Cyber-Attacks on Energy Infrastructure—A Literature Overview and Perspectives on the Current Situation
Abstract
1. Introduction
- Represented a successful, publicly documented cyber-attack on petroleum or power grid sectors.
- Occurred between 2010 and 2023.
- Contained sufficient technical detail to map at least partially to the MITRE ATT&CK for ICS framework.
- Originated from credible, verifiable sources such as peer-reviewed studies or official investigation reports.
- Overview of cyberattacks on power grids, especially APTs, including those involved in the war in Ukraine.
- Overview of cyberattacks on petroleum installations, including an evaluation of potential societal impacts based on the current geopolitical situation.
- Discussion of the potential societal impacts of APTs and sophisticated cyberattacks on power grids and petroleum installations.
2. Energy Infrastructures and Their Subsystems
2.1. Petroleum Industry
2.2. Power Grid
3. Overview of Cyberattacks on the Petroleum Industry
Types of CyberAttacks Targeting Oil and Gas Systems
- Ransomware: Ransomware attacks, such as the 2020 attack targeting a natural gas compression facility, are designed to encrypt critical systems and demand payment in exchange for decryption. These attacks are often indiscriminate, i.e., not explicitly designed to affect oil and gas systems, but can have profound consequences for operational continuity.
- Malware and Phishing Attacks: Malware and phishing attacks are often the entry points for more sophisticated breaches. Attackers may infiltrate networks via malicious emails or websites, using malware to move laterally through the system and target ICS environments. Phishing attacks, particularly those targeting employees with access to sensitive OT systems, remain among the most common methods adversaries use to gain initial access.
- Advanced Persistent Threats (APTs): APTs, typically associated with nation-state actors, are highly targeted and designed to remain undetected within the system for extended periods. These attacks focus on gathering intelligence, manipulating processes, or degrading the functionality of critical systems over time. APTs are particularly dangerous because they can be used to launch more devastating attacks at crucial moments, such as during geopolitical tension or economic crises.
4. Overview of Cyberattacks on the Power Grids Industry
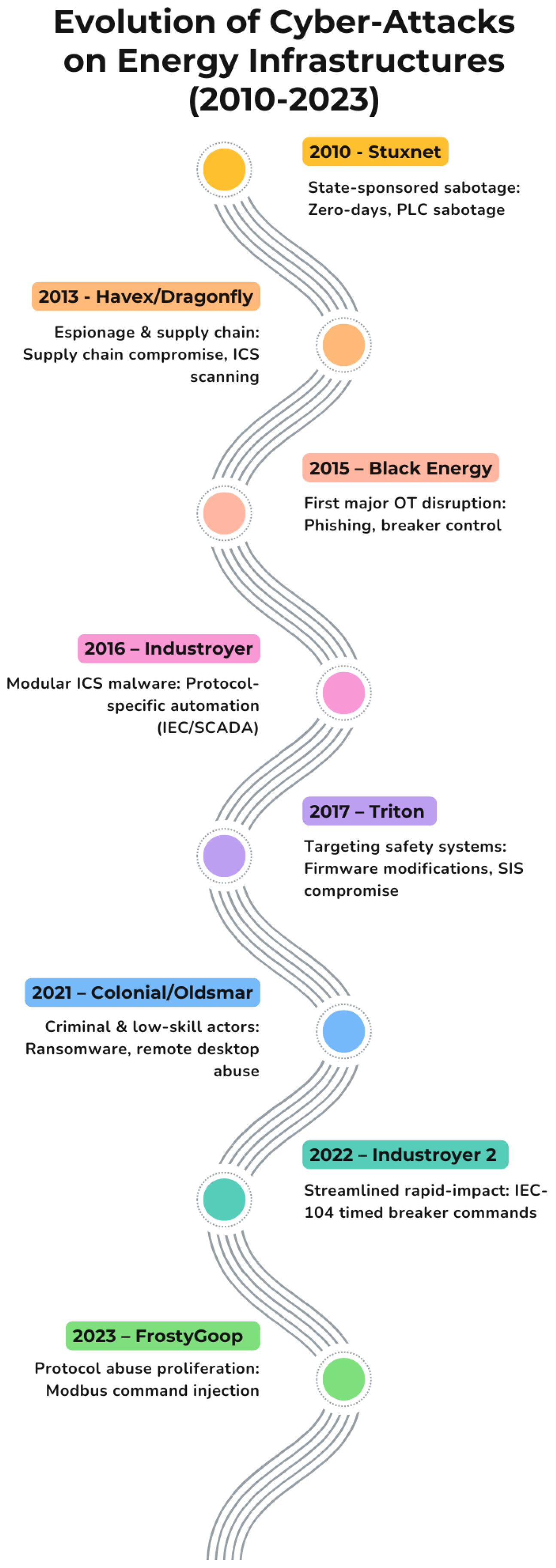
5. Attack Evolution Summary
5.1. Stuxnet (2010) — Iranian Nuclear Facility
5.2. Havex (2013) — Energy Sector ICS (EU, US)
5.2.1. Operation Cleaver (2014)—Global Energy Infrastructure
5.2.2. Dragonfly (Energetic Bear, 2014)—Energy Sector (EU, US)
5.2.3. BlackEnergy (2015)—Ukrainian Power Grid
5.2.4. Industroyer (2016)—Transmission Substations (Ukraine)
5.2.5. Triton (Trisis, 2017)—Saudi Petrochemical Plant
5.2.6. Colonial Pipeline (2021)—U.S. Fuel Pipeline
5.3. Oldsmar Water Plant (2021)
5.3.1. Industroyer2 (2022)—Ukraine Substations
5.3.2. FrostyGoop (2023)—Ukrainian Heating Systems
6. Comparative Technical Pathways of Cyberattack Methodology
- Identify convergence and divergence in attack sequences across critical energy sectors.
- Understand which MITRE ATT&CK tactics are most frequently exploited.
- Contextualize sector-specific resilience needs by mapping technical pathways to potential defensive measures.
7. Trends in Attack Evolution–Comparative Analysis
7.1. Comparative Evolution of Attack Patterns and Techniques
7.1.1. Shift from Targeted Sabotage to Strategic Persistence (2010–2014)
- Representative incidents: Stuxnet (2010), Havex (2013), Dragonfly and Operation Cleaver (2014).
- Patterns: State-sponsored actors leveraged bespoke ICS malware, exploiting zero-days and supply chain vulnerabilities to infiltrate critical systems. Early campaigns balanced sabotage (Stuxnet) with broad industrial espionage (Havex/Dragonfly).
- Techniques: Initial Access via zero-day exploitation (T0866) and trojanized vendor software (T0862); Discovery of ICS assets using OPC scanning (T0843).
- Mitigation Trends: Vendor software integrity verification, segmentation between IT and OT, and proactive patch management.
7.1.2. Operational Disruption and Weaponized ICS Malware (2015–2017)
- Representative incidents: BlackEnergy (2015), Industroyer (2016), Triton (2017).
- Patterns: A tactical shift from espionage to deliberate operational disruption. Industroyer introduced modular, protocol-aware automation for rapid substation breaker manipulation, while Triton expanded targeting to Safety Instrumented Systems (SIS), raising direct safety risks.
- Techniques: Credential harvesting via phishing (T0865), valid account abuse (T0859), firmware modification (T0857), and unauthorized control commands (T0855).
- Mitigation Trends: Deployment of ICS-aware intrusion detection, SIS monitoring, and strict firmware change control.
7.1.3. Diversification of Threat Actors and IT/OT Convergence (2020–2021)
- Representative incidents: Colonial Pipeline ransomware (2021), Oldsmar water facility intrusion (2021).
- Patterns: Cybercriminal groups achieved OT impact indirectly via IT compromise, while low-skill adversaries exploited misconfigured remote access tools for direct process manipulation.
- Techniques: Use of stolen credentials (T1078), ransomware encryption for impact (T1486), and GUI manipulation over remote desktop (T0856).
- Mitigation Trends: Multi-factor authentication, restrictive remote access policies, and continuous activity monitoring.
7.1.4. Streamlined, Rapid-Impact ICS Malware and Protocol Abuse (2022–2023)
- Representative incidents: Industroyer2 (2022), FrostyGoop (2023).
- Patterns: Highly focused, compact attack toolkits designed for fast execution with minimal detection footprint. Industroyer2 deployed timed IEC-104 breaker commands; FrostyGoop leveraged Modbus to directly manipulate device parameters.
- Techniques: Brute-forcing I/O addresses (T0806), unauthorized command messaging (T0855), exploitation of unpatched network devices.
- Mitigation Trends: Real-time anomaly detection, protocol command whitelisting, and hardening of endpoint network devices.
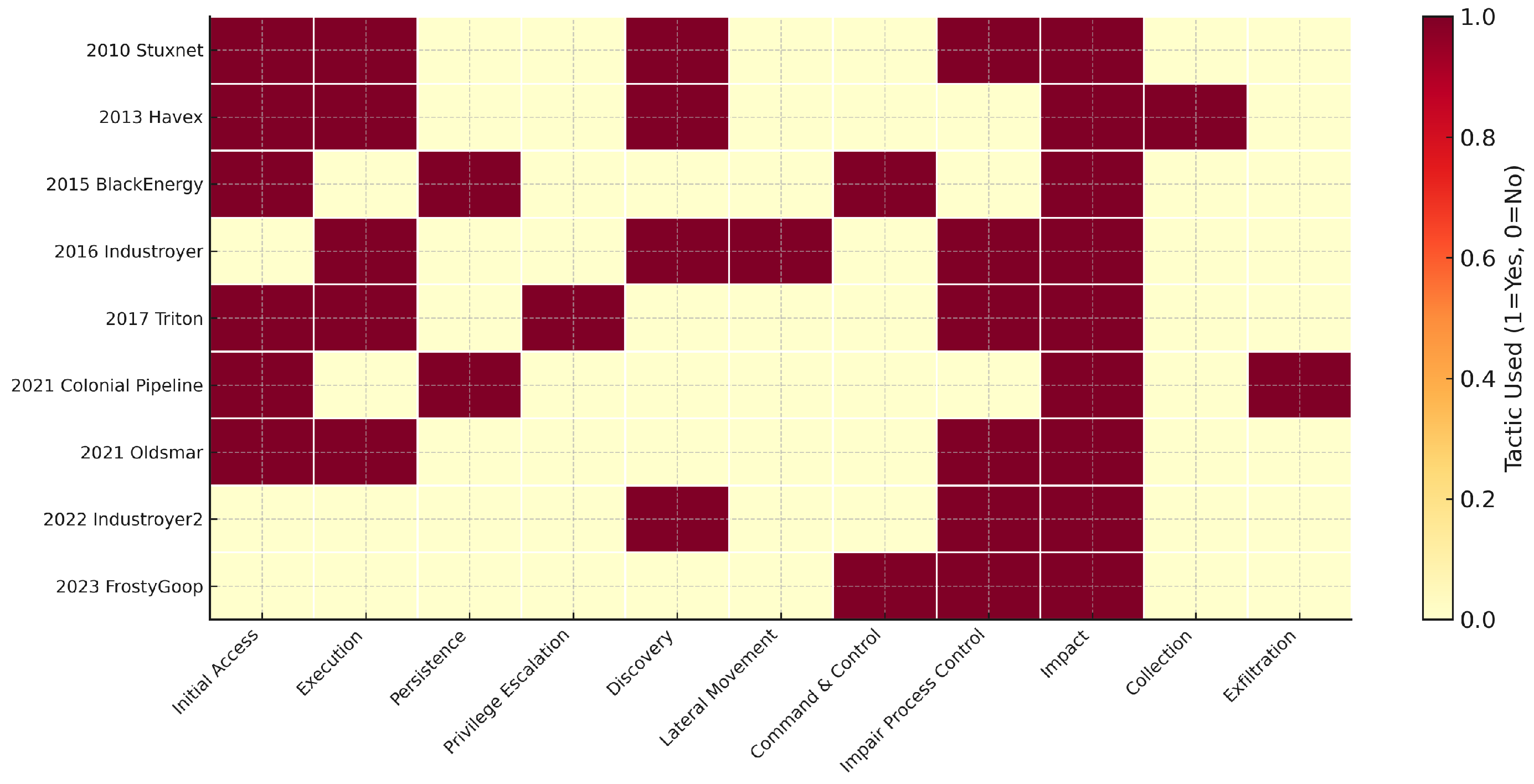
7.2. Cross-Case Comparative Insights
7.3. Visual Comparative Overview
- 1.
- Early campaigns (2010–2014) exhibited broader tactic coverage, often spanning from Initial Access through Collection and Impact.
- 2.
- Disruption-oriented campaigns (2015–2017) emphasized Impair Process Control and Impact, reflecting a shift toward operational consequences.
- 3.
- Recent campaigns (2022–2023) concentrate on a minimal set of high-impact tactics, often omitting intermediate stages to reduce exposure time.
7.4. Implications for Mitigation Strategies
- 1.
- Integrate IT/OT security operations to address the blending of attack surfaces.
- 2.
- Adopt protocol- and device-specific monitoring, as adversaries increasingly abuse trusted industrial protocols.
- 3.
- Implement threat-informed resilience planning, using frameworks like MITRE ATT&CK for ICS to model adversary pathways and design layered mitigations.
7.5. Mitigation Measures, Resilience Strategies, and Lessons Learned
7.5.1. Technical Controls (MITRE ATT&CK Mitigation IDs)
- Network Segmentation (M0930): Segregate operational technology (OT) from corporate IT networks to limit lateral movement. Post-Stuxnet, many operators implemented strict firewall zoning and unidirectional gateways to prevent cross-network propagation.
- Access Management (M0912): Enforce strong authentication, least privilege, and regular credential rotation. Multi-factor authentication was deployed after BlackEnergy to protect remote access points.
- Restrict Removable Media (M0953): Disable or tightly control USB and portable device use to mitigate initial infection vectors, as recommended after Stuxnet.
- Application Whitelisting (M0811): Allow only approved executables in control networks, reducing the risk of malware execution.
- Filter Network Traffic (M0937): Implement ICS-protocol-aware intrusion detection systems (IDS) and deep packet inspection to detect suspicious commands.
7.5.2. Resilience & Operational Strategies
- Redundant Systems & Automated Failover: Ensures operational continuity during disruptive attacks (e.g., Industroyer’s effect on grid substations).
- Incident Response Exercises (M0918): Regularly simulate OT-specific attack scenarios to improve coordination between IT and OT teams.
- Threat Intelligence Sharing (M0942): Participate in ISACs and national CERT programs to exchange indicators of compromise (IOCs) and TTPs.
- Continuous Monitoring (M0808): Deploy security monitoring tailored to OT environments, capable of detecting MITRE ATT&CK technique patterns.
7.5.3. Lessons Learned Overview
- Purely reactive measures are insufficient; proactive threat hunting (M0804) and regular control system security audits are essential.
- Providing OT engineers with dedicated cybersecurity awareness training can reduce their susceptibility to phishing and social engineering tactics, complementing their existing operational expertise. (M0910).
- Adoption of IEC 62443 and NIST Cybersecurity Framework aligns with MITRE mitigation strategies, offering a structured, repeatable approach for risk reduction.
8. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- North Atlantic Treaty Organization (NATO). Nato Standard AJP-3.20 Allied Joint Doctrine for Cyberspace Operations; Nato Standardization Office (NSO) ©NATO/OTAN: Brussels, Belgium, 2020. [Google Scholar]
- North Atlantic Treaty Organization (NATO). Allies Agree New NATO Integrated Cyber Defence Centre. Available online: https://www.nato.int/cps/en/natohq/news_227647.htm (accessed on 11 November 2024).
- European Union. Directive (EU) 2022/2555 of the European Parliament and of the Council of 14 December 2022 on Measures for a High Common Level of Cybersecurity across the Union, Amending Regulation (EU) No 910/2014 and Directive (EU) 2018/1972, and Repealing Directive (EU) 2016/1148 (NIS 2 Directive). Official Journal of the European Union. L 333. 27 December 2022, pp. 1–116. Available online: https://eur-lex.europa.eu/eli/dir/2022/2555/oj (accessed on 20 October 2024).
- European Union. Directive (EU) 2022/2557 of the European Parliament and of the Council of 14 December 2022 on the Resilience of Critical Entities and Repealing Council Directive 2008/114/EC. Official Journal of the European Union. L 333. 27 December 2022, pp. 164–196. Available online: https://eur-lex.europa.eu/eli/dir/2022/2557/oj (accessed on 20 October 2024).
- Liu, Y.; Deng, Q.; Zeng, Z.; Liu, A.; Li, Z. A hybrid optimization framework for age of information minimization in UAV-assisted MCS. IEEE Trans. Serv. Comput. 2025, 18, 527–542. [Google Scholar] [CrossRef]
- Chen, M.; Luo, K.; Wang, P.; Xiao, W.; Liu, Z.; Liu, A.; Farouk, A.; Chen, M. Federated deep reinforcement learning for combating cyber-threats specific to EV charging in next-gen WPT infrastructure. IEEE Trans. Intell. Transp. Syst. 2025, 1–12. [Google Scholar] [CrossRef]
- Vassiliou, M.S. The A to Z of the Petroleum Industry; Scarecrow Press: Lanham, Maryland, 2009. [Google Scholar]
- Norwegian Oil Industry Association (OLF). Summary Report: Deepwater Horizon-Lessons Learnt and Follow-Up. Available online: https://www.offshorenorge.no/contentassets/0ff3e58e6da243eeb0db267cff486c7d/dwh-summary-june-2012.pdf (accessed on 21 October 2024).
- Gutierrez, S.; Botero, J.F.; Gaviria, N.; Fletscher, L.A.; Leal, E.A. Next-Generation Power Substation Communication Networks: IEC 61850 Meets Programmable Networks; IEEE: Piscataway, NJ, USA, 2022. [Google Scholar]
- International Electrotechnical Commission (IEC). IEC 61850:2024 SER Communication Networks and Systems for Power Utility Automation—All Parts; IEC: Geneva, Switzerland, 2024; Available online: https://webstore.iec.ch/publication/6028 (accessed on 20 October 2024).
- Stergiopoulos, G.; Gritzalis, D.A.; Limnaios, E. Cyber-attacks on the Oil & Gas sector: A survey on incident assessment and attack patterns. IEEE Access 2020, 8, 128440–128475. [Google Scholar] [CrossRef]
- Cybersecurity and Infrastructure Security Agency (CISA). Ransomware Impacting Pipeline Operations. 18 February 2020. Available online: https://www.us-cert.gov/ncas/alerts/aa20-049a (accessed on 11 September 2024).
- Langner, R. Stuxnet: Dissecting a cyberwarfare weapon. IEEE Secur. Priv. 2011, 9, 49–51. [Google Scholar] [CrossRef]
- Venkatachary, S.K.; Prasad, J.; Samikannu, R. Cybersecurity and Cyber Terrorism in Energy Sector—A Review; Taylor & Francis: Abingdon, UK, 2018; Volume 2, pp. 111–130. [Google Scholar]
- Kovanen, T.; Nuojua, V.; Lehto, M. Cyber Threat Landscape in Energy Sector. In Proceedings of the ICCWS 2018 13th International Conference on Cyber Warfare and Security, Academic Conferences and Publishing Limited, Reading, UK, 8–9 March 2018; p. 353. [Google Scholar]
- Wangen, G. The Role of Malware in Reported Cyber Espionage: A Review of the Impact and Mechanism. Information 2015, 6, 183–211. [Google Scholar]
- Defense Use Case. Analysis of the Cyber Attack on the Ukrainian Power Grid; Electricity Information Sharing and Analysis Center (E-ISAC): Washington, DC, USA, 2016; Volume 388, p. 3. [Google Scholar]
- Slowik, J. Crashoverride: Reassessing the 2016 Ukraine Electric Power Event as a Protection-Focused Attack; Dragos, Inc.: Hanover, MD, USA, 2019. [Google Scholar]
- Di Pinto, A.; Dragoni, Y.; Carcano, A. TRITON: The First ICS Cyber Attack on Safety Instrument Systems. In Proceedings of the Black Hat USA, Las Vegas, NV, USA, 8–9 August 2018; pp. 1–26. [Google Scholar]
- Beerman, J.; Berent, D.; Falter, Z.; Bhunia, S. A Review of Colonial Pipeline Ransomware Attack. In Proceedings of the 2023 IEEE/ACM 23rd International Symposium on Cluster, Cloud and Internet Computing Workshops (CCGridW), Bangalore, India, 1–4 May 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 8–15. [Google Scholar]
- Grubbs, R.; Stoddard, J.; Freeman, S.; Fisher, R. Evolution and Trends of Industrial Control System Cyber Incidents Since 2017; Wiley Online Library: Hoboken, NJ, USA, 2021; Volume 2, pp. 45–79. [Google Scholar]
- Gaspar, J.; Cruz, T.; Lam, C.-T.; Simões, P. Smart Substation Communications and Cybersecurity: A Comprehensive Survey; IEEE Communications Surveys & Tutorials; IEEE: Piscataway, NJ, USA, 2023; Volume 25, pp. 2456–2493. [Google Scholar]
- Parsons, D. What’s the Scoop on FrostyGoop: The Latest ICS Malware and ICS Controls Considerations; SANS Institute Blog: North Bethesda, MA, USA, 2024; Available online: https://www.sans.org/blog/whats-the-scoop-on-frostygoop-the-latest-ics-malware-and-ics-controls-considerations/ (accessed on 15 July 2024).
- IEEE Spectrum. The Real Story of STUXNET. February 2013. Available online: https://spectrum.ieee.org/the-real-story-of-stuxnet (accessed on 22 August 2024).
- Chlela, M. Cyber Security Enhancement Against Cyber-Attacks On Microgrid Controllers; McGill University Montréal: Montréal, QC, Canada, 2017; Available online: https://escholarship.mcgill.ca/concern/theses/1c18dh978 (accessed on 22 August 2024).
- Bencsáth, B.; Pék, G.; Buttyán, L.; Félegyházi, M. Duqu: A Stuxnet-like malware found in the wild. CrySyS Lab Technical. Rep. 2011, 14, 1–60. [Google Scholar]
- SANS Blog. Confirmation of a Coordinated Attack on the Ukrainian Power Grid, January 2016. Available online: https://ics.sans.org/blog/2016/01/09/confirmation-of-a-coordinated-attack-on-the-ukrainian-power-grid (accessed on 22 August 2024).
- Finance News. Hackers Attacked Prykarpattiaoblenerho, de-Energizing Half of the Region for 6 h. January 2016. Available online: http://news.finance.ua/ua/news/-/366136/hakery-atakuvaly-prykarpattyaoblenergo-znestrumyvshy-polovynu-regionu-na-6-godyn (accessed on 22 August 2024).
- Cybersecurity & Infrastructure Security Agency. Cyber-Attack Against Ukrainian Critical Infrastructure. February 2016. Available online: https://ics-cert.us-cert.gov/alerts/IR-ALERT-H-16-056-01 (accessed on 22 August 2024).
- Geiger, M.; Bauer, J.; Masuch, M.; Franke, J. An Analysis of Black Energy 3, Crashoverride, and Trisis, Three Malware Approaches Targeting Operational Technology Systems. In Proceedings of the International Conference on Emerging Technologies and Factory Automation (ETFA), Vienna, Austria, 8–11 September 2020. [Google Scholar]
- Zetter, K. Everything We Know about Ukraine’s Power Plant Hack. Available online: https://www.wired.com/2016/01/everything-we-know-about-ukraines-power-plant-hack/ (accessed on 20 October 2024).
- REUTERS. Ukraine’s power outage was a cyber attack: Ukrenergo. January 2017. Available online: https://www.reuters.com/article/us-ukraine-cyber-attack-energy-idUSKBN1521BA (accessed on 24 August 2024).
- DRAGOS. CRASHOVERRIDE Analysis of the Threat to Electric Grid Operations. February 2017. Available online: https://www.dragos.com/wp-content/uploads/CrashOverride-01.pdf (accessed on 24 August 2024).
- ESET Research. Industroyer2: Industroyer Reloaded. Available online: https://www.welivesecurity.com/2022/04/12/industroyer2-industroyer-reloaded/ (accessed on 21 October 2022).
- Netresec. Industroyer2 IEC-104 Analysis. Available online: https://www.netresec.com/?page=Blog&month=2022-04&post=Industroyer2-IEC-104-Analysis (accessed on 21 October 2022).
| Attack Name/Incident | Year | Targeted Infrastructure | Attack Methodology | Root Cause | Impact | Mitigation Measures | Lessons Learned |
|---|---|---|---|---|---|---|---|
| Stuxnet [13] | 2010 | Iranian Nuclear Facility | Malware (Worm) | Exploited zero-day vulnerabilities in Siemens PLCs | Physical damage to centrifuges, disrupting uranium enrichment | Regularly update and patch systems; implement network segmentation | Importance of securing industrial control systems (ICS) against sophisticated malware |
| Havex [14] | 2013 | Energy sector ICS (EU, US) | Remote Access Trojan via software supply chain | Compromised ICS software installers | Unauthorized access to ICS networks; potential data exfiltration | Verify integrity of software updates; monitor network traffic for anomalies | Vigilance in supply chain security; importance of monitoring ICS networks |
| Operation Cleaver [15] | 2014 | Global Energy Infrastructure | Advanced Persistent Threats | Exploited vulnerabilities in critical infrastructure systems | Unauthorized access to sensitive systems; potential for sabotage | Implement advanced threat detection; enhance system hardening | Importance of monitoring for APTs and securing critical infrastructure |
| Dragonfly (Energetic Bear) [16] | 2014 | Energy Sector (EU, US) | Malware (Havex RAT) via phishing and watering hole attacks | Compromised ICS software and websites | Unauthorized access to energy sector networks; potential data exfiltration | Regularly update and patch systems; monitor network traffic for anomalies | Vigilance in supply chain security; importance of monitoring ICS networks |
| BlackEnergy [17] | 2015 | Power Grid (Ukraine) | Malware (Trojan) delivered via phishing emails | Lack of employee cybersecurity training; inadequate email filtering | Power outage affecting 225,000 customers for several hours | Employee cybersecurity training; implement advanced email filtering | Need for comprehensive cybersecurity training and robust email security |
| Industroyer (CrashOverride) [18] | 2016 | Transmission Substations (Ukraine) | Malware targeting industrial communication protocols | Exploited specific ICS protocol vulnerabilities | Power outage in Kyiv for about an hour | Regularly update ICS protocols; implement intrusion detection systems | Importance of securing ICS protocols and continuous monitoring |
| Triton (Trisis) [19] | 2017 | Saudi Petrochemical Plant | Malware targeting safety instrumented systems (SIS) | Inadequate segmentation between IT and OT networks | Potential physical damage; plant shutdown | Network segmentation; monitor SIS for unauthorized changes | Criticality of securing SIS and enforcing strict network segmentation |
| Colonial Pipeline [20] | 2021 | U.S. Fuel Pipeline | Ransomware via compromised password | Use of a single-factor VPN password; lack of multifactor authentication | Pipeline shutdown causing fuel shortages in the Eastern U.S. | Implement multifactor authentication; regular password audits | Necessity of multifactor authentication and regular security assessments |
| Oldsmar Water Plant [21] | 2021 | Water treatment OT system | Remote access tool exploitation | Poor password security; lack of network segmentation | Attempted alteration of water chemical levels; thwarted by operator | Implement strong password policies; restrict remote access; monitor system activity | Criticality of securing remote access and monitoring ICS environments |
| Industroyer2 [22] | 2022 | Transmission Substations (Ukraine) | Malware targeting power substations with IEC 60870-5-104 protocol commands | Having access to the controlling station computer | Opening circuit breakers to cut the power | Prevent access to the controlling station and its network, prevent information disclosure regarding protocol level details (Information Object Addresses) and network level details (IP addresses) | IEC104 protocol is an easy target if the attacker has access to one of the endpoints. Network level information (IP addresses) and Protocol level information (Information Object Addresses) should have been better protected |
| FrostyGoop [23] | 2023 | Urban Heating Infrastructure (Ukraine) | Modbus-based device command manipulation | Unpatched MikroTik routers; exposed Modbus access | Disruption of heating services to 600 buildings for 48 h | Regularly update and patch network devices; monitor for unauthorized access | Regularly update and patch network devices; monitor for unauthorized access |
| Phase | Description | Representative Techniques (MITRE ATT&CK for ICS) | Observed in Petroleum Sector | Observed in Power Grid Sector |
|---|---|---|---|---|
| 1. Reconnaissance | Adversaries gather technical and organizational information about the target | Gather Victim Host Information (T0866), Gather Victim Network Information (T0840), Phishing for Information (T1598) | Dragonfly/Havex reconnaissance of OPC servers in oil & gas vendors | Pre-Industroyer OSINT and network mapping of substation control systems |
| 2. Initial Access | First entry into IT or OT environments through exploitation or deception | Spearphishing Attachment (T1566.001), Supply Chain Compromise (T1195), Exploit Public-Facing Application (T1190), Replication Through Removable Media (T1091) | Colonial Pipeline via compromised VPN credentials | Stuxnet via infected USB drives in nuclear power plant ICS |
| 3. Execution | Running of malicious code or payload in target systems | Command-Line Interface (T1059), User Execution (T1204), Exploitation for Client Execution (T1203) | Havex malware execution after delivery via trojanized software installers | CrashOverride payload deployment on grid control systems |
| 4. Persistence | Maintaining access to the environment despite system reboots or changes | Valid Accounts (T1078), Create Account (T1136), Modify Authentication Process (T1556) | Dragonfly maintaining persistence through legitimate remote access accounts | Industroyer persistence via scheduled tasks |
| 5. Privilege Escalation | Gaining higher permissions within compromised systems | Exploitation for Privilege Escalation (T1068), Abuse Elevation Control Mechanism (T1548) | Operation Cleaver escalation within petroleum ICS networks | Industroyer escalation to manipulate relay protection systems |
| 6. Lateral Movement | Moving between hosts or network zones to expand access | Remote Services (T1021), Pass the Hash (T1550.002), Exploitation of Remote Services (T1210) | Havex pivoting from vendor IT to OT via shared credentials | Ukraine 2015 attackers pivoting from IT to SCADA networks |
| 7. Impact/Disruption | Manipulating or halting physical processes and operations | Modify Control Logic (T0831), Inhibit Response Function (T0803), Impair Process Control (T0814), Denial of Service (T0813) | Dragonfly attempting disruption of petroleum operations | Industroyer disrupting substation operations; Stuxnet impairing process control |
| Dimension | Early State-Sponsored (2010–2014) | Disruption-Oriented (2015–2017) | Persistence-Oriented (2020–2021) | Streamlined-Modular (2022–2023) |
|---|---|---|---|---|
| Primary Objective | Espionage & sabotage preparation | Physical disruption of OT | Financial gain/opportunistic | Rapid, high-impact disruption |
| Target Systems | PLCs, ICS management stations | SCADA, substations, SIS | IT systems, exposed OT HMIs | ICS endpoints via protocol |
| MITRE Tactics Emphasis | Initial Access, Discovery, Collection | Impair Process Control, Impact | Persistence, Exfiltration, Impact | Discovery, Impair Process Control |
| Access Vectors | Zero-days, supply chain | Phishing, credential theft | Stolen creds, RDP/VPN abuse | Known protocol abuse, device exploit |
| Skill/Resource Level | High (nation-state) | High (nation-state) | Medium to low | Medium to high |
| Mitigation Evolution | Patch mgmt., vendor assurance | Protocol-aware IDS, SIS security | MFA, remote access controls | Real-time monitoring, network device hardening |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abraham, D.; Houmb, S.H.; Erdodi, L. Cyber-Attacks on Energy Infrastructure—A Literature Overview and Perspectives on the Current Situation. Appl. Sci. 2025, 15, 9233. https://doi.org/10.3390/app15179233
Abraham D, Houmb SH, Erdodi L. Cyber-Attacks on Energy Infrastructure—A Literature Overview and Perspectives on the Current Situation. Applied Sciences. 2025; 15(17):9233. https://doi.org/10.3390/app15179233
Chicago/Turabian StyleAbraham, Doney, Siv Hilde Houmb, and Laszlo Erdodi. 2025. "Cyber-Attacks on Energy Infrastructure—A Literature Overview and Perspectives on the Current Situation" Applied Sciences 15, no. 17: 9233. https://doi.org/10.3390/app15179233
APA StyleAbraham, D., Houmb, S. H., & Erdodi, L. (2025). Cyber-Attacks on Energy Infrastructure—A Literature Overview and Perspectives on the Current Situation. Applied Sciences, 15(17), 9233. https://doi.org/10.3390/app15179233








