Multi-Bit Data Hiding Scheme for Compressing Secret Messages †
Abstract
:1. Introduction
2. Related Work
2.1. Run-Length Encoding
2.2. Exploiting Modification Direction Method
2.3. Generalized Exploiting Modification Direction
2.4. Multi-Bit Generalized Exploiting Modification Direction
3. The Proposed Scheme
3.1. Multi-Bit Data Hiding Scheme for Compressing Secret Messages
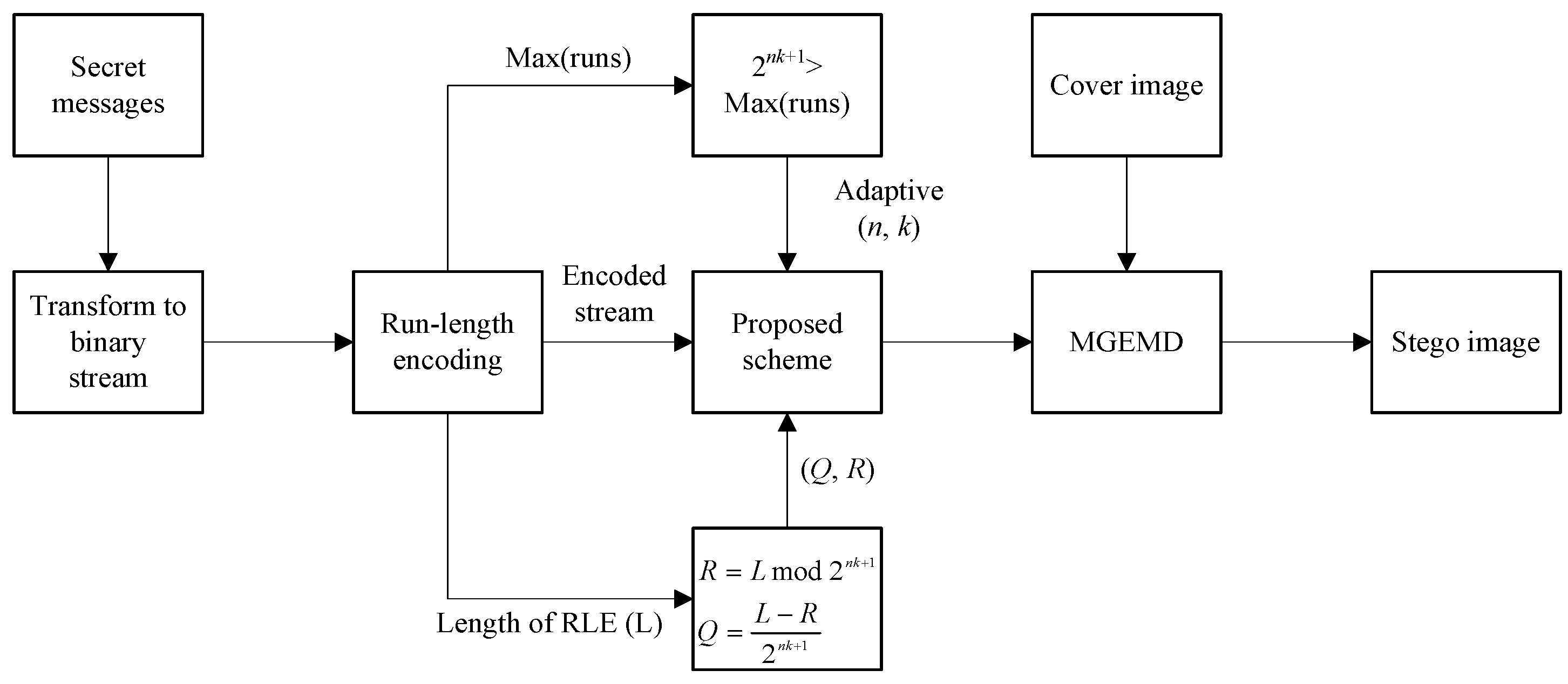
3.2. Secret Image Compression Phase
| Algorithm 1. The multi-bit data hiding scheme for compressing secret messages. |
| Input: A cover image and secret image (S) with gray level image |
| Output: A stego image () |
| Step 1. The gray level secret image is transformed into a binary stream. |
| Step 2. Compressing the binary stream by RLE for the new secret message (), which includes maximum runs, total length information and the embedding secret messages (s). |
| Step 3. Check if the new secret is zero or one in the high-order bit. This information tells us the beginning bit is zero or one by using RLE. Then, the first pixel’s LSB of the cover image will be changed. Simultaneously, we also count the zeros and ones to record the total length information. |
| Step 4. Find parameters (n and k), such as > Max(runs) and . Quotient (Q) and remainder (R) are calculated from total length (L) information using Equation (5).
|
| Step 5. For the second pixel to the last, decision variables n and k divide the pixels into n adjacent pixels as a non-overlapping group. |
| Step 6. Compute the value and the difference D, i.e., . |
| Step 7. If , then cover pixels do not change; else if , then and . else if , then , and for . else if , then , and for . |
| Step 8. Repeat Step 6 to Step 7 until all secret messages are hidden. |
| Example 1: Let and . Given the cover image’s pixels (), secret messages . The secret messages are compressed with RLE and hidden in the cover pixels. Finally, we get the stego pixels = () from Algorithm 1 by the following steps. |
| Step 1. Convert the secret message into the binary stream . |
| Step 2. Use RLE to compress the secret stream, . The new secret = from the s value sequence and the RLE begins at one. |
| Step 3. The least significant bit of the first pixel is equal to one, meaning it is not modified, i.e., the first pixel is still 155. |
| Step 4. Compute the value and . |
| Step 5. Since and , we can compute the stego pixels by using the following equation. For , compute and ; For , compute and ; For , compute . |
| The stego pixels are . |
3.3. Data Embedding
3.3.1. Speeding up the Modified Method
| Item | Formula | Example |
|---|---|---|
| (10 + 1, 19 − 2, 5 − 5, 9 + 0) |
| Item | Formula | Example |
|---|---|---|
| 832 | ||
| (10 + 0, 19 − 5, 5 + 4, 9 + 1) |
3.3.2. The Solution for the Overflow/Underflow Problems
3.4. Data Extracting Phase
| Algorithm 2: Data extracting. |
|
4. Experimental Results




| Method | Item | F-16 | Baboon | Boat | Elaine | Gold Hill | Lena | Pepper | Tiffany |
|---|---|---|---|---|---|---|---|---|---|
| Proposed Scheme | PSNR (dB) | 46.93 | 44.62 | 44.84 | 44.68 | 44.56 | 44.53 | 44.57 | 44.52 |
| non-modified (pixel) | 238,872 | 221,987 | 222,598 | 222,046 | 221,895 | 222,121 | 222,054 | 221,880 | |
| MGEMD Scheme | PSNR (dB) | 42.21 | 42.20 | 42.30 | 42.22 | 42.20 | 42.15 | 42.14 | 42.08 |
| non-modified (pixel) | 192,284 | 191,912 | 192,564 | 191,993 | 192,151 | 192,253 | 191,920 | 191,885 |
| Binary Image | Item | Method | F-16 | Baboon | Boat | Elaine | Gold Hill | Lena | Pepper | Tiffany |
|---|---|---|---|---|---|---|---|---|---|---|
| F-16 | PSNR (dB) | Proposed | 51.55 | 51.59 | 51.59 | 51.61 | 51.42 | 51.55 | 51.66 | 51.29 |
| MGEMD | 41.79 | 41.80 | 41.96 | 41.83 | 41.84 | 41.76 | 41.77 | 41.69 | ||
| non-modified pixel | Proposed | 254,072 | 254,067 | 254,093 | 254,079 | 254,023 | 254,082 | 254,093 | 253,976 | |
| MGEMD | 185,830 | 185,397 | 186,226 | 185,592 | 185,790 | 185,795 | 185,414 | 185,328 | ||
| Baboon | PSNR (dB) | Proposed | 44.59 | 44.58 | 44.79 | 44.64 | 44.47 | 44.53 | 44.53 | 44.53 |
| MGEMD | 41.79 | 41.80 | 41.95 | 41.82 | 41.83 | 41.77 | 41.76 | 41.76 | ||
| non-modified pixel | Proposed | 221,746 | 221,671 | 221,948 | 221,743 | 221,569 | 221,799 | 221,548 | 221,548 | |
| MGEMD | 185,796 | 185,485 | 186,242 | 185,542 | 185,774 | 185,735 | 185,456 | 185,456 | ||
| Boat | PSNR (dB) | Proposed | 50.65 | 50.56 | 50.58 | 50.65 | 50.14 | 50.48 | 50.59 | 50.33 |
| MGEMD | 41.79 | 41.81 | 41.97 | 41.82 | 41.82 | 41.76 | 41.77 | 41.69 | ||
| non-modified pixel | Proposed | 251,898 | 251,957 | 251,933 | 251,995 | 251,808 | 251,920 | 251,888 | 251,747 | |
| MGEMD | 185,811 | 185,418 | 186,225 | 185,512 | 185,650 | 185,834 | 185,503 | 185,366 | ||
| Elaine | PSNR (dB) | Proposed | 48.13 | 48.20 | 48.23 | 48.25 | 48.02 | 48.08 | 48.23 | 47.97 |
| MGEMD | 41.80 | 41.80 | 41.96 | 41.83 | 41.82 | 41.76 | 41.76 | 41.70 | ||
| non-modified pixel | Proposed | 244,532 | 244,614 | 244,661 | 244,653 | 244,657 | 244,657 | 244,548 | 244,340 | |
| MGEMD | 185,791 | 185,309 | 186,177 | 185,497 | 185,667 | 185,831 | 185,396 | 185,367 | ||
| Gold Hill | PSNR (dB) | Proposed | 48.51 | 48.59 | 48.60 | 48.59 | 48.37 | 48.51 | 48.61 | 48.36 |
| MGEMD | 41.79 | 41.80 | 41.93 | 41.83 | 41.83 | 41.79 | 41.76 | 41.70 | ||
| non-modified pixel | Proposed | 246,027 | 246,120 | 246,198 | 246,057 | 246,062 | 246,159 | 246,088 | 245,940 | |
| MGEMD | 185,802 | 185,420 | 186,190 | 185,555 | 185,742 | 185,829 | 185,333 | 185,409 | ||
| Lena | PSNR (dB) | Proposed | 51.64 | 51.65 | 51.65 | 51.66 | 51.34 | 51.51 | 51.61 | 51.50 |
| MGEMD | 41.79 | 41.80 | 41.93 | 41.83 | 41.83 | 41.78 | 41.76 | 41.70 | ||
| non-modified pixel | Proposed | 254,132 | 254,123 | 254,126 | 254,127 | 254,072 | 254,110 | 254,107 | 254,041 | |
| MGEMD | 185,775 | 185,401 | 186,198 | 185,520 | 185,773 | 185,795 | 185,311 | 185,388 | ||
| Pepper | PSNR (dB) | Proposed | 52.66 | 52.76 | 52.60 | 52.69 | 52.42 | 52.65 | 52.64 | 52.47 |
| MGEMD | 41.80 | 41.81 | 41.95 | 41.82 | 41.82 | 41.76 | 41.76 | 41.70 | ||
| non-modified pixel | Proposed | 255,739 | 255,816 | 255,810 | 255,764 | 255,790 | 255,796 | 255,801 | 255,748 | |
| MGEMD | 185,743 | 185,409 | 186,155 | 185,516 | 185,764 | 185,756 | 185,400 | 185,367 | ||
| Tiffany | PSNR (dB) | Proposed | 49.11 | 49.13 | 49.14 | 49.16 | 48.91 | 49.04 | 49.11 | 48.90 |
| MGEMD | 41.80 | 41.80 | 41.93 | 41.82 | 41.84 | 41.76 | 41.75 | 41.71 | ||
| non-modified pixel | Proposed | 247,911 | 247,934 | 247,975 | 247,967 | 247,840 | 247,955 | 247,911 | 247,732 | |
| MGEMD | 185,824 | 185,433 | 186,138 | 185,567 | 185,819 | 185,760 | 185,264 | 185,386 |
| Payload | Proposed Scheme | BRL-Scheme [15] | LSW [18] Scheme | ||
|---|---|---|---|---|---|
| 100,000 | 60.12 | 51.13 | 48.46 | 46.32 | 49.85 |
| 200,000 | 56.85 | 48.12 | 45.46 | 43.32 | 48.85 |
| 400,000 | 53.69 | 45.11 | 42.45 | 40.31 | 43.85 |
4.1. Maximum Embedding Capacity
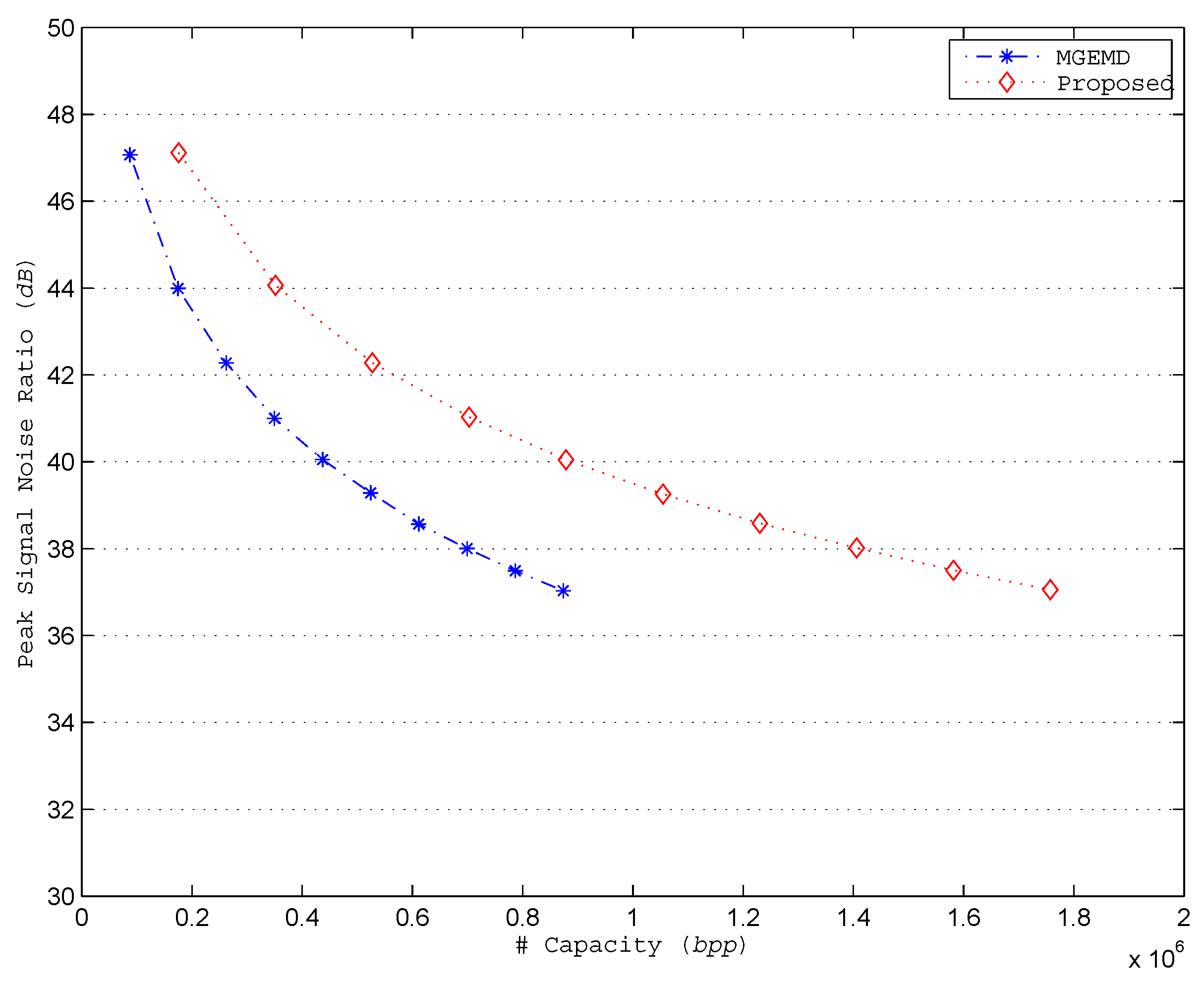
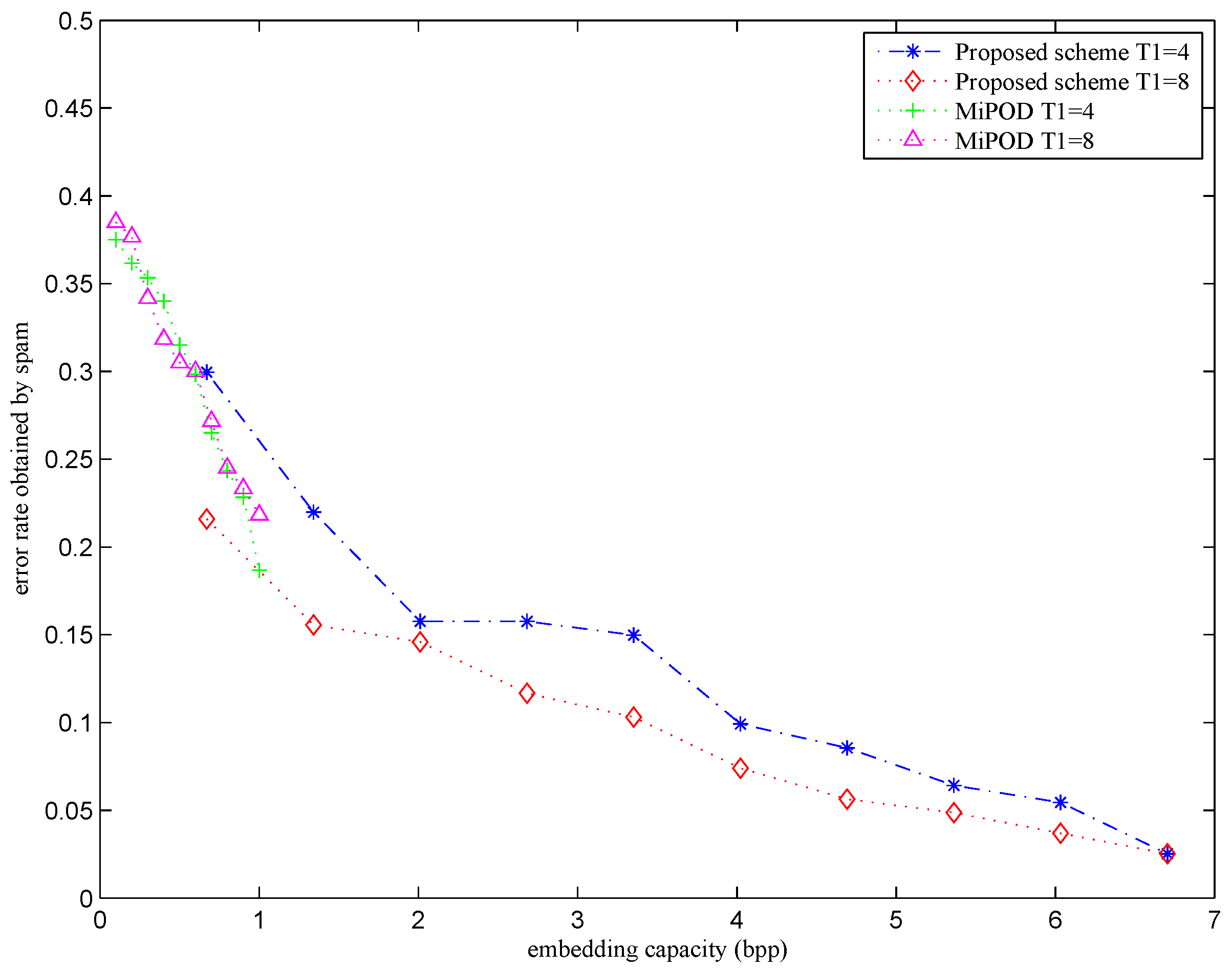
4.2. Image Steganalysis
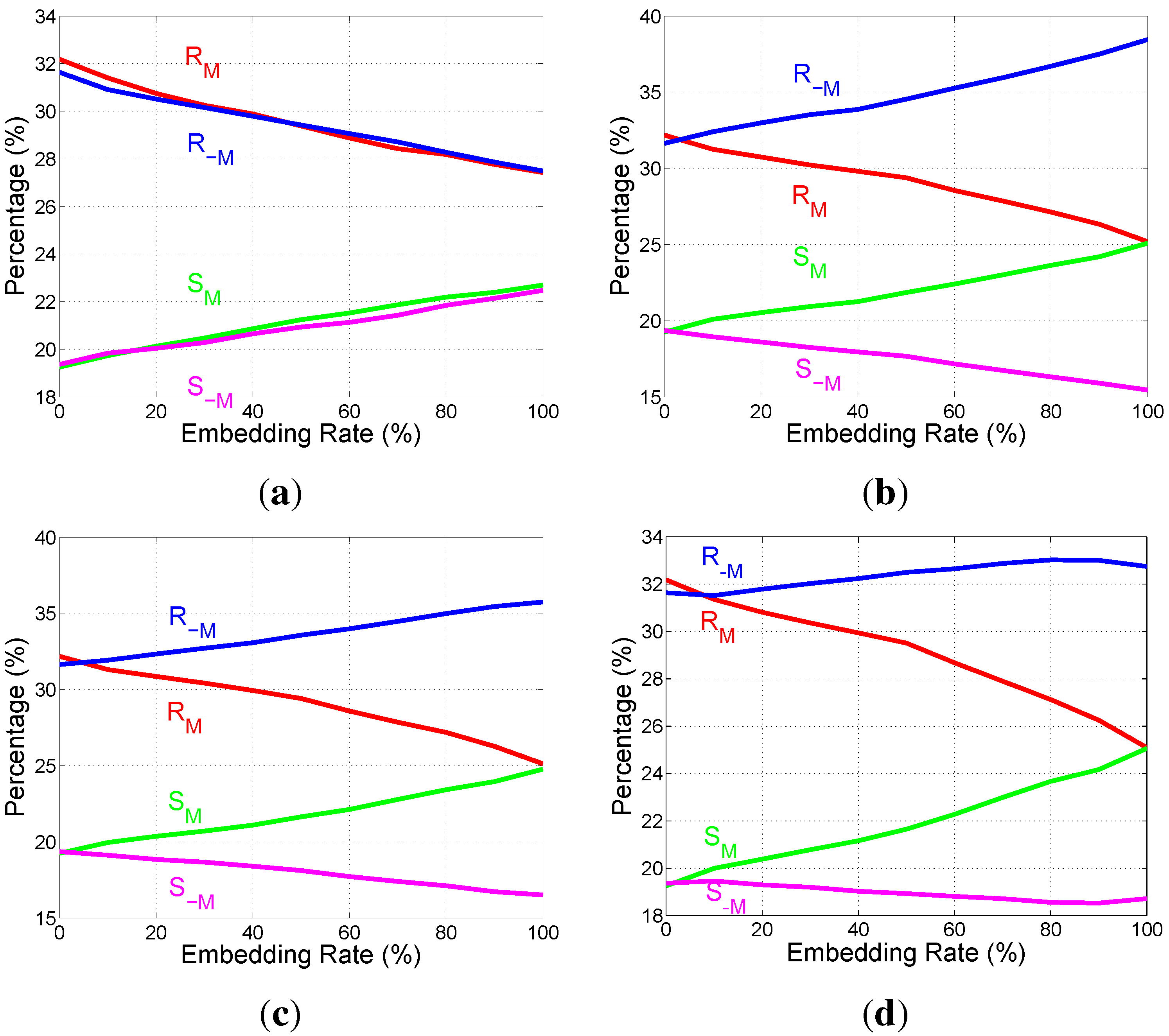
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Petitcolas, F.A.P.; Anderson, R.J.; Kuhn, M.G. Information Hiding – A Survey. Proc. IEEE 1999, 87, 1062–1078. [Google Scholar] [CrossRef]
- Cox, I.J.; Miller, M.L.; Bloom, J.A.; Fridrich, J.; Kalker, T. Digital Watermarking and Steganography, 2nd ed.; Morgan Kaufmann: San Francisco, CA, USA, 2008. [Google Scholar]
- Swanson, M.D.; Kobayashi, M.; Tewfik, A.H. Multimedia Data-Embedding and Watermarking Technologies. Proc. IEEE 1998, 86, 1064–1087. [Google Scholar] [CrossRef]
- Ker, A. Improved Detection of LSB Steganography in Grayscale Images. Inf. Hiding Lect. Notes Comput. Sci. 2004, 3200, 97–115. [Google Scholar]
- Zhang, X.; Wang, S. Efficient Stegano graphic Embedding by Exploiting Modification Direction. IEEE Comm. Lett. 2006, 10, 1–3. [Google Scholar] [CrossRef]
- Sayood, K. Introduction to Data Compression, 4th ed.; Morgan Kaufmann: San Francisco, CA, USA, 2012. [Google Scholar]
- Ma, X.; Pan, Z.; Hu, S.; Wang, L. Reversible Data Hiding Scheme for VQ Indices based on Modified Locally Adaptive Coding and Double-Layer Embedding Strategy. J. Vis. Commun. Image Represent. 2015, 28, 60–70. [Google Scholar] [CrossRef]
- Qin, C.; Chang, C.C.; Chen, Y.C. A Novel Reversible Data Hiding Scheme for VQ-Comp ressed Images Using Index Set Construction Strategy. KSII Trans. Internet Inf. Syst. 2013, 7, 2027–2041. [Google Scholar]
- Wang, W.J.; Huang, C.T.; Yang, C.H.; Wang, S.J. VQ-based Algorithms Extended to Non-Embedded Watermarking for Multimedia Ownership Prevention Systems. Peer-to-Peer Netw. Appl. 2014, 7, 676–686. [Google Scholar] [CrossRef]
- Chen, L.S.T.; Lin, J.C. Steganography Scheme Based on Side Match Vector Quantization. Opt. Eng. 2010, 49, 037008. [Google Scholar] [CrossRef]
- Shie, S.C.; Jiang, J.H. Reversible and High-Payload Image Steganographic Scheme based on Side-Match Vector Quantization. Signal Process. 2012, 92, 2332–2338. [Google Scholar] [CrossRef]
- Kuo, W.C.; Wuu, L.C.; Kuo, S.H. The High Embedding Steganographic Method based on General Multi-EMD. In Proceedings of the 2012 International Conference on Information Security and Intelligent Control (ISIC’12), Yunlin, Taiwan, 14–16 August 2012; pp. 286–289.
- Kuo, W.C.; Wang, C.C. Data Hiding based on Generalised Exploiting Modification Direction Method. Imaging Sci. J. 2013, 61, 484–490. [Google Scholar] [CrossRef]
- Run-length encoding. Wikipedia Archive. Available online: http://en.wikipedia.org/wiki/Run-length_encoding (accessed on 1 July 2015).
- Chang, C.C.; Lin, C.Y.; Wang, Y.Z. New Image Steganographic Methods Using Run-Length Approach. Inf. Sci. 2006, 176, 3393–3408. [Google Scholar] [CrossRef]
- Chang, C.C.; Tseng, H.W. A Stegano graphic Method for Digital Images Using Side Match. Pattern Recognit. Lett. 2004, 25, 1431–1437. [Google Scholar] [CrossRef]
- Againan, S.S.; Cherukuri, R.C. Run Length Based Steganography for Binary Images. Pattern Recognit. Mach. Intell. Lect. Notes Comput. Sci. 2005, 3776, 481–484. [Google Scholar]
- Lee, C.F.; Weng, C.Y.; Sharma, A. Stega nographic Access Control in Data Hiding Using Run Length Encoding and Modulo Operations. Secur. Commun. Netw. 2011. [Google Scholar] [CrossRef]
- Pevn, T.; Bas, P.; Fridrich, J. Steganalysis by subtractive pixel adjacency matrix. IEEE Trans. Inf. Forensics Secur. 2010, 5, 215–224. [Google Scholar]
- The USC-SIPI Image Database. Available online: http://sipi.usc.edu/database/ (accessed on 1 July 2015).
- Sedighi, V.; Cogranne, R.; Fridrich, J. Content-Adaptive Steganography by Minimizing Statistical Detectability. IEEE Trans. Inf. Forensics Secur. 2015. [Google Scholar] [CrossRef]
- Fridrich, J.; Kodovsky, J. Multivariate Gaussian model for designing additive distortion for steganography. In Proceedings of the 2013 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Vancouver, BC, Canada, 26–31 May 2013; pp. 2949–2953.
- Sedighi, V.; Fridrich, J.; Cogranne, R. Content-adaptive pentary steganography using the multivariate generalized Gaussian cover model. In SPIE, Electronic Imaging, Media Watermarking, Security, and Forensics, San Francisco, CA, USA, 4 March 2015; p. 94090H.
- Fridrich, J.; Kodovsk, J. Rich models for steganalysis of digital images. IEEE Trans. Inf. Forensics Secur. 2012, 7, 868–882. [Google Scholar] [CrossRef]
- Denemark, T.; Sedighi, V.; Holub, V.; Cogranne, R.; Fridrich, J. Selection-channel-aware rich model for steganalysis of digital images. In Proceedings of the IEEE International Workshop on Information Forensics and Security (WIFS), Atlanta, GA, USA, 3–5 December 2014; pp. 48–53.
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kuo, W.-C.; Kuo, S.-H.; Wuu, L.-C. Multi-Bit Data Hiding Scheme for Compressing Secret Messages. Appl. Sci. 2015, 5, 1033-1049. https://doi.org/10.3390/app5041033
Kuo W-C, Kuo S-H, Wuu L-C. Multi-Bit Data Hiding Scheme for Compressing Secret Messages. Applied Sciences. 2015; 5(4):1033-1049. https://doi.org/10.3390/app5041033
Chicago/Turabian StyleKuo, Wen-Chung, Shao-Hung Kuo, and Lih-Chyau Wuu. 2015. "Multi-Bit Data Hiding Scheme for Compressing Secret Messages" Applied Sciences 5, no. 4: 1033-1049. https://doi.org/10.3390/app5041033
APA StyleKuo, W.-C., Kuo, S.-H., & Wuu, L.-C. (2015). Multi-Bit Data Hiding Scheme for Compressing Secret Messages. Applied Sciences, 5(4), 1033-1049. https://doi.org/10.3390/app5041033





