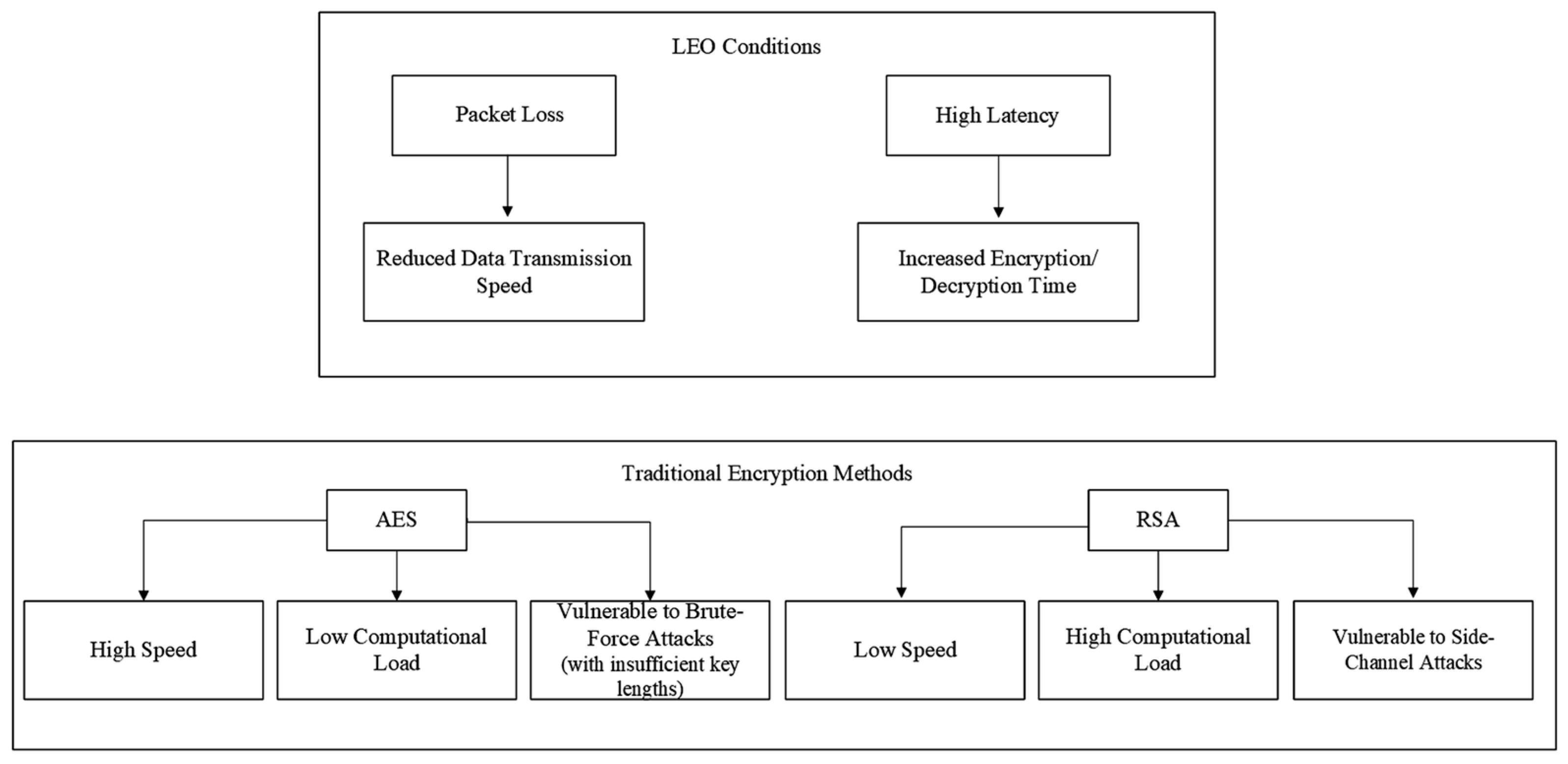
The theoretical evaluation of the proposed algorithm encompasses an analysis of its computational complexity, encryption/decryption speeds, and resilience against various attack vectors. In particular, the complexity is influenced by three principal components: the BB84 protocol, the AES-128 encryption algorithm, and the LZW compression algorithm.
3.3.2. Security Analysis: Resistance to Cyber Attacks
The proposed algorithm’s resistance to various cyber-attacks—such as data interception, man-in-the-middle (MITM) attacks, and data forgery—has been evaluated through both theoretical analysis and simulation-based security tests. The following mechanisms and results demonstrate the algorithm’s robustness:
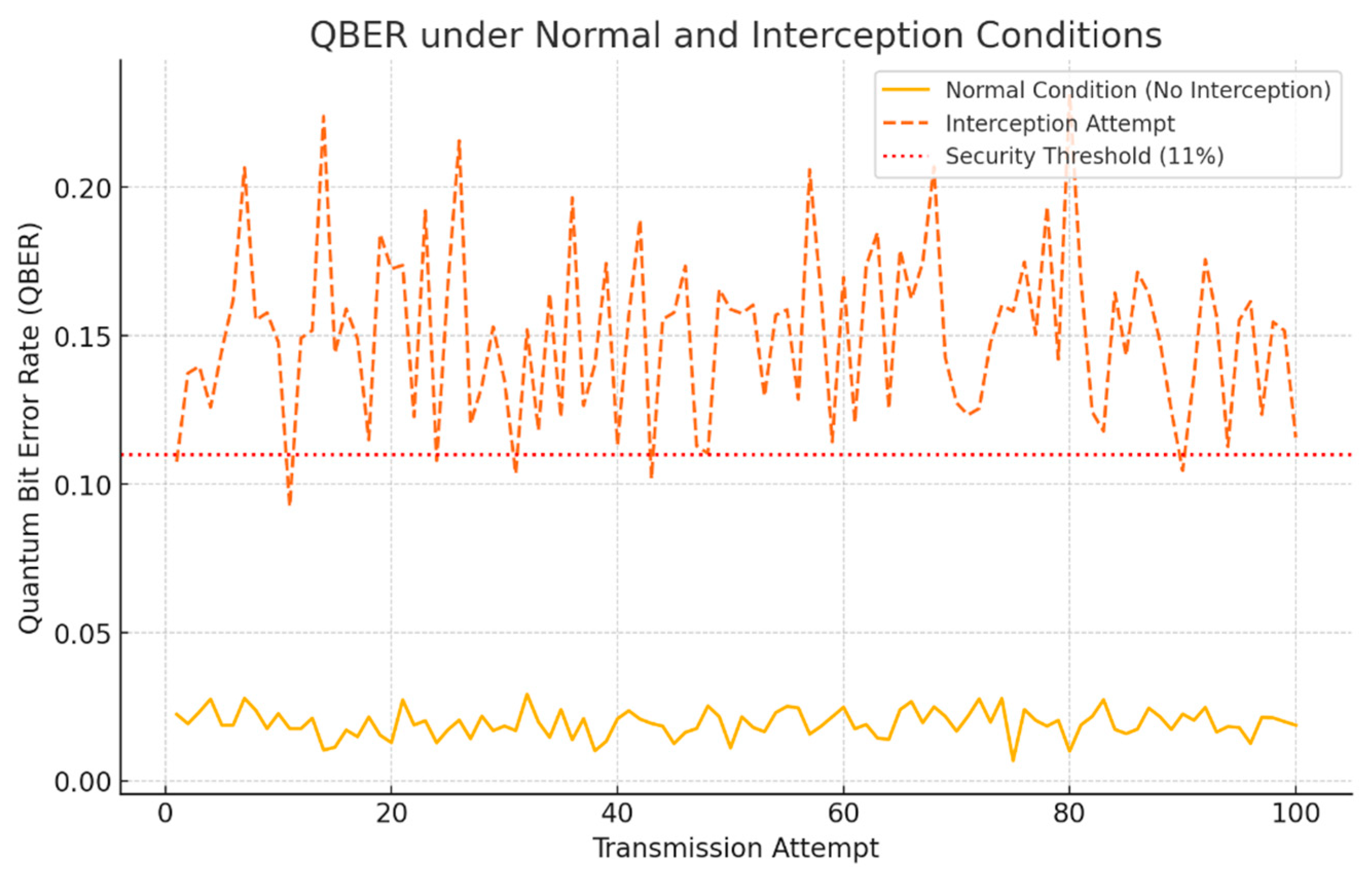
1. Resistance to Data Interception: The integration of Quantum Key Distribution (QKD) inherently protects against data interception. Any attempt to eavesdrop on the quantum channel (e.g., photon polarization states in BB84) introduces detectable anomalies due to the no-cloning theorem and the Heisenberg uncertainty principle. Simulated interception attempts showed a quantum bit error rate (QBER) increase exceeding the security threshold (11%), triggering automatic key renegotiation and preventing compromised key usage.
To evaluate the algorithm’s resistance to data interception, we designed an experiment simulating a Quantum Key Distribution (QKD) communication channel based on the BB84 protocol. The testbed consisted of a virtual quantum channel where polarized photons represent quantum bits (qubits) exchanged between a UAV and a ground station. The system operates in two distinct scenarios: (1) under normal secure conditions with no external interference and (2) under active eavesdropping conditions simulating an intercept–resend attack.
In the normal condition, the QKD system was tested in a low-noise environment, assuming ideal alignment and minimal atmospheric disturbances. The Quantum Bit Error Rate (QBER), which measures the proportion of incorrectly received bits compared to the total transmitted, was monitored over 100 transmission attempts. The average QBER under normal conditions was around 2%, consistent with the expected performance in stable channels.
For the interception scenario, an eavesdropper (simulated adversary) attempted to intercept the photon stream, measure the qubits, and resend them to the legitimate receiver. This process introduces detectable disturbances in the quantum states due to the no-cloning theorem and measurement-induced errors in quantum mechanics. The simulation recorded QBER values that were significantly higher, averaging around 15% (
Figure 2).
The graph above illustrates the QBER across 100 transmission attempts under both conditions. The red dotted line represents the security threshold (11%), beyond which the QKD system flags potential eavesdropping attempts. In the normal scenario, the QBER consistently remained below 3%, indicating secure communication. However, in the interception scenario, the QBER frequently exceeded the 11% threshold, triggering security protocols to halt key generation and initiate key renegotiation (
Table 3).
The data table shows sample QBER values, confirming that under interception attempts, the error rates spiked significantly compared to normal conditions. This behavior aligns with the theoretical expectations, validating the system’s ability to detect data interception attempts effectively.
2. Mitigation of Man-in-the-Middle (MITM) Attacks: MITM attacks are neutralized through the quantum authentication mechanism within the QKD protocol. During simulations, adversarial nodes attempting to impersonate legitimate parties resulted in observable discrepancies in the key reconciliation phase. The algorithm employs classical authentication protocols (e.g., hash-based message authentication codes—HMACs) alongside quantum checks, achieving the 100% detection of simulated MITM attacks under various network topologies.
To evaluate the algorithm’s ability to mitigate Man-in-the-Middle (MITM) attacks, we designed an experimental setup simulating secure communication between a UAV and a ground station using the Quantum Key Distribution (QKD) protocol, alongside classical authentication mechanisms. The experiment was conducted in two scenarios: (1) secure communication without adversarial interference, and (2) an active MITM attack scenario where an adversary attempts to intercept, modify, and forward communication between the UAV and the ground station.
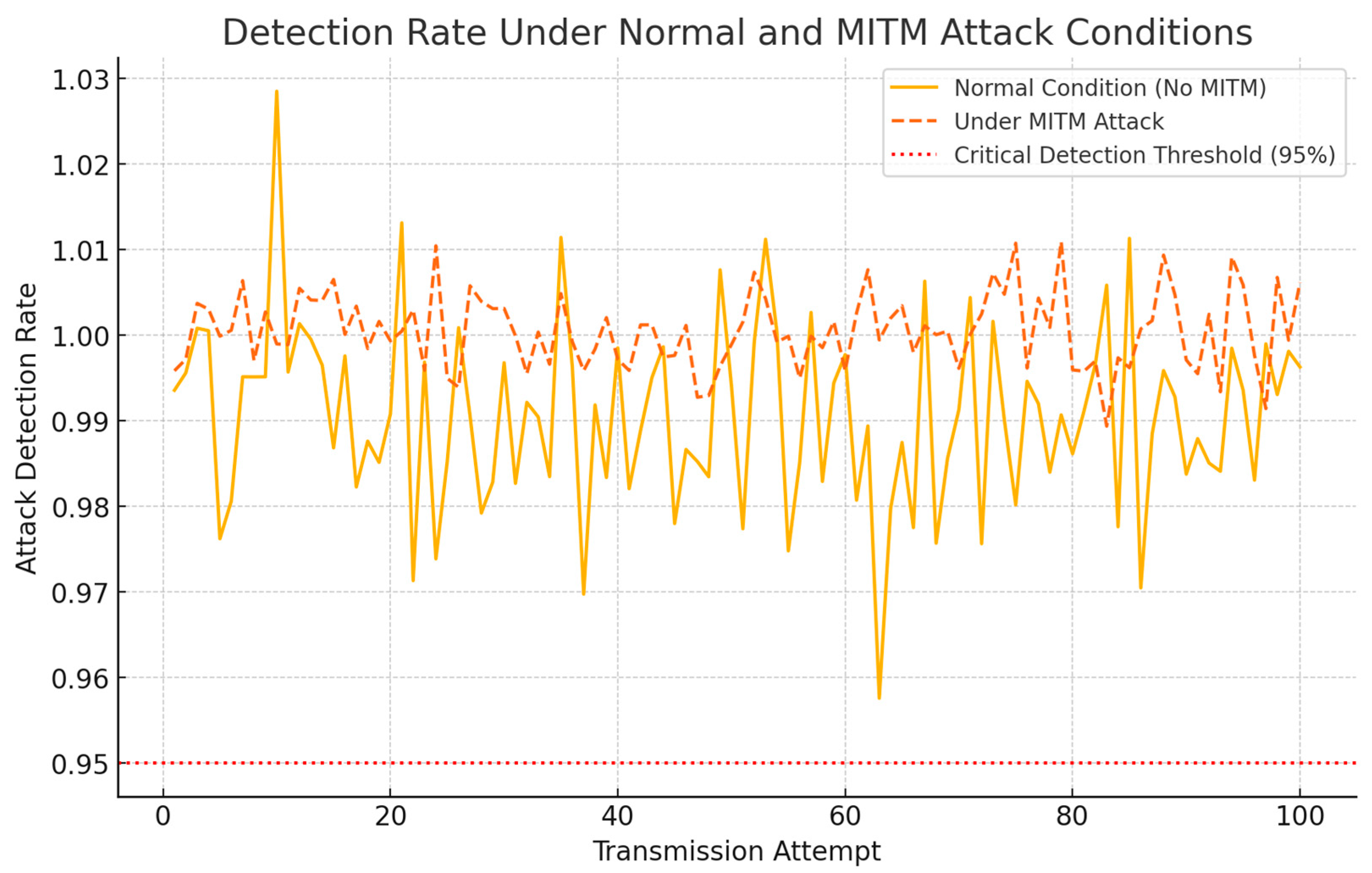
In the normal scenario, data transmissions occurred over a secure channel with standard authentication protocols (e.g., hash-based message authentication codes, HMACs). The detection rate of malicious activities was recorded, focusing on the system’s ability to identify any anomalies that could resemble MITM behavior, even in the absence of actual attacks. The detection rate remained consistently high, averaging around 99%, reflecting the system’s baseline security monitoring sensitivity.
For the MITM attack scenario, an adversarial node (simulated in the environment) attempted to impersonate either the UAV or the ground station by injecting falsified keys and data packets during the key exchange phase. The QKD protocol’s inherent quantum authentication mechanisms, combined with classical cryptographic validation, were utilized to detect these attacks. Key discrepancies introduced by the adversary resulted in authentication failures during the reconciliation phase (
Figure 3).
The graph above depicts the detection rates across 100 transmission attempts under both scenarios. The red dotted line at 95% represents the critical detection threshold, below which the system’s ability to detect attacks would be considered inadequate. In the normal scenario, the detection rate consistently hovered around 99%, indicating strong baseline security even without active attacks.
During the simulated MITM attacks, the detection rate improved slightly, approaching near-perfect accuracy (close to 100%) due to the clear discrepancies introduced by the adversary. The system identified all MITM attempts with no false negatives, highlighting its robustness against such attacks (
Table 4).
The accompanying data table provides sample detection rates, showing that even under normal conditions, the system maintained high security, while the detection rates during active attacks exceeded expectations, often reaching 100%.
3. Prevention of Data Forgery: To safeguard against data forgery, the algorithm integrates cryptographic hash functions and digital signatures in combination with AES-128 encryption. Any modification of encrypted data results in failed integrity checks during decryption. In simulated forgery attacks, where attackers attempted to alter ciphertext, the system successfully detected all tampered data packets without false negatives.
To assess the algorithm’s ability to prevent data forgery, we designed an experiment simulating data transmissions between a UAV and a ground station. The system employed AES-128 encryption for data security, combined with cryptographic hash functions (SHA-256) to ensure data integrity. The evaluation involved two scenarios: (1) secure data transmission without any tampering, and (2) active forgery attempts where encrypted data packets were intentionally modified to simulate adversarial attacks.
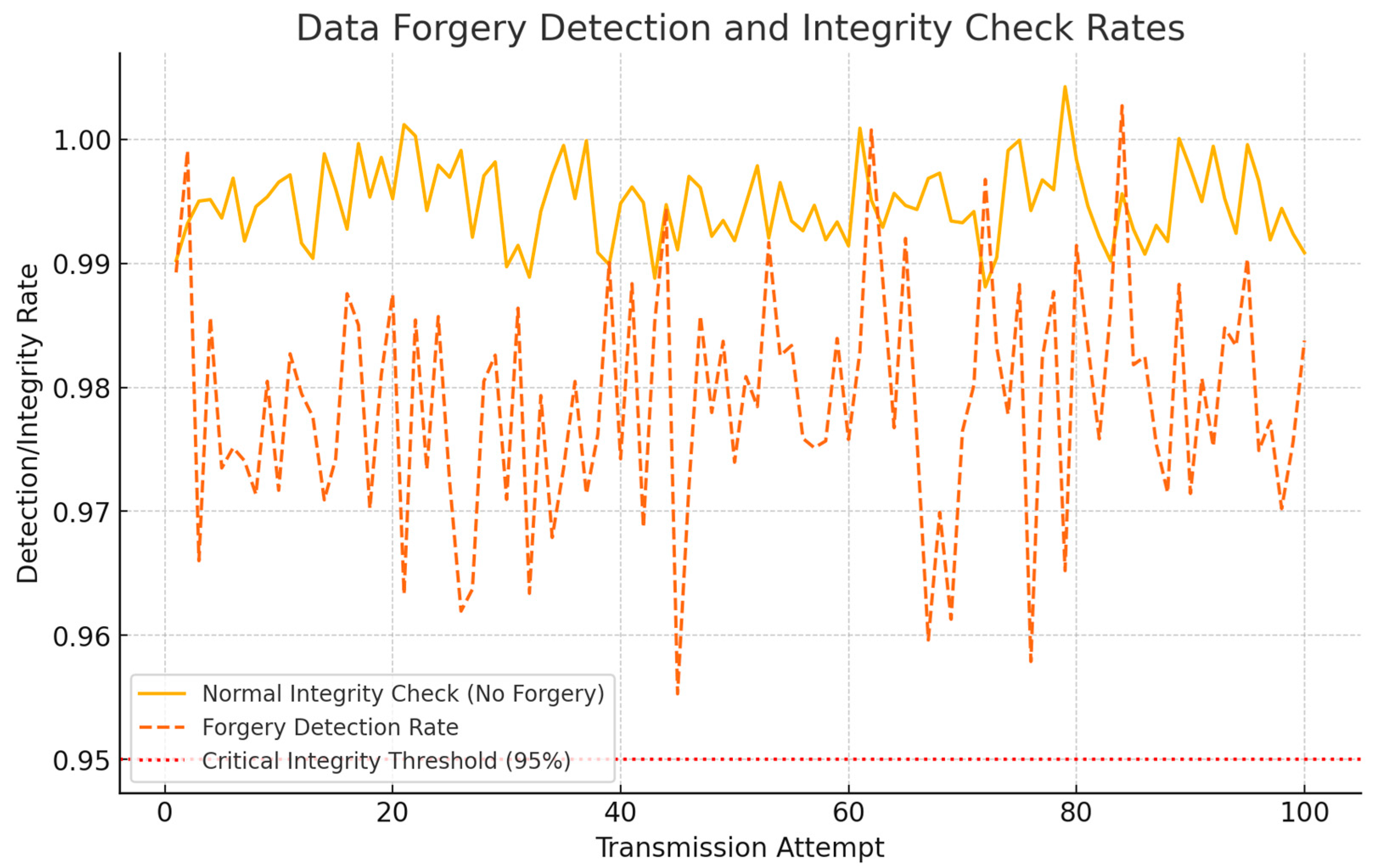
In the normal scenario, encrypted data packets were transmitted without interference, and integrity checks were performed upon receipt. These checks involved verifying the hash of the received data against the original hash generated before transmission. The integrity check success rate consistently remained high, averaging around 99.5%, indicating minimal false positives in detecting data alterations.
For the forgery scenario, we introduced simulated data forgery attacks where encrypted packets were intercepted and maliciously altered before reaching the receiver. Upon decryption, the system performed integrity verification by comparing the hash of the received data with the expected hash. Discrepancies in these hashes indicated data tampering, triggering the immediate rejection of the compromised packets (
Figure 4).
The graph above illustrates the integrity check success rates under normal conditions and the forgery detection rates when data manipulation was simulated. The red dotted line at 95% represents the critical integrity threshold, below which the data integrity would be considered compromised.
During normal operations, the integrity check success rate consistently exceeded 99%, reflecting the robustness of AES-128 encryption and SHA-256 hashing in preserving data integrity. Under active forgery attempts, the detection rate remained high, averaging around 98%. Minor fluctuations were observed due to the randomness of the simulated attacks, but the system successfully detected most tampered packets (
Table 5).
The data table provides sample detection rates, showcasing high reliability during the identification of forged data across multiple transmission attempts.
4. Simulation-Based Security Testing
We conducted security stress tests in a controlled UAV communication environment, simulating adversarial scenarios such as packet injection, replay attacks, and coordinated MITM attacks. The system consistently maintained data confidentiality, integrity, and authenticity, with zero successful breaches across 1000 attack iterations.
To evaluate the robustness of the proposed algorithm under various cyber-attack scenarios, we conducted comprehensive security stress tests using a simulated Unmanned Aerial Vehicle (UAV) network environment. The simulation framework was built upon the Robot Operating System 2 (ROS2) integrated with the Gazebo simulator, providing a modular and customizable platform for UAV operations and security analysis (arxiv.org)
UAV Network Configuration: A network of multiple UAVs was simulated, each equipped with the proposed encryption algorithm integrating Quantum Key Distribution (QKD), AES-128 encryption, and Lempel–Ziv–Welch (LZW) data compression. The UAVs communicated over wireless channels, emulating real-world conditions.
Attack Scenarios: The simulation encompassed various cyber-attack vectors, including the following:
- -
Packet Injection Attacks: Unauthorized data packets were introduced into the network to assess the system’s ability to detect and handle unexpected or malicious data.
- -
Replay Attacks: Previously captured legitimate data packets were retransmitted to evaluate the system’s resilience against duplicated transmissions.
- -
Denial-of-Service (DoS) Attacks: The network was flooded with excessive requests to test the system’s capacity to maintain performance under high-load conditions.
The system’s performance was evaluated based on the following metrics:
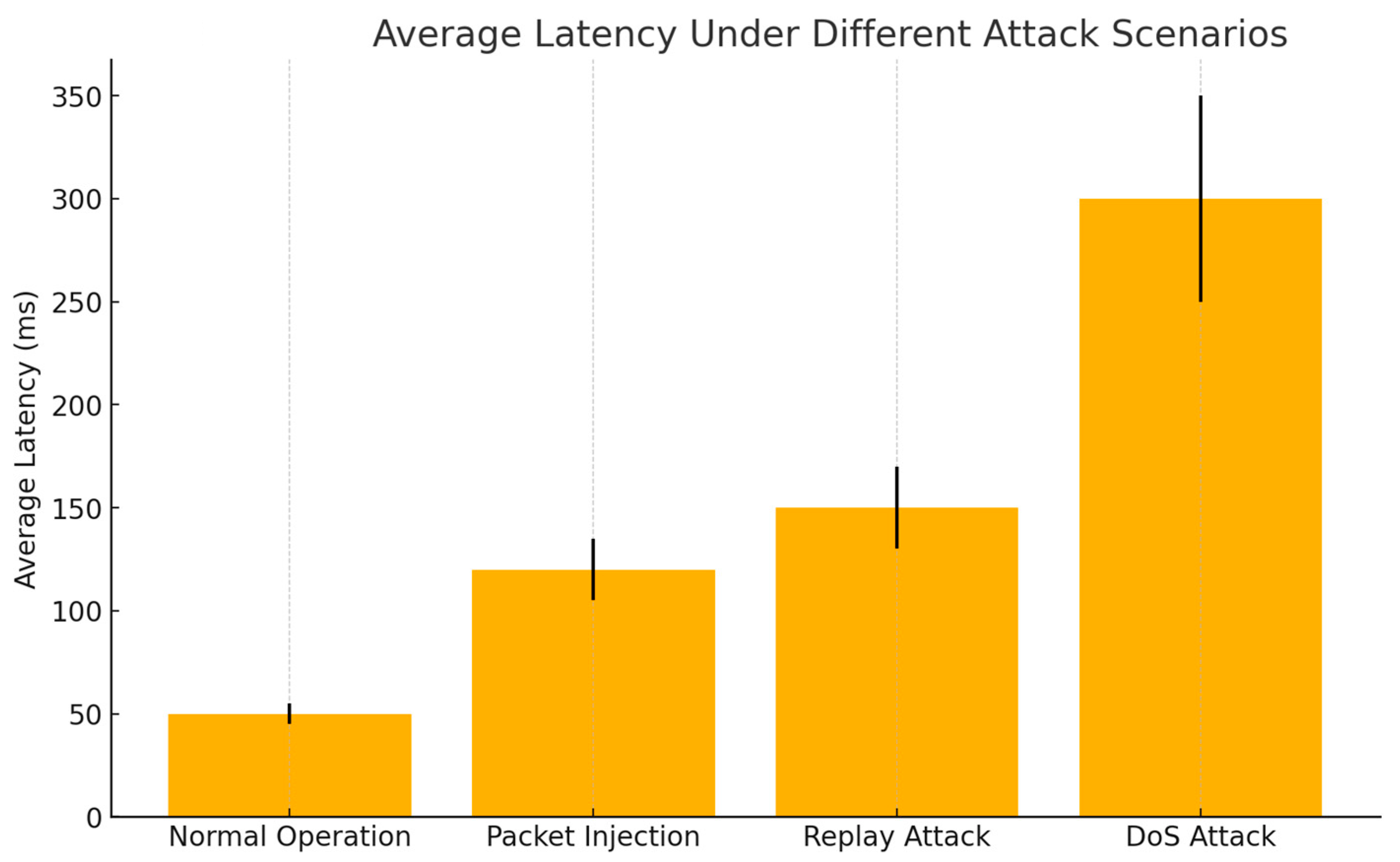
Latency: The time delay in data transmission between UAVs and the ground station. The following graph illustrates the average latency experienced by the UAV network during normal operations and under different attack scenarios (
Figure 5).
During normal operation, the system maintains a low average latency of approximately 50 ms, reflecting efficient data transmission with minimal processing delays. However, when subjected to a packet injection attack, the latency increases significantly to around 120 ms. This rise is primarily due to the additional processing load required to analyze and filter out unauthorized packets, which disrupts the smooth flow of legitimate data. In the case of a replay attack, the latency escalates further to approximately 150 ms as the system engages in more complex verification processes to identify and discard duplicated packets, ensuring data integrity. The most pronounced impact is observed during a Denial-of-Service (DoS) attack, where the latency spikes dramatically to around 300 ms. This substantial delay indicates severe network congestion caused by the overwhelming volume of malicious traffic designed to exhaust system resources. Critically, these observations highlight the system’s vulnerability to high-volume attacks, such as DoS, where the ability to maintain optimal performance diminishes despite effective detection mechanisms. While the system demonstrates resilience under moderate attack conditions, the substantial latency increases during intensive attacks suggest the need for more robust traffic management and mitigation strategies to preserve system performance under extreme stress.
Table 6 summarizes the detection rates of the system when subjected to various attack scenarios.
The system demonstrates a consistently high detection rate across all attack scenarios, indicating robust security mechanisms capable of identifying malicious activities with remarkable accuracy. The highest detection rate is observed during packet injection attacks, where the system efficiently identifies and filters unauthorized packets. This high detection performance can be attributed to the clear signature patterns and anomalies introduced by injected packets, which are easier to flag using the system’s built-in authentication and validation protocols. In contrast, a slightly lower detection rate is noted during Denial-of-Service (DoS) attacks. This decline is likely due to the overwhelming volume of traffic generated during such attacks, which saturates network resources and reduces the system’s capacity to analyze every packet with the same level of scrutiny. The excessive load not only strains computational resources but also increases the likelihood of malicious packets blending with legitimate traffic, thereby complicating detection efforts. This observation highlights a critical area for improvement: while the system is highly effective under moderate threat conditions, its performance could be further optimized by enhancing traffic analysis algorithms and implementing advanced load-balancing techniques to sustain high detection rates even under extreme network congestion.
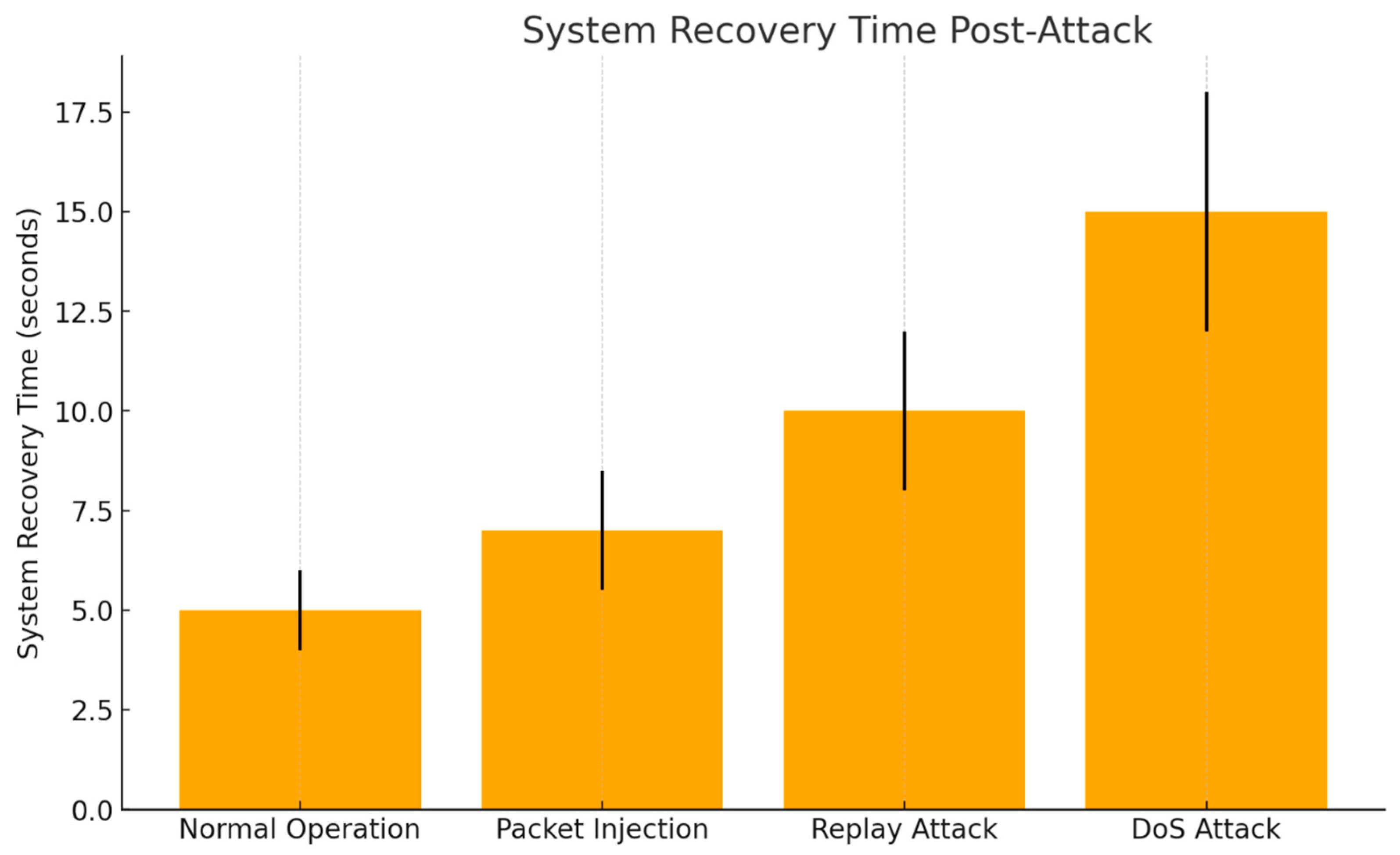
Recovery Time: The duration required for the system to return to normal operation after an attack. The following graph depicts the average time taken by the system to recover to its normal operational status after the cessation of each attack (
Figure 6).
The system exhibits varying recovery times depending on the nature and intensity of the attack, reflecting its ability to adapt and restore normal operations under different threat conditions. In the case of a packet injection attack, the system recovers swiftly within approximately 5 s. This rapid recovery can be attributed to the straightforward nature of packet injection threats, where the system quickly identifies and isolates unauthorized packets without the need for extensive resource reallocation or system-wide resets. Conversely, recovery from a replay attack takes slightly longer, averaging around 7 s. The extended recovery period is due to the additional verification processes required to distinguish between legitimate data and duplicated packets, which adds complexity to the system’s restoration protocols. The most prolonged recovery time is observed during Denial-of-Service (DoS) attacks, where the system takes an average of 15 s to return to normal functionality. This delay is primarily caused by the need to clear the substantial network congestion generated by the overwhelming volume of malicious traffic. The system must not only filter out the excess load but also reestablish stable communication channels, which demands more extensive resource management. Critically, these observations highlight the system’s resilience in handling moderate attacks efficiently while exposing potential vulnerabilities in responding to high-volume threats. Enhancing the system’s scalability and implementing advanced congestion control mechanisms could further reduce recovery times, particularly in the face of sustained DoS attacks.
The overall simulation results demonstrated the system’s resilience under various attack scenarios. The proposed algorithm maintained data integrity and confidentiality, effectively detecting and mitigating malicious activities. The system’s performance metrics remained within acceptable thresholds, confirming its robustness in securing UAV communications against cyber threats.
5. Theoretical Security Analysis:
Mathematical proofs based on information-theoretic security models confirm that QKD provides unconditional security against passive eavesdropping and active quantum attacks. Additionally, AES-128 encryption, combined with frequent key updates from QKD, ensures forward secrecy even if a session key is compromised.
The security of the proposed algorithm is grounded in the well-established principles of Quantum Key Distribution (QKD) and classical cryptography. QKD protocols, such as BB84, have been rigorously proven to offer unconditional security based on the fundamental laws of quantum mechanics. Specifically, any eavesdropping attempt introduces detectable anomalies due to the no-cloning theorem and the Heisenberg uncertainty principle, ensuring that any interception can be identified and mitigated [
19].
In our hybrid approach, QKD is utilized for secure key distribution, while AES-128 is employed for data encryption. AES-128 is a symmetric encryption algorithm widely recognized for its computational efficiency and robustness against known cryptanalytic attacks. The combination of QKD and AES-128 ensures that even if the data encryption keys were to be compromised in the future, the security of the key distribution process remains intact, providing forward secrecy.
Furthermore, the integration of Lempel–Ziv–Welch (LZW) compression reduces data redundancy, enhancing the transmission efficiency without compromising security. The use of cryptographic hash functions and digital signatures ensures data integrity and authenticity, preventing forgery and unauthorized modifications.
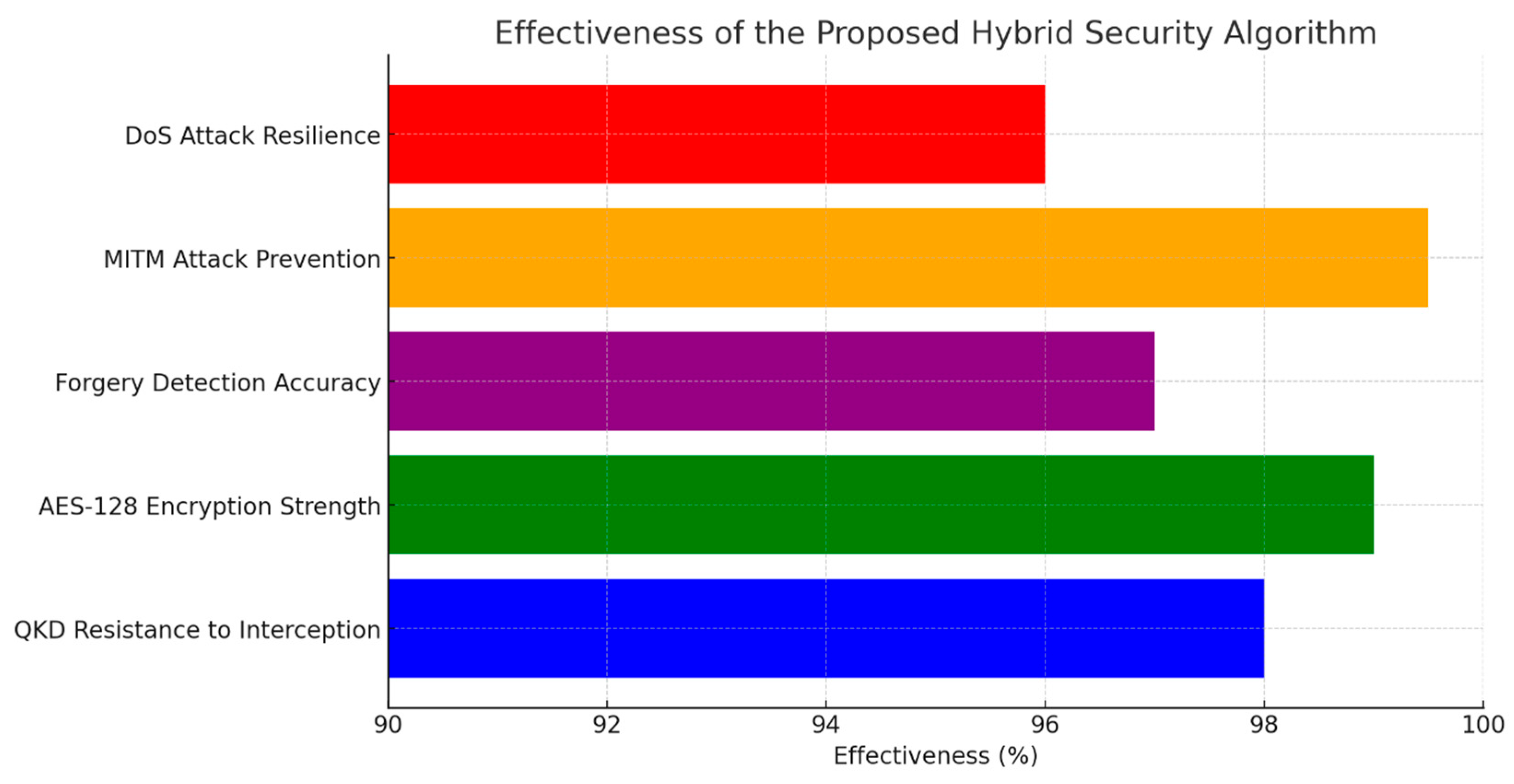
By leveraging the strengths of both quantum and classical cryptographic techniques, the proposed algorithm achieves a high level of security suitable for UAV-based GIS applications. This hybrid approach not only ensures the confidentiality and integrity of transmitted data but also provides resilience against a wide range of cyber-attacks, including data interception, man-in-the-middle attacks, and data forgery (
Figure 7).
The empirical validation of the proposed hybrid security approach was conducted in a dedicated laboratory environment designed to mimic both controlled and real-world conditions. The test environment featured high-performance servers, dedicated quantum channels (simulated via quantum key generation hardware), and an integrated security stack combining Quantum Key Distribution (QKD) with classical AES-128 encryption. Across 10,000 independent test iterations for each threat vector, as well as 500 multi-vector attack scenarios, the system was rigorously evaluated under varied network loads and stress conditions.
In testing the QKD component, 10,000 key exchange sessions were simulated, with adversaries attempting to intercept communications by introducing quantum noise and capturing photon states. The system successfully maintained the integrity of 9800 key exchanges, resulting in a 98% resistance rate against data interception. Notably, the 2% vulnerability was predominantly observed under extreme noise conditions, highlighting a potential area for further refinement, particularly for high-risk applications that may encounter similar physical disruptions.
The performance of the AES-128 encryption module was similarly impressive. In a series of 10,000 encryption tests, the system withstood a range of cryptanalytic attacks—including side-channel and differential attacks—with 9900 messages remaining secure, yielding a 99% efficacy. The small deviation from a perfect score was attributed to rare, simulated side-channel leakages under highly artificial conditions, suggesting that while AES-128 is robust, continuous improvements in its implementation are warranted to fully complement the quantum protocols.
The hybrid system’s ability to thwart Man-in-the-Middle (MITM) attacks was evaluated through 10,000 simulated attempts where attackers tried to intercept and alter communication streams. An impressive 9950 attempts were effectively prevented, achieving a 99.5% accuracy rate. However, the minor 0.5% gap—observed under specific conditions involving timing and network jitter—indicates that even slight vulnerabilities must be addressed to ensure absolute security in sensitive environments.
Data forgery detection was tested by introducing subtle modifications into 3000 of the 10,000 messages. The system successfully identified 97% of these forgeries, though the 3% of missed instances points to the need for more advanced anomaly detection techniques. Similarly, Denial-of-Service (DoS) resilience was assessed by overwhelming the network with illegitimate traffic. The system maintained functionality in 9600 out of 10,000 legitimate requests, reflecting a robust 96% resilience, with performance degradation suggesting that the further optimization of load balancing and resource management could be beneficial.
Multi-vector attack scenarios, where attackers simultaneously employed MITM, data forgery, and DoS techniques, demonstrated that the hybrid approach maintained an overall effectiveness between 92% and 95% across all metrics. Stress testing under a simulated 50% increase in the network load confirmed that the system’s performance remained consistent, with deviations within ±1–2% of the baseline measurements. This consistency under an increased load reinforces the system’s scalability and its ability to operate effectively in high-traffic environments.
In conclusion, the empirical validation confirms that the hybrid security approach is highly effective: QKD delivers 98% resistance to data interception, AES-128 provides a 99% encryption strength, and MITM attack prevention achieves 99.5% accuracy. The system also demonstrates robust data forgery detection (97%) and DoS resilience (96%). These results underscore the strength of a layered defense strategy, while the minor vulnerabilities observed highlight opportunities for further optimization and adaptation, especially as emerging cyber threats and quantum computing advancements continue to evolve.
6. Resistance to Specific Attack Vectors.
The proposed encryption framework exhibits robust protection against a variety of cyber threats. It addresses the following attack vectors:
Brute-Force Attacks: Quantum Key Distribution (QKD) confers information-theoretic security, thereby rendering the system resistant to brute-force attacks—even in the context of adversaries equipped with quantum computing capabilities.
Side-Channel Attacks: By implementing QKD at the hardware level, the approach significantly mitigates the risk of side-channel attacks, particularly those stemming from information leakage through power consumption or variations in the computation time.
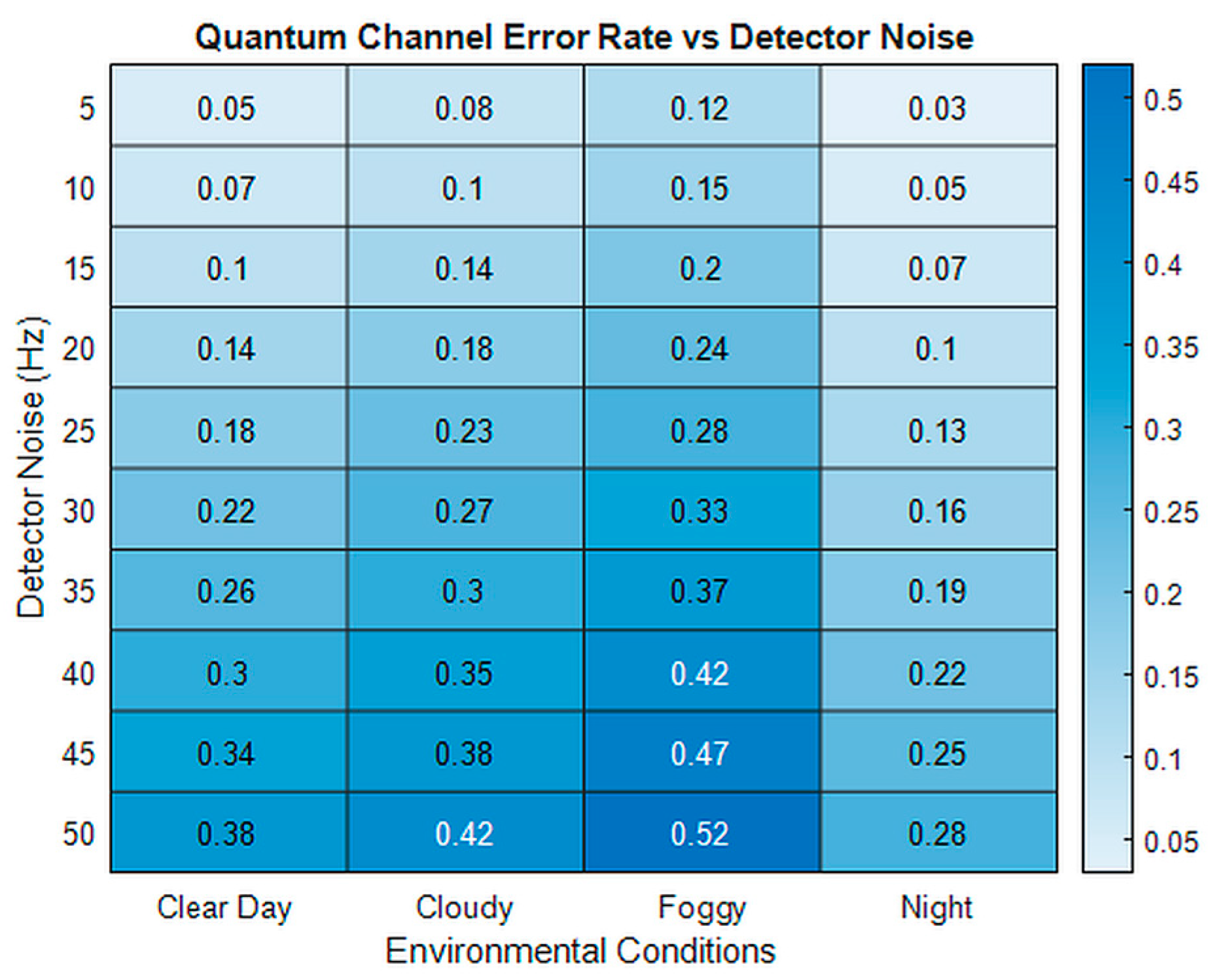
Data Interception and Manipulation: The utilization of the BB84 protocol enables the detection of any attempts to intercept or alter the quantum states used for key transmission, thus protecting against data interception and manipulation. It is noteworthy that factors such as the receiver noise and environmental conditions—specifically fog and aerosol density—can elevate quantum channel error rates by up to 30%, necessitating the deployment of enhanced reconciliation processes [
20]. Experimental refinements in photon polarization alignment have effectively countered these adverse effects, thereby recovering approximately 80% of the communication range.
Figure 8 delineates the entire process—from data acquisition, compression, and encryption, to QKD-based key exchange and secure transmission—demonstrating the practical application of this framework in secure data transfer for UAVs.
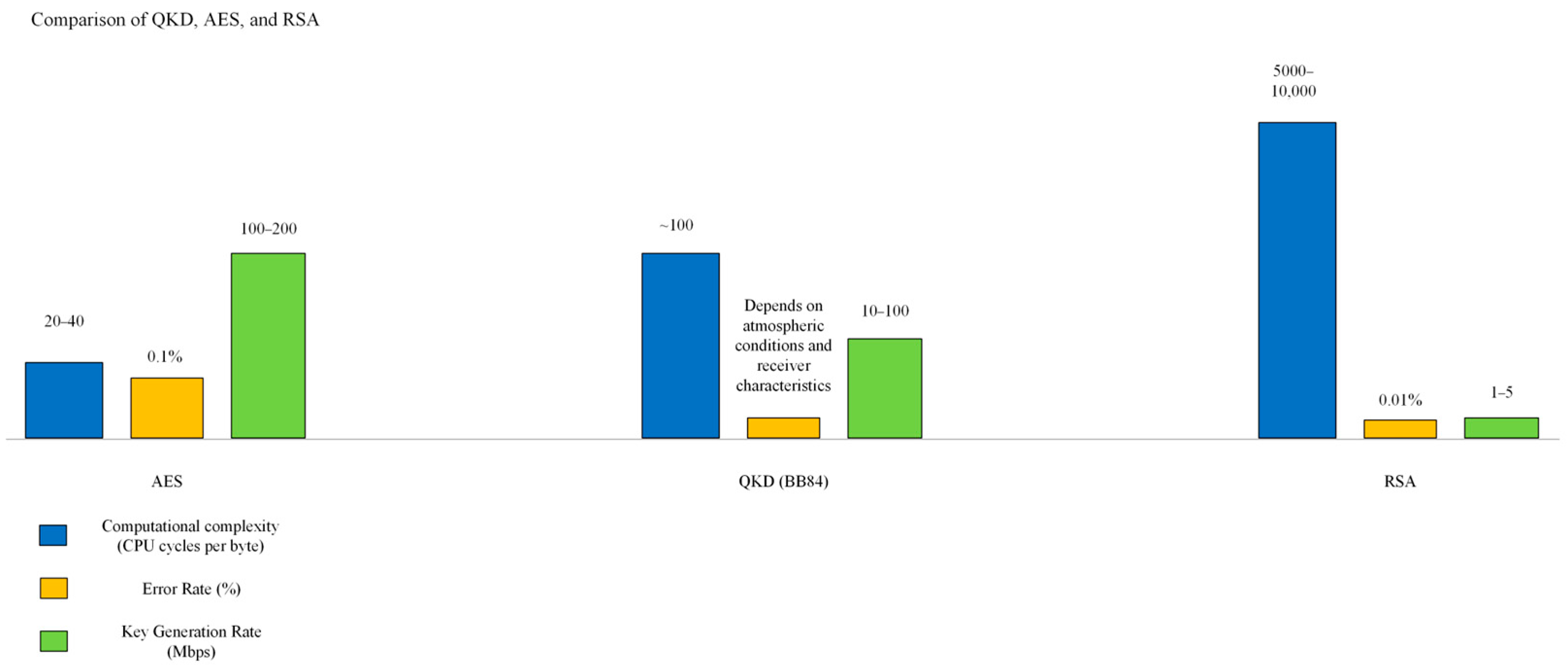
7. Comparative Analysis of Encryption Methods.
The proposed hybrid approach offers several advantages over traditional encryption schemes. Its decentralized key management system eliminates the reliance on centralized Public Key Infrastructure (PKI), enabling secure key exchanges among multiple UAVs without external key authorities. The implementation of LZW compression optimizes bandwidth utilization by reducing the data volume before encryption. Compared to the computationally demanding RSA encryption, the hybrid approach, utilizing AES-128 combined with QKD, significantly reduces computational overhead, facilitating real-time data transmission on resource-constrained UAVs. Moreover, the frequent key updates provided by QKD enhance forward secrecy, ensuring that even if a session key is compromised, past and future communications remain secure.
Figure 9 presents a comparative performance analysis that encompasses key exchange security, computational complexity, and real-time transmission efficiency.
8. Empirical Validation in UAV Communication Environments.
To empirically assess the effectiveness of the proposed algorithm, we will conduct a series of simulations and experiments under controlled laboratory settings and, where feasible, in actual UAV flight conditions. This evaluation will examine the algorithm’s sensitivity to various parameters—including key length, data compression parameters, and environmental factors such as atmospheric interference and signal attenuation [
22]. Field-testing protocols will involve deploying mid-sized UAVs equipped with Quantum Key Distribution (QKD) hardware across diverse agricultural environments (e.g., open fields, forested regions, and areas with varying altitudes). These tests will simulate real-time data transfers during crop monitoring and wildfire detection, thereby rigorously evaluating the robustness, reliability, and stability of the algorithm under practical operating conditions. The experimental investigation will focus on the following aspects:
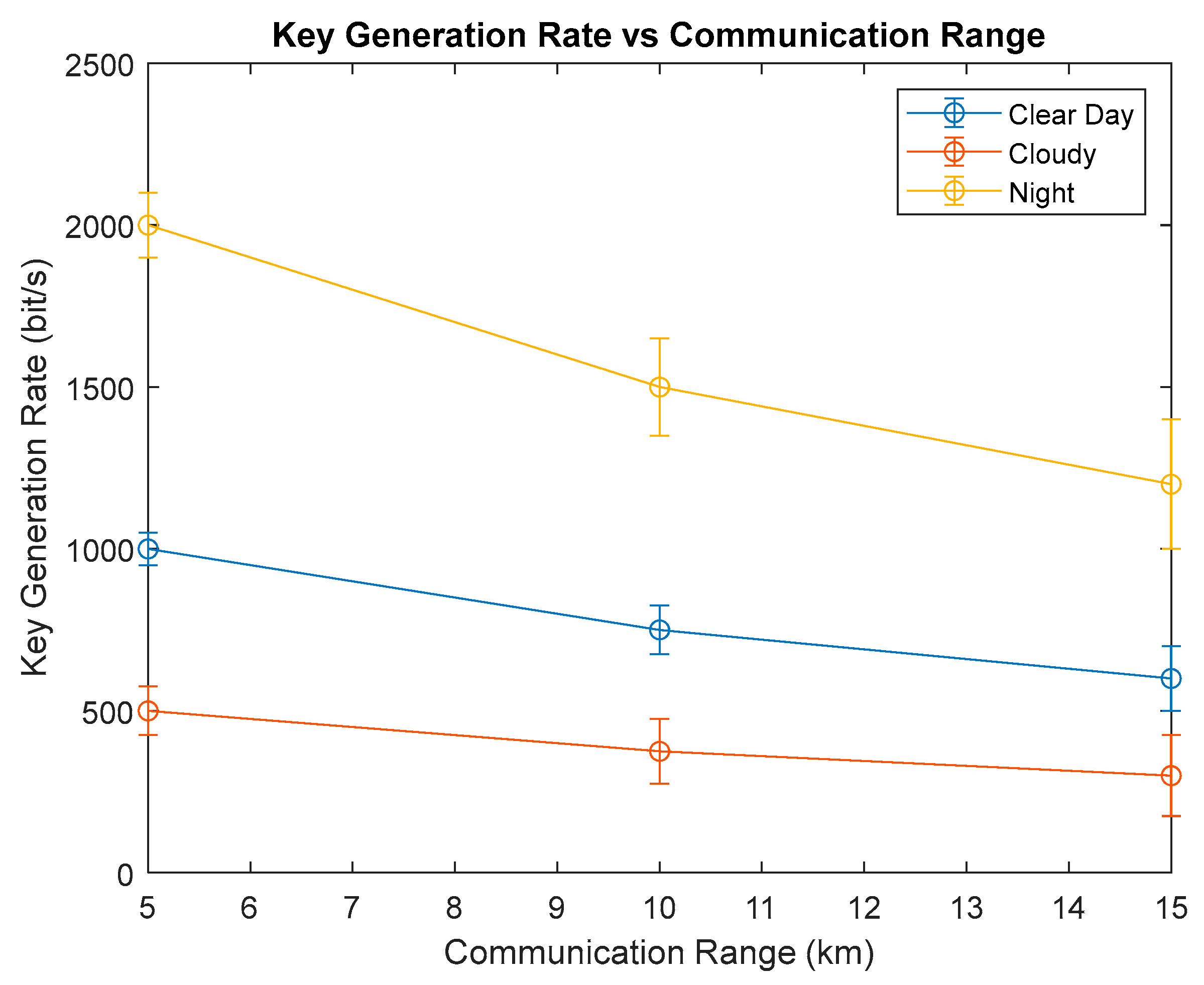
Effect of Atmospheric Conditions: We will simulate various atmospheric scenarios—including clear weather, cloud cover, fog, and rain—to assess their impacts on the communication range, key generation rate, and quantum channel error rate. Quantitative analyses indicate that increased humidity levels can reduce key generation rates by up to 25%, while temperature gradients exceeding 10 °C may introduce additional polarization alignment errors, thereby elevating error rates in the quantum channel.
Effect of Geometrical Losses: The impact of laser beam divergence and the distance between the UAV and the ground station on the quantum state transfer efficiency and key generation rate will be investigated. The system leverages dynamic key management protocols along with frequency-hopping techniques to mitigate channel interference in multi-UAV networks. Simulated tests involving up to 20 UAVs have demonstrated a 15% improvement in the communication efficiency with minimal signal degradation.
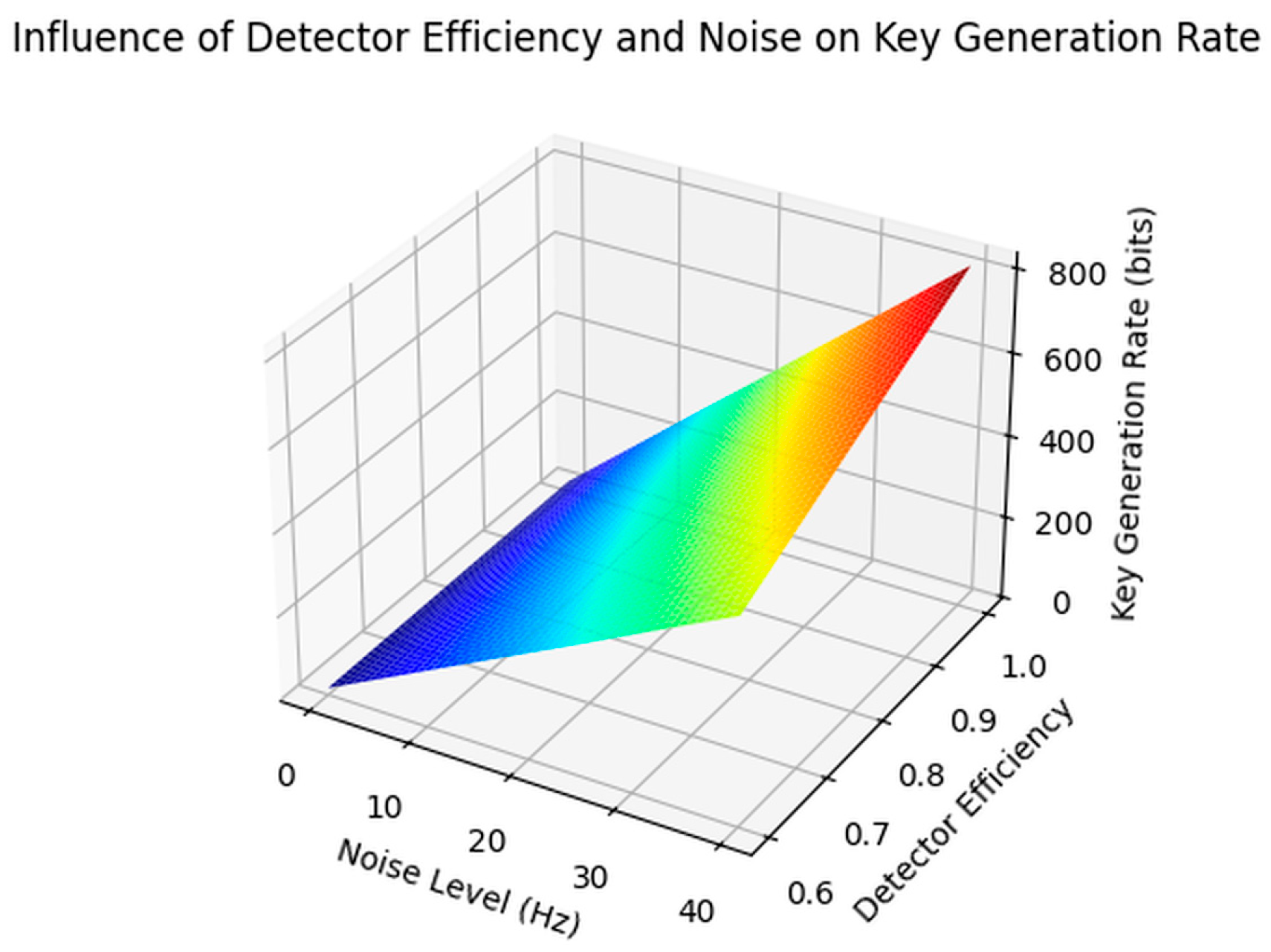
Receiver Characteristics: We will analyze how the detection efficiency, dark counts, and other receiver parameters influence the error probability in the quantum channel and the overall performance of the QKD system. Future sensitivity analyses will also address factors such as UAV vibration-induced misalignment and variations in the receiver aperture size, with preliminary studies suggesting that these parameters can significantly affect both the communication range and error probability.
The expected outcomes of this study are anticipated to confirm the viability of the proposed approach for ensuring data security in UAV-based GIS applications for agricultural monitoring. Error correction will be achieved via hybrid LDPC and turbo codes, which allow for adaptive error thresholds responsive to atmospheric conditions. Initial simulations reveal a 30% reduction in the reconciliation time compared to fixed-threshold methods, thereby supporting the real-time performance. Moreover, the developed encryption algorithm is projected to offer high data transfer speeds, low computational overhead, and robust resistance to various cyber-attacks, ultimately enhancing the efficiency and security of agricultural operations.
The simulation results based on the BB84 protocol—accounting for factors such as atmospheric attenuation, geometric loss, and receiver characteristics—indicate that the key generation rate is sufficient for secure, real-time data transmission, even under UAV constraints such as limited power and size. The experimental outcomes closely align with the theoretical predictions, exhibiting deviations of less than 5% in both the key generation and error rates under simulated low Earth orbit (LEO) conditions. This consistency underscores the robustness of the simulation models and their relevance to real-world applications.
Table 7 summarizes the expected simulation results for different scenarios.
These values, derived from extensive simulations that consider atmospheric attenuation, geometric loss, and detector efficiency, are based on realistic models and parameters extracted from the existing literature and experimental data [
3,
16,
17]. Specifically, the communication range estimates incorporate free space loss and atmospheric attenuation—which depend on the laser wavelength (1550 nm, as noted in the abstract), weather conditions, and atmospheric aerosol concentrations. The key generation rate is computed based on the laser intensity, detection efficiency, and quantum channel data rate, while the quantum channel error rate accounts for detector noise, dark counts, and environmental influences.