A Novel Ensemble of Deep Learning Approach for Cybersecurity Intrusion Detection with Explainable Artificial Intelligence
Abstract
1. Introduction
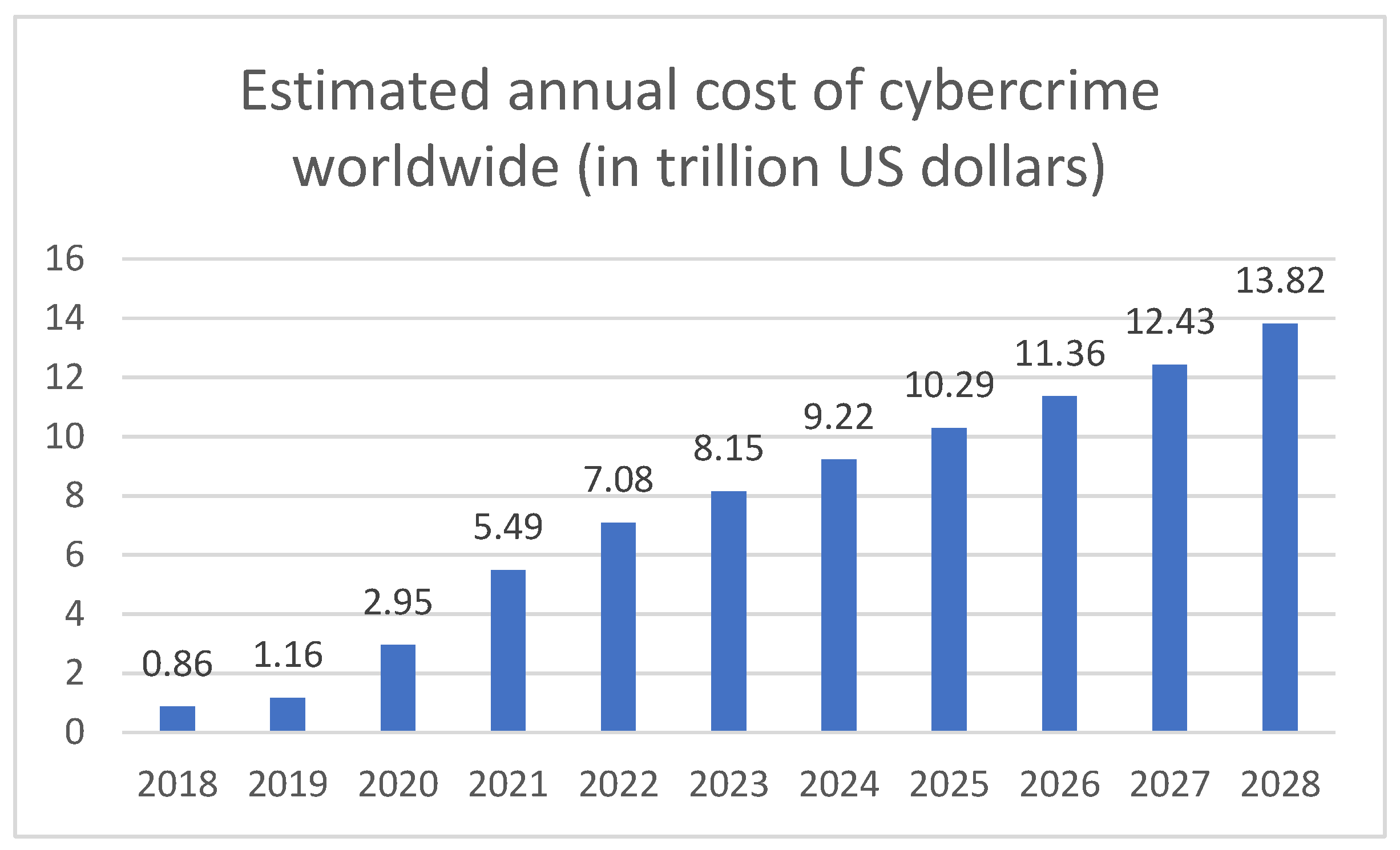
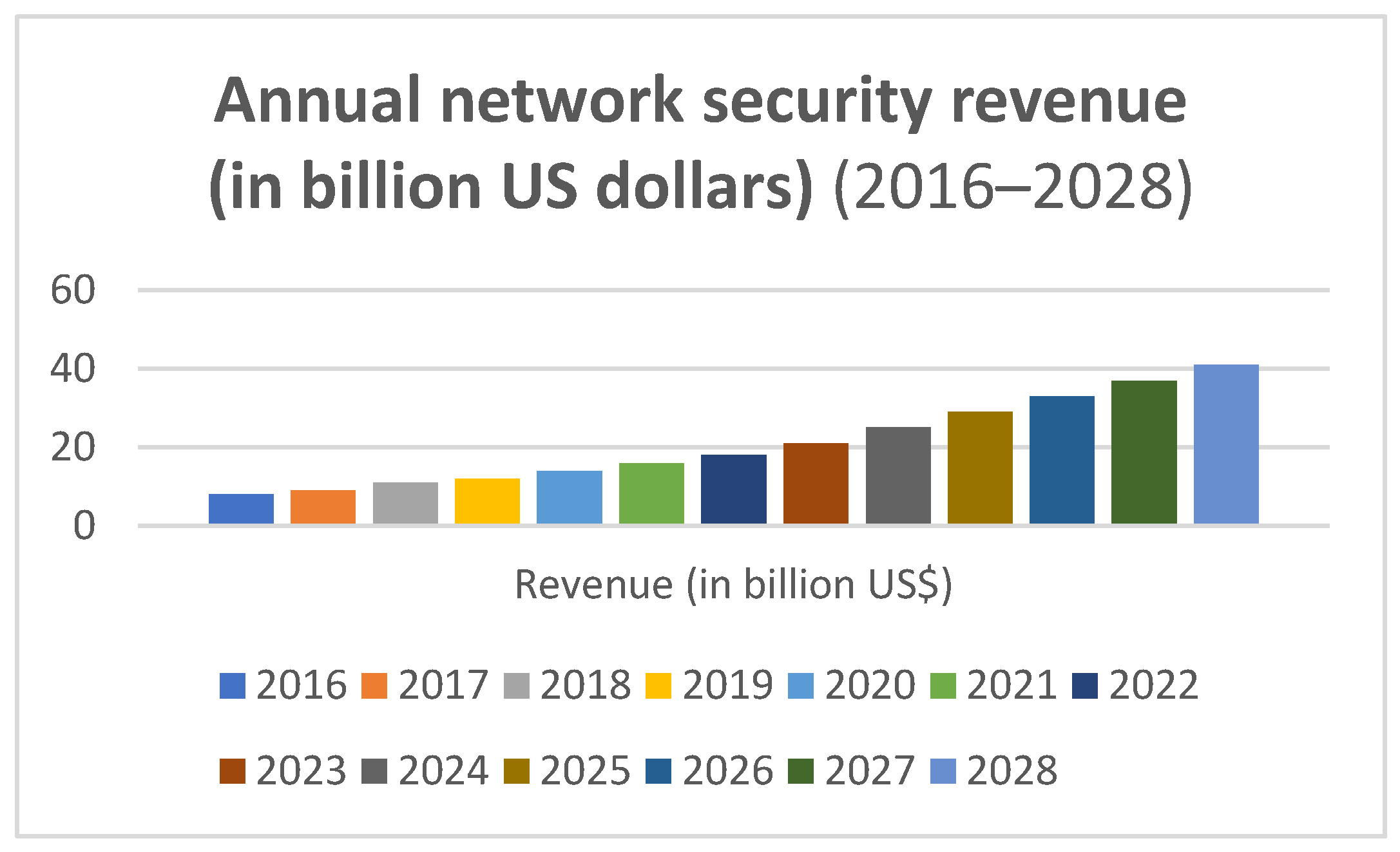
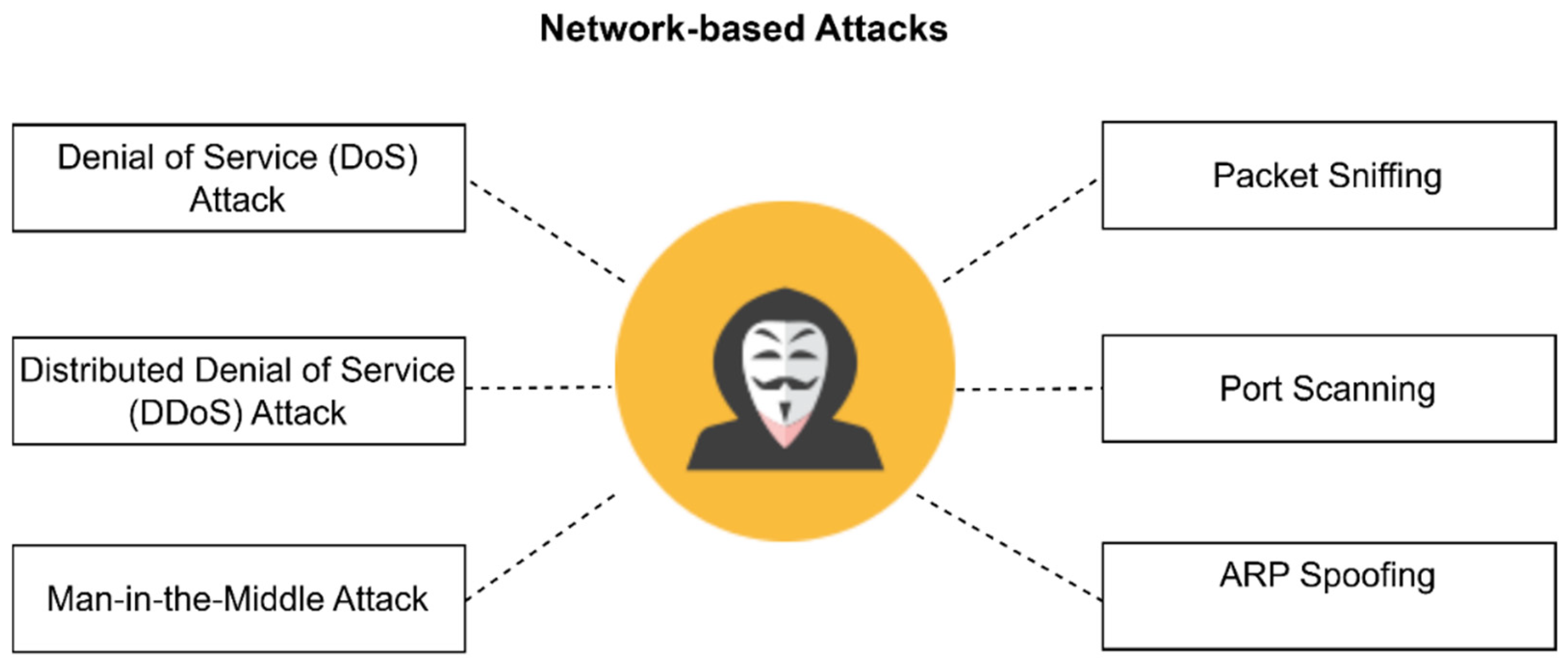
- Increased attack complexity: Modern threats such as Distributed Denial of Service (DDoS) and polymorphic malware evolve rapidly, often bypassing static, pattern-based detection methods [4].
- Proposing a novel ensemble learning framework (ANN + SVM with RF meta-classifier) that achieves competitive performance compared to state-of-the-art intrusion detection models.
- Employing Recursive Feature Elimination (RFE) to dynamically select the most relevant features and reduce model complexity.
- Incorporating explainable artificial intelligence (XAI) to interpret individual detection decisions and improve transparency.
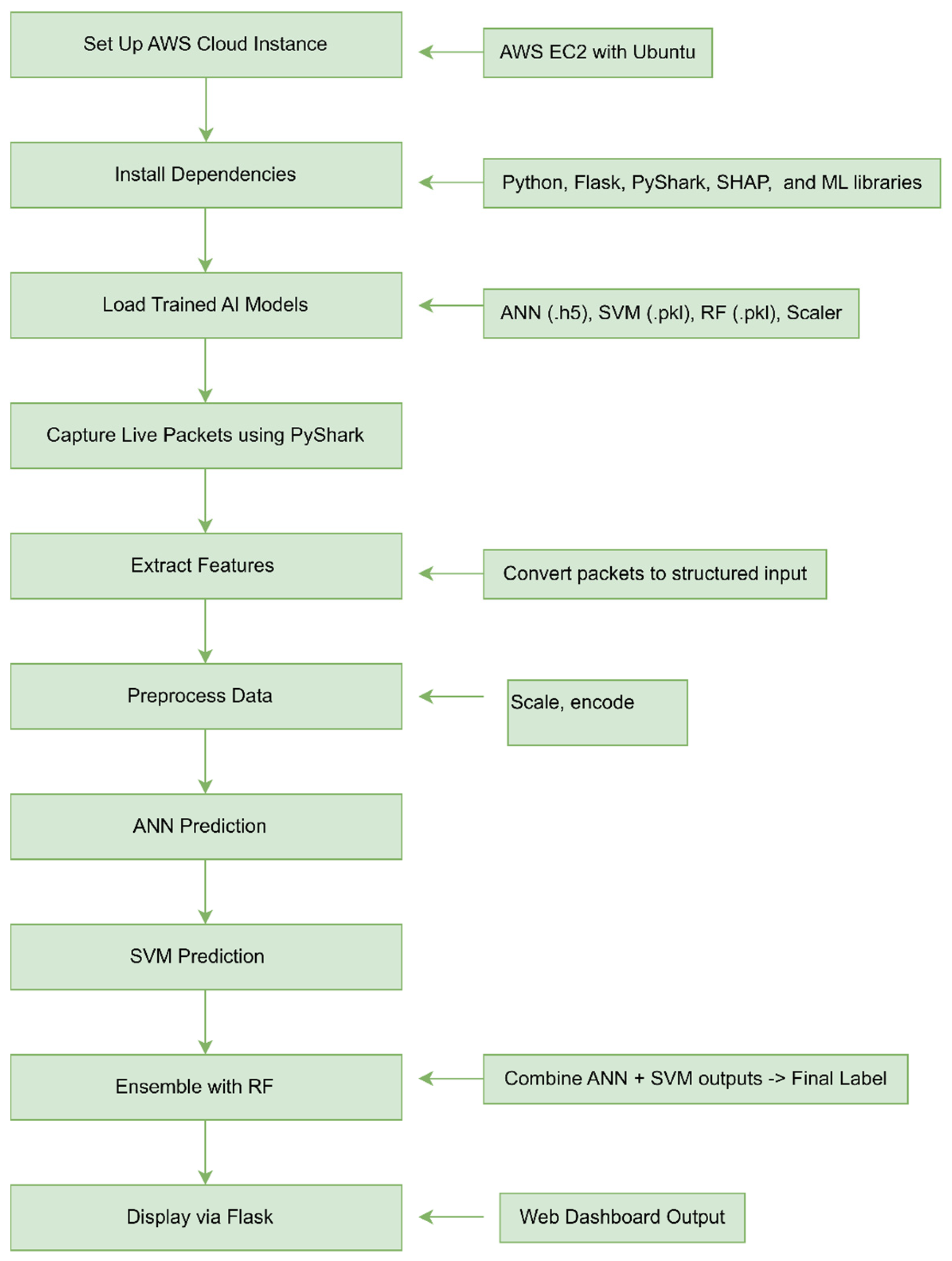
- Developing a real-time deployment pipeline using Flask and live packet capture for immediate anomaly detection and dashboard reporting, in the real cloud environment.
2. Background and Literature Review
- Real-time cloud-based detection: Our framework integrates live network traffic capture within a cloud environment (e.g., AWS), enabling continuous monitoring and immediate anomaly detection, a capability often missing in previous works.
- Hybrid ensemble learning: By combining an ANN and SVM as base classifiers with an RF meta-classifier, our approach leverages the strengths of both DL and traditional ML. This hybrid model achieves superior performance over standalone models.
- Explainable AI integration (SHAP): We incorporate SHAP (SHapley Additive exPlanations) to provide both global and local interpretability, addressing the black-box nature of most DL-based IDS and increasing trust among security analysts.
- End-to-end system architecture: Our work goes beyond theoretical accuracy by delivering a fully functional real-time deployment pipeline using Flask, offering a web-based interface for monitoring and actionable threat alerts, closing the gap between research and real-world usability.
3. Methodology
3.1. Data Acquisition
- Total Records: 22,544.
- Normal Records: 9711.
- Attack Records: 12,833 (including both known and unknown attack types).
- Each record in the dataset represents a single network connection and includes 41 features grouped into three categories:
- Basic features (e.g., duration, protocol type, service).
- Content features (e.g., number of failed logins, root shell).
- Traffic features (e.g., same host connections, packet rates).
3.2. Data Preprocessing, Feature Selection, and Feature Scaling
3.2.1. Recursive Feature Elimination (RFE)
3.2.2. Standardization with StandardScaler
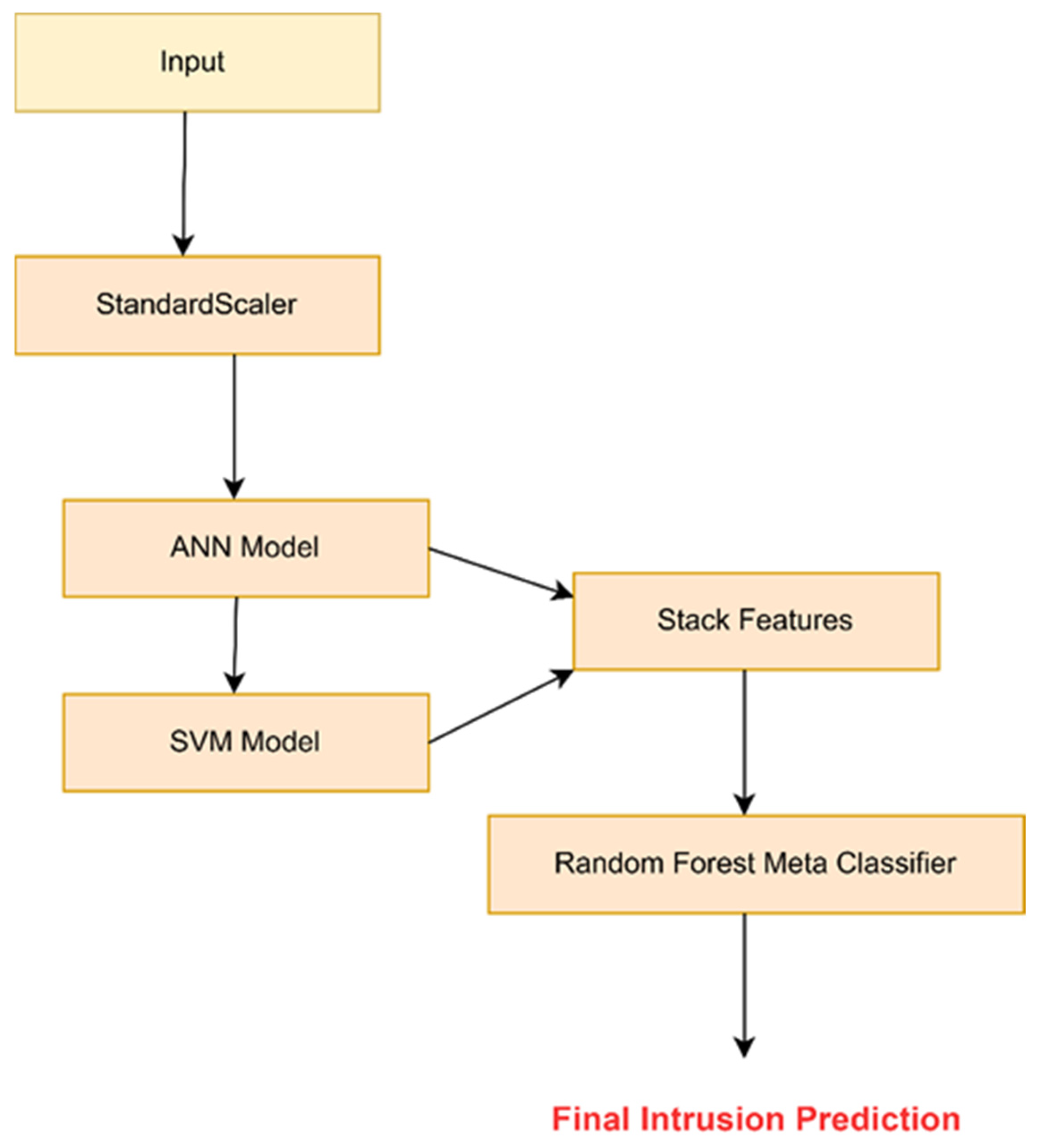
3.3. Model Construction
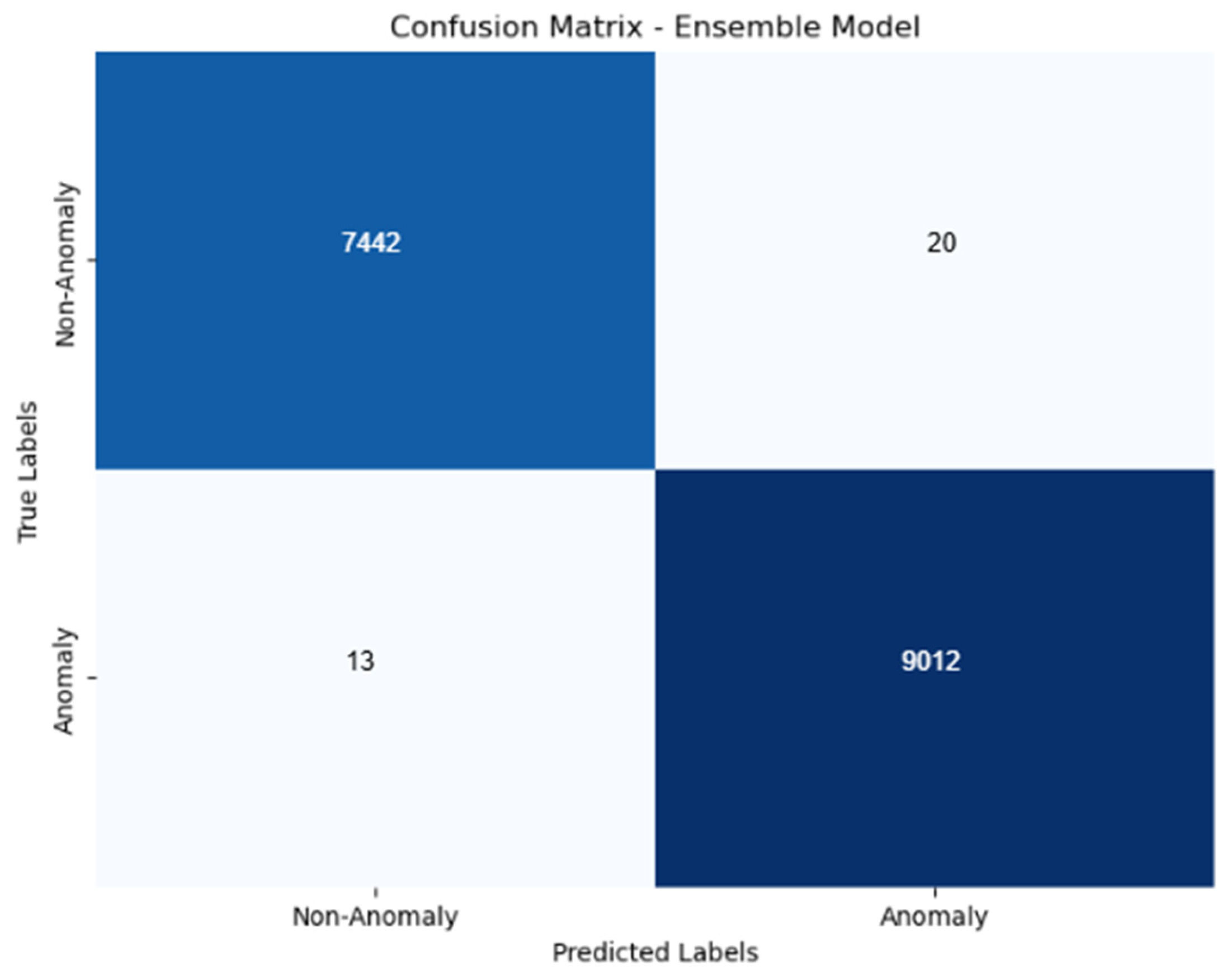
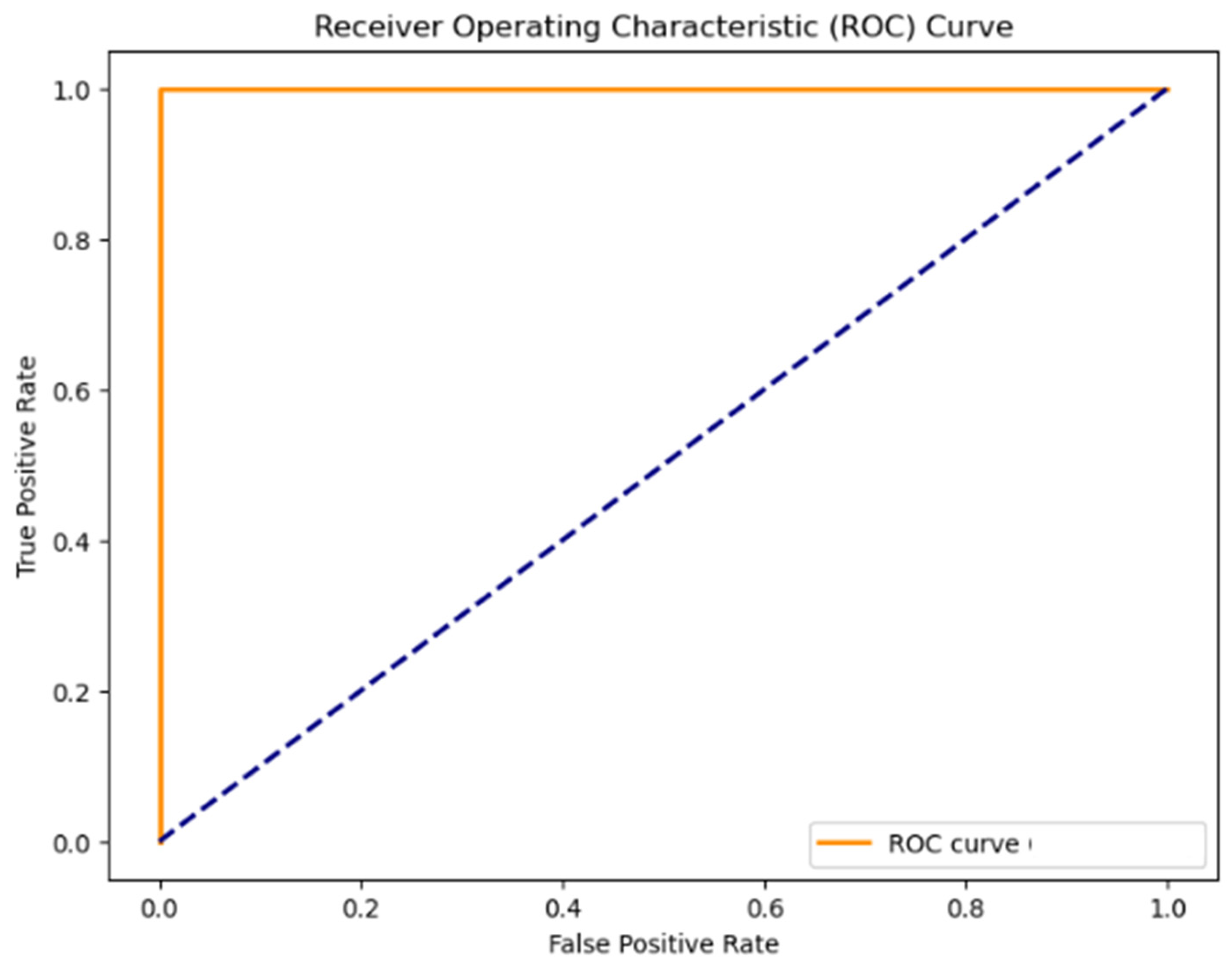
3.4. Model Evaluation
- TP (True Positives): Correctly predicted anomalies;
- TN (True Negatives): Correctly predicted normal instances;
- FP (False Positives): Normal instances incorrectly classified as anomalies;
- FN (False Negatives): Anomalies incorrectly classified as normal.
- Accuracy
- Precision
- Recall (also known as Sensitivity or True Positive Rate)
- F1-Score
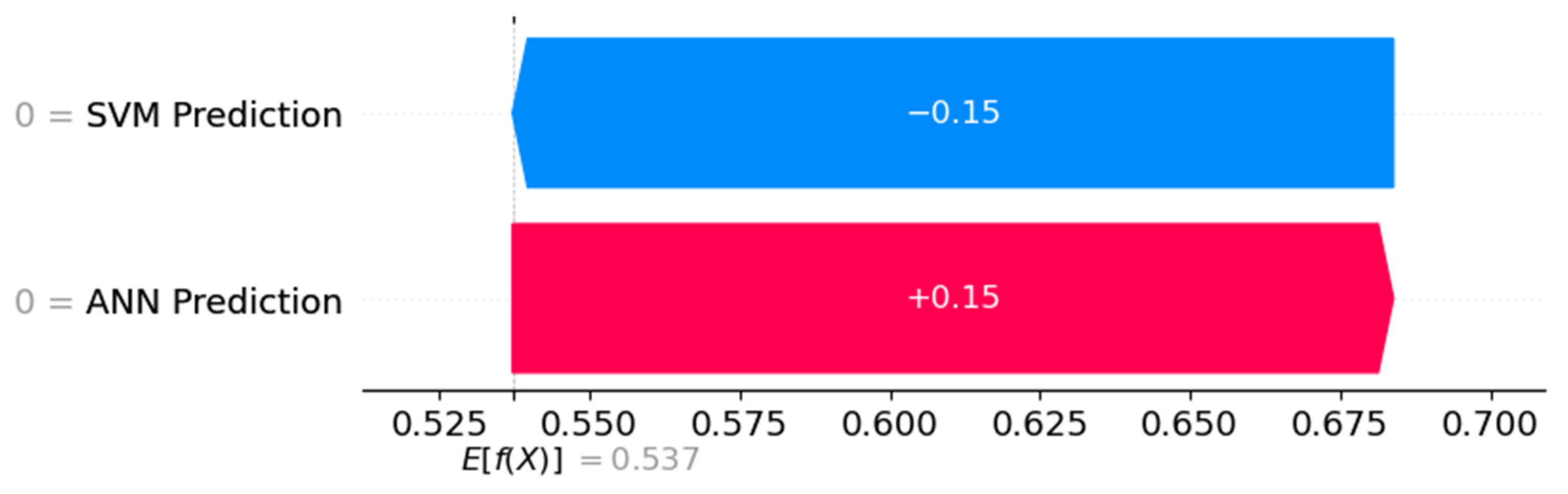
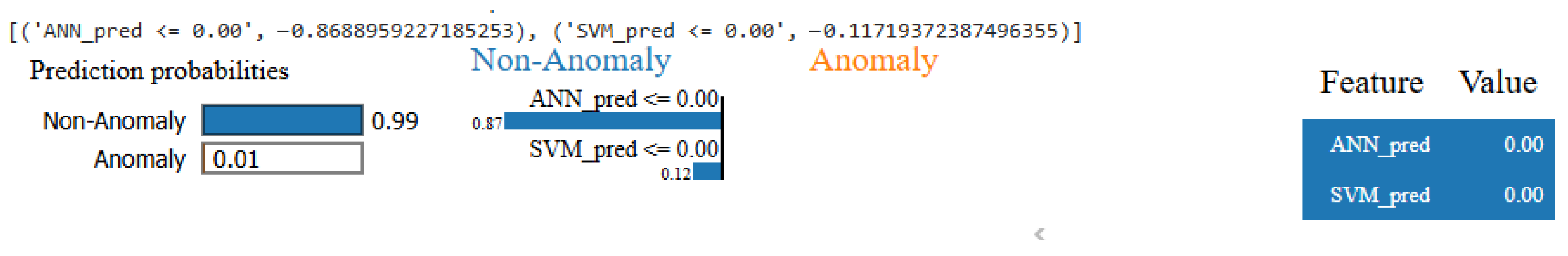
3.5. Explainability Integration
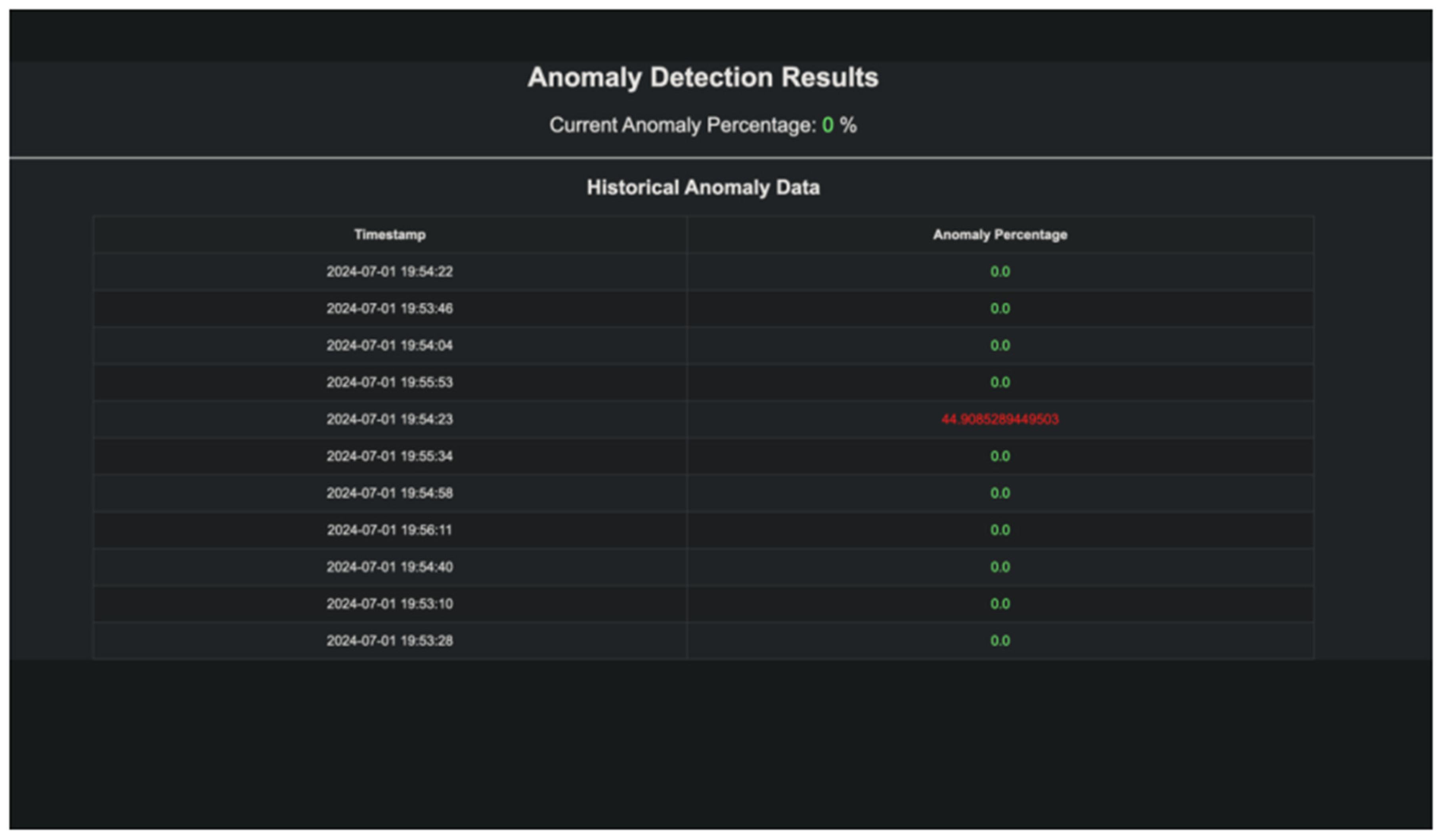
3.6. Real-Time Integration (Deployment)
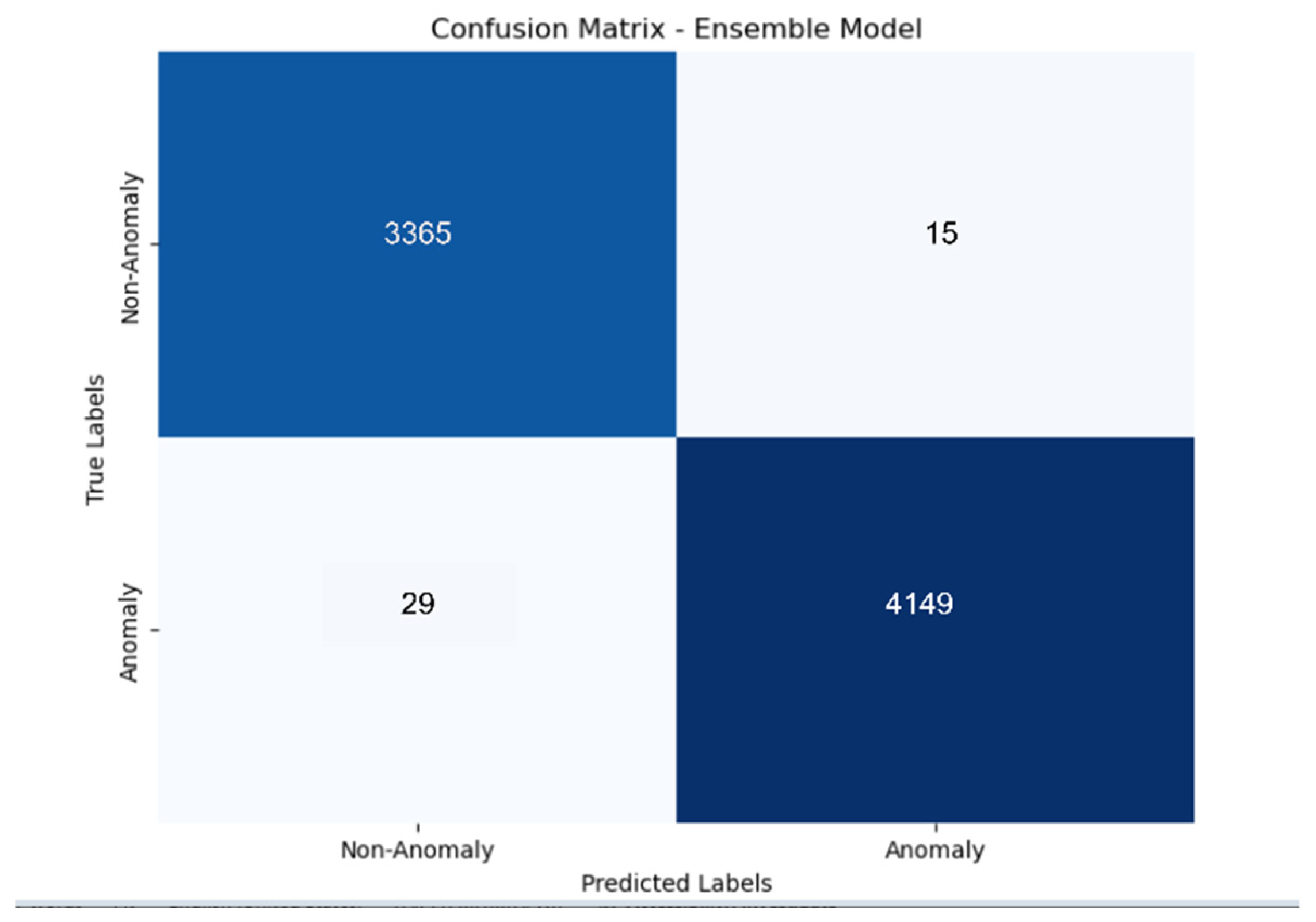
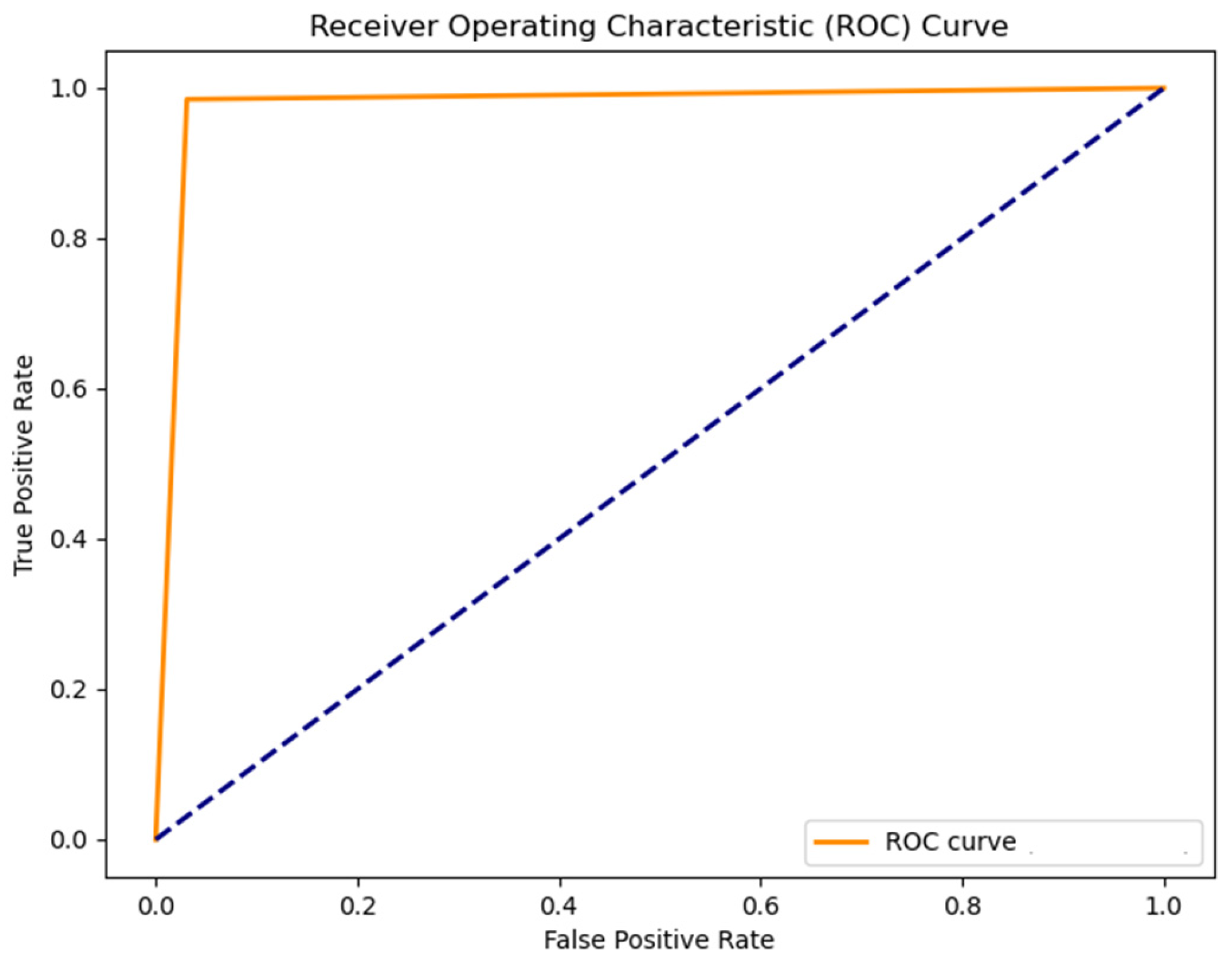
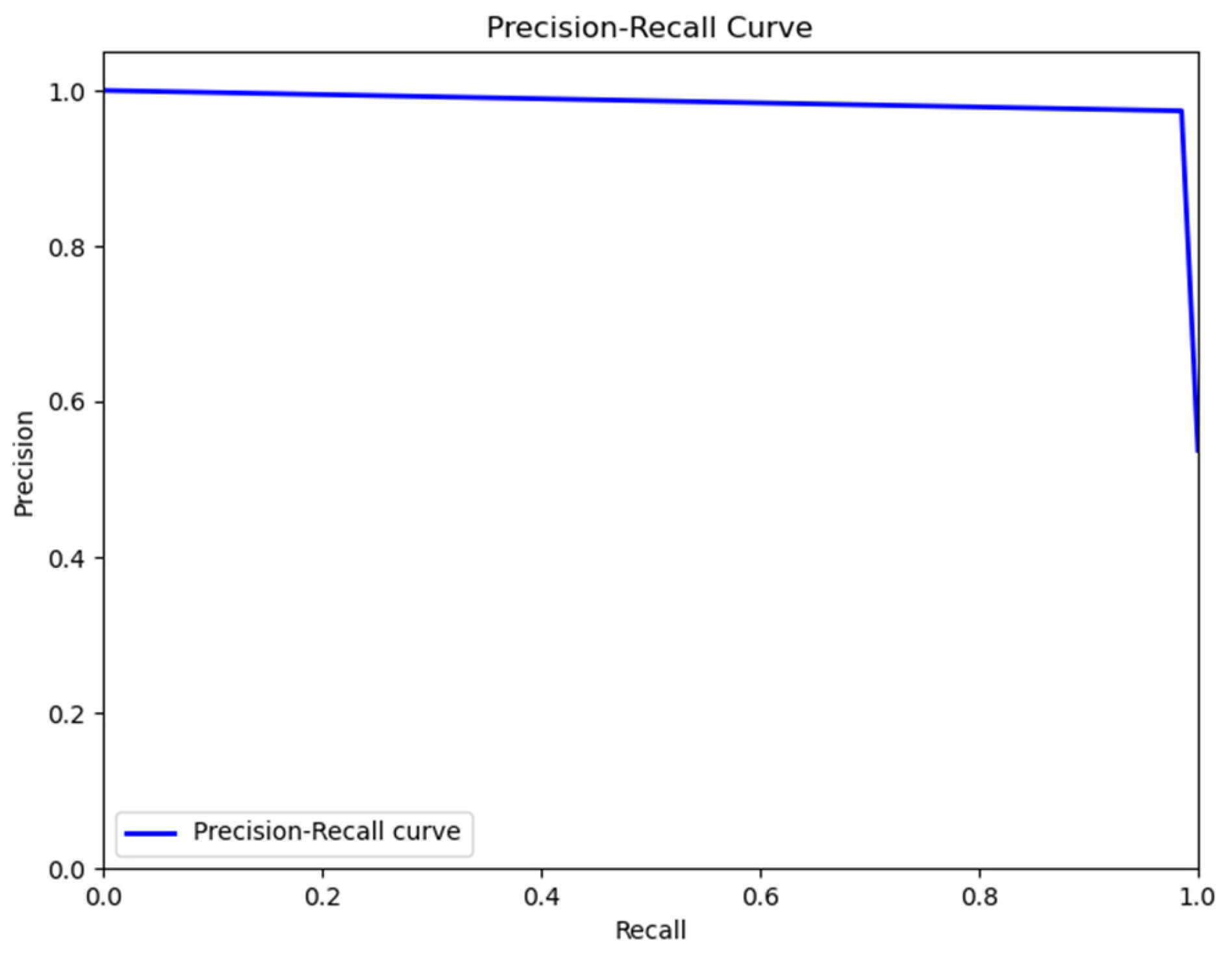
4. Results and Discussion
Discussion
5. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Perez, S.I.; Criado, R. Increasing the Effectiveness of Network Intrusion Detection Systems (NIDSs) by Using Multiplex Networks and Visibility Graphs. Mathematics 2022, 11, 107. [Google Scholar] [CrossRef]
- 100+ Network Security Statistics in 2025. AIMultiple. Available online: https://research.aimultiple.com/network-security-statistics/ (accessed on 23 May 2025).
- Infographic: Cybercrime Expected to Skyrocket in Coming Years. Statista Daily Data. Available online: https://www.statista.com/chart/28878/expected-cost-of-cybercrime-until-2027 (accessed on 23 May 2025).
- Mousavi, S.M.; St-Hilaire, M. Early detection of DDoS attacks against SDN controllers. In Proceedings of the 2015 International Conference on Computing, Networking and Communications (ICNC), Garden Grove, CA, USA, 16–19 February 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 77–81. [Google Scholar] [CrossRef]
- Dora, V.R.S.; Lakshmi, V.N. Optimal feature selection with CNN-feature learning for DDoS attack detection using meta-heuristic-based LSTM. Int. J. Intell. Robot. Appl. 2022, 6, 323–349. [Google Scholar] [CrossRef]
- Kuang, C. Research on Network Traffic Anomaly Detection Method Based on Deep Learning. J. Phys. Conf. Ser. 2021, 1861, 012007. [Google Scholar] [CrossRef]
- “2025 DDoS Attack Statistics: Alarming Prediction—VPNRanks Predicts 1 in 20 Internet Users Will Likely To Be Hit!”. Available online: https://www.vpnranks.com/resources/ddos-attack-statistics/ (accessed on 23 May 2025).
- “NSL-KDD|Datasets|Research|Canadian Institute for Cybersecurity|UNB.”. Available online: https://www.unb.ca/cic/datasets/nsl.html (accessed on 24 May 2025).
- Alshammari, A.; Aldribi, A. Apply machine learning techniques to detect malicious network traffic in cloud computing. J Big Data 2021, 8, 90. [Google Scholar] [CrossRef]
- Ahmad, Z.; Khan, A.S.; Shiang, C.W.; Abdullah, J.; Ahmad, F. Network intrusion detection system: A systematic study of machine learning and deep learning approaches. Trans. Emerg. Telecommun. Technol. 2021, 32, e4150. [Google Scholar] [CrossRef]
- Yost, J.R. The March of IDES: Early History of Intrusion-Detection Expert Systems. IEEE Annals Hist. Comput. 2016, 38, 42–54. [Google Scholar] [CrossRef]
- Dong, B.; Wang, X. Comparison deep learning method to traditional methods using for network intrusion detection. In Proceedings of the 2016 8th IEEE International Conference on Communication Software and Networks (ICCSN), Beijing, China, 4–6 June 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 581–585. [Google Scholar] [CrossRef]
- Hosseini, S.; Zade, B.M.H. New hybrid method for attack detection using combination of evolutionary algorithms, SVM, and ANN. Comput. Netw. 2020, 173, 107168. [Google Scholar] [CrossRef]
- Kurniabudi, K.; Purnama, B.; Sharipuddin, S.; Darmawijoyo, D.; Stiawan, D.; Samsuryadi, S.; Heryanto, A.; Budiarto, R. Network anomaly detection research: A survey. Indones. J. Electr. Eng. Inform. (IJEEI) 2019, 7, 37–50. [Google Scholar] [CrossRef]
- Wattanapongsakorn, N.; Srakaew, S.; Wonghirunsombat, E.; Sribavonmongkol, C.; Junhom, T.; Jongsubsook, P.; Charnsripinyo, C. A Practical Network-Based Intrusion Detection and Prevention System. In Proceedings of the 2012 IEEE 11th International Conference on Trust, Security and Privacy in Computing and Communications, Liverpool, UK, 25–27 June 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 209–214. [Google Scholar] [CrossRef]
- Kalinaki, K.; Thilakarathne, N.N.; Mubarak, H.R.; Malik, O.A.; Abdullatif, M. Cybersafe Capabilities and Utilities for Smart Cities. In Cybersecurity for Smart Cities. Advanced Sciences and Technologies for Security Applications; Ahmed, M., Haskell-Dowland, P., Eds.; Springer: Cham, Switzerland, 2023. [Google Scholar]
- Bakar, R.A.; Huang, X.; Javed, M.S.; Hussain, S.; Majeed, M.F. An Intelligent Agent-Based Detection System for DDoS Attacks Using Automatic Feature Extraction and Selection. Sensors 2023, 23, 3333. [Google Scholar] [CrossRef]
- Masum, M.; Shahriar, H.; Haddad, H.; Faruk, J.H.; Valero, M.; Khan, A.; Rahman, M.A.; Adnan, M.I.; Cuzzocrea, A.; Wu, F. Bayesian Hyperparameter Optimization for Deep Neural Network-Based Network Intrusion Detection. In Proceedings of the 2021 IEEE International Conference on Big Data (Big Data), Orlando, FL, USA, 15–18 December 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 5413–5419. [Google Scholar] [CrossRef]
- Thockchom, N.; Singh, M.M.; Nandi, U. A novel ensemble learning-based model for network intrusion detection. Complex. Intell. Syst. 2023, 9, 5693–5714. [Google Scholar] [CrossRef]
- Seth, S.; Chahal, K.K.; Singh, G. A Novel Ensemble Framework for an Intelligent Intrusion Detection System. IEEE Access 2021, 9, 138451–138467. [Google Scholar] [CrossRef]
- Verma, P.; Dumka, A.; Singh, R.; Ashok, A.; Gehlot, A.; Malik, P.K.; Gaba, G.S.; Hedabou, M. A Novel Intrusion Detection Approach Using Machine Learning Ensemble for IoT Environments. Appl. Sci. 2021, 11, 10268. [Google Scholar] [CrossRef]
- Yousefnezhad, M.; Hamidzadeh, J.; Aliannejadi, M. Ensemble classification for intrusion detection via feature extraction based on deep Learning. Soft Comput. 2021, 25, 12667–12683. [Google Scholar] [CrossRef]
- Shtayat, M.M.; Hasan, M.K.; Sulaiman, R.; Islam, S.; Khan, A.U.R. An Explainable Ensemble Deep Learning Approach for Intrusion Detection in Industrial Internet of Things. IEEE Access 2023, 11, 115047–115061. [Google Scholar] [CrossRef]
- Divakar, S.; Priyadarshini, R.; Mishra, B.K. A Robust Intrusion Detection System using Ensemble Machine Learning. In Proceedings of the 2020 IEEE International Women in Engineering (WIE) Conference on Electrical and Computer Engineering (WIECON-ECE), Bhubaneswar, India, 26–27 December 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 344–347. [Google Scholar] [CrossRef]
- Mohy-Eddine, M.; Guezzaz, A.; Benkirane, S.; Azrour, M.; Farhaoui, Y. An Ensemble Learning Based Intrusion Detection Model for Industrial IoT Security. Big Data Min. Anal. 2023, 6, 273–287. [Google Scholar] [CrossRef]
- Thakkar, A.; Lohiya, R. Attack Classification of Imbalanced Intrusion Data for IoT Network Using Ensemble-Learning-Based Deep Neural Network. IEEE Internet Things J. 2023, 10, 11888–11895. [Google Scholar] [CrossRef]
- Thilakarathne, N.N.; Bakar, M.S.A.; Abas, P.E.; Yassin, H. A novel cyber threat intelligence platform for evaluating the risk associated with smart agriculture. Sci. Rep. 2025, 15, 3904. [Google Scholar] [CrossRef]
- Kalaivani, D. An Intrusion Detection System Based on Data Analytics and Convolutional Neural Network in NSS-KDD dataset. In Machine Learning Algorithms for Intelligent Data Analytics; Technoarete Research and Development Association: Chennai, India, 2022. [Google Scholar] [CrossRef]
- Yedukondalu, G.; Bindu, G.H.; Pavan, J.; Venkatesh, G.; SaiTeja, A. Intrusion Detection System Framework Using Machine Learning. In Proceedings of the 2021 Third International Conference on Inventive Research in Computing Applications (ICIRCA), Coimbatore, India, 2–4 September 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1224–1230. [Google Scholar] [CrossRef]
- Alabdulatif, A.; Thilakarathne, N.N. A Novel Cloud-Enabled Cyber Threat Hunting Platform for Evaluating the Cyber Risks Associated with Smart Health Ecosystems. Appl. Sci. 2024, 14, 9567. [Google Scholar] [CrossRef]
- Nwakanma, C.I.; Ahakonye, L.A.C.; Njoku, J.N.; Odirichukwu, J.C.; Okolie, S.A.; Uzondu, C.; Nweke, C.C.N.; Kim, D.-S. Explainable Artificial Intelligence (XAI) for Intrusion Detection and Mitigation in Intelligent Connected Vehicles: A Review. Appl. Sci. 2023, 13, 1252. [Google Scholar] [CrossRef]
- Mahbooba, B.; Timilsina, M.; Sahal, R.; Serrano, M. Explainable Artificial Intelligence (XAI) to Enhance Trust Management in Intrusion Detection Systems Using Decision Tree Model. Complexity 2021, 2021, 6634811. [Google Scholar] [CrossRef]
- Hariharan, S.; Robinson, R.R.R.; Prasad, R.R.; Thomas, C.; Balakrishnan, N. XAI for intrusion detection system: Comparing explanations based on global and local scope. J. Comput. Virol. Hack. Tech. 2022, 19, 217–239. [Google Scholar] [CrossRef]
- Kim, A.; Park, M.; Lee, D.H. AI-IDS: Application of Deep Learning to Real-Time Web Intrusion Detection. IEEE Access 2020, 8, 70245–70261. [Google Scholar] [CrossRef]
- Viharika, S.; Balaji, N. AI-Driven Intrusion Detection Systems in Cloud Infrastructures: A Comprehensive Review of Hybrid Security Models and Future Directions. In Proceedings of the 2024 4th International Conference on Ubiquitous Computing and Intelligent Information Systems (ICUIS), Gobichettipalayam, India, 12–13 December 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 1201–1207. [Google Scholar] [CrossRef]
- Andronikidis, G.; Eleftheriadis, C.; Batzos, Z.; Kyranou, K.; Maropoulos, N.; Sargsyan, G.; Grammatikis, P.R.; Sarigiannidis, P. AI-Driven Anomaly and Intrusion Detection in Energy Systems: Current Trends and Future Direction. In Proceedings of the 2024 IEEE International Conference on Cyber Security and Resilience (CSR), London, UK, 2–4 September 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 777–782. [Google Scholar] [CrossRef]
- Ali, M.; Pervez, S.; Hosseini, S.E.; Siddu, M.K. Intelligent parameter-based in-network IDS for IoT using UNSW-NB15 and BoT-IoT datasets. J. Frankl. Inst. 2025, 362, 107440. [Google Scholar] [CrossRef]
- Ali, M.; Pervez, S.; Hosseini, S.E.; Siddhu, M.K. Evaluation and Detection of Cyberattack in IoT-Based Smart City Networks Using Machine Learning on the UNSW-NB15 Dataset.|EBSCOhost. Available online: https://openurl.ebsco.com/contentitem/doi:10.3991%2Fijoe.v21i02.52671?sid=ebsco:plink:crawler&id=ebsco:doi:10.3991%2Fijoe.v21i02.52671 (accessed on 28 June 2025).

| Reference | Composed of Real-Time Cloud Integration | Composed of XAI Integration | Key Contributions | Limitations of the Study |
|---|---|---|---|---|
| [5]/2022 | x | x | Proposes a deep learning-based DDoS detection model called CNN-O-LSTM, integrating CNNs and optimized LSTM. It uses Closest Position-based Grey Wolf Optimization (CP-GWO) for optimal feature selection, enhancing detection performance across five benchmark datasets by minimizing feature correlation and optimizing LSTM parameters for improved accuracy. | This approach lacks interpretability, live data integration, and human-readable outputs. It focuses solely on DDoS attacks, not covering broader threat types. No web interface or hybrid classifier architecture limits its transparency, generalizability, and operational usability in dynamic environments. |
| [6]/2021 | x | x | Proposes a dynamic adaptive CNN-based framework for detecting abnormal network traffic. Unlike traditional fixed pooling, the model uses dynamic adaptive pooling to enhance feature extraction. Experimental results demonstrate improved detection accuracy and lower loss compared to standard DL methods, highlighting its effectiveness in identifying evolving network attacks. | This method lacks model explainability, real-time deployment, and ensemble integration. It also focuses solely on CNNs, without leveraging complementary classifiers or hybrid strategies for broader threat detection and robustness in varying attack scenarios. |
| [9]/2021 | x | x | Proposes an ML-based intrusion detection framework trained on the ISOT-CID dataset to identify network traffic anomalies. It introduces a novel feature, based on the variability of packet payload length, to enhance model accuracy. The framework demonstrates improved detection performance by enriching the dataset with both flow-based and interval-based features. | Lacks model interpretability, dynamic inference capabilities, and support for diverse attack types. It does not integrate hybrid classifiers or explainable AI tools like SHAP, limiting its transparency, scalability, and adaptability to evolving threats in live environments. |
| [17]/2023 | x | x | Presents an intelligent agent-based system for detecting DDoS attacks using automatic feature extraction and selection. Leveraging the CICDDoS2019 dataset, the system combines ML with sequential feature selection to dynamically detect attacks, achieving 99.7% accuracy and outperforming existing ML-based DDoS detection methods in both speed and precision. | This agent-based DDoS detection system lacks real-time deployment, explainability, and ensemble model robustness. Furthermore, it does not demonstrate web-based visualization or SHAP-based interpretability, limiting transparency and adaptability in dynamic environments. |
| [18]/2021 | x | x | Proposes a Bayesian optimization framework for automatically tuning hyperparameters of deep neural networks (DNNs) used in network intrusion detection systems. Evaluated on the NSL-KDD dataset, the framework significantly outperforms random search methods in terms of accuracy, precision, recall, and F1-score, providing an efficient and scalable solution for optimizing DNN-based intrusion detection. | While this study improves DNN performance through hyperparameter tuning, it lacks explainability, real-time deployment, and multi-model ensemble integration. |
| [13]/2020 | x | x | Introduces a hybrid intrusion detection method named MGA-SVM-HGS-PSO-ANN. It uses a wrapper-based feature selection technique (MGA-SVM) and a neural network trained with a hybrid of gravitational search and particle swarm optimization. Using the NSL-KDD dataset, the model achieves 99.3% accuracy, reduces features from 42 to 4, and trains in 3 s. | This model lacks real-time deployment, explainable AI, and multi-threat handling. It focuses solely on offline analysis without a web interface or interpretability tools. |
| [19]/2023 | x | x | The study introduces an ensemble intrusion detection model using lightweight classifiers, Gaussian Naive Bayes, Logistic Regression, and Decision Tree, with Stochastic Gradient Descent as the meta-classifier. It employs Chi-square-based feature selection and demonstrates superior performance on KDD 1999, UNSW-NB15, and CIC-IDS2017 datasets for both binary and multiclass classifications. | The study lacks integration of deep learning or real-time detection capabilities and does not incorporate explainable AI. Unlike our study, it does not address live deployment or use hybrid ANN and SVM architecture with interpretability features like SHAP. |
| [20]/2021 | x | x | This study presents an ensemble intrusion detection framework that ranks base classifiers by F1-score for each attack category, selecting the most effective one per class instead of relying on traditional voting. This targeted ensemble approach achieves 96.97% accuracy and improves detection rates across diverse multi-attack classification environments. | The model is limited to static datasets and lacks real-time detection or adaptability. It also omits deep learning techniques and explainable AI integration, unlike our approach, which supports live traffic analysis and interpretable predictions using ANN, SVM, and SHAP-based explanations. |
| [21]/2021 | x | x | This study introduces a binary classification model for IoT intrusion detection using a Gradient Boosting Machine ensemble. The model is trained on preprocessed packet data to detect anomalies, particularly zero-day attacks. It achieves high performance with 98.27% accuracy, demonstrating its suitability for critical IoT applications. | The model is binary-only and tailored to static datasets, lacking support for multiclass attack detection, real-time operation, or interpretability. |
| [22]/2021 | x | x | This study proposes an ensemble-based intrusion detection system that integrates kNN, SVM, and Dempster–Shafer theory to manage uncertainty in classification. Deep learning is used for feature extraction, and ensemble margin-based sample selection improves training efficiency. The method outperforms existing models on UNSW-NB15, CICIDS2017, and NSL-KDD benchmark datasets. | The model lacks real-time detection capability and does not incorporate explainability features. Unlike our approach, it does not demonstrate live deployment or interpret model outputs using XAI, limiting transparency and real-world usability in critical network environments. |
| [23]/2023 | x | ✓ | This paper presents an explainable deep learning-based ensemble intrusion detection system for industrial IoT (IIoT) security. The model integrates SHAP and LIME to enhance decision transparency. Evaluated using the ToN_IoT dataset, the approach demonstrates improved detection performance and interpretability, aiding cybersecurity experts in developing resilient IIoT systems. | While explainability is addressed, the study lacks real-time deployment and practical implementation discussion. In contrast, our research offers live traffic integration and a hybrid ANN and SVM framework with SHAP, bridging performance and interpretability in operational environments. |
| [24]/2020 | x | x | This study proposes a boosting-powered ensemble method to identify the most efficient classifier for real-time network traffic analysis using the UNSW-NB15 dataset. By evaluating 10 classifiers, it selects XGBoost based on both accuracy and training time and demonstrates performance improvements on CPU vs. GPU environments for faster detection. | The study focuses on classifier selection and runtime optimization but lacks model explainability, hybrid learning, or live deployment integration. |
| [25]/2023 | x | x | This study introduces an intrusion detection system for industrial IoT (IIoT) by integrating Isolation Forest (IF) and Pearson Correlation Coefficient (PCC) for efficient feature selection and outlier removal. Using Random Forest as the classifier, the model achieves over 99% accuracy on Bot-IoT and NF-UNSW-NB15-v2 datasets with reduced prediction time. | Despite strong accuracy, the model lacks deep learning integration and explainable AI components. Unlike our study, it does not offer real-time detection or transparent reasoning for predictions, which limits its interpretability and applicability in high-stakes, adaptive cybersecurity environments. |
| [26]/2023 | x | x | This study presents a bagging ensemble framework using deep neural networks to address class imbalance in IoT intrusion detection. By integrating class weighting during training, the model achieves better generalization and balanced classification across four datasets (NSL-KDD, UNSW-NB15, CIC-IDS2017, BoT-IoT), evaluated using accuracy, F1-score, and statistical validation. | Although class imbalance is addressed, the study lacks real-time deployment and explainable AI integration. Our research provides live anomaly detection with interpretable outputs (via SHAP) and a hybrid ANN and SVM ensemble, offering greater transparency and operational relevance in security-critical environments. |
| Category | Description | Example Attack Types in the Dataset |
|---|---|---|
| DoS/DDoS | Overwhelms resources to make a system or network unavailable to legitimate users. | neptune, smurf, back, teardrop, pod, land |
| Probe | Attempts to gather information about the network or system for reconnaissance. | portsweep, ipsweep, nmap, satan |
| User to Root (U2R) | Attempts to gain root (admin) access from a normal user account. | buffer_overflow, loadmodule, perl, rootkit |
| Remote to Local (R2L) | Tries to gain unauthorized access to a local system from a remote location. | guess_passwd, ftp_write, imap, phf, warezclient, warezmaster, multihop, spy |
| Stage | Component | Layer | Output | Connected to |
|---|---|---|---|---|
| Input | Input Layer | Preprocessed and selected features (e.g., 20) | Feature vector | ANN Input, SVM Input |
| ANN block | Dense Layer 1 | 64 neurons, ReLU activation | Activation map | Dense Layer 2 |
| Dropout Layer | Dropout rate: 0.3 | Regularized activation | Dense Layer 2 | |
| Dense Layer 2 | 32 neurons, ReLU activation | Activation map | Dense Layer 3 | |
| Dropout Layer | Dropout rate: 0.2 | Regularized activation | Dense Layer 3 | |
| Dense Layer 3 | 16 neurons, ReLU activation | Activation map | Output Layer | |
| Output Layer | 1 neuron, Sigmoid activation | ANN prediction (probability) | RF Input | |
| SVM block | SVM | RBF kernel (or linear), C = 1.0 | SVM prediction (probability) | RF Input |
| Fusion | Meta Layer (Random Forest) | Input: ANN prob + SVM prob (2 features) | Final prediction (binary output) | Decision Interface |
| Explainability | SHAP/visualization layer | Feature importance for RF input | Explanation plots/rankings | User/Analyst Interface |
| Component | Specification |
|---|---|
| Processor (CPU) | Intent Core i5-72000 2.5 GHz |
| Graphics card (GPU) | NVIDIA GeForce 2 GB (NVIDIA, Santa Clara, CA, USA) |
| RAM | 16 GB DDR4 |
| Integrated development environment | Jupyter Notebook |
| Libraries used | TensorFlow, Scikit-learn, Pandas, Numpy etc. |
| Label | Precision (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|
| 0, Normal | 98 | 97 | 97 |
| 1, Anomaly | 98 | 99 | 97 |
| Label | Precision (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|
| 0, Normal | 95 | 94 | 93 |
| 1, Anomaly | 93 | 96 | 94 |
| Label | Precision (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|
| 0, Normal | 99 | 98 | 98 |
| 1, Anomaly | 99 | 99 | 98 |
| Rank | Feature | Mean SHAP Value | Description |
|---|---|---|---|
| 1 | src_bytes | 0.1423 | Bytes transferred from source to destination; indicates data volume sent by host. |
| 2 | dst_bytes | 0.1376 | Bytes transferred from destination to source; reflects server-side response. |
| 3 | count | 0.1198 | Number of connections to the same host within a 2 s window. |
| 4 | same_srv_rate | 0.1082 | Percentage of connections to the same service. |
| 5 | diff_srv_rate | 0.0974 | Rate of connections to different services; high values may indicate scanning. |
| 6 | protocol_type | 0.0921 | Protocol used (e.g., TCP, UDP); can hint at abnormal protocol usage. |
| 7 | flag | 0.0847 | TCP flag status; used to detect connection behavior. |
| 8 | dst_host_srv_count | 0.0763 | Connections to the same service on the destination host. |
| 9 | dst_host_same_srv_rate | 0.0689 | Rate of same service usage across connections to the destination host. |
| 10 | dst_host_diff_srv_rate | 0.0615 | Rate of different services across connections to destination host. |
| Reference | Dataset Employed | Algorithm/(s) Used | Achieved Accuracy (%) | Added Value |
|---|---|---|---|---|
| (Hosseini & Zade, 2020), [13] | NSL-KDD | Multi-parent genetic algorithm + SVM + ANN | 99.30 | Not applicable |
| (Masum et al., 2021), [18] | NSL-KDD | Deep neural network | 82.95 | Not applicable |
| (Dr. Kalaivani, 2022), [28] | NSL-KDD | Convolutional neural network | 92.23 | Not applicable |
| (Yedukondalu et al., 2021), [29] | NSL-KDD | ANN | 97.00 | Not applicable |
| Our study | NSL-KDD | XGBoost (Gradient Boosting) | 98.70 | Not applicable |
| Our study | NSL-KDD | AdaBoost (Adaptive Boosting) | 97.60 | Not applicable |
| Our study | NSL-KDD | Ensemble of ANN, SVM, and RF | 99.40 | Presents an ensemble of ANN, SVM, and RF with RFE-based feature selection, achieving 99.40% accuracy. Overall, it improves classification performance and robustness, offering a practical, scalable solution for real-world binary classification tasks across multiple domains. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alabdulatif, A. A Novel Ensemble of Deep Learning Approach for Cybersecurity Intrusion Detection with Explainable Artificial Intelligence. Appl. Sci. 2025, 15, 7984. https://doi.org/10.3390/app15147984
Alabdulatif A. A Novel Ensemble of Deep Learning Approach for Cybersecurity Intrusion Detection with Explainable Artificial Intelligence. Applied Sciences. 2025; 15(14):7984. https://doi.org/10.3390/app15147984
Chicago/Turabian StyleAlabdulatif, Abdullah. 2025. "A Novel Ensemble of Deep Learning Approach for Cybersecurity Intrusion Detection with Explainable Artificial Intelligence" Applied Sciences 15, no. 14: 7984. https://doi.org/10.3390/app15147984
APA StyleAlabdulatif, A. (2025). A Novel Ensemble of Deep Learning Approach for Cybersecurity Intrusion Detection with Explainable Artificial Intelligence. Applied Sciences, 15(14), 7984. https://doi.org/10.3390/app15147984






