Mathematical Modeling and Statistical Evaluation of the Security–Performance Trade-Off in IoT Cloud Architectures: A Case Study of UBT Smart City
Abstract
1. Introduction
Background and Related Work
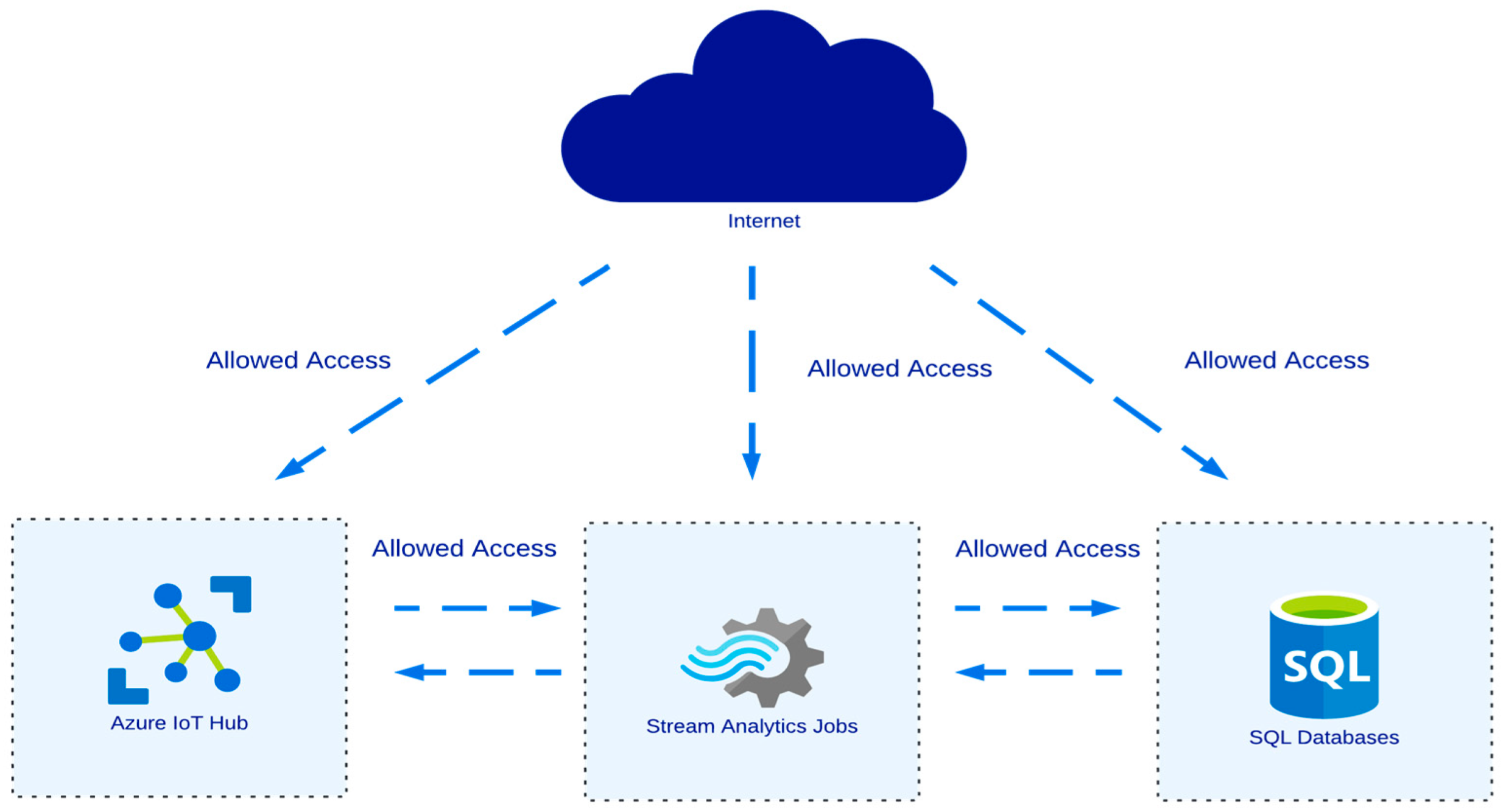
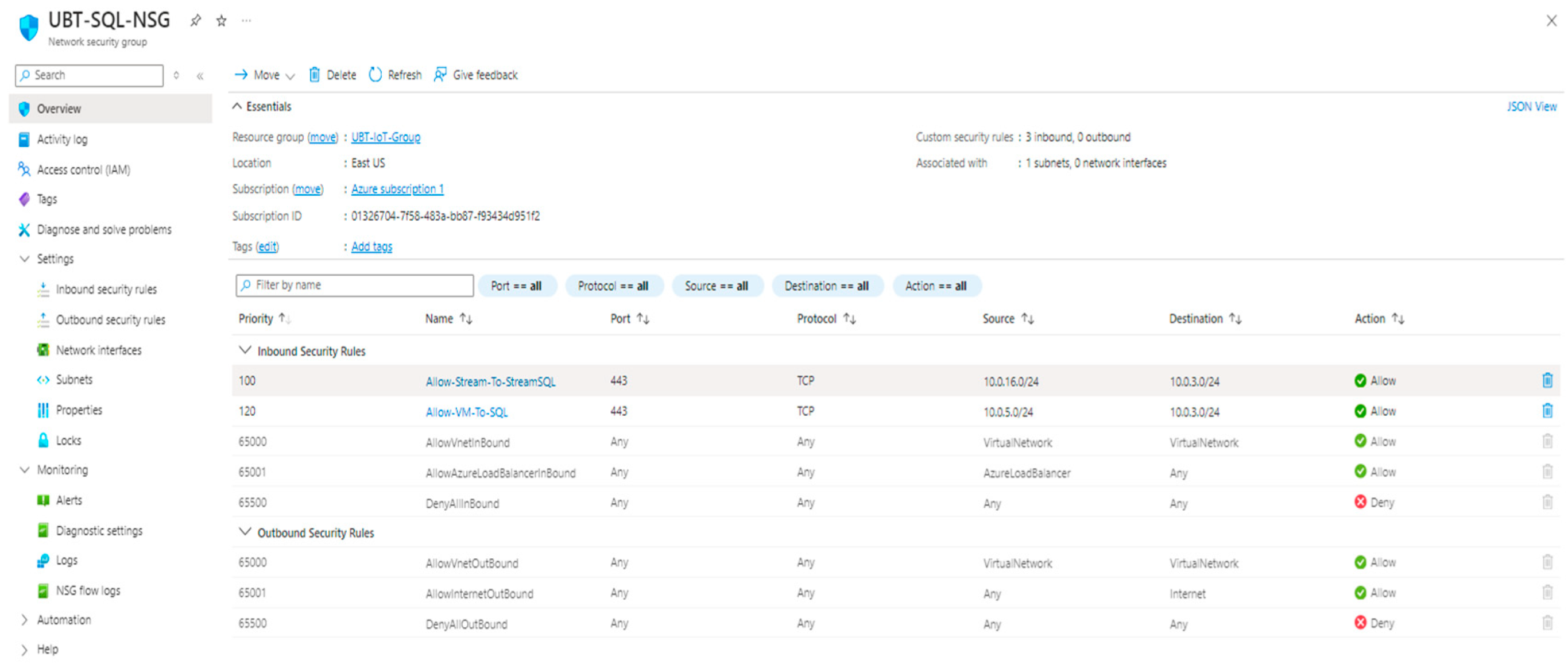
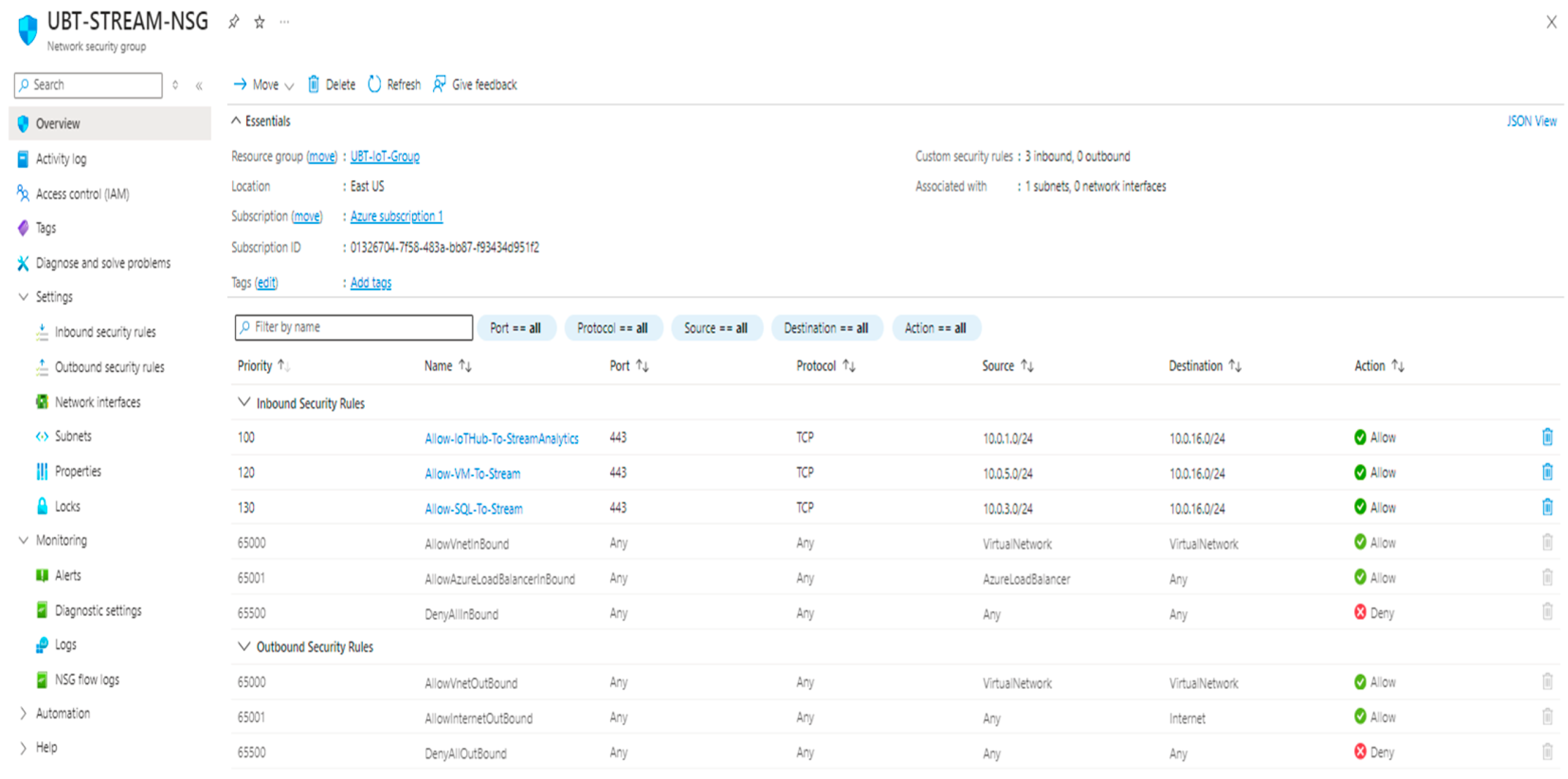
2. Materials and Methods
3. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Correction Statement
References
- Abdullayeva, F. Cyber resilience and cyber security issues of intelligent cloud computing systems. Results Control Optim. 2023, 12, 100268. [Google Scholar] [CrossRef]
- Albaijan, M.; Alyahya, F.; Alsubaie, M.; Bashar, A. Security and Performance Challenges, Solutions, and Future of Cloud-Based IoT Systems: A Brief Review. In Security and Performance Challenges, Solutions, and Future of Cloud-Based IoT Systems; Springer: Berlin/Heidelberg, Germany, 2024; pp. 1–21. [Google Scholar] [CrossRef]
- Azam, H.; Tajwar, A.M.; Mayhialagan, S.; Davis, A.J.; Yik, C.J.; Ali, D.; Sindiramutty, S.R. Innovations in Security: A Study of Cloud Computing and IoT. J. Emerg. Multidiscip. Comput. Sci. Artif. Intell. 2023, 2, 1–29. [Google Scholar] [CrossRef]
- Azure Services. Microsoft Azure Services Documentation. 2024. Available online: https://learn.microsoft.com/en-us/azure/networking/ (accessed on 5 May 2025).
- Borra, P. Impact and Innovations of Azure IoT: Current Applications, Services, and Future Directions. Int. J. Recent Technol. Eng. 2024, 13, 21–26. [Google Scholar] [CrossRef]
- Singh, N.; Buyya, R.; Kim, H. Securing Cloud-Based Internet of Things: Challenges and Mitigations. arXiv 2024, arXiv:2402.00356. [Google Scholar] [CrossRef] [PubMed]
- Bokefode, J.D.; Bhise, A.S.; Satarkar, P.A.; Modani, D.G. Developing A Secure Cloud Storage System for Storing IoT Data by Applying Role Based Encryption. Procedia Comput. Sci. 2016, 89, 43–50. [Google Scholar] [CrossRef]
- Westergren, U.H.; Mähler, V.; Jadaan, T. Enabling digital transformation: Organizational implementation of the internet of things. Inf. Manag. 2024, 61, 103996. [Google Scholar] [CrossRef]
- Brewster, C.; Roussaki, I.; Kalatzis, N.; Doolin, K.; Ellis, K.A. IoT in Agriculture: Designing a Europe-Wide Large-Scale Pilot. IEEE Commun. Mag. 2017, 55, 26–33. [Google Scholar] [CrossRef]
- Laghari, A.A.; Li, H.; Khan, A.A.; Shoulin, Y.; Karim, S.; Khani, M.A.K. Internet of Things (IoT) Applications: Security Trends and Challenges. Internet Things 2024, 4, 36. [Google Scholar] [CrossRef]
- Chen, Z.; Sivaparthipan, C.; Muthu, B. IoT based smart and intelligent smart city energy optimization. Sustain. Energy Technol. Assess. 2022, 49, 101724. [Google Scholar] [CrossRef]
- Kaneko, R.; Saito, T. Detection of Cookie Bomb Attacks in Cloud Computing Environment Monitored by SIEM. J. Adv. Inf. Technol. 2023, 14, 193–203. [Google Scholar] [CrossRef]
- Kashani, M.H.; Madanipour, M.; Nikravan, M.; Asghari, P.; Mahdipour, E. A systematic review of IoT in healthcare: Applications, techniques, and trends. J. Netw. Comput. Appl. 2021, 192, 103164. [Google Scholar] [CrossRef]
- Kumar, H.; Singh, M.K.; Gupta, M.; Madaan, J. Moving towards smart cities: Solutions that lead to the Smart City Transformation Framework. Technol. Forecast. Soc. Change 2020, 153, 119281. [Google Scholar] [CrossRef]
- Microsoft Azure. Azure Pricing. 2024. Available online: https://azure.microsoft.com/en-us/pricing#Pricing-by-product (accessed on 7 July 2024).
- Qureshi, M.B.; Qureshi, M.S.; Tahir, S.; Anwar, A.; Hussain, S.; Uddin, M.; Chen, C.-L. Encryption Techniques for Smart Systems Data Security Offloaded to the Cloud. Symmetry 2022, 14, 695. [Google Scholar] [CrossRef]
- Rahman, M.A.; Asyhari, A.T.; Leong, L.; Satrya, G.; Tao, M.H.; Zolkipli, M. Scalable machine learning-based intrusion detection system for IoT-enabled smart cities. Sustain. Cities Soc. 2020, 61, 102324. [Google Scholar] [CrossRef]
- UBT Smart City. (23 January 2022). UBT Smart City, UBT Innovation Ecosystem. Available online: https://www.ubt-uni.net/sq/ubt-smart-city-ubt-innovation-ecosystem-ubt-innovations/ (accessed on 9 July 2024).
- Wang, J.; Lim, M.K.; Wang, C.; Tseng, M.-L. The evolution of the Internet of Things (IoT) over the past 20 years. Comput. Ind. Eng. 2021, 155, 107174. [Google Scholar] [CrossRef]
- Williams, P.; Dutta, I.K.; Daoud, H.; Bayoumi, M. A survey on security in internet of things with a focus on the impact of emerging technologies. Internet Things 2022, 19, 100564. [Google Scholar] [CrossRef]
- Zhou, J.; Cao, Z.; Dong, X.; Vasilakos, A. Security and Privacy for Cloud-Based IoT: Challenges. IEEE Commun. Mag. 2017, 55, 26–33. [Google Scholar] [CrossRef]


| Postman to IoT Hub (seconds) | Event Received & Enqueued From IoT Hub to Stream Analytic | Event Processed in SQL Database | Total Delay (s) | Total Delay (ms) |
|---|---|---|---|---|
| 0.141 | 11:34:59.5600000 | 11:34:59.7522558 | 0.3332558 | 333.2558 |
| 0.140 | 11:35:37.2810000 | 11:35:37.3325194 | 0.1915194 | 191.5194 |
| 0.140 | 11:36:21.5620000 | 11:36:21.7218104 | 0.2998104 | 299.8104 |
| 0.140 | 11:36:49.2820000 | 11:36:49.3193850 | 0.1773850 | 177.3850 |
| 0.141 | 11:36:59.0000000 | 11:36:59.4567142 | 0.5977142 | 597.7142 |
| 0.141 | 11:37:01.0000000 | 11:37:01.4535031 | 0.5945031 | 594.5031 |
| 0.141 | 11:37:43.0000000 | 11:37:43.6309585 | 0.7719585 | 771.9585 |
| 0.141 | 11:37:50.0000000 | 11:37:50.5196650 | 0.6606650 | 660.6650 |
| 0.140 | 11:38:15.0000000 | 11:38:15.8199687 | 0.9599687 | 959.9687 |
| 0.141 | 11:38:43.0000000 | 11:38:43.5339984 | 0.6749984 | 674.9984 |
| 0.141 | 11:39:11.0000000 | 11:39:11.7082835 | 0.8492835 | 849.2835 |
| 0.141 | 11:39:35.0000000 | 11:39:35.5139984 | 0.6549984 | 654.9984 |
| 0.141 | 11:39:49.0000000 | 11:39:49.6918658 | 0.8328658 | 832.8658 |
| 0.141 | 11:39:59.0000000 | 11:39:59.6926158 | 0.8336158 | 833.6158 |
| 0.141 | 11:39:28.0000000 | 11:39:28.7982800 | 0.9392800 | 939.2800 |
| 0.141 | 11:39:49.0000000 | 11:39:49.5055097 | 0.6465097 | 646.5097 |
| Average Delay | 626.1457 |
| Postman to IoT Hub (seconds) | Event Received & Enqueued From IoT Hub to Stream Analytic | Event Processed in SQL Database | Total Delay (s) | Total Delay (ms) |
|---|---|---|---|---|
| 0.581 | 10:04:09.6070000 | 10:04:09.8347807 | 0.8087807 | 808.7807 |
| 0.510 | 10:04:11.2320000 | 10:04:12.4144696 | 1.6924696 | 1692.4696 |
| 0.564 | 10:04:12.3110000 | 10:04:12.4160150 | 0.6690150 | 669.0150 |
| 0.57 | 10:04:13.2480000 | 10:04:13.3988495 | 0.7208495 | 720.8495 |
| 0.546 | 10:04:14.1540000 | 10:04:14.2737461 | 0.6657461 | 665.7461 |
| 0.554 | 10:04:25.3420000 | 10:04:25.5392885 | 0.7512885 | 751.2885 |
| 0.531 | 10:04:29.3580000 | 10:04:29.4769821 | 0.6499821 | 649.9821 |
| 0.536 | 10:04:31.0300000 | 10:04:31.2268609 | 0.7328609 | 732.8609 |
| 0.576 | 10:05:22.1090000 | 10:05:22.1033898 | 0.5703898 | 570.3898 |
| 0.548 | 10:05:25.2500000 | 10:05:25.3832814 | 0.6812814 | 681.2814 |
| 0.544 | 10:05:26.4380000 | 10:05:26.4774513 | 0.5834513 | 583.4513 |
| 0.544 | 10:05:27.5940000 | 10:05:27.6801260 | 0.6301260 | 630.1260 |
| 0.548 | 10:05:29.2970000 | 10:05:29.4301508 | 0.6811508 | 681.1508 |
| 0.521 | 10:05:30.5940000 | 10:05:30.7422885 | 0.6692885 | 669.2885 |
| 0.502 | 10:05:31.5630000 | 10:05:31.7270345 | 0.6660345 | 666.0345 |
| 0.534 | 09:01:40.6520000 | 09:01:40.8793610 | 0.7613610 | 761.3610 |
| Average Delay | 745.8797 |
| Component | Light Use | Medium Use | High Use |
|---|---|---|---|
| VPN Gateway (Basic Tier) | €65 | €90 | €120 |
| DDoS Protection Standard | €250 | €250 | €250 |
| Network Security Groups | €0 | €0 | €0 |
| Data Egress (10–50 GB) | €5 | €15 | €30 |
| Total Estimated Cost | €320 | €355 | €400 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Qehaja, B.; Hajrizi, E.; Haxhismajli, B.; Menxhiqi, L.; Marinova, G.; Mollakuqe, E. Mathematical Modeling and Statistical Evaluation of the Security–Performance Trade-Off in IoT Cloud Architectures: A Case Study of UBT Smart City. Appl. Sci. 2025, 15, 7518. https://doi.org/10.3390/app15137518
Qehaja B, Hajrizi E, Haxhismajli B, Menxhiqi L, Marinova G, Mollakuqe E. Mathematical Modeling and Statistical Evaluation of the Security–Performance Trade-Off in IoT Cloud Architectures: A Case Study of UBT Smart City. Applied Sciences. 2025; 15(13):7518. https://doi.org/10.3390/app15137518
Chicago/Turabian StyleQehaja, Besnik, Edmond Hajrizi, Behar Haxhismajli, Lavdim Menxhiqi, Galia Marinova, and Elissa Mollakuqe. 2025. "Mathematical Modeling and Statistical Evaluation of the Security–Performance Trade-Off in IoT Cloud Architectures: A Case Study of UBT Smart City" Applied Sciences 15, no. 13: 7518. https://doi.org/10.3390/app15137518
APA StyleQehaja, B., Hajrizi, E., Haxhismajli, B., Menxhiqi, L., Marinova, G., & Mollakuqe, E. (2025). Mathematical Modeling and Statistical Evaluation of the Security–Performance Trade-Off in IoT Cloud Architectures: A Case Study of UBT Smart City. Applied Sciences, 15(13), 7518. https://doi.org/10.3390/app15137518







