Comparative Analysis of SQL Injection Defense Mechanisms Based on Three Approaches: PDO, PVT, and ART
Abstract
1. Introduction
- -
- It presents the first unified comparative analysis of three widely used SQLi defense mechanisms—PDO, PVT, and ART—under consistent experimental conditions.
- -
- It provides practical implementation guidelines and code-level validation for each technique, offering reproducible reference materials for academic and educational use.
- -
- It clarifies the relative strengths, weaknesses, and trade-offs among the techniques, helping practitioners choose suitable combinations for real-world deployment.
2. Related Works
2.1. SQL Injection Vulnerability
2.2. Literature Analysis
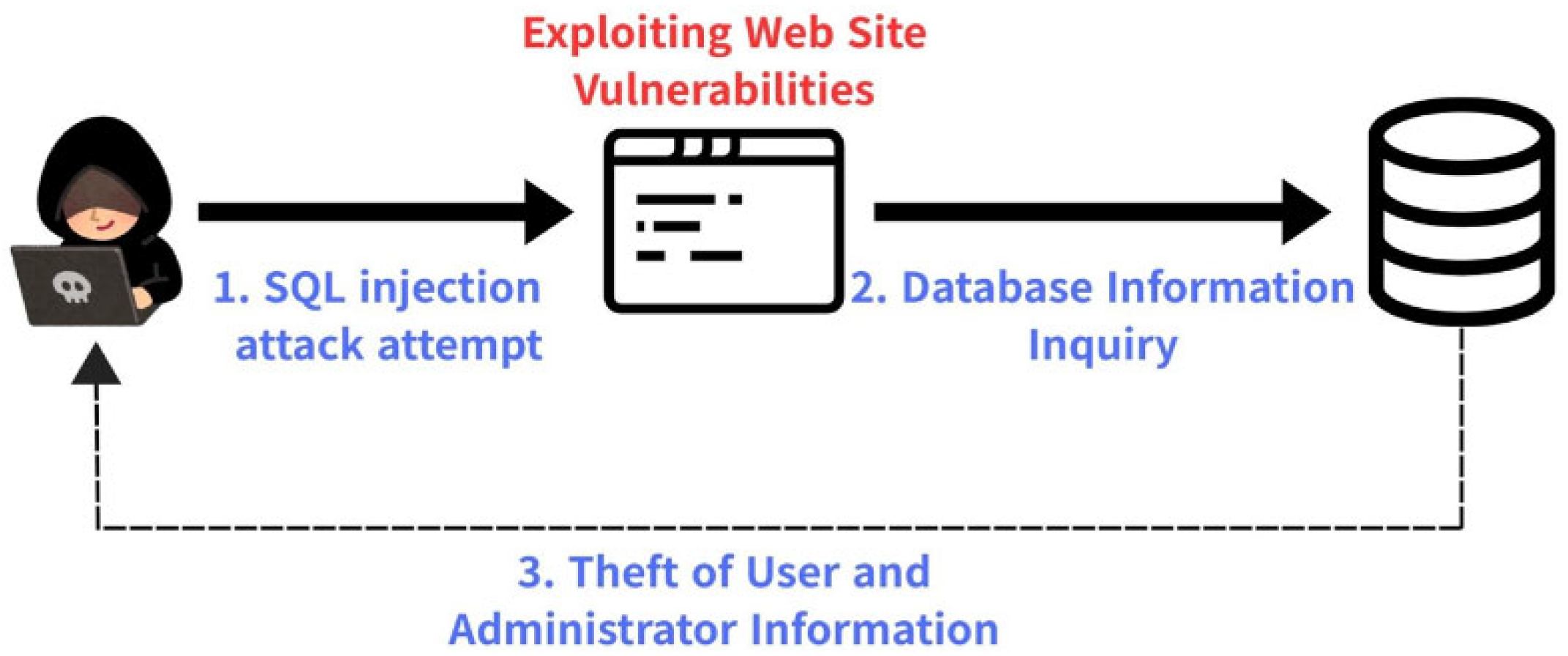
3. SQL Injection Mitigation and Defense
- -
- PHP Data Objects (PDO) exemplifies structural defenses that separate query logic from user input using parameterized queries.
- -
- Pattern Validation Technique (PVT) represents input validation approaches that rely on detecting suspicious patterns before query execution.
- -
- Attacker Redirection Technique (ART) illustrates behavioral and deception-based responses that handle detected attacks through diversion and logging.
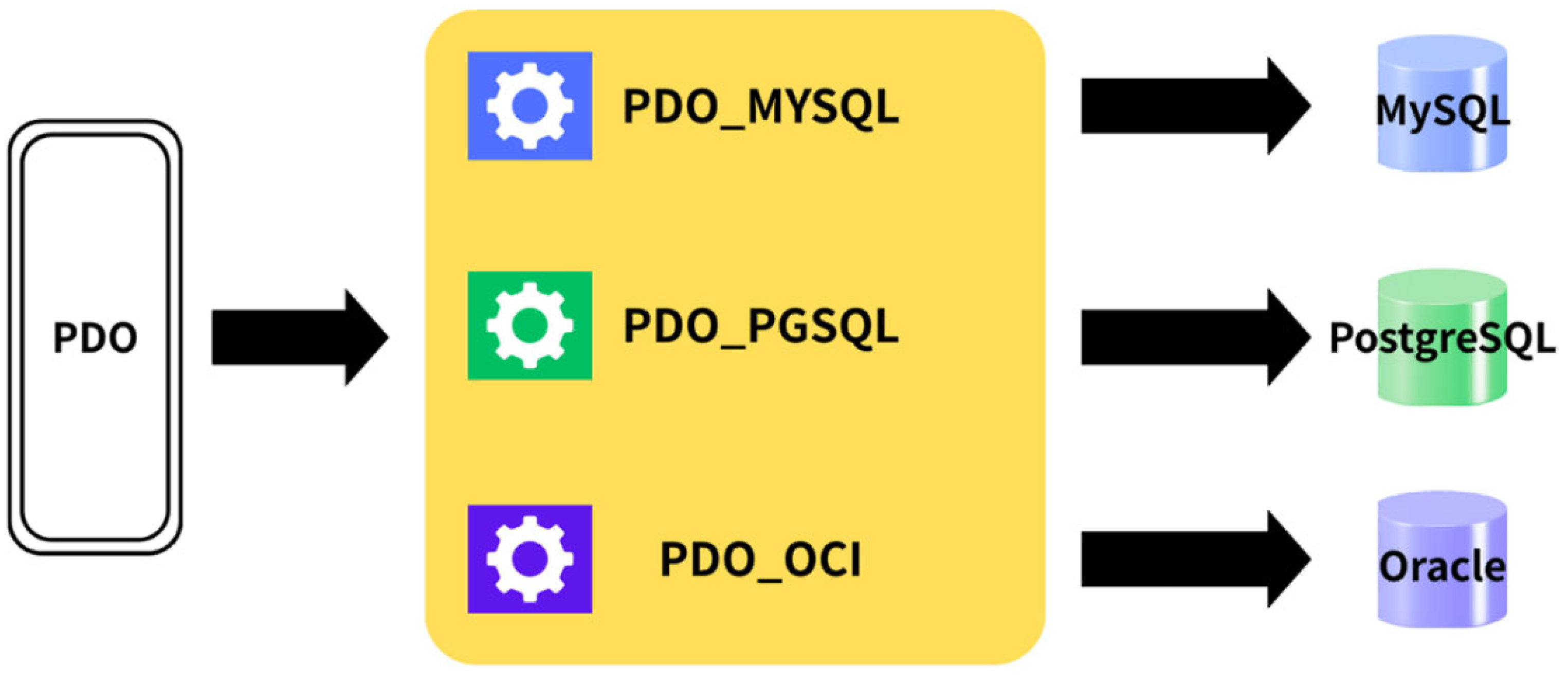
3.1. PHP Data Objects (PDO)
3.2. Input Pattern Validation Technique for Injection Defense (PVT)
| Algorithm 1: Filtering-based Protection Technique |
1: Define suspicious patterns for SQL injection:
2.1. Compare the user input id against the pattern using regular expression matching. 2.2. If the input matches a forbidden pattern:
|
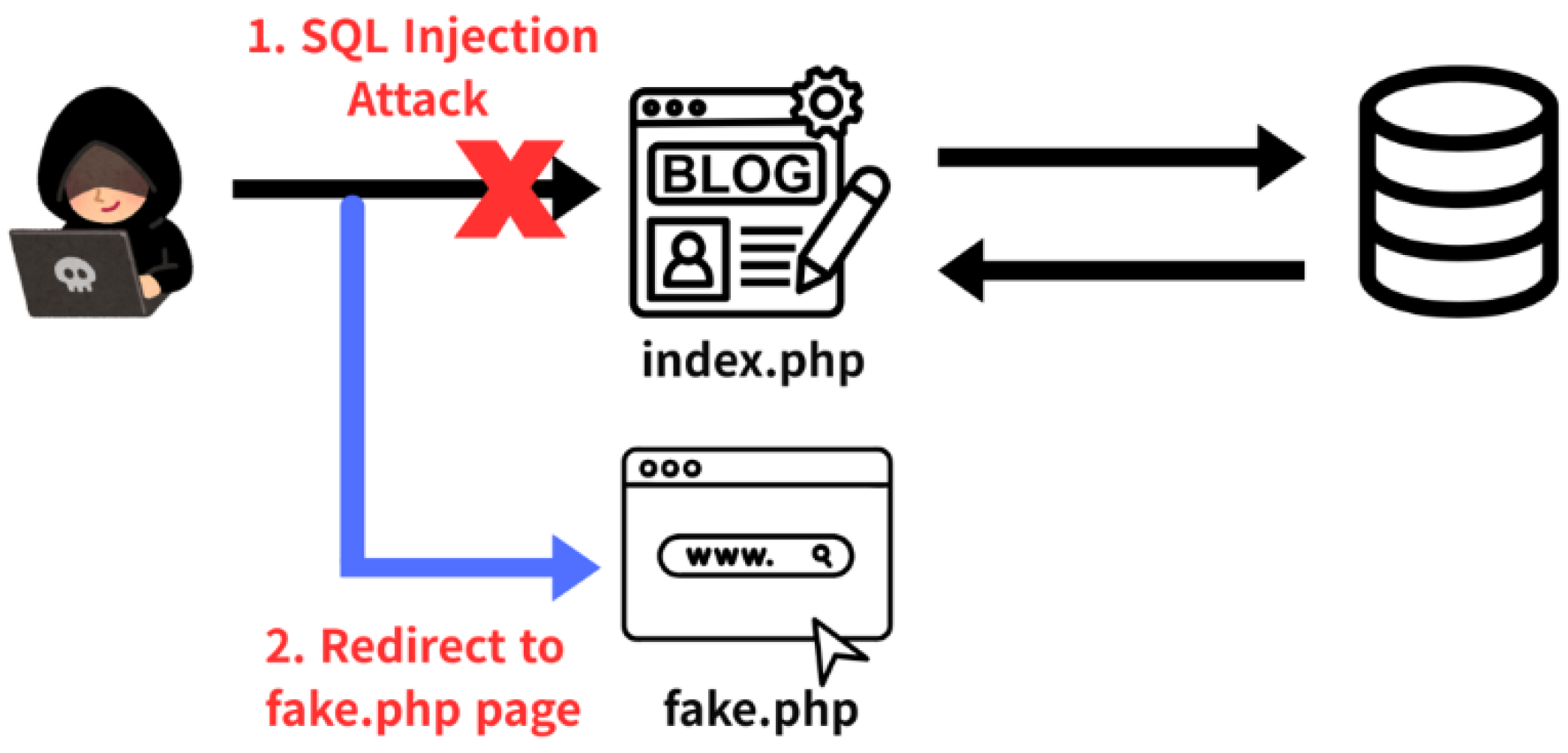
3.3. Attacker Redirection Technique (ART)
4. Experiment and Analysis
4.1. PHP Data Object (PDO) Defense
| Algorithm 2: PDO-based SQL Injection Defense with Prepared Statements |
| 1: Establish PDO connection with host, database name, charset, and credentials 2: Set the PDO error mode to ERRMODE_EXCEPTION 3: Read input userid from the HTTP request 4: Prepare SQL query: SELECT * FROM member WHERE userid = : userid 5: Bind parameter : userid with the input value (string type) 6: Execute the prepared statement 7: Fetch the query result 8: If a record exists, return the result; otherwise, return “not found.” |
| Algorithm 3: PDO-based User Authentication Process |
| 1: Prepare SQL query using PDO with parameter binding: SELECT * FROM member WHERE id = : id LIMIT 1 2: Execute query with the user-provided id value 3: Fetch one row from the result set 4: Check user existence:
|
| Algorithm 4: Filtering-based Protection Technique |
1: Define injection patterns to detect suspicious input:
3: Check user input against the current pattern using regular expression matching 4: If a match is found:
|
4.2. Input Pattern Validation Technique for Injection Prevention
4.3. Attacker Redirection Technique via Input Filtering

4.4. Comparative Analysis of Three Methods
4.4.1. Comparison and Analysis Between Techniques
4.4.2. Integration of Practical Application and Combination Strategies
4.4.3. Security Operations Strategy Proposal
4.4.4. Limitations and Applicability
- -
- PDO (Prepared Statements): Requires extensive code refactoring in legacy systems that rely on string-based SQL queries; limited flexibility with dynamic query structures such as variable table or column names.
- -
- PVT (Pattern Validation Technique): Vulnerable to bypass via obfuscated or encoded payloads; may trigger false positives when legitimate inputs contain reserved SQL keywords.
- -
- ART (Attacker Redirection Technique): Not a structural defense when deployed in isolation; effectiveness is reduced if malicious queries are executed before redirection takes place.
- -
- Employing a layered defense strategy, where PDO is used as the primary structural safeguard, PVT serves as a lightweight pre-filter, and ART functions as a deception-based deterrent.
- -
- Continuously updating pattern lists and using advanced regex or lexical analysis to reduce bypass attempts and false positives in PVT.
- -
- Integrating machine learning–based anomaly detection models and Web Application Firewalls (WAFs) to complement traditional defenses and adapt to new attack variants.
- -
- Ensuring secure coding practices and developer training to reduce misconfigurations and strengthen the overall defense framework.
- -
- E-commerce and financial platforms: Protecting sensitive user information such as payment details, which are prime targets for SQL Injection.
- -
- Online reservation and service portals: Reservation systems and ticketing platforms that often rely on PHP–MySQL backends can benefit from lightweight yet effective defense layers.
- -
- Educational and organizational intranet systems: University portals, learning management systems, and internal bulletin boards where legacy code and resource constraints are common.
4.4.5. Comparative Discussion with Previous Studies
4.5. Threat Model and Evaluation Criteria
- -
- Union-based injections (e.g., UNION SELECT …) for extracting structured records,
- -
- Boolean-based injections that rely on conditional logic to infer database content,
- -
- Tautology-based payloads such as OR 1 = 1 to force query success, and
- -
- Obfuscated payloads that use encoding or alternative representations to evade detection.
- -
- True Positives (TP): correctly detected and blocked attack attempts,
- -
- False Positives (FP): legitimate inputs incorrectly flagged as malicious,
- -
- False Negatives (FN): undetected injections that succeeded,
- -
- False Positive Rate (FPR): FP/(FP + TN),
- -
- Accuracy: (TP + TN)/(TP + FP + FN + TN), and
- -
- Latency: additional processing time (ms) introduced by each defense technique.
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| PDO | PHP Data Object |
| PVT | Pattern Validation Technique |
| ART | Attacker Redirection Technique |
| SQLi | SQL Injection |
| SSRF | Server-Side Request Forgery |
| CSRF | Cross-Site Request Forgery |
| XSS | Cross-Site Scripting |
| WAFs | Web Application Firewalls |
Appendix A. Vulnerable Code, Attack Payload, and Secure Code
Appendix A.1. Vulnerable Authentication Example (Minimal, Reproducible)
- /* Appendix A.1: Vulnerable login example (reproduction) */
- $id = $_POST[′userid′];
- $pw = $_POST[′userpw′];
- $sql = “SELECT * FROM member WHERE userid = ′$id′”;
- $result = mysqli_query($conn, $sql);
- $row = mysqli_fetch_assoc($result);
- if ($row) {
- // Vulnerability: the returned username is trusted and used to create a session
- $_SESSION[′username′] = $row[′username′];
- header(“Location: index.php”);
- exit;
- }
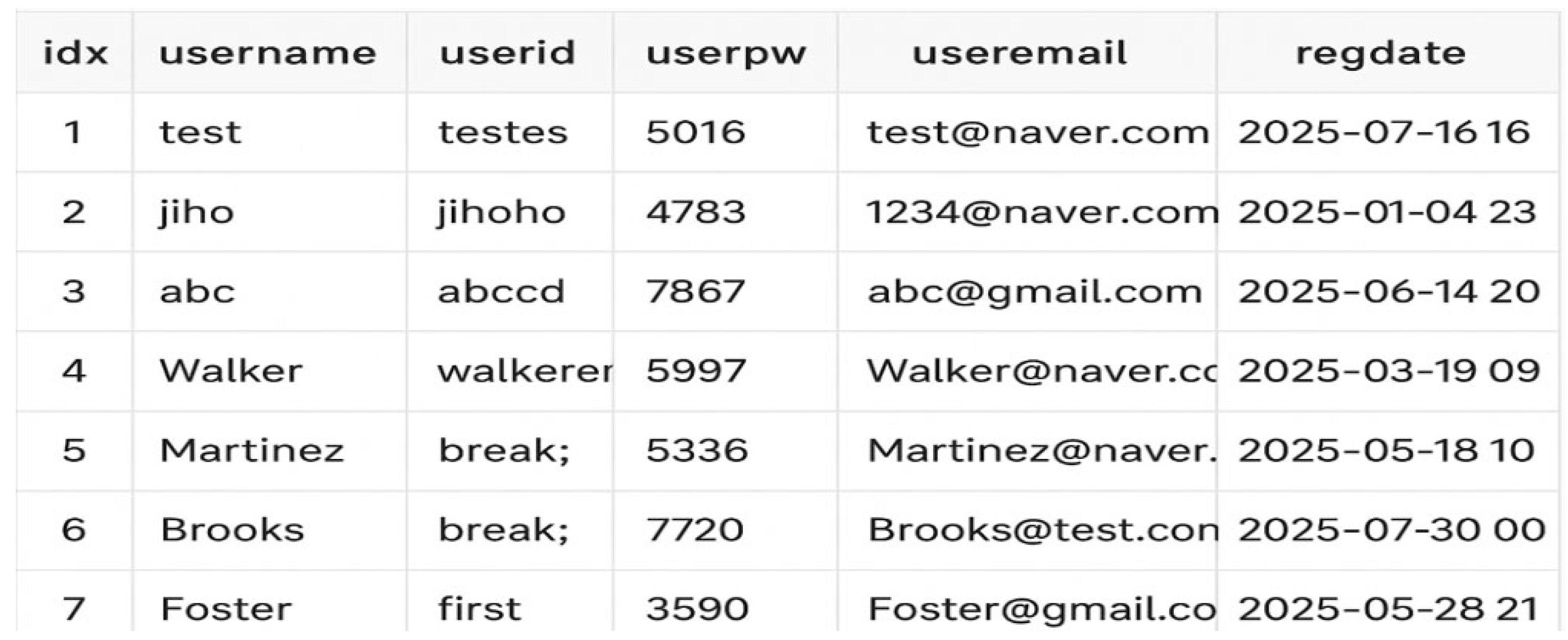
Appendix A.2. Typical UNION Payload Used in Experiments(Example)
- ID input:
- ‘UNION SELECT 1, ‘admin’, ‘dummy’, ‘dummy’, ‘dummy@example.com’, ‘2024-01-01’ --
- Password: (any value)
Appendix A.3. Secure Implementation Example (PDO + Password Verification)
- $stmt = $pdo->prepare(‘SELECT userpw, username FROM member WHERE userid = :id LIMIT 1’);
- $stmt->execute([‘:id’ => $id]);
- $row = $stmt->fetch(PDO::FETCH_ASSOC);
- if ($row && password_verify($pw, $row[‘userpw’])) {
- $_SESSION[‘username’] = $row[‘username’];
- // successful login
- } else {
- // login failure
- }
References
- Bertino, E.; Sandhu, R. Database security—Concepts, approaches, and challenges. IEEE Trans. Dependable Secur. Comput. 2005, 2, 2–19. [Google Scholar] [CrossRef]
- Nasereddin, M.; Alkhamaiseh, A.; Qasaimeh, M.; Al-Qassas, R. A systematic review of detection and prevention techniques of SQL injection attacks. Inf. Secur. J. Glob. Perspect. 2021, 32, 252–265. [Google Scholar] [CrossRef]
- Appelt, D.; Panichella, A.; Briand, L. Automatically repairing web application firewalls based on successful SQL injection attacks. In Proceedings of the 2017 IEEE 28th International Symposium on Software Reliability Engineering (ISSRE), Toulouse, France, 23–26 October 2017; pp. 339–350. [Google Scholar]
- Alkhalaf, A.; Alkhatib, B.; Ghanem, S. SQL Injection Attack Detection Using Machine Learning Techniques. In Proceedings of the 7th International Conference on Advanced Computing and Intelligent Engineering, Cuttack, India, 23–24 December 2022; pp. 145–156. [Google Scholar]
- Jemal, I.; Cheikhrouhou, O.; Hamam, H.; Mahfoudhi, A. Sql injection attack detection and prevention techniques using machine learning. Int. J. Appl. Eng. Res. 2020, 15, 569–580. [Google Scholar]
- Bisht, P.; Venkatakrishnan, V.N. XSS-GUARD: Precise dynamic prevention of cross-site scripting attacks. In Proceedings of the International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, Paris, France, 10–11 July 2008; pp. 23–43. [Google Scholar]
- Tasdemir, K.; Khan, R.; Siddiqui, F.; Sezer, S.; Kurugollu, F.; Yengec-Tasdemir, S.B.; Bolat, A. Advancing SQL injection detection for high-speed data centers: A novel approach using cascaded NLP. arXiv 2023, arXiv:2312.13041. [Google Scholar] [CrossRef]
- Dasari, N.S.; Badii, A.; Moin, A.; Ashlam, A. Enhancing SQL Injection Detection and Prevention Using Generative Models. arXiv 2025, arXiv:2502.04786. [Google Scholar] [CrossRef]
- Kakisim, A.G. A deep learning approach based on multi-view consensus for SQL injection detection. Int. J. Inf. Secur. 2024, 23, 1541–1556. [Google Scholar] [CrossRef]
- Viegas, J.; Halfond, W.; Orso, A. A classification of SQL-injection attacks and countermeasures. In Proceedings of the IEEE International Symposium Secure Software Engineering 2006, Arlington, VA, USA, 16–17 March 2006; pp. 13–15. [Google Scholar]
- Yash, V. SQL Injection Attack Detection Using Naive Bayes Classifier. Doctoral Dissertation, Institute of Technology, Sydney, Australia, 2022. [Google Scholar]
- Arasteh, B.; Aghaei, B.; Farzad, B.; Arasteh, K.; Kiani, F.; Torkamanian-Afshar, M. Detecting SQL injection attacks by binary gray wolf optimizer and machine learning algorithms. Neural Comput. Appl. 2024, 36, 6771–6792. [Google Scholar] [CrossRef]
- Das, D.; Sharma, U.; Bhattacharyya, D.K. An approach to detection of SQL injection attack based on dynamic query matching. Int. J. Comput. Appl. 2010, 1, 28–34. [Google Scholar]
- Hasan, M.; Balbahaith, Z.; Tarique, M. Detection of SQL injection attacks: A machine learning approach. In Proceedings of the 2019 International Conference on Electrical and Computing Technologies and Applications (ICECTA), Ras Al Khaimah, United Arab Emirates, 19–21 November 2019; pp. 1–6. [Google Scholar]
- Muntaha, S.T.; Ashraf, F.; Shahzad, I.; Iqbal, J. DESIGNING AN ADAPTIVE HONEYPOT FOR ADVANCED CYBERSECURITY THREAT DETECTION. Spectr. Eng. Sci. 2025, 3, 816–847. [Google Scholar]
- Morić, Z.; Dakić, V.; Regvart, D. Advancing Cybersecurity with Honeypots and Deception Strategies. Informatics 2025, 12, 14. [Google Scholar] [CrossRef]
- Halfond, W.G.; Orso, A. AMNESIA: Analysis and monitoring for NEutralizing SQL-injection attacks. In Proceedings of the IEEE/ACM International Conference on Automated Software Engineering, Long Beach, CA, USA, 7–11 November 2005; pp. 174–183. [Google Scholar]
- Muhammad, T.; Ghafory, H. SQL Injection Attack Detection Using Machine Learning Algorithm. Mesopotamian J. Cybersecur. 2022, 2022, 5–17. [Google Scholar] [CrossRef]
- Alarfaj, F.K.; Khan, N.A. Enhancing the Performance of SQL Injection Attack Detection through Probabilistic Neural Networks. Appl. Sci. 2023, 13, 4365. [Google Scholar] [CrossRef]
- Souza, M.S.; Ribeiro, S.E.S.B.; Lima, V.C.; Cardoso, F.J.; Gomes, R.L. Combining Regular Expressions and Machine Learning for SQL Injection Detection in Urban Computing. J. Internet Serv. Appl. 2024, 15, 103–111. [Google Scholar] [CrossRef]


| Item | PHP Data Objects (PDO) | Input Pattern Validation | Attacker Redirection |
|---|---|---|---|
| Basic Principle | Separates SQL query structure from user input using prepared statements. | Blocks suspicious patterns using regex for SQL keywords/special characters. | Redirects user to a fake page upon detecting malicious input. |
| Security Strength | Very high–provides structural protection. | Medium–depends on detection pattern quality. | Low–ineffective if detection fails. |
| Input Validation Method | Parameter binding with explicit type validation. | Regex-based keyword/pattern matching using preg_match. | Pattern check followed by conditional redirection. |
| Bypass Possibility | Low (if implemented correctly). | Present–obfuscated inputs may evade detection. | Present–attacker may detect redirection. |
| Accuracy (False Positives/Negatives) | High–clear separation between data and query. | Low–risks of false positives and missed detections. | Low–depends on pattern quality. |
| Implementation Difficulty | Medium to high–may require restructuring code. | Low–simple regex implementation. | Low–basic conditional logic. |
| Maintenance Overhead | High–requires consistent PDO usage. | Medium–regular updates to patterns needed. | Medium–managing fake pages and policies. |
| Integration with Existing Systems | Difficult–legacy code migration required. | Easy–can be injected into existing logic. | Easy–minimal modification required. |
| Performance Impact | Low–may improve due to query plan reuse. | Medium–many regex checks may slow down system. | Low–redirection incurs minimal cost. |
| Logging and Response Capability | Limited–requires custom logging. | Possible–log filtered attempts. | Excellent–logs and behavior analysis enabled. |
| Key Advantages | Strong structural defense, DBMS compatibility, auto escaping. | Easy to implement, preemptive blocking, client-side possible. | Disrupts attacker behavior, supports logging and analysis. |
| Key Disadvantages | Steep learning curve, hard with dynamic queries, migration effort. | Bypassable, false positives, needs frequent update. | No structural defense, ineffective if undetected. |
| Technique | Blocking Success Rate | False Positives | Performance Impact | Notes |
|---|---|---|---|---|
| PDO | ~100% (all tested UNION/Boolean/Tautology queries blocked) | None observed | Low (query plan reuse improves efficiency) | Strong structural defense, requires refactoring legacy code |
| PVT | 80–85% (most keyword-based injections blocked; obfuscation bypassed some cases) | Occasional blocking of legitimate inputs with “union” in username field | Medium (regex checks on input) | Lightweight, requires regular updates to patterns |
| ART | 70–75% (attacks redirected to decoy; some undetected queries passed) | None | Very low | Effective as a deterrent/logging method, but not standalone |
| Technique | Advantages | Disadvantages |
|---|---|---|
| PDO (PHP Data Objects) |
|
|
| PVT (Pattern Validation Technique) |
|
|
| ART (Attacker Redirection Technique) |
|
|
| Technique | TP | FP | FN | FPR | Accuracy | Latency (ms) | Notes |
|---|---|---|---|---|---|---|---|
| PDO | 50 | 0 | 0 | 0% | 100% | +2–3 | Strong structural defense |
| PVT | 42 | 3 | 5 | ~6.7% | ~91% | +5–6 | Regex bypass possible |
| ART | 38 | 0 | 12 | 0% | ~88% | +1–2 | Logging & deterrence only |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Choi, J.; Jung, Y.-A.; Ko, H. Comparative Analysis of SQL Injection Defense Mechanisms Based on Three Approaches: PDO, PVT, and ART. Appl. Sci. 2025, 15, 12351. https://doi.org/10.3390/app152312351
Choi J, Jung Y-A, Ko H. Comparative Analysis of SQL Injection Defense Mechanisms Based on Three Approaches: PDO, PVT, and ART. Applied Sciences. 2025; 15(23):12351. https://doi.org/10.3390/app152312351
Chicago/Turabian StyleChoi, Jiho, Young-Ae Jung, and Hoon Ko. 2025. "Comparative Analysis of SQL Injection Defense Mechanisms Based on Three Approaches: PDO, PVT, and ART" Applied Sciences 15, no. 23: 12351. https://doi.org/10.3390/app152312351
APA StyleChoi, J., Jung, Y.-A., & Ko, H. (2025). Comparative Analysis of SQL Injection Defense Mechanisms Based on Three Approaches: PDO, PVT, and ART. Applied Sciences, 15(23), 12351. https://doi.org/10.3390/app152312351








