1. Introduction
Blockchain is a distributed ledger technology that securely connects data blocks using cryptographic hash pointers, forming a tamper-resistant ledger. By employing cryptographic techniques and consensus mechanisms, blockchain removes the need for centralized control, which enhances security, transparency, and robustness. Its broad applicability extends across various fields, including cryptocurrency transactions, smart contracts, supply chain management, healthcare record management, and digital asset trading platforms [
1,
2,
3,
4,
5,
6,
7,
8,
9,
10,
11,
12].
The emergence of smart-contract-based cryptocurrencies such as Ethereum has expanded the application areas of blockchain technology. Smart contracts are self-executing code designed to run in a distributed virtual machine spanning a global network. They enable the application of various business logics beyond simple cryptocurrency transactions using blockchain technology [
13,
14]. The use of smart contracts is widely applied in various areas such as prediction markets [
15,
16,
17], fractional ownership [
18,
19,
20], and digital asset exchanges [
21,
22], driving innovations in blockchain-based asset trading.
Blockchain technology offers several advantages for trading certain types of physical assets. For instance, if a physical asset can be tokenized on the blockchain and endowed with digital uniqueness, it can benefit from digitalization in various ways. Specifically, if token transactions on the blockchain network can be recognized as equivalents of actual asset transactions, this could significantly enhance the security and efficiency of the asset trading process [
21,
23,
24]. In this study, we define the process of tokenizing and making assets tradable on the blockchain network as
digital assetization, and the assets themselves as
digital assets. Furthermore, platforms that facilitate the trading of such digital assets will be referred to as
Digital Asset Trading Platforms (DATPs).
This paper explores a blockchain method for tokenizing specific physical assets and facilitating a DATP for such tokenized assets. In this study, we refer to the blockchain developed for this purpose as the
platform chain of the DATP. The primary goal of the platform chain is to tokenize physical assets, reduce transaction costs through token-based trading, and increase market accessibility. Furthermore, the platform chain seeks to increase trust in trading activities on the DATP utilizing the transparency and immutability of blockchain technology. Moreover, as observed in other business applications of blockchain [
23,
25], the platform chain can enhance overall efficiency of DATPs by streamlining the transaction process through the integration of cryptocurrencies and smart contracts.
To ensure the platform chain effectively supports DATP operations, certain conditions must be met to guarantee its reliability. These conditions are as follows:
C1: Transactions recorded on the platform chain are practically immutable and cannot be arbitrarily deleted or altered.
C2: Transactions recorded on the platform chain are acknowledged by the vast majority of participants.
This condition (C3) is crucial in preventing platform administrators from arbitrarily rejecting or delaying the registration of specific transactions.
Currently, to satisfy conditions
C1,
C2, and
C3, most blockchain projects related to platform management implement reward mechanisms for block mining (the process of adding new blocks to the blockchain) to encourage broad participation. However, these mechanisms can significantly increase operational costs, as competitive block mining may require excessive energy consumption. Some blockchain networks also charge transaction fees as compensation for transaction processing on the blockchain. While this approach may be sustainable for blockchains with high transaction volumes, it poses a challenge for blockchains with low transaction volumes, where higher per-transaction fees are required to sustain operations [
26,
27,
28,
29,
30].
Various methods have been proposed to reduce the operational costs of blockchain. The most commonly adopted approach is to implement cost-effective consensus algorithms for block mining [
31,
32,
33,
34,
35,
36]. While this approach can achieve certain cost savings, it is not ideal for platform chains for small-scale DATPs. The main limitation is the inability to offer sufficient incentives for block mining within these smaller platform chains, making it challenging to attract a sufficient number of block miners. Another approach is to delegate block mining authority to specific individuals or a limited group, as seen in private or consortium blockchains [
37]. However, this approach may struggle to build trust among general users, as block mining authority is restricted to certain entities or individuals.
1.1. Objectives of Study
This study proposes a blockchain-based system optimized for managing small-scale Digital Asset Trading Platforms (DATPs). Before presenting the proposed approach, it is important to explain why this study focuses on blockchain-based platform management, particularly why small-scale platforms are emphasized.
First, the need for blockchain-based platform management stems from the ability to leverage blockchain’s decentralized nature to neutralize platform governance. Platform monopolization often has detrimental effects: it restricts fair competition by creating barriers for new entrants and stifling innovation. Users are compelled to conform to monopolistic platform policies and pricing, which limits choice, while the risk of data misuse for private gain raises privacy concerns. Moreover, limited transparency in decision-making can lead to decisions that overlook user needs, ultimately hindering the platform’s potential for broad adoption across diverse fields.
Next, this study focuses on small-scale platforms because blockchain-based tokenization is highly dependent on the characteristics of the associated physical assets, making it likely that platforms facilitating the trade of tokenized assets will be small in scale. In other words, a specialized small-scale platform tailored to specific physical assets is expected to be necessary. The blockchain-based tokenization model assumed in this study goes beyond merely recording the transfer of digital asset ownership; rather, it considers cases where transactions of blockchain-based tokens directly affect the ownership rights of the corresponding physical assets.
For instance, if a tokenized digital asset represents the right to operate a specific electric vehicle, ownership of the token on the blockchain serves as definitive proof of the right to use the vehicle. In such cases, the tokenization process is influenced not only by the attributes of the digital asset but also by the characteristics of the associated physical asset. Therefore, a DATP must account not only for digital token transactions but also for the operational rights of the physical asset—such as driving range, usage duration, and liability—alongside the specific characteristics of the individual vehicle. Given these considerations, small-scale platforms designed for specific assets are expected to be more effective and more widely adopted than large-scale platforms.
Thus, this study’s exploration of blockchain methods tailored to small-scale platforms for trading specific tokenized assets is particularly valuable and contributes to the growing field of asset-specific digital trading platforms.
One of the primary challenges in converting a small-scale platform that trades physical assets or associated rights into a blockchain-based tokenized asset trading platform is the high operational cost associated with blockchain technology. For instance, ensuring the reliability of the platform chain (the blockchain that governs the operation of the tokenized asset trading platform) by incentivizing a large number of participants to engage in block mining is particularly challenging for platform chains designed for small-scale digital asset trading. This is because, if the incentives are insufficient, the number of participants will decrease, making it difficult for the blockchain to satisfy conditions C1, C2, and C3 at any meaningful capacity. Conversely, if the rewards are set too high, the operational costs of the platform chain will increase, thus reducing the benefits of adopting the platform chain.
Most existing blockchain projects seek to mitigate this cost issue through the use of native cryptocurrencies. However, for this model to be sustainable, it relies on the assumption that the value of the cryptocurrency will continuously increase or at least remain stable. This assumption is often unrealistic, and without it, most blockchain networks cannot sustain their operations.
In this study, we propose the use of a private blockchain as a practical solution to address the cost challenges associated with operating small-scale digital asset trading platforms. Specifically, we propose a method that foregoes condition C3 under ideal blockchain conditions, while still satisfying conditions C1 and C2. For this proposal to be meaningful, the following question must be answered:
1.2. Outline of Proposed Method
To address the aforementioned issue Q, this study proposes constructing the platform chain, which governs the operation of the tokenized asset trading platform, as a sidechain anchored to a reliable existing blockchain, such as Bitcoin or Ethereum, rather than as an independent blockchain. This approach allows the platform chain to inherit the security and trust of the existing blockchain (hereafter referred to as the reference chain), while maintaining platform-specific configurations. The platform chain operates independently of modifications to the reference chain, minimizing dependency on it and thus reducing operational costs. All computations related to tokenization are performed exclusively on the platform chain, ensuring that the specialized configuration of the platform remains unaffected by external factors.
Additionally, all platform operations are managed through predefined smart contracts on the platform chain, ensuring that all activities strictly adhere to preset regulations. Only the hash value of each transaction is stored on the platform chain, while the actual transaction data are selectively disclosed on the dual platform chain upon request, after secure registration. This mechanism is designed to prevent platform operators from manipulating transaction registrations for personal gain. Furthermore, the proposed approach leverages the fact that only hash values are stored on the platform chain. By aggregating multiple transactions into a Merkle tree and recording its root hash on the platform chain, all transactions within the Merkle tree can be stored on the secondary platform chain, supporting scalable and efficient platform operations.
This paper focuses on the blockchain architecture required for operating small-scale digital asset trading platforms, and specific blockchain tokenization methods for digital assets are omitted. This decision stems from the inherent difficulty of describing blockchain tokenization methods as a single approach, given their reliance on the unique characteristics of the underlying physical assets. Future research on specific blockchain tokenization methods will be addressed in a separate study.
1.3. Key Contributions
This study proposes a method for constructing a platform chain optimized for small-scale DATPs. Instead of building the platform chain as a standalone blockchain, the proposed method constructs a platform chain anchored to established blockchains, such as Bitcoin and Ethereum, which serve as reference chains due to their proven stability and reliability.
The main contributions of the proposed method are as follows:
Designing the platform chain as a sidechain of existing blockchains within a private or consortium blockchain framework. This setup leverages the trust and security of established blockchains, while reducing the setup and maintenance costs of the platform chain.
Enabling seamless integration of the platform chain without requiring any modifications to the reference chain, thereby preserving its autonomy and facilitating the deployment of customized platform blockchains.
Recording only the hash values of transactions on the platform chain, while disclosing the actual transaction contents on the dual platform chain, thereby enhancing data privacy and confidentiality.
Enabling scalable transaction processing by consolidating multiple transactions into a single hash value, thereby enhancing the efficiency and flexibility of the platform.
These contributions collectively provide a scalable, privacy-aware, and economically viable foundation for digital asset trading on small-scale platforms.
In lieu of empirical results or simulation-based benchmarks, this study adopts a formal threat analysis to evaluate the robustness and trustworthiness of the proposed framework. This approach is aligned with the design-oriented nature of the work, where system security and integrity are ensured by structural safeguards and role-specific constraints rather than probabilistic performance metrics.
Since the framework is intended for permissioned blockchain environments with explicit governance mechanisms, well-defined participant roles, and contract-based execution, its effectiveness is best demonstrated through adversarial modeling. Accordingly, the security evaluation is structured to identify potential vulnerabilities and to analyze how each threat is mitigated by the proposed design.
1.4. Organization of the Paper
The remainder of this paper is organized as follows:
Section 2 provides background on blockchain technology and reviews related work.
Section 3 introduces the proposed method in detail.
Section 4 evaluates the proposed method through a comprehensive threat analysis and discusses its limitations as well as directions for future research. Finally,
Section 5 provides discussions and concluding remarks.
2. Background and Related Work
In this section, we define the key terms and notations used in this paper and provide relevant background on blockchain technology. Additionally, we review prior research on sidechain methods and rewardless block mining.
2.1. Blockchain Fundamentals
A blockchain can be conceptualized as a state machine that maintains a record of historical states and user interactions. Specifically, miners, participants in the blockchain network who compete to compute a new block and are typically incentivized by rewards, gather
transactions to form a new block, denoted as
. Miners then attempt to compute a
proof of work (explained shortly) to append this new block
to the existing blockchain
, which contains all previous states and interactions up to the
-th state. The addition of
enables a state transition from the
-th state to the
n-th state, formally expressed as
where
denotes concatenation.
The proof of work mechanism establishes a competitive process for appending new blocks (referred to as block mining) to the blockchain, thereby preventing monopolization by a small number of miners. Specifically, let
denote the set of transactions collected by a miner for inclusion in block
, where
denotes the total number of transactions in
.
Block
consists of the hash value
of the immediately preceding block
, the transaction set
, and a nonce
that ensures the block meets predefined conditions. When a miner is said to have obtained the proof of work to add their constructed block
to the existing blockchain
, this implies that they have successfully calculated the nonce
to satisfy the required conditions based on the transaction set
they intend to register. This process can be expressed as
where
H is a cryptographic hash function,
represents the set of conditions that the hash value
of
must meet, and
is the nonce number that satisfies (
3). In Bitcoin,
H is the SHA-256 hash function [
38], and
is defined as the set of 256-bit strings that are smaller than a predetermined target value. In (
3), the blockchain includes the hash value of the last connected block in a new block, ensuring the integrity of the blockchain by preventing arbitrary modifications to previously linked blocks.
A smart contract is a self-executing computer program deployed on a blockchain that automates the execution of contractual logic between parties. As demonstrated in Ethereum, a smart contract consists of program code that maintains internal variables and state, and can generate outputs deterministically based on input data. While a smart contract cannot initiate itself, it is triggered explicitly by a user through a transaction. For example, the transaction
instructs all nodes in the blockchain network to execute the smart contract
with input
d, based on a valid request from user
u. To verify the authenticity of the initiating user, the transaction must include a digital signature, though this aspect is omitted in this discussion for simplicity. Once invoked, a smart contract can maintain cryptocurrency balances, update internal state, and even trigger other smart contracts during its execution.
In the standard format of a transaction, this is represented as follows:
For the sake of simplicity, we will use the owners instead of their addresses in the sender and receiver fields. For example, in (
4),
u represents
. Here,
refers to the address of
X, which acts as an identifier on the blockchain network. This simplification does not lead to any ambiguity in the sender and receiver fields, as only addresses are permitted in these fields. However, in the transmitted content field, omitting addresses may cause confusion, as the distinction between an address and its owner can have different implications in this context.
A sidechain is a blockchain that operates autonomously but remains closely connected to the main blockchain network (hereafter referred to as the mainchain). Sidechains are frequently utilized to perform specific functions or provide specialized capabilities, thereby extending the utility of the mainchain.
In this study, sidechains are employed to construct platform chains optimized for the operation of small-scale platforms, while leveraging the established reliability of an existing blockchain. The existing blockchain serves as a reference for recording platform activities on the platform chain in an immutable manner. Instead of using the more common term mainchain, we use the term reference chain to describe this existing blockchain in relation to the platform chain, emphasizing its role as a trust anchor and integrity reference.
2.2. Previous Studies on Sidechain Methods and Rewardless Block Mining
Previous research on sidechain methods has explored various aspects, highlighting their diverse applications and technical challenges in blockchain ecosystems. For example, studies such as [
39,
40,
41,
42,
43,
44,
45] have focused on the technical design and implementation of sidechains, investigating key aspects, including interoperability, security, scalability, sharding, and consensus mechanisms. In contrast, the research in [
46,
47,
48] examined the security and trust implications of sidechains, including their impact on the security of the mainchain, potential vulnerabilities, and strategies to ensure trust and integrity in sidechain operations.
Additionally, studies such as [
24,
49,
50] have explored the practical applications of sidechains across various domains, including finance, digital content management, supply chain management, healthcare, and identity management. These works sought to identify use cases in which sidechains can offer specific benefits and address industry-specific challenges. Furthermore, the economic and incentive models associated with sidechains, including token economics, staking mechanisms, and reward structures, were investigated in [
51,
52], with the goal of aligning incentives for participants in sidechain networks.
Two notable sidechain implementations, Liquid and RSK, illustrate contrasting approaches to trust and incentive structures. Liquid, developed by Blockstream [
53], is a federated sidechain governed by a consortium of functionaries and offers no monetary rewards for block production, instead relying on institutional trust and multisignature consensus. RSK [
54], by contrast, employs merge mining, where Bitcoin miners are incentivized through transaction fees and token rewards. While both systems provide strong security, they are better suited to large-scale or token-driven environments. For small-scale digital asset trading platforms without native tokens or the infrastructure to manage economic incentives, these models may be unnecessarily complex.
Alternative incentive models for decentralized blockchain systems without block mining rewards have attracted considerable attention within the blockchain research community. Most studies have concentrated on developing consensus algorithms that do not rely on block mining rewards [
34,
35,
55]. Other research has explored alternative compensation models, such as transaction-fee-based systems or community governance and funding mechanisms, to replace traditional mining incentives [
36,
56,
57,
58].
However, these approaches encounter several challenges. Consensus mechanisms such as Byzantine Fault Tolerance (BFT) and Proof of Stake (PoS), despite eliminating the need for mining rewards, encounter scalability challenges and security vulnerabilities, such as the ‘nothing-at-stake’ problem, particularly in high-throughput environments [
55]. Additionally, the absence of traditional block rewards complicates the design of effective incentive mechanisms, making it challenging to sustain validator participation and ensure network security during low transaction periods [
34]. Transitioning to new consensus mechanisms can also introduce governance complexities and adoption barriers, potentially leading to reduced participation or even network splits [
59].
Moreover, reliance on transaction fees or community funding models can reduce validator incentives during periods of low transaction volumes, thereby affecting both security and decentralization [
36,
57]. Governance complexities and the transition from existing reward models further complicate the adoption of these approaches [
56,
58]. While these models present promising alternatives, their practical implementation requires further research to address these critical challenges comprehensively.
Unlike previous studies that emphasized extending mainchain functionalities through sidechains, this study adopts a different approach by using the mainchain as a reference for independently purposed sidechain networks. A key contribution of this study is its focus on addressing block mining reward issues through the use of private or consortium blockchains, rather than designing new consensus algorithms primarily for public blockchains.
3. Proposed Method
3.1. Notations and Terminologies
This study aims to introduce an efficient and reliable sidechain solution for a small-scale digital asset trading platform (DATP). To simplify the discussion, we denote the target DATP as M and the platform chain responsible for operating M as .
As discussed in
Section 1.2, this study proposes constructing the
not as an independent blockchain but as a sidechain linked to well-established blockchains like Bitcoin and Ethereum. In this context, the blockchain serving as the mainchain is referred to as the reference chain, denoted by
.
The proposed approach supports the use of either fiat currency or the ’s cryptocurrency (denoted as ) as the medium of exchange within the DATP M. This study does not consider creating a dedicated cryptocurrency within the for transactions, as this is deemed unsuitable for small-scale DATPs.
While fiat currency can be used as a medium of exchange, this study primarily focuses on utilizing the ’s cryptocurrency, , for transactions. The fiat-currency-based model requires financial institutions to mediate credit-related transactions, incurring intermediary fees. However, this paper does not discuss this model in detail, as it naturally follows from the cryptocurrency-based approach presented.
Table 1 summarizes the key symbolic notations used throughout the framework. All symbols listed in
Table 1 are used to represent conceptual roles, smart contracts, blockchain entities, or their operational relationships, rather than referring to any experimentally derived data or adjustable parameters. Each symbol’s conceptual significance is briefly explained in the table caption or surrounding text to enhance the reader’s understanding.
3.2. Platform Chain as Sidechain
The proposed method assumes that is a private or consortium blockchain where block mining is restricted to a select group of entities. In this scenario, it is likely that the designated miner of and the operator of M are the same entity, or at least have aligned interests in the operation of M. Accordingly, we assume that the designated miner of and the manager of M are the same entity, denoted by .
Since holds significant authority over both the platform chain and the operations of M, there is a risk that could arbitrarily manipulate transactions or enforce rules that disproportionately benefit itself. If left unchecked, such unilateral control may undermine user trust and discourage participation in M. To address this concern, the proposed method introduces a solution using a sidechain mechanism along with smart-contract-guided transaction registration (the details of which will be explained in the next section).
In the proposed method,
, acting as the platform manager, defines the interaction rules between
and
using smart contracts, collectively denoted as
. Additionally, it specifies the operational rules of
M through smart contracts, collectively denoted as
, which are to be registered and used within
. These are submitted for registration on
and
as follows:
where
and
represent the designated addresses for smart contract registration requests on
and
, respectively. Since
is the designated miner of
, the transaction
serves to publicly announce and register
within
. The block containing transaction
in (
6), denoted as
, is treated as the genesis block of
. Here,
functions as the gateway between
and
, while
defines the operational rules governing
.
Using the transaction defined in (
6), the platform operator
establishes the operational rules of DATP
M through the smart contracts
and
, both of which are immutably recorded on
. This design aims to enhance user participation in DATP
M. To achieve this,
and
must be designed to operate fairly and transparently to gain user trust.
It is also important to note that operates the platform for economic benefit, typically through fees or value captured from user participation. Therefore, the long-term sustainability of the platform depends heavily on maintaining user trust and ensuring that the operational logic encoded in and is both reliable and fair. If users suspect that the rules are biased or insecure, they may avoid participating, undermining both the platform’s integrity and ’s own incentives.
However, evaluating the technical adequacy of and solely by or general users presents challenges. Since has direct influence over these contracts, conflicts of interest may arise. On the other hand, general users often lack the expertise needed to assess the complexity of smart contracts. Thus, an impartial technical evaluation of and by external experts is essential. Accordingly, the platform manager is expected to rely on a neutral external entity to ensure a fair assessment of the validity of these smart contracts. The specific methods for obtaining this impartial evaluation are outside the scope of this paper, as it focuses on proposing a general framework rather than detailing external validation procedures.
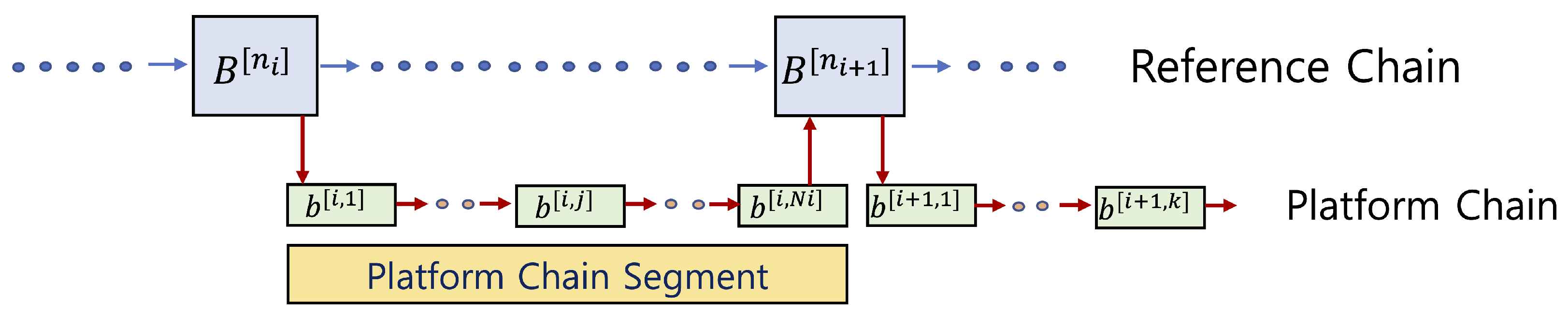
As a sidechain of , operates independently under normal conditions but periodically establishes connections to based on the rules immutably coded in . Let denote consecutive blocks connected to after . We denote the sequence of consecutive blocks within from to as , , …, (hereafter referred to as the platform chain segment).
The platform chain segment
,
,
…,
starting at
indicates that the header of
includes the hash value of
:
Similarly, the fact that the platform chain segment
,
,
…,
ends at
implies that the following transaction
is included in
:
Blocks within the platform chain segment , , …, also follow the standard hash value chaining rules. Once is securely recorded on , modifying transactions within , , …, becomes virtually impossible, even for . In this case, we say that , , …, are connected to . This framework is autonomous, as does not need to perform explicit actions to initiate or finalize a segment within its own blocks. The operations on proceed automatically, following the predefined rules in .
Using a well-established blockchain such as Bitcoin or Ethereum as
provides significant advantages, as it allows the system to inherit its stability and security without requiring active intervention from these well-known blockchains.
Figure 1 illustrates these concepts; segment
,
,
…,
is finalized when its commitment is recorded in block
on
, ensuring immutability and trust inheritance.
3.3. Smart Contract-Guided Transaction Registration
In the previous section, we proposed constructing as a sidechain of , where , the designated miner of the platform chain , holds minimal influence. This design serves to mitigate arbitrary behavior by . In this section, we introduce an additional safeguard against misuse: smart-contract-guided transaction registration.
To enhance clarity, we now present a concrete example. Assume that the digital asset traded in DATP M is derived from a specific type of physical asset. Specifically, let represent the digitized ownership of certain rights associated with a physical asset, denoted by , which is uniquely identified by K. Let denote the smart contract deployed on to manage .
Suppose user u owns . This means that u can generate a valid digital signature using the private key corresponding to the public key linked to . In this case, is uniquely represented by a blockchain token, and ensures that u retains exclusive control over it.
The specific enforcement mechanism depends not only on the physical properties of but also on the legal status of . For instance, if is an electric vehicle and represents the right to operate it, then may enforce ownership by allowing only users with a valid digital signature linked to to start the engine of .
This paper does not elaborate on the exact mechanism through which
enforces the ownership of
. Furthermore, the process of blockchain tokenization for
is beyond the scope of this work. For a detailed discussion on blockchain tokenization, see [
21].
The proposed method restricts the transactions that can be registered on
to those that request specific operations from
, a set of predefined smart contracts announced in (
6), as well as additional operation requests or public disclosures of results generated during the execution of these smart contracts. In other words, this approach limits the transactions registered on
to predefined operations, thereby simplifying the procedures required to verify their validity.
For example, suppose that
u agrees to transfer their ownership of
to
v in exchange for
, which represents
L units of
. To complete this transaction,
u must execute a predefined smart contract
on
, which is designed to transfer ownership of the
tokens, by submitting the following transaction for registration on
,
where
n is a nonce used to prevent
from being replayed, and
r is a random number chosen by
u to ensure that
cannot be predicted from its hash value. The reason for this will be explained in the next section. Here, recall that the digital signature
by
u on
is omitted for simplicity. This transaction triggers the execution of
under the predefined conditions
, which include details such as the digital asset
, the addresses of the seller
u and the buyer
v in both
and
, the sale price
, and the time limit
T. We represent these dependencies as follows:
where, for clarity,
u and
v denote the addresses of the participants in
, while
and
represent their corresponding addresses in
. The procedures following the registration of
will be discussed in the next section.
Before concluding this subsection, we note that in (
9), lowercase notation is used to indicate that
is a transaction on
, whereas in (
6) and (
8), uppercase notation indicates that
and
are transactions on
. Throughout this paper, we follow this convention to specify the blockchain associated with each transaction.
3.4. Dual Platform Chain
The subsequent actions for transaction
in (
9) are sequentially executed by predetermined smart contracts once all conditions in (
10) have been satisfied. However, for these actions to proceed,
must first be registered in
by
. To prevent
from selectively rejecting transactions for personal gain, the proposed method initially records only the hash value
in
at the request of its creator (in the case of
, by
u). Then,
is disclosed in the
dual platform chain immediately after the
segment containing
is connected to
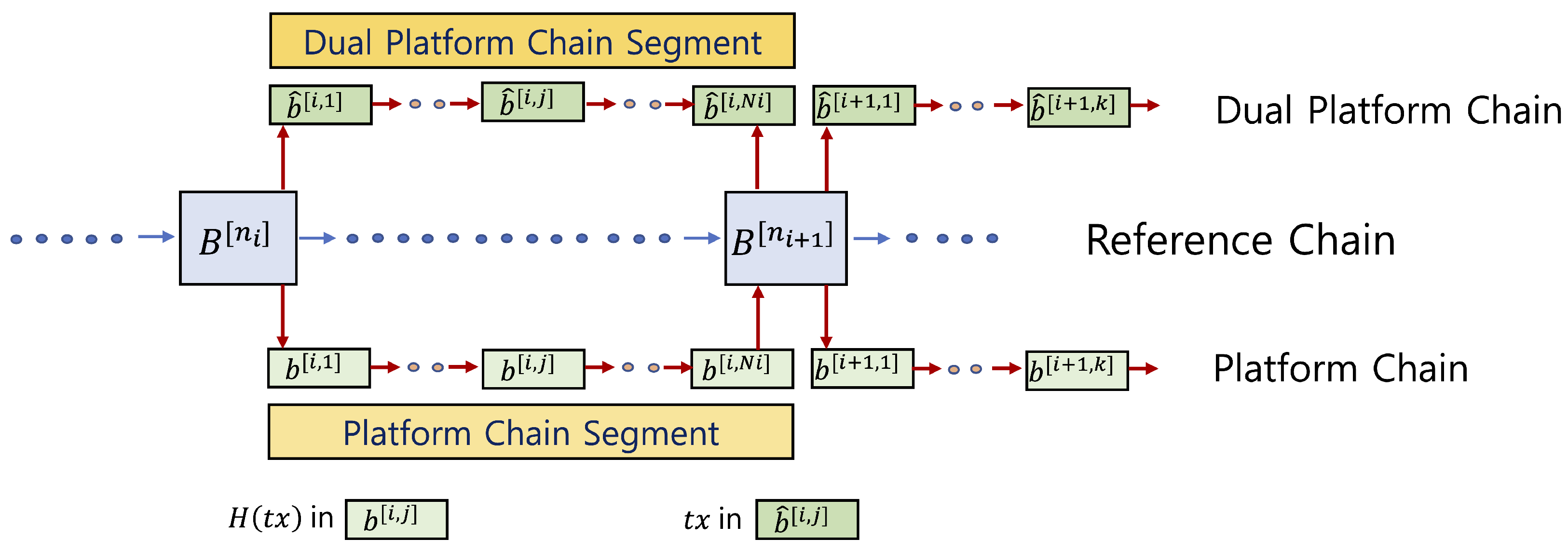
. Here, the dual platform chain
is defined as a sidechain of
with the same structure as
, where the correspondence between
and
is established as follows: If a hash value
is registered in block
of
, then transaction
is disclosed in the corresponding block
of
. Conversely, if transaction
is directly registered in block
of
without hashing, it is also placed in the corresponding block
of
.
Figure 2 illustrates this scenario; each block
in
corresponds to a block
in
that discloses the transaction content associated with the hash values recorded in
To further explain how the proposed method prevents
from selectively rejecting or delaying the registration of certain transactions, let
be the
block containing
in (
9), and let
be the
block at which the
segment containing
ends. Once this segment of
is connected to
, modifying or removing
becomes virtually impossible, as it would require altering
and all subsequent blocks in
. Additionally, the use of the random number
r in (
9) ensures that
cannot infer the content of
from
alone, thus providing no basis for selectively rejecting or delaying its registration.
It is also worth noting that not all transactions are initially registered as hash values in . For example, transactions explicitly requested by their creator to be directly registered in , transactions generated by , and transactions occurring between smart contracts must be disclosed. Furthermore, any transaction intended for public visibility from the outset can be directly registered in .
To make the process of disclosing transactions in autonomous, the proposed method uses an independent entity D from , whose role is to store hashed transactions and corresponding transactions uploaded from users, and to disclose in , after the block containing is connect to . Notice that the disclose of does not need help from . Anyone can provide the transaction, as long as its hash value matches the one in . The data warehouse D can make itself independent from by providing a neutral mechanism that allows an anonymous uploading of and (the encryption of by a user) and the conditional decryption of after the block containing is connected to .
In this process, misconduct by (preventing D from disclosing transactions in ) or D (failing to promptly disclose transactions in ) is easily detectable. Users can report misconduct by or D to A, a designated auditing entity, using the information recorded in as evidence. Although could technically continue to resist allowing transactions to be disclosed in , doing so would undermine the credibility of DATP M’s operations, an outcome that would likely seek to avoid. The same holds true for D.
Additionally, once DATP M is launched, the role of becomes limited to registering requested transactions and initiating predefined smart contracts under immutable operating rules. Consequently, the functions of within DATP M can be automated and are readily replaceable, serving as a deterrent against potential misconduct by . Similarly, this concept of role automation also applies to entities D and A. Thus, the assumption that D and A will act neutrally in accordance with predefined rules is practical within the proposed method.
3.5. Subsequent Operations by Smart Contracts
Once
is disclosed in
of
,
checks its validity, if necessary, using the hash value recorded in
of
. If the validity test fails,
disregards
, and no further actions are taken. This ensures that only valid transactions proceed, thereby maintaining the integrity of the system. On the other hand, if the validity test succeeds,
instructs
(the smart contract specified in the output field of (
9)) to request
to verify whether the ownership of
belongs to
u by executing the following transaction:
where the function
returns ‘True’ if
, and ‘False’ otherwise. This transaction instructs
to report the result of
back to
. If the return value of
in (
11) is ‘True’, then
instructs one of the smart contracts in
, which is designed to act as an escrow service, to check whether the buyer
v has transferred
to
by executing
Conversely, if the return value of
is ‘False’,
disregards
and no further actions are taken.
Now, consider the case where
v sends
to
, which is verifiable by the following transaction on
:
Through this transaction,
v instructs
to hold
under the conditions defined in
.
Note that v could technically send directly to u without using . However, the proposed method enforces the use of as in to ensure the entire process remains visible in both and .
The smart contract
, specified in the output field of
in (
12), scans newly added blocks in
within a predefined time window to determine whether
has been recorded. If it finds
, it returns ‘True’ to
, as specified in
. Otherwise, it returns ‘False’, and
disregards
, with no further action taken.
Recall that the goal of
is to transfer
from
u to
v at a sale price of
. If both
and
return ‘True’ within the time period defined by
T in
(see (
10)), then
proceeds to request
to transfer
from
u to
v, and
to release
to
u by executing
In response to
,
updates the ownership of
in its internal memory from
to
, which are the
addresses of
u and
v, respectively. Likewise, in response to
,
sends
to
u by submitting the following transaction for registration in
:
The execution of
, and consequently the registration of
,
,
,
, and
, can only occur after
is disclosed, i.e., only after
, the
block finalizing the
segment containing
, has been mined.
Note that is also the starting point for the next segment, , , …, . The proposed method enforces that the mining of , , …, begins only after the execution of all transactions registered as hash values in the prior segment , , …, is completed. This ensures that the sequential integrity across segments is preserved.
To better understand what it means for a transaction to be fully executed, consider
in (
9), where user
u sells digital asset
to
v. Suppose the hash of
is included in the
segment
,
,
…,
, which ends at the
block
. The execution of
begins only after
is anchored to
and the full content of
is disclosed on
. This rule applies equally to all transactions registered as hash values in the segment, and only once all such executions are completed can the subsequent segment
,
,
…,
be created.
However, defining the execution of
as complete only after all of
in (
11),
in (
12),
in (
13),
in (
14),
in (
15), and
in (
16) have been completed is not practical. This is because
and
are executed on the reference chain
, and the platform has no mechanism to enforce their timely execution. To address this, the framework requires
to be pre-registered when
is created, and it is expected to be completed before
is triggered. As for
, there is no need to wait for its completion to consider
finalized, since
is executed by the smart contract
and, by its deterministic nature, its successful execution is guaranteed once invoked. Accordingly, in this study, we define the execution of
as complete once
has been successfully processed.
Before closing this section, we emphasize that transactions , , , , and are automatically derived from the registration of . Therefore, they do not require separate registration. In fact, is not even recorded in , as the reference chain does not store the outcomes of smart contract executions. Nonetheless, the proposed framework records all of these derived transactions in both and , so that the results of the smart contract executions remain publicly verifiable without requiring users to re-execute the logic themselves.
3.6. Cost-Effective and Privacy-Preserving Transaction Registration
To prevent operator abuse of power, the proposed method only registers the hash values of transactions on the platform chain , while their full content is disclosed later on the dual platform chain . This enables a cost-effective and privacy-preserving approach to transaction registration.
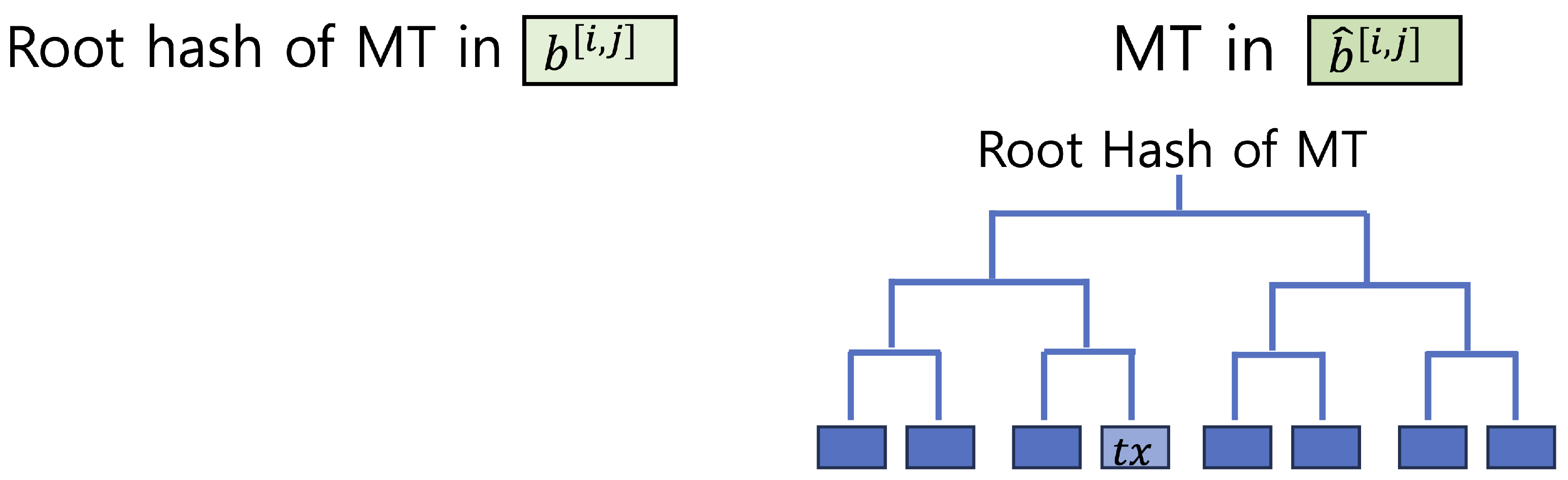
One key feature of the proposed method is its ability to aggregate multiple transaction hashes into a Merkle tree. For example, the data warehouse
D may collect transaction hashes
to be disclosed in
, construct a Merkle tree
, and request that the root hash is recorded in
via a smart contract
. This allows a large number of transactions to be registered through a single root hash, optimizing storage and bandwidth.
Figure 3 illustrates this scenario; Transaction hashes collected by
D are aggregated into a Merkle tree, with the root hash recorded in
and the corresponding transaction contents disclosed in
after finalization.
To ensure the correctness of batch registration, the method requires that transactions grouped under the same Merkle tree be logically and temporally independent. If dependencies exist between transactions, such a grouping may result in erroneous or unpredictable execution outcomes. However, D has no access to transaction content at the time of Merkle tree construction and thus cannot assess such dependencies. Even if full transaction data were available, detecting interdependencies would require semantic understanding beyond the scope of D’s role. Therefore, the framework deliberately excludes D from responsibility for verifying transaction independence.
3.7. User Responsibility for Transaction Independence
To address the difficulty of system-level dependency analysis, the proposed method assigns the responsibility for verifying transaction independence to users during transaction creation. Although this may initially appear burdensome, in practice, users typically base new transactions on data that have already be confirmed and finalized.
Specifically, users are advised to reference only those transactions that are fully registered. A transaction is considered fully registered when its hash is included in a platform chain segment that has been finalized by anchoring to the reference chain
. For instance, if a user wishes to register transaction
in block
of the segment
to
, then other transactions in the same segment are not yet finalized at the time of
’s creation. Finalization occurs only when the terminal block
is recorded on
. See
Section 3.5 for more details.
Failing to follow this guideline is risky. For example, suppose user w submits a transaction to buy asset from user v, assuming that transaction , in which u sells to v, will be successfully executed. If is not finalized or fails execution, w’s transaction becomes invalid. In this framework, such risk is borne entirely by the user. By enforcing this design principle, the system preserves transactional integrity, while maintaining decentralized control over dependency validation.
4. Results: Threat Analysis
This section adopts a structured threat analysis to evaluate the robustness and trustworthiness of the proposed framework. This approach is particularly well suited to permissioned blockchain environments, where the effectiveness of the system depends on role separation, structural constraints, and cryptographic accountability, rather than stochastic performance metrics.
Rather than presenting empirical data or simulation results, this study conducts a structured threat analysis to evaluate how the proposed architectural design systematically mitigates adversarial behaviors. Since core system properties—such as post-anchoring immutability, confinement to predefined smart contracts, and content-obscured transaction registration—are enforced by structural design constraints rather than by probabilistic mechanisms, threat analysis provides an appropriate and focused evaluation framework for validating the proposed method.
The following subsections categorize and examine key adversarial scenarios and describe the mechanisms by which the proposed method neutralizes each threat.
4.1. Threat 1: Transaction Manipulation by
A major threat in permissioned blockchain platforms is the possibility that the operator could exert discretionary control over transaction processing. This includes selectively rejecting, delaying, or reordering transactions for arbitrary or self-serving purposes. The proposed method systematically eliminates these threats through a combination of transaction hash commitment and dual-chain disclosure. We explain each aspect below:
Rejection and Delay: Users submit only the hash value of their transaction for initial registration in , which includes a random number r that conceals the transaction’s content. As cannot know what the transaction contains, it cannot selectively reject or delay it for content-based reasons. Any delay without justification becomes auditable once the segment is anchored to .
Reordering: Since all transaction hashes appear opaque at the time of registration, cannot prioritize or rearrange them meaningfully. For batch-registered transactions, their positions within the Merkle tree can be verified later, preventing order manipulation.
Modification: In conventional blockchains, transaction content is safeguarded against tampering through the use of digital signatures. In the proposed method, an additional concern arises from the requirement to disclose the results of smart contract executions for the sake of user convenience and transparency. This introduces the risk that could manipulate the published results to distort the intended execution outcome. To counter this, the framework allows the auditor A to independently recompute the outputs of all contract executions based on the original transaction and the associated smart contract logic. By comparing the actual disclosures on the platform chain with the expected outputs, A can detect and report any inconsistencies. This verification process ensures the integrity of execution results and deters manipulation by .
In summary, the proposed method mitigates operator manipulation through a combination of transaction hash commitment and dual-chain disclosure. By hiding transaction content during registration while ensuring cryptographic verifiability, it prevents content-based manipulation by the operator. This reduces discretionary control and reinforces trust in the fairness of transaction processing.
4.2. Threat 2: Intentional or Accidental Misconduct by Users
The framework gives users the flexibility to generate their own transactions, but it relies on their responsible behavior to maintain system integrity. Misconduct, whether intentional or accidental, can lead to inconsistencies, execution failures, or denial-of-service risks. The proposed framework addresses these concerns through the following mechanisms:
Dependency Validation Responsibility: Users are required to construct transactions based only on data from finalized transactions whose hash values have been recorded in a platform chain segment already anchored to the main chain. If a user references unconfirmed transactions that later fail, the resulting transaction is invalid and the responsibility lies entirely with the user. This rule prevents accidental inconsistencies and protects the platform from reliance on unguaranteed outcomes.
Double Selling: Double selling refers to an attempt by a user to sell the same digital asset to multiple recipients before the completion of the first transaction. Consider a case where a user
u attempts to sell the same digital asset
to both
v and
w, by submitting the transaction
as in (
9) to transfer
to
v, while simultaneously initiating another transaction
to transfer
to
w, before
is finalized. In the proposed framework, both
and
can be registered successfully, since neither
D nor
checks transaction dependencies during the registration phase. However, transactions are executed one at a time in the order they were registered. For each transaction, the smart contract
first validates its inputs, such as ownership and predefined execution conditions. Only if the transaction is valid is it executed. Therefore, once
is successfully executed and
is transferred to
v, the subsequent transaction
fails the validity check because
u no longer owns
.
Since the invalid transaction originates from
u’s misconduct,
does not refund the execution cost
that
u paid to invoke
. Instead, the smart contract redirects this cost to compensate
w, assuming
w has already initiated a payment transfer as in (
13) based on the expected receipt of
. To enable this compensation, the framework requires that
, where
is the execution cost of the
transfer on the reference chain
. This design ensures that the fee collected from
u’s invalid transaction is sufficient to cover the refund cost to
w, while leaving no incentive for
u to exploit the system. By setting the execution fee for asset transfer contracts higher than a standard
transfer, the framework effectively deters malicious users from attempting double selling.
Replay Attack: A replay attack occurs when a malicious actor attempts to reuse a previously submitted and valid transaction in a different context or time, aiming to duplicate its effect. In blockchain systems, such attacks can lead to unauthorized asset transfers or contract invocations if proper safeguards are not put in place.
In the proposed framework, replay attacks are prevented by including a unique nonce in each user-generated transaction, as shown in (
9). This nonce ensures that each transaction is executed only once and cannot be validly replayed in the future. If a transaction with the same nonce is submitted again, it will be rejected by the smart contract as a duplicate. This mechanism guarantees transaction uniqueness and defends the system against replay-based exploits.
Payment Refusal: A potential threat in digital asset transactions arises when a buyer refuses to complete payment after initiating or receiving a transaction. While refusing payment after receiving the asset would be a critical issue, such a scenario cannot occur in the proposed framework due to its sequential execution model.
Consider a case where a user
u attempts to sell the digital asset
to
v as in (
9), by submitting
to transfer
, and
v subsequently refuses to initiate the payment transaction
as described in (
13). In this case, the smart contract
detects the missing payment step during execution. As a result, the intermediate effects of
, including those from
in (
11) and
in (
12), are rolled back, keeping the asset
in
u’s ownership. Thus,
u suffers only the loss of the transaction execution cost for
, while
v incurs no penalty.
To discourage such opportunistic refusal, the framework introduces a deposit mechanism. Each participant is required to stake a small refundable security deposit when initiating asset-related transactions. If a user fails to complete a payment obligation after committing to a trade, the deposit can be partially or fully redirected to compensate the affected party. This mechanism aligns user incentives and prevents dishonest behavior such as strategic payment refusal.
Smart Contract Confinement: All user-created transactions must only interact with predefined and registered smart contract interfaces. This restriction ensures standardized behavior, prevents arbitrary operations, and enables the platform to detect, reject, and recover from any invalid or unexpected transactions in a verifiable and controlled manner.
Deterrence Against Malicious Behavior: Users who attempt to submit deliberately invalid transactions, such as flooding the system or triggering executions that are bound to fail, gain no advantage in the proposed framework. Every transaction is subject to validity checks by predefined smart contracts before execution, and any invalid transaction is immediately rejected without altering the system state. In addition, users must pay the execution fee regardless of whether the transaction succeeds, which makes repeated abuse financially unviable and discourages malicious attempts.
4.3. Threat 3: Transaction Manipulation by D
As the data warehouse responsible for handling user-submitted transactions, D plays a critical role in the proposed framework. It receives transaction hash values and encrypted transaction content from users, relays the hash values to for inclusion in , and later discloses the actual transactions in after the corresponding segment is finalized. Given this central role, D may be tempted to manipulate the transaction flow in ways similar to , such as selectively publishing, delaying, or reordering transaction content. The proposed framework prevents such behavior through the design features described below:
Rejection, Delay, and Reordering: Since transactions are uploaded in encrypted form and anonymously, D cannot infer their content or origin, and is required to disclose them in the order of hash registration immediately after the corresponding segment is anchored to , making any attempt to selectively delay, reorder, or omit transactions both auditable and easily detectable.
Collusion with : A potential threat is that D could collaborate with to selectively delay, reorder, or censor transactions. However, because users upload only hash values and encrypted transaction content anonymously, D cannot associate transactions with specific users or interpret their semantics prior to registration.
Although D performs a non-privileged and auditable role, further resilience could be achieved by designing the system to allow competition or redundancy among multiple candidate entities. Rather than relying on a single designated data warehouse, the platform could adopt a modular architecture where any qualified provider may fulfill D’s role as long as it conforms to the disclosure protocol. If any instance of D is found to be unreliable or malicious, another compatible provider can be deployed without disrupting the system. This approach enhances accountability through substitutability and aligns with the fault-tolerant principles used in decentralized infrastructure design.
4.4. Threat 4: Dishonest Behavior by Auditor A
In the proposed framework, the auditor A plays a crucial role in verifying transaction validity, detecting potential misconduct, and resolving disputes based on data from and . However, this responsibility also introduces a risk: if A acts dishonestly, either by misreporting outcomes or by neglecting its verification duties, this could undermine the trust and credibility of the entire platform. The framework addresses this risk through the following safeguards:
Issuing incorrect or misleading verification results: All evaluations by A are based on data that are immutably recorded on-chain, including transaction hashes, smart contract logic, and execution results. Because these data are publicly accessible and verifiable, any incorrect or dishonest report by A can be independently verified and, if necessary, refuted.
Exercising exclusive control over validation: The framework ensures that A does not rely on private information or privileged access. All necessary verification inputs are available on-chain, allowing others to replicate A’s role using independent or automated tools. This design supports the development of decentralized or community-driven auditing models and reduces the dependency on a single authority.
Legal accountability and institutional enforcement: To complement technical safeguards, the framework assumes that A operates under a legally binding agreement or regulatory oversight. This institutional structure clearly defines A’s obligations, grants it authority to act independently, and holds it accountable for negligence or willful misconduct through enforceable consequences. Given the auditor’s privileged role in verifying transaction validity and resolving disputes, assigning legal responsibility is not merely optional but practically indispensable to ensure trustworthy and reliable oversight.
In addition, because A performs a transparent and non-privileged function, any misconduct is readily detectable and remediable. If dishonesty is observed, A can be replaced without impacting the platform’s functionality.
4.5. Summary of Security Guarantees
The proposed method achieves a balanced division of trust and responsibility among key components of the system, supported by cryptographic guarantees and role-specific constraints:
The operator only executes predefined operations through smart contracts, without knowledge of the underlying transaction content at the time of registration, ensuring that its actions remain limited, predictable, and verifiable.
Users create transactions through predefined smart contracts, which ensures consistent interaction with the platform and protects against unintended behavior or execution failures.
The data warehouse D is responsible for handling user requests to register transaction hash values, publishing the original transaction content to after the corresponding segment has been finalized, and providing mechanisms such as anonymous uploading and delayed decryption to ensure confidentiality until disclosure.
The auditor A acts as a neutral third party, with access to all necessary information from and to resolve disputes and detect misconduct through verifiable evidence.
5. Discussion: Limitations and Future Work
While the proposed framework presents a robust and scalable approach to preventing operator abuse and enabling verifiable transaction processing, several limitations and open issues remain that warrant further investigation.
First, a fundamental limitation of the proposed method lies in the requirement that all permissible operations on the platform be encoded in advance as predefined smart contracts. While this ensures strict enforcement and transparency, it also introduces challenges in practice. Defining all relevant operations upfront may not be feasible for complex or rapidly evolving platforms. As business logic changes or new types of transactions are introduced, the system must support timely updates of smart contracts, while maintaining consistency, security, and auditability. Future research should explore mechanisms for managing contract evolution, including versioning, upgrade policies, and governance frameworks that allow controlled modification, without undermining trust.
Second, operational rules are typically authored by the platform operator or their commissioned experts, which raises concerns about fairness and legitimacy. While minor issues may be corrected post-launch, platforms intentionally designed to mislead users must be identified beforehand. In this study, we suggested oversight by neutral experts; however, such entities must not only be technically competent but also empowered to prevent or suspend harmful platforms. Future research should explore governance mechanisms for such oversight authorities.
Third, while users are assumed to be capable of verifying the logical and temporal independence of their transactions, mistakes may occur, leading to invalid transactions. Developing tools or user interfaces that support dependency analysis or provide transaction feedback could improve usability and reduce errors, especially for non-expert users.
Fourth, although the dual-chain architecture ensures that transaction content remains hidden from the platform operator until finalization, it introduces additional latency between the time of hash registration and the moment of full transaction execution. In time-sensitive applications such as financial settlement or interactive marketplaces, this delay may degrade system responsiveness. However, once the corresponding segment is finalized and anchored to the reference chain , the execution of each transaction can proceed quickly within the private or consortium-based platform chain. Since all transactions are predefined smart contract invocations with deterministic logic and bounded input sizes, their execution latency is predictable and can be kept low when executed on sufficiently fast computing infrastructure. To mitigate this delay, the choice of reference chain is crucial. A chain with short inter-block intervals allows more frequent anchoring and faster segment finalization. Future deployments may benefit from using high-throughput blockchains with fast consensus cycles, or from designing a dedicated reference chain that aggregates multiple sidechains, while ensuring stable and predictable anchoring.
Fifth, the auditing mechanism depends on the presence of a neutral and trusted entity A. While this role is clearly defined and the verification process is based on publicly available on-chain data, the governance and accountability of A require further institutional support. In practical terms, A should operate within a legally enforceable framework, whether contractual or regulatory in nature, that explicitly outlines its responsibilities, grants it the authority to conduct impartial validation, and imposes accountability for negligence or misconduct. By assigning legal responsibility in this way, the framework ensures that A not only operates transparently but also reliably, with consequences that are enforceable in the event of failure. To reinforce this legal foundation, technical measures can serve as complementary safeguards that enhance the verifiability of A’s actions. For instance, publicly auditable logs, reproducible verification procedures, and fallback mechanisms such as multi-party or community-based dispute resolution can increase transparency and resilience. However, these technical features are most effective when embedded within a governance structure that prioritizes real-world accountability.
Sixth, although the framework supports anonymous submission of transaction hashes and encrypted content, the practical burden of this may lead some users to submit unencrypted data to D, enabling potential collusion with . This could allow censorship or manipulation based on transaction content. Future research should consider user-friendly submission methods—such as automated encryption tools, independent relayers, or decentralized mixers—that reduce reliance on the honesty of D and .
Seventh, in dynamic business environments, it may become necessary to introduce new operational rules or revise existing ones. In such cases, it is the responsibility of the platform manager
to manage the registration of updated smart contracts, either by submitting new ones or replacing deprecated versions. As noted in
Section 3.2, any contract submitted for registration should be reviewed by a neutral external expert to ensure platform reliability and user trust. When the economic benefits of platform operation are shared among multiple stakeholders, a governance mechanism may be required, to determine which contracts are adopted. For example, voting weights based on a predefined profit distribution ratio can be used to reflect stakeholder influence, while general users without economic stakes would not participate in such decisions. Although this model introduces additional complexity, it offers a flexible framework for contract-level adaptability and is proposed as a direction for future enhancement.
Another important limitation is the absence of an empirical or simulation-based evaluation. While this study focused on the architectural and security design of the framework, future work should include a proof-of-concept implementation and performance benchmarking under real-world conditions. Such efforts will help quantify the anchoring latency, transaction throughput, and operational costs, and will provide essential insights into the practical feasibility, scalability, and optimization potential of the proposed method.
In summary, while the proposed method lays a strong foundation for secure and transparent transaction execution in decentralized platforms, further research is needed to improve the usability, reduce latency, evolve smart contracts, enforce oversight, minimize trust dependencies, and validate real-world performance.
6. Conclusions
This study proposed a sidechain-based framework for building efficient, secure, and transparent digital asset trading platforms. The core idea lies in introducing a dedicated platform chain as a private or consortium blockchain functioning as a sidechain to a well-established mainchain . This design allows the platform to inherit the stability and trustworthiness of the mainchain, without requiring any modifications to it, thereby significantly reducing the costs typically associated with establishing high levels of security and reliability.
Moreover, by adopting a private or consortium model for the platform chain, the system benefits from faster consensus and transaction processing, customized blockchain configurations tailored to the specific needs of the platform, and greater adaptability to rapidly evolving business requirements. These characteristics make the proposed framework especially well-suited for dynamic digital asset trading environments that demand both performance and flexibility, alongside trust and verifiability.
Controlling the behavior of the platform operator is a central concern in this study, particularly given the semi-centralized nature of private- or consortium-based blockchains. To ensure transparency and prevent operator misconduct, the proposed method introduces a dual-sidechain architecture. In this structure, only the hash values of transactions are initially recorded in , while the full transaction contents are disclosed and executed later in a paired dual platform chain , after the corresponding segment of is finalized and anchored to .
This architecture ensures that the operator cannot make decisions based on transaction content at the time of registration, effectively mitigating risks such as semantic-based censorship or favoritism. Once anchored, all registered hash values become irreversibly bound to their corresponding transactions when disclosed in , enabling transparent auditing.
All operations are executed according to predefined smart contracts, which strictly constrain the range of actions that the platform operator can perform. Rather than minimizing centralized control in a general sense, the system explicitly limits operator authority by ensuring that all behaviors adhere to the logic encoded in immutable contracts. This safeguard is especially critical in private- or consortium-based settings, where the operator (e.g., ) would otherwise retain significant control over the platform. Through this approach, the framework effectively mitigates the risk of arbitrary or self-serving actions by the operator.
To enhance scalability and efficiency, the method employs Merkle tree constructions that allow multiple transactions to be aggregated into a single root hash for registration. The framework defines the conditions under which such aggregation is valid, particularly when the transactions are logically and temporally independent. Since verifying such independence at the system level is inherently difficult, the framework delegates this responsibility to users. They are best positioned to judge whether their transaction depends on the outcome of another. To support this process, users are instructed to reference only transactions that have already been confirmed and finalized on the chain.
The responsibility for managing transaction dependencies is explicitly assigned to users at the time of transaction creation. They must ensure that their transactions do not rely on the outcomes of other transactions that have not yet been finalized. This rule is essential to preserve the integrity of the system and applies regardless of whether transactions are registered individually or aggregated using Merkle trees.
In addition, just as the platform operator is restricted to predefined smart contracts, users are also required to only create transactions through designated smart contract interfaces. This constraint prevents users from interfering with platform operations through arbitrary or unauthorized actions. Furthermore, because transaction creation is guided by smart contracts, the system can maintain an internal execution state that allows it to roll back or safely recover from partial executions in the event of a failure. This mechanism provides an additional layer of protection for users by ensuring transactional consistency and recoverability when problems occur.
A detailed threat analysis confirmed the robustness and practical soundness of the proposed framework. Potential vulnerabilities, including operator manipulation, user misconduct, data warehouse abuse, and auditor failure, were carefully examined and addressed through specific safeguards. These included hash-based transaction commitment, dual-chain disclosure, anonymous uploading, deterministic smart contract execution, and transparent auditing mechanisms. The system design constrains the actions of all participants and distributes responsibilities in a way that reduces reliance on trust. Overall, the proposed framework offers a reliable and resilient solution for secure, transparent, and tamper-resistant transaction processing in permissioned blockchain environments.
Despite its strengths, the proposed framework presents several open challenges. These include the difficulty of predefining all platform operations as smart contracts, the need for enforceable oversight prior to platform launch, and the burden on users in ensuring transaction independence and secure submission. Potential collusion among system actors also highlights the importance of practical mechanisms that preserve transparency and confidentiality. Future work should address these limitations to support reliable implementation and broader applicability.
In conclusion, this architecture offers a practical and cost-effective solution for digital asset trading platforms in semi-centralized environments. It combines mainchain-level trust with platform-level efficiency and enforces bounded operator control through smart contracts. By aligning transparency, automation, and role accountability, the system provides a solid foundation for scalable digital asset management and future innovations in decentralized platform design.