GDPR-Compliant Academic Certification via Blockchain: Legal and Technical Validation of the GAVIN Project
Abstract
1. Introduction
2. Legal and Technological Background
2.1. General Data Protection Regulation (GDPR)
- Data Subject: This is the natural person who owns the personal data. They have the right to control how their information is collected, used, and protected.
- Data Controller: This is the entity, which can be either an organization or an individual, which decides what personal data is collected, for what purpose it is processed, and what means are used. Although it may outsource processing, it remains the primary guarantor of compliance with the GDPR and must ensure that data processing is legitimate, transparent, and secure.
- Data Processor: This acts on behalf of the Data Controller, performing operations on personal data in accordance with their instructions. They are required to implement appropriate technical and organizational measures to ensure data protection and comply with the provisions of the GDPR. We should point out that personal data processing is any operation or set of operations performed on personal data or sets of personal data, whether or not by automated means, such as collection, recording, organization, structuring, storage, adaptation or alteration, retrieval, consultation, use, disclosure by transmission, dissemination or otherwise making available, alignment or combination, restriction, erasure or destruction, in accordance with Article 4 of the GDPR.
2.2. Blockchain
- Public blockchain: These are completely open networks where any user can participate by sending transactions, operating nodes, or even mining new blocks. Although this model guarantees high transparency and censorship resistance, it has significant limitations in terms of scalability and privacy. All stored information is visible to all participants, which implies total data exposure. Although encryption can be used, its use in immutable environments poses future risks due to the obsolescence of cryptographic algorithms, especially with the emergence of technologies such as quantum computing. Representative examples of this model are Bitcoin and Ethereum [11].
- Private blockchain: Unlike the previous model, private blockchains are managed by a centralized organization that restricts access to authorized nodes. This type of implementation allows for greater control over the network, improving both efficiency and privacy. Frameworks such as the Linux Foundation’s Hyperledger Fabric [12] enable the development of these types of solutions, adapted to contexts where confidentiality and performance are essential, such as in the financial or corporate sectors.
- Consortium or federated blockchain: This approach combines elements of public and private networks. They are maintained by a group of organizations that share governance of the system. Although participation is restricted, certain levels of openness for public consultation can be enabled. This balance between controlled decentralization and privacy enables its use in inter-institutional collaborative contexts, such as higher education.
3. Related Works
3.1. Blockchain in Education
3.2. GDPR Challenges in Blockchain Systems
- Immutability vs. the Right to Erasure (“Right to be Forgotten”).
- Regulatory Issue: Under Article 17 of the GDPR, data subjects have the right to request the erasure of their personal data. Blockchain, by design, ensures that data written to the ledger is immutable and cannot be deleted.
- Conflict: If personal data (e.g., student names, transcripts, or identifiers) are stored directly on-chain, this may conflict with the ability to comply with erasure requests. Even if off-chain storage is used, references or hashes may still be considered personal data.
- Data Minimization and Purpose Limitation.
- Regulatory Issue: GDPR enshrines data minimization (Article 5(1)(c)) and purpose limitation (Article 5(1)(b)), personal data should be collected only when necessary and for specified, explicit purposes.
- Conflict: The transparency and redundancy of blockchain means that data is replicated across multiple nodes, which can challenge the principle of data minimization. Once on-chain, it is also difficult to limit or redefine purposes for which data is used.
- Lawfulness, Fairness, and Transparency of Processing.
- Regulatory Issue: Article 5(1)(a) requires processing to be lawful, fair, and transparent.
- Conflict: In blockchain systems, especially decentralized ones, data subjects may not have a clear understanding of how their data is processed or who the participants (nodes) are, which limits transparency and undermines informed consent (Article 7) [76].
- Pseudonymization vs. Anonymization.
- Regulatory Issue: GDPR does not apply to anonymous data but continues to apply to pseudonymized data if re-identification is possible (Recital 26).
- Conflict: Blockchain implementations often use pseudonymous identifiers (e.g., public keys), but these can sometimes be linked to individuals using auxiliary data, meaning GDPR still applies.
- Identification of the Data Controller in Decentralized Systems.
- Regulatory Issue: The GDPR requires the identification of a data controller, the entity that determines the purposes and means of processing personal data (Article 4(7)).
- Conflict: In public, permissionless blockchains, there is often no clearly identifiable data controller or centralized authority. This undermines the accountability and governance structures expected by GDPR.
- Cross-border Data Transfers.
- Regulatory Issue: GDPR restricts the transfer of personal data outside the EU to jurisdictions that do not ensure adequate protection (Chapter V).
- Conflict: Public blockchains involve international nodes, making it difficult to control or monitor data flows. This potentially constitutes unlawful international data transfer under the GDPR.
- A participation policy that establishes the conditions under which and with what role one participates in the network.
- A distributed information storage policy.
- A data sharing policy.
- A consensus policy to validate new information in the system.
- An information integrity management policy.
- Who can access or participate in the network;
- With what permissions;
- What levels of service are provided;
- Block validation strategies;
- Traceability of information, etc.
- Recording transactions on the blockchain, which requires transforming the data into operations valid for the blockchain.
- Validating transaction blocks, proceeding to verify them according to the selected consensus mechanism.
- Implementing other additional processing operations that a node can perform on transactions, such as managing pending transactions, reordering them, storing historical data, processing events associated with smart contracts, providing data and services to applications, etc. In this sense, the use of a specific blockchain infrastructure as an element for the processing of personal data could generate specific non-compliance and risks to the rights and freedoms of data subjects. One of its key aspects is ensuring compliance with data protection principles, as well as allowing the exercise of data subjects’ rights, and particularly the principle of accuracy, the principle of retention, and the rights of rectification and erasure.
- (1)
- ensuring regulatory compliance and once achieved,
- (2)
- evaluating and assessing the risks, some of which can be mitigated with legal, organizational, and technical measures. In cases of high risk, the assessment of the suitability, necessity, and proportionality of the processing must be completed.”
4. Methodology
- Definition of the normative legal question: Can a blockchain-based model for academic certification comply with the GDPR, particularly concerning data protection principles such as data minimization, purpose limitation, and the right to erasure?
- Comprehensive legal source analysis: Examination of relevant EU primary and secondary legislation (especially the GDPR), official regulatory guidance (e.g., EDPB—European Data Protection Board, CNIL—Commission Nationale de l’Informatique et des Libertés), and pertinent case law from the Court of Justice of the EU).
- Synthesis with existing legal doctrine: Integration of academic literature addressing blockchain, privacy law, and data protection compliance.
- Doctrinal interpretation: Interpretation of the GDPR core principles in light of the facts and architecture of the proposed model.
- Application and conclusion: Reasoned legal judgment regarding whether the proposed architecture satisfies these requirements, along with a discussion of limitations and possible regulatory developments.
5. Technical Architecture of the GAVIN Model
5.1. Derivation of the Requirements of the Theoretical Model
- Compatibility with existing systems: It must be possible to use this system without modifying the existing information systems of academic/training institutions or other organizations that issue certificates or academic information and accreditations. This is a key point since the usefulness of this solution goes hand in hand with its massive adoption and given that most issuing institutions store their data in their proprietary systems [6], the system’s ability to adapt to reality is crucial for its success.
- Format flexibility: It must be flexible enough to accommodate different types of academic information, accreditations, etc., regardless of the underlying information models and it must be usable in all types of education: formal, non-formal, and informal. This is defined in the model as a fundamental requirement, since the idea is that it supports the verification of any type of academic certification without format or content restrictions.
- Independence of the issuing institution: It must be possible to verify the validity of the certificate content and associated accreditations even after the dissolution of the institution that originally issued the certificate and all its information systems. Since it is considered that any duly authorized institution can issue academic certifications according to the previous point, it is not ruled out that some will disappear and therefore, a premise of the developed system is that it continues to function even in this scenario.
- Operational scalability: It must be scalable and capable of supporting transactions and operations related to the registration, verification, and query of information by the model’s end users. As also explained in [6] to set this requirement, millions of academic certificates [87] are registered in the world every year, so the solution must be scalable to accommodate them.
- Regulatory compliance: It must comply with personal data protection regulations, and particularly with the GDPR in cases where it affects individuals located in the European Union, which is the subject of validation in this report.
- The model, as already explained, is based on the scientific publication entitled “Application of Blockchain in Education: GDPR-Compliant and Scalable Certification and Verification of Academic Information” [6], which presents the system developed by GAVIN.
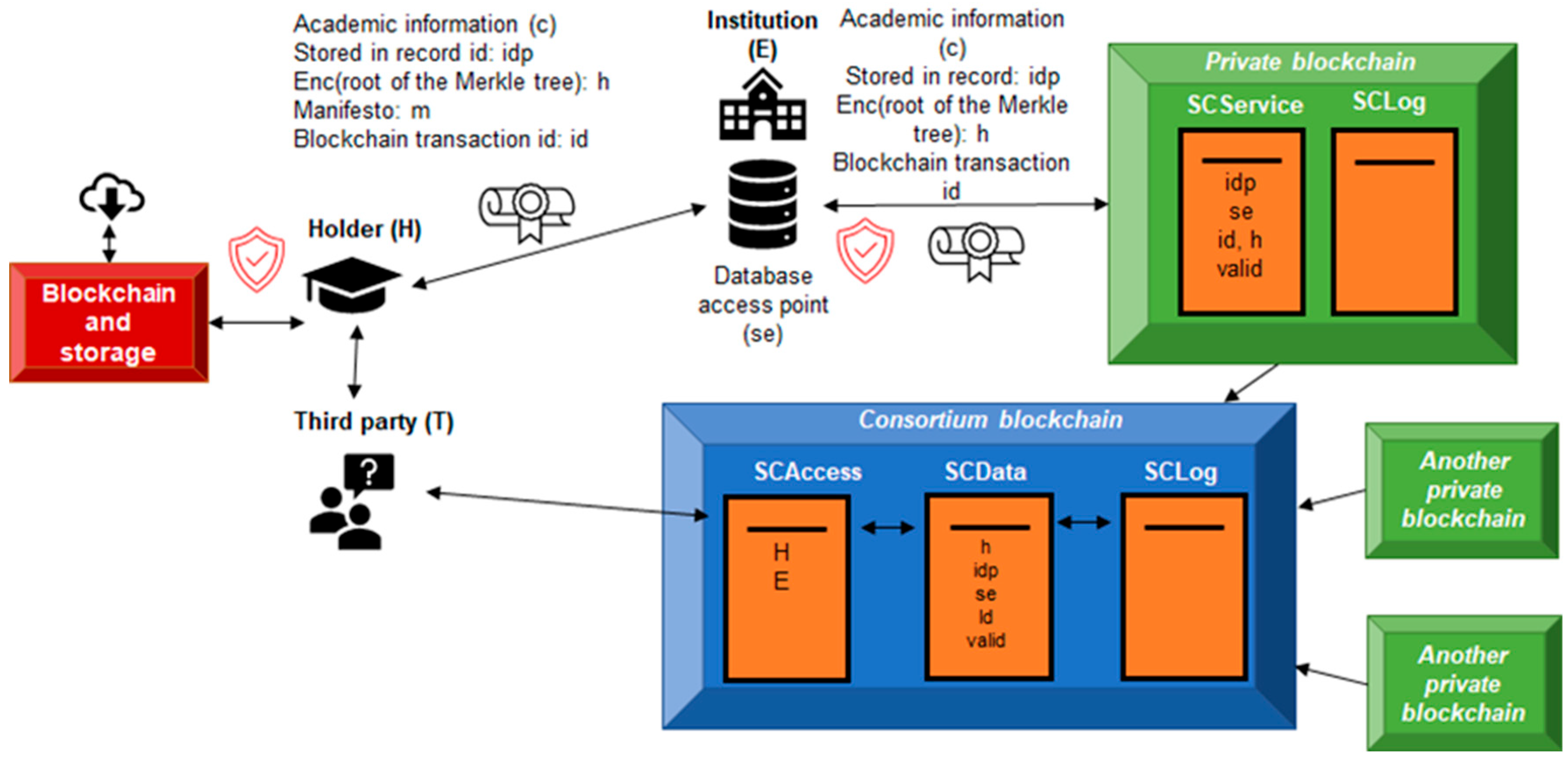
5.2. Off-Chain Data Storage
5.3. Blockchain Layers, Access Control and Use Scenarios
- SCData: A smart contract stored on a consortium blockchain that stores the anonymized values of credentials, implemented using HMACs in the developed prototype.
- SCAccess: A smart contract stored on the consortium blockchain that verifies access permissions granted by data subjects. In the current implementation of the project a Blockchain Application Firewall (BAF) [90] controls data queries and enforces user permissions, functioning as a decentralized access gateway, but this element could not necessarily be used in other implementations as it will be later discussed.
- SCLog: A smart contract in charge of registering all access to the information.
- Scenario 1: Full verification: H sends T the full certificate along with the manifest (m), including all the keys necessary to reconstruct the Merkle tree. T requests the encrypted value (h) from the SCAccess contract, verifies it against SCData, and checks its integrity.
- Scenario 2: Partial verification: H decides to share only part of the academic content. To do so, he transmits to T only the relevant elements and verification paths of the Merkle tree. After receiving the encrypted tree root from SCData (after authorization validated by SCAccess), T can verify that the partial information corresponds to a valid, unrevoked certificate.
- Scenario 3: Direct query to the issuing authority: H delegates the delivery of the information to T to E. In this case, T accesses the database pointer (stored in SCData), and after its authorization is validated in SCAccess, it can obtain the certificate (c) directly from E. This interaction is logged in SCLog.
- Store any type of academic information in a free format.
- Implement smart contracts on the platform.
- Allow the interconnection of blockchains (consortium).
- Implement storage with a blockchain-based access control system [91], where data is stored encrypted and access is restricted to the data subject.
5.4. Consortium Governance, Interconnection and Scalability
- Multiple private blockchains, managed by academic institutions.
- A central consortium blockchain aggregating anonymized information to verify academic information and verifying access rights.
6. Legal Analysis
6.1. Scope of the GDPR
- On the one hand, to the processing of personal data when the controller or processor (RT/ET) has an establishment in the EU, regardless of whether the processing takes place in the Union or not.
- On the other hand, to the processing of personal data of data subjects located in the Union by a controller or processor not established in the Union, when the processing activities are related to:
- ○
- the offering of goods or services to said data subjects in the Union, regardless of whether payment is required from them, or
- ○
- the monitoring of their behavior, to the extent that this takes place in the Union.
6.2. Personal Data Processed by the GAVIN Project
- Registration Identifier (Code).
- University Registration Identifier (Code).
- National Registration Identifier (Code).
- Surname.
- First Name.
- Identity Document.
- Gender.
- Date of Birth.
- Country of Birth.
- City of Birth.
- Country where the student currently resides.
- Student’s current city of residence.
- Postal Code.
- Student’s email address.
- Student’s phone number.
- Type of study.
- Degree.
- Area of specialization.
- Study ID.
- Issuing Entity ID.
- Start date of studies.
- End date of studies.
- Hours dedicated to completion.
- Number of academic credits (ECTS or equivalent).
- Language of study.
- Program subjects and content description.
6.3. Implications for Compliance with the Principles of Article 5 of the GDPR
6.4. Data Flows in the Model and Characterization of the Participants as Data Controllers, Processors, or Co-Controllers
- Where two or more controllers jointly determine the purposes and means of processing, they shall be considered joint controllers. The joint controllers shall determine, in a transparent manner and by mutual agreement, their respective responsibilities for compliance with the obligations imposed by this Regulation, in particular with regard to the exercise of data subject rights and their respective obligations to provide information referred to in Articles 13 and 14, unless and to the extent that their respective responsibilities are governed by Union or Member State law to which they apply. Such agreement may designate a contact point for data subjects.
- The agreement referred to in paragraph 1 shall duly reflect the respective roles and relationships of the joint controllers in relation to the data subjects. The essential aspects of the agreement shall be made available to the data subject.
- Regardless of the terms of the agreement referred to in paragraph 1, data subjects may exercise their rights under this Regulation against and against each of the controllers.
- A joint controllership agreement template, outlining:
- Purpose and legal basis for processing.
- Allocation of roles, defining clearly which institution handles data subject rights requests.
- Mechanisms for accountability, documentation and audit.
- Dispute resolution clauses
- A proposed enforcement mechanism based on:
- Periodic governance audits.
- A steering committee representing participating institutions.
- Internal dispute resolution mechanisms and escalation paths.
- Inclusion of these governance terms as binding clauses in consortium agreements.
6.5. Application of GDPR Principles
- Lawfulness, Fairness, and Transparency (Art. 5.1.a): Clear privacy policies, user-informed consent, and transparent data processing.
- Purpose Limitation (Art. 5.1.b): Academic certification as the sole purpose, no other purposes being contemplated at present.
- Data Minimization (Art. 5.1.c): Only essential data is processed and stored off-chain. The data processed is only the HMAC (as recommended by AEPD [80]) and the final result is additionally encrypted before being saved on the blockchain.
- Accuracy (Art. 5.1.d): Regarding this right, the GAVIN project model can fulfill this right by deleting the HMAC of the previous academic certificate, rendering the data arbitrary, which would effectively amount to deletion. A new academic certificate could subsequently be generated with the correct data. In any case, it is worth mentioning that the issuing institution (I) should delete the data from its off-chain systems if permitted by law. It also marks the certificate as invalid, and access control mechanisms [91] ensure that no one can access it, in addition to deleting all related information.
- Storage Limitation (Art. 5.1.e): Data remains available only while necessary or archived under public interest exceptions.
- Integrity and Confidentiality (Art. 5.1.f): According to this article of GDPR, personal data must be processed in a manner that ensures appropriate security of the personal data, including protection against unauthorized or unlawful processing and against accidental loss, destruction, or damage, by applying appropriate technical or organizational measures (“integrity and confidentiality”). The principle of data integrity is fulfilled by the blockchain technique. Furthermore, we must note that confidentiality is also guaranteed, since the academic transcript data is not visible on the blockchain since an HMAC function has been applied to it and it has been subsequently encrypted. The developed prototype implements a firewall, specifically the so-called BAF [90], which prevents unauthorized access to verification data, although it is true that it is an element outside the consortium blockchain. The BAF performs filtering and access control, verifying which resources can be accessed within SCAccess (it is even possible that the BAF may consult the rules embedded in a blockchain to reinforce trust). In this way, any user with access to said blockchain is prevented from viewing data requested by other entities, thus limiting access to information for which they do not have permissions. This is because with current blockchain technology it is not possible to perform this dynamic segmentation of permissions between accounts considered in the proposed model, so this perfectly valid technological solution is used for its real implementation in the reference technical model. In summary, encryption, access logs, and tamper-proof chains ensure data security.
- Accountability (Art. 5.2): The GAVIN project has defined and implemented appropriate technical and organizational measures to ensure and demonstrate that the processing complies with this Regulation, since, as explained, a robust pseudonymization or anonymization system is in place. Therefore, the impact of an attack or security breach would be low, given that the data stored in the blockchain is the result of several HMAC generation processes with different keys and has been subjected to an encryption process. Furthermore, the BAF mechanism is in place, which provides additional security. It should be noted that the prototype records access notarization information (a hash summary of the log recorded in the BAF to potentially detect tampering) on a blockchain (equivalent to SCLog, defined in the model) so that traceability of what has happened to their data can be maintained. Likewise, the holder can always check in SCAccess who has access permission to their academic information, and the BAF records the accesses and periodically notarizes them on a blockchain to detect potential tampering. In this way, the holder could check who has accessed specific academic information and when. This is performed because current blockchain technology does not allow reading operations to be recorded, only those that modify data. This is how this article is fulfilled in the GAVIN Project.
6.6. Privacy by Default
- As explained, both the conceptual theoretical model and the prototype developed at GAVIN comply with the principles of the GDPR, including minimization, retention limitation, and purpose limitation, as already explained.
- Regarding access, the model restricts access to only authorized users to consult the information, which is also implemented with the BAF in the reference technical model.
- Access to data by service providers is managed by users, who can choose when to provide such access and can restrict it at any time. Furthermore, all access to the blockchain is recorded.
6.7. Data Subject Rights
- Right to Access (Art. 15): The model’s design allows for automatic access by the user (holder) at any time, without the need for third-party intervention. Furthermore, access to certification records that may be stored on the blockchain by third parties other than the data subject must be authorized by the data subject, who can also revoke this authorization at any time. In this sense, we can clearly infer that the GAVIN project is ready to fulfill this right.
- Right to Rectification (Art. 16): This right can be fulfilled in two ways, as explained in the project:
- ○
- One way to fulfill this right would be to remove the keys used to generate the HMACs for the different fields, meaning that the data stored in the blockchain would become arbitrary and dissociated, and therefore could not be associated with a holder. From this point on, the new information could be uploaded to the blockchain, meaning the academic certification would be “rectified” and the data would be accurate, thus complying with the principle of accuracy.
- ○
- On the other hand, the project’s blockchain could also fulfill this right by generating the new information and linking it to the previous information using the transaction identifier or other data.
- Right to Erasure (Art. 17): It is possible to exercise this right by deleting the keys and data used to generate the HMACs of the Merkle tree, whose signed HMAC was stored in the blockchain, such that the data stored in the blockchain now becomes arbitrary and dissociated data, without the possibility of recovering the original data from it (and access is withdrawn from everyone in SCAccess and, in addition, it is marked as invalid).
- Right to Portability (Art. 20): The Implementation in the reference technical model of the project GAVIN would also guarantee this right, as it allows the download of information in a structured, commonly used, and machine-readable data format.
- Right not be subject to a decision based solely on automated processing. (Art. 22): This right would not apply since the proposed model does not consider automated processes on or off-chain. The model proposes that, for the issuance of a new certificate, the issuing institution is responsible for executing this issuance. Furthermore, the interested party is the only one who can grant or revoke access permissions to their information. Finally, to verify data, the verifying entity is the one who actively interacts with the blockchain. Automated decisions are not made, nor are data subject profiles created. This is not applicable since there is no automated decision-making by either the promoters of the initiative or third parties, as mass access to user data is not possible, as the theoretical model and the technical implementation of the prototype have adequate access control mechanisms. Specifically, in the theoretical model, the record is made in the SCLog, while in the technical reference model, the record is achieved with the BAF, since read accesses are not recorded in the blockchain. In the prototype, although access control is implemented through smart contracts and the BAF, which operate automatically, these mechanisms do not constitute automated decision-making within the meaning of Article 22 of the GDPR. Access permissions are explicitly granted by the data subject, who retains full control over who can access their academic information. The system does not create profiles or make decisions that produce legal effects or similar impacts without human intervention. Therefore, the right not to be subject to automated decision-making is not activated in this context.
6.8. Roles and Responsibilities
6.9. Cross-Border Data Flows
7. Discussion
7.1. Innovations and Contributions
7.2. Technical and Legal Challenges
- Immutability vs. Erasure: This challenge is achieved through deletion of off-chain data and hash revocation.
- Shared Responsibility: The final deployment of the model proposed by the GAVIN project requires robust legal frameworks among consortia.
- International Hosting: It is clearly an ongoing risk due to limited global GDPR harmonization.
- At the legal level, GAVIN also successfully addresses the complexities arising from co-responsibility in consortium networks. The proposal to formalize co-responsibility agreements between participating institutions and the correct identification of roles in data processing constitute a solid starting point that can be replicated in other institutional contexts.
7.3. Policy and Standardization Implications
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Gräther, W.; Kolvenbach, S.; Ruland, R.; Schütte, J.; Torres, C.F.; Wendland, F. Blockchain for Education: Lifelong Learning Passport. In Proceedings of the 1st ERCIM Blockchain Workshop 2018, Amsterdam, The Netherlands, 8–9 May 2018; European Society for Socially Embedded Technologies: Nancy, France; pp. 1–8. [Google Scholar] [CrossRef]
- Saleh, O.S.; Ghazali, O.; Rana, M.E. Blockchain based framework for educational certificates verification. J. Crit. Rev. 2020, 7, 79–84. [Google Scholar] [CrossRef]
- Tan, E.; Lerouge, E.; Caju, J.D.; Seuil, D.D. Verification of Education Credentials on European Blockchain Services Infrastructure (EBSI): Action Research in a Cross-Border Use Case between Belgium and Italy. Big Data Cogn. Comput. 2023, 7, 79. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://ssrn.com/abstract=3440802 (accessed on 15 June 2025).
- Lyons, T.; Courcelas, L.; Timsit, K. Blockchain and the GDPR. The European Union Blockchain Observatory and Forum. 2018. Available online: https://blockchain-observatory.ec.europa.eu/document/download/b3a919ed-0045-46f8-89de-f23ca140e037_en?filename=20181016_report_gdpr.pdf (accessed on 15 June 2025).
- Delgado-von-Eitzen, C.; Anido-Rifón, L.; Fernández-Iglesias, M.J. Application of Blockchain in Education: GDPR-Compliant and Scalable Certification and Verification of Academic Information. Appl. Sci. 2021, 11, 4537. [Google Scholar] [CrossRef]
- Voigt, P.; Von dem Bussche, A. The EU General Data Protection Regulation (GDPR); Springer: Cham, Switzerland, 2017. [Google Scholar] [CrossRef]
- Casino, F.; Dasaklis, T.K.; Patsakis, C. A systematic literature review of blockchain-based applications: Current status, classification and open issues. Telemat. Inform. 2019, 36, 55–81. [Google Scholar] [CrossRef]
- Khezr, S.; Moniruzzaman, M.; Yassine, A.; Benlamri, R. Blockchain Technology in Healthcare: A Comprehensive Review and Directions for Future Research. Appl. Sci. 2019, 9, 1736. [Google Scholar] [CrossRef]
- Zetzsche, D.A.; Arner, D.W.; Buckley, R.P. Decentralized Finance. J. Financ. Regul. 2020, 6, 172–203. [Google Scholar] [CrossRef]
- Wu, X.; Zou, Z.; Song, D. Ethereum Tools and Frameworks. In Learn Ethereum: Build Your Own Decentralized Applications with Ethereum and Smart Contracts; Packt: Birmingham, UK, 2019; pp. 294–335. [Google Scholar]
- Hyperledger. Whitepaper Introduction Hyperledger; Hyperledger Foundation: Francisco, CA, USA, 2018; Available online: https://www.hyperledger.org/learn/white-papers (accessed on 15 June 2025).
- Yang, D.; Long, C.; Xu, H.; Peng, S. A Review on Scalability of Blockchain. In Proceedings of the 2020 2nd International Conference on Blockchain Technology ICBCT ’20, Hawaii-Hilo, HI, USA, 12–14 March 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Fan, C.; Ghaemi, S.; Khazaei, H.; Musilek, P. Performance Evaluation of Blockchain Systems: A Systematic Survey. IEEE Access 2020, 8, 126927–126950. [Google Scholar] [CrossRef]
- Sguanci, C.; Spatafora, R.; Vergani, A.M. Layer 2 Blockchain Scaling: A Survey. 2021. Available online: https://arxiv.org/abs/2107.10881 (accessed on 15 June 2025).
- Gangwal, A.; Gangavalli, H.R.; Thirupathi, A. A Survey of Layer-two Blockchain Protocols. J. Netw. Comput. Appl. 2023, 209, 103539. [Google Scholar] [CrossRef]
- Dabbagh, M.; Choo, K.-K.R.; Beheshti, A.; Tahir, M.; Safa, N.S. A Survey of Empirical Performance Evaluation of Permissioned Blockchain Platforms: Challenges and Opportunities. Comput. Secur. 2021, 100, 102078. [Google Scholar] [CrossRef]
- Monrat, A.A.; Schelén, O.; Andersson, K. Performance Evaluation of Permissioned Blockchain Platforms. In Proceedings of the 2020 IEEE Asia-Pacific Conference on Computer Science and Data Engineering (CSDE), Gold Coast, Australia, 16–18 December 2020; pp. 1–8. [Google Scholar] [CrossRef]
- Gorenflo, C.; Lee, S.; Golab, L.; Keshav, S. FastFabric: Scaling hyperledger fabric to 20,000 transactions per second. Int. J. Netw. Manag. 2020, 30, e2099. [Google Scholar] [CrossRef]
- Castro, M.; Liskov, B. Practical Byzantine Fault Tolerance. OsDI 1999, 99, 173–186. [Google Scholar]
- Yuan, F.; Huang, X.; Zheng, L.; Wang, L.; Wang, Y.; Yan, X.; Gu, S.; Peng, Y. The Evolution and Optimization Strategies of a PBFT Consensus Algorithm for Consortium Blockchains. Information 2025, 16, 268. [Google Scholar] [CrossRef]
- Du, M.; Chen, Q.; Ma, X. MBFT: A New Consensus Algorithm for Consortium Blockchain. IEEE Access 2020, 8, 87665–87675. [Google Scholar] [CrossRef]
- Wu, X.; Jiang, W.; Song, M.; Jia, Z.; Qin, J. An Efficient Sharding Consensus Algorithm for Consortium Chains. Sci. Rep. 2023, 13, 20. [Google Scholar] [CrossRef] [PubMed]
- Correia, P.H.B.; Marques, M.A.; Simplicio, M.A.; Ermlivitch, L.; Miers, C.C.; Pillon, M.A. Comparative Analysis of Permissioned Blockchains: Cosmos, Hyperledger Fabric, Quorum, and XRPL. In Proceedings of the 2024 IEEE International Conference on Blockchain (Blockchain), Copenhagen, Denmark, 19–22 August 2024; pp. 464–469. [Google Scholar] [CrossRef]
- Hossain, D.; Mamun, Q.; Islam, R. Unleashing the Potential of Permissioned Blockchain: Addressing Privacy, Security, and Interoperability Concerns in Healthcare Data Management. Electronics 2024, 13, 5050. [Google Scholar] [CrossRef]
- Xiao, J.; Luo, T.; Li, C.; Zhou, J.; Li, Z. CE-PBFT: A High Availability Consensus Algorithm for Large-Scale Consortium Blockchain. J. King Saud Univ. Comput. Inf. Sci. 2024, 36, 101957. [Google Scholar] [CrossRef]
- Fan, C.; Lin, C.; Khazaei, H.; Musilek, P. Performance Analysis of Hyperledger Besu in Private Blockchain. In Proceedings of the 2022 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPS), Newark, CA, USA, 15–18 August 2022; pp. 64–73. [Google Scholar] [CrossRef]
- Nakai, T.; Sakurai, A.; Hironaka, S.; Shudo, K. A Formulation of the Trilemma in Proof of Work Blockchain. IEEE Access 2024, 12, 80559–80578. [Google Scholar] [CrossRef]
- Polge, J.; Robert, J.; Le Traon, Y. Permissioned Blockchain Frameworks in the Industry: A Comparison. ICT Express 2021, 7, 229–233. [Google Scholar] [CrossRef]
- Helliar, C.V.; Crawford, L.; Rocca, L.; Teodori, C.; Veneziani, M. Permissionless and Permissioned Blockchain Diffusion. Int. J. Inf. Manag. 2020, 54, 102136. [Google Scholar] [CrossRef]
- Sharma, N.; Kumar, N.; Kaushal, R.K. Exploring Blockchain Frameworks and Their Comprehensive Analysis Based on Key Metrics. In Proceedings of the 2024 IEEE 11th Uttar Pradesh Section International Conference on Electrical, Electronics and Computer Engineering (UPCON), Lucknow, India, 1 December 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Capocasale, V.; Gotta, D.; Perboli, G. Comparative Analysis of Permissioned Blockchain Frameworks for Industrial Applications. Blockchain Res. Appl. 2022, 4, 100113. [Google Scholar] [CrossRef]
- Lustenberger, M.; Spychiger, F. Blockchain in Supply Chains: An Unfulfilled Promise. Supply Chain Manag. An Int. J. 2025, 30, 178–194. [Google Scholar] [CrossRef]
- Gazi, S.F. In Code We Trust: Blockchain’s Decentralization Paradox. Vanderbilt J. Entertain. Technol. Law 2025, 27, 59. [Google Scholar] [CrossRef]
- Solat, S.; Calvez, P.; Naït-Abdesselam, F. Permissioned vs. Permissionless Blockchain: How and Why There Is Only One Right Choice. J. Softw. 2020, 16, 95–106. [Google Scholar] [CrossRef]
- Wüst, K.; Gervais, A. Do You Need a Blockchain? In Proceedings of the 2018 Crypto Valley Conference on Blockchain Technology (CVCBT), Zug, Switzerland, 20–22 June 2018; pp. 45–54. [Google Scholar] [CrossRef]
- Ozili, P.K. eNaira Central Bank Digital Currency (CBDC) for Financial Inclusion in Nigeria. In Digital Economy, Energy and Sustainability: Opportunities and Challenges; El Amine Abdelli, M., Shahbaz, M., Eds.; Springer International Publishing: Cham, Switzerland, 2023; pp. 41–54. [Google Scholar] [CrossRef]
- Alonso, S.L.N.; Jorge-Vazquez, J.; Forradellas, R.F.R. Central Banks Digital Currency: Detection of Optimal Countries for the Implementation of a CBDC and the Implication for Payment Industry Open Innovation. J. Open Innov. Technol. Mark. Complex. 2021, 7, 72. [Google Scholar] [CrossRef]
- Szabo, N. Formalizing and Securing Relationships on Public Networks. First Monday 1997, 2. [Google Scholar] [CrossRef]
- Buterin, V. A Next-Generation Smart Contract and Decentralized Application Platform. White Pap. 2014, 3, 2-1. [Google Scholar]
- Grech, A.; Camilleri, A.F. Blockchain in Education; Publications Office of the European Union: Luxembourg City, Luxembourg, 2017. [Google Scholar] [CrossRef]
- Pathak, S.; Gupta, V.; Malsa, N.; Ghosh, A.; Shaw, R.N. Blockchain-Based Academic Certificate Verification System—A Review. In Advanced Computing and Intelligent Technologies; Shaw, R.N., Das, S., Piuri, V., Bianchini, M., Eds.; Springer Nature: Singapore, 2022; pp. 527–539. [Google Scholar] [CrossRef]
- Saadati, Z.; Zeki, C.P.; Barenji, R.V. On the Development of Blockchain-based Learning Management System as a Metacognitive Tool to Support Self-Regulation Learning in Online Higher Education. Interact. Learn. Environ. 2023, 31, 3148–3171. [Google Scholar] [CrossRef]
- Arenas, R.; Fernandez, P. CredenceLedger: A Permissioned Blockchain for Verifiable Academic Credentials. In Proceedings of the IEEE International Conference on Engineering, Technology and Innovation (ICE/ITMC), Stuttgart, Germany; 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Alammary, A.; Alhazmi, S.; Almasri, M.; Gillani, S. Blockchain-Based Applications in Education: A Systematic Review. Appl. Sci. 2019, 9, 2400. [Google Scholar] [CrossRef]
- Delgado-von-Eitzen, C.; Anido-Rifón, L.; Fernández-Iglesias, M.J. Blockchain Applications in Education: A Systematic Literature Review. Appl. Sci. 2021, 11, 11811. [Google Scholar] [CrossRef]
- Yumna, H.; Khan, M.M.; Ikram, M.; Ilyas, S. Use of Blockchain in Education: A Systematic Literature Review. In Intelligent Information and Database Systems; Nguyen, N.T., Gaol, F.L., Hong, T.-P., Trawiński, B., Eds.; Springer: Cham, Switzerland, 2019; Volume 11432, pp. 191–202. [Google Scholar] [CrossRef]
- Sharples, M.; Domingue, J. The blockchain and kudos: A distributed system for educational record, reputation and reward. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Heidelberg, Germany, 2016; pp. 490–496. [Google Scholar] [CrossRef]
- Turkanović, M.; Hölbl, M.; Košič, K.; Heričko, M.; Kamišalić, A. EduCTX: A blockchain-based higher education credit platform. IEEE Access 2018, 6, 5112–5127. [Google Scholar] [CrossRef]
- Malibari, N.A. A Survey on Blockchain-based Applications in Education. In Proceedings of the 2020 7th International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 12–14 March 2020; pp. 266–270. [Google Scholar] [CrossRef]
- Ocheja, P.; Agbo, F.J.; Oyelere, S.S.; Flanagan, B.; Ogata, H. Blockchain in Education: A Systematic Review and Practical Case Studies. IEEE Access 2022, 10, 99525–99540. [Google Scholar] [CrossRef]
- Raimundo, R.; Rosário, A. Blockchain System in the Higher Education. Eur. J. Investig. Heal. Psychol. Educ. 2021, 11, 276–293. [Google Scholar] [CrossRef]
- Razia, B.; Awwad, B. A Comprehensive Review of Blockchain Technology and Its Related Aspects in Higher Education. In Technologies, Artificial Intelligence and the Future of Learning Post-COVID-19: The Crucial Role of International Accreditation; Hamdan, A., Hassanien, A.E., Mescon, T., Alareeni, B., Eds.; Springer International Publishing: Cham, Switzerland, 2022; pp. 553–571. [Google Scholar] [CrossRef]
- Talat, M.; Riaz, S.; Farooq, M.S. Effect of Blockchain on Education: A Systemic Literature Review. VFAST Trans. Softw. Eng. 2022, 10, 116–124. [Google Scholar] [CrossRef]
- Chinnasamy, P.; Ramani, D.R.; Ayyasamy, R.K.; Jebamani, B.J.A.; Dhanasekaran, S.; Praveena, V. Applications of Blockchain Technology in Modern Education System—Systematic Review. In Proceedings of the 2023 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 23–25 January 2023; pp. 1–4. [Google Scholar] [CrossRef]
- Hu, D.; Pongpatcharatrontep, D.; Timsard, S.; Khamaksorn, A. Blockchain Applications in Higher Education: A Systematic Literature Review. In Proceedings of the 2023 Joint International Conference on Digital Arts, Media and Technology with ECTI Northern Section Conference on Electrical, Electronics, Computer and Telecommunications Engineering (ECTI DAMT & NCON), Phuket, Thailand, 22–25 March 2023; pp. 188–193. [Google Scholar] [CrossRef]
- Rustemi, A.; Dalipi, F.; Atanasovski, V.; Risteski, A. A Systematic Literature Review on Blockchain-Based Systems for Academic Certificate Verification. IEEE Access 2023, 11, 64679–64696. [Google Scholar] [CrossRef]
- Al-Tawara, F.; Qasaimeh, M.; Jarad, D.; Al-Qassas, R.S. Utilizing the Blockchain Technology for Higher Education in the Era of Pandemics: A Systematic Review. In Proceedings of the 2023 14th International Conference on Information and Communication Systems (ICICS), Irbid, Jordan, 21–23 November 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Molopa, S.T.; Cronje, J. Research on Blockchain Adoption in Higher Education: A Systematic Review and Conceptual Model. In Advances in Information and Communication; Arai, K., Ed.; Springer Nature: Cham, Switzerland, 2024; pp. 110–130. [Google Scholar]
- Vaezinejad, S.; Chen, Y.; Kouhizadeh, M.; Ozpolat, K. Blockchain Technology for Higher Education and Recruitment: A Systematic Literature Review. Eurasian J. Bus. Econ. 2024, 17, 1–27. [Google Scholar] [CrossRef]
- Wang, X.; Younas, M.; Jiang, Y.; Imran, M.; Almusharraf, N. Transforming Education Through Blockchain: A Systematic Review of Applications, Projects, and Challenges. IEEE Access 2025, 13, 13264–13284. [Google Scholar] [CrossRef]
- Silaghi, D.L.; Popescu, D.E. A Systematic Review of Blockchain-Based Initiatives in Comparison to Best Practices Used in Higher Education Institutions. Computers 2025, 14, 141. [Google Scholar] [CrossRef]
- Jain, R.; Seth, N.; Sood, K.; Grima, S. Mapping the Research on Blockchain in Education: A Systematic Review and Bibliometric Analysis. In Digital Transformation, Strategic Resilience, Cyber Security and Risk Management. In Contemporary Studies in Economic and Financial Analysis; Sood, K., Balusamy, B., Grima, S., Eds.; Emerald Publishing Limited: Leeds, UK, 2023; Volume 111C, pp. 53–66. [Google Scholar] [CrossRef]
- de Alwis, A.; Shrestha, A.; Sarker, T. Exploring Governance for Accreditation in the Education Sector using Blockchain Technology: A Systematic Literature Review. Discov. Educ. 2025, 4, 57. [Google Scholar] [CrossRef]
- Joshi, P.; Ayare, A.A.; Jadhav, V.A.; Banatwala, M.K.; Changllere, S.V.; Mote, A. A Systematic Review on Blockchain-Based Framework for Storing Educational Records Using InterPlanetary File System. Cureus. J. Comput. Sci. 2025, 2. [Google Scholar] [CrossRef]
- Bhaskar, P.; Tiwari, C.K.; Joshi, A. Blockchain in Education Management: Present and Future Applications. Interact. Technol. Smart Educ. 2020, 18, 1–17. [Google Scholar] [CrossRef]
- Caldarelli, G.; Ellul, J. Trusted Academic Transcripts on the Blockchain: A Systematic Literature Review. Appl. Sci. 2021, 11, 4. [Google Scholar] [CrossRef]
- Castro, R.Q.; Au-Yong-Oliveira, M. Blockchain and Higher Education Diplomas. Eur. J. Investig. Heal. Psychol. Educ. 2021, 11, 154–167. [Google Scholar] [CrossRef] [PubMed]
- Dash, M.K.; Panda, G.; Kumar, A.; Luthra, S. Applications of blockchain in government education sector: A comprehensive review and future research potentials. J. Glob. Oper. Strateg. Sourc. 2022, 15, 449–472. [Google Scholar] [CrossRef]
- Hameed, B.; Murad, M.; Noman, A.; Javed, M.; Ramzan, M.; Ashfaq, F.; Usman, H.; Yousaf, M. “A Review of Blockchain based Educational Projects. Int. J. Adv. Comput. Sci. Appl. 2019, 10. [Google Scholar] [CrossRef]
- Kabashi, F.; Snopce, H.; Aliu, A.; Luma, A.; Shkurti, L. A Systematic Literature Review of Blockchain for Higher Education. In Proceedings of the 2023 International Conference on IT Innovation and Knowledge Discovery (ITIKD), Manama, Bahrain, 8–9 March 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Loukil, F.; Abed, M.; Boukadi, K. Blockchain adoption in education: A systematic literature review. Educ. Inf. Technol. 2021, 26, 5779–5797. [Google Scholar] [CrossRef]
- Molina, F.; Betarte, G.; Luna, C. A Blockchain Based and GDPR-compliant Design of a System for Digital Education Certificates. Clei Electron. J. 2023, 26. [Google Scholar] [CrossRef]
- Delgado-von-Eitzen, C.; Anido-Rifón, L.; Fernández-Iglesias, M.J. NFTs for the Issuance and Validation of Academic Information That Complies with the GDPR. Appl. Sci. 2024, 14, 706. [Google Scholar] [CrossRef]
- Finck, M. Blockchain and the General Data Protection Regulation. Can Distributed Ledgers be Squared with European Data Protection Law? Publications Office of the European Union: Luxembourg, 2019. [Google Scholar] [CrossRef]
- Zyskind, G.; Nathan, O. Decentralizing Privacy: Using Blockchain to Protect Personal Data. In Proceedings of the 2015 IEEE Security and Privacy Workshops, San Jose, CA, USA, 21–22 May 2015; pp. 180–184. [Google Scholar] [CrossRef]
- Dang, Q. Secure Hash Federal Information Processing Standards (NIST FIPS); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2015. [Google Scholar] [CrossRef]
- Baldi, M.; Chiaraluce, F.; Kodra, M.; Spalazzi, L. Security analysis of a blockchain-based protocol for the certification of academic credentials. arXiv 2019, arXiv:1910.04622. [Google Scholar] [CrossRef]
- Badyal, S.; Chowdhary, A. Alumnichain: Blockchain based records verification service. Int. J. Innov. Technol. Explor. Eng. 2019, 8, 4296–4299. [Google Scholar] [CrossRef]
- Agencia Española de Protección de Datos (AEPD) and European Data Protection Supervisor (EDPS). Introduction to the Hash Function as a Personal Data Pseudonymisation Technique. 2019. Available online: https://edps.europa.eu/data-protection/our-work/publications/papers/introduction-hash-function-personal-data_en (accessed on 15 June 2025).
- Gencia Española de Protección de Datos (AEPD). Proof of Concept Blockchain and the Right to Erasure. 2024. Available online: https://www.aepd.es/guias/Tech-note-blockchain.pdf (accessed on 15 June 2025).
- Hutchinson, T.; Duncan, N. Defining and Describing what We Do: Doctrinal Legal Research. Deakin Law Rev. 2012, 17, 83–119. Available online: https://search.informit.org/doi/10.3316/agis_archive.20125043 (accessed on 15 June 2025). [CrossRef]
- Chui, W.H.; McConville, M. Research Methods for Law; Edinburgh University Press Edinburgh: Scotland, UK, 2007; Volume 104. [Google Scholar]
- van Hoecke, M. Methodologies of Legal Research: Which Kind of Method for What Kind of Discipline? Bloomsbury Publishing: London, UK, 2011; Available online: https://search.worldcat.org/es/title/687705093 (accessed on 15 June 2025).
- Delgado-von-Eitzen, C.; Fernández-Iglesias, M.J.; Anido-Rifón, L. A GDPR-Compliant Blockchain Architecture for the Verification of Educational Credentials: Design, Implementation, and Evaluation. Prepr. Available SSRN 2025. [Google Scholar] [CrossRef]
- Kotonya, G.; Sommerville, I. Requirements Engineering: Processes and Techniques; Wiley Publishing: Hoboken, NJ, USA, 1998. [Google Scholar]
- Eurostat. Tertiary Education Statistics. 2025. Available online: https://ec.europa.eu/eurostat/statistics-explained/index.php?title=Tertiary_education_statistics#Graduates (accessed on 5 April 2025).
- Krawczyk, H.; Bellare, M.; Canetti, R. HMAC: Keyed-hashing for message authentication. RFC 2104. 1997. Available online: https://www.rfc-editor.org/rfc/rfc2104 (accessed on 15 June 2025).
- Liu, H.; Luo, X.; Liu, H.; Xia, X. Merkle Tree: A Fundamental Component of Blockchains. In Proceedings of the 2021 International Conference on Electronic Information Engineering and Computer Science (EIECS), Changchun, China, 23–26 September 2021; pp. 556–561. [Google Scholar] [CrossRef]
- Delgado-von-Eitzen, C.; Iglesias, M.J.F.; Rifón, L.E.A.; Mikic-Fonte, F.A. Blockchain Beyond Immutability: Application Firewalls on Ethereum-Based Platforms. Comput. Stand. Interfaces 2025, 95, 104038. [Google Scholar] [CrossRef]
- Delgado-von-Eitzen, C.; Fernández-Iglesias, M.J.; Anido-Rifón, L.; Llamas-Nistal, M. Ethereum Blockchain Interconnectivity for Dynamic and Privacy-Preserving Access Control. IEEE Access 2025, 13, 112918–112931. [Google Scholar] [CrossRef]
- Kenler, E.; Razzoli, F. MariaDB Essentials; Packt Publishing Ltd.: Birmingham, UK, 2015. [Google Scholar]
- Delgado-von-Eitzen, C.; Anido-Rifón, L.; Ruiz-Molina, M.; Fernández-Iglesias, M.J. Bridging the Gap: Achieving Seamless Interoperability Between Ethereum-Based Blockchains Using Inter-Blockchain Communication Protocols. Softw. Pract. Exp. 2025. [Google Scholar] [CrossRef]
- Dorsala, M.R.; Sastry, V.N.; Chapram, S. Blockchain-based Solutions for Cloud Computing: A Survey. J. Netw. Comput. Appl. 2021, 196, 103246. [Google Scholar] [CrossRef]
- Khanna, A.; Sah, A.; Bolshev, V.; Burgio, A.; Panchenko, V.; Jasiński, M. Blockchain–Cloud Integration: A Survey. Sensors 2022, 22, 5238. [Google Scholar] [CrossRef]
- Mechkaroska, D.; Popovska-Mitrovikj, A.; Mitrevska, S. Overview of Blockchain and Cloud Computing Services Integration. In Proceedings of the 2022 30th Telecommunications Forum (TELFOR), Belgrade, Serbia, 15–16 November 2022; pp. 1–4. [Google Scholar] [CrossRef]
- Anido-Rifón, L. A Proposal for a Blockchain-based Academic Certification System that Complies with the GDPR. 2025. Available online: https://blockstand.eu/blockstand/uploads/2025/05/Anido-Blockstand-report1-v1.4.pdf (accessed on 15 June 2025).
- Anido-Rifón, L. Standardization of a Blockchain-Based Interoperability Platform for Academic Credentials. 2025. Available online: https://blockstand.eu/blockstand/uploads/2025/05/Anido-Blockstand-report2-v1.pdf (accessed on 15 June 2025).

| Article | Principle | Description |
|---|---|---|
| GDPR, art. 5.1.a | Lawfulness, fairness and transparency. | Personal data shall be processed lawfully, fairly and in a transparent manner in relation to individuals. |
| GDPR, art. 5.1.b | Purpose limitation. | Personal data shall be collected for specified, explicit and legitimate purposes and not further processed in a manner that is incompatible with those purposes; further processing for archiving purposes in the public interest, scientific or historical research purposes or statistical purposes shall not be considered to be incompatible with the initial purposes. |
| GDPR, art. 5.1.c | Data minimization. | Personal data shall be adequate, relevant and limited to what is necessary in relation to the purposes for which they are processed. |
| GDPR, art. 5.1.d | Accuracy. | Personal data shall be accurate and, where necessary, kept up to date; every reasonable step must be taken to ensure that personal data that are inaccurate, having regard to the purposes for which they are processed, are erased or rectified without delay. |
| GDPR, art. 5.1.e | Storage limitation. | Personal data shall be kept in a form which permits identification of data subjects for no longer than is necessary for the purposes for which the personal data are processed; personal data may be stored for longer periods insofar as the personal data will be processed solely for archiving purposes in the public interest, scientific or historical research purposes or statistical purposes subject to implementation of the appropriate technical and organisational measures required by the GDPR in order to safeguard the rights and freedoms of individuals. |
| GDPR, art. 5.1.f | Integrity and confidentiality (security). | Personal data shall be processed in a manner that ensures appropriate security of the personal data, including protection against unauthorised or unlawful processing and against accidental loss, destruction or damage, using appropriate technical or organisational measures. |
| GDPR, art. 5.2 | Accountability. | The controller shall be responsible for and be able to demonstrate compliance with. |
| GDPR, art. 16 | Right to rectification. | The data subject shall have the right to obtain from the controller without undue delay the rectification of inaccurate personal data concerning him or her. Taking into account the purposes of the processing, the data subject shall have the right to have incomplete personal data completed, including by means of providing a supplementary statement. |
| GDPR, art. 17 | Right to erasure (right to be forgotten). | The data subject shall have the right to obtain from the controller the erasure of personal data concerning him or her without undue delay and the controller shall have the obligation to erase personal data without undue delay where one of the following grounds applies: (a) the personal data are no longer necessary in relation to the purposes for which they were collected or otherwise processed; (b) the data subject withdraws consent on which the processing is based according to point (a) of Article 6(1), or point (a) of Article 9(2), and where there is no other legal ground for the processing; (c) the data subject objects to the processing pursuant to Article 21(1) and there are no overriding legitimate grounds for the processing, or the data subject objects to the processing pursuant to Article 21(2); (d) the personal data have been unlawfully processed; |
| GDPR, art. 20 | Right to data portability. | The data subject shall have the right to receive the personal data concerning him or her, which he or she has provided to a controller, in a structured, commonly used and machine-readable format and have the right to transmit those data to another controller without hindrance from the controller to which the personal data have been provided; |
| GDPR, art. 22 | Right not be subject to a decision based solely on automated processing. | The data subject shall have the right not to be subject to a decision based solely on automated processing, including profiling, which produces legal effects concerning him or her or similarly significantly affects him or her; |
| GDPR, art. 25. | Data protection by design and by default. | Taking into account the state of the art, the cost of implementation and the nature, scope, context and purposes of processing as well as the risks of varying likelihood and severity for rights and freedoms of natural persons posed by the processing, the controller shall, both at the time of the determination of the means for processing and at the time of the processing itself, implement appropriate technical and organisational measures (…) in an effective manner and to integrate the necessary safeguards into the processing in order to meet the requirements of this Regulation and protect the rights of data subjects. |
| Feature | GAVIN (This Article) | Molina et al. [73] |
|---|---|---|
| Number of blockchains | A combination of private and consortium blockchains is used to improve scalability. | It does not clearly mention whether it uses more than one blockchain. |
| Partial data sharing | Sharing only certain parts of academic information is allowed (for example, title only, no grades). | It does not explicitly mention this aspect. |
| Data regeneration in case of data loss | A strategy is offered to recover certificates even if the issuing institution disappears. | It does not explicitly mention this aspect. |
| Scalability | Solutions are proposed for managing large volumes of academic data. | Not specifically addressed. |
| Prototype | There is a prototype in development with current blockchain technology. | It does not explicitly mention this aspect. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gómez Vieites, A.; Delgado-von-Eitzen, C.; Estévez Garcia, D. GDPR-Compliant Academic Certification via Blockchain: Legal and Technical Validation of the GAVIN Project. Appl. Sci. 2025, 15, 9191. https://doi.org/10.3390/app15169191
Gómez Vieites A, Delgado-von-Eitzen C, Estévez Garcia D. GDPR-Compliant Academic Certification via Blockchain: Legal and Technical Validation of the GAVIN Project. Applied Sciences. 2025; 15(16):9191. https://doi.org/10.3390/app15169191
Chicago/Turabian StyleGómez Vieites, Alvaro, Christian Delgado-von-Eitzen, and Diego Estévez Garcia. 2025. "GDPR-Compliant Academic Certification via Blockchain: Legal and Technical Validation of the GAVIN Project" Applied Sciences 15, no. 16: 9191. https://doi.org/10.3390/app15169191
APA StyleGómez Vieites, A., Delgado-von-Eitzen, C., & Estévez Garcia, D. (2025). GDPR-Compliant Academic Certification via Blockchain: Legal and Technical Validation of the GAVIN Project. Applied Sciences, 15(16), 9191. https://doi.org/10.3390/app15169191






