Enhancing Secure Multi-Party Computation with Damgård–Jurik and NIZK Proofs: A Lightweight Protocol for Scalable Aggregation
Abstract
1. Introduction
- (i)
- The additive homomorphic structure of Damgård–Jurik enables direct aggregation of encrypted values without intermediate decryption operations, thereby reducing the overall computational complexity to , [18,19]. By encrypting inputs end-to-end and performing computations on ciphertexts, the protocol ensures that no party—including the trusted server—learns individual contributions, adhering to PETs’ principle of data minimization and thus, making it suitable for large-scale applications such as federated learning, secure voting, or collaborative analytics.
- (ii)
- (iii)
- The use of NIZK’s to validate the total sum of encrypted values sent by the last participating node to the mediator node eliminates the need for additional verification rounds, thereby reducing communication overhead without compromising the validity of the final result. The proofs are compactly attached to the last shared ciphertext, enabling efficient verification, [22]. This mechanism empowers parties to audit the trusted server’s output independently, ensuring transparency and trust in the computation—a critical aspect of PETs that balances accountability with privacy.
- (iv)
- By assuming a semi-honest trusted server and validating outputs via ZKPs, our design mitigates risks of tampering while maintaining practicality. This trust model reflects PETs’ emphasis on reducing single points of failure and enhancing system resilience, enabling privacy-by-design data aggregation, directly supporting use cases like medical research, financial auditing, and IoT sensor networks, domains in which it is critical to minimize personal data exposure while preserving functionality.
2. Theoretical Framework
2.1. Protocol Proposed by Mehnaz et al
2.2. Homomorphic Encryption
2.3. Damgård–Jurik Cryptosystem
- Key Generation
- Input: Security parameter
- Output: Public key , private key
- Select large primes p and q such that
- Compute and define
- Compute
- Select a generator that belongs to the subgroup of elements congruent to 1 modulo n
- Define auxiliary function
- Compute
- Return: Public key , private key
- Encryption
- Input: Message , public key
- Output: Ciphertext c
- Select random
- Compute
- Return: c
- Decryption
- Input: Ciphertext c, private key
- Output: Message m
- Compute
- Retrieve
- Return: m
2.4. Non-Interactive Zero-Knowledge Proof of Schnorr
- The prover selects a random and computes .
- The prover computes the challenge , where H denotes a cryptographic hash function.
- The prover computes the response .
- The proof consists of the tuple .
- The verifier accepts the proof if and only if .
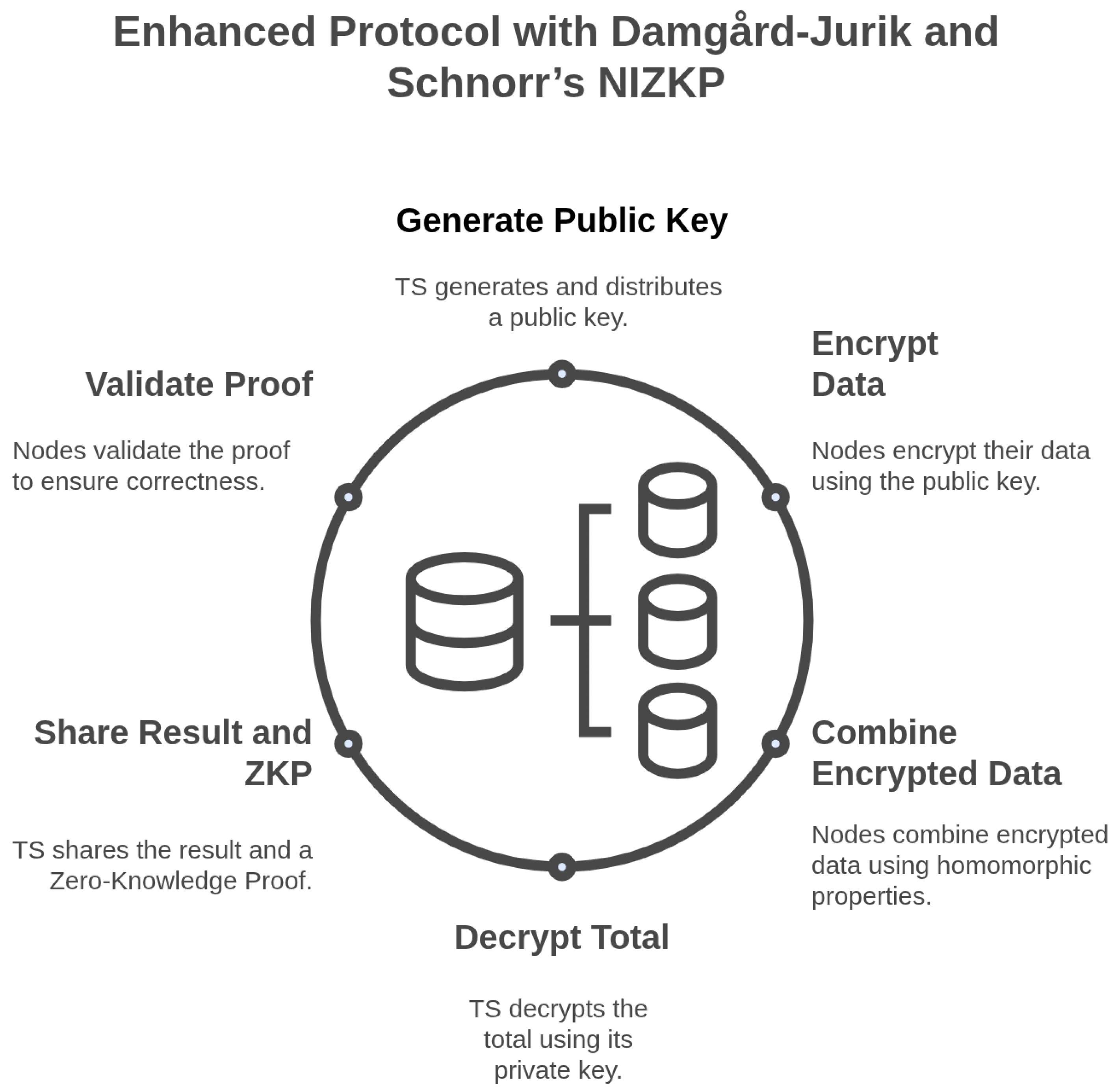
3. An Enhanced Protocol with Damgård–Jurik and Schnorr’s NIZKP
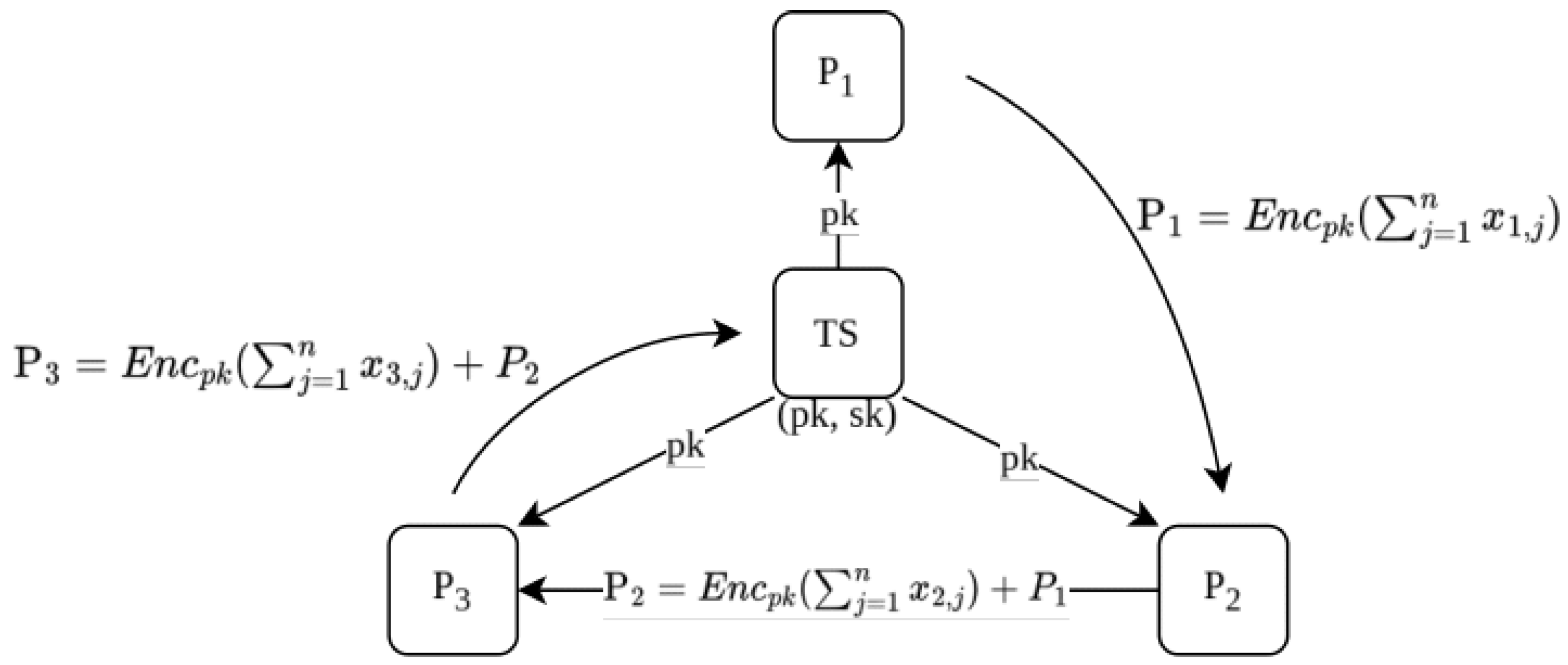
3.1. Initialization, Encryption, and Homomorphic Addition
| Algorithm 1 Initialization, data encryption, and generalized homomorphic summation |
|
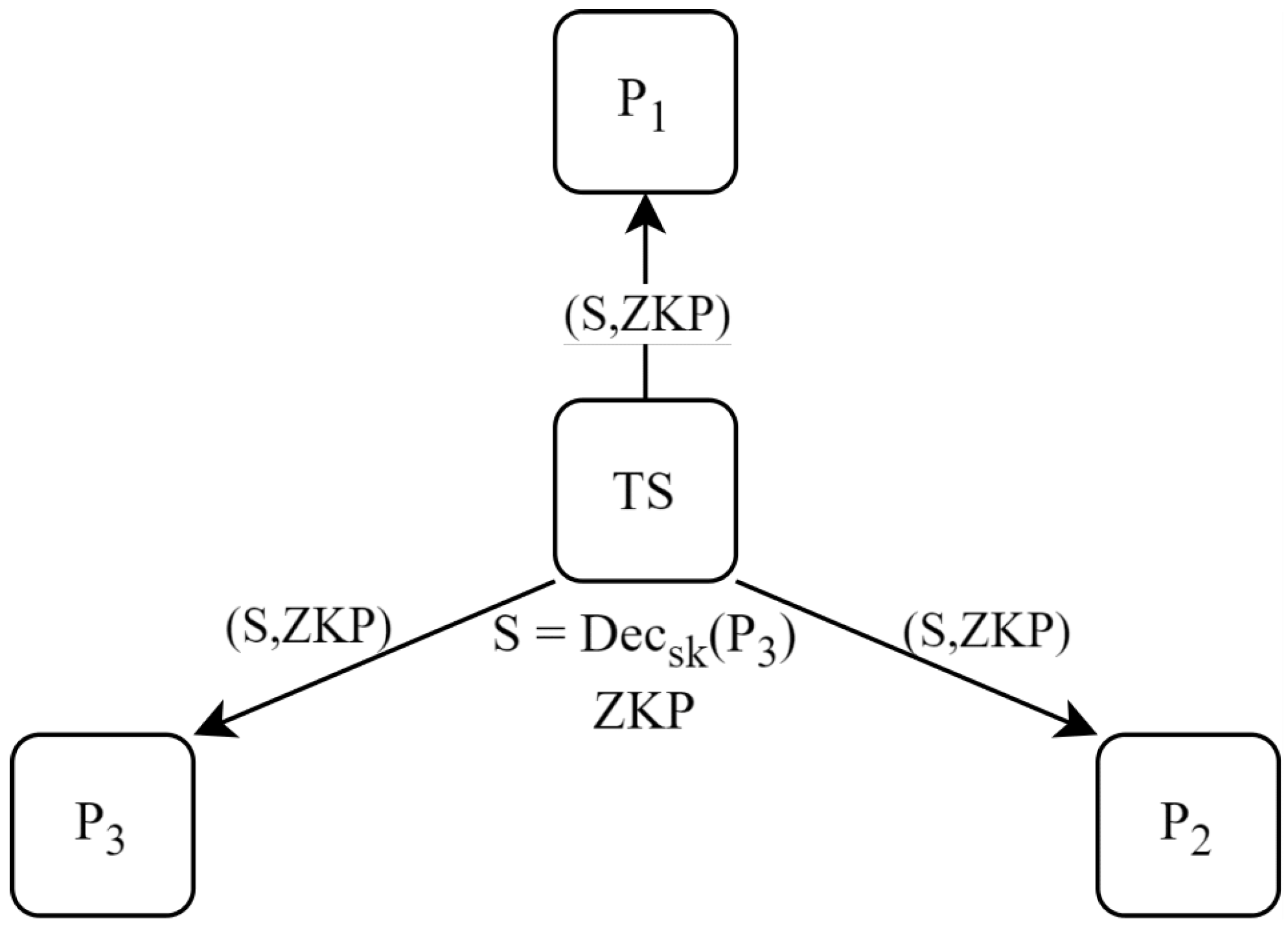
3.2. Decryption and Verification
| Algorithm 2 Decryption and verification using Schnorr proof |
|
4. Comparative Evaluation of Communication and Computational Complexity
- Linear complexity: Denoted by , where the number of messages grows proportionally to the number of participants. Each entity exchanges a constant number of messages, thereby enhancing scalability.
- Quadratic complexity: Represented by , arises when each participant must communicate with every other, as in protocols requiring exhaustive interaction to preserve security in distributed computations.
- Logarithmic and sublinear complexity: Denoted by and , respectively, these complexities emerge in optimized protocols that employ hierarchical structures or efficient networks to reduce inter-party communication.
- Processing: Includes operations such as encryption, decryption, key generation, digital signing, and verification. These processes may be intensive, depending on the underlying algorithm.
- Resources: Protocols with high computational complexity require more processing power and memory capacity, posing challenges in resource-constrained devices such as sensors, mobile platforms, or IoT devices.
4.1. Communication Complexity of the Proposed Protocol as a Function of N
- The mediator shares the public key with the N parties: N messages.
- Each pair of consecutive parties exchanges encrypted data: messages.
- The last party sends the aggregate to the mediator: 1 message.
- The mediator sends the result and the noninteractive challenge to all parties: N messages.
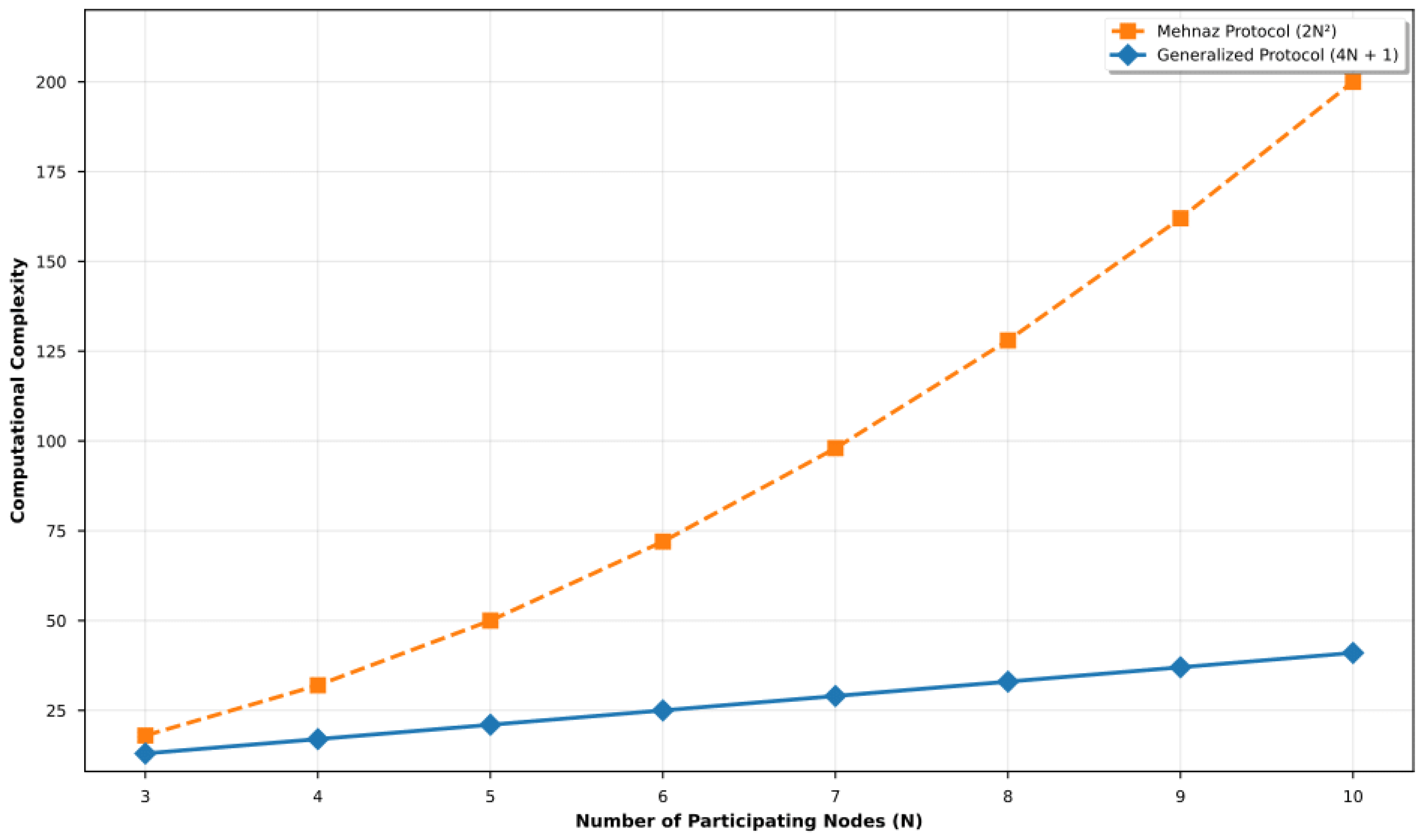
- Direct-sharing method: In this scheme, each participant, including the mediator, communicates directly with each other to share keys. This results in exchanges, added to the initially considered. The total complexity becomes , indicating a quadratic growth with additional linear and constant terms, which negatively affects scalability.
- Publish-subscribe (Pub-Sub) model: In this approach, each participant publishes their key on a shared channel accessible to all others, requiring N write operations. Subsequently, each participant reads the keys of the others, generating N additional reads. This introduces exchanges for key sharing, which added to the initial results in , producing linear complexity with an additional constant term. This model improves communication efficiency and enhances the scalability of the protocol.
4.2. Computational Complexity of the Proposed Protocol as a Function of N
- denotes encryption operations.
- denotes decryption operations.
- denotes homomorphic transformations.
- Key generation: performed by the mediator (1 operation).
- Individual encryption: each participant performs one encryption (n operations).
- Sequential aggregation: requires homomorphic operations.
- Final decryption: performed by the trusted entity (1 operation).
- Non-interactive verification: each participant conducts verification checks (n operations).
- Distributed key generation: each participant generates a public-private key pair (N operations).
- Parallel encryption: operations are executed.
- Multiple re-encryptions: transformations are required.
5. Proof of Concept in a Local Environment
5.1. Experimental Setup
- Operating system: Ubuntu Server 24.04 LTS
- CPU: Each machine utilized a Ryzen 5 3500U processor.
- RAM: 2 GB per machine.
- Storage: 10 GB per machine.
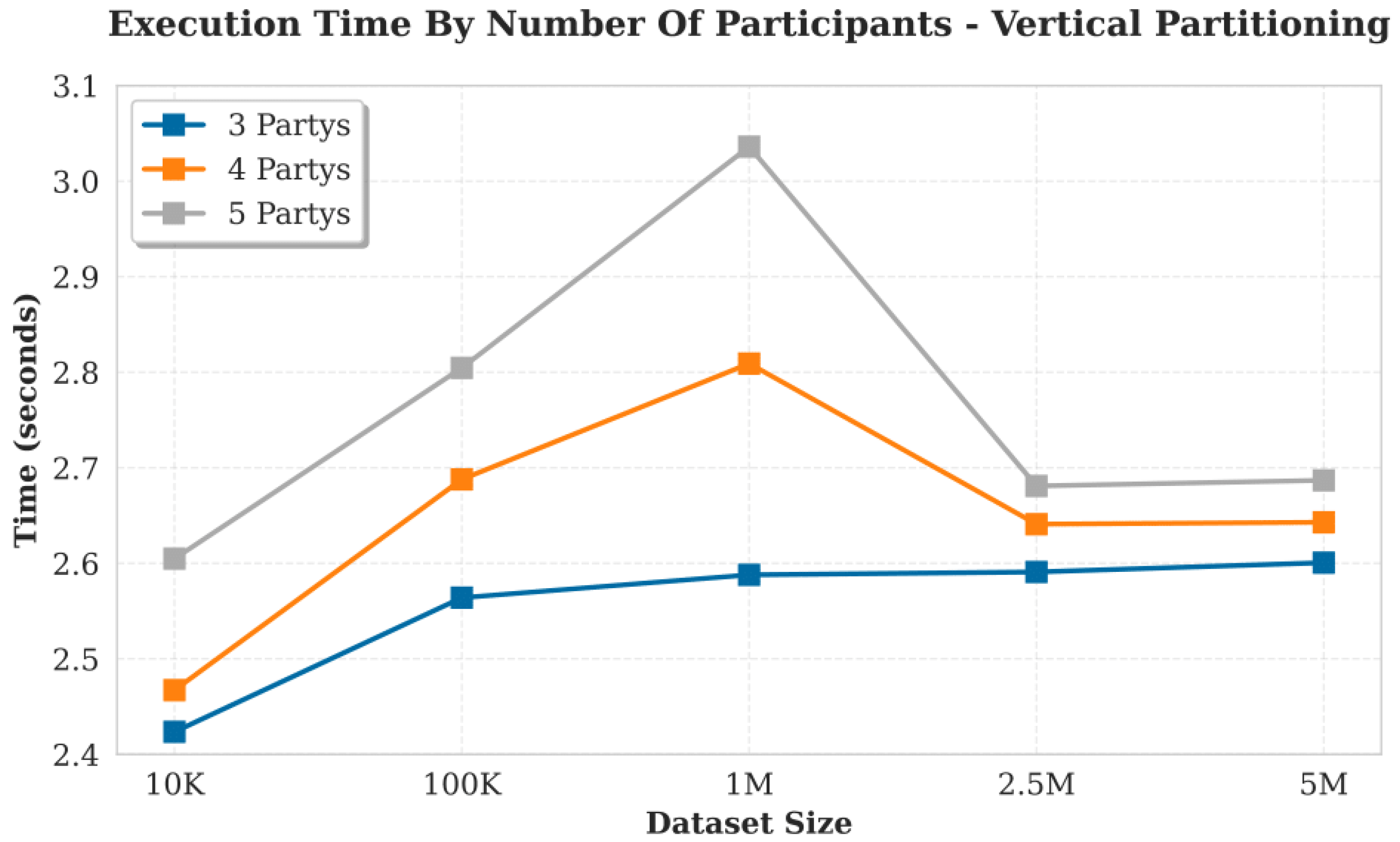
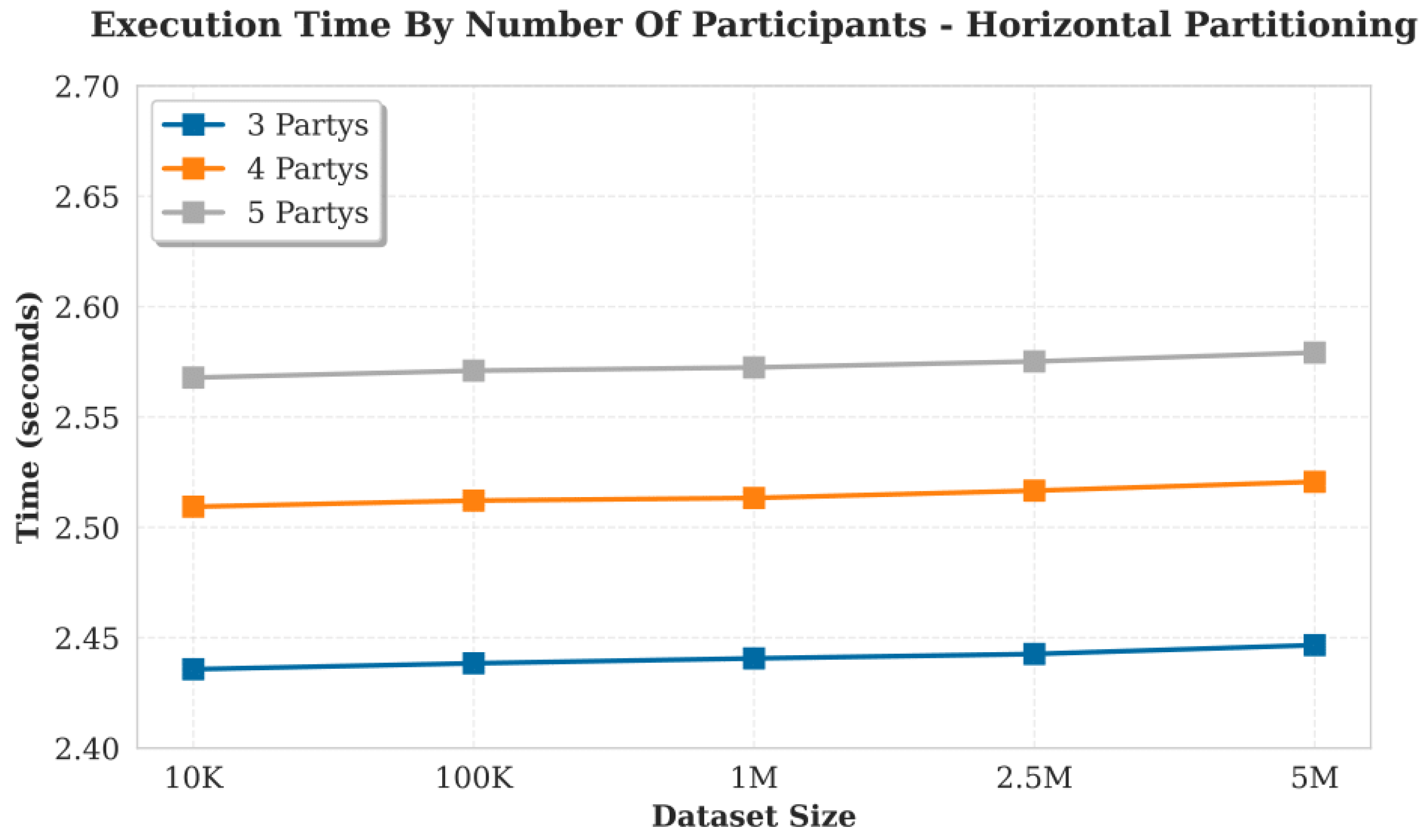
5.2. Performance of the Proof of Concept
5.3. Result of the Proof of Concept
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Yu, C.; Shen, S.; Wang, S.; Zhang, K.; Zhao, H. Communication-Efficient Hybrid Federated Learning for E-Health with Horizontal and Vertical Data Partitioning. IEEE Trans. Neural Netw. Learn. Syst. 2024, 36, 5614–5628. [Google Scholar] [CrossRef] [PubMed]
- Mishra, A.; Saha, S.; Mishra, S.; Bagade, P. A federated learning approach for smart healthcare systems. CSI Trans. ICT 2023, 11, 39–44. [Google Scholar] [CrossRef]
- Lian, Z.; Yang, Q.; Wang, W.; Zeng, Q.; Alazab, M.; Zhao, H.; Su, C. DEEP-FEL: Decentralized, Efficient and Privacy-Enhanced Federated Edge Learning for Healthcare Cyber Physical Systems. IEEE Trans. Netw. Sci. Eng. 2022, 9, 3558–3569. [Google Scholar] [CrossRef]
- Ni, W.; Ao, H.; Tian, H.; Eldar, Y.; Niyato, D. FedSL: Federated Split Learning for Collaborative Healthcare Analytics on Resource-Constrained Wearable IoMT Devices. IEEE Internet Things J. 2024, 11, 18934–18935. [Google Scholar] [CrossRef]
- Aminifar, A.; Shokri, M.; Aminifar, A. Privacy-Preserving Edge Federated Learning for Intelligent Mobile-Health Systems. Future Gener. Comput. Syst. 2024, 161, 625–637. [Google Scholar] [CrossRef]
- Armknecht, F.; Boyd, C.; Carr, C.; Gjøsteen, K.; Jäschke, A.; Reuter, C.A.; Strand, M. A guide to fully homomorphic encryption. Cryptol. ePrint Arch. 2015. Available online: https://eprint.iacr.org/2015/1192 (accessed on 24 June 2025).
- Fan, J.; Vercauteren, F. Somewhat practical fully homomorphic encryption. Cryptol. ePrint Arch. 2012. Available online: https://eprint.iacr.org/2012/144 (accessed on 24 June 2025).
- Damgård, I.; Jurik, M. A generalization, a simplification and some applications of Paillier’s probabilistic public-key system. In Public Key Cryptography: 4th International Workshop on Practice and Theory in Public Key Cryptosystems, PKC 2001, Cheju Island, Korea, February 13–15, 2001 Proceedings 4; Springer: Berlin/Heidelberg, Germany, 2001; pp. 119–136. [Google Scholar]
- Paillier, P. Paillier Encryption and Signature Schemes. In Encyclopedia of Cryptography and Security; Springer: Berlin/Heidelberg, Germany, 2005. [Google Scholar]
- Kleinjung, T.; Aoki, K.; Franke, J.; Lenstra, A.K.; Thomé, E.; Bos, J.W.; Gaudry, P.; Kruppa, A.; Montgomery, P.L.; Osvik, D.A.; et al. Factorization of a 768-bit RSA modulus. In Advances in Cryptology—CRYPTO 2010: 30th Annual Cryptology Conference, Santa Barbara, CA, USA, August 15–19, 2010. Proceedings 30; Springer: Berlin/Heidelberg, Germany, 2010; pp. 333–350. [Google Scholar]
- Luo, Y.; Ouyang, X.; Liu, J.; Cao, L. An image encryption method based on elliptic curve elgamal encryption and chaotic systems. IEEE Access 2019, 7, 38507–38522. [Google Scholar] [CrossRef]
- Das, A.; Castiglia, T.; Wang, S.; Patterson, S. Cross-Silo Federated Learning for Multi-Tier Networks with Vertical and Horizontal Data Partitioning. ACM Trans. Intell. Syst. Technol. (TIST) 2021, 13, 1–27. [Google Scholar] [CrossRef]
- Braun, L.; Demmler, D.; Schneider, T.; Tkachenko, O. MOTION—A Framework for Mixed-Protocol Multi-Party Computation. ACM Trans. Priv. Secur. 2022, 25, 1–35. [Google Scholar] [CrossRef]
- Abascal, J.; Sereshgi, M.H.F.; Hazay, C.; Ishai, Y.; Venkitasubramaniam, M. Is the Classical GMW Paradigm Practical? The Case of Non-Interactive Actively Secure 2PC. In Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, Online, 9–13 November 2020. [Google Scholar] [CrossRef]
- Lindell, Y.; Pinkas, B.; Smart, N.; Yanai, A. Efficient Constant-Round Multi-party Computation Combining BMR and SPDZ. J. Cryptol. 2019, 32, 1026–1069. [Google Scholar] [CrossRef]
- Mehnaz, S.; Bellala, G.; Bertino, E. A secure sum protocol and its application to privacy-preserving multi-party analytics. In Proceedings of the 22nd ACM on Symposium on Access Control Models and Technologies, Indianapolis, IN, USA, 21–23 June 2017; pp. 219–230. [Google Scholar]
- Hao, F. Schnorr Non-Interactive Zero-Knowledge Proof; RFC 8235; Newcastle University: Newcastle upon Tyne, UK, 2017. [Google Scholar]
- Dimitoglou, G.; Jim, C. Performance Evaluation of Partially Homomorphic Encryption Algorithms. In Proceedings of the 2022 International Conference on Computational Science and Computational Intelligence (CSCI), Las Vegas, NV, USA, 14–16 December 2022; pp. 910–915. [Google Scholar] [CrossRef]
- Pistono, M.; Bellafqira, R.; Coatrieux, G. Cryptosystem Conversion, Packing and Matrix Processing of Homomorphically Encrypted Data: Application to IOT Devices. IEEE Access 2021, 9, 28302–28316. [Google Scholar] [CrossRef]
- Li, J.; Yao, W.; Han, J.; Zhang, Y.; Shen, J. User Collusion Avoidance CP-ABE With Efficient Attribute Revocation for Cloud Storage. IEEE Syst. J. 2018, 12, 1767–1777. [Google Scholar] [CrossRef]
- Patil, S.; Purushothama, B.R. Non-transitive and collusion resistant quorum controlled proxy re-encryption scheme for resource constrained networks. J. Inf. Secur. Appl. 2020, 50, 102411. [Google Scholar] [CrossRef]
- Jutla, C.; Roy, A. Shorter Quasi-Adaptive NIZK Proofs for Linear Subspaces. J. Cryptol. 2013, 30, 1116–1156. [Google Scholar] [CrossRef]
- Ranbaduge, T.; Vatsalan, D.; Christen, P. Secure multi-party summation protocols: Are they secure enough under collusion? Trans. Data Priv. 2020, 13, 25–60. [Google Scholar]
- Acar, A.; Aksu, H.; Uluagac, A.S.; Conti, M. A survey on homomorphic encryption schemes: Theory and implementation. ACM Comput. Surv. (CSUR) 2018, 51, 1–35. [Google Scholar] [CrossRef]
- Koç, Ç.K.; Özdemir, F.; Ödemiş Özger, Z. Damgård-Jurik Algorithm. In Partially Homomorphic Encryption; Springer: Cham, Switzerland, 2021; pp. 107–121. [Google Scholar]
- Ruzai, W.N.A.; Ariffin, M.; Asbullah, M.A.; Mahad, Z.; Nawawi, A. On the Improvement Attack Upon Some Variants of RSA Cryptosystem via the Continued Fractions Method. IEEE Access 2020, 8, 80997–81006. [Google Scholar] [CrossRef]
- Nitaj, A.; Ariffin, M.; Adenan, N.N.H.; Lau, T.; Chen, J. Security Issues of Novel RSA Variant. IEEE Access 2022, 10, 53788–53796. [Google Scholar] [CrossRef]
- Agal, M.; Kishan, K.; Shashidhar, R.; Vantmuri, S.S.; Honnavalli, P. Non-interactive zero-knowledge proof based authentication. In Proceedings of the 2021 IEEE Mysore Sub Section International Conference (MysuruCon), Hassan, India, 24–25 October 2021; pp. 837–843. [Google Scholar]
- Kumar, V.; Kumar, R.; Barbhuiya, M.A.; Saikia, M. Multiple Encryption using ECC and its Time Complexity Analysis. Int. J. Comput. Eng. Res. Trends 2016, 3, 568–572. [Google Scholar] [CrossRef]
- Escobar Jara, F.A.; Fenner Lopez, J.E. ESMC_Damgard-Juric, Zenodo: Geneva, Switzerland, 2025. [CrossRef]

| Attack Type | Resistance Level |
|---|---|
| Interception attack (MITM, Sniffing) | Secure (encrypted values traverse the network and cannot be decrypted without the mediator’s private key). |
| Forced decryption attack (ciphertext cryptanalysis) | Secure (Damgård–Jurik is asymmetric and RSA-based, offering resistance to factorization attacks). |
| Partial sum attack (deduction attack) | Partially vulnerable if parties collude (they may reconstruct the remaining participant’s value). |
| Brute force attacks | Secure, provided large key sizes are used (typically 2048 bits or higher). |
| Compromised private key attack | Vulnerable if the mediator’s private key is stolen (all encrypted values could be decrypted). |
| Protocol | Communication Complexity | Computational Complexity | |
|---|---|---|---|
| Broker Communication | Direct Communication | ||
| Mehnaz protocol | |||
| Proposed protocol (Damgård–Jurik Based) | — | ||
| Attribute 1 | Attribute 2 | Attribute 3 | Attribute 4 |
|---|---|---|---|
| 80 | 110 | 40 | 60 |
| 92 | 120 | 60 | 86 |
| 78 | 100 | 90 | 73 |
| Attribute 1 | Attribute 2 | Attribute 3 | Attribute 4 |
| 80 | 110 | 40 | 60 |
| 92 | 120 | 60 | 86 |
| 78 | 100 | 90 | 73 |
| Protocol | Nodes | Key Gen (s) | SD | Key Dist (s) | SD | Enc (s) | SD | Dec (s) | SD |
|---|---|---|---|---|---|---|---|---|---|
| Proposed | 4 | 0.89128 | 0.2041 | 0.9645 | 0.5619 | 0.3019 | 0.0526 | 0.3398 | 0.0434 |
| Mehnaz | 4 | 13.4363 | 7.4428 | 20.2525 | 6.3362 | 2.9850 | 0.5626 | 1.5040 | 0.8516 |
| Proposed | 5 | 0.9778 | 0.3400 | 0.9721 | 0.5357 | 0.3541 | 0.0854 | 0.3642 | 0.0611 |
| Mehnaz | 5 | 15.0448 | 6.9638 | 23.2300 | 7.0628 | 2.7923 | 0.4032 | 1.2717 | 0.7915 |
| Protocol | Nodes | ZKP Val. (s) | SD | Total (s) | SD |
|---|---|---|---|---|---|
| Proposed | 4 | 0.2171 | 0.0807 | 3.3177 | 0.1882 |
| Mehnaz | 4 | 0.0000 | 0.0000 | 55.4722 | 2.9796 |
| Proposed | 5 | 0.2133 | 0.0590 | 3.4906 | 0.3806 |
| Mehnaz | 5 | 0.0000 | 0.0000 | 82.6498 | 11.4219 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fenner-López, J.; Castillo-Muñoz, C.; Escobar-Jara, F.; Bustamante-Mora, A.; Burgos-López, M. Enhancing Secure Multi-Party Computation with Damgård–Jurik and NIZK Proofs: A Lightweight Protocol for Scalable Aggregation. Appl. Sci. 2025, 15, 10357. https://doi.org/10.3390/app151910357
Fenner-López J, Castillo-Muñoz C, Escobar-Jara F, Bustamante-Mora A, Burgos-López M. Enhancing Secure Multi-Party Computation with Damgård–Jurik and NIZK Proofs: A Lightweight Protocol for Scalable Aggregation. Applied Sciences. 2025; 15(19):10357. https://doi.org/10.3390/app151910357
Chicago/Turabian StyleFenner-López, Julio, Carlos Castillo-Muñoz, Francisco Escobar-Jara, Ana Bustamante-Mora, and María Burgos-López. 2025. "Enhancing Secure Multi-Party Computation with Damgård–Jurik and NIZK Proofs: A Lightweight Protocol for Scalable Aggregation" Applied Sciences 15, no. 19: 10357. https://doi.org/10.3390/app151910357
APA StyleFenner-López, J., Castillo-Muñoz, C., Escobar-Jara, F., Bustamante-Mora, A., & Burgos-López, M. (2025). Enhancing Secure Multi-Party Computation with Damgård–Jurik and NIZK Proofs: A Lightweight Protocol for Scalable Aggregation. Applied Sciences, 15(19), 10357. https://doi.org/10.3390/app151910357









