate nodes would degenerate into the former or the latter scheme, respectively [
20].
Entanglement swapping is a phenomenon of paramount importance for the entanglement distribution process between two distant nodes. In a most elementary scenario, we consider that there is a node
O halfway between Alice (
A) and Bob (
B) that can generate entangled pairs of particles and then distribute them accordingly. This distribution scheme can be improved, as proposed in [
9]. It was demonstrated that a significant speedup is exhibited when further nodes are introduced on the routes
and
. Considering Alice and Bob are separated by a distance
L and assuming entangled qubits travel at a speed
v, the time required for our parties to receive their qubits generated at
O is no less than
. By placing distribution nodes
C and
D halfway on paths
and
, they generate entangled pairs and simultaneously send a qubit to
O and the other one to
A and
B, respectively. The time generated qubits require to arrive at their destination nodes is reduced to
. Following a Bell measurement performed at
O that takes
to complete, Alice and Bob finally share entanglement. Without accounting for the time necessary for classical information associated with the measurement to be received, then
A and
B are supplied after an interval of
, which is less than
, provided
.
Having analyzed the framework of the problem and several existing protocols, we now continue with presenting our approach to how entanglement can be restored between Alice and Bob in a practical quantum network scenario, improving and generalizing previous results.
2.2. Our Proposal
Given the already existing network infrastructure and taking into account financial costs, a future large scale quantum network would most likely be mapped onto it. Therefore, optical fiber links will represent quantum channels and most nodes will likely use quantum equipment to achieve various tasks. Our solution is formulated in such a context and has at the very basis the idea described in [
9], which we improve and generalize. We now define our general model of the network and the elements that are part of our scheme.
We consider a hybrid network (having both classical and quantum nodes) with a graph-like topology. Each component node is identified by an address (as an IP address), it is linked by a quantum channel to at least one other node and has a particular status, i.e., it is tasked with accomplishing a certain operation. An important class of nodes we consider is represented by quantum switches (QS), devices that are able to execute quantum routing protocols, generate entangled pairs of particles and perform various types of measurements on qubits. Our parties Alice and Bob are two nodes separated by an arbitrary distance that frequently exchange quantum information via teleportation. Thus, shared entanglement is a key resource they require to achieve their task. After each completed teleportation, their entangled pair is destroyed and another teleportation is not possible. Considering arbitrary distances between end nodes, they cannot afford to locally create entangled pairs of particles and send half of each to their partner. The idea we investigate is how they can be efficiently supplied with another entangled resource. Before discussing it, we present the assumptions based on which the scheme operates.
Assumptions:
entanglement generation, Bell measurement (BSM) and other local quantum operations are performed perfectly in a negligible amount of time;
transmission of entangled qubits between adjacent nodes is realized with high fidelity and does not require purification mechanisms.
These quantum operations are treated as theoretical processes that are abstract. We are not concerned with their physical nature; otherwise, we would not be able to model them as perfect and instantaneous in our scheme. Travel time between nodes can be neglected as well; however, that is not the most important aspect for our analysis. We discuss the time efficiency of the protocol in
Section 2.2.2 by considering through how many hops entangled particles must pass until shared entanglement is achieved between the two parties.
We consider that Alice and Bob initially share several entangled pairs of particles described, for example, by Bell state
. After the last teleportation is performed, Alice and Bob acknowledge their resupply need and synchronize with each other in order to send an appropriate classical message to each other at the same time. We label this special message
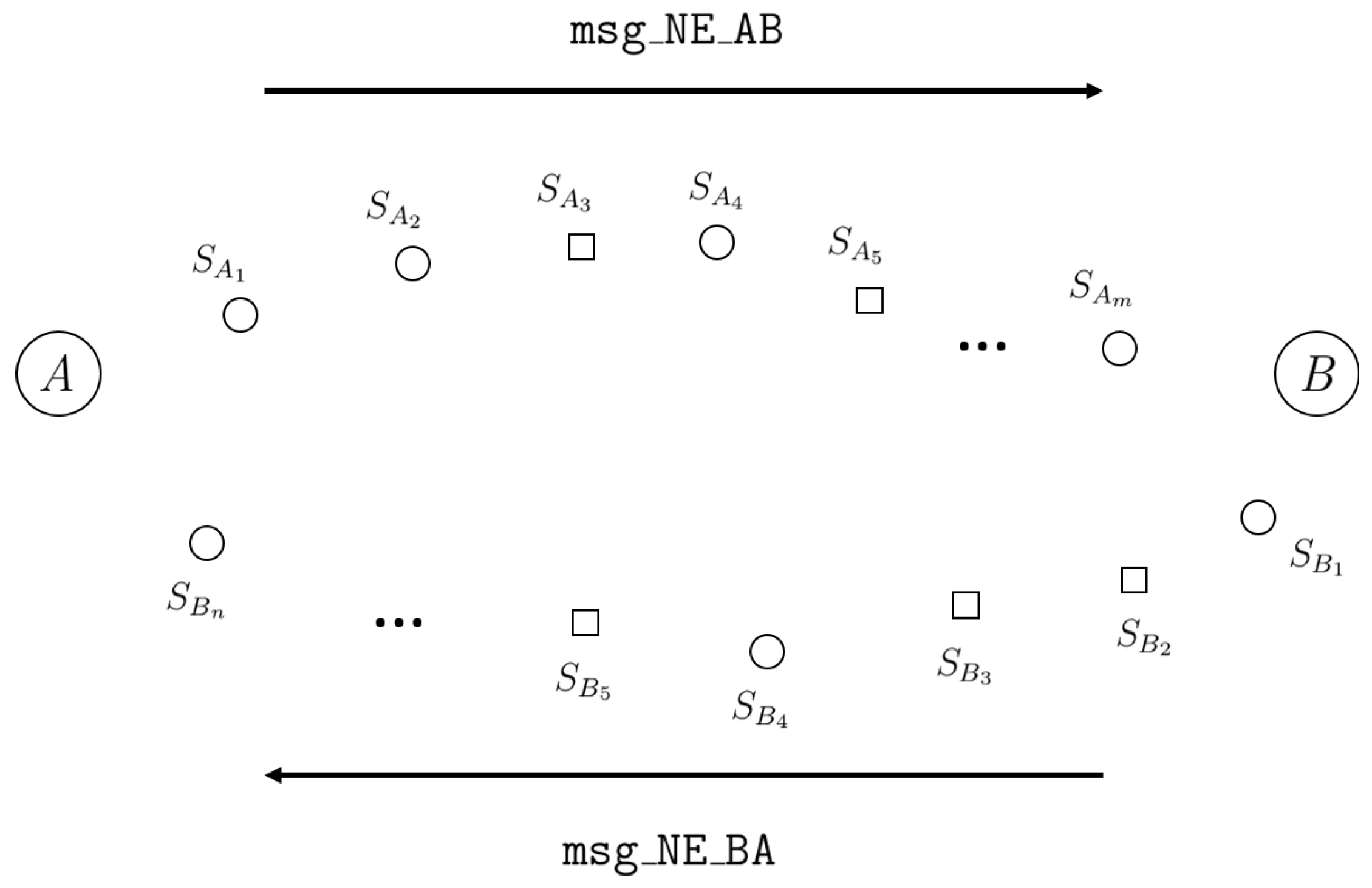
msg_NE_XY, where “NE” stands for “Need entanglement”, “X” is the sender and “Y” is the receiver. These two messages may reach their destination by different routes, as depicted in
Figure 1. We denote the route taken by each message by the set of nodes it passes through:
Alice to Bob:
Bob to Alice:
These sets of nodes may coincide; however, this particular circumstance will rarely occur when considering that a continuous level of network activity would make some routes congested, therefore requiring a different route to be found.
Among each set of nodes, there is a subset consisting entirely of quantum switches.
Each quantum switch is able to interpret the special message
msg_NE_XY and subsequently make itself visible to sender
X by confirming its status as a quantum node through a classical message sent back to source,
msg_ACK_X:
Upon receiving confirmation from each quantum switch, Alice and Bob have their own list of IP addresses that describes a route between them consisting exclusively of quantum nodes:
Route from Alice to Bob (known by Alice):
Route from Bob to Alice (known by Bob):
To begin the distribution process, Alice and Bob each send an encoded classical message, as seen in
Table 1, to every node
and
, respectively and also to their partner in order to instruct them on how to act further. This classical information is labeled
msg_ACT_A and
msg_ACT_B to suggest who it is sent from, Alice or Bob:
Our designed scheme operates by isolating the number of active quantum switches (AQS) on a route between source and destination to , for . The protocol is symmetric; therefore, we will discuss here the case regarding Alice’s perspective.
Considering that , we may label the selected subset of AQS as , with . Quantum switches that are not part of this subset will be referred to as being inactive (IQS). An important aspect must be clarified here. IQS are designated by Alice or Bob in order to restrict the number of quantum switches that actively participate during the protocol to . This is how our scheme is devised and it operates on this symmetry argument given by the number N of AQS. There can be at most three IQS and they will be sent an instruction message that makes them operate as classical switches (CS).
For now, we consider that for brevity in notation (the case when means that differs from by three maximum IQS, which can be considered as classical ones operating just for qubit routing).
According to the choice of
N, there will be an odd number of such AQS. Following the labeling convention in Equations (
1) and (2) and considering the common notation (see [
9]), we will refer to the node situated halfway in the set
as
. There are
quantum switches on each of the segments
and
. Considering
and
, halfway on the list of quantum switches found on paths
and
are nodes
and
, respectively. Taking into account both paths relative to the position of
, the nodes will act in the following manner:
each node from generates a pair of particles in Bell state ; Alice and Bob may agree on any Bell state to be shared after the completion of the protocol. To accomplish this task, they would need to exchange classical information encoding the identity of the Bell state (for example, ), followed by Alice’s instructions sent to every quantum switch she discovered to prepare the appropriate state. The distribution process will then continue as before, making sure that after each BSM the necessary classical information is transmitted between nodes to reconstruct each time, so that Alice and Bob share this state in the end.
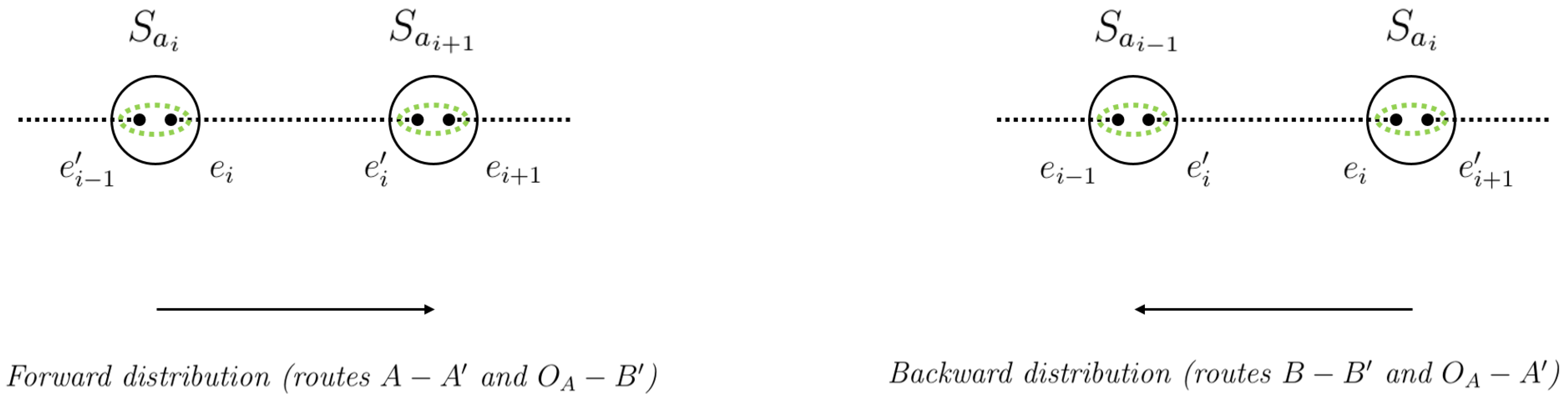
particle e is kept and is sent to an adjacent node, according to the following rules:
Path :
Path :
- –
- –
We make an important remark here. According to the particle flow previously represented, Alice sends one particle of her EPR pair to her nearest node, which is a quantum one. Halfway node and Bob’s nearest node are also quantum nodes. This choice makes the notation consistent, although that node might as well be a classical switch, in which case it would just forward the qubit until it reaches a quantum switch. IQS and CS are not explicitly present in these representations, but they assist in the dynamics of the scheme.
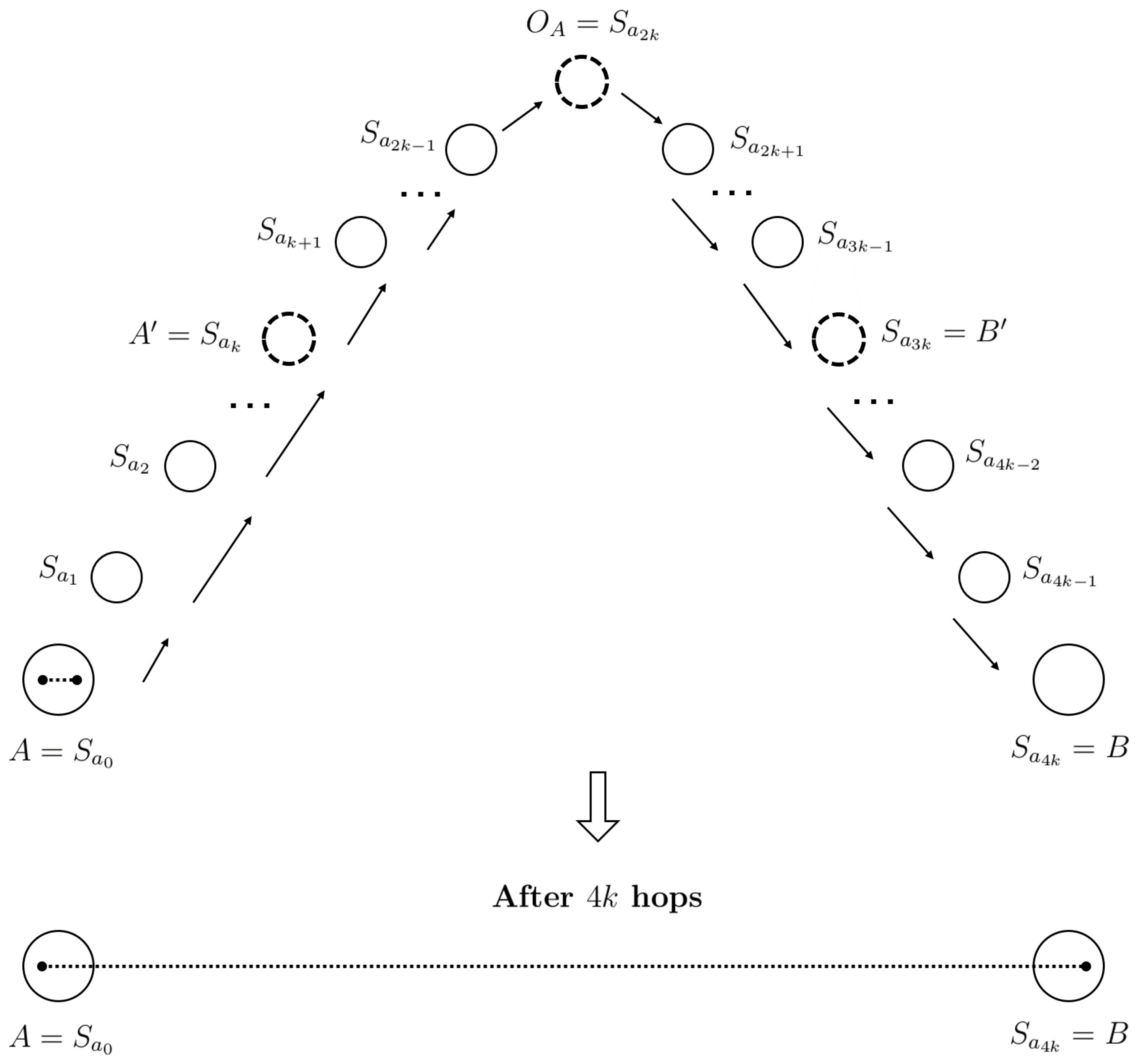
A distribution of entanglement performed in a manner that does not imply swapping is depicted in
Figure 2. Alice initially prepares her entangled pair of qubits and then sends one particle to her nearest node, which in turn forwards it to its neighbor and so on. There are
hops required during this process for Bob to receive the particle. Assuming each hop is realized in one unit of time, then Alice and Bob will share entanglement after
units of time.
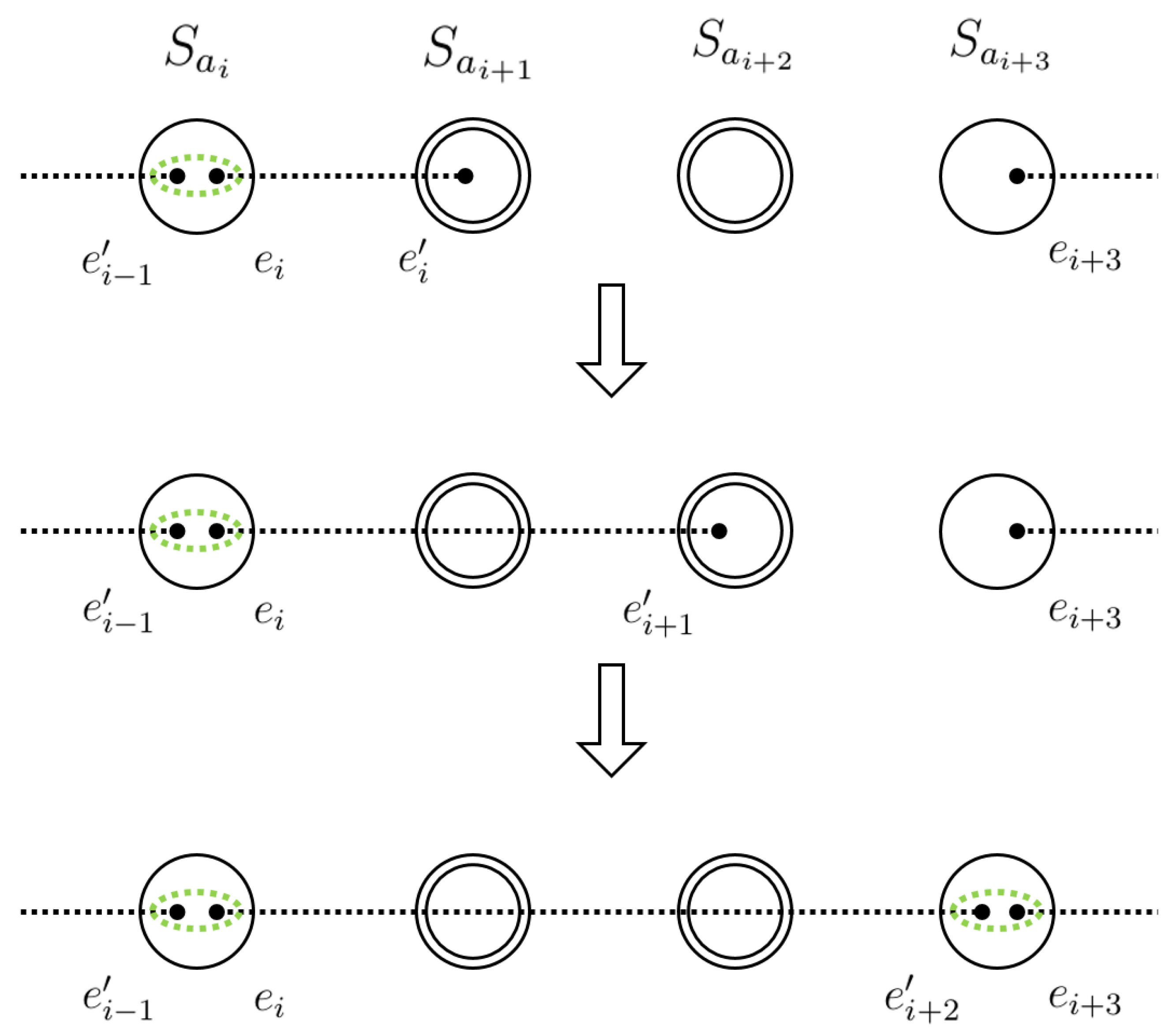
Based on these distribution rules, there are four path segments from A to B as the following sets:
Then, as expressed in (3)–(6),
and
contain indices that identify active quantum switches on
forward and
backward distribution routes, respectively, as shown in
Figure 3.
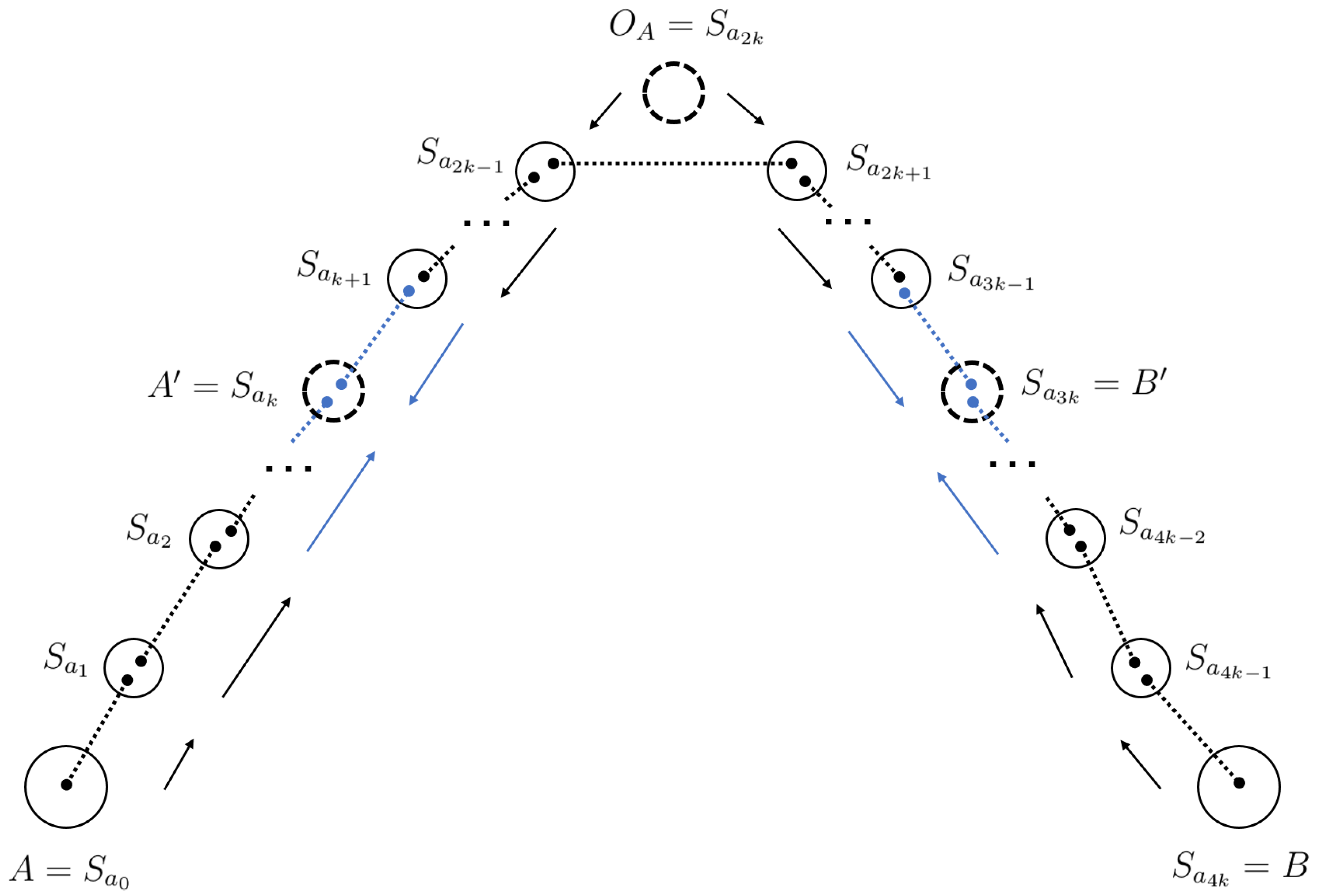
Considering that a classical switch cannot execute quantum-specific operations, it will not require a particular instruction message, since it can only route the received qubit further until it reaches a quantum switch.
The main goal of the protocol is to ensure particles reach nodes
and
via both upstream (from
A and
B towards
) and downstream (from
towards
A and
B) routes. Considering each intermediate quantum switch, i.e., each node from
has successfully received the qubit from its nearest node and has itself sent one from its generated pair, then it performs a BSM on the two qubits from different pairs to accomplish entanglement swapping, thus propagating the entanglement towards middle nodes
and
. Additional classical information resulting from the measurement is required to be provided to the destination node in order to preserve the original Bell state
. This step is completed by applying an appropriate corrective operation
to the received qubit. These two nodes
and
will be the last ones to possess two qubits received from upstream and downstream. A subsequent BSM performed by both of them on their qubits will then establish entanglement between Alice and Bob, therefore achieving the original task. We remark that a total of
Bell measurements are performed during the entire process, along with the same number of classical messages sent to assist in adjusting the received state to be the correct one. A visual representation of the the distribution process is shown in
Figure 4.
As previously mentioned, the scheme we have presented takes advantage of a configuration of
quantum switches between Alice and Bob. Thus,
quantum switches will not participate in the protocol. Since each active quantum switch must receive a qubit, be able to generate an entangled pair and then send one qubit to the next quantum switch, the inactive
ones will act as classical switches and only route the qubit further, until another AQS is reached. Under these circumstances, there will be
at most three IQS on the route from Alice to Bob:
| ● |
⇒ | all QS are AQS, |
| ● | ⇒ | IQS, |
| ● | ⇒ | IQS, |
| ● | ⇒ | IQS, |
| ● |
Figure 5 depicts a scenario that involves two IQS between two AQS.
After receiving Alice’s request message msg_NE_A, each QS sends an acknowledgment message back to Alice, revealing its address to her. When there is a non-zero difference between the number of QS (p) and the number of AQS (N), Alice makes a decision regarding which switches will participate in the protocol. Those excluded will be sent a classical message msg_ACT_A = 0 to assist those AQS just by forwarding the qubits received from them. She identifies nodes , and in order to properly instruct the remaining ones about the distribution rules. Bob (B) will receive an instruction msg_ACT_A = 1 (the corresponding operation is also performed by Alice), while will receive msg_ACT_A = 2. Nodes and will receive from Alice msg_ACT_A = 3 to denote their BSM operation. The remaining AQS must generate entangled pairs and then perform a BSM, an operation which is communicated as msg_ACT_A = 4.
Alice generates her entangled pair and sends one particle to the nearest node; then, she waits for the protocol to execute and finally receives two bits of information from after its measurement, in order to recover the accurate Bell state. On Bob’s segment, also provides him with this classical information. After these last two measurements, Alice and Bob share an entangled pair in Bell state to be used in yet another teleportation they wish to perform.
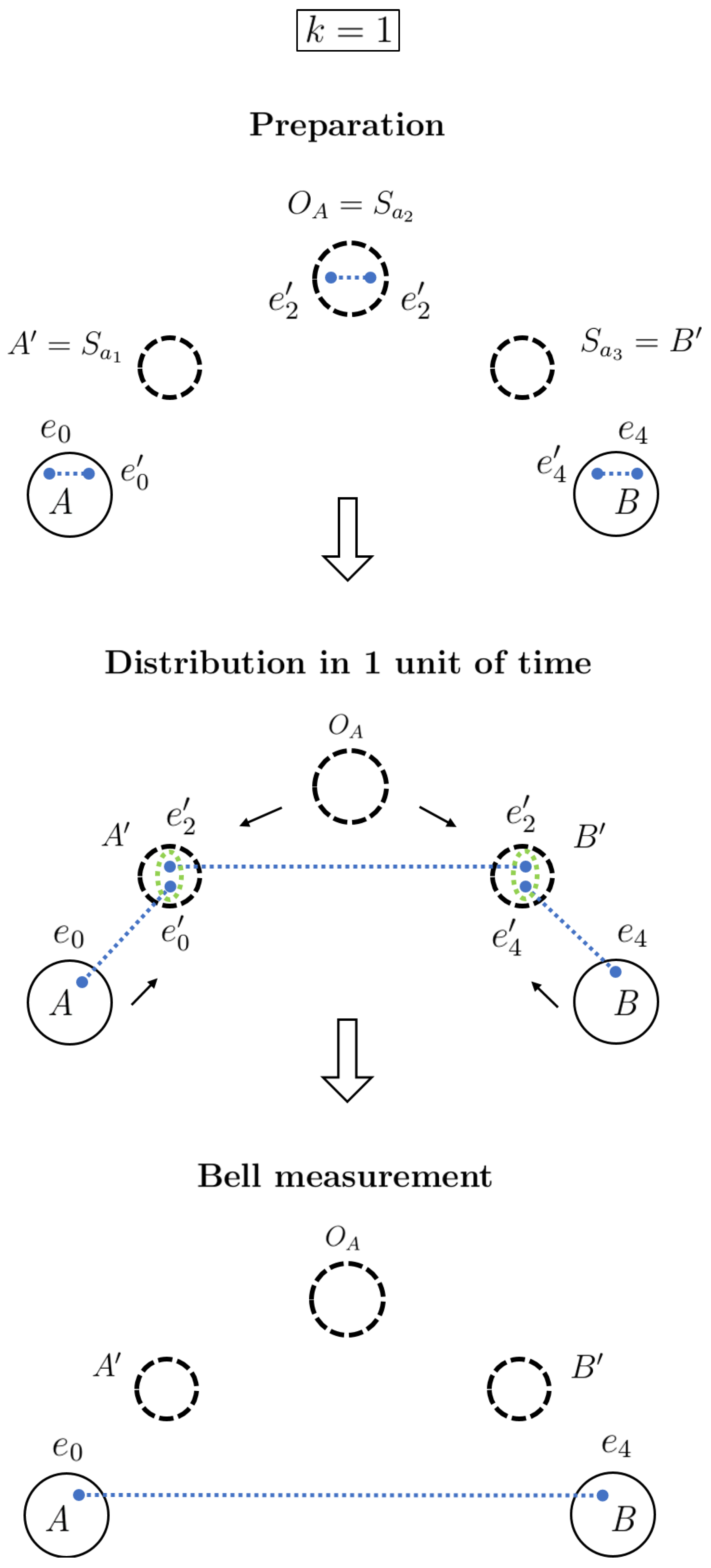
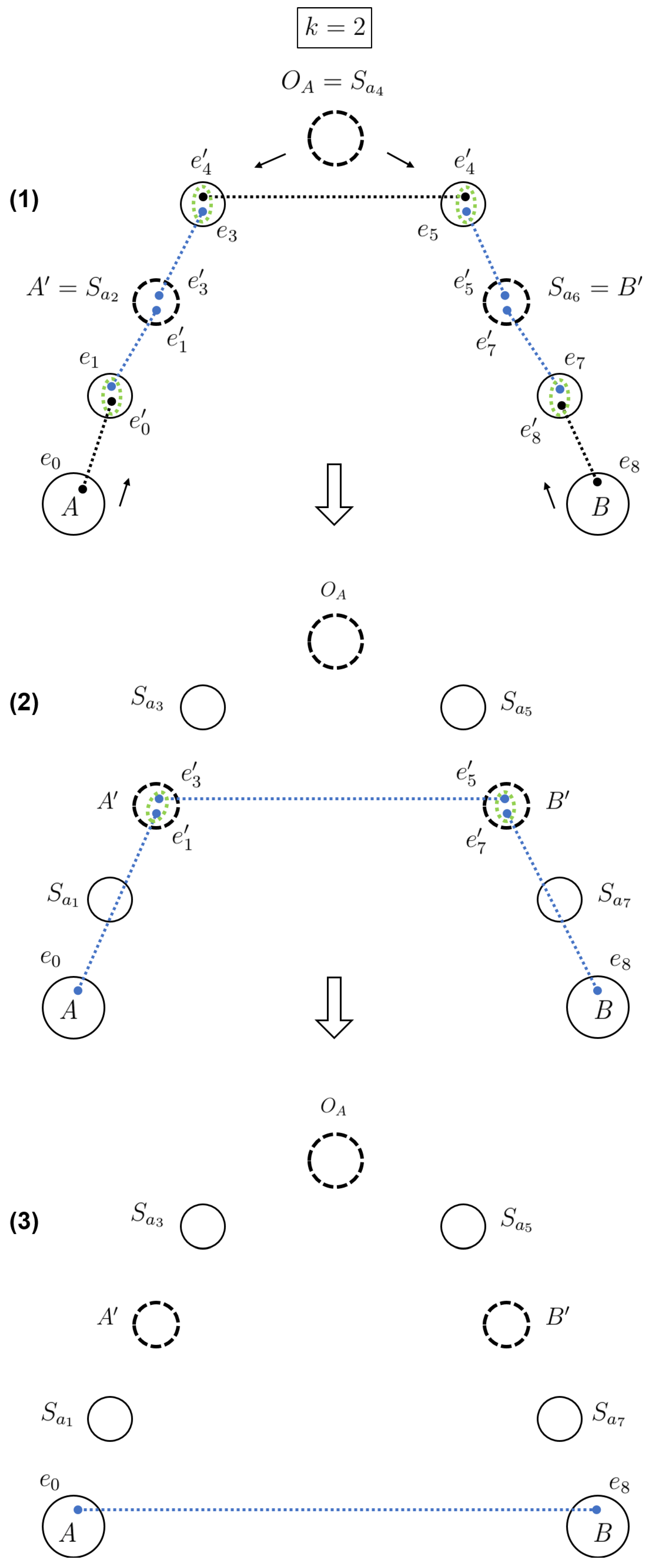
2.2.1. Exemplification
A representation of the protocol for the first and second particular cases is depicted in
Figure 6 and
Figure 7, respectively. It should be noted that CS and IQS are not pictured explicitly; however, their actions contribute to the functionality of the scheme. In
Figure 6, we consider
, so there are three AQS between Alice and Bob. Nodes
distribute generated entangled qubits directly to
and
, which then perform a BSM and provide Alice and Bob with entanglement. In
Figure 7, we consider
; therefore, seven AQS are present on the path from Alice to Bob. This time the distribution of particles propagates towards
and
by intermediate Bell measurements performed by the other AQS. Finally,
and
are the last ones to perform a BSM, which entangles the qubits kept by Alice and Bob.
2.2.2. Efficiency
We continue with emphasizing a feature of our proposal based on a time efficiency analysis. The general scenario involves the existence of these
active quantum switches between Alice and Bob. As depicted in
Figure 2, the straightforward approach of Alice preparing an entangled pair and sending the other particle to Bob is done in
units of time, an interval we label as
. When the quantum switch
between
A and
B is employed in the protocol, it prepares its entangled pair and sends each particle to them. Thus, the time required for each qubit to reach its destination is reduced to
, assuming the intermediate node is located halfway on the route from Alice to Bob and qubits travel at the same speed.
The first particular case of our protocol is , for which there are nodes between Alice and Bob that participate in the distribution, i.e., one additional quantum switch found halfway on the segments and . According to the steps of the scheme, qubits must arrive at and . A BSM is then performed at these stations, followed by (two) transmissions of classical information as part of entanglement swapping. Considering this classical information takes a time to reach its destination and the transmissions occur in parallel, we observe that Alice and Bob will have their desired pair in an interval of .
As the number of quantum switches
N increases, we derive the general relation that describes the time resources needed to supply Alice and Bob with entanglement,
As
N becomes larger, the distance between quantum switches will be short enough to consider
negligible. Therefore, the protocol reduces the distribution time by a factor of
relative to direct transmission of qubits from Alice to Bob,
We make some important remarks here. Once all AQS receive Alice’s instruction messages, they begin executing their specific actions in parallel. For the overall distribution time, we do not account for the time it takes for AQS to receive their instructions. Given that entanglement swapping is the key principle of operation, the order in which it happens is not important because the entanglement propagates between nodes until it eventually reaches Alice and Bob. Therefore, Alice’s particle from her EPR pair must only go through one hop, unlike standard distribution which requires hops.
The series of operations we have presented so far are related to the route from Alice to Bob. The protocol is symmetric, i.e., the analogous operations are performed from Bob’s perspective. Hence, Alice and Bob are actually supplied with two ebits in the time interval , one ebit from each route.