Defense Mechanism of PV-Powered Energy Islands Against Cyber-Attacks Utilizing Supervised Machine Learning
Abstract
1. Introduction
Relevant Literature
- (1)
- An early warning detection system has been established using the ANN-based SML algorithm, which enhances system reliability and enables rapid intervention against cyber threats.
- (2)
- The proposed ANN structure has attained satisfactory accuracies with convenient training datasets. While ANN-I is tasked with detecting cyber threats, the other ANN-II supports the subsequent demand for delivered power, leading to a complementary scheme.
- (3)
- Within the scope of this study, it is demonstrated that ANN-based SML algorithms provide faster and more effective analysis mechanisms than traditional methods, asserting their strong resistance to emerging threats through continuous learning and adaptation.
- (4)
- Future studies should focus on strengthening the resilience of critical infrastructures, such as energy systems, by emphasizing early cyber-attack detection.
- (5)
- Consequently, the study assesses measures to counter cyber-attacks in PV-supported microgrids, revealing that integrating ANNs and anomaly detection algorithms can significantly aid in early detection and prevention processes.
- (6)
- It is concluded that ANN-based solutions should be integrated with additional security layers and that human oversight is crucial for improving the accuracy of these systems.
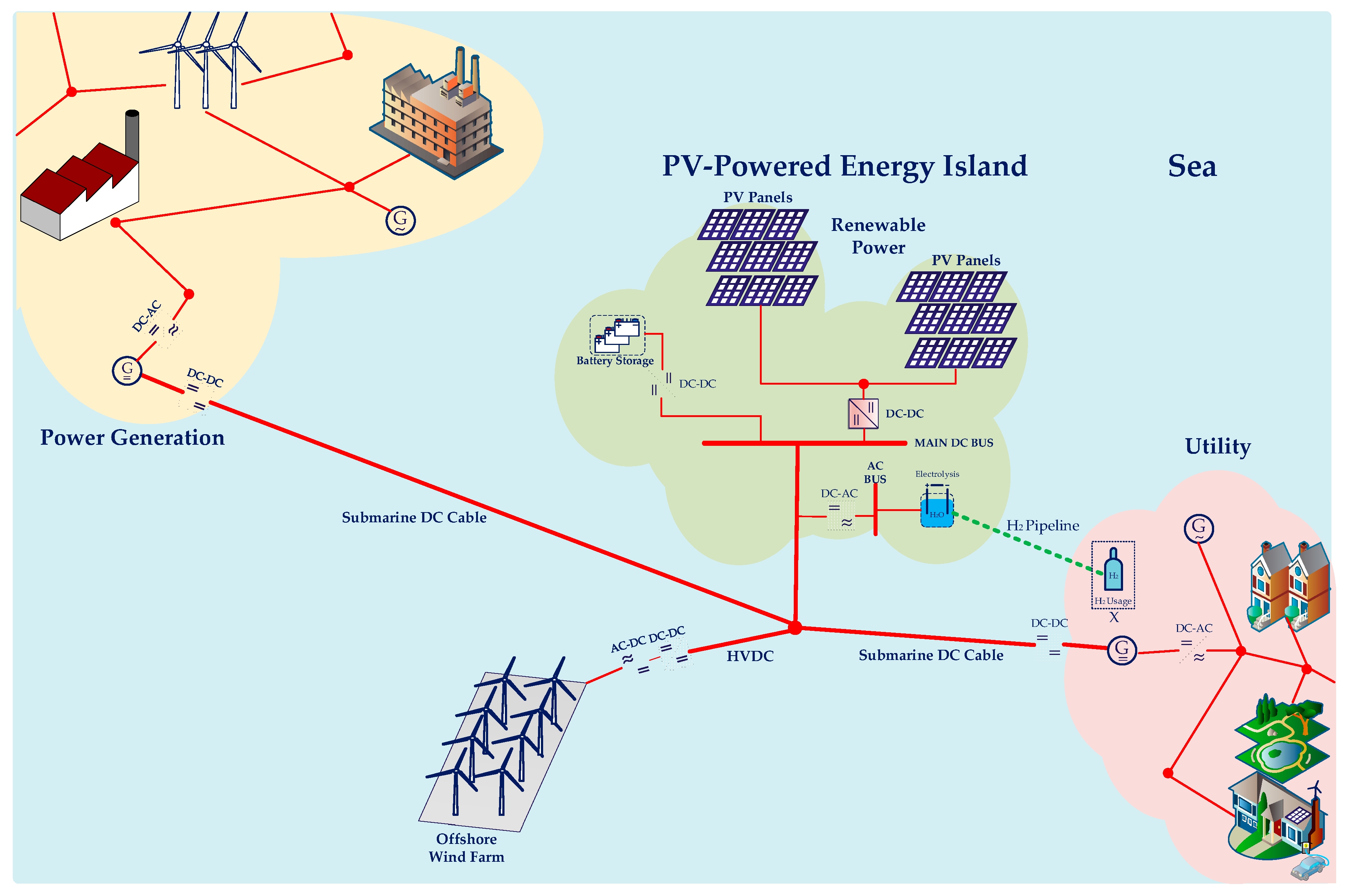
2. Description of PV-Powered Energy Island Structure
3. Detection of Cyber-Attacks with Supervised Machine Learning-Artificial Neural Networks
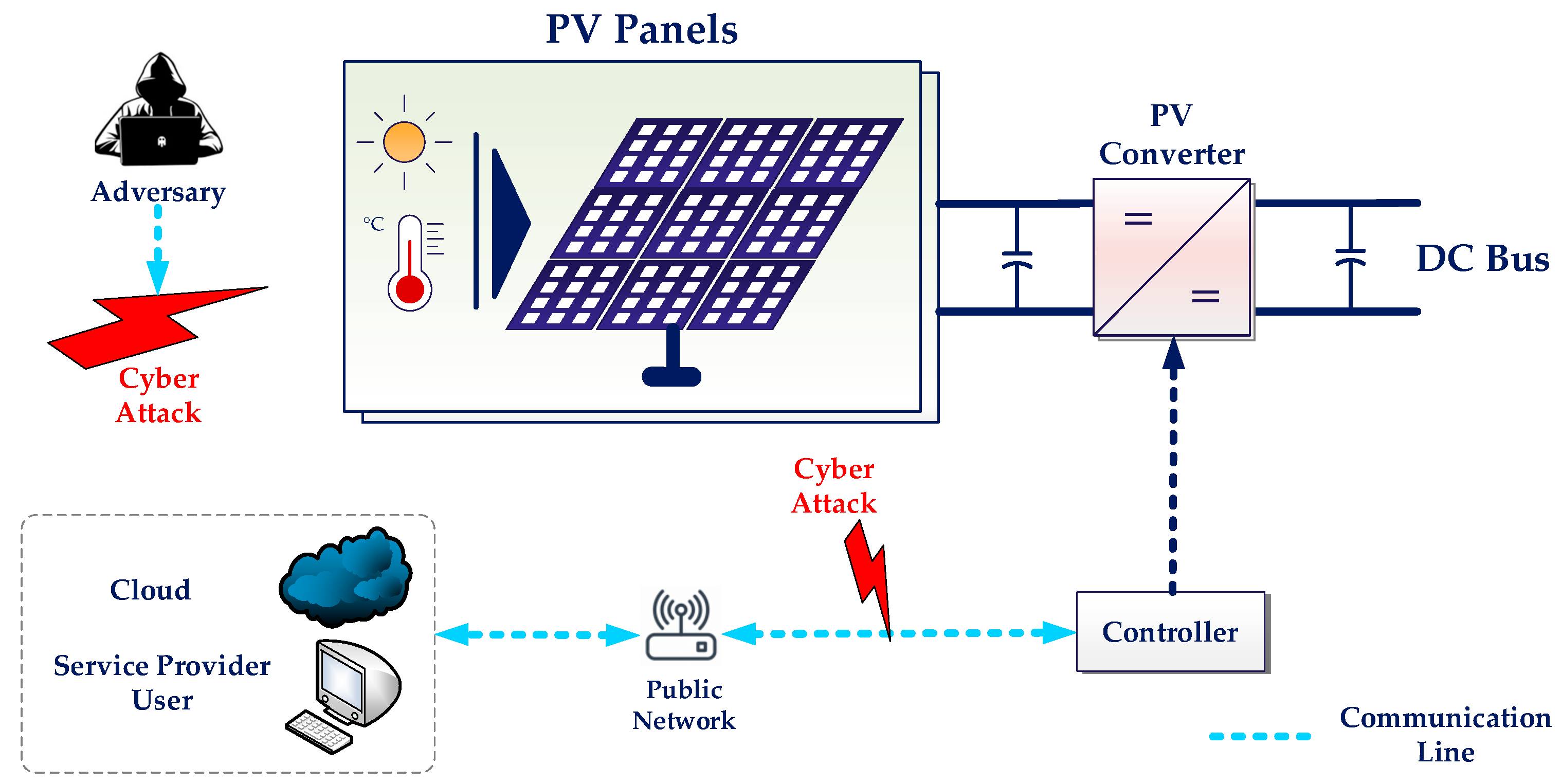
3.1. Cyber-Physical PV-Powered Energy Island Structure
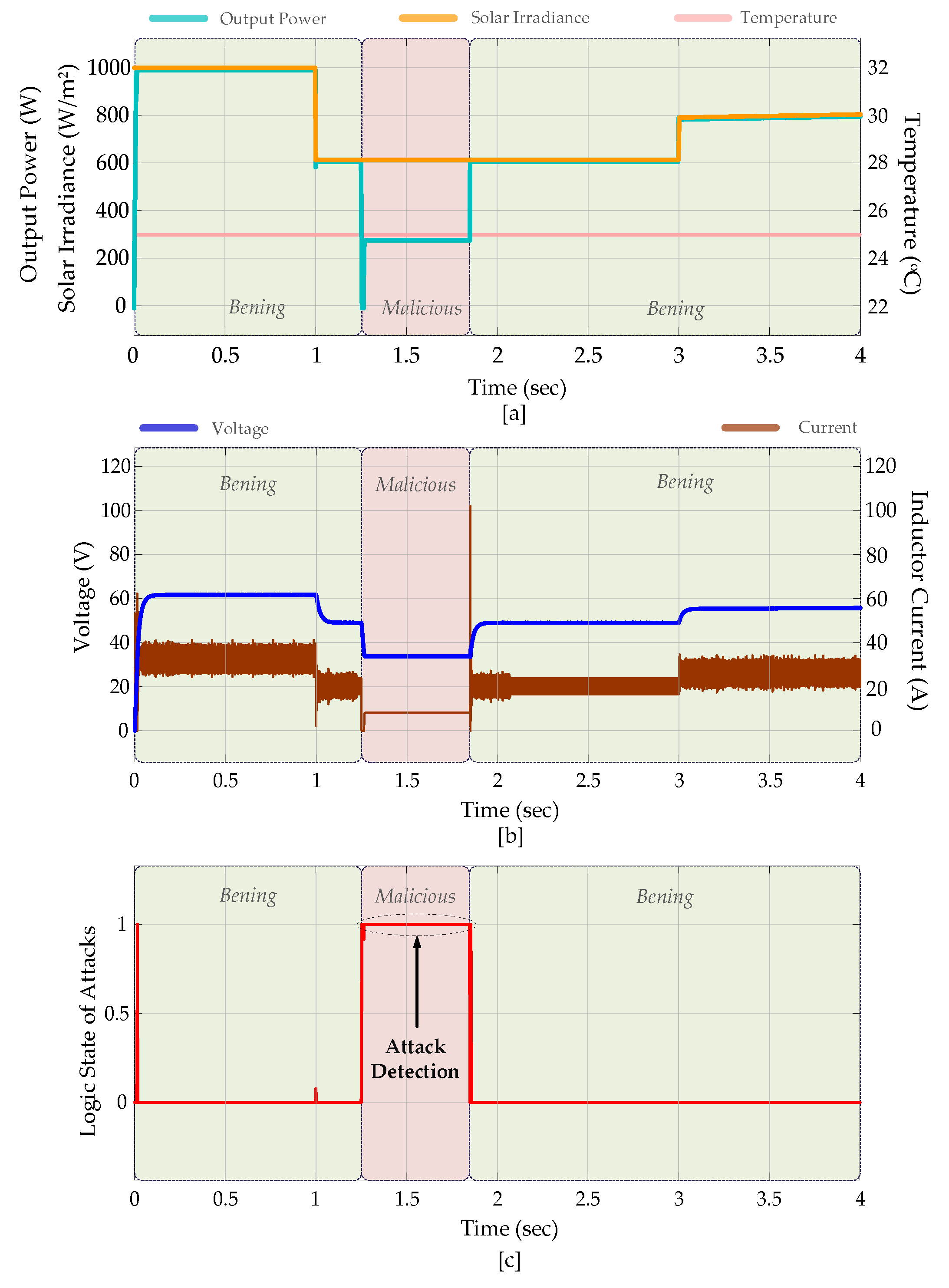
- ✓ DoS or distributed denial of service (DDoS) attacks inundate the controller and management systems with large amounts of fake data or traffic, overloading and crashing the system. If a DoS/DDoS attack occurs in an EI, control mechanisms may be incapacitated, disrupting energy distribution.
- ✓ MitM attacks target communication between the controller and the central management unit. Cyber attackers can interrupt data flow, send deceptive control signals, or modify information. As a result of such an attack, energy production and consumption may be mismanaged, leading to overload or energy outages.
- ✓ In hijacking attacks, the adversary can intercept data, alter it, or inject fake commands by acting as a bridge between the EI’s control devices and the central energy management, as seen in Figure 2. For better illustration, false signals can be sent that reduce the production level of PV panels or overload the microgrid.
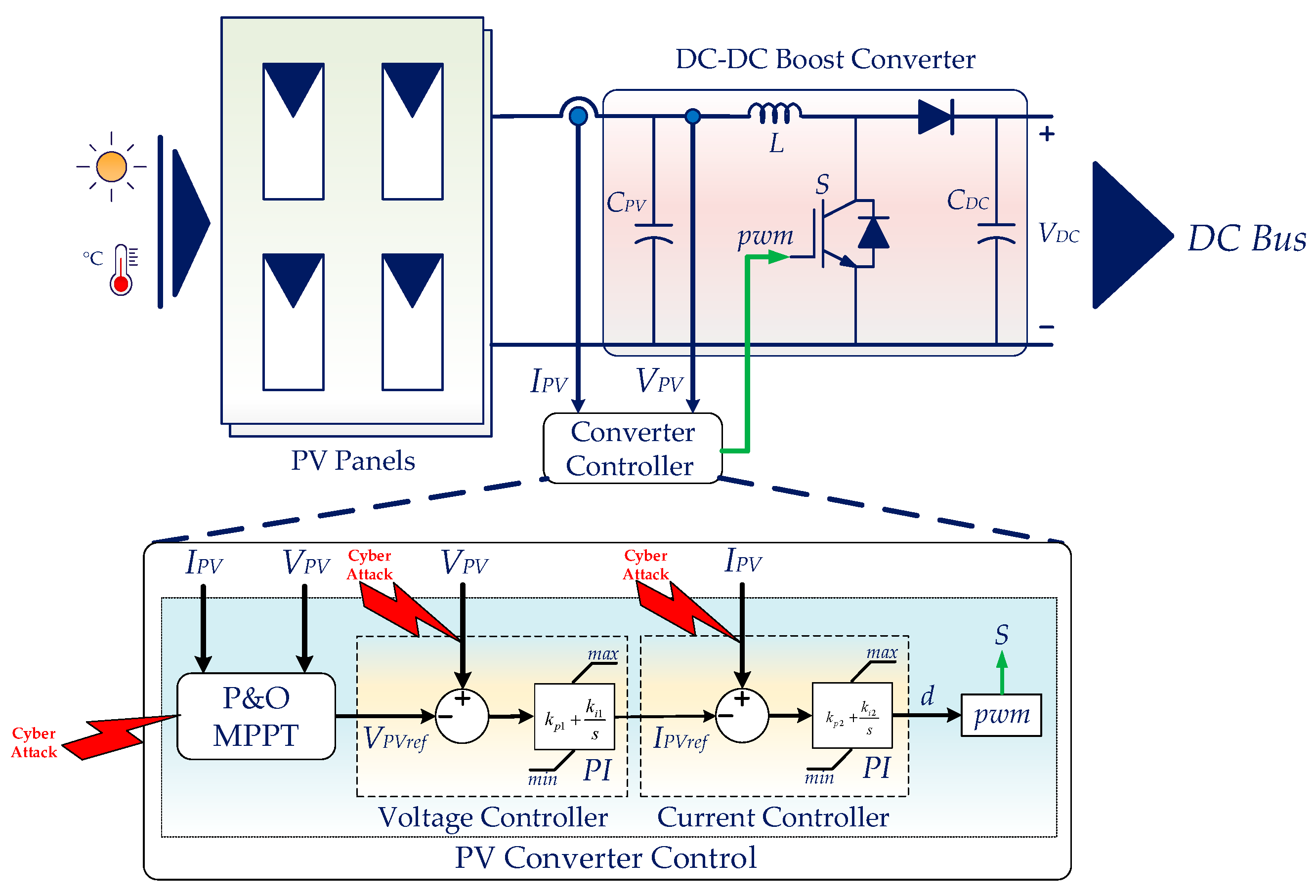
- ✓ In FDI attacks, attackers inject misleading sensor data into the system, leading the system to make incorrect decisions. For instance, sending fake voltage and frequency data can misdirect energy production or storage, resulting in system instability, overload, or equipment failures, as shown in Figure 3.
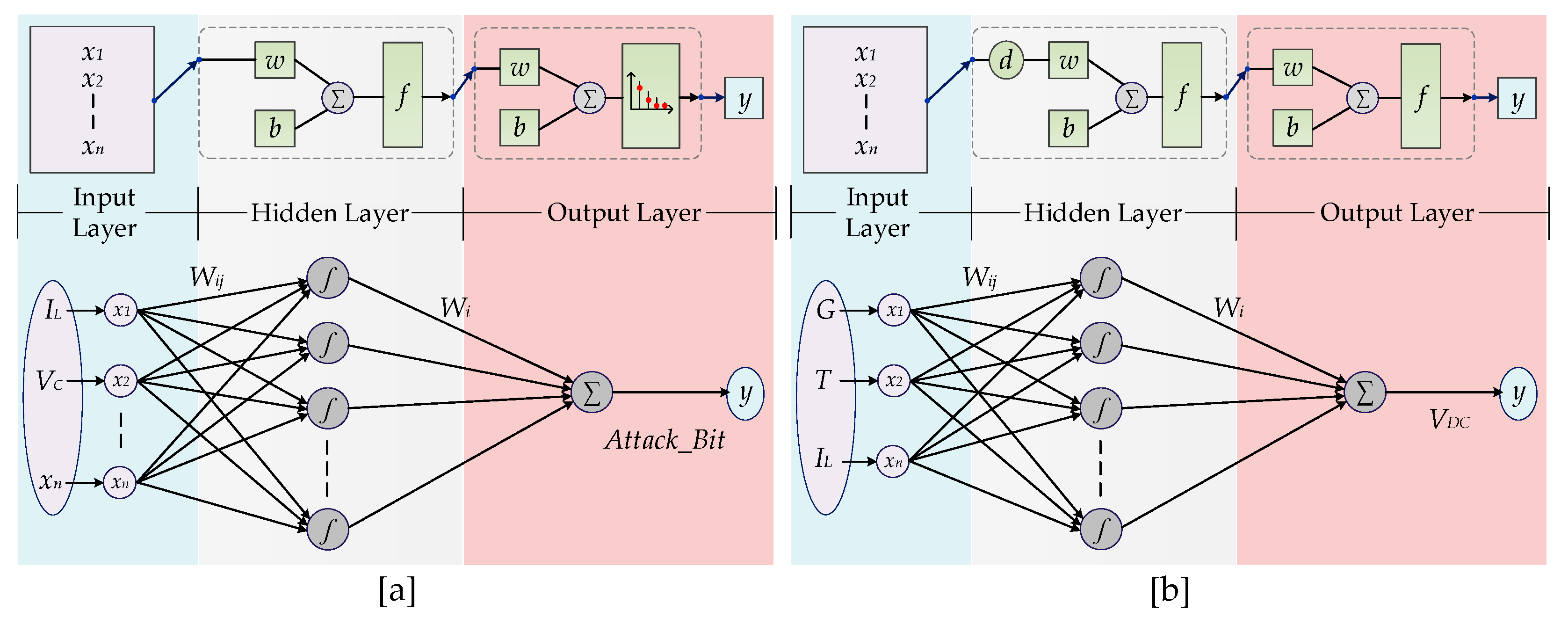
3.2. Deployment of Supervised Machine Learning-Based Artificial Neural Networks
| Algorithm 1 Pseudo-code flow of the executed ANN structures |
| Input: [xn: VC, IL, dVC/dt, dIL/dt, G, T] |
| Output: Weighting factors of cyber-attack situation [Attack_Bit, VDC] |
| 1: Initialize network_parameters (wt,ij, bk,j) with proper values |
| #Training Phase 2: For epoch in range(num_epochs): For each training_sample (x, y) in training_data: For each layer j in the network: ht,j = wt,ij * xt,i + bk,j rt,j = fhidden_activation_function(ht,j) |
| #Error Calculation-Loss Function 3: Loss = compute_loss(Attack_Bit, VDC [output_layer], y) |
| #Backpropagation 4: Compute gradients of loss with wt,ij and bk,j 5: Update new w and b through gradient descent |
| #Test Phase 6: For each test_sample x in test_data: For each layer j in the network: ht,j = wt,ij * xt,i + bk,j rt,j = factivation_function(ht,j) 7: Attack_Bit = factivation_function(wt,ij, rt,j, by) Estimated_output =Attack_Bit, VDC [output_layer] 8: Return trained_model |
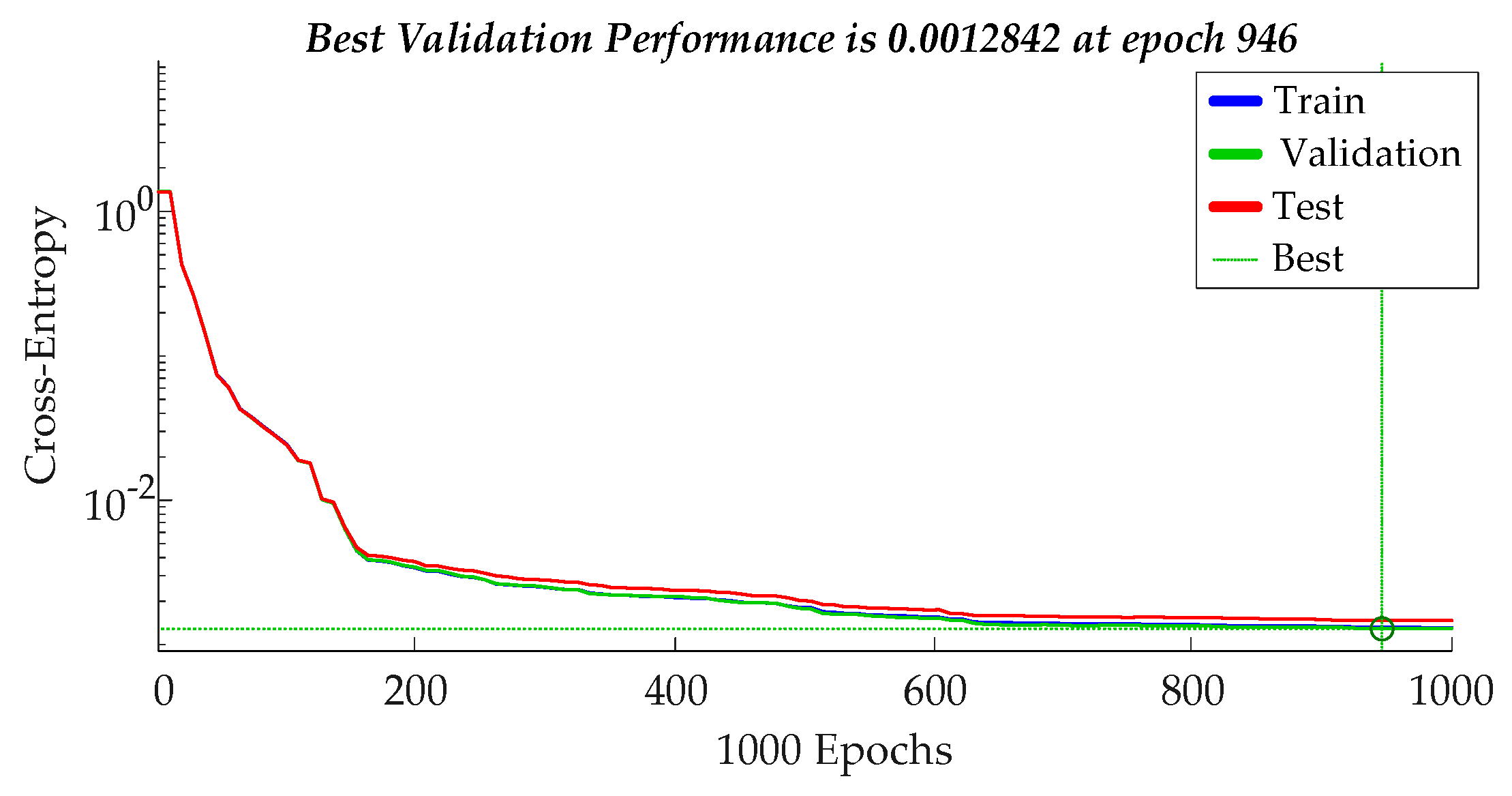
| 9: Calculate the Cross-Entropy after training for ANN-I 10: Calculate the mean squared error (MSE) after training for ANN-II |
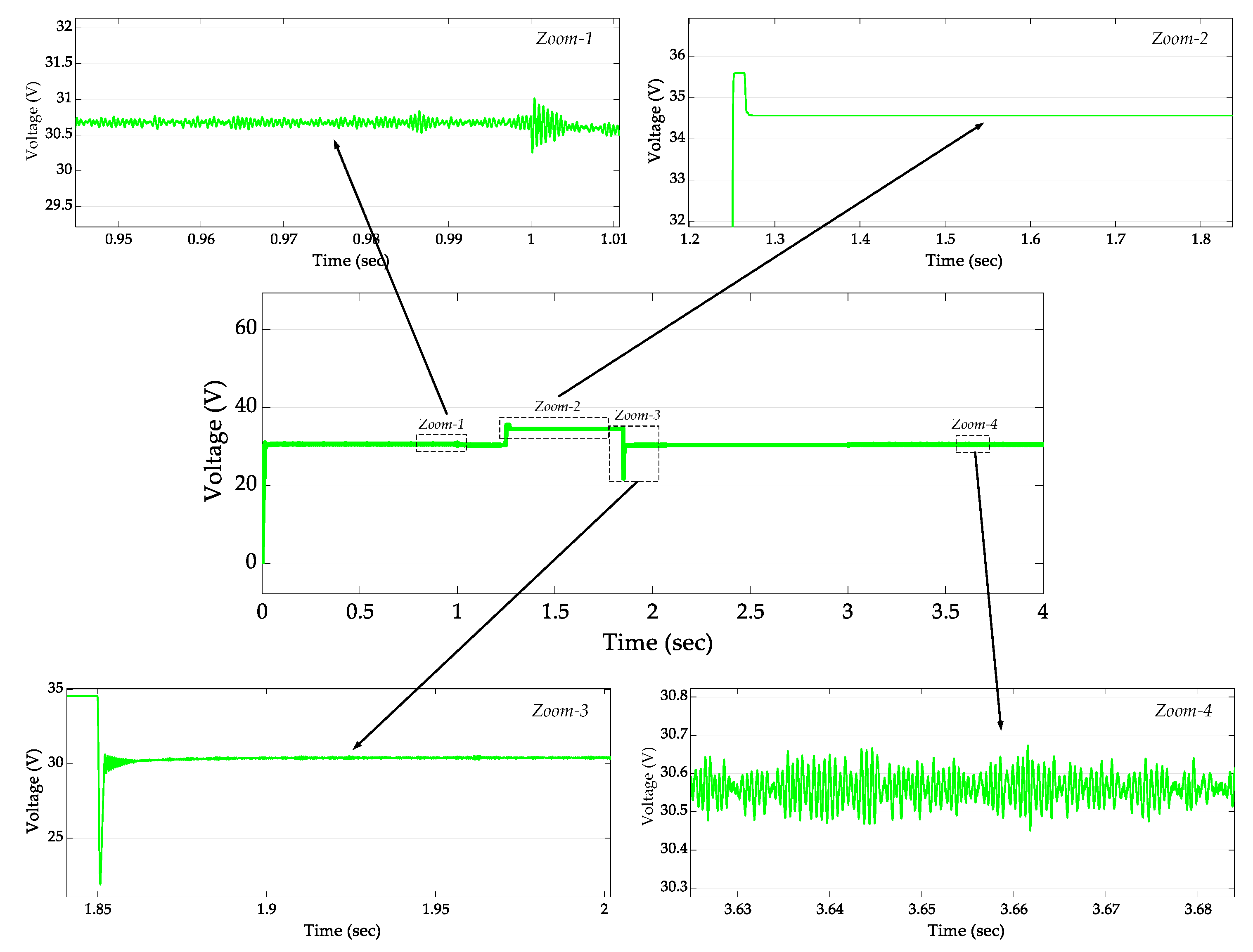
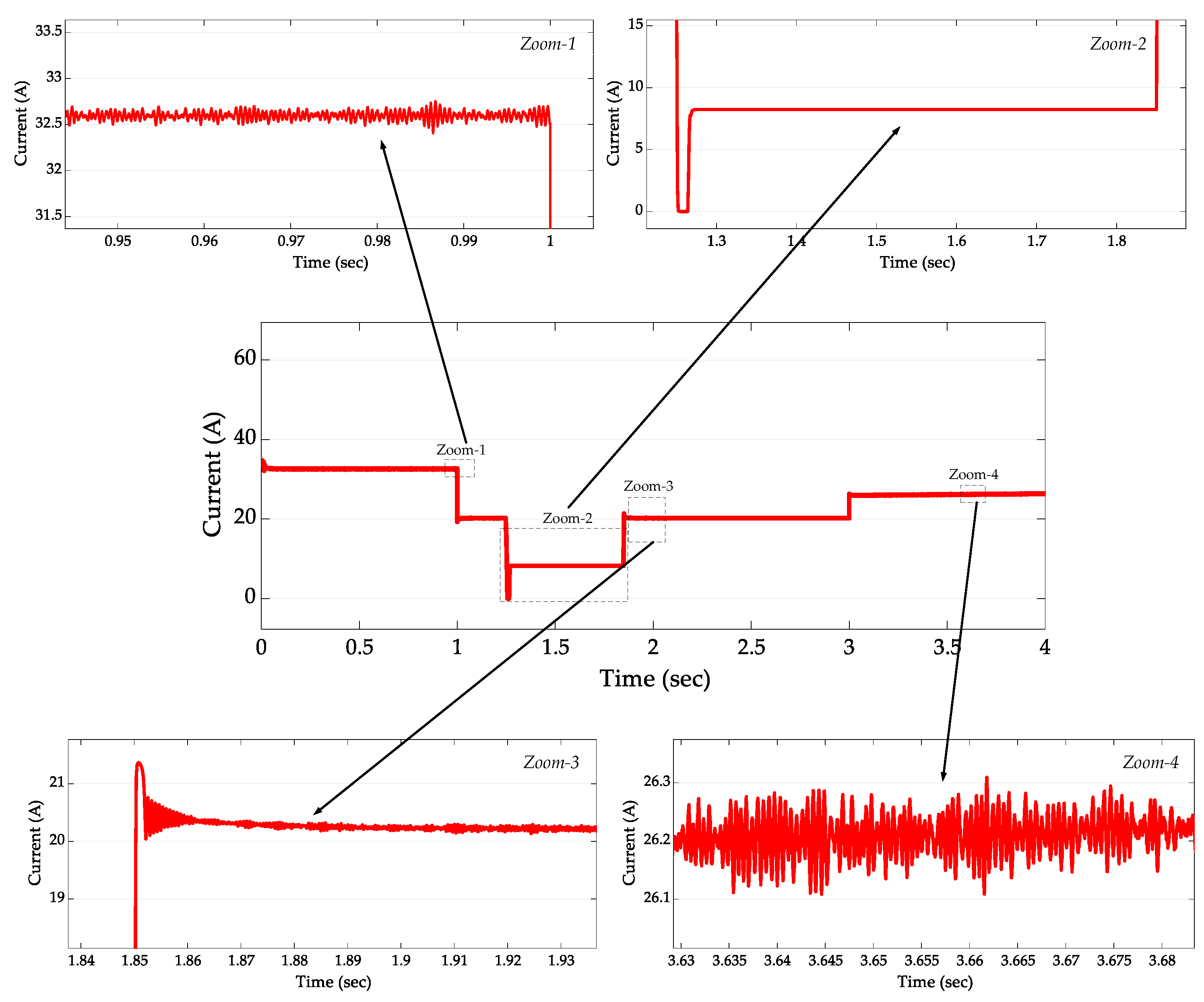
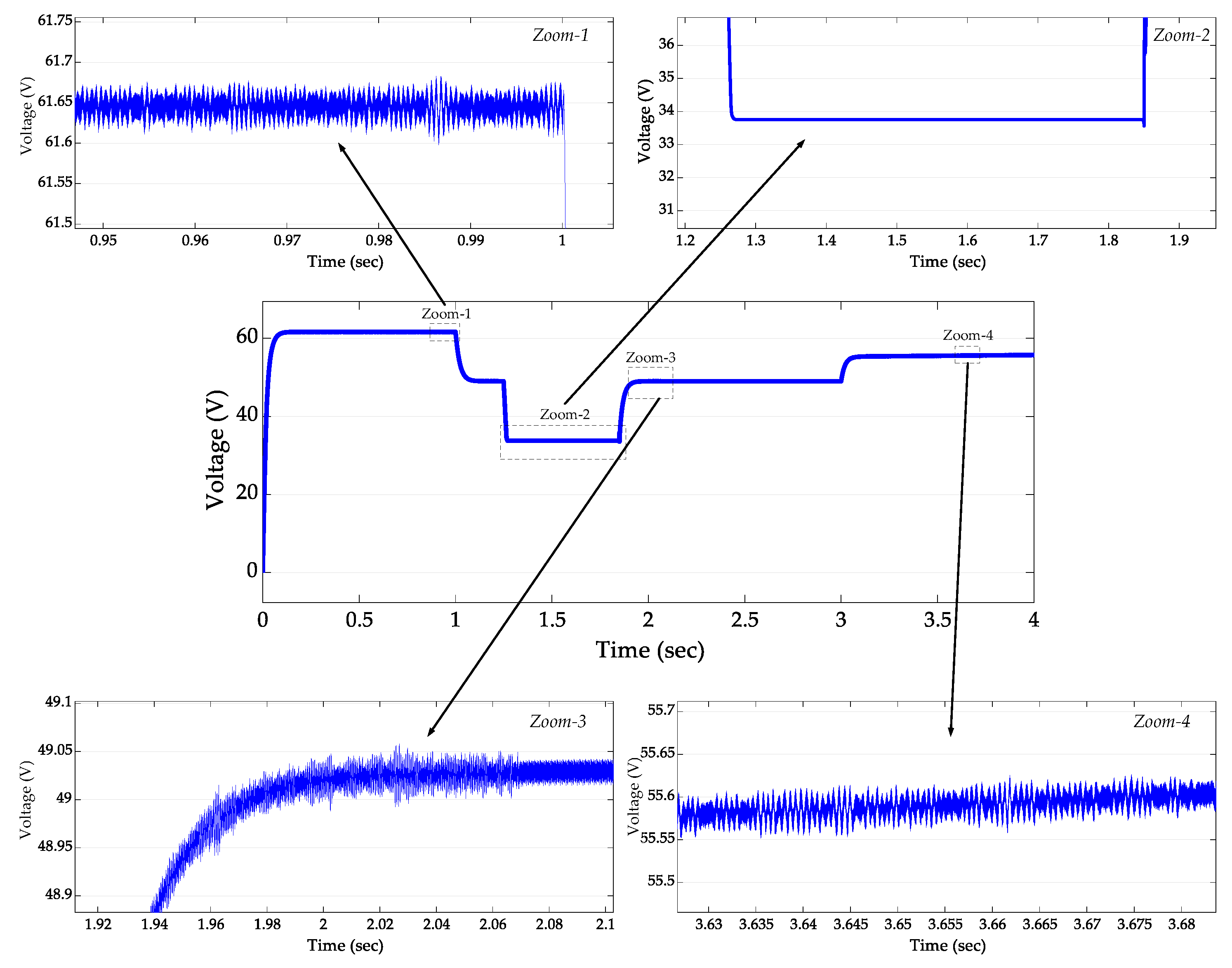
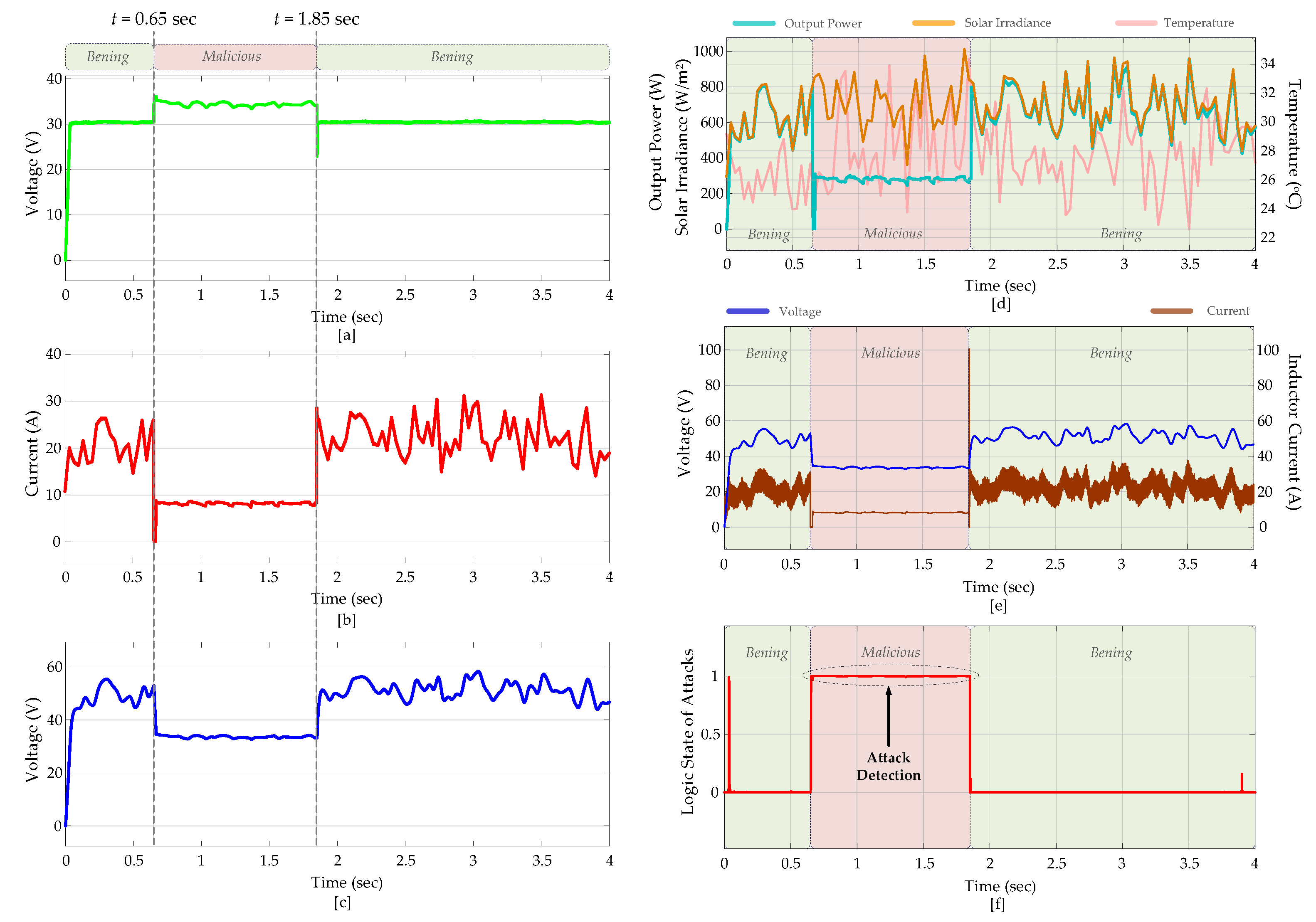
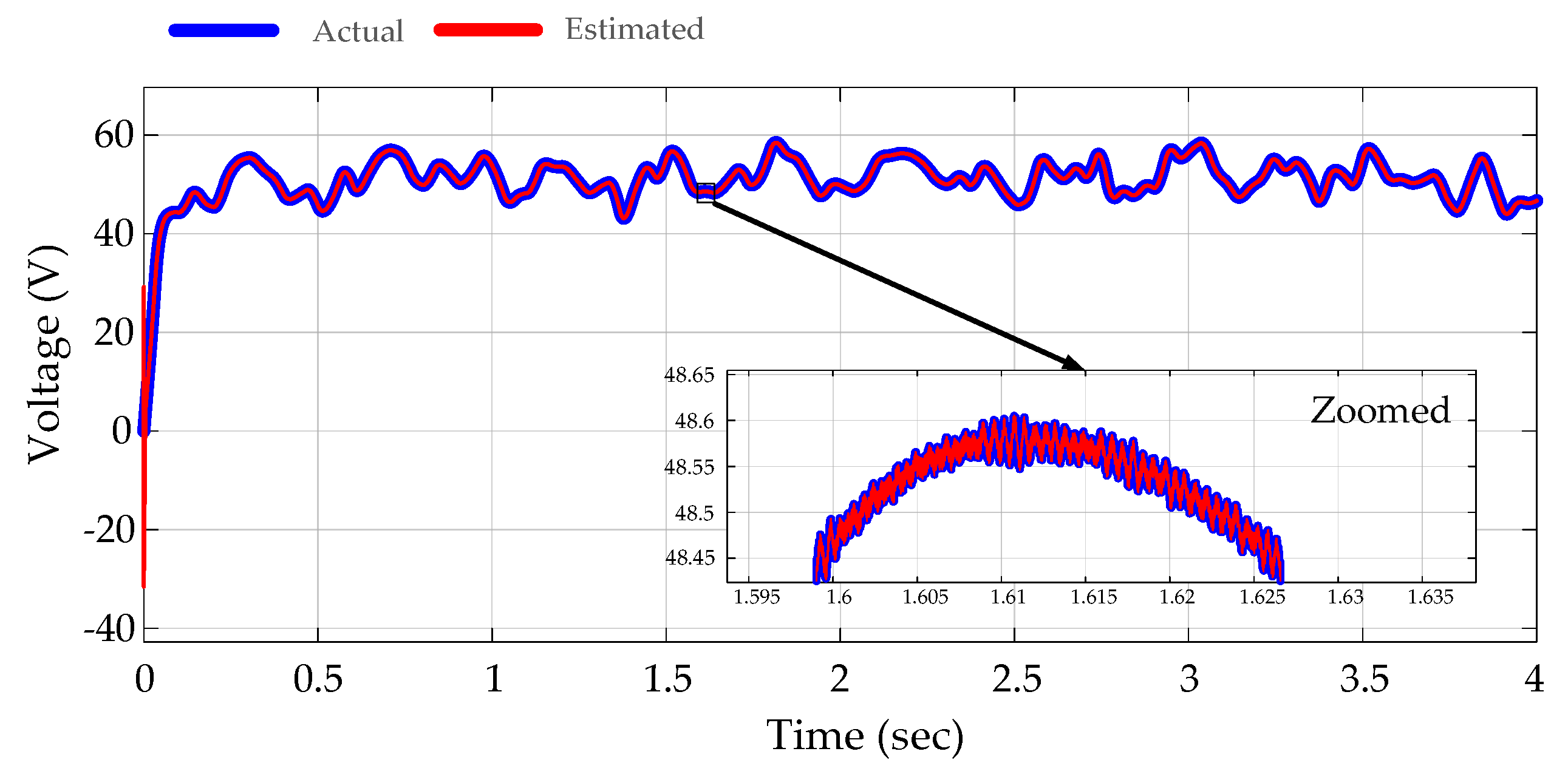
4. Operation Results, Verification, and Analysis
5. Discussion and Future Outlook
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Kuang, Y.; Zhang, Y.; Zhou, B.; Li, C.; Cao, Y.; Li, L.; Zeng, L. A review of renewable energy utilization in islands. Renew. Sustain. Energy Rev. 2016, 59, 504–513. [Google Scholar] [CrossRef]
- Akpolat, A.N.; Dursun, E.; Yang, Y. Performance analysis of a PEMFC-based grid-connected distributed generation system. Appl. Sci. 2023, 13, 3521. [Google Scholar] [CrossRef]
- Xu, Y.; Ji, M.; Klemeš, J.J.; Tao, H.; Zhu, B.; Varbanov, P.S.; Yuan, M.; Wang, B. Optimal renewable energy export strategies of islands: Hydrogen or electricity? Energy 2023, 269, 126750. [Google Scholar] [CrossRef]
- Yin, S.; Rodriguez-Andina, J.J.; Jiang, Y. Real-time monitoring and control of industrial cyber-physical systems: With integrated plant-wide monitoring and control framework. IEEE Ind. Electron. Mag. 2019, 13, 38–47. [Google Scholar] [CrossRef]
- Habibi, M.R.; Baghaee, H.R.; Dragičević, T.; Blaabjerg, F. Detection of false data injection cyber-attacks in DC microgrids based on recurrent neural networks. IEEE J. Emerg. Sel. Top. Power Electron. 2020, 9, 5294–5310. [Google Scholar] [CrossRef]
- Kaewnukultorn, T.; Sepúlveda-Mora, S.B.; Broadwater, R.; Zhu, D.; Tsoutsos, N.G.; Hegedus, S. Smart PV Inverter Cyberattack Detection Using Hardware-in-the-Loop Test Facility. IEEE Access 2023, 11, 90766–90779. [Google Scholar] [CrossRef]
- Rajkumar, Y.; Santhosh Kumar, S.V.N. A comprehensive survey on communication techniques for the realization of intelligent transportation systems in IoT based smart cities. Peer-to-Peer Netw. Appl. 2024, 17, 1263–1308. [Google Scholar] [CrossRef]
- AlZubi, A.A.; Al-Maitah, M.; Alarifi, A. Cyber-attack detection in healthcare using cyber-physical system and machine learning techniques. Soft Comput. 2021, 25, 12319–12332. [Google Scholar] [CrossRef]
- Yildiz, S.; Yildirim, B.; Ozdemir, M.T. Enhancing load frequency control and cybersecurity in renewable energy microgrids: A fuel cell-based solution with non-integer control under cyber-attack. Int. J. Hydrogen Energy 2024, 75, 438–449. [Google Scholar] [CrossRef]
- Khan, A.A.; Beg, O.A.; Alamaniotis, M.; Ahmed, S. Intelligent anomaly identification in cyber-physical inverter-based systems. Electr. Power Syst. Res. 2021, 193, 107024. [Google Scholar] [CrossRef]
- Bhusal, N.; Gautam, M.; Benidris, M. Detection of cyber attacks on voltage regulation in distribution systems using machine learning. IEEE Access 2021, 9, 40402–40416. [Google Scholar] [CrossRef]
- Qiu, W.; Sun, K.; Li, K.J.; Li, Y.; Duan, J.; Zhu, K. Cyber-attack detection: Modeling and roof-PV generation system defending. IEEE Trans. Ind. Appl. 2022, 59, 160–168. [Google Scholar] [CrossRef]
- Scruggs, D.; Timilsina, L.; Papari, B.; Arsalan, A.; Muriithi, G.; Ozkan, G.; Edrington, C.S. Neural Network-based Cyber-Threat Detection Strategy in Four Motor-Drive Autonomous Electric Vehicles. IEEE Access 2024, 12, 124220–124230. [Google Scholar] [CrossRef]
- Călin, A.M.; Cotfas, D.T.; Cotfas, P.A. A Review of Smart Photovoltaic Systems Which Are Using Remote-Control, AI, and Cybersecurity Approaches. Appl. Sci. 2024, 14, 7838. [Google Scholar] [CrossRef]
- Du, D.; Zhu, M.; Li, X.; Fei, M.; Bu, S.; Wu, L.; Li, K. A review on cybersecurity analysis, attack detection, and attack defense methods in cyber-physical power systems. J. Mod. Power Syst. Clean Energy 2022, 11, 727–743. [Google Scholar] [CrossRef]
- Yang, B.; Wu, S.; Hu, K.; Ye, J.; Song, W.; Ma, P.; Shi, J.; Liu, P. Enhanced cyber-attack detection in intelligent motor drives: A transfer learning approach with convolutional neural networks. IEEE J. Emerg. Sel. Top. Ind. Electron. 2023, 5, 710–719. [Google Scholar] [CrossRef]
- Ortega-Fernandez, I.; Liberati, F. A review of denial of service attack and mitigation in the smart grid using reinforcement learning. Energies 2023, 16, 635. [Google Scholar] [CrossRef]
- Selim, A.; Zhao, J.; Ding, F.; Miao, F.; Park, S.Y. Adaptive deep reinforcement learning algorithm for distribution system cyber attack defense with high penetration of DERs. IEEE Trans. Smart Grid 2023, 15, 4077–4089. [Google Scholar] [CrossRef]
- Chen, P.; Liu, S.; Chen, B.; Yu, L. Multi-agent reinforcement learning for decentralized resilient secondary control of energy storage systems against DoS attacks. IEEE Trans. Smart Grid 2022, 13, 1739–1750. [Google Scholar] [CrossRef]
- Takiddin, A.; Rath, S.; Ismail, M.; Sahoo, S. Data-driven detection of stealth cyber-attacks in dc microgrids. IEEE Syst. J. 2022, 16, 6097–6106. [Google Scholar] [CrossRef]
- Mao, J.; Zhang, M.; Xu, Q. CNN and LSTM based Data-driven Cyberattack Detection for Grid-connected PV Inverter. In Proceedings of the 2022 IEEE 17th International Conference on Control & Automation (ICCA), Naples, Italy, 27–30 June 2022; pp. 704–709. [Google Scholar]
- Ye, J.; Giani, A.; Elasser, A.; Mazumder, S.; Farnell, C.; Mantooth, H.A.; Kim, T.; Liu, J.; Chen, B.; Seo, G.-S.; et al. A review of cyber–physical security for photovoltaic systems. IEEE J. Emerg. Sel. Top. Power Electron. 2021, 10, 4879–4901. [Google Scholar] [CrossRef]
- Galbraith, K. Solar Panels are Vanishing, Only to Reappear on the Internet. Available online: https://www.nytimes.com/2008/09/24/technology/24solar.html (accessed on 16 September 2024).
- Rajkumar, V.S.; Stefanov, A.; Presekal, A.; Palensky, P.; Torres, J.L.R. Cyber attacks on power grids: Causes and propagation of cascading failures. IEEE Access 2023, 11, 103154–103176. [Google Scholar] [CrossRef]
- Mtukushe, N.; Onaolapo, A.K.; Aluko, A.; Dorrell, D.G. Review of cyberattack implementation, detection, and mitigation methods in cyber-physical systems. Energies 2023, 16, 5206. [Google Scholar] [CrossRef]
- Liang, G.; Weller, S.R.; Zhao, J.; Luo, F.; Dong, Z.Y. The 2015 Ukraine blackout: Implications for false data injection attacks. IEEE Trans. Power Syst. 2017, 32, 3317–3318. [Google Scholar] [CrossRef]
- Rajkumar, Y.; Santhosh Kumar, S.V.N. A Dickson polynomial based group key agreement authentication scheme for ensuring conditional privacy preservation and traceability in VANETs. Sci. Rep. 2025, 15, 6211. [Google Scholar] [CrossRef]
- Shees, A.; Tariq, M.; Sarwat, A.I. Cybersecurity in Smart Grids: Detecting False Data Injection Attacks Utilizing Supervised Machine Learning Techniques. Energies 2024, 17, 5870. [Google Scholar] [CrossRef]
- Aghazadeh Ardebili, A.; Martella, C.; Longo, A.; Rucco, C.; Izzi, F.; Ficarella, A. IoT-Driven Resilience Monitoring: Case Study of a Cyber-Physical System. Appl. Sci. 2025, 15, 2092. [Google Scholar] [CrossRef]
- Khalid, M. Energy 4.0: AI-enabled digital transformation for sustainable power networks. Comput. Ind. Eng. 2024, 193, 110253. [Google Scholar] [CrossRef]
- Yaacoub, J.P.; Noura, H.; Azar, J.; Salman, O.; Chahine, K. Cybersecurity in Smart Renewable Energy Systems. In Proceedings of the 2024 International Wireless Communications and Mobile Computing (IWCMC), Ayia Napa, Cyprus, 27–31 May 2024; pp. 1534–1540. [Google Scholar]
- Hassan, G.F.; Ahmed, O.A.; Sallal, M. Evaluation of Deep Learning Techniques in PV Farm Cyber Attacks Detection. Electronics 2025, 14, 546. [Google Scholar] [CrossRef]
- Wang, W.; Harrou, F.; Bouyeddou, B.; Senouci, S.M.; Sun, Y. Cyber-attacks detection in industrial systems using artificial intelligence-driven methods. Int. J. Crit. Infrastruct. Prot. 2022, 38, 100542. [Google Scholar] [CrossRef]
- Paul, S.; Vijayshankar, S.; Macwan, R. Demystifying Cyberattacks: Potential for Securing Energy Systems With Explainable AI. In Proceedings of the 2024 International Conference on Computing, Networking and Communications (ICNC), Big Island, HI, USA, 19–22 February 2024; pp. 430–434. [Google Scholar]
- Sourav, S.; Biswas, P.P.; Chen, B.; Mashima, D. Detecting hidden attackers in photovoltaic systems using machine learning. In Proceedings of the 2022 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Singapore, 25–28 October 2022; pp. 360–366. [Google Scholar]
- Li, Q.; Li, F.; Zhang, J.; Ye, J.; Song, W.; Mantooth, A. Data-driven cyberattack detection for photovoltaic (PV) systems through analyzing micro-PMU data. In Proceedings of the 2020 IEEE Energy Conversion Congress and Exposition (ECCE), Detroit, MI, USA, 11–15 October 2020; pp. 431–436. [Google Scholar]
- Akpolat, A.N. Enhancing operational reliability for high penetration of green hydrogen production in energy islands: A power-to-X case study. Int. J. Hydrogen Energy 2025, in press, Corrected Proof. [Google Scholar] [CrossRef]
- Habibi, M.R.; Guerrero, J.M.; Vasquez, J.C. Artificial intelligence for cybersecurity monitoring of cyber-physical power electronic converters: A DC/DC power converter case study. Sci. Rep. 2024, 14, 22072. [Google Scholar] [CrossRef] [PubMed]
- Taher, M.A.; Iqbal, H.; Tariq, M.; Sarwat, A.I. Recurrent neural network-based sensor data attacks identification in distributed renewable energy-based DC microgrid. In Proceedings of the 2024 IEEE Texas Power and Energy Conference (TPEC), College Station, TX, USA, 12–13 February 2024; pp. 1–6. [Google Scholar]
- Suprabhath, K.S.; Prasad, M.V.S.; Madichetty, S.; Mishra, S. A deep learning based cyber attack detection scheme in DC microgrid systems. CPSS Trans. Power Electron. Appl. 2023, 8, 119–127. [Google Scholar] [CrossRef]
- Habibi, M.R.; Golestan, S.; Guerrero, J.M.; Vasquez, J.C. Deep learning for forecasting-based applications in cyber–physical microgrids: Recent advances and future directions. Electronics 2023, 12, 1685. [Google Scholar] [CrossRef]
- Cil, A.E.; Yildiz, K.; Buldu, A. Detection of DDoS attacks with feed forward based deep neural network model. Expert Syst. Appl. 2021, 169, 114520. [Google Scholar] [CrossRef]


| Author [Ref]-Year | System Description | Performance Metrics |
|---|---|---|
| Hassan et al. [32]-2025 | A deep learning model for detecting data integrity attacks in PV farms. | Highest accuracy of 99.8% in detecting cyber-attacks |
| Wang et al. [33]-2022 | A deep learning method for detecting malicious attacks in SCADA systems. | Accuracy of 98.7% in detecting cyber-attacks |
| Paul et al. [34]-2024 | Detection of cyber-attacks (data falsification attacks) in energy systems using the XGBoost algorithm. | Accuracy of 95.5% |
| Sourav et al. [35]-2022 | Detecting hidden attackers in PV systems with ML algorithm. | Accuracy of up to 95% |
| Li et al. [36]-2020 | Cyber-attack detection for PV systems. | Accuracy of 99.23% and 0.9963 F1 score |
| Parameters | ANN-I | ANN-II |
|---|---|---|
| Number of Input | 2 | 3 |
| Number of Output | 1 | 1 |
| Number of Hidden Neurons | 10 | 10 |
| Number of Delays | NaN | 4 |
| Number of Samples (Training) | 2,800,001 | 2,800,001 |
| Number of Samples (Validation) | 600,000 | 600,000 |
| Number of Samples (Testing) | 600,000 | 600,000 |
| Maximum Number of Episodes | 1000 | 1000 |
| Activation Functions | Sigmoid & SoftMax | Sigmoid |
| Loss Functions | Cross-Entropy | MSE |
| Hardware of Server PC | NVIDIA GTX GeForce 1080 TI 11 GB GPU | |
| Training Data | Validation Data | Test Data | All Data | |
|---|---|---|---|---|
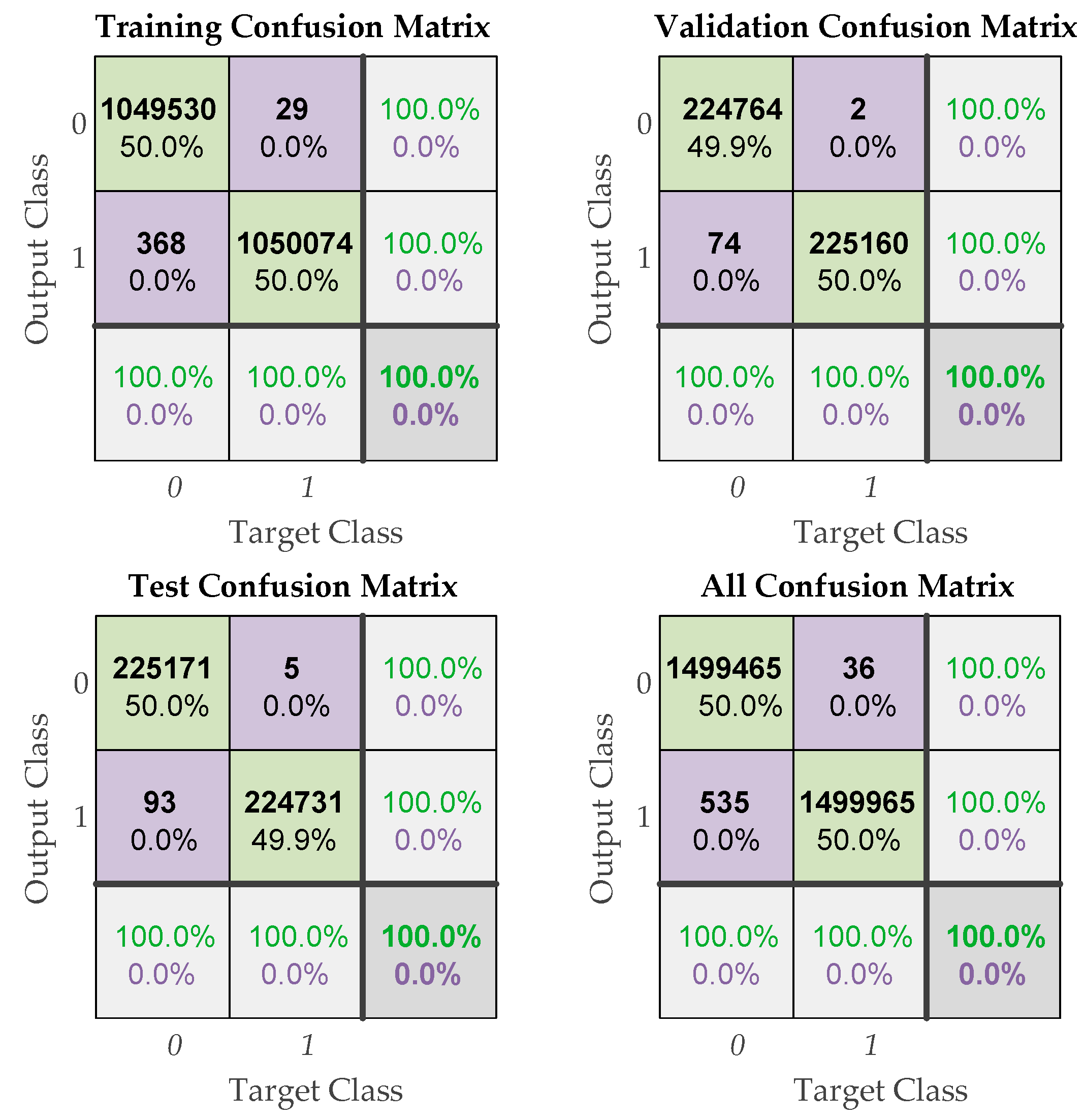
| Accuracy | 99.98% | 99.98% | 99.98% | 99.98% |
| Precision | 99.997% | 99.999% | 99.998% | 99.998% |
| Recall | 99.96% | 99.97% | 99.96% | 99.96% |
| F1 score | 99.98% | 99.98% | 99.98% | 99.98% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Akpolat, A.N.; Kalay, M.S. Defense Mechanism of PV-Powered Energy Islands Against Cyber-Attacks Utilizing Supervised Machine Learning. Appl. Sci. 2025, 15, 5021. https://doi.org/10.3390/app15095021
Akpolat AN, Kalay MS. Defense Mechanism of PV-Powered Energy Islands Against Cyber-Attacks Utilizing Supervised Machine Learning. Applied Sciences. 2025; 15(9):5021. https://doi.org/10.3390/app15095021
Chicago/Turabian StyleAkpolat, Alper Nabi, and Muhammet Samil Kalay. 2025. "Defense Mechanism of PV-Powered Energy Islands Against Cyber-Attacks Utilizing Supervised Machine Learning" Applied Sciences 15, no. 9: 5021. https://doi.org/10.3390/app15095021
APA StyleAkpolat, A. N., & Kalay, M. S. (2025). Defense Mechanism of PV-Powered Energy Islands Against Cyber-Attacks Utilizing Supervised Machine Learning. Applied Sciences, 15(9), 5021. https://doi.org/10.3390/app15095021





