1. Introduction
In recent years, Wireless Body Area Networks (WBAN) have been attracting the national interest of biomedical informatics by meeting the communication technology requirement. Many related studies have concentrated on fusing medical services and communication technologies to realize unexplored fields of medical service for enhanced quality of life. This development can conserve the cost of medical services and allow wide distribution of medical knowledge to nonmedical personnel.
In this setup, all information of the users who wear the healthcare equipment should be gathered by micro-sized sensors, which measure and collect body signals, such as electrocardiogram (ECG), electroencephalogram (EEG), or Vital Sign (e.g., heart rate, blood pressure, temperature, pH, respiration, oxygen saturation) [
1]. These signals should be delivered to a remote base station for diagnosis and prescription, with harmless personal communication method.
This situation requires all physical and physiologic data monitored from the human body for the synthetic data fusion and the central preprocess with high efficiency of energy utilization. Another significant requirement is guaranteeing the minimized latency for emergency data transmission. It is clear that the emergency data has to be urgently reported as soon as possible for immediate rescue whenever a node senses dangerous signal of body condition.
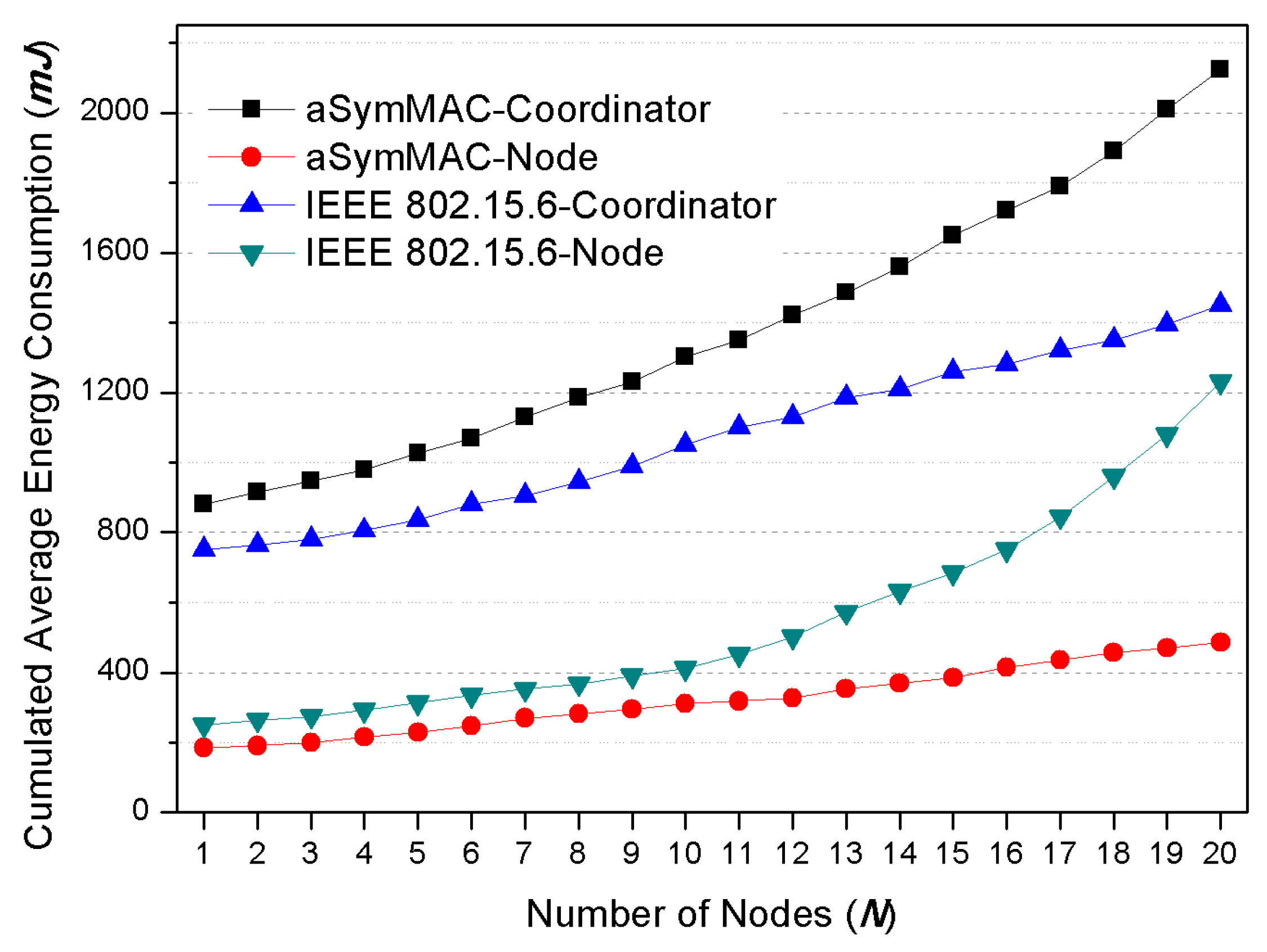
Meanwhile, communication devices in WBAN are generally composed of nodes sensing the body signal and a coordinator analyzing the sensed body signal. Another significant role of the coordinator is harmonizing multiple nodes against collisions, interferences, and unnecessary energy consumptions. The main difference on the specific environment of WBAN is energy resource. While the nodes contacting the body have extremely limited battery capacity due to their light-weighted and micro-sized feature, a coordinator (e.g., mobile phone) has relatively sufficient energy resource because it has abundant hardware resources and rechargeable battery. Hence, the main focus for designing WBAN should consider the energy balance between nodes and coordinator.
WBAN technology has been investigated for near distance (3 m–10 m) communication within or around the body with conditional radio transmission power which must be ergonomically harmless to human health. Moreover, it is clear that the Medium Access Control (MAC) layer is the most crucial layer in terms of energy efficiency because it handles idle listening, retransmission, carrier sensing, and control of the transmission power. Consequently, WBAN has to meet these restricted requirements and the MAC protocol can become a key technique for addressing these emerging issues.
Furthermore, it is possible to analyze the general conditions of the WBAN environment by focusing on the MAC layer. First, we can find that most of the transmissions might be incurred in uplink direction, that is, from nodes to coordinator. Second, a coordinator should support the registration for newly participating node at any time. Third, all data can be classified into periodic report data and emergency data to allow the MAC protocol to provide different Quality of Service (QoS). Fourth, when the MAC protocol considers energy efficiency, it has to adaptively and asymmetrically control the energy balance between nodes and coordinator.
Many WBAN MAC protocols have long been designed and proposed. However, they have not considered the above issues, especially in adapting different energy balance between nodes and a coordinator, while also guaranteeing the minimized delivery delay for transmission of emergency data. Hence, this motivates us to design a new MAC protocol, called aSymMAC, to analyze the above four issues with dealing solutions on time registration, allocating downlink transmission only if needed, handling QoS between periodic report data and emergency data, and designing an asymmetric energy-balanced model for efficient energy distribution belonging to WBAN environment.
2. Related Work
Given that WBAN was spotlighted, much research has been conducted to address this limited environment. IEEE 802.15.6 [
2] standard technology, which was published for communications of WBAN environment in 2012, illustrated an energy-efficient scheme on both Physical (PHY) and MAC layers. This standard technology allowed only the star-topology; therefore, all nodes deployed on the human body should be supervised by a coordinator named as hub, and the scheme on the MAC layer of the standard employed combined approach between slot-assigned and random-accessed methods. The superframe is classified into several time periods and a beacon frame determines the length of each frame duration. In this protocol, all nodes can transmit their reserved data through the slot-assigned period without any contention, denoted as Type-I/II Access Phase. Furthermore, this technology employed Exclusive Access Phase (EAP) and Random Access Phase (RAP) for non-reserved data transmissions. Nodes can use these periods to transmit data when they have emergency data or remaining data in only EAP and RAP with the approach of Carrier Sense Multiple Access/Collision Avoidance (CSMA/CA) or Slotted-Aloha. The main challenge of IEEE 802.15.6 compared to other standard technologies (e.g., 802.15.4 [
3]) is the consideration for emergency data transmissions. However, non-reserved emergency data transmission is allowed in only EAP and RAP, so this can be limited point of this protocol.
Besides IEEE 802.15.6, there are many types of research for enhancing and developing the communication method, and H-MAC [
4] was a representative novelty mechanism that employs Time-Division Multiple Access (TDMA) approaches for body sensor networks. The general TDMA-based MAC protocols should require base time tick for synchronization such as beacon. However, H-MAC did simply address this problem by using the heartbeat vibration measured from the physiological signal with some sensors as a synchronization tick for TDMA. Hence, all nodes could transmit data without any contention under the assumption of that all nodes already had the sequence for slot assigned ownership. Nevertheless, they did not receive any beacon frame from the coordinator.
Some research [
5,
6] had been proposed to facilitate WBAN use-cases with developing previous IEEE 802.15.4 standard which was widely used for wireless sensor networks. Dynamic Time-Division Multiple Access (DTDMA) [
7] designed a reservation-based dynamic TDMA MAC protocol for evolving energy efficiency. The overall superframe of this protocol was composed of the beacon, Contention Free Period (CFP), Contention Access Period (CAP), and an inactive period. But the frame sequence of DTDMA structure was contrary to IEEE 802.15.4. This protocol prioritized CFP to minimize the latency for emergency data transmissions, and then assigned CAP for periodic or remaining data transmissions. The rest of the technical parts including the beacon interval and the length of the inactive period complied with IEEE 802.15.4 protocol.
Another representative scheme of the 802.15.4-based protocol is BodyMAC [
8]. In this protocol, device roles were classified into coordinator and implant, and these would be matched to the hub and node in IEEE 802.15.6. This protocol had cut off the inactive period from IEEE 802.15.4 and newly assigned downlink subframe instead of CFP in the superframe. All implants are guaranteed to be assigned to respective downlink slots to conserve energy from idle. Furthermore, this protocol allowed that some implants do not receive a beacon from the coordinator. The coordinator will perform wake-up signal transmission process to activate a corresponding implant if it had data to be sent. After the sleeping implant was activated with this process, it synchronizes to the wake-up signal and receives data from the coordinator after finding the next beacon frame.
More recent research for WBAN has been also conducted with the same goal. Moulik et al. [
5] designed a priority-based MAC frame depending on the energy efficiency of the healthcare system. This research employed Fuzzy interference system to accomplish an optimization method for individual sensor nodes which can have independent environments, such as radio status, data length, or transmission interval derived from divergent sensor types. The main contribution of this work is to consider the different characteristics from individual node to find the optimization of ideal energy efficiency.
In addition, Zhou et al. [
6] developed an intelligent management method for WBAN with game theory. The authors endeavored to find an appropriate way in MAC layer between contention access approach and contention free approach. In this work, a network has dynamic strategies considering the application requirements and radio channel status so that the proposed scheme supports flexible energy resource allocation. This research also has an optimized method for energy efficiency to satisfy the requirements from various networks. Other researches tried to consider WBAN routing environment [
9] and to design low power MAC [
10].
3. Protocol Framework
Recently, many types of research related to WBAN has been designed to handle the energy efficiency and latency under the human body network environment and they have made many contributions. However, some points to satisfy the significant requirements of WBAN remain as challenging issues and these could be classified into two phenomena below.
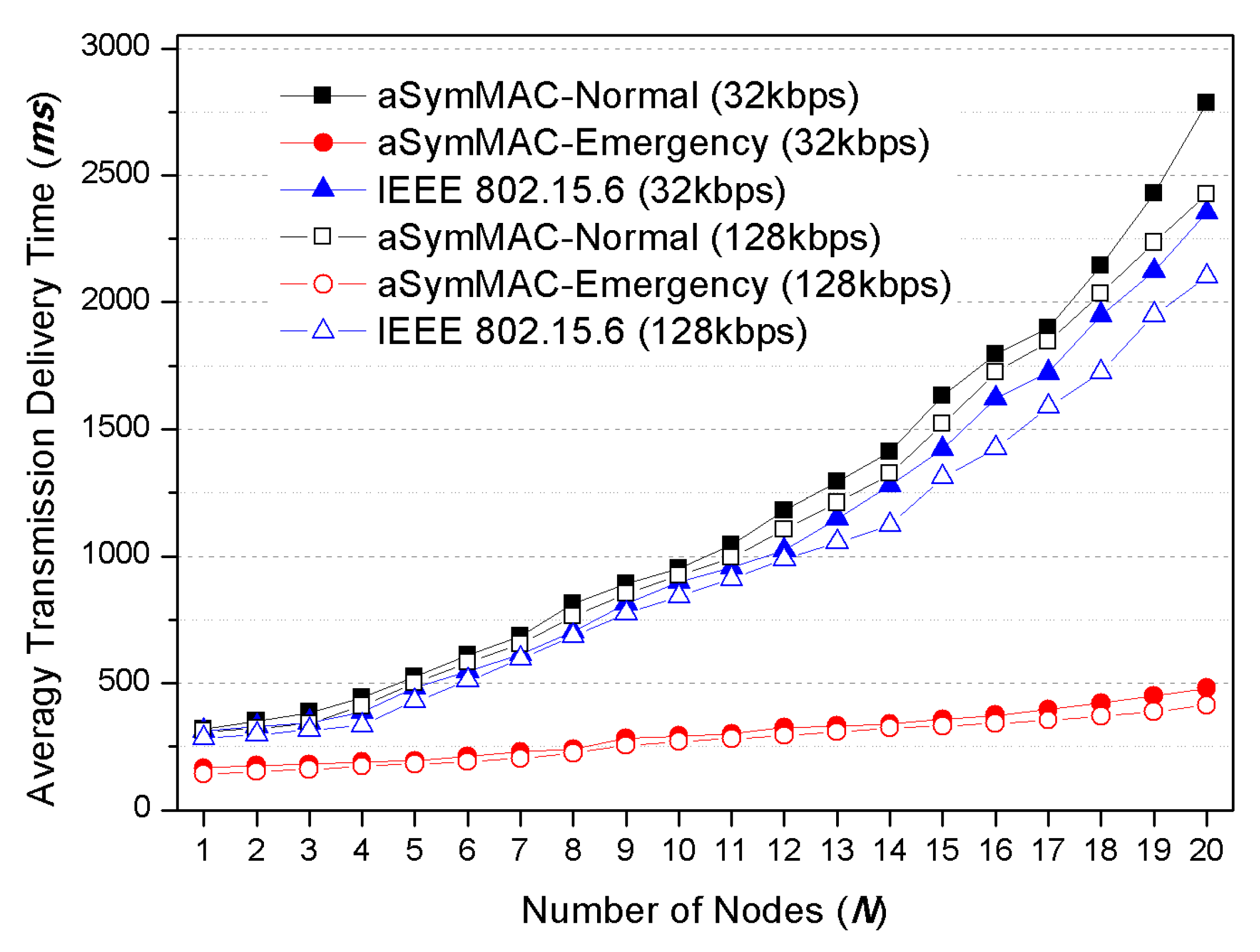
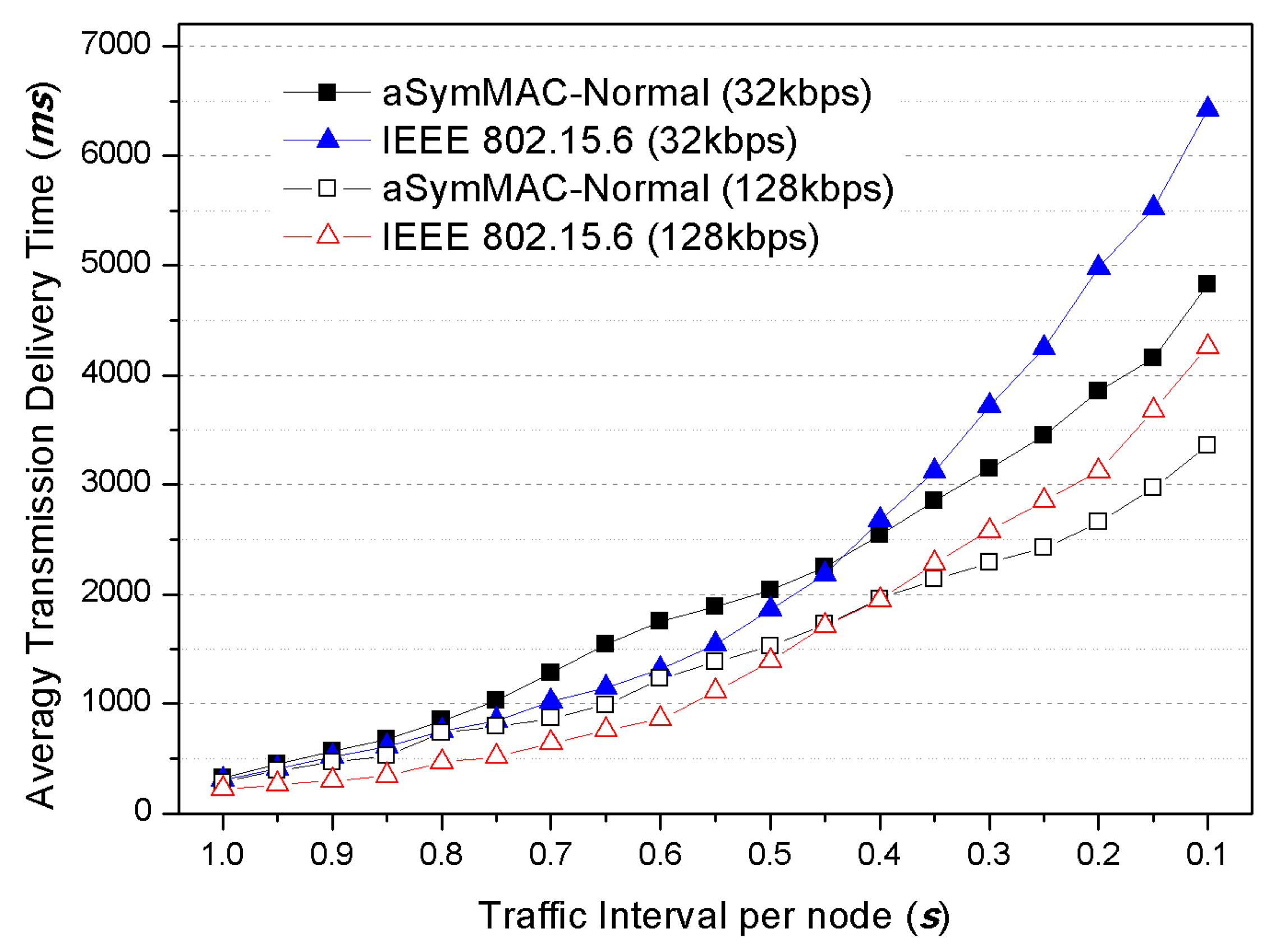
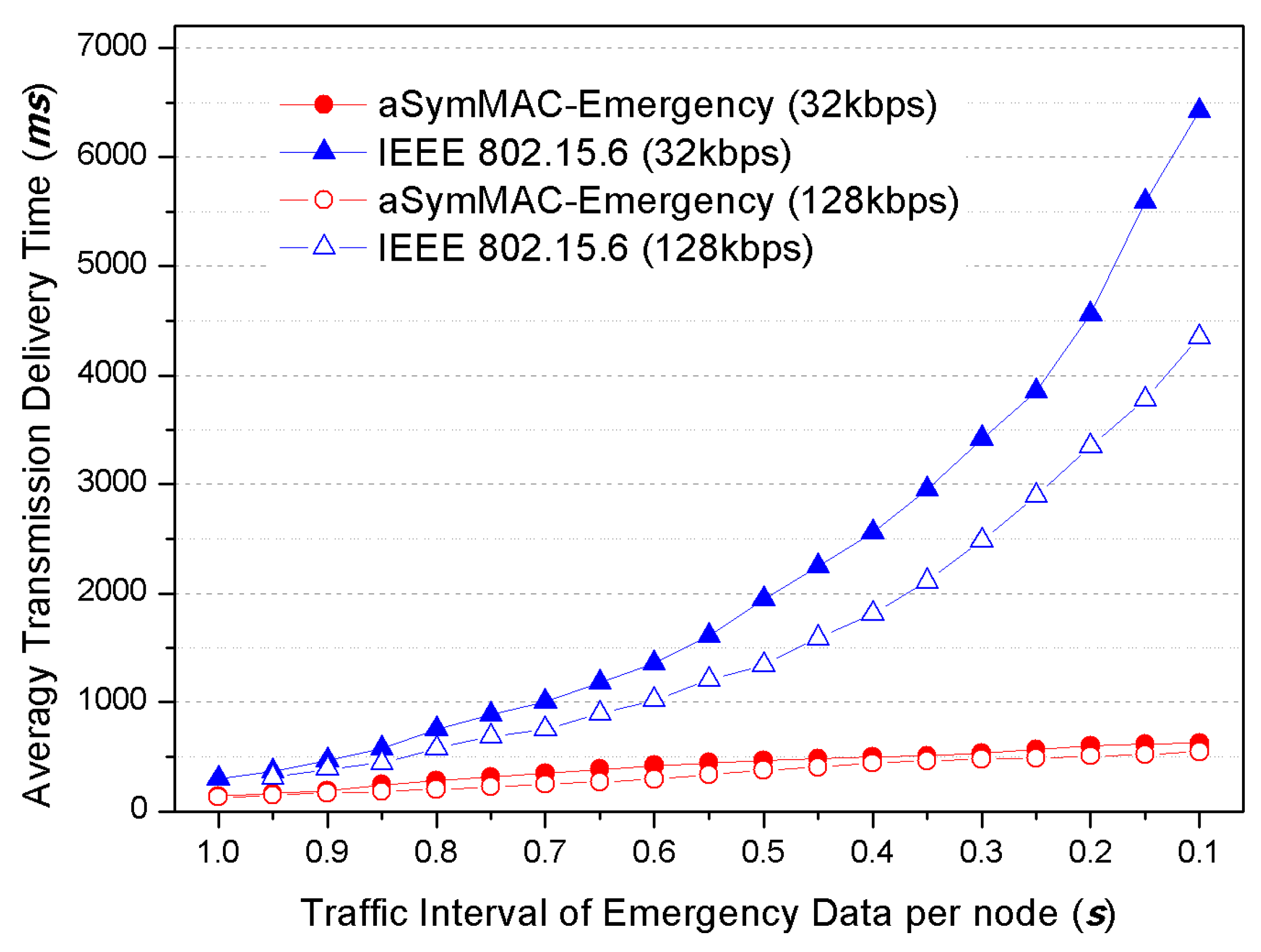
The first point is the immediate transmission for emergency data. Most research, except for the IEEE 802.15.6 standard, focused on the overall energy efficiency and overall latency, but could not make an effort for emergency data transmission because they just allocate separate time slots for this purpose. Moreover, it is not clear that the standard technology of IEEE 802.15.6 efficiently accomplished this issue under EAP and RAP; it just employed the Slotted Aloha and CSMA approach without any prioritization for emergency data. Specifically, all data were just fairly transmitted during these periods regardless of whether it is an emergency or not. The emergency data can be incurred at any time regardless of time slot structure. Therefore, the superframe-based WBAN MAC protocol has to support an immediate transmission method for emergency data within the overall time domain.
The second fundamental requirement for WBAN is that the energy balance between nodes and coordinator must be differently considered. Most smart devices (e.g., phone, watch, and wristband) can generally play a role of coordinator in WBAN environment because they have more sufficient energy resource than the nodes, and their battery might be rechargeable. WBAN MAC protocols have to consider this issue by asymmetrically allocating the energy consumption point on the both roles.
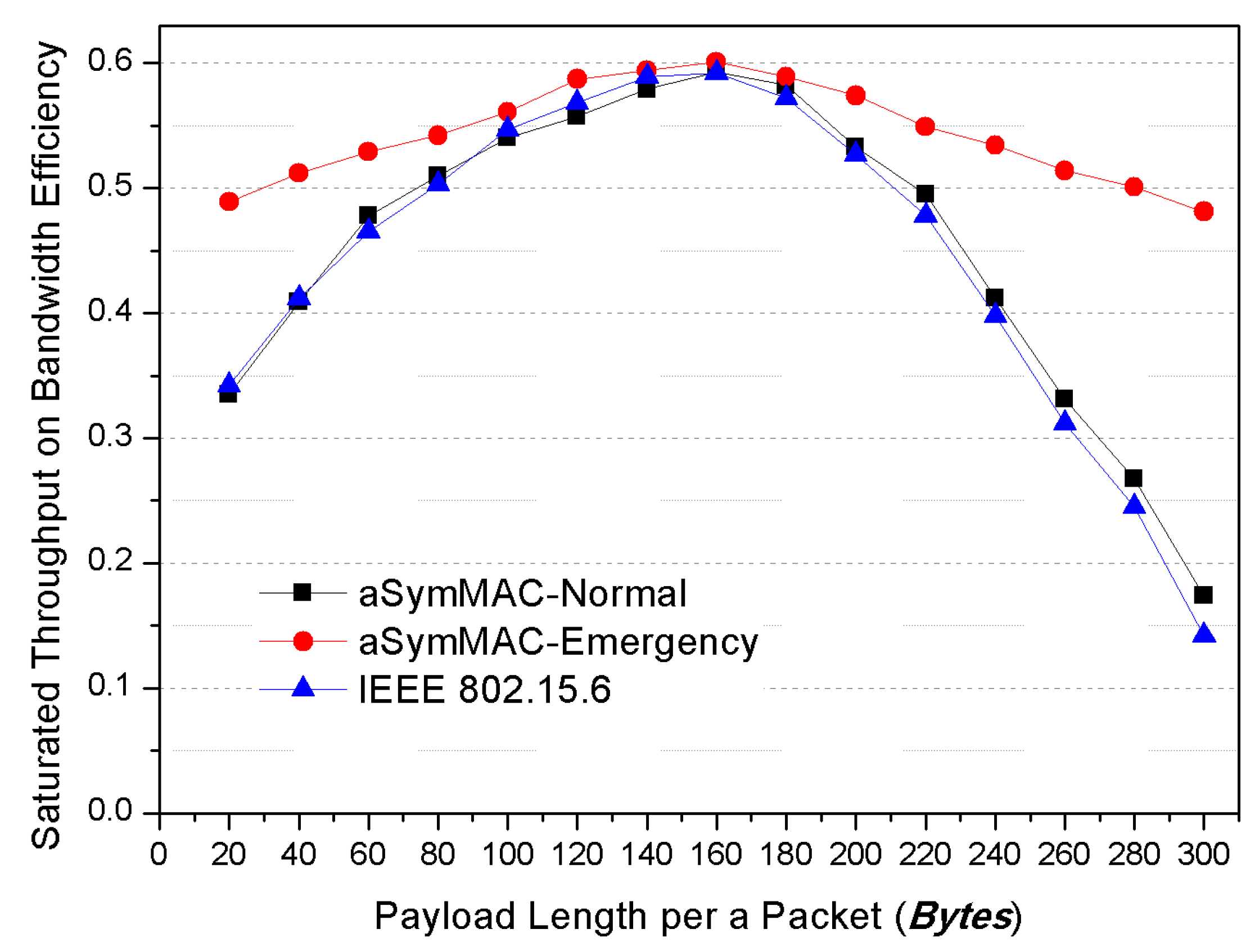
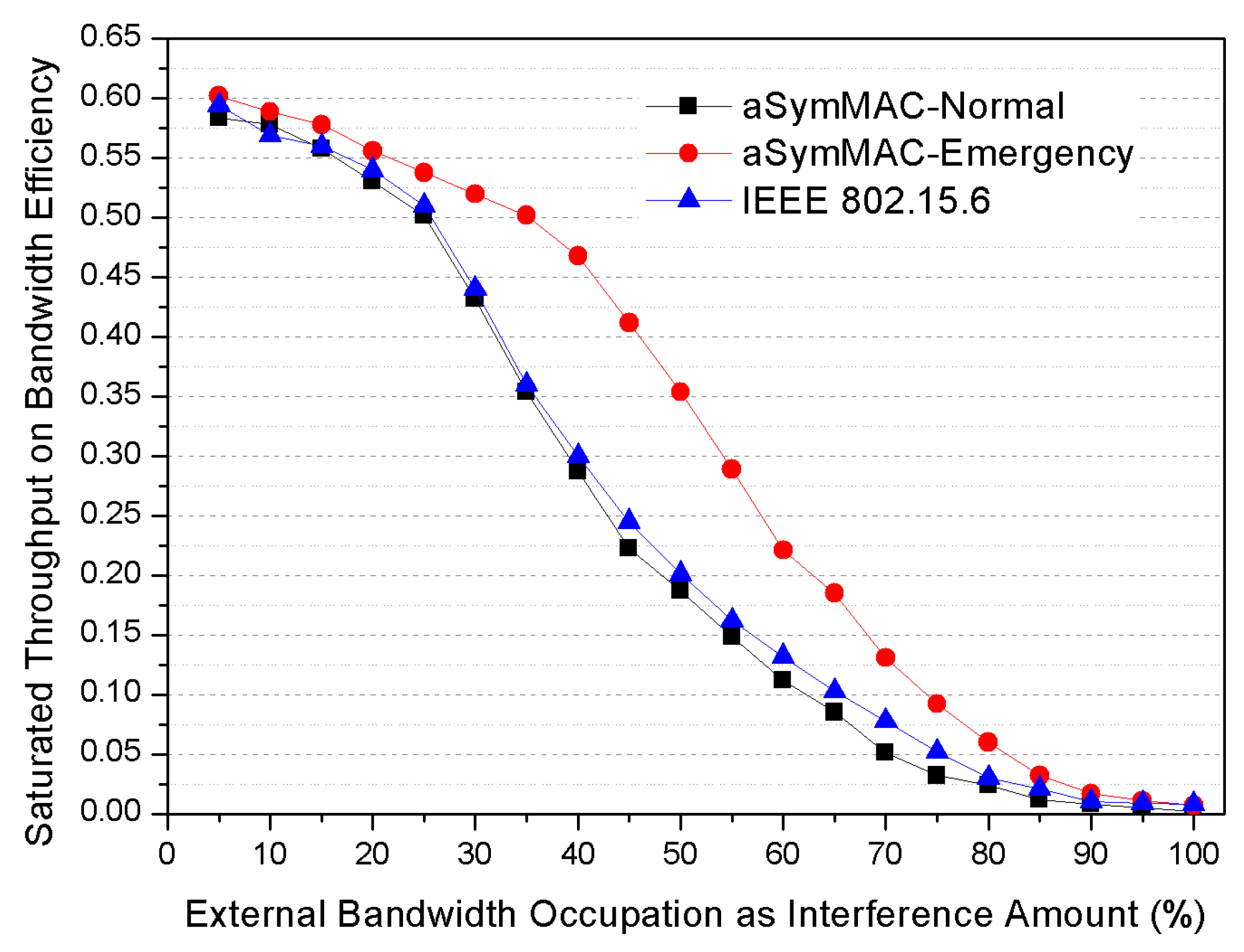
As a result, the proposed scheme on this paper was focused on the above two significant issues to satisfy the essential requirement of WBAN environment by handling the emergency data transmissions and designing asymmetric energy balance model between nodes and coordinator.
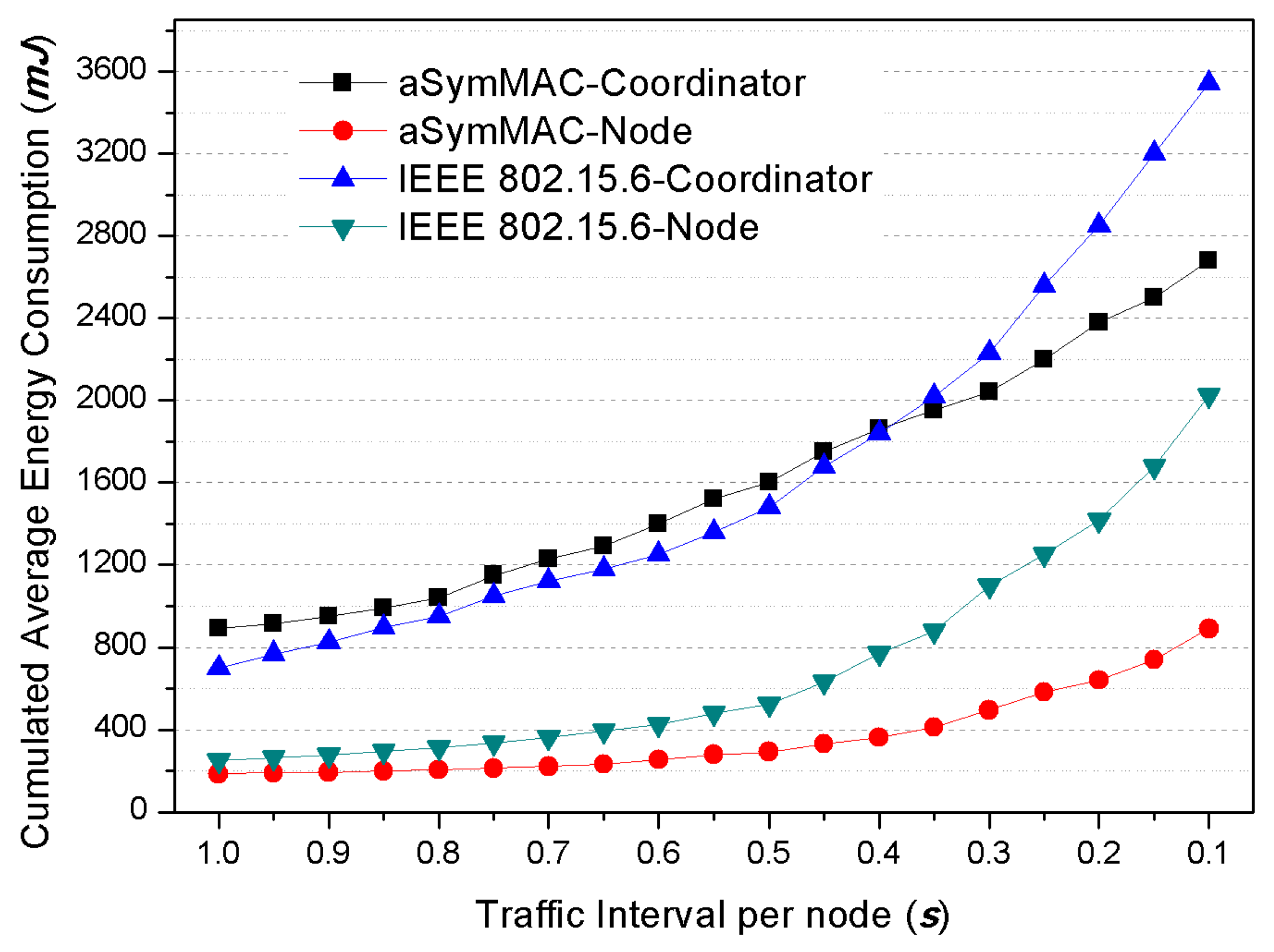
IEEE 802.15.6 standard technology employed CSMA-based mechanism when transmitting emergency data from nodes. However, CSMA-based mechanism absolutely depended on Clear Channel Assessment (CCA) which was provided in a radio transceiver, but the reliability of CCA effect cannot be guaranteed because Medical Implant Communication Service (MICS) band, which is a widely used radio band for WBAN, does not permit over the transmission power of −85 dBm. Moreover, CSMA-based protocols have some energy-waste problems (e.g., idle listening, overhearing, protocol overhead, and preamble sampling). With these reasons, we found that CSMA-based protocol is not appropriate for WBAN and decided to hybridize both CSMA and TDMA for WBAN MAC protocol.
Before describing the proposed protocol in detail, we named the coordinator as Personal Coordinator (PC) and assumed that the communications of node-to-node were not presented because general WBAN nodes report their sensed data only to a coordinator. Note that this paper is mainly aiming to design of both asymmetrical energy-balanced model and QoS for emergency data transmission. Based on the prioritized scheme, the proposed protocol concurrently supports both transmission types of normal and emergency without any operation mode change, contrarily to IEEE 802.15.6.
3.1. Basic Framework
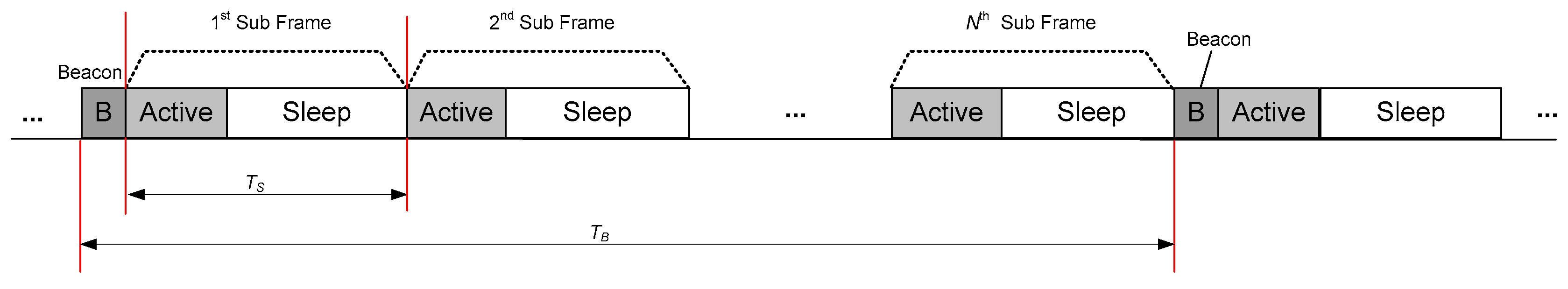
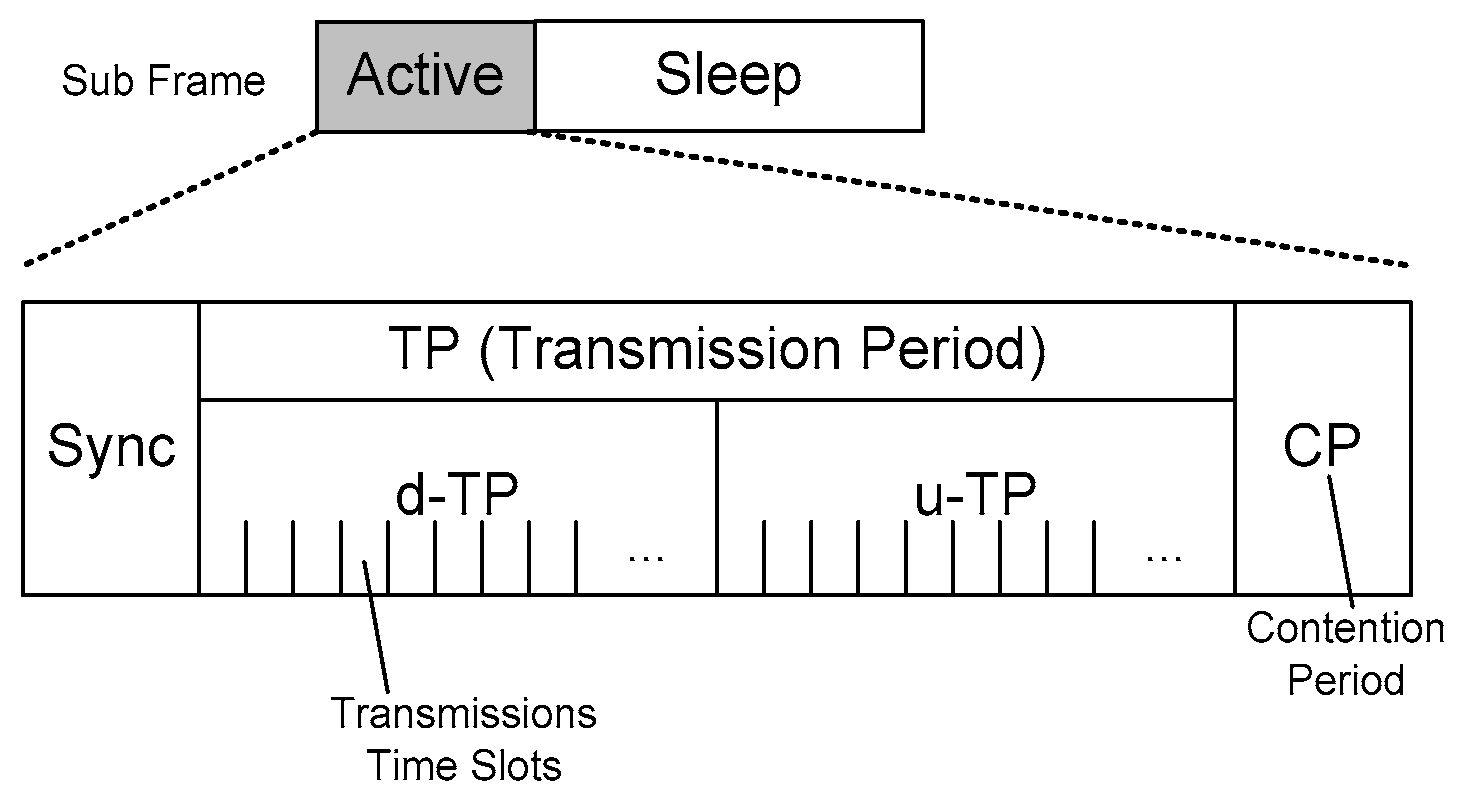
Figure 1 illustrates the overall structure of the MAC protocol which we proposed in this paper. The superframe is composed of a Beacon frame and multiple subframes, and each subframe is combined with an Active frame and a Sleep frame. Furthermore, each Active frame at every subframe is composed of several periods; Sync, Transmission Period (TP), and Contention Period (CP) as shown in
Figure 2. TP in the Active frame is composed of both d-TP and u-TP; d-TP denoted for downlink directional transmission period from a PC to an individual node, and u-TP denoted for uplink transmission.
The beacon packet is generated from PC and it is disseminated to all nodes in Beacon frame with relatively long term interval denoted as
TB. As discussed in the previous paragraph, one beacon frame is followed by multiple frames in each
TB as shown in
Figure 1. Moreover,
TS, which denotes the time duration of each subframe, has relatively short term value compared with
TB. Each subframe is composed of an Active frame and a Sleep frame in which the RF transceiver should keep the wake-up condition and the sleep condition. Hence,
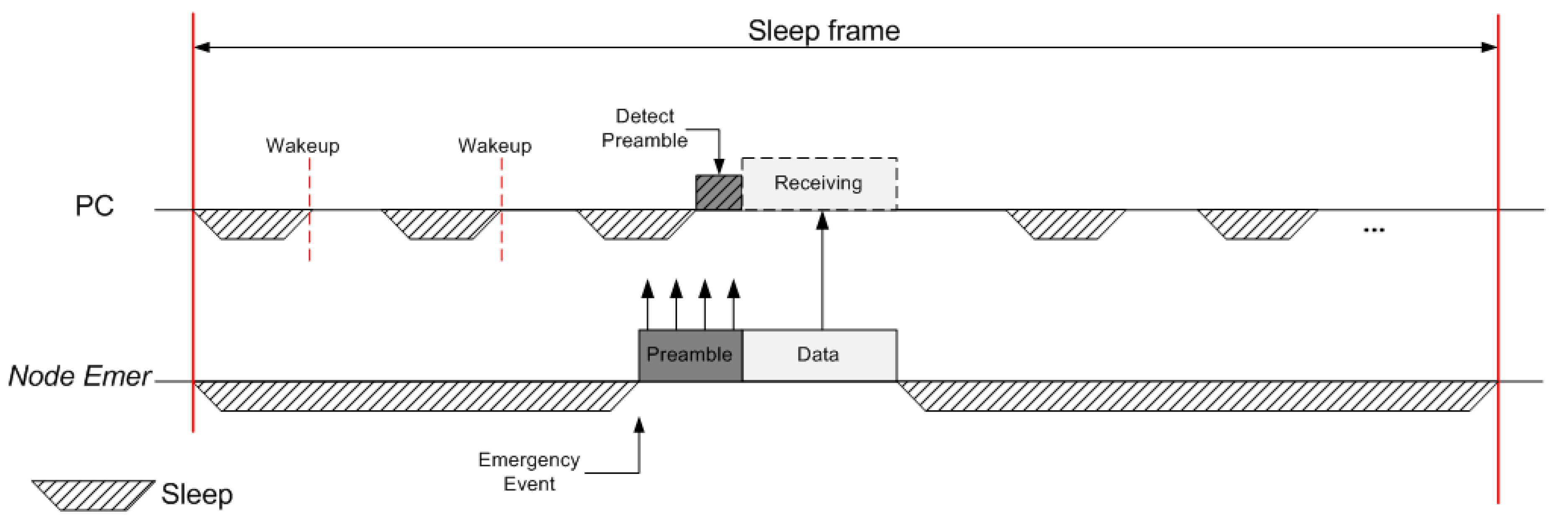
TB could be considered as the duty cycle of the transceiver. Moreover, in Sleep frame, the PC and all nodes enter to the condition of deep sleep or standby status for energy conservation. Hence, all transmissions are basically absent during Sleep frame, but we allowed for an exception in the case of emergency data transmission.
To synchronize every frame between the coordinator and each correspondent node, the PC should periodically transmit the beacon packet containing both TB and TS. Every node belonging to the same coordinator can be aware of the start time to be awake depending on TB and reception time of the packet, and each node can also estimate the reception time of the next beacon packet from the same PC. Consequently, if a node does not have any packet to send, it can omit all forwarding frames and can just sleep until the next Beacon frame.
On the other hand, Sync period is for disseminating Sync packet to awaken nodes from PC, which contains each time offset values for d-TP, u-TP, CP, and Sleep frame. The Sync packet is always sent from a PC at every TB, and we design that each subframe can be alternatively applied to each node. Each corresponding node should decide to participate in the current subframe or not. The rest of a subframe is CP, and we adapt the exceptional case of allowing contentions based on CSMA/CA from nodes on this period, in which this period supports the registration of a new node joining in.
Under the given timeframes above, all transmissions except in CP should be critically controlled by the PC. By the way, emergency data transmission must be transmitted without any authentication by PC. IEEE 802.15.6 protocol allows the emergency data transmission by out of coordinator, but it allowed in only EAP and RAP. However, emergency data related to the biomedical signal must be immediately sent regardless of the timeframe condition. For this reason, we also designed a mechanism to minimize the latency of emergency data transmission. In the proposed scheme, the emergency data transmission can be allowed in overall time frames (i.e., d-TP, u-TP, CP. And even Sleep frame) with prioritized channel preemption.
As we described previously, the PC relatively has sufficient energy resource than nodes so that the main goal of the proposed MAC protocol is designing an asymmetrical energy balance model between PC and nodes. Meanwhile, it is fundamentally required that the energy consumption point should be loaded into a PC as possible for conserving the energy of nodes side. The nodes should wake up on the only essentially required moment.
3.2. Transmit Period (TP)
TP is assigned for transmission duration between PC and nodes. Under the characteristics of WBAN, we focused on transmission topology as Piconet cluster which is used in Bluetooth technology. The direct transmission between nodes is not allowed, but can be forwarded via PC. Hence, we considered two-way transmissions of downlink and uplink in TP.
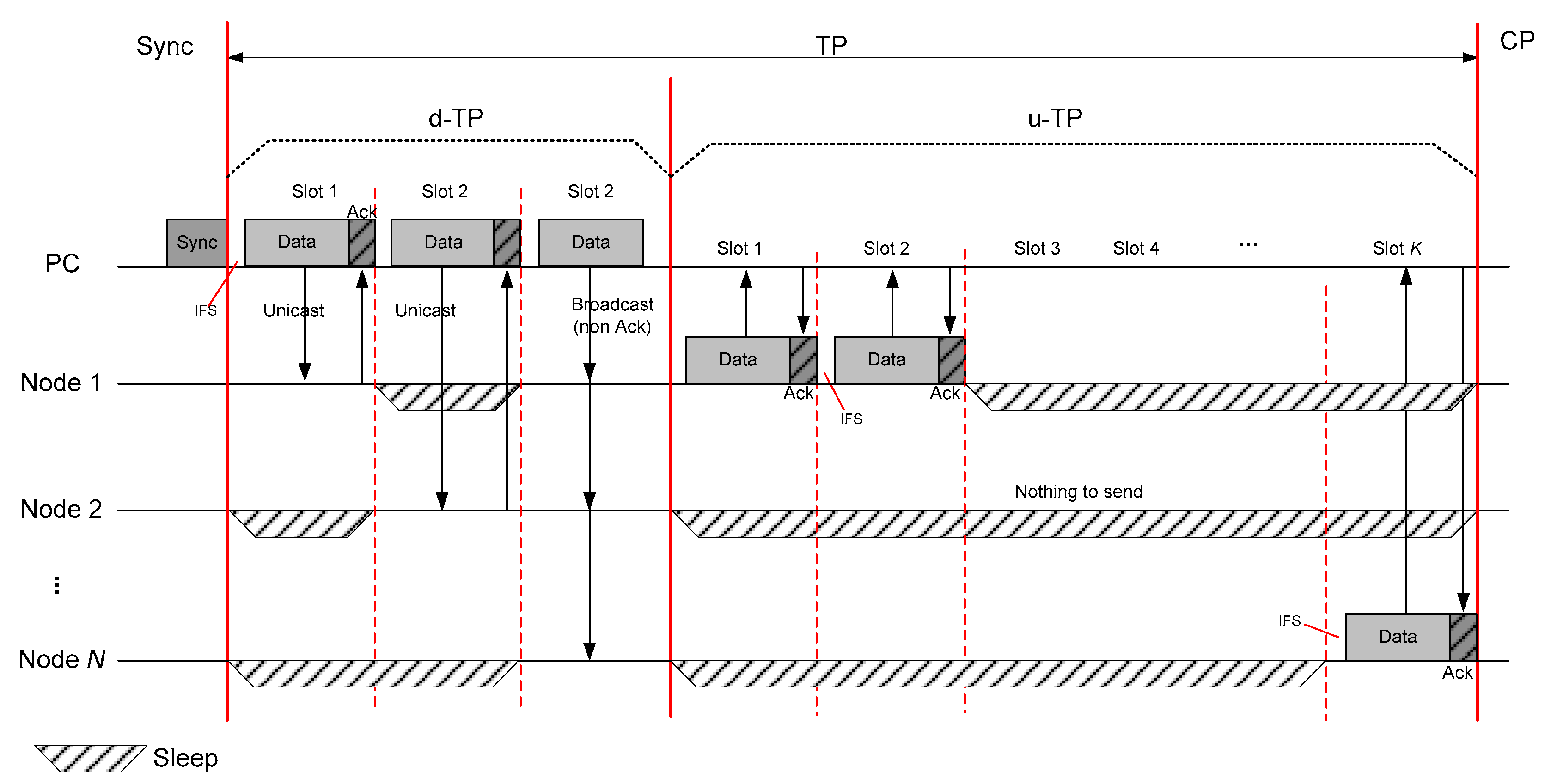
d-TP allows data to be sent from PC; both unicast and broadcast methods. Regardless of unicast or broadcast, the PC can transmit data anywhere, but the nodes cannot be aware of when the PC can send to them. Hence, we divide the d-TP by multiple time slots, and considered both unicast and broadcast. The Sync packet contains time offsets, destination address, and type (unicast or broadcast), depending on each d-TP slot.
After a node receives the Sync packet from the PC, it finds all d-TP slots assigned to broadcast type, and also finds the destination addresses matched to itself if the type is unicast. Based on the Sync packet, each node can be aware of when it has to be awake to receive data from PC and when it can sleep. If a node is selected as a receiver but cannot detect any preamble after Inter Frame Space (IFS), it should process an Early-sleep mechanism [
11]. Note that IFS is existed for guaranteeing the turnaround time of transceiver transaction and for supporting the prioritized emergency data transmission.
For the next step, u-TP is also divided into multiple time slots as shown in
Figure 2, and all slots are fairly assigned for all nodes. In this period, all nodes do not have to keep a wake-up state. The node only wakes up if it has data to send to the PC. After a node finds the schedule of d-TP from the Sync packet reception, it accesses the assigned d-TP slots and transmits data. If a node cannot complete the transmission during the assigned time slots, it can continue to transmit the remaining data during CP using the competition approach. Moreover, the PC always wakes up during overall u-TP for successful reception.
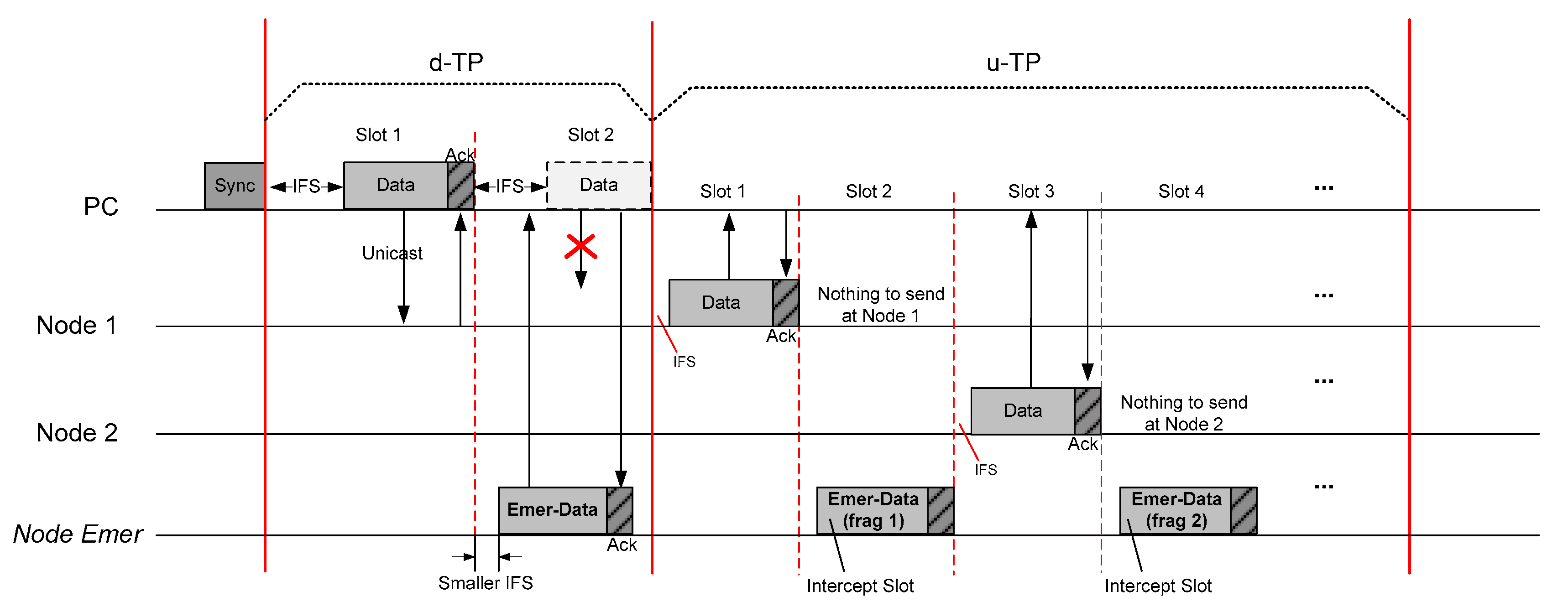
In both d-TP and u-TP, the Ack mechanism should be performed within the same time slot of the corresponding data transmission as shown in
Figure 3. Specifically, one-time slot covers one data packet and one Ack packet. That is, the overall TP can be considered as a contentionless period because any packet does not collide in this period.
The downlink transmission occurs only when the PC will configure or change some parameters of time schedule. u-TP is helpfully used to report periodic medical signals, such as vital sign, ECG, and EEG, meanwhile d-TP is not frequently required. For these characteristics, we employed selective d-TP assignment to allow the Sync packet to include the information of d-TP schedule only when it is required.
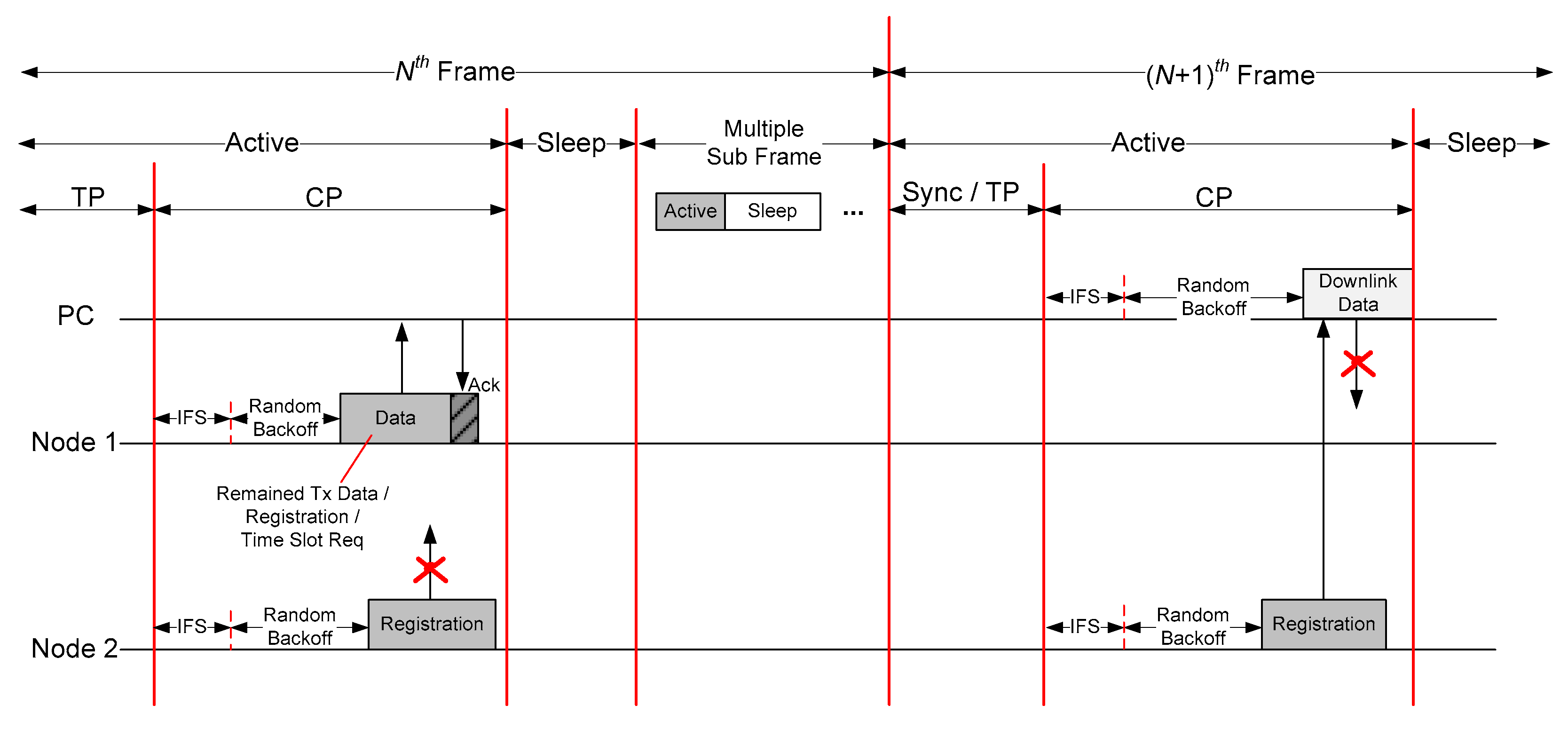
3.3. Contention Period
CP is assigned for transmission of remaining data to be sent to the PC from the node and for transmission of specific control packets such as new node registration or slot request for u-TP. In this period, as shown in
Figure 4, all nodes and PC are performing transmission including emergency data with CSMA/CA mechanism after IFS duration since the start time of CP.
All transmissions in CP can be classified into the remaining data, emergency data, and specific control frames such as registration and u-TP slot request. If a node or some nodes did not complete data transmission during the assigned u-TP, they can additionally continue to transmit it in this period with competition based on CSMA/CA, so this period can be alternatively used with TP. Furthermore, if a node tries to register at the given network or changes its slot, it can also try to request to the PC via this period.
As the mechanism of TP, CP also employs Ack so all types of packet should be followed by Ack. After PC receives a request for registration or slot change, it should apply and broadcast the changed schedule after the next subframe through the Sync packet. On the contrary, PC can deny the request from nodes by notifying Nack to the corresponding node if there is any reason to reject the request (e.g., overheated congestion or overflowed capacity). In this case, the node neglected by PC can try to again at the next Beacon time. Note that all transmissions should be competitively sent based on CSMA/CA regardless of any direction (downlink or uplink), and also note that PC should also participate in the competitive transmission with the nodes in CP.
Basically, CP would be required in a few cases. Hence, it is very low frequency to be incurred. To address this situation, it is recommended to allocate CP whenever multiple frames are passed. As a result, all nodes can participate in the competition of CP when it is detected via Sync packet. If a new node failed to be registered, it should keep going on sleep state before the next CP which can be found by each Sync packet.
3.4. Sleep Frame
Presently, many low-powered MAC protocols have employed the Duty Cycle mechanism to overcome the energy constraints so this paper also employed it. As described in Basic Framework subsection, every subframe is composed of an Active frame and Sleep frame. There is no transmission in Sleep frame except emergency data transmission, so all nodes maintain the sleep state during Overall Sleep frame. However, the PC has to perform the Duty Cycle mechanism by periodically switching both wake-up and sleep status because the proposed MAC protocol adapts emergency data transmission with conservation of energy efficiency at most periods.