Near Real-Time Ethereum Fraud Detection Using Explainable AI in Blockchain Networks
Abstract
1. Introduction
- An artificial intelligence model was developed using labeled data from publicly available blockchain datasets. This model extracts behavioral and transactional features of individual wallet addresses in near real time, and subsequently to classify them as either suspicious or benign based on patterns of fraudulent activity that have been learned.
- A near real-time monitoring framework was implemented for the identification and analysis of recently active wallet addresses. The system is designed to ingest on-chain transaction data in a continuous manner, with the capacity to detect newly active wallets. Utilizing a trained model, it is then able to evaluate the likelihood of these wallets being involved in illicit activities.
- In order to enhance the interpretability of the model and thus support trust in automated decision-making processes, explainable artificial intelligence (XAI) techniques were incorporated. These techniques facilitate the attribution of model predictions to specific features or behaviors, thereby providing transparency into the rationale behind the classification of a wallet as suspicious.
2. Related Works
2.1. Classical ML Approaches
2.2. Self-Supervised and Deep Learning Methods
2.3. Graph-Based Techniques
2.4. Hybrid Systems
2.5. Background on Ethereum and Fraud Typologies
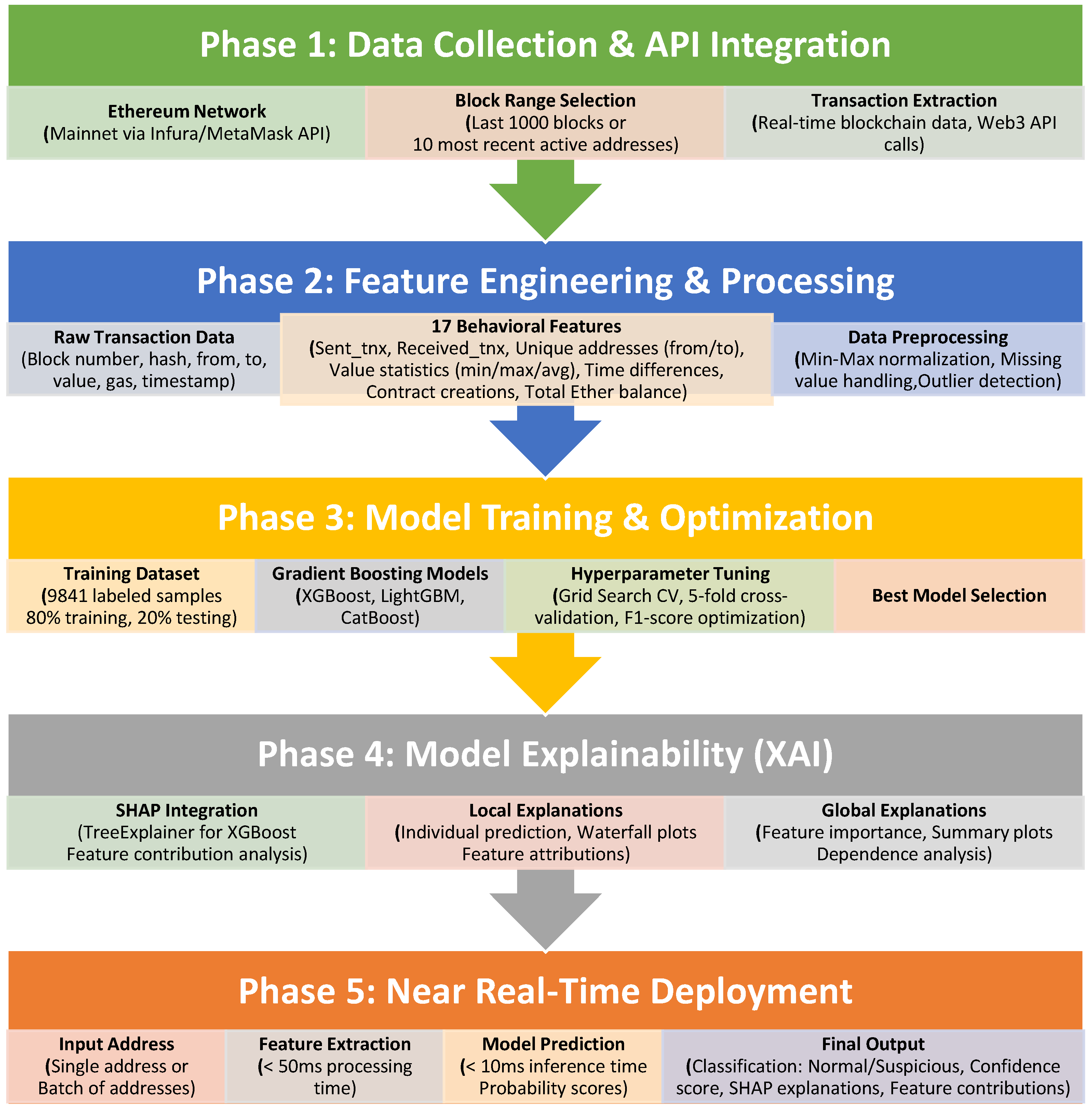
3. Materials and Method
3.1. Feature Selection and Reference Dataset
3.2. Performance Metrics
3.3. Classification
- is the set of prior samples with the same categorical value as ,
- p is the prior mean of the target,
- a is a regularization (smoothing) parameter.
3.4. Hyperparameter Optimization
- n_estimators: 300
- max_depth: 5
- learning_rate: 0.2
- subsample: 1.0
- colsample_bytree: 1.0
3.5. Ablation Study
4. Results and Discussion
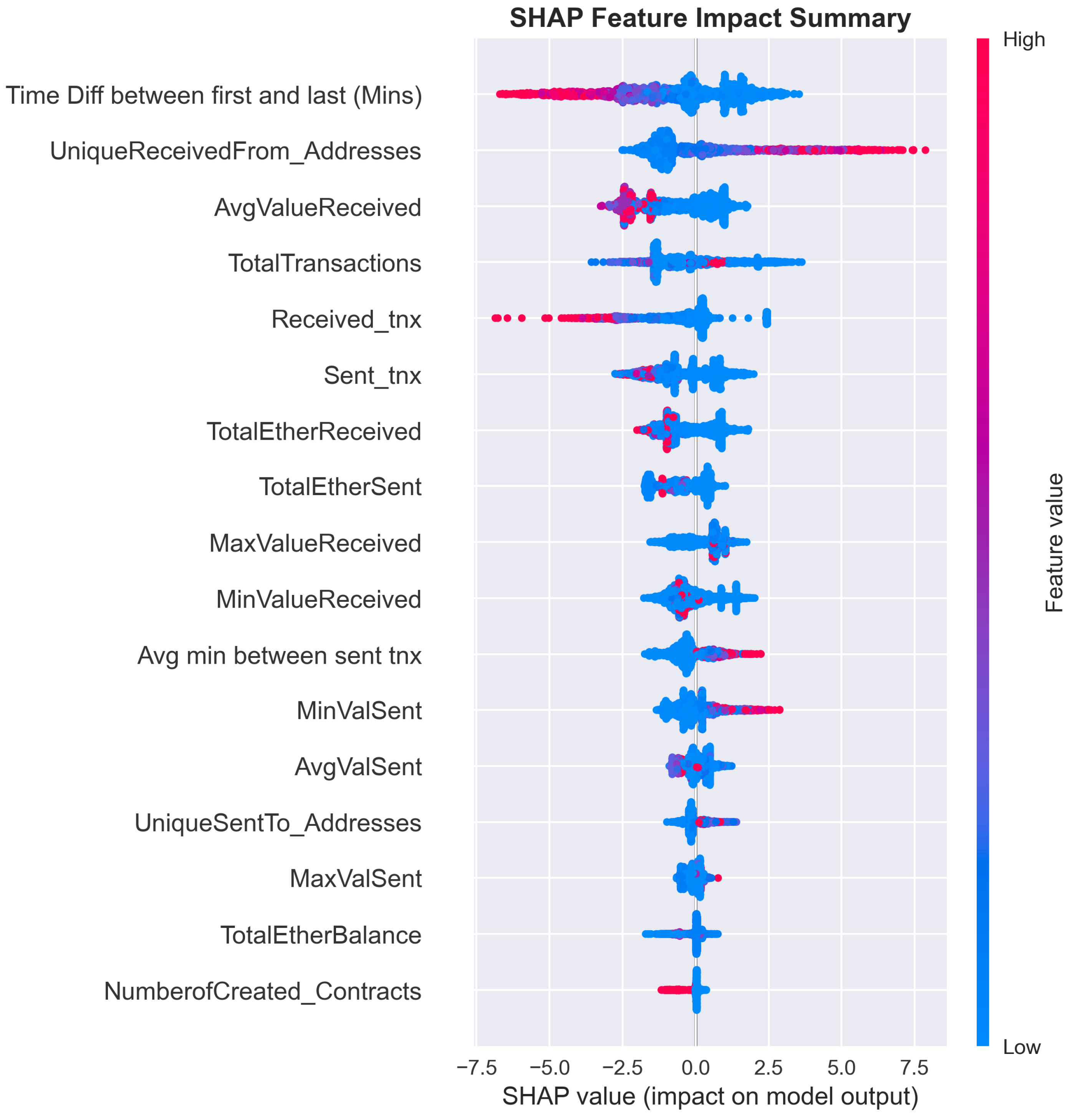
4.1. SHAP (SHapley Additive exPlanations)
Algorithm 1 Fraud Detection in Blockchain Transactions Using XGBoost and SHAP |
Input: Dataset file path |
Output: Trained XGBoost model, normalization scaler, accuracy score, SHAP summary plot |
1: Load dataset from CSV file |
2: Separate input features X and target variable y: |
3: Remove Address column from X |
4: Extract class column as target y |
5: Normalize features X using Min-Max scaling to obtain |
6: Split data into training and test sets: |
7: |
8: Initialize XGBoost classifier with parameters: |
9: use_label_encoder=False, eval_metric="logloss", tree_method="hist" |
10: Train model M on training data |
11: Save trained model and scaler to disk |
12: Predict target values for using model M |
13: Calculate accuracy score between and |
14: Initialize SHAP explainer with model M |
15: Compute SHAP values for test data |
16: Generate and save SHAP summary plot |
4.2. Feature Extraction for Given Wallet Address
4.3. Detection of the Last 10 Active Wallet Addresses and Extraction of the Properties of These Wallets and Model Estimation
| Algorithm 2 Ethereum Account Feature Extraction |
Input: Ethereum account address, start block, end block |
Output: Transaction features for the account in a CSV file |
1:
Connect to Ethereum via Web3 provider |
2:
Initialize empty list transactions |
3:
Loop over blocks from start_block to end_block: |
4:
for each block number in the range do |
5:
Retrieve block with full transaction data |
6:
for each transaction in block do |
7:
if transaction is sent from or received by the given address then |
8:
Extract transaction data: block number, hash, sender, recipient, value in ETH, gas, timestamp |
9:
Append data to transactions |
10:
end if |
11:
end for |
12:
end for |
13:
Extract timestamps and compute: |
14:
Time difference between first and last transaction |
15:
Average time between sent transactions |
16:
Separate sent and received transactions |
17:
Compute the number of unique senders and recipients |
18:
Count the number of contract creations |
19:
Compute statistical values for sent and received ETH: |
20:
Min, Max, and Average values |
21:
Total ETH sent and received |
22:
Balance = Received - Sent |
23:
Build a feature dictionary with all computed metrics |
24:
Save the feature dictionary as a row in a CSV file |
Algorithm 3 Extracting Latest Active Ethereum Addresses |
Input: Ethereum node access, block range N, number of addresses k |
Output: A CSV file with the k most recent active Ethereum addresses |
1: Connect to Ethereum using Web3 |
2: Get the latest block number |
3: Set the scan range as the last N blocks |
4: Initialize an empty set active_addresses |
5: for block number from latest to latest (in reverse) do |
6: Fetch the block with full transaction data |
7: for each transaction in the block do |
8: Add from and to addresses to active_addresses, if present |
9: if size of active_addresses then |
10: Return the list of active addresses |
11: end if |
12: end for |
13: end for |
14: Save the collected addresses into a CSV file |
Algorithm 4 Extract Ethereum Account Features |
Input: Ethereum address list from CSV, start and end block numbers |
Output: Extracted features for each address saved in output CSV |
1: Connect to Ethereum mainnet via Web3 |
2:
Load Ethereum addresses from latest_active_addresses.csv |
3:
Define output CSV eth_account_features.csv |
4:
Get current block as latest_block, set start_block = latest_block - 500 |
5:
for each address in input CSV do |
6:
if address is valid then |
7:
Initialize empty transaction list |
8:
for each block from start_block to latest_block do |
9:
Get block with full transactions |
10:
for each transaction in block do |
11:
if transaction involves address then |
12:
Collect transaction info (value, gas, timestamp, etc.) |
13:
end if |
14:
end for |
15:
Wait 0.5 s to avoid rate limits |
16:
end for |
17:
Compute: |
• Number of sent/received transactions |
• Number of contracts created |
• Unique sent-to and received-from addresses |
• Min, max, avg sent/received values |
• Total Ether sent/received, balance |
• Time statistics |
18:
Write all features to output CSV |
19:
end if |
20:
end for |
Algorithm 5 Ethereum Account Fraud Classification Pipeline |
Input: CSV file path |
Output: Prediction (Normal or Suspicion) |
1:
Load: Saved scaler from scaler.pkl |
2:
Load: Trained model from xgboost_fraud_detection_model.pkl |
3:
Load dataset as dataframe df from CSV |
4:
Store the Address column separately in addresses |
5:
Remove the Address column from df |
6:
for all columns in df do |
7:
Convert values to numeric (coerce invalid values as NaN) |
8:
end for |
9:
Fill missing values in df with column medians |
10:
Load scaler using joblib |
11:
Apply scaler transformation to df to obtain X_new_scaled |
12:
Load XGBoost model using joblib |
13:
Predict labels for X_new_scaled using the loaded model |
14:
Create a new dataframe output_df with: |
15:
Address from original data |
16:
Class as "NORMAL" if prediction is 0, else "SUSPICION" |
17:
Save output_df to eth_account_predictions.csv |
5. Limitation
- The paucity of high-quality, publicly labeled datasets for Ethereum fraud detection poses a significant constraint. The present study is predicated on a dataset comprising 9.841 transactions, which, while substantial, may not encompass the full spectrum of fraudulent behavior present in the current ecosystem.
- It is imperative to acknowledge the perpetual adaptability exhibited by cybercriminals in their endeavors to circumvent detection systems. This perpetual adaptability renders training data as a representation of evolving fraud patterns as inadequate. This temporal bias has the potential to compromise the model’s efficacy in addressing novel attack vectors.
- The binary classification approach (normal and suspicious) may be an oversimplification of the complex nature of blockchain activity. It is important to note that some transactions may fall into a gray area that is neither clearly fraudulent nor entirely legitimate. The current model does not differentiate between different fraudulent activities (e.g., phishing, Ponzi schemes, and money laundering).
- Despite the fact that our set of 17 features captures fundamental behavioral patterns, it is possible that these features do not encompass all relevant fraud indicators. It is possible that more sophisticated fraud schemes may employ patterns not yet captured in our current feature set. The prevailing feature engineering approach is static, which may hinder its ability to adapt to the evolving nature of fraud.
- At present, the system’s design is exclusively tailored for Ethereum, thereby limiting its generalizability to disparate blockchain networks characterized by varied transaction structures and consensus mechanisms.
- The system’s reliance on external APIs (Ethereum nodes, Etherscan) introduces potential points of failure and rate-limiting constraints that could impact real-time performance.
- Despite the system’s optimization for efficiency, concurrent processing of voluminous address groups can necessitate substantial memory resources, a factor that could impede the system’s applicability in environments characterized by resource constraints.
- In the context of sophisticated attacks, entities that possess an understanding of the model’s decision boundaries may devise specially designed transactions with the intent to evade detection. It should be noted that this particular scenario has not been the focus of a comprehensive evaluation within the scope of our current research.
- While SHAP offers interpretability, it concomitantly unveils the model’s decision-making process, leaving it vulnerable to exploitation by potential attackers.
6. Future Works
7. Conclusions
Funding
Data Availability Statement
Conflicts of Interest
References
- Xu, M.; Chen, X.; Kou, G. A systematic review of blockchain. Financ. Innov. 2019, 5, 27. [Google Scholar] [CrossRef]
- Ressi, D.; Romanello, R.; Piazza, C.; Rossi, S. AI-enhanced blockchain technology: A review of advancements and opportunities. J. Netw. Comput. Appl. 2024, 225, 103858. [Google Scholar] [CrossRef]
- Sun, J.; Jia, Y.; Wang, Y.; Tian, Y.; Zhang, S. Ethereum fraud detection via joint transaction language model and graph representation learning. Inf. Fusion 2025, 120, 103074. [Google Scholar] [CrossRef]
- Gad, A.G.; Mosa, D.T.; Abualigah, L.; Abohany, A.A. Emerging trends in blockchain technology and applications: A review and outlook. J. King Saud Univ.-Comput. Inf. Sci. 2022, 34, 6719–6742. [Google Scholar] [CrossRef]
- Zheng, Z.; Su, J.; Chen, J.; Lo, D.; Zhong, Z.; Ye, M. Dappscan: Building large-scale datasets for smart contract weaknesses in dapp projects. IEEE Trans. Softw. Eng. 2024, 50, 1360–1373. [Google Scholar] [CrossRef]
- Han, H.; Shiwakoti, R.K.; Jarvis, R.; Mordi, C.; Botchie, D. Accounting and auditing with blockchain technology and artificial Intelligence: A literature review. Int. J. Account. Inf. Syst. 2023, 48, 100598. [Google Scholar] [CrossRef]
- Tripathi, G.; Ahad, M.A.; Casalino, G. A comprehensive review of blockchain technology: Underlying principles and historical background with future challenges. Decis. Anal. J. 2023, 9, 100344. [Google Scholar] [CrossRef]
- Ma, F.; Ren, M.; Fu, Y.; Wang, M.; Li, H.; Song, H.; Jiang, Y. Security reinforcement for Ethereum virtual machine. Inf. Process. Manag. 2021, 58, 102565. [Google Scholar] [CrossRef]
- Wu, S.; Yu, Z.; Wang, D.; Zhou, Y.; Wu, L.; Wang, H.; Yuan, X. Defiranger: Detecting DeFI price manipulation attacks. IEEE Trans. Dependable Secur. Comput. 2023, 21, 4147–4161. [Google Scholar] [CrossRef]
- Faqir-Rhazoui, Y.; Arroyo, J.; Hassan, S. A comparative analysis of the platforms for decentralized autonomous organizations in the Ethereum blockchain. J. Internet Serv. Appl. 2021, 12, 9. [Google Scholar] [CrossRef]
- Li, S.; Gou, G.; Liu, C.; Xiong, G.; Li, Z.; Xiao, J.; Xing, X. TGC: Transaction Graph Contrast Network for Ethereum Phishing Scam Detection. In Proceedings of the 39th Annual Computer Security Applications Conference, Austin, TX, USA, 4–8 December 2023; pp. 352–365. [Google Scholar]
- Wu, J.; Lin, D.; Fu, Q.; Yang, S.; Chen, T.; Zheng, Z.; Song, B. Toward understanding asset flows in crypto money laundering through the lenses of Ethereum heists. IEEE Trans. Inf. Forensics Secur. 2023, 19, 1994–2009. [Google Scholar] [CrossRef]
- Wronka, C. Money laundering through cryptocurrencies-analysis of the phenomenon and appropriate prevention measures. J. Money Laund. Control 2022, 25, 79–94. [Google Scholar] [CrossRef]
- Chainalysis, T. The Chainalysis 2025 Crypto Crime Report. 2025. Available online: https://go.chainalysis.com/2025-Crypto-Crime-Report.html (accessed on 19 May 2025).
- Chen, Z.; Hu, Y.; He, B.; Luo, D.; Wu, L.; Zhou, Y. Dissecting payload-based transaction phishing on Ethereum. arXiv 2024, arXiv:2409.02386. [Google Scholar] [CrossRef]
- Aziz, R.M.; Baluch, M.F.; Patel, S.; Ganie, A.H. LGBM: A machine learning approach for Ethereum fraud detection. Int. J. Inf. Technol. 2022, 14, 3321–3331. [Google Scholar] [CrossRef]
- Farrugia, S.; Ellul, J.; Azzopardi, G. Detection of illicit accounts over the Ethereum blockchain. Expert Syst. Appl. 2020, 150, 113318. [Google Scholar] [CrossRef]
- Ravindranath, V.; Nallakaruppan, M.; Shri, M.L.; Balusamy, B.; Bhattacharyya, S. Evaluation of performance enhancement in Ethereum fraud detection using oversampling techniques. Appl. Soft Comput. 2024, 161, 111698. [Google Scholar] [CrossRef]
- Dahiya, M.; Mishra, N.; Singh, R. Neural network based approach for Ethereum fraud detection. In Proceedings of the 2023 4th International Conference on Intelligent Engineering and Management (ICIEM), London, UK, 9–11 May 2023; 2023; pp. 1–4. [Google Scholar]
- Hu, T.; Liu, X.; Chen, T.; Zhang, X.; Huang, X.; Niu, W.; Lu, J.; Zhou, K.; Liu, Y. Transaction-based classification and detection approach for Ethereum smart contract. Inf. Process. Manag. 2021, 58, 102462. [Google Scholar] [CrossRef]
- Ehsan, A.; Iqbal, Z.; Abuowaida, S.; Aljaidi, M.; Zia, H.U.; Alshdaifat, N.; Alshammry, N.K. Enhanced Anomaly Detection in Ethereum: Unveiling and Classifying Threats with Machine Learning. IEEE Access 2024, 12, 176440–176456. [Google Scholar] [CrossRef]
- Liu, L.; Tsai, W.T.; Bhuiyan, M.Z.A.; Peng, H.; Liu, M. Blockchain-enabled fraud discovery through abnormal smart contract detection on Ethereum. Future Gener. Comput. Syst. 2022, 128, 158–166. [Google Scholar] [CrossRef]
- Tan, R.; Tan, Q.; Zhang, P.; Li, Z. Graph neural network for ethereum fraud detection. In Proceedings of the 2021 IEEE international conference on big knowledge (ICBK), Auckland, New Zealand, 7–8 December 2021; pp. 78–85. [Google Scholar]
- Jin, C.; Zhou, J.; Xie, C.; Yu, S.; Xuan, Q.; Yang, X. Enhancing Ethereum Fraud Detection via Generative and Contrastive Self-supervision. IEEE Trans. Inf. Forensics Secur. 2024, 20, 839–853. [Google Scholar] [CrossRef]
- Tan, R.; Tan, Q.; Zhang, Q.; Zhang, P.; Xie, Y.; Li, Z. Ethereum fraud behavior detection based on graph neural networks. Computing 2023, 105, 2143–2170. [Google Scholar] [CrossRef]
- Liu, S.Z.; Yu, X.Y.; Li, Y.T.; Zhang, H.; Guo, X.P.; Ma, C.H.; Long, H.X. Detection of Ethereum Phishing Fraud Nodes Based on Feature Enhancement Strategy and GBM. Electronics 2024, 13, 5060. [Google Scholar] [CrossRef]
- Sheng, Z.; Song, L.; Wang, Y. Dynamic Feature Fusion: Combining Global Graph Structures and Local Semantics for Blockchain Phishing Detection. IEEE Trans. Netw. Serv. Manag. 2025, 22, 4706–4718. [Google Scholar] [CrossRef]
- Jia, Y.; Wang, Y.; Sun, J.; Tian, Y.; Qian, P. LMAE4Eth: Generalizable and Robust Ethereum Fraud Detection by Exploring Transaction Semantics and Masked Graph Embedding. IEEE Trans. Inf. Forensics Secur. 2025, 20, 10260–10274. [Google Scholar] [CrossRef]
- Li, P.; Xie, Y.; Xu, X.; Zhou, J.; Xuan, Q. Phishing fraud detection on ethereum using graph neural network. In Proceedings of the International Conference on Blockchain and Trustworthy Systems, Chengdu, China, 4–5 August 2022; Springer: Singapore, 2022; pp. 362–375. [Google Scholar]
- Pahuja, L.; Kamal, A. EnLEFD-DM: Ensemble Learning Based Ethereum Fraud Detection Using CRISP-DM Framework. Expert Syst. 2023, 40, e13379. [Google Scholar] [CrossRef]
- Github. Github Repository Dataset. 2025. Available online: https://github.com/fatihertam/ethereumfrauddetection (accessed on 19 May 2025).
- Kilincer, I.F. Explainable AI supported hybrid deep learnig method for layer 2 intrusion detection. Egypt. Inform. J. 2025, 30, 100669. [Google Scholar] [CrossRef]
- Ahn, J.M.; Kim, J.; Kim, K. Ensemble machine learning of gradient boosting (XGBoost, LightGBM, CatBoost) and attention-based CNN-LSTM for harmful algal blooms forecasting. Toxins 2023, 15, 608. [Google Scholar] [CrossRef]
- Chen, T.; Guestrin, C. Xgboost: A scalable tree boosting system. In Proceedings of the 22nd ACM Sigkdd International Conference on Knowledge Discovery and Data Mining, San Francisco, CA, USA, 13–17 August 2016; pp. 785–794. [Google Scholar]
- Ke, G.; Meng, Q.; Finley, T.; Wang, T.; Chen, W.; Ma, W.; Ye, Q.; Liu, T.Y. Lightgbm: A highly efficient gradient boosting decision tree. Adv. Neural Inf. Process. Syst. 2017, 30, 3149–3157. [Google Scholar]
- Prokhorenkova, L.; Gusev, G.; Vorobev, A.; Dorogush, A.V.; Gulin, A. CatBoost: Unbiased boosting with categorical features. Adv. Neural Inf. Process. Syst. 2018, 31, 6639–6649. [Google Scholar]
- Li, Z. Extracting spatial effects from machine learning model using local interpretation method: An example of SHAP and XGBoost. Comput. Environ. Urban Syst. 2022, 96, 101845. [Google Scholar] [CrossRef]
| Feature Name | Description |
|---|---|
| Address | Ethereum wallet address. |
| Sent_tnx | Total number of standard (non-contract) transactions sent from the address. |
| Received_tnx | Total number of standard (non-contract) transactions received by the address. |
| NumberofCreated_Contracts | Number of smart contract creation transactions initiated by the account. |
| UniqueReceivedFrom_Addresses | Count of distinct sender addresses that sent Ether to this account. |
| UniqueSentTo_Addresses | Count of distinct recipient addresses this account has sent Ether to. |
| MinValueReceived | The smallest single Ether amount received in a transaction. |
| MaxValueReceived | The largest single Ether amount received in a transaction. |
| AvgValueReceived | Average Ether value received across all incoming transactions. |
| MinValSent | The smallest single Ether amount sent in a transaction. |
| MaxValSent | The largest single Ether amount sent in a transaction. |
| AvgValSent | Average Ether value sent across all outgoing transactions. |
| TotalEtherSent | Cumulative Ether sent from this address across all transactions. |
| TotalEtherReceived | Cumulative Ether received by this address across all transactions. |
| TotalEtherBalance | Net Ether balance after all incoming and outgoing transactions. |
| TotalTransactions | Total count of transactions including normal and contract creation ones. |
| TimeDiffBetweenFirstandLast | Time duration in minutes between the first and the most recent transaction. |
| AvgMinBetweenSentTnx | Average time in minutes between two consecutive sent transactions. |
| Metric | XGBoost | LightGBM | CatBoost |
|---|---|---|---|
| Best Hyperparameters | colsample_bytree: 1.0 learning_rate: 0.2 max_depth: 5 n_estimators: 300 reg_alpha: 0 reg_lambda: 1.5 subsample: 1.0 | bagging_fraction: 0.8 feature_fraction: 0.9 learning_rate: 0.2 max_depth: 5 n_estimators: 200 num_leaves: 31 | depth: 7 iterations: 300 l2_leaf_reg: 3 learning_rate: 0.2 |
| CV Accuracy Mean | 0.9588 | 0.9646 | 0.9583 |
| CV Accuracy Std | 0.0090 | 0.0071 | 0.0066 |
| CV F1 Mean | 0.9585 | 0.9643 | 0.9580 |
| CV F1 Std | 0.0090 | 0.0071 | 0.0066 |
| Test Accuracy | 0.9589 | 0.9634 | 0.9584 |
| Test Precision | 0.9586 | 0.9633 | 0.9582 |
| Test Recall | 0.9589 | 0.9634 | 0.9584 |
| Test F1 | 0.9581 | 0.9628 | 0.9575 |
| Test ROC AUC | 0.9882 | 0.9898 | 0.9880 |
| Training Time (s) | 833.96 | 471.86 | 220.65 |
| Model Size (KB) | 548.79 | 516.15 | 639.19 |
| Latency (ms) | 0.72 | 0.72 | 0.72 |
| Metric | Value | Requirement |
|---|---|---|
| Average Processing Time | 0.72 ms | <100 ms |
| P95 Response Time | 0.76 ms | <200 ms |
| P99 Response Time | 1.03 ms | <500 ms |
| Throughput (10 samples) | 12,021.0 samples/s | >50 samples/s |
| Time per Sample (batch) | 0.08 ms | <20 ms |
| Memory Usage | 410.0 MB | <1000 MB |
| Model Size | 548.8 KB | <1000 KB |
| Feature | Baseline Accuracy | Without Feature Accuracy | Accuracy Drop | Relative Accuracy Impact | Baseline F1 | Without Feature F1 | F1 Drop | Relative F1 Impact |
|---|---|---|---|---|---|---|---|---|
| Time Diff between first and last (Mins) | 0.9589 | 0.9487 | 0.0102 | 1.0593 | 0.9581 | 0.9474 | 0.0107 | 1.1209 |
| TotalTransactions | 0.9589 | 0.9487 | 0.0102 | 1.0593 | 0.9581 | 0.9477 | 0.0104 | 1.0895 |
| MinValueReceived | 0.9589 | 0.9563 | 0.0025 | 0.2648 | 0.9581 | 0.9556 | 0.0026 | 0.2677 |
| TotalEtherReceived | 0.9589 | 0.9563 | 0.0025 | 0.2648 | 0.9581 | 0.9554 | 0.0027 | 0.2851 |
| MaxValueReceived | 0.9589 | 0.9568 | 0.0020 | 0.2119 | 0.9581 | 0.9558 | 0.0023 | 0.2375 |
| Sent_tnx | 0.9589 | 0.9573 | 0.0015 | 0.1589 | 0.9581 | 0.9565 | 0.0017 | 0.1725 |
| TotalEtherSent | 0.9589 | 0.9573 | 0.0015 | 0.1589 | 0.9581 | 0.9565 | 0.0016 | 0.1682 |
| UniqueReceivedFrom_Addresses | 0.9589 | 0.9573 | 0.0015 | 0.1589 | 0.9581 | 0.9566 | 0.0015 | 0.1598 |
| AvgValueReceived | 0.9589 | 0.9573 | 0.0015 | 0.1589 | 0.9581 | 0.9564 | 0.0017 | 0.1768 |
| TotalEtherBalance | 0.9589 | 0.9573 | 0.0015 | 0.1589 | 0.9581 | 0.9565 | 0.0016 | 0.1682 |
| Avg min between sent tnx | 0.9589 | 0.9578 | 0.0010 | 0.1059 | 0.9581 | 0.9569 | 0.0012 | 0.1291 |
| MaxValSent | 0.9589 | 0.9578 | 0.0010 | 0.1059 | 0.9581 | 0.9571 | 0.0010 | 0.1079 |
| UniqueSentTo_Addresses | 0.9589 | 0.9578 | 0.0010 | 0.1059 | 0.9581 | 0.9570 | 0.0011 | 0.1163 |
| Received_tnx | 0.9589 | 0.9584 | 0.0005 | 0.0530 | 0.9581 | 0.9575 | 0.0006 | 0.0602 |
| MinValSent | 0.9589 | 0.9584 | 0.0005 | 0.0530 | 0.9581 | 0.9577 | 0.0005 | 0.0478 |
| NumberofCreated_Contracts | 0.9589 | 0.9589 | 0.0000 | 0.0000 | 0.9581 | 0.9580 | 0.0001 | 0.0082 |
| AvgValSent | 0.9589 | 0.9599 | −0.0010 | −0.1059 | 0.9581 | 0.9592 | −0.0011 | −0.1119 |
| Feature | Mean Absolute SHAP Value |
|---|---|
| Time Diff between first and last (Mins) | 1.6933 |
| UniqueReceivedFrom_Addresses | 1.4526 |
| AvgValueReceived | 1.1515 |
| TotalTransactions | 1.0833 |
| Received_tnx | 0.9854 |
| Sent_tnx | 0.9066 |
| TotalEtherReceived | 0.8005 |
| TotalEtherSent | 0.6614 |
| MaxValueReceived | 0.6227 |
| MinValueReceived | 0.6016 |
| Avg min between sent tnx | 0.5552 |
| MinValSent | 0.5397 |
| AvgValSent | 0.3124 |
| UniqueSentTo_Addresses | 0.2595 |
| MaxValSent | 0.2215 |
| TotalEtherBalance | 0.1875 |
| NumberofCreated_Contracts | 0.1364 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ertam, F. Near Real-Time Ethereum Fraud Detection Using Explainable AI in Blockchain Networks. Appl. Sci. 2025, 15, 10841. https://doi.org/10.3390/app151910841
Ertam F. Near Real-Time Ethereum Fraud Detection Using Explainable AI in Blockchain Networks. Applied Sciences. 2025; 15(19):10841. https://doi.org/10.3390/app151910841
Chicago/Turabian StyleErtam, Fatih. 2025. "Near Real-Time Ethereum Fraud Detection Using Explainable AI in Blockchain Networks" Applied Sciences 15, no. 19: 10841. https://doi.org/10.3390/app151910841
APA StyleErtam, F. (2025). Near Real-Time Ethereum Fraud Detection Using Explainable AI in Blockchain Networks. Applied Sciences, 15(19), 10841. https://doi.org/10.3390/app151910841






