Research on a Robust Traceability Method for the Assembly Manufacturing Supply Chain Based on Blockchain
Abstract
1. Introduction
- (1)
- The assembly and manufacturing supply chain involves multiple production stages. Under the cloud model, manufacturing enterprises are widely and highly dispersed geographically. Each enterprise usually stores production information independently in local databases, lacking unified data standards and cross-enterprise information sharing mechanisms. This leads to a severe “information island” phenomenon, which restricts the effective improvement of the overall traceability capability of the supply chain.
- (2)
- In the cloud mode, manufacturing enterprises generally rely on data collection devices to integrate multi-source heterogeneous production data and manage it centrally through a centralized database. They also achieve information interconnection and interoperability through cloud platforms. However, such a centralized architecture is vulnerable to malicious attacks during data storage and transmission, posing security risks such as data leakage, tampering, or loss, and thus is difficult to meet the high-trustworthiness requirements for data management.
- (3)
- In the distributed collaborative manufacturing model, as the manufacturing process of products continues to advance, each manufacturing node continuously generates a large amount of streaming data. There is an urgent need for strong data storage capabilities and efficient retrieval mechanisms to extract key information. Currently, the on-chain query function of blockchain systems is relatively limited, and the retrieval efficiency is low. Especially when quickly locating specific production stages or equipment status, the response is slow, which may lead to delays in obtaining key information and thereby affect the real-time monitoring and decision-making efficiency of the manufacturing process.
- (1)
- A research framework for a trusted traceability method of assembly manufacturing supply chain based on blockchain is constructed to address the problems of centralized storage being prone to tampering and low efficiency in cross-enterprise data traceability in the traceability process of the assembly manufacturing supply chain under the cloud mode. Starting from three dimensions: secure storage of traceability data, consensus mechanism of the traceability network, and efficient traceability verification, a trusted, efficient, and auditable traceability of the assembly manufacturing supply chain in the cloud environment is achieved.
- (2)
- In light of the operational characteristics of the assembly manufacturing supply chain in the cloud environment and the demand for secure data storage, this paper designs a traceability system for the assembly manufacturing supply chain based on a master–slave multi-chain architecture, and uses the Channel isolation technology to protect the data privacy among different business links. On this basis, a blockchain-based traceability data security storage model is proposed: the SHA-256 hash algorithm is adopted on the chain to encrypt the sensitive information of enterprises, and the ECDSA digital signature algorithm is combined to authenticate the on-chain data, ensuring the authenticity and non-repudiation of the data source; while off-chain, detailed traceability content is stored through traditional databases, achieving the collaborative storage of on-chain metadata and off-chain detailed data. This solution effectively integrates the tamper-proof advantage of blockchain with the high-capacity storage capability of traditional databases, ensuring the security and integrity of core data while alleviating the storage pressure of the blockchain system.
- (3)
- In response to the practical demand for efficient traceability in industrial scenarios, this paper proposes a high-efficiency traceability verification method for assembly manufacturing supply chains based on a blockchain and a hierarchical storage architecture. In the main traceability chain, the Bloom filter in the B-Merkle structure is utilized to screen out the problem links related to the target traceability code and extract the corresponding block index. In the sub-chains, a Skip List multi-level index structure is introduced to accelerate the acquisition of specific traceability content through a parallel retrieval mechanism, significantly reducing query latency. Off-chain, the elliptic curve digital signature algorithm is used to verify the hash value of the on-chain data and compare it with the hash value of the original off-chain data to complete the dual verification of the integrity and authenticity of the traceability data. Experimental results show that the proposed traceability verification method has high retrieval efficiency and good scalability, and can effectively meet the actual demand for rapid and accurate traceability in assembly manufacturing supply chains.
2. Related Technologies
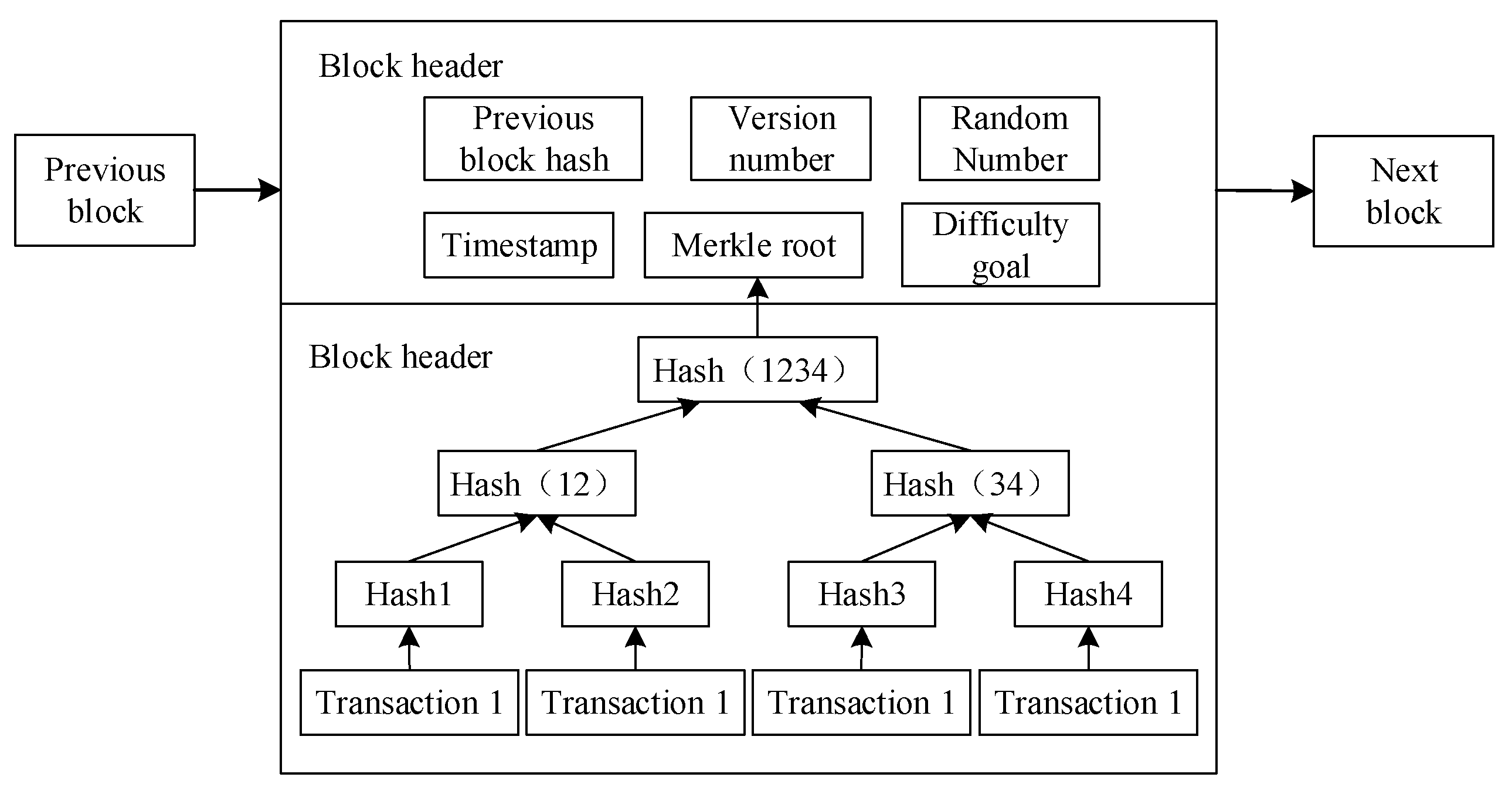
2.1. Blockchain
2.2. Consensus Mechanism
2.3. Improved EG-PBFT Consensus Algorithm
2.4. Smart Contract
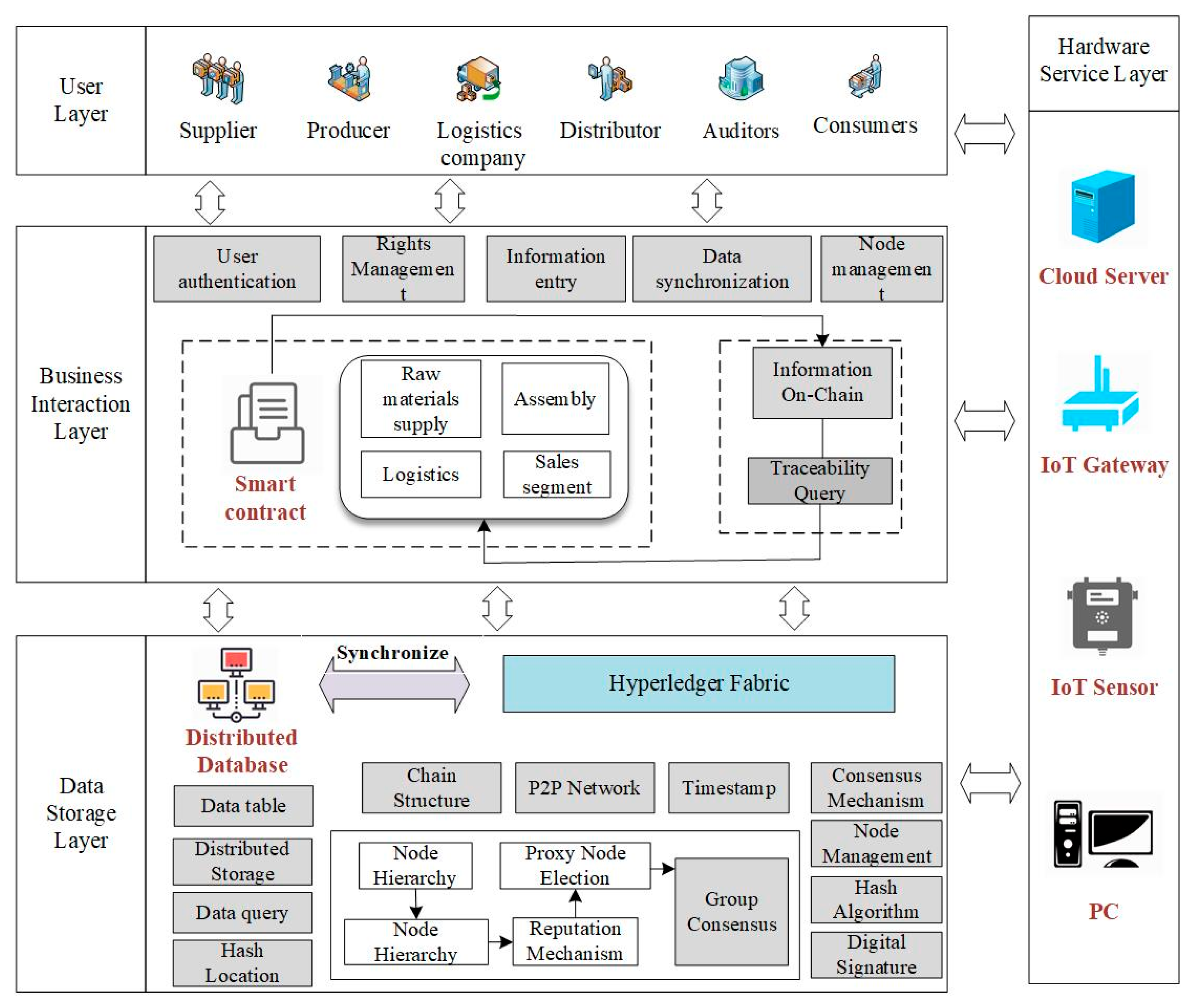
3. Design of a Traceability Framework for Assembly Manufacturing Supply Chain
3.1. Hardware Support Layer (Data Acquisition Layer)
3.2. Data Storage Layer
3.3. Business Functional Layer
3.4. Application Layer
4. Key Technologies for Achieving Traceability in Assembly Manufacturing Supply Chains
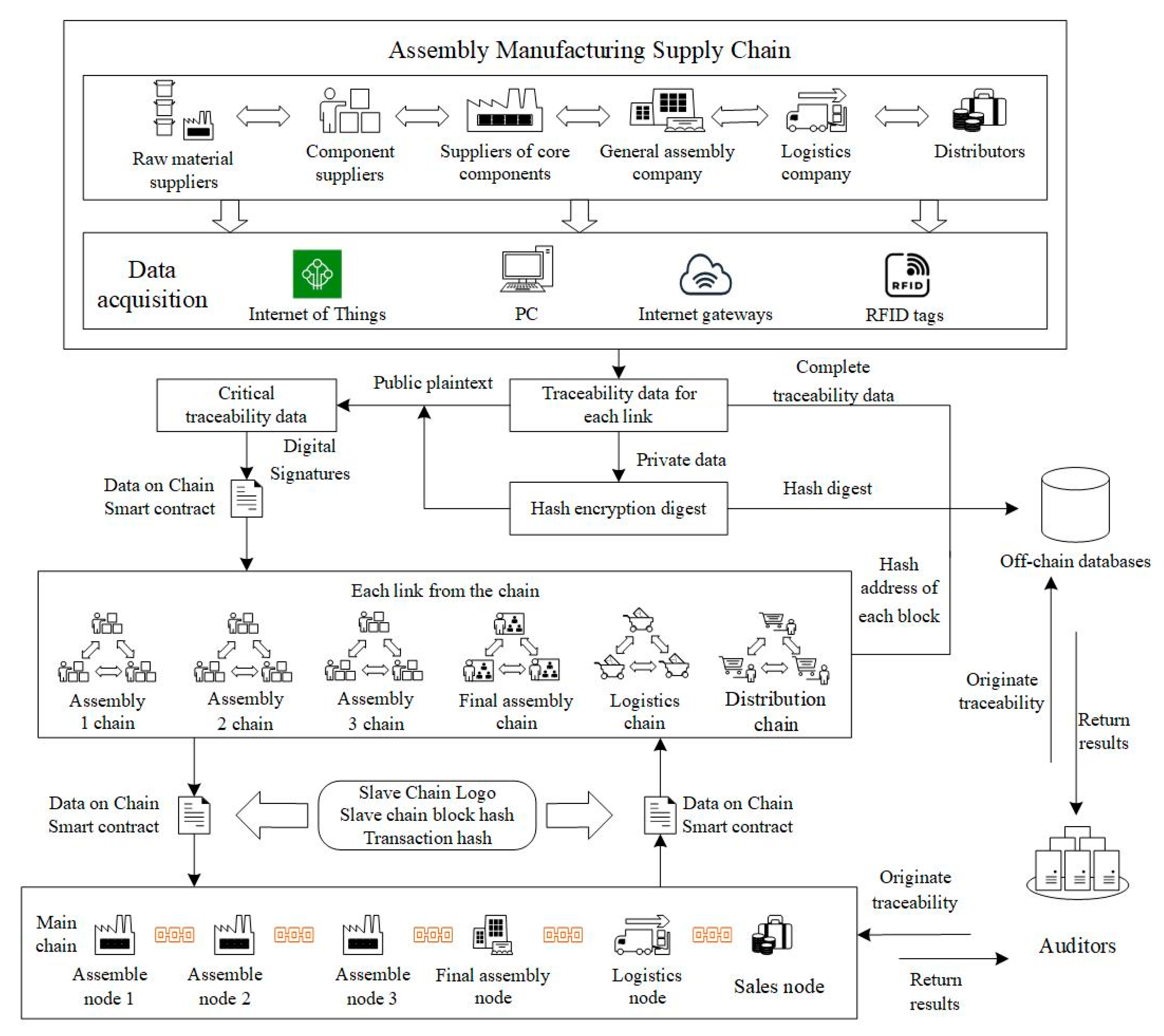
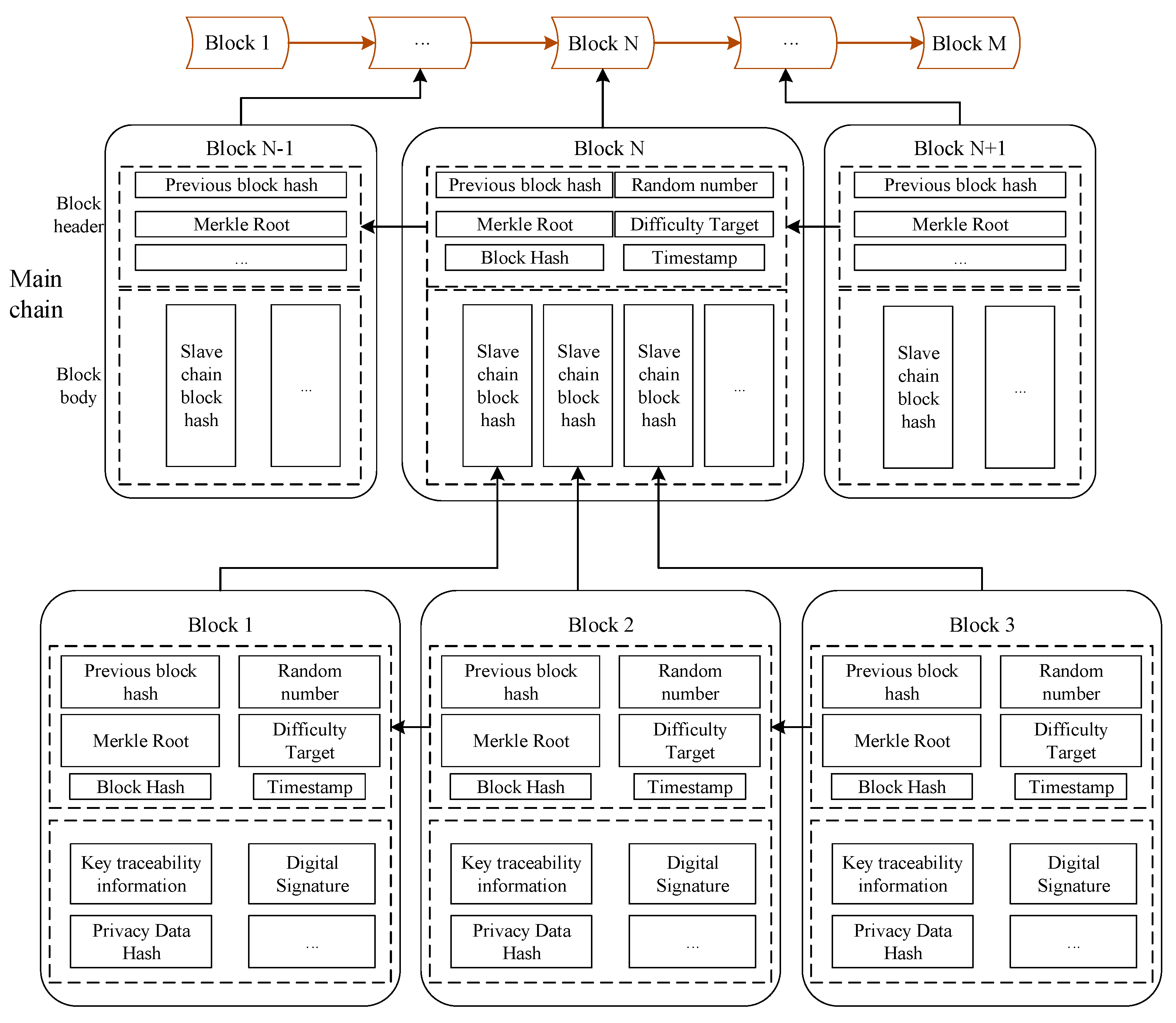
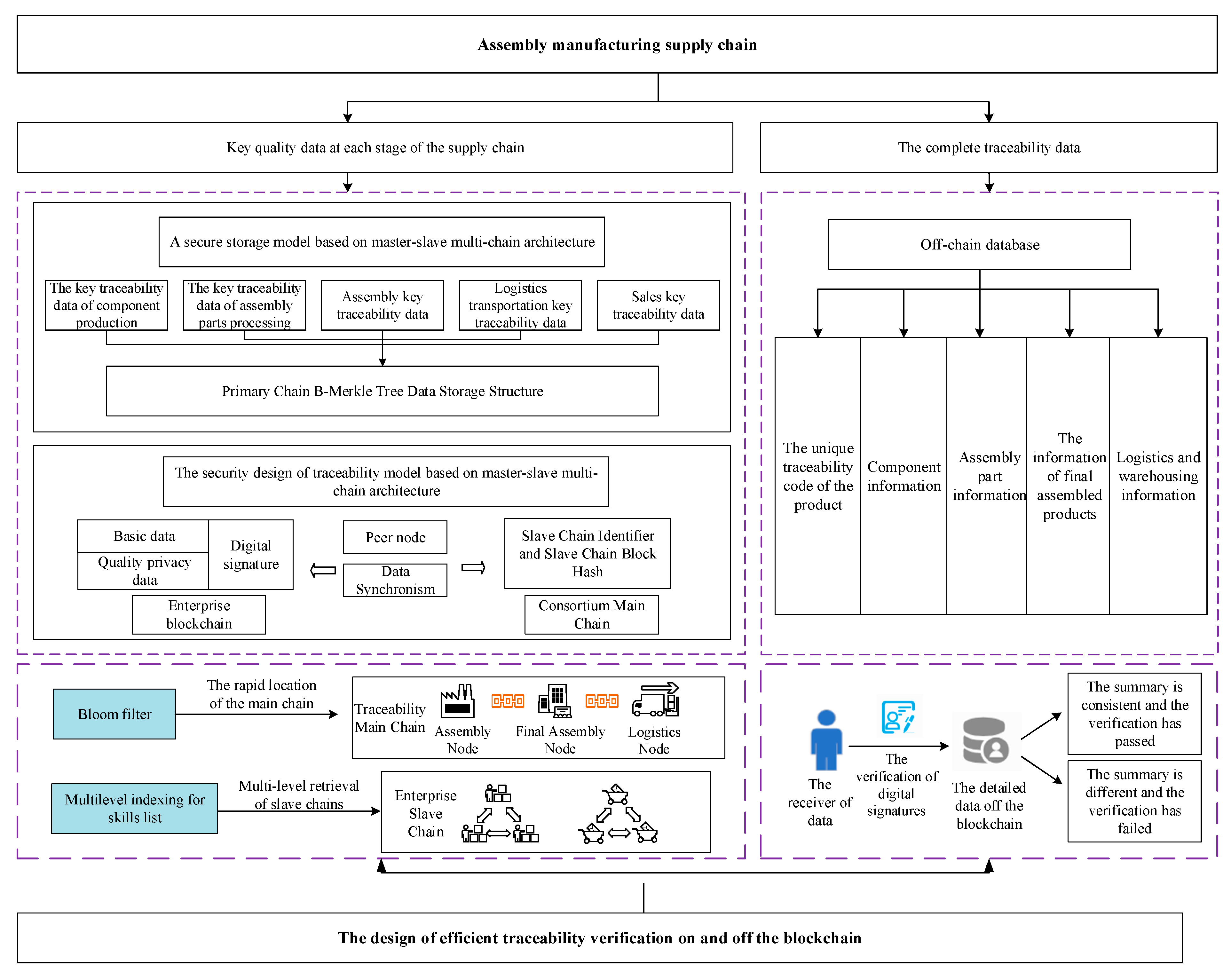
4.1. The Architecture of Multi-Chain Traceability with a Master–Slave Structure
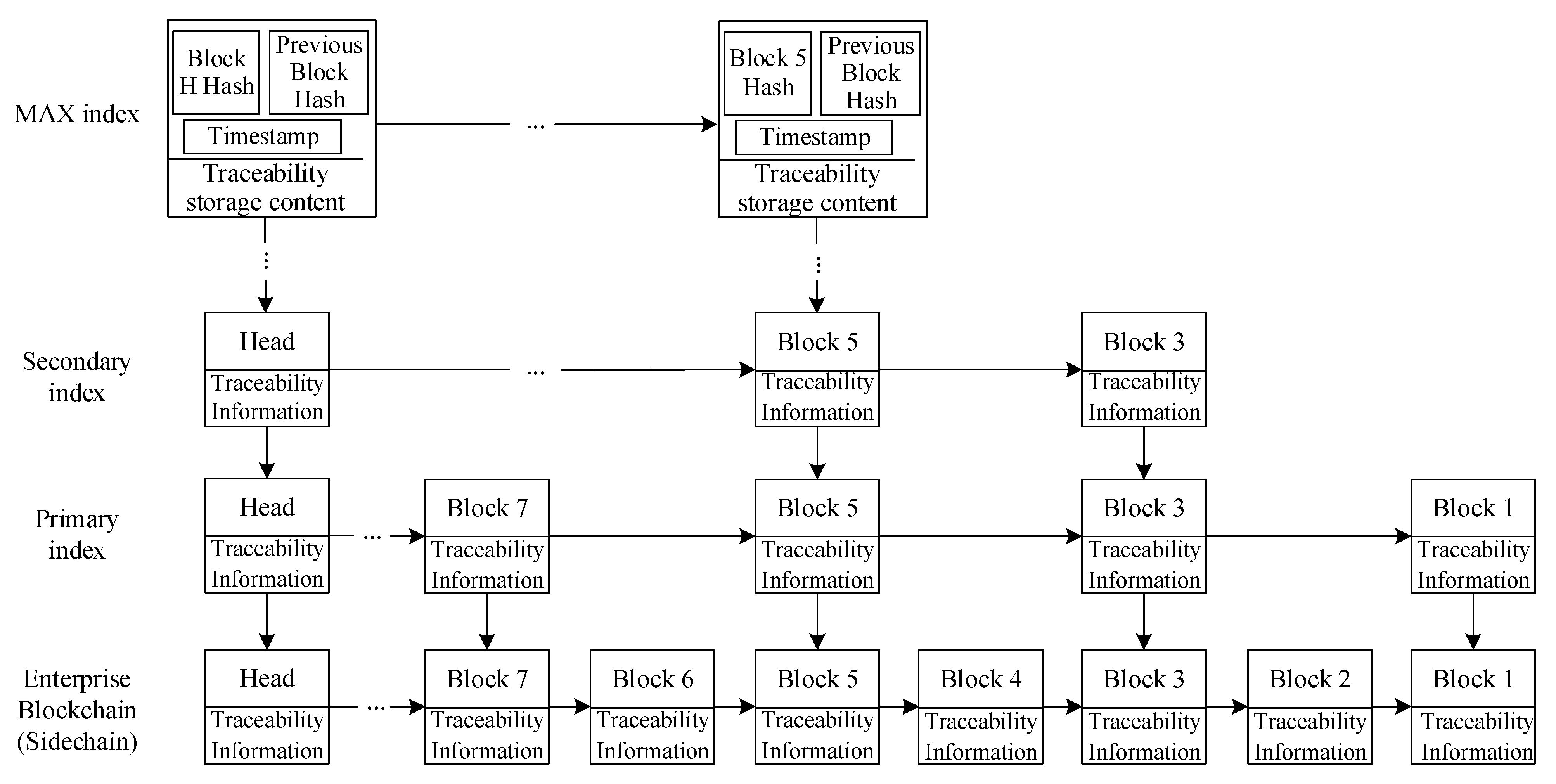
4.2. Hierarchical Storage Model
4.3. Efficient Traceability Verification Model
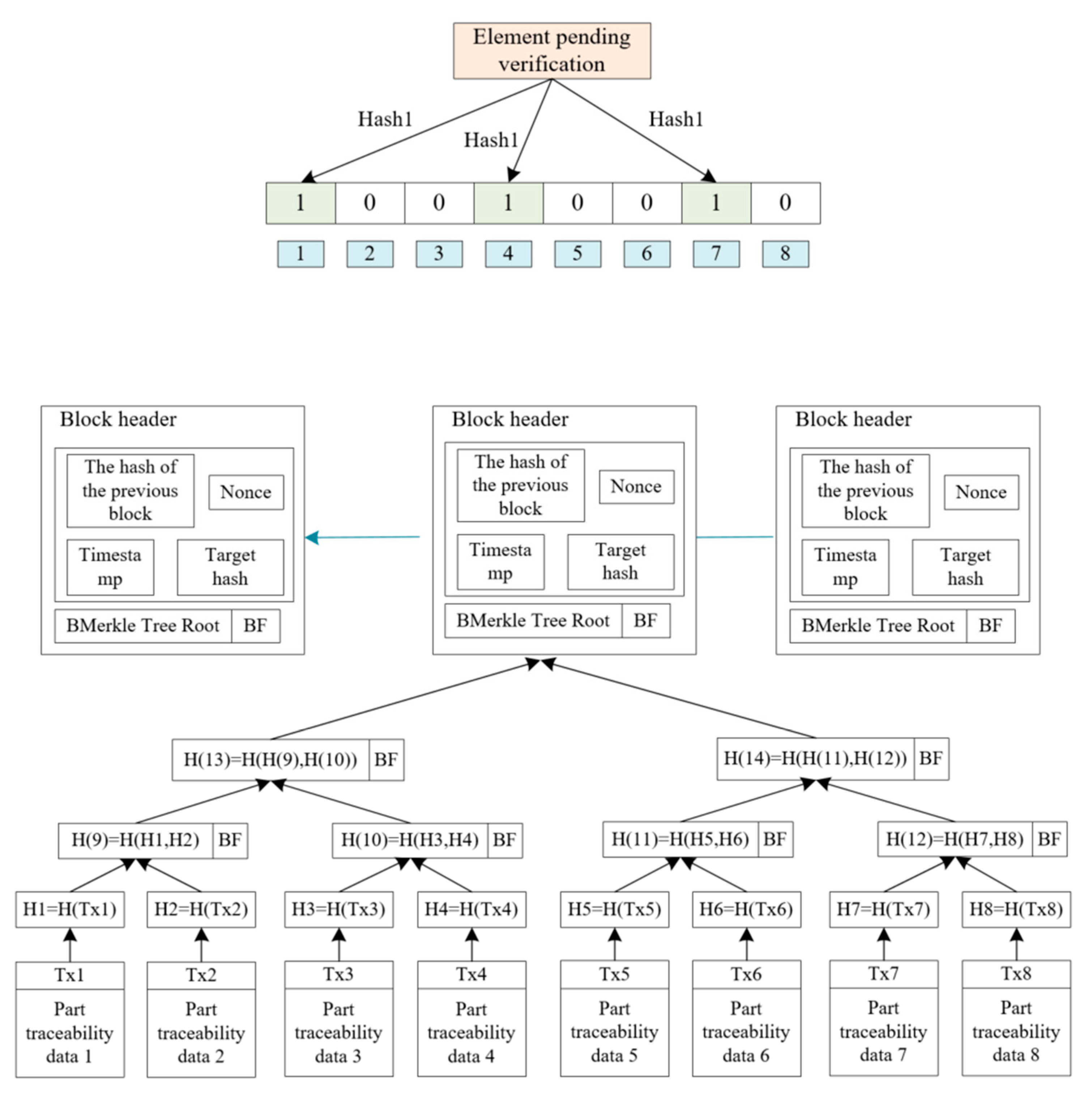
4.3.1. Efficient Retrieval on the Blockchain
- (1)
- Block structure based on B-Merkle tree
- (2)
- Fast query based on Skip List
- (3)
- Efficient on-chain retrieval
4.3.2. Off-Chain Data Verification
- (1)
- The inspector enters the unique traceability source code ZID of the product, retrieves the traceable transaction set Tc from the blockchain, and extracts the transaction hash address, digital signature = ECDSA(h(M),dM), and the enterprise’s public key Qm.
- (2)
- The plaintext information corresponding to the Tc in the local database should be queried based on the transaction hash address stored on the chain. If the transaction address exists, detailed traceability information N can be extracted from the local database.
- (3)
- The signature (r,s) is verified to be an integer within the interval [1, n − 1]. If it meets this criterion, Hash(N) is computed using the same hash algorithm employed in the signature step for local detailed traceability information N.
- (4)
- The inspector verifies the Qm digital signature by validating it against the public key provided by the enterprise, in order to ascertain the reliability of the message source. Initially, input message summary h(m), signature value public key QA(x,y), signature(r,s) and base point G(x,y); Calculate w = s−1modn, u1 = (h(m) × w)modn, u2 = rwmodn, and R = (xR,yR) = u1G + u2QA. If R = 0, then the signature is deemed invalid and rejected. If v = xRmodn, only when v = r holds true can it be proven that the corresponding private key generated the signature and thus affirming the trustworthiness of the data source. Upon successful verification, Hash(M) is returned.
- (5)
- The consistency between Hash(M) and Hash(N) determines the integrity of data N in the chain; if they match, it verifies that N has not been tampered with, whereas any discrepancy indicates a change in N and renders the traceable data unreliable.
5. Traceability Scheme Implementation
5.1. Traceability Data Acquisition
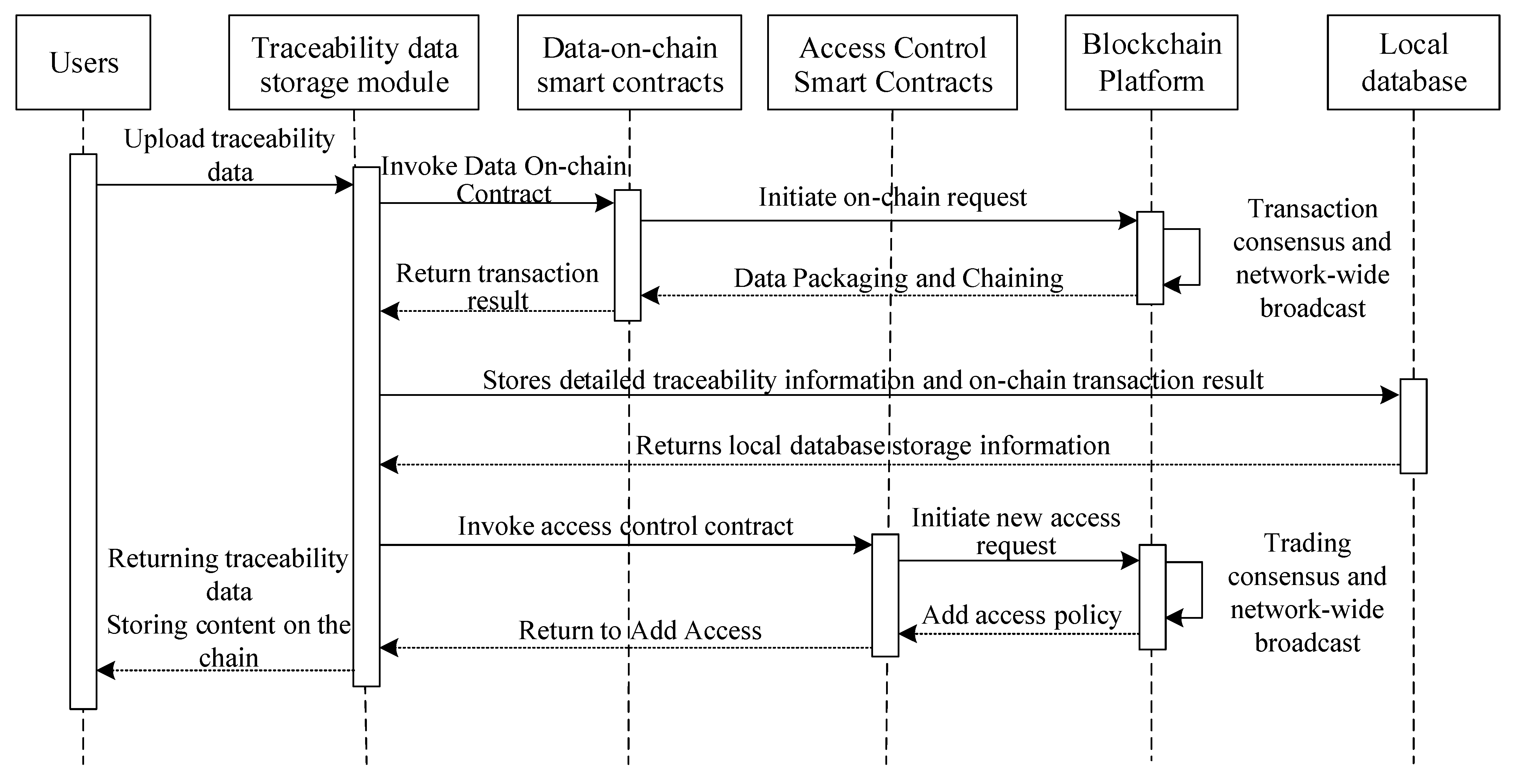
5.2. Traceable Data Storage Uplink
5.3. Efficient Examination of Traceability Data
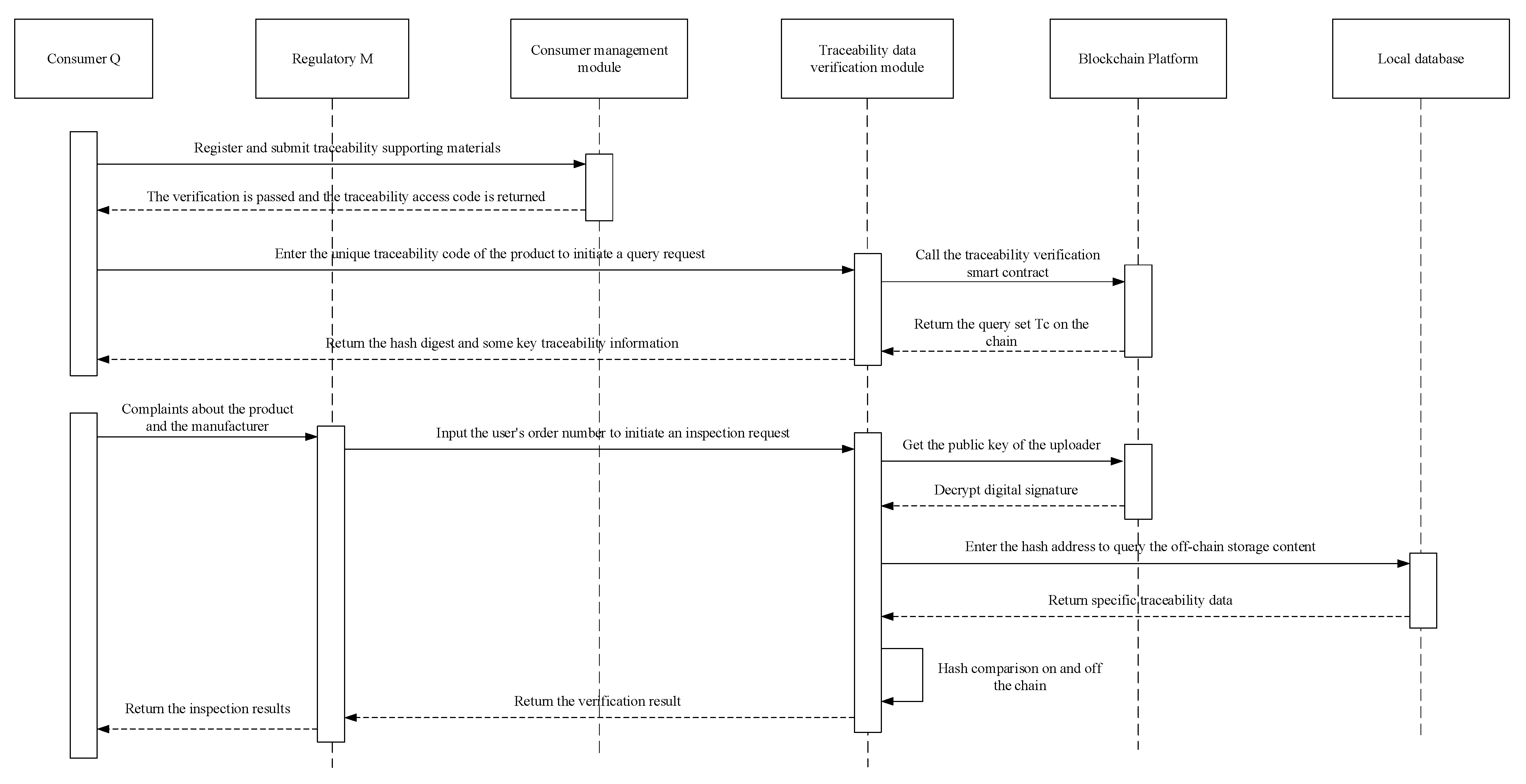
- (1)
- The consumers log into the traceability system and provide personal information, such as their name and contact details, through the registration interface. They also submit relevant supporting documents required for traceability qualification certification, including the purchase order number, order creation time, transaction location, etc.
- (2)
- After receiving consumer support materials, the system manager verifies the authenticity of the information. Once the audit is successfully completed, a unique traceability access code is issued to the consumer, enabling them to enter the traceability data inspection module using this code.
- (3)
- The consumers input the unique traceability code ZID to inquire about product parameters, component origins, and logistics information. This includes crucial traceability data stored on the blockchain, such as hash values and transaction hash addresses. Additionally, they have the ability to file complaints regarding problematic products and manufacturers.
- (4)
- After receiving the user’s complaint, the supervisor will investigate the specific quality information of the batch of products produced by the enterprise in question based on the order number and specific content of the complaint. The backend system can retrieve comprehensive traceability data through the transaction address stored in the background database.
- (5)
- The regulator conducts an anti-tamper check on the complete traceability data within the blockchain, and verifies whether the hash summary stored in the blockchain aligns with the hash value derived from decrypting the digital signature and extracting complete traceability information from the local database. In case of inconsistency, it indicates potential data tampering, thereby determining that the credibility of enterprise’s locally stored quality traceability information is compromised, necessitating immediate initiation of responsibility investigation procedures.
6. Case Analysis
6.1. Case Validation
6.2. Performance Analysis of the Scheme
- (1)
- Time complexity analysis
- (2)
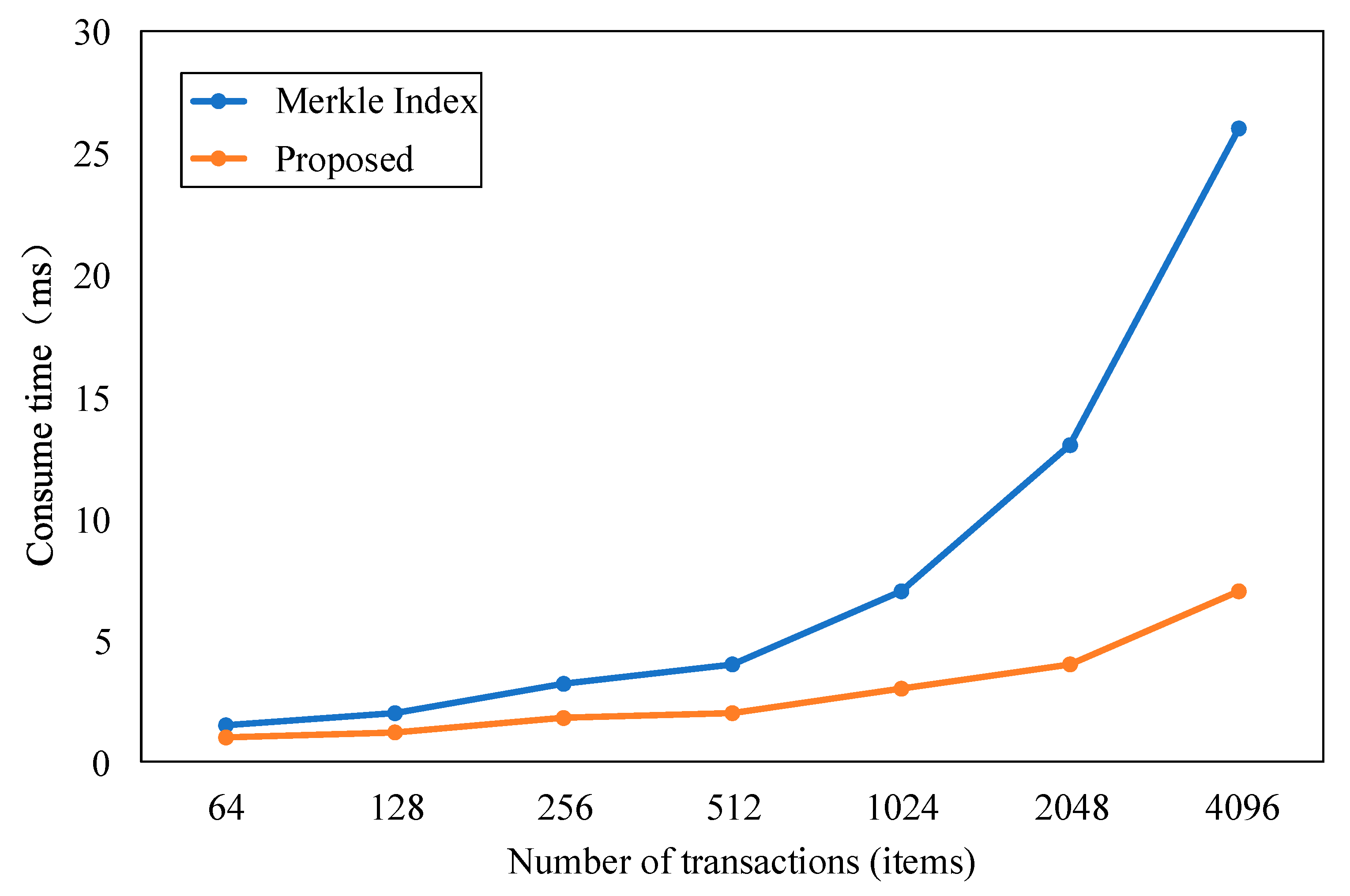
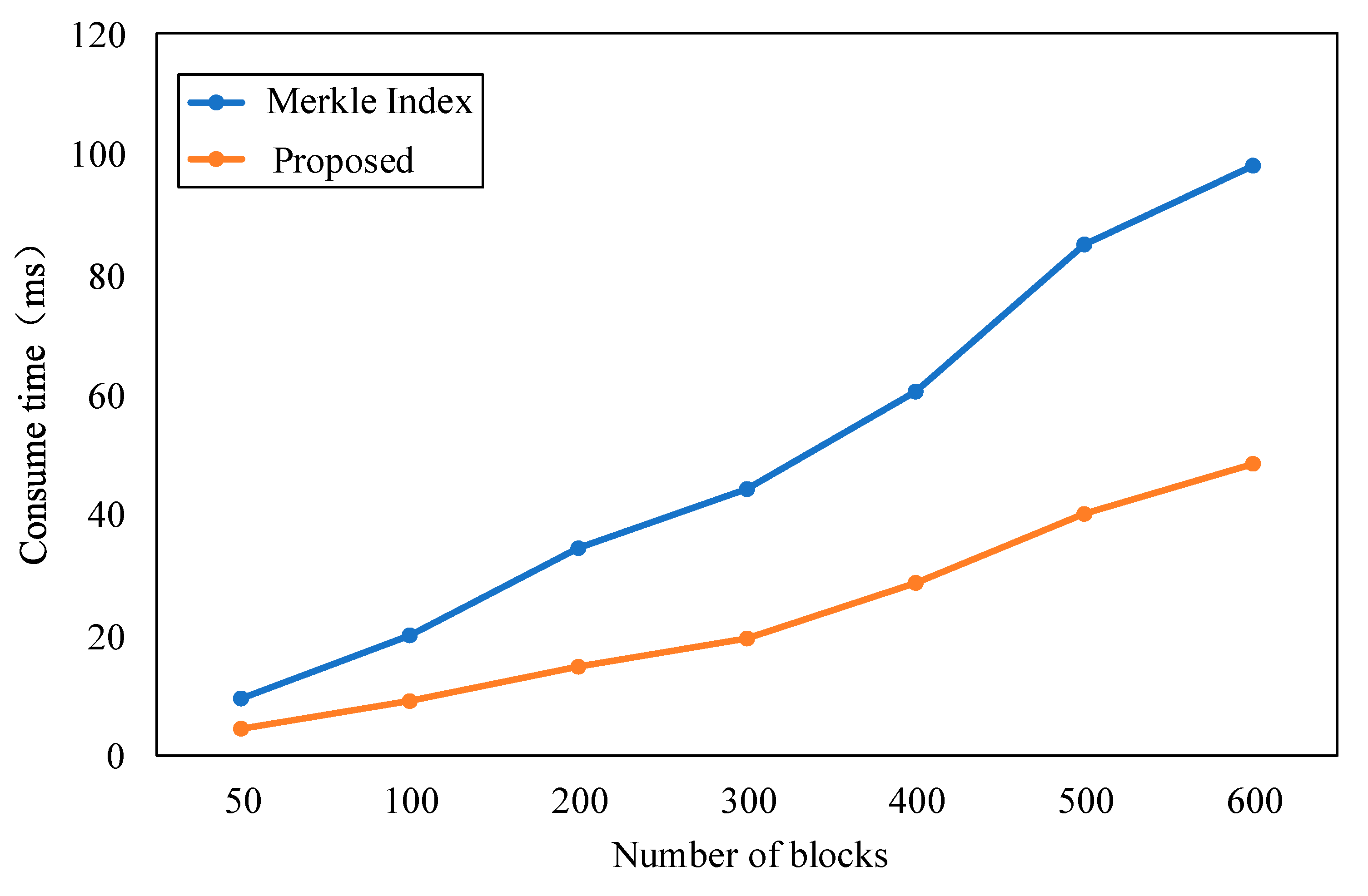
- Efficiency of traceability query
7. Conclusions
- (1)
- Supply chain traceability data analysis and resilience optimization. Relying on high-precision supply chain data obtained through a multi-chain traceability architecture, combined with key performance indicator (KPI) analysis and anomaly detection algorithms, identify bottleneck links and potential risk points in the supply chain network. Further integrate discrete event simulation (DES) and multi-agent simulation (MAS) methods to construct a dynamic supply chain optimization model, simulating the system response behavior under different disturbance scenarios such as raw material shortages, logistics disruptions, and demand fluctuations. Through sensitivity analysis and Pareto optimal solution, propose targeted supply chain resilience improvement strategies to achieve adaptive regulation capabilities for multi-agent collaborative assembly manufacturing supply chains.
- (2)
- Data-driven demand forecasting and inventory optimization. By leveraging deep learning techniques such as LSTM time series prediction models and graph neural networks, deep feature extraction and correlation relationship mining are conducted on the entire supply chain data. Through the integration of historical operational data, market intelligence, and macroeconomic indicators, an end-to-end dynamic demand forecasting model is constructed to achieve adaptive adjustment of safety stock levels. Under the constraint of service level, inventory holding costs and stockout losses can be effectively reduced.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Li, X.; Li, F. Research on production Model and Resource Scheduling of large-scale manufacturing products under Cloud environment. J. Softw. Guide 2019, 19, 65–68. [Google Scholar]
- Sahoo, S.; Halder, R. Traceability and ownership claim of data on big data marketplace using blockchain technology. J. Inf. Telecommun. 2021, 5, 35–61. [Google Scholar] [CrossRef]
- Wu, H.; Cao, J.; Yang, Y.; Tung, C.L.; Jiang, S.; Tang, B. Data management in supply chain using blockchain: Challenges and a case study. In Proceedings of the 2019 28th International Conference on Computer Communication and Networks (ICCCN), Valencia, Spain, 29 July–1 August 2019; pp. 1–8. [Google Scholar]
- Galvez, J.F.; Mejuto, J.C.; Simal-Gandara, J. Future challenges on the use of blockchain for food traceability analysis. TrAC Trends Anal. Chem. 2018, 2018, 222–232. [Google Scholar] [CrossRef]
- Shao, Q.; Jin, C.; Zhang, Z.; Qian, W.; Zhou, A. Blockchain technology: Architecture and progress. J. Comput. 2018, 41, 969–988. [Google Scholar]
- Liu, W.; Zhang, C.; She, W.; Song, X.; Tian, Z. Data trusted traceability method based on Merkle Mountains. J. Comput. Appl. 2022, 42, 2765–2771. [Google Scholar]
- Gao, G.; Shi, X.; Liu, C.; Dang, W.; Wang, N. A Privacy Protection Method for Medical Data Based on Blockchain. Appl. Res. Comput. 2024, 41, 1–7. [Google Scholar]
- Sun, C.; Yu, H.J.; Luo, N.; Xu, D.; Xing, B.; Yang, X. Research on the Storage Method of Traceability Data for Fruits and Vegetables Based on Smart Contracts in Blockchain. Trans. Chin. Soc. Agric. Mach. 2022, 53, 361–370. [Google Scholar]
- Lai, C.; Ma, Z.; Guo, R.; Zheng, D. Secure medical data sharing scheme based on traceable ring signature and blockchain. Peer-to-Peer Netw. Appl. 2022, 15, 1562–1576. [Google Scholar] [CrossRef]
- Singh, P.; Masud, M.; Hossain, M.S.; Kaur, A. Cross-domain secure data sharing using blockchain for industrial IoT. J. Parallel Distrib. Comput. 2021, 156, 176–184. [Google Scholar] [CrossRef]
- Xiong, L.; Xie, Y.; Chen, N. Research on the Information Traceability System of Vaccines Based on Blockchain. Inf. Sci. 2023, 41, 39–46. [Google Scholar]
- Li, Y.; Zhang, X.; Zhao, Z.; Xu, J.; Jiang, Z.; Yu, J.; Cui, X. Research on grain food blockchain traceability information management model based on master-slave multichain. Comput. Intell. Neurosci. 2022, 2022, 7498025. [Google Scholar] [CrossRef]
- Ren, Y.; Huang, D.; Wang, W.; Yu, X. BSMD: A blockchain-based secure storage mechanism for big spatio-temporal data. Future Gener. Comput. Syst. 2023, 138, 328–338. [Google Scholar] [CrossRef]
- Ye, H.; Park, S. Reliable vehicle data storage using blockchain and IPFS. Electronics 2021, 10, 1130. [Google Scholar] [CrossRef]
- Ho, G.T.S.; Tang, Y.M.; Tsang, K.Y.; Tang, V.; Chau, K.Y. A blockchain-based system to enhance aircraft parts traceability and trackability for inventory management. Expert Syst. Appl. 2021, 179, 115101. [Google Scholar] [CrossRef]
- Zhu, Z.; Wang, S.; Liang, X. Technical Strategies for the Supply Chain of the Automotive Manufacturing Industry from the Perspective of Blockchain. Mach. Des. Manuf. 2022, 11, 1–5. [Google Scholar]
- Kuhn, M.; Funk, F.; Franke, J. Blockchain architecture for automotive traceability. Procedia Cirp 2021, 97, 390–395. [Google Scholar] [CrossRef]
- Cohen, Y.; Rozenes, S. New framework for complex assembly digitalization and traceability using bill of assembly and smart contracts. Appl. Sci. 2023, 13, 1884. [Google Scholar] [CrossRef]
- Zhu, J.; Yang, Z.; Pang, L.; Ding, J. A Data Traceability Scheme for Industrial Internet Based on Blockchain. J. Xi’an Univ. Posts Telecommun. 2022, 27, 102–110. [Google Scholar]
- Hasegawa, Y.; Yamamoto, H. Reliable IoT data management platform based on real-world cooperation through blockchain. IEEE Consum. Electron. Mag. 2020, 10, 82–92. [Google Scholar] [CrossRef]
- Lin, S.-S.; Zhang, L.; Liu, D. Application research of blockchain-based smart contracts. Appl. Res. Comput. 2021, 38, 2570–2581. [Google Scholar] [CrossRef]
- Guo, S.; Wang, R.; Zhang, F. Overview of the principle and application of blockchain technology. Comput. Sci. 2021, 48, 271–281. [Google Scholar]
- Xia, Q.; Dou, W.-S.; Guo, K.-W.; Liang, G.; Zuo, C.; Zhang, F.-J. Overview of blockchain consensus protocol. J. Softw. 2021, 32, 277–299. [Google Scholar]
- He, H.; Yan, A.; Chen, Z. Smart contract technology and application based on blockchain. J. Comput. Res. Dev. 2018, 55, 2452–2466. [Google Scholar]
- Chen, W.-Y.; Li, X.-D.; Yang, X.; Xu, Y.-Z. A Blockchain based DNSSEC Public key verification mechanism. Acta Autom. Sin. 2023, 49, 731–743. [Google Scholar]



| PoW | PoS | DPoS | PBFT | |
|---|---|---|---|---|
| Energy Consumption | High | Moderate | Low | Low |
| Latency | High | High | Low | Low |
| Fault Tolerance | 50% | 50% | 50% | 33% |
| Throughput | Low | Low | High | High |
| Scalability | Good | Good | Fair | Poor |
| Applicable Environment | Public Chain | Public Chain | Consortium Chain | Consortium Chain |
| Supply Chain Stage | Key Traceability Data | Privacy Data |
|---|---|---|
| Component Tracing | Component supplier, component product information, and quality inspection status | Component processing information |
| Assembly Tracing | Assembly manufacturer, assembly parameters, and quality inspection status | Assembly production information |
| Logistics Tracing | Transport company, transport route, and arrival quality inspection status | Other storage and transportation information |
| Sales and After-sales Service | Sales company, transaction number, and repair order number | Other sales and after-sales service information |
| Order Number | Transaction Manufacturer | Supply Chain Segment | Product Name | Blockchain Storage Index |
|---|---|---|---|---|
| 91535211710887 | Vehicle Manufacturer | Final Assembly | Vehicle TA-6000-B | 35027396aa96cda4f6a7 59ce54d841afa73179b4992dcc6e |
| Engine Manufacturer | Sub-Assembly | Engine WD6 15.95E | 2f9b1fde9487a1f4820a91ad6e2e4 77eaf4ea16919784e951796f4fed4c67cec | |
| Connecting Rod Manufacturer | Component Level | Connecting Rod CA-6000-B | 65dd3e29ba67f678b2bd3cobd37860732Ca26837b1d62a0106ab544e6e938761 | |
| Camshaft Manufacturer | Component Level | Camshaft TA-6000-8 | 53fef53c032140279c8535a61c54ed 8cf6925770c4579fc3e1567cbb30ffcc12 |
| Data Type | Content | Processing Type | Processed Value |
|---|---|---|---|
| Original Data | PartName: “Connecting Rod CA-6000-B” PartID: “E4056983” AP_Quality: “Qualified” | Digital Signature | xNgw4i5g7jk0MugxOYiujARe/es 0R8uE+8TRWrPq5VMdrhf43isgXXcJ Pw3UrChXBEgLC8T0pLTex46vc0hc8g== |
| Decrypted Hash | 7008ce649c55b90adc3de5171f1c91 543ed80a368e28039de0055f4818722b2b | ||
| Tampered Data | PartName: “Connecting Rod CA-6000-B” PartID: “E4056980” AP_Quality: “Qualified” | Same Hash | 2e0677896a1b4b3827bcb5d4b5e915 feff29326ab471f1176ca7492e4b97efdc |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, C.; Gao, X.; Chu, J.; Tang, J. Research on a Robust Traceability Method for the Assembly Manufacturing Supply Chain Based on Blockchain. Appl. Sci. 2025, 15, 11598. https://doi.org/10.3390/app152111598
Li C, Gao X, Chu J, Tang J. Research on a Robust Traceability Method for the Assembly Manufacturing Supply Chain Based on Blockchain. Applied Sciences. 2025; 15(21):11598. https://doi.org/10.3390/app152111598
Chicago/Turabian StyleLi, Cheng, Xinqin Gao, Jia Chu, and Jiahuan Tang. 2025. "Research on a Robust Traceability Method for the Assembly Manufacturing Supply Chain Based on Blockchain" Applied Sciences 15, no. 21: 11598. https://doi.org/10.3390/app152111598
APA StyleLi, C., Gao, X., Chu, J., & Tang, J. (2025). Research on a Robust Traceability Method for the Assembly Manufacturing Supply Chain Based on Blockchain. Applied Sciences, 15(21), 11598. https://doi.org/10.3390/app152111598





