Enhancing Traditional Reactive Digital Forensics to a Proactive Digital Forensics Standard Operating Procedure (P-DEFSOP): A Case Study of DEFSOP and ISO 27035
Abstract
1. Introduction
2. Development and Application of Proactive Digital Forensics Technology
2.1. Definition of P-DEFSOP
2.2. Application of Emerging Technologies in Proactive Digital Forensics
3. International Standard for Information Security Incident Management: ISO/IEC 27035
- 1.
- Prevention Phase: Focuses on reducing the likelihood of security incidents by implementing appropriate security controls and proactive risk mitigation strategies.
- 2.
- Preparation Phase: Involves the development of incident response plans, communication strategies, and personnel training to ensure a timely and effective organizational response to potential incidents.
- 3.
- Identification and Assessment Phase: Ensures the timely detection and evaluation of incidents to determine their severity, potential impact, and required response actions.
- 4.
- Investigation Phase: Conducts forensic analysis to identify the root cause, origin, and scope of the security incident.
- 5.
- Resolution Phase: Implements mitigation and recovery strategies to contain and remediate the incident while restoring affected systems to normal operations.
- 6.
- Documentation Phase: Involves comprehensive recording of incident details, actions taken, and lessons learned, which contribute to continuous improvement of future incident response capabilities.
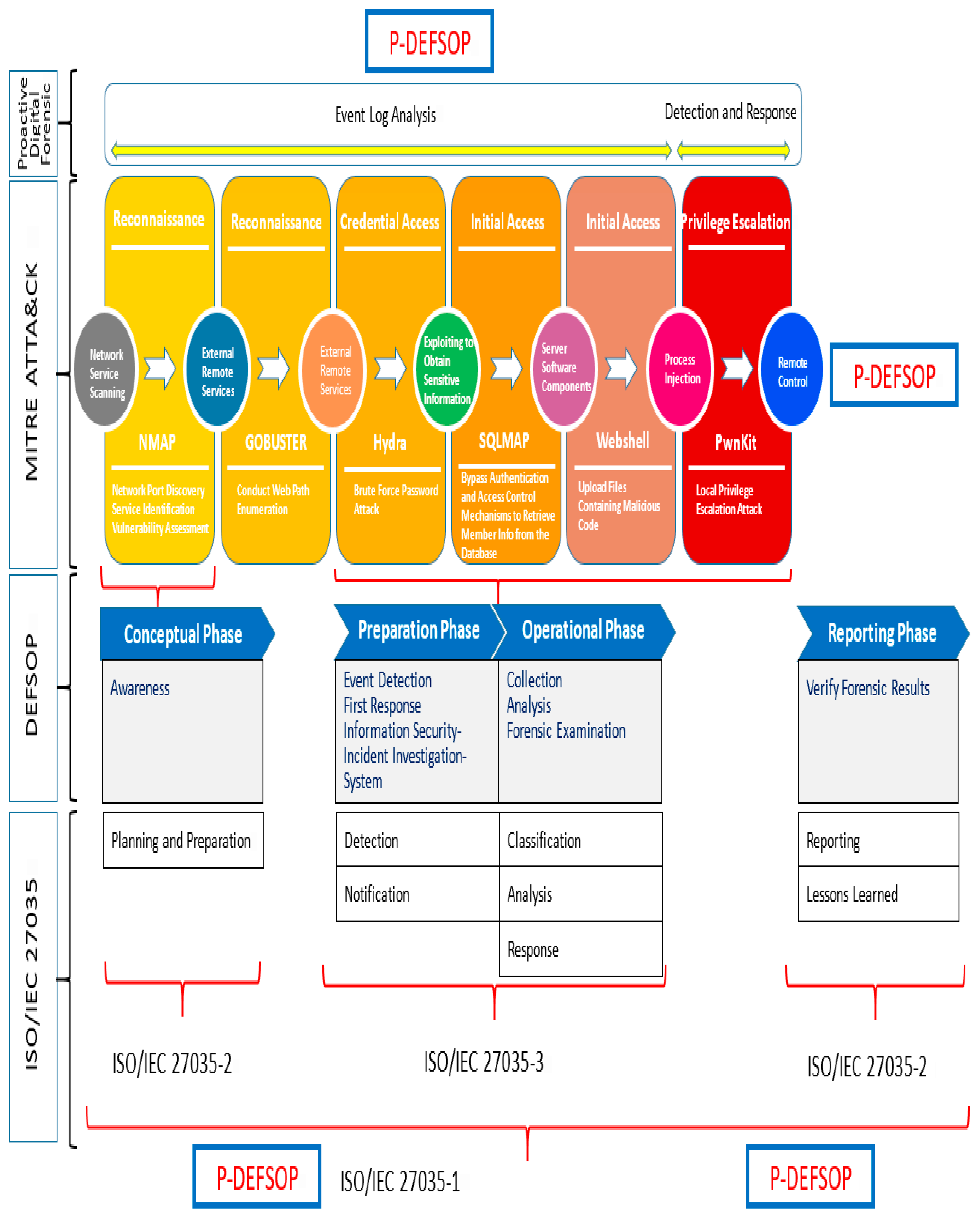
3.1. ISO/IEC 27035-1:2023—Overview of Information Security Incident Management (Part 1: Principles and Process, Second Edition)
3.2. ISO/IEC 27035-2:2023—Guidelines to Plan and Prepare for Incident Response (Part 2: Principles of Information Security Incident Management, Second Edition)
3.3. ISO/IEC 27035-3:2020—Guidelines for ICT Incident Response Operations (Part 3: Guidelines for Incident Response Operations, First Edition)
3.4. ISO/IEC 27035-4—Coordination in Information Security Incident Management (Part 4: Coordination)
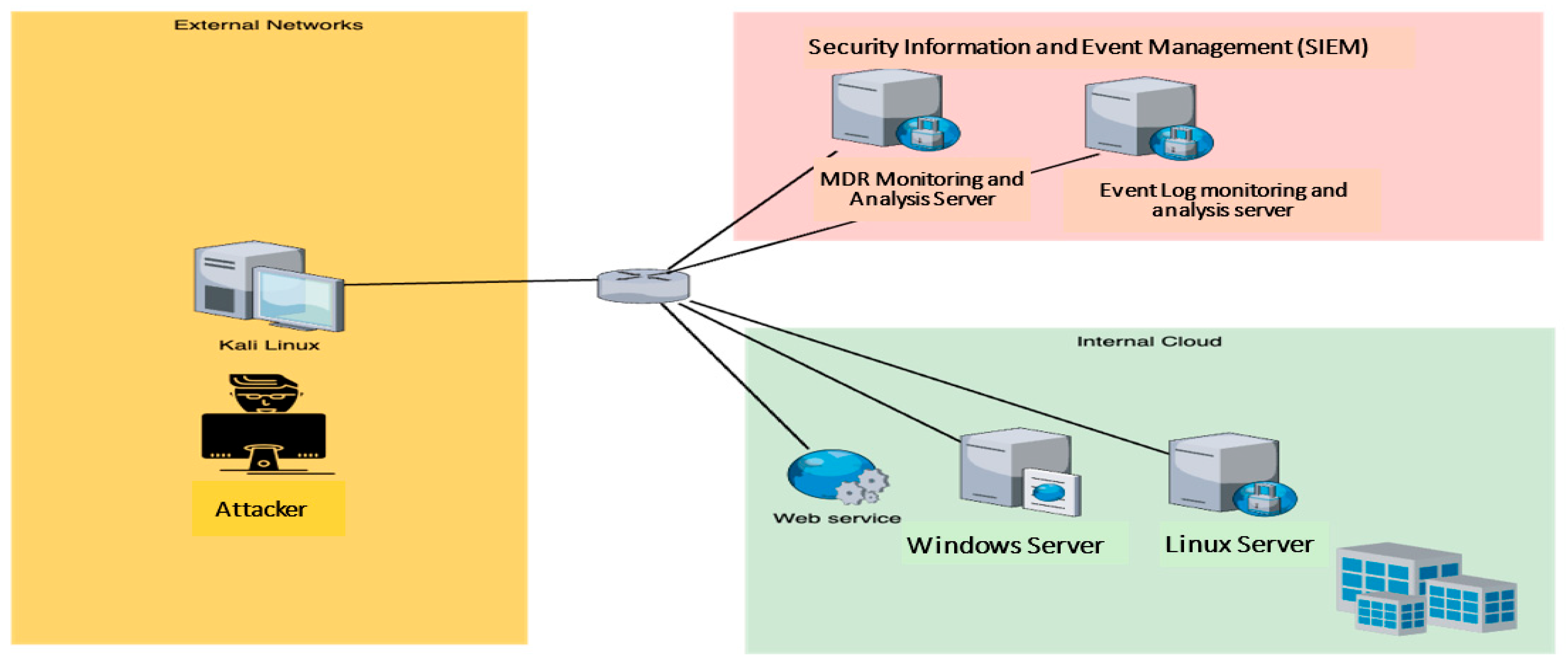
4. System Architecture for Attack–Defense Simulation and Exercises
- (1)
- Attacker:
- (2)
- Server:
- (3)
- Security Information and Event Management (SIEM):
- SOPHOS Managed Detection and Response (MDR) Server:
- This server continuously monitors security events and analyzes endpoint activity. SOPHOS MDR Clients are deployed on all servers to collect logs and transmit them to the MDR Server for real-time threat detection and analysis.
- ManageEngine EventLog Analyzer Server:
- This subsystem focuses on analyzing system logs, including web and FTP logs, to provide deeper forensic insights into security incidents.
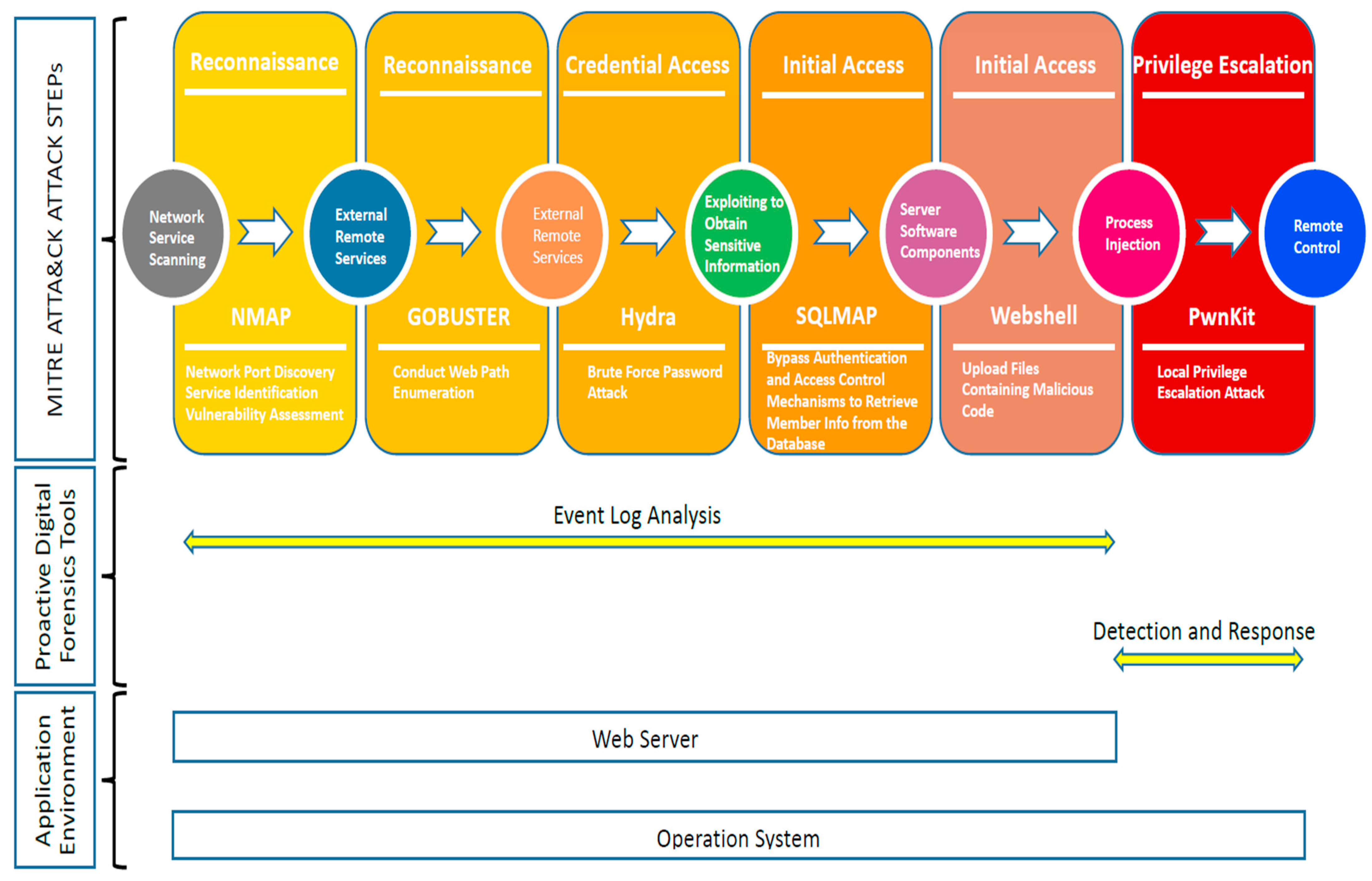
5. Simulating Attacks Using the MITRE ATT&CK Framework and Proactive Digital Forensics Tools
5.1. Simulating Attacks Using the MITRE ATT&CK Framework
- (1)
- Nmap Scanning
- Tactic: TA0043—Reconnaissance.
- Technique: T1046—Network Service Scanning.
- Procedure: Tool—Nmap.
- (2)
- Gobuster Enumeration
- Tactic: TA0043—Reconnaissance.
- Technique: T1133—External Remote Services.
- Procedure: Tool—Gobuster.
- (3)
- Hydra Brute-Force Attack
- Tactic: TA0006—Credential Access.
- Technique: T1110—Brute Force.
- Procedure: Tool—Hydra.
- (4)
- SQL Injection
- Tactic: TA0001—Initial Access.
- Technique: T1210—Exploitation for Privilege Escalation.
- Procedure: Tool—SQLMap.
- (5)
- File Upload Attack
- Tactic: TA0001—Initial Access.
- Technique: T1505—Server Software Component Injection.
- Procedure: Tools—Webshell, PwnKit.
- (6)
- Privilege Escalation
- Tactic: TA0004—Privilege Escalation.
- Technique: T1055—Process Injection.
- Procedure: Tool—PwnKit.
5.2. Proactive Digital Forensics Tools
- (1)
- A Managed Detection and Response (MDR) solution is deployed on the web server to provide continuous endpoint monitoring, threat intelligence integration, and automated mitigation. In parallel, a Security Information and Event Management (SIEM) system is used to aggregate and correlate security events across multiple sources.
- (2)
- In this study, ManageEngine EventLog Analyzer is adopted as the primary SIEM tool. It is configured to collect and analyze logs from web servers, FTP servers, and operating systems. The system generates real-time alerts on anomalous or suspicious activities, supporting both immediate triage and in-depth forensic investigation.
- (3)
- The SIEM platform utilizes structured event logs to proactively identify emerging attack patterns and trace threat actors. It plays a critical role in shortening detection-to-response timeframes and improving the organization’s security posture through actionable insights.
5.3. SIEM System Performance Evaluation and Improvement
6. Deployment Design and Implementation of the Proactive Digital Forensics Mechanism
6.1. Deployment Design of the Proactive Digital Forensics Mechanism
- (1)
- Attack Simulation:
- (2)
- Detection and Logging:
- (3)
- Log Storage and Analysis:
- (4)
- Digital Forensic Investigation:
6.2. Mapping SIEM Forensic Capabilities to ISO/IEC 27035 Within the P-DEFSOP Framework
- (1)
- Information Security Incident Management Analysis
- Tracks and documents security incidents in real time;
- Provides configurable alerting and incident notification mechanisms.
- (2)
- Security Audit Trail Analysis
- Collects system events, application activity, and network traffic;
- Generates detailed audit logs and forensic reports for accountability.
- (3)
- Incident Response Preparedness Analysis
- Supports automated alerting and reporting workflows;
- Enables predefined incident response playbooks and emergency handling mechanisms.
- (4)
- Security Testing Analysis
- Conducts continuous security testing for network and application layers;
- Performs vulnerability scanning and updates detection patterns.
- (5)
- Information Security Incident Logging Analysis
- Collects, logs, analyzes, and reviews security events with timestamped integrity;
- Supports long-term retention and retrieval of forensic logs.
- (6)
- Monitoring and Measurement Analysis
- Monitors critical system metrics and behaviors;
- Utilizes collectors to gather telemetry data and triggers real-time alerts based on anomaly detection.
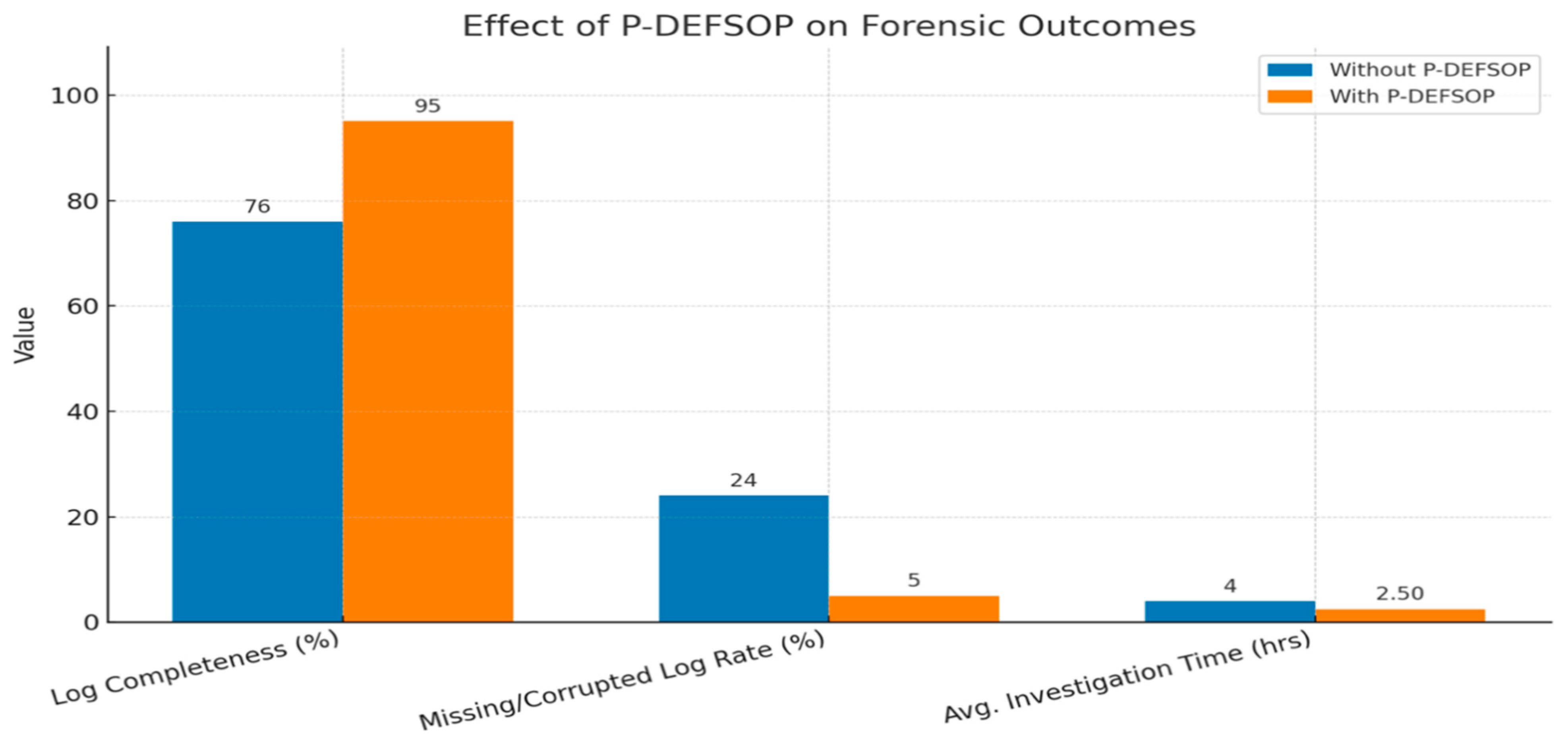
6.3. Performance Evaluation Results for the P-DEFSOP Framework
- (1)
- Quality and Integrity of Log Data
- In the scenario without P-DEFSOP, approximately 24% of the test cases exhibited missing or inconsistent logs.
- With P-DEFSOP implemented, the log loss rate was reduced to 5%, indicating a significant improvement in forensic reliability.
- (2)
- Efficiency of Forensic Investigation
- In the scenario without P-DEFSOP, the average investigation time was approximately 4.0 h.
- With P-DEFSOP applied, the investigation time was reduced to 2.5 h, reflecting an efficiency improvement of about 37.5%.
- (3)
- Clarity of Forensic Analysis
- In the absence of P-DEFSOP, the reports often lacked a consistent timeline and presented fragmented log references.
- With P-DEFSOP, the reports were able to reconstruct incident progressions step by step, aligning them with the ATT&CK matrix. This not only facilitated clearer interpretation of adversary behavior, but also improved communication with stakeholders.
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Correction Statement
References
- CardinalOps. 5th Annual State of SIEM Detection Risk Report. Available online: https://www.prnewswire.com/news-releases/enterprise-siems-miss-79-of-mitre-attck-techniques-used-by-adversaries-according-to-cardinalops-5th-annual-report-302473779.html (accessed on 2 September 2025).
- Brno, T. The Proactive and Reactive Digital Forensics Investigation Process: A Systematic Literature Review. In Proceedings of the International Conference on Information Security and Assurance (ISA), Brno, Czech Republic, 15–17 August 2011. [Google Scholar] [CrossRef]
- Machaka, V.; Balan, T. Investigating Proactive Digital Forensics Leveraging Adversary Emulation. Appl. Sci. 2022, 12, 9077. [Google Scholar] [CrossRef]
- Kohn, M.D.; Eloff, M.M.; Eloff, J.H. Integrated Digital Forensic Process Model. Comput. Secur. 2013, 38, 103–115. [Google Scholar] [CrossRef]
- Patil, H.; Kohli, R.K.; Puri, S.; Puri, P. Potential applicability of blockchain technology in the maintenance of chain of custody in forensic casework. Egypt. J. Forensic Sci. 2024, 14, 12. [Google Scholar] [CrossRef]
- Grobler, C.P.; Louwrens, C.P.; von Solms, S.H. A Framework to Guide the Implementation of Proactive Digital Forensics in Organisations. In Proceedings of the 2010 International Conference on Availability, Reliability and Security (ARES), Krakow Poland, 15–18 February 2010. [Google Scholar]
- Makura, S.M.; Venter, H.S.; Ikuesan, R.A.; Kebande, V.R.; Karie, N.M. Proactive Forensics: Keystroke Logging from the Cloud as Potential Digital Evidence for Forensic Readiness Purposes. In Proceedings of the 2020 IEEE International Conference on Informatics, IoT, and Enabling Technologies (ICIoT), Doha, Qatar, 2–5 February 2020. [Google Scholar]
- Yang, S.-H.; Chao, H.-C.; Lin, I.-L. A Study on Establishing Cybersecurity Incident Response Procedures and Practical Validation: Implementing ISO 27035 as an Example. Master’s Thesis, National Ilan University, Yilan, Taiwan, 2020. [Google Scholar]
- Lin, I.-L. Establishing an Integrated Digital Evidence Forensics Standard Operating Procedure for Mobile Forensics (iDEFSOP-MF) and Actual Cases Verification Research-taking the actual cases and verification of the Criminal Investigation Bureau as an example. Crim. Policy Crime Res. Pap. 2019, 22, 361–404. [Google Scholar] [CrossRef]
- Lin, I.-L.; Chen, Y.-R. Research on the Construction of the Mobile Forensics Standard Operating Procedure (DEFSOP-MF) and the Integration of International Forensic Standards—Integration of ISO27037, ISO27041, ISO27042 and ISO27043 Comparative Analysis as an Example. Inf. Secur. Newsl. 2019, 25, 39–57. Available online: https://www.airitilibrary.com/Article/Detail?DocID=a0000270-201902-201903150006-201903150006-39-57 (accessed on 2 September 2025).
- ISO/IEC 27035-1:2023; Information Technology—Information Security Incident Management—Part 1: Principles and Process. ISO: Geneva, Switzerland, 2023.
- ISO/IEC 27035-3:2020; Information Technology—Information Security Incident Management—Part 3: Guidelines for Incident Response Operations. ISO: Geneva, Switzerland, 2020.
- Heriyanto, T.; Ali, S. Kali Linux—Assuring Security by Penetration Testing: Master the Art of Penetration Testing with Kali Linux; Packt Publishing: Birmingham, UK, 2014. [Google Scholar]
- Williams, K.; Thompson, D.; Kim, J. Building Resilient Cybersecurity Strategies: Integration of ISO/IEC 27001 and ISO/IEC 27035 for 2025. Int. J. Inf. Secur. 2025, 24, 67–85. [Google Scholar] [CrossRef]
- Prastowo, S.L.; Sudiana, D. Recommendations for a framework for handling security incidents of electronic-based government systems (SPBE) using the ISO/IEC 27035: 2023 standard. JINAV J. Inf. Vis. 2024, 5, 107–114. [Google Scholar] [CrossRef]
- MITRE ATT&CK. ATT&CK Design and Philosophy; MITRE: Bedford, MA, USA, 2020. [Google Scholar]
- Akbari, I. MITRE ATT&CK Framework as a Standard for Developing SIEM Use Cases. 2025. Available online: https://medium.com/@imanvanpersien/mitre-att-ck-framework-as-a-standard-for-developing-siem-use-cases-d7dc7db4e1ba (accessed on 2 September 2025).
- Nurusheva, A.M.; Abdiraman, A.S.; Satybaldina, D.Z.; Goranin, N. Machine learning algorithms in SIEM systems for enhanced detection and management of security events. Bull. L.N. Gumilyov Eurasian Natl. Univ. Math. Comput. Sci. Mech. Ser. 2024, 148, 123–135. [Google Scholar] [CrossRef] [PubMed]
- NIST. Digital Forensics-Based Early Detection of Ongoing Cyber-Attacks (Fronesis); NIST: Gaithersburg, MD, USA, 2022. [Google Scholar]
- Murphy, A. Inside a MITRE ATT&CK Evaluation: How CrowdStrike’s MDR Services Operate in the Real World. 2022. Available online: https://www.crowdstrike.com/en-us/blog/inside-mitre-attack-evaluation-how-crowdstrikes-elite-managed-services-operate-in-the-real-world/ (accessed on 2 September 2025).
- Tabassum, S.; Rahman, M.M. Digital and Cloud Forensic Challenges. arXiv 2023, arXiv:2305.03059. [Google Scholar] [CrossRef]
- Alenezi, A.; Atlam, H.F.; Wills, G.B. Experts reviews of a cloud forensic readiness framework for organizations. J. Cloud Comput. 2019, 8, 11. [Google Scholar] [CrossRef]
- Zhang, Y.; Liu, H.; Wang, S. Comparative Study of NIST SP 800-86 and ISO/IEC 27037 Standards as A Framework for Digital Forensic Evidence Analysis. J. Inf. Syst. Inform. 2024, 6, 415–430. [Google Scholar]
- Faizal, A.; Luthfi, A. Comparison Study of NIST SP 800-86 and ISO/IEC 27037 Standards as a Framework for Digital Forensic Evidence Analysis. J. Inf. Syst. Inform. 2024, 6, 701–718. [Google Scholar] [CrossRef]
- Akter, O.; Akther, A.; Uddin, M.A.; Islam, M.M. Cloud forensics: Challenges and blockchain based solutions. Int. J. Wirel. Microw. Technol. 2020, 10, 1–12. [Google Scholar] [CrossRef]
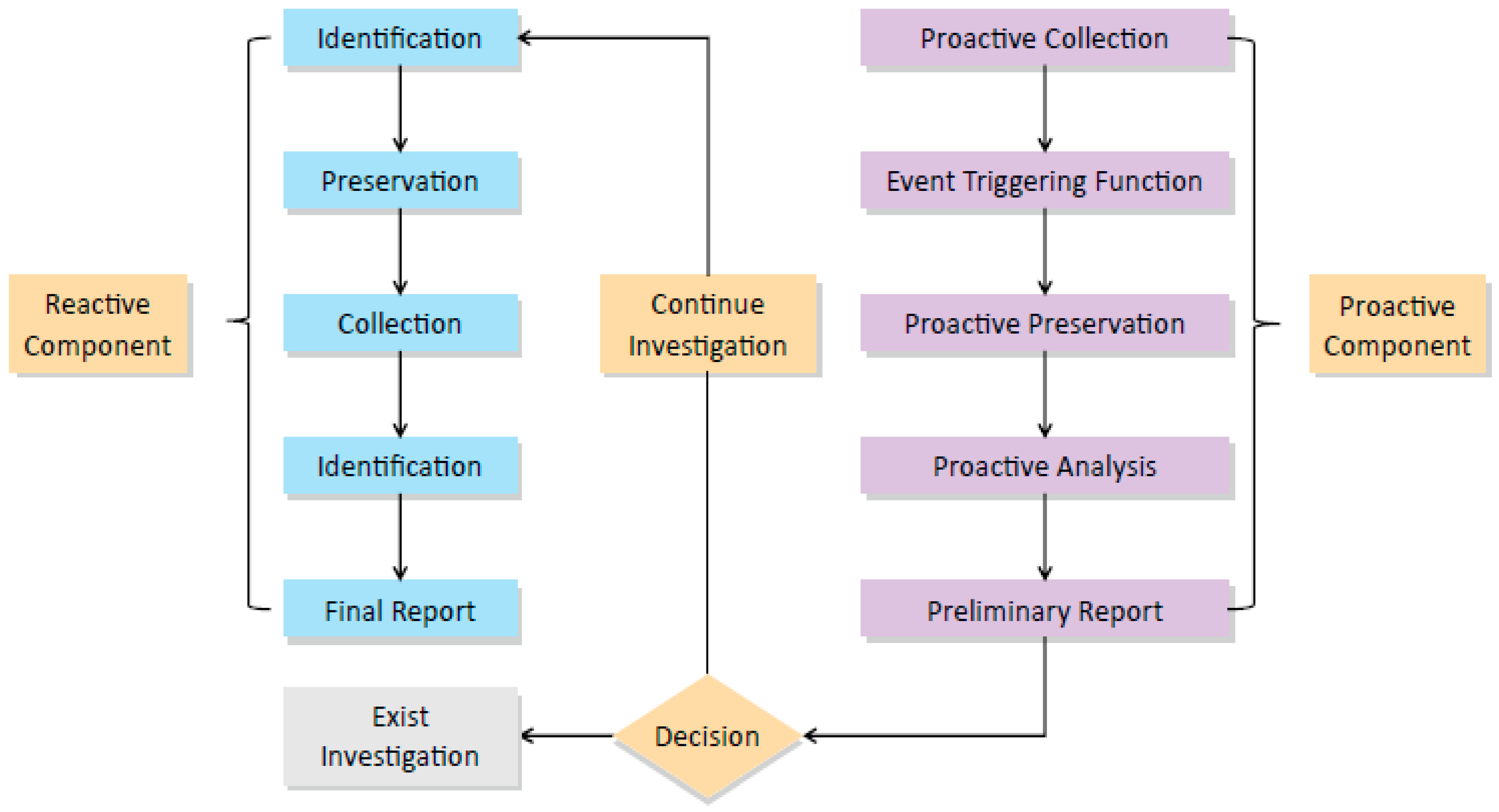
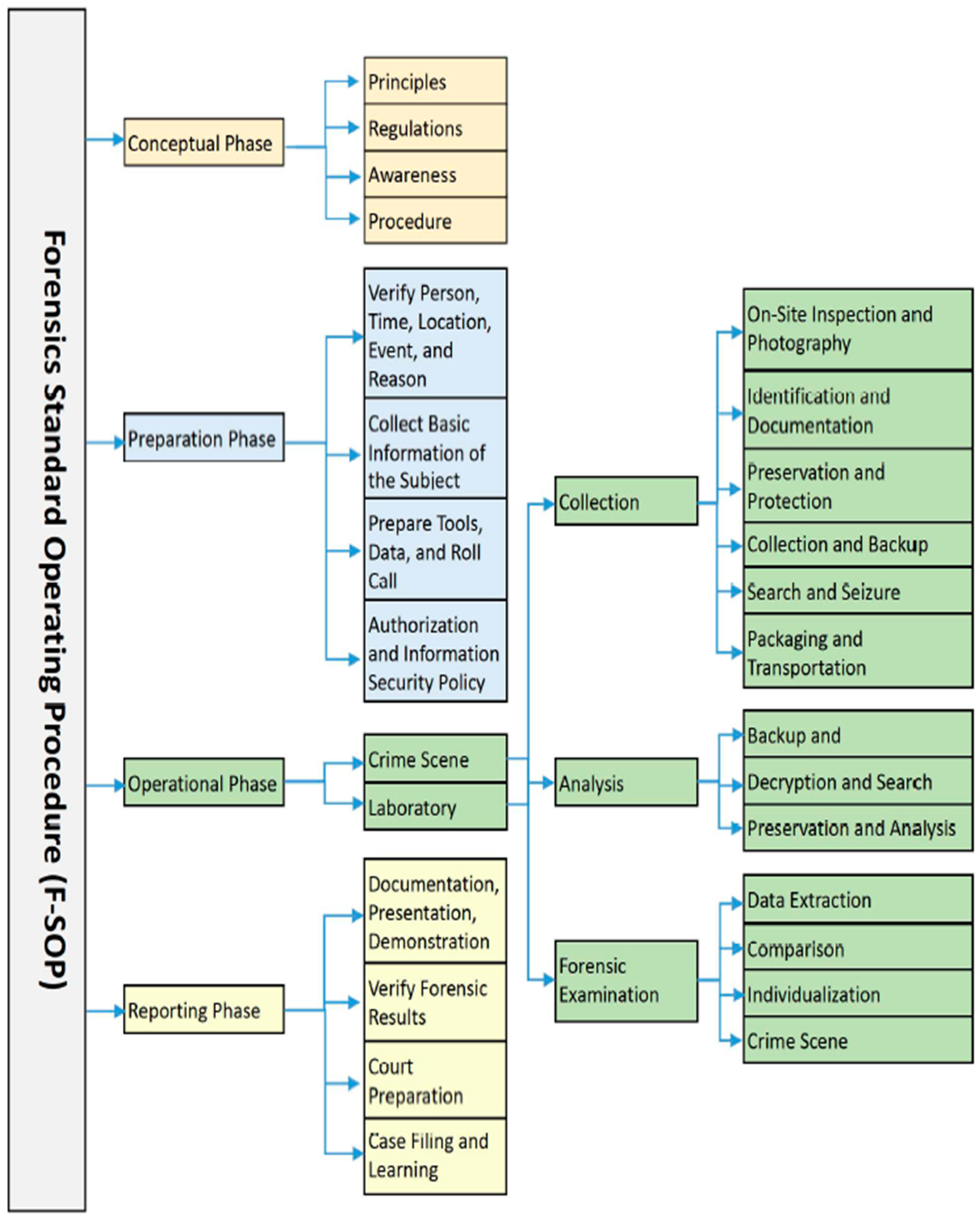
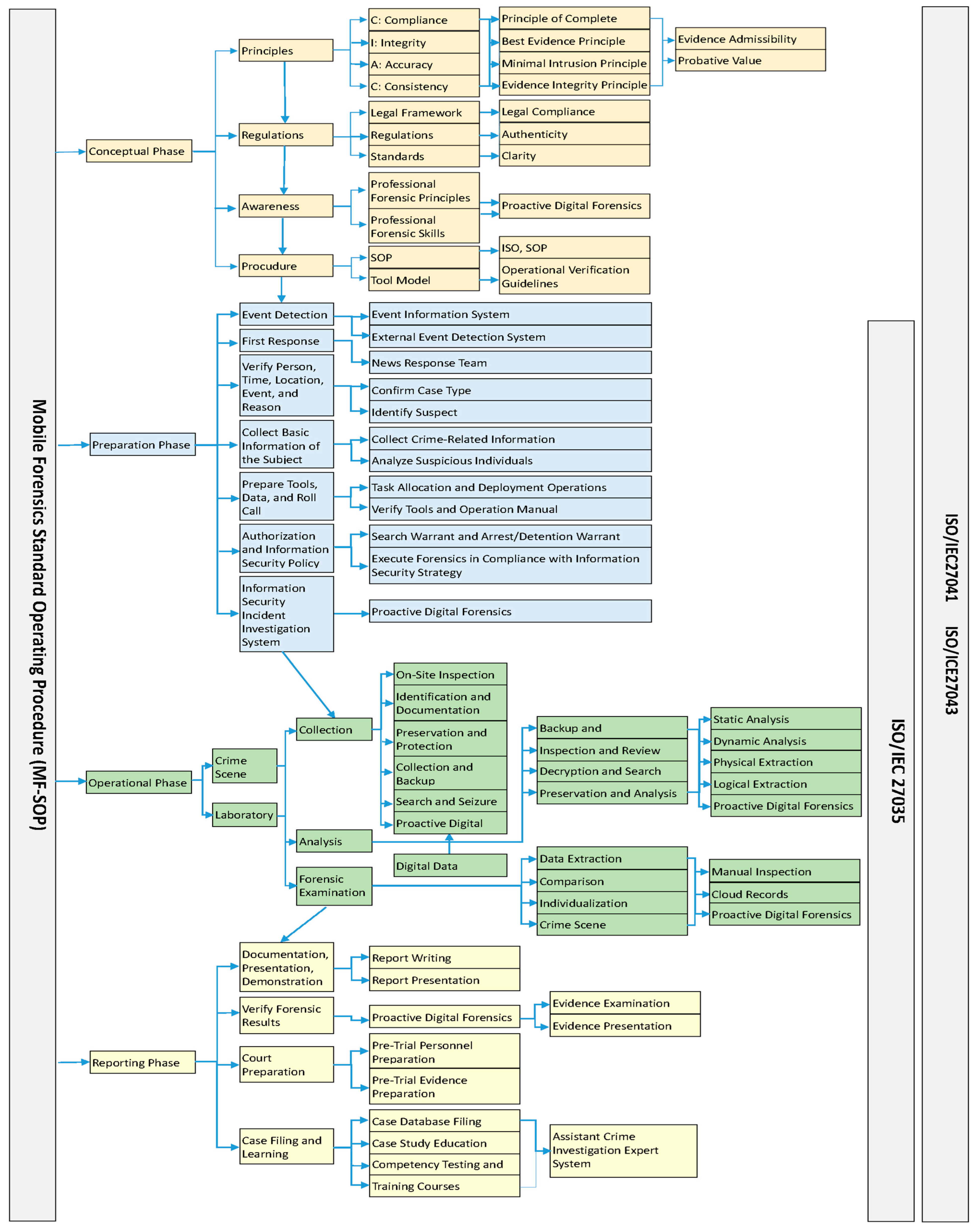


| Dimension | Reactive | DEFSOP | P-DEFSOP |
|---|---|---|---|
| Trigger | Post-incident | Post-/pre-mixed | Proactive readiness prior to incidents |
| ATT&CK mapping | None/Ad hoc | Partial | Technique-level rules, audited |
| Evidence integrity | Ad hoc hashing | Basic | Hash-chain + time-sync + sealed export |
| SIEM use | Log store | Dashboards | Normalization + correlation + metrics |
| Legal admissibility | Case-by-case | Partial | Controls aligned to ISO/IEC 27037/41/42/43 |
| Cloud readiness | N/A | Limited | Multi-cloud collectors & custody hooks |
| ISO Clause | Requirement | P-DEFSOP Control | Evidence Artifact |
|---|---|---|---|
| ISO/IEC 27037 §6–8 | Identification & acquisition | Pre-positioned collectors; sealed exports | CoC-Form-02, hash-manifest, export logs |
| ISO/IEC 27041 §5 | Method adequacy | Calibrated tools & validation runs | Tool version list, test run logs |
| ISO/IEC 27042 §7–9 | Analysis & interpretation | Correlation rules + analyst SOP | Analyst worksheet, rule hits, timeline |
| ISO/IEC 27043 §8–10 | Incident investigation | End-to-end workflow | Case file, audit trail, approvals |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yang, H.-C.; Lin, I.-L.; Chao, Y.-H. Enhancing Traditional Reactive Digital Forensics to a Proactive Digital Forensics Standard Operating Procedure (P-DEFSOP): A Case Study of DEFSOP and ISO 27035. Appl. Sci. 2025, 15, 9922. https://doi.org/10.3390/app15189922
Yang H-C, Lin I-L, Chao Y-H. Enhancing Traditional Reactive Digital Forensics to a Proactive Digital Forensics Standard Operating Procedure (P-DEFSOP): A Case Study of DEFSOP and ISO 27035. Applied Sciences. 2025; 15(18):9922. https://doi.org/10.3390/app15189922
Chicago/Turabian StyleYang, Hung-Cheng, I-Long Lin, and Yung-Hung Chao. 2025. "Enhancing Traditional Reactive Digital Forensics to a Proactive Digital Forensics Standard Operating Procedure (P-DEFSOP): A Case Study of DEFSOP and ISO 27035" Applied Sciences 15, no. 18: 9922. https://doi.org/10.3390/app15189922
APA StyleYang, H.-C., Lin, I.-L., & Chao, Y.-H. (2025). Enhancing Traditional Reactive Digital Forensics to a Proactive Digital Forensics Standard Operating Procedure (P-DEFSOP): A Case Study of DEFSOP and ISO 27035. Applied Sciences, 15(18), 9922. https://doi.org/10.3390/app15189922







