Empirical Evaluation of TLS-Enhanced MQTT on IoT Devices for V2X Use Cases
Abstract
1. Introduction
- End-to-end implementation and evaluation on physical IoT hardware: We deploy all MQTT roles, i.e., broker, publisher, and subscriber, on separate Raspberry Pi 4B boards, leveraging Paho-MQTT, Mosquitto, and OpenSSL for TLS 1.3. This provides an empirical edge-device testbed, moving beyond prior VM- or simulation-based studies and enabling direct measurement of resource demands under realistic hardware constraints.
- Comprehensive profiling of TLS-secured MQTT: We systematically benchmark the impact of TLS 1.3 on MQTT performance, quantifying CPU cycles, execution time, energy consumption, memory usage, and goodput for each MQTT role and each phase of the TLS protocol, over both Ethernet and WiFi. We provide a direct, side-by-side comparison of the ChaCha20_Poly1305 and AES_256_GCM cipher suites, highlighting their suitability for constrained V2X and IoT deployment.
- Standard-driven analysis of message packaging strategies: We evaluate the effect of five distinct message size/count configurations, mapped to V2X-relevant standards, on system performance and resource consumption. This analysis provides actionable insights into the trade-offs among batching, latency, goodput, and energy efficiency, guiding application-specific protocol configuration.
- Empirical foundation for real-world deployment: Our results synthesize practical recommendations for selecting secure communication parameters, optimizing for both performance and energy efficiency in real-world, resource-constrained vehicular and IoT environments.
2. Related Work
2.1. Lightweight Cryptographic Protocols and IoT
2.2. Lightweight IoT Protocols and V2X
2.3. TLS-Secured MQTT and IoT
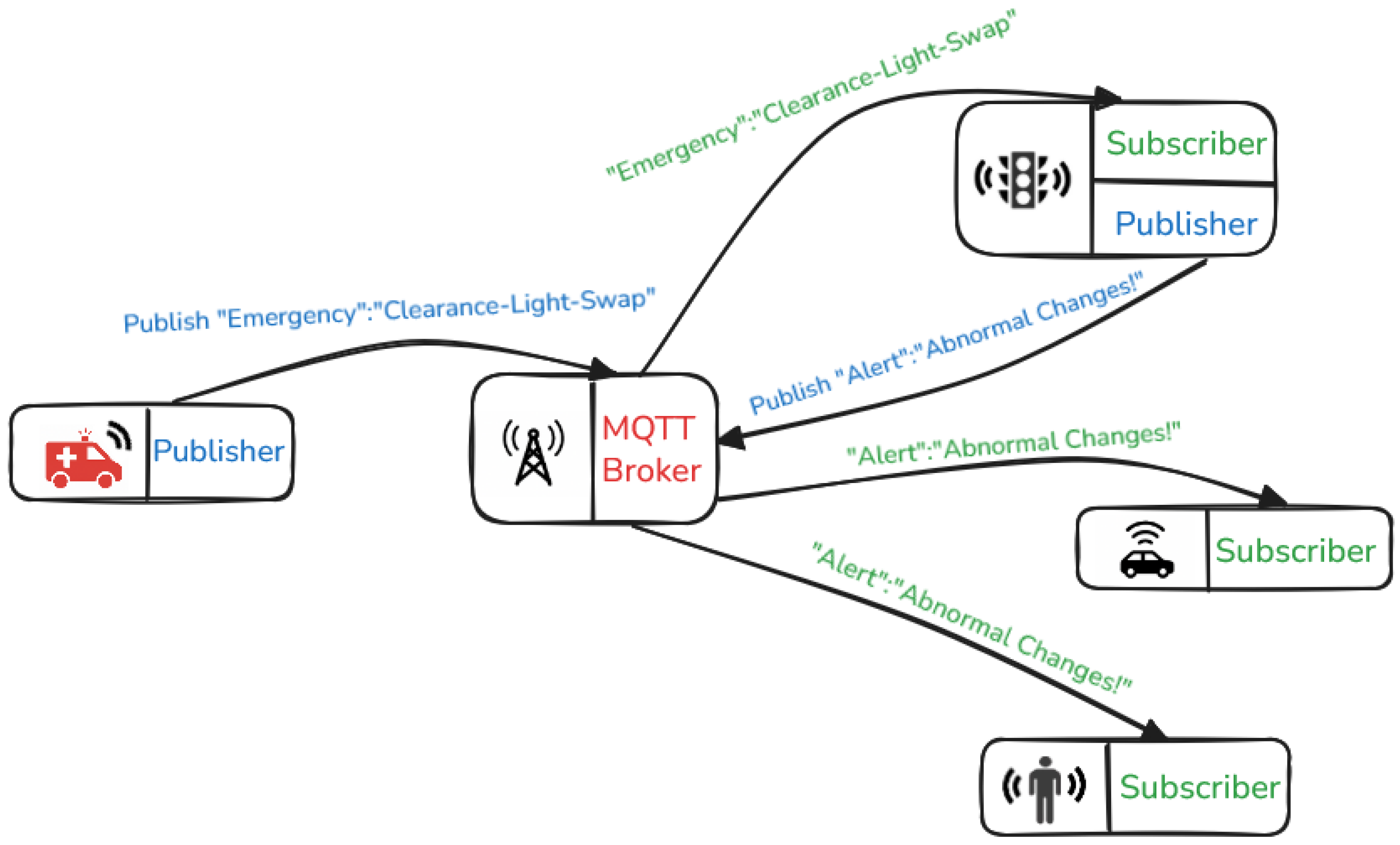
3. MQTT and V2X Use Cases
4. Implementation and Methodology Overview
4.1. Experimental Setup and Metrics
4.2. Libraries
4.3. Benchmarking Strategy
5. Performance Evaluation
5.1. TLS Handshake Evaluation
5.2. Symmetric Encryption Evaluation
6. Discussion and Future Work Directions
- Quality of Service (QoS) analysis under load and mobility: Although the current study focused on MQTT QoS level 1, further research could explore the performance implications of QoS levels 0 and 2 under different traffic intensities and mobility patterns. Evaluating packet delivery guarantees, retransmission overhead, and latency under WiFi and 5G mobility scenarios could offer critical insights for QoS selection in highly dynamic V2X contexts.
- Feasibility in Ultra-Constrained Platforms (ESP32, ARM Cortex-M, etc.): It would be worthwhile to assess the feasibility of TLS -secured MQTT on highly constrained platforms, such as ESP32 or ARM Cortex-M microcontrollers, which are common in low-power embedded deployment. Benchmarking these devices in terms of handshake execution time, memory usage, and cipher suite performance could help define minimum operational thresholds for secure communication in the most resource-limited environments.
- Wireless Network Dynamics and TLS Session Robustness: Wireless environments are prone to jitter, handoffs, and dynamic IP address changes, all of which may affect the stability of TLS sessions. Investigating how these dynamics influence session persistence, reconnection latency, and throughput degradation, particularly in realistic multi-hop WiFi or 5G networks, would provide valuable evidence for secure session design in mobile IoT applications.
- MQTT and CoAP Comparison in V2X Contexts: Another promising direction would be a comparative analysis of MQTT over TLS and DTLS-secured CoAP in realistic V2X environments. Such a study could examine key performance metrics, such as end-to-end latency, bandwidth efficiency, fault tolerance, and energy consumption, to determine the suitability of each protocol for time- and safety-critical applications such as hazard notifications or vehicular telemetry. Additional focus could be placed on the protocol behavior under network congestion and retransmission conditions.
- Post-Quantum Cryptography on Resource-Constrained Devices: Finally, as TLS 1.3 evolves to support quantum-resistant cryptographic primitives, it would be interesting to investigate the feasibility of the Kyber, Dilithium, and SPHINCS+ algorithms [44,45], recently standardized by NIST, on ARMv8-based IoT platforms. These schemes introduce larger keys and higher computational demands, raising questions about their impact on handshake latency, energy consumption, and memory usage. Future studies could explore both Key Encapsulation Mechanisms (e.g., Kyber-KEM) and Digital Signature Algorithms (e.g., Dilithium and SPHINCS+) in real-world IoT hardware, extending earlier simulation-based assessments such as those by Opilka et al. [11].
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| ACE | Authentication and Authorization in Constrained Environments |
| ADAS | Advanced Driver Assistance System |
| AES | Advanced Encryption Standard |
| ABE | Attribute-Based Encryption |
| BSM | Basic Safety Message |
| CA | Certificate Authority |
| C-ITS | Cooperative-Intelligent Transport System |
| CoAP | Constrained Application Protocol |
| CAM | Cooperative Awareness Message |
| CPU | Central Processing Unit |
| C-V2X | Cellular V2X |
| DENM | Decentralized Environmental Notification Message |
| DES | Data Encryption Standard |
| DTLS | Datagram Trasport Layer Security |
| ECC | Elliptic Curve Cryptography |
| ECDHE | Elliptic Curve Diffie–Hellman Ephemeral |
| GPS | Global Positioning System |
| IBC | Identity-Based Cryptography |
| IoT | Internet of Things |
| MIN | Multi-Identifier Network |
| MQTT | Message Queuing Telemetry Transport |
| M2M | Machine-to-Machine |
| OBU | On-Board Unit |
| OTA | Over the air |
| QoS | Quality of Service |
| ROS | Robot Operating System |
| RSA | Rivest, Shamir, and Adelman |
| RQ | Research question |
| RSS | Resident Set Size |
| RSU | Road-Side Unit |
| SpaT | Signal Phase and Timing |
| TLS | Transport Layer Security |
| TCP/IP | Transmission Control Protocol/Internet Protocol |
| VM | Virtual machine |
| V2I | Vehicle to Infrastructure |
| V2N | Vehicle to Network |
| V2P | Vehicle to Pedestrian |
| V2V | Vehicle to Vehicle |
| V2X | Vehicle to Everything |
| WiFi | Wireless Fidelity |
| WSN | Wireless Sensor Network |
References
- Tariq, U.; Ahmed, I.; Bashir, A.K.; Shaukat, K. A critical cybersecurity analysis and future research directions for the internet of things: A comprehensive review. Sensors 2023, 23, 4117. [Google Scholar] [CrossRef] [PubMed]
- Shanmugapriya, D.; Patel, A.; Srivastava, G.; Lin, J.C.W. MQTT protocol use cases in the Internet of Things. In Proceedings of the Big Data Analytics: 9th International Conference, BDA 2021, Virtual Event, 15–18 December 2021; Springer: Berlin/Heidelberg, Germany, 2021; pp. 146–162. [Google Scholar]
- Silva, D.; Carvalho, L.I.; Soares, J.; Sofia, R.C. A Performance Analysis of Internet of Things Networking Protocols: Evaluating MQTT, CoAP, OPC UA. Appl. Sci. 2021, 11, 4879. [Google Scholar] [CrossRef]
- Seoane, V.; Garcia-Rubio, C.; Almenares, F.; Campo, C. Performance evaluation of CoAP and MQTT with security support for IoT environments. Comput. Netw. 2021, 197, 108338. [Google Scholar] [CrossRef]
- Thangavel, D.; Ma, X.; Valera, A.; Tan, H.X.; Tan, C.K.Y. Performance evaluation of MQTT and CoAP via a common middleware. In Proceedings of the 2014 IEEE Ninth International Conference on Intelligent Sensors, Sensor Networks and Information Processing (ISSNIP), Singapore, 21–24 April 2014; pp. 1–6. [Google Scholar]
- Çorak, B.H.; Okay, F.; Güzel, M.; Murt, S.; Ozdemir, S. Comparative Analysis of IoT Communication Protocols. In Proceedings of the 2018 International Symposium on Networks, Computers and Communications (ISNCC), Rome, Italy, 19–21 June 2018; pp. 1–6. [Google Scholar]
- Dimov, V.; Kirdan, E.; Pahl, M.O. Resource tradeoffs for TLS-secured MQTT-based IoT Management. In Proceedings of the NOMS 2022-2022 IEEE/IFIP Network Operations and Management Symposium, Budapest, Hungary, 25–29 April 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–6. [Google Scholar]
- Alsukayti, I.S. A multidimensional internet of things testbed system: Development and evaluation. Wirel. Commun. Mob. Comput. 2020, 2020, 8849433. [Google Scholar] [CrossRef]
- Papadopoulos, G.Z.; Gallais, A.; Schreiner, G.; Jou, E.; Noel, T. Thorough IoT testbed characterization: From proof-of-concept to repeatable experimentations. Comput. Netw. 2017, 119, 86–101. [Google Scholar] [CrossRef]
- Farina, L.; Piccoli, M.; Iandolo, S.; Solida, A.; Grazia, C.A.; Raviglione, F.; Casetti, C.; Bazzi, A. Low Cost C-ITS Stations Using Raspberry Pi and the Open Source Software OScar. arXiv 2025, arXiv:2503.15461. [Google Scholar]
- Opiłka, F.; Niemiec, M.; Gagliardi, M.; Kourtis, M.A. Performance analysis of post-quantum cryptography algorithms for digital signature. Appl. Sci. 2024, 14, 4994. [Google Scholar] [CrossRef]
- Rana, M.; Mamun, Q.; Islam, R. Lightweight cryptography in IoT networks: A survey. Future Gener. Comput. Syst. 2022, 129, 77–89. [Google Scholar] [CrossRef]
- Thabit, F.; Can, O.; Aljahdali, A.O.; Al-Gaphari, G.H.; Alkhzaimi, H.A. Cryptography algorithms for enhancing IoT security. Internet Things 2023, 22, 100759. [Google Scholar] [CrossRef]
- Mandal, M.; Sharma, G.; Bala, S.; Verma, A.K. Feasibility of public key cryptography in wireless sensor networks. J. Theor. Phys. Cryptogr. 2014, 7, 20–24. [Google Scholar]
- Ambrosin, M.; Anzanpour, A.; Conti, M.; Dargahi, T.; Moosavi, S.R.; Rahmani, A.M.; Liljeberg, P. On the feasibility of attribute-based encryption on internet of things devices. IEEE Micro 2016, 36, 25–35. [Google Scholar] [CrossRef]
- Karantaidou, I.; Halkidis, S.T.; Petridou, S.; Mamatas, L.; Stephanides, G. Pairing-based cryptography on the Internet of Things: A feasibility study. In Proceedings of the International Conference on Wired/Wireless Internet Communication, Boston, MA, USA, 18–20 June 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 219–230. [Google Scholar]
- Gavriilidis, N.O.; Halkidis, S.T.; Mjeda, A.; Petridou, S. Identity-Based Cryptography on IoT devices: Balancing security and efficiency for modern use cases. In Proceedings of the 2024 IEEE Future Networks World Forum (FNWF), Dubai, United Arab Emirates, 15–17 October 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 273–278. [Google Scholar]
- Amanlou, S.; Bakar, K.A.A. Lightweight security mechanism over MQTT protocol for IoT devices. Int. J. Adv. Comput. Sci. Appl. 2020, 11, 202–207. [Google Scholar] [CrossRef]
- Chavan, A.A.; Nighot, M.K. Secure and cost-effective application layer protocol with authentication interoperability for IOT. Procedia Comput. Sci. 2016, 78, 646–651. [Google Scholar] [CrossRef]
- De Oliveira, D.L.; Veloso, A.F.d.S.; Sobral, J.V.; Rabêlo, R.A.; Rodrigues, J.J.; Solic, P. Performance evaluation of mqtt brokers in the internet of things for smart cities. In Proceedings of the 2019 4th International Conference on Smart and Sustainable Technologies (SpliTech), Split, Croatia, 18–21 June 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]
- Ebleme, M.A.; Bayilmis, C.; Cavusoglu, U. Examination and performance evaluation of mqtt. In Proceedings of the 3rd International Conference on Computer Science and Engineering, Sarajevo, Bosnia and Herzegovina, 20–23 September 2018; pp. 246–250. [Google Scholar]
- Katsikeas, S.; Fysarakis, K.; Miaoudakis, A.; Van Bemten, A.; Askoxylakis, I.; Papaefstathiou, I.; Plemenos, A. Lightweight & secure industrial IoT communications via the MQ telemetry transport protocol. In Proceedings of the 2017 IEEE Symposium on Computers and Communications (ISCC), Heraklion, Greece, 3–6 July 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1193–1200. [Google Scholar]
- Michaelides, M.; Sengul, C.; Patras, P. An experimental evaluation of MQTT authentication and authorization in IoT. In Proceedings of the 15th ACM Workshop on Wireless Network Testbeds, Experimental evaluation & Characterization, New Orleans, LA, USA, 31 January–4 February 2022; pp. 69–76. [Google Scholar]
- Ferrari, P.; Sisinni, E.; Brandão, D.; Rocha, M. Evaluation of communication latency in industrial IoT applications. In Proceedings of the 2017 IEEE International Workshop on Measurement and Networking (M & N), Naples, Italy, 27–29 September 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–6. [Google Scholar]
- Yadav, P.S. Enhancing Real-Time Data Communication and Security in Connected Vehicles Using MQTT Protocol. J. Artif. Intell. Cloud Comput. 2022, 1, 2–6. [Google Scholar] [CrossRef]
- Reiher, L.; Lampe, B.; Woopen, T.; Van Kempen, R.; Beemelmanns, T.; Eckstein, L. Enabling connectivity for automated mobility: A novel mqtt-based interface evaluated in a 5g case study on edge-cloud lidar object detection. In Proceedings of the 2022 International Conference on Electrical, Computer, Communications and Mechatronics Engineering (ICECCME), Malé, Maldives, 16–18 November 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–9. [Google Scholar]
- Gupta, H.; Nayak, A. Security Architecture for Vehicle to Emergency Services (V2S) Communicating Over MQTT-SN. In Proceedings of the 2024 IEEE 100th Vehicular Technology Conference (VTC2024-Fall), Washington, DC, USA, 7–10 October 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 1–6. [Google Scholar]
- Chen, Y.; Li, H.; Bai, H.; Ding, Z.; Guo, Z.; Wang, X.; Lu, P. MIN-MQTT: A Publish/Subscribe Approach Based on Multi-Identifier Network in V2X. In Proceedings of the 2024 3rd International Joint Conference on Information and Communication Engineering (JCICE), Fuzhou, China, 10–12 May 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 6–12. [Google Scholar]
- Raslan, W.; El Sherbiny, Z.A.; saad Mohamed, M.; Eid, N.E.N.S.; Elmasry, M.A.Y.; Mawla, A.E.A.; Shabana, A.M.; Soliman, E.H.; ELshamy, H.A.; Hassan, K.M.; et al. Smart Vehicle Safety: AI-Driven Driver Assistance and V2X Communications. In Proceedings of the 2024 international telecommunications conference (ITC-Egypt), Cairo, Egypt, 22–25 July 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 787–792. [Google Scholar]
- Viterbo, R.; Campolo, F.; Cerutti, M.; Awasthi, S.S.; Arrigoni, S.; Brambilla, M.; Nicoli, M. A 5G Roadside Infrastructure Assisting Connected and Automated Vehicles in Vulnerable Road User Protection. IEEE Open J. Intell. Transp. Syst. 2025, 6, 346–362. [Google Scholar] [CrossRef]
- Oliva, F.; Landolfi, E.; Salzillo, G.; Massa, A.; D’Onghia, S.M.; Troiano, A. Implementation and Testing of V2I Communication Strategies for Emergency Vehicle Priority and Pedestrian Safety in Urban Environments. Sensors 2025, 25, 485. [Google Scholar] [CrossRef] [PubMed]
- AJ, B.; Kaythry, P. Secure IoV communications for smart fleet systems empowered with ASCON. Sci. Rep. 2025, 15, 19103. [Google Scholar] [CrossRef] [PubMed]
- Zitouni, R.; Petit, J.; Djoudi, A.; George, L. IoT-based urban traffic-light control: Modelling, prototyping and evaluation of MQTT protocol. In Proceedings of the 2019 International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Atlanta, GA, USA, 14–17 July 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 182–189. [Google Scholar]
- Palos-Angulo, F.A.; Ruiz-Ibarra, E.C. Secure MQTT emergency messaging system for C-V2X networks based on IoT. J. Inf. Technol. 2022, 9, 7–16. [Google Scholar] [CrossRef]
- Vermesan, O.; Bahr, R.; Falcitelli, M.; Brevi, D.; Bosi, I.; Dekusar, A.; Velizhev, A.; Alaya, M.B.; Firmani, C.; Simeon, J.F.; et al. IoT technologies for connected and automated driving applications. In Internet of Things—The Call of the Edge; River Publishers: Gistrup, Denmark, 2022; pp. 255–306. [Google Scholar]
- Papadakis, A.; Mamatas, L.; Petridou, S. Investigating the latency dynamics in vehicular platooning networks. In Proceedings of the 2024 IEEE International Mediterranean Conference on Communications and Networking (MeditCom), Madrid, Spain, 8–11 July 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 371–376. [Google Scholar]
- Mishra, N.; Verma, L.P.; Srivastava, P.K.; Gupta, A. An analysis of IoT congestion control policies. Procedia Comput. Sci. 2018, 132, 444–450. [Google Scholar] [CrossRef]
- Kegenbekov, Z.; Saparova, A. Using the MQTT protocol to transmit vehicle telemetry data. Transp. Res. Procedia 2022, 61, 410–417. [Google Scholar] [CrossRef]
- European Telecommunications Standards Institute (ETSI). Intelligent Transport Systems (ITS); Vehicular Communications; Basic Set of Applications; Part 2: Specification of Cooperative Awareness Basic Service. 2019. Available online: https://www.etsi.org/deliver/etsi_en/302600_302699/30263702/01.03.02_60/en_30263702v010302p.pdf (accessed on 21 July 2021).
- SAE International. V2X Communications Message Set Dictionary. 2020. Available online: https://www.sae.org/standards/content/j2735_202007/ (accessed on 21 July 2021).
- 3rd Generation Partnership Project (3GPP). Study on Enhancement of 3GPP Support for 5G V2X Services. Technical Report 22.886, 3GPP. 2020. Available online: https://www.3gpp.org/DynaReport/22886.htm (accessed on 21 July 2021).
- European Telecommunications Standards Institute (ETSI). 5G; Service Requirements for Enhanced V2X Scenarios (3GPP TS 22.186 Version 16.2.0 Release 16). 2020. Available online: https://www.etsi.org/deliver/etsi_ts/122100_122199/122186/16.02.00_60/ts_122186v160200p.pdf (accessed on 21 July 2021).
- SAE International. Relating Experimental Drive Distraction and Driving Performance Metrics to Crash Involvement. 2018. Available online: https://www.sae.org/standards/content/j3151_201810/ (accessed on 21 July 2021).
- Lyubashevsky, V. Basic Lattice Cryptography: The Concepts behind Kyber (ML-KEM) and Dilithium (ML-DSA). Cryptology ePrint Archive, Report 2024/1287. 2024. Available online: https://eprint.iacr.org/2024/1287 (accessed on 21 July 2021).
- Bernstein, D.J.; Hülsing, A.; Kölbl, S.; Niederhagen, R.; Rijneveld, J.; Schwabe, P. The SPHINCS+ signature framework. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 2129–2146. [Google Scholar]


| CoAP | MQTT | |
|---|---|---|
| Delay reduction | ✓ | ✕ |
| Minimized power consumption | ✓ | ✕ |
| Higher sleep time | ✓ | ✕ |
| Reliability | ✕ | ✓ |
| QoS flexibility | ✕ | ✓ |
| Congestion control | ✕ | ✓ |
| Client simplicity | ✕ | ✓ |
| CPU (Mcycles) | Execution Time (s) | Energy (J) | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Role | no-TLS | Key Exch. (ECDHE) | Server Auth (Ed25519) | Client Auth (Ed25519) | no-TLS | Key Exch. (ECDHE) | Server Auth (Ed25519) | Client Auth (Ed25519) | no-TLS | Key Exch. (ECDHE) | Server Auth (Ed25519) | Client Auth (Ed25519) |
| Publisher | 321 | |||||||||||
| Subscriber | 362 | 426 | ||||||||||
| Broker | 19 | |||||||||||
| Bytes | 16 B | 64 B | 256 B | 1 KB | 8 KB | |
|---|---|---|---|---|---|---|
| Cipher | ||||||
| AES_256_GCM (MB/s) | ||||||
| Chacha20_Poly1305 (MB/s) | 140 | |||||
| Role | ChaCha20 | AES-GCM | |||||
|---|---|---|---|---|---|---|---|
| 1000 × 100 B | 100 × 1000 B | 10 × 10,000 B | 1000 × 100 B | 100 × 1000 B | 10 × 10,000 B | ||
| ETH | Publisher | ||||||
| Subscriber | |||||||
| Broker | |||||||
| WIFI | Publisher | ||||||
| Subscriber | |||||||
| Broker | |||||||
| Role | ChaCha20 | AES-GCM | |||||
|---|---|---|---|---|---|---|---|
| 1000 × 100 B | 100 × 1000 B | 10 × 10,000 B | 1000 × 100 B | 100 × 1000 B | 10 × 10,000 B | ||
| ETH | Publisher | ||||||
| Subscriber | |||||||
| Broker | |||||||
| WIFI | Publisher | ||||||
| Subscriber | |||||||
| Broker | |||||||
| Role | ChaCha20 | AES-GCM | |||||
|---|---|---|---|---|---|---|---|
| 1000 × 100 B | 100 × 1000 B | 10 × 10,000 B | 1000 × 100 B | 100 × 1000 B | 10 × 10,000 B | ||
| ETH | Publisher | ||||||
| Subscriber | |||||||
| Broker | |||||||
| WIFI | Publisher | ||||||
| Subscriber | |||||||
| Broker | |||||||
| Role | Chacha20 | AES-GCM | |||||
|---|---|---|---|---|---|---|---|
|
100 KB (1000 × 100 B) |
1 MB (1000 × 1000 B) |
100 MB (10,000 × 10,000 B) |
100 KB (1000 × 100 B) |
1 MB (1000 × 1000 B) |
100 MB (10,000 × 10,000 B) | ||
| ETH | Publisher | 10,071 ± 84.7 | 10,170.3 ± 95.5 | ||||
| Subscriber | 13,325.3 ± 294.7 | ||||||
| Broker | |||||||
| WIFI | Publisher | ||||||
| Subscriber | |||||||
| Broker | |||||||
| Role | ChaCha20 | AES-GCM | |||||
|---|---|---|---|---|---|---|---|
|
100 KB (1000 × 100 B) |
1 MB (1000 × 1000 B) |
100 MB (10,000 × 10,000 B) |
100 KB (1000 × 100 B) |
1 MB (1000 × 1000 B) |
100 MB (10,000 × 10,000 B) | ||
| ETH | Publisher | ||||||
| Subscriber | |||||||
| Broker | |||||||
| WIFI | Publisher | ||||||
| Subscriber | |||||||
| Broker | |||||||
| Role | ChaCha20 | AES-GCM | |||||
|---|---|---|---|---|---|---|---|
|
100 KB (1000 × 100 B) |
1 MB (1000 × 1000 B) |
100 MB (10,000 × 10,000 B) |
100 KB (1000 × 100 B) |
1 MB (1000 × 1000 B) |
100 MB (10,000 × 10,000 B) | ||
| ETH | Publisher | ||||||
| Subscriber | |||||||
| Broker | |||||||
| WIFI | Publisher | ||||||
| Subscriber | |||||||
| Broker | |||||||
| Role | Non-TLS | TLS |
|---|---|---|
| Publisher | ||
| Subscriber | ||
| Broker |
| Direction | 100 KB | 1 MB | 100 MB | |||
|---|---|---|---|---|---|---|
| 1000 × 100 B | 100 × 1000 B | 10 × 10,000 B | 1000 × 1000 B | 10,000 × 10,000 B | ||
| ETH | Client → Broker | |||||
| Broker → Client | ||||||
| WIFI | Client → Broker | |||||
| Broker → Client | ||||||
| Direction | 100 KB | 1 MB | 100 MB | |||
|---|---|---|---|---|---|---|
| 1000 × 100 B | 100 × 1000 B | 10 × 10,000 B | 1000 × 1000 B | 10,000 × 10,000 B | ||
| ETH | Client → Broker | |||||
| Broker → Client | ||||||
| WIFI | Client → Broker | |||||
| Broker → Client | ||||||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gavriilidis, N.O.; Halkidis, S.T.; Petridou, S. Empirical Evaluation of TLS-Enhanced MQTT on IoT Devices for V2X Use Cases. Appl. Sci. 2025, 15, 8398. https://doi.org/10.3390/app15158398
Gavriilidis NO, Halkidis ST, Petridou S. Empirical Evaluation of TLS-Enhanced MQTT on IoT Devices for V2X Use Cases. Applied Sciences. 2025; 15(15):8398. https://doi.org/10.3390/app15158398
Chicago/Turabian StyleGavriilidis, Nikolaos Orestis, Spyros T. Halkidis, and Sophia Petridou. 2025. "Empirical Evaluation of TLS-Enhanced MQTT on IoT Devices for V2X Use Cases" Applied Sciences 15, no. 15: 8398. https://doi.org/10.3390/app15158398
APA StyleGavriilidis, N. O., Halkidis, S. T., & Petridou, S. (2025). Empirical Evaluation of TLS-Enhanced MQTT on IoT Devices for V2X Use Cases. Applied Sciences, 15(15), 8398. https://doi.org/10.3390/app15158398






