An Improved GN-AK Protocol Using Double-Base Scalar Multiplication and Point Halving over Elliptic Curves
Abstract
1. Introduction
2. Background and Related Work
3. Mathematical Foundations of ECC Scalar Multiplication
- Double-and-add algorithm: A binary method where the scalar k is represented in base-2, and at each bit, the current point is doubled and conditionally added to an accumulator.
- Non-Adjacent Form (NAF): A signed-digit representation of k that minimizes the Hamming weight, thereby reducing the number of additions.
- Windowed methods: These include fixed-base comb, sliding window, and w-NAF methods that precompute powers of P for faster computation.
- Montgomery ladder: A side-channel-resistant method where each iteration performs both addition and doubling.
- Joint Sparse Form (JSF): Optimized for simultaneous multiple scalar multiplications.
4. Double-Base Chains with Point Halving: Theory and Algorithms
Point Halving Algorithm
- Compute the DBC representation of the scalar k: a sequence of signed terms .
- Initialize the result (the point at infinity).
- Initialize a working point .
- For each term in the DBC sequence (from most to least significant):
- Apply successive tripling operations to Q.
- Apply successive point halvings to Q.
- If , set .
- Add Q to the result: .
- Return R as the final result .
- Fewer overall elliptic curve operations.
- Substantial reduction in field inversions and multiplications.
- Improved side-channel resistance due to less predictability in operation patterns.
5. Review of the Original GN-AK Protocol
- Mutual authentication: Both T and R must confirm each other’s identities.
- Key agreement: The protocol must result in both parties computing the same session key K.
- Session freshness: Each session should be based on pseudorandom values to ensure forward secrecy.
- Resistance to impersonation and replay attacks: The protocol must use cryptographic techniques that prevent adversaries from masquerading as legitimate participants.
- : An elliptic curve defined over a finite field.
- : Publicly agreed curve points.
- , : Secret and public key pair of T.
- , : Secret and public key pair of R.
- , : pseudorandom session-specific scalars generated by T and R.
- : A cryptographic hash function (e.g., SHA-1).
- , : Asymmetric encryption and decryption.
5.1. Protocol Steps
- Generate a random pseudorandom scalar .
- Compute .
- Compute hash .
- Compute digital signature or encryption .
- Send to R.
- Compute .
- Verify authenticity by checking .
- If valid, generate pseudorandom scalar .
- Compute .
- Compute .
- Compute .
- Compute session key .
- Send to T.
- Compute .
- Verify .
- If valid, compute session key .
5.2. Security Properties
- Known-key security: Each session key is derived from pseudorandom values, ensuring compromise of one session does not affect others.
- Forward secrecy: Even if long-term keys are exposed, past session keys remain secure.
- Key confirmation: Optional third step confirms that both parties agree on the session key.
- Impersonation resistance: Encrypted hashes act as challenge-response values binding session keys to identities.
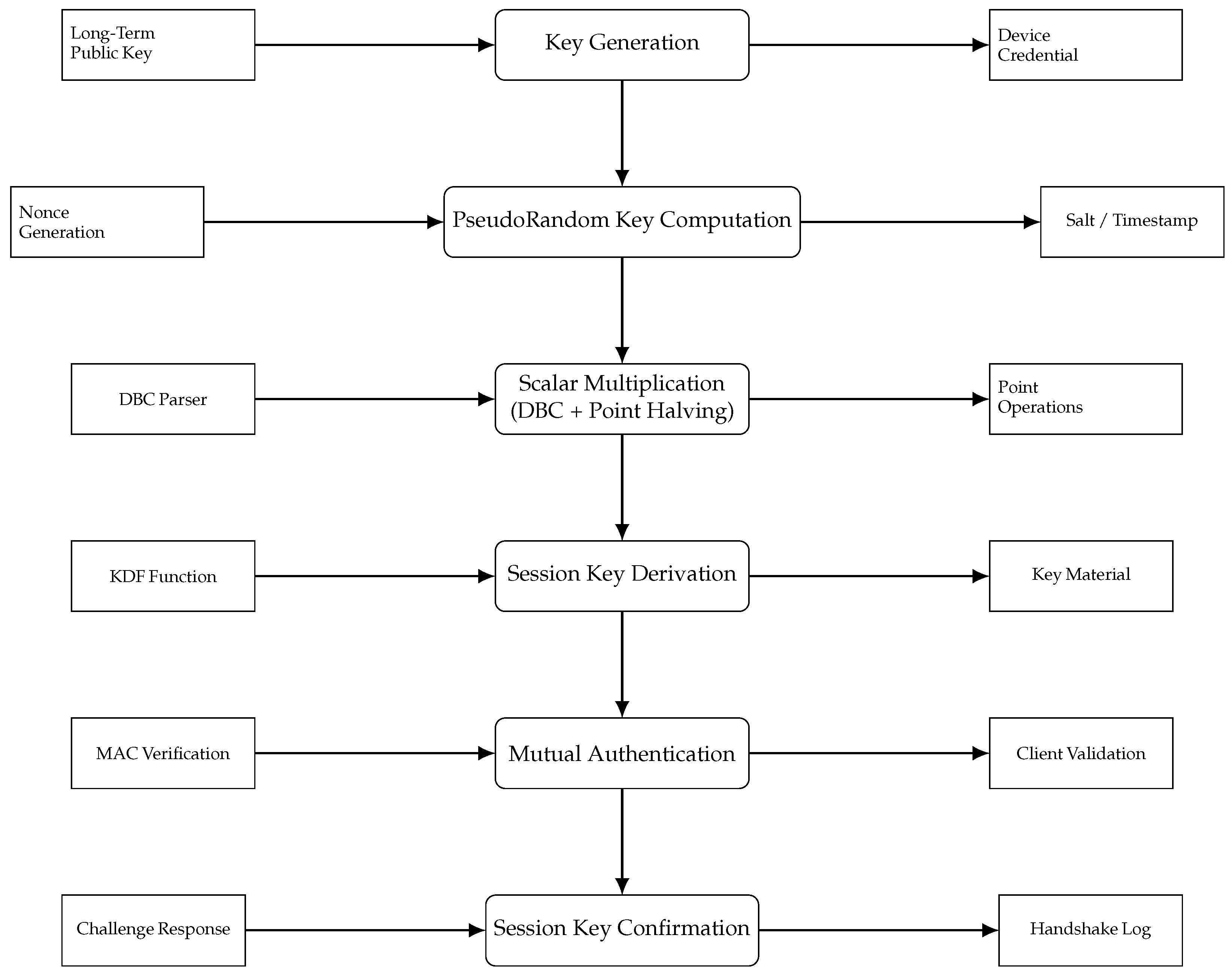
6. Refined Authenticated Key Exchange Protocol with Point Halving Optimization
6.1. Design Objectives and Parameter Initialization
- : private/public key pair of initiator ;
- : private/public key pair of responder ;
- : a cryptographic hash function (e.g., SHA-256);
- : asymmetric encryption function under private key;
- : corresponding decryption function.
6.2. Revised Protocol Steps
- Step 1—Initiator (Request Generation):
- Generate a session-specific random scalar and compute its DBC representation using bases and 3:
- Compute pseudorandom public component: using point halving and tripling.
- Derive authentication hash: .
- Generate commitment: .
- Transmit the pair to .
- Step 2—Responder (Response Computation and Verification):
- Recompute hash: .
- Verify authenticity: .
- Generate independent scalar and derive its DBC representation.
- Compute response point: via DBC-based scalar multiplication.
- Compute confirmation hash: .
- Encrypt confirmation: .
- Derive session key: .
- Send to .
- Step 3—Initiator (Final Verification and Key Derivation):
- Recompute .
- Verify: .
- Derive session key: .
6.3. Session Key Equivalence and Properties
7. Security Analysis and Cryptographic Guarantees
7.1. Cryptographic Assumptions
- Elliptic Curve Discrete Logarithm Problem (ECDLP): Given a point on an elliptic curve , it is computationally infeasible to recover the scalar for appropriately chosen P and curve parameters.
- Collision Resistance of the Hash Function: The function behaves as a random oracle and is resistant to collision and preimage attacks.
- IND-CPA Security of Asymmetric Encryption: The encryption function is semantically secure against chosen plaintext attacks.
7.2. Mutual Authentication Guarantees
- The initiator proves possession of by transmitting
- The responder authenticates using
7.2.1. Session Key Confidentiality
7.2.2. Key Compromise Impersonation Vs. Forward Secrecy
7.2.3. Forward Secrecy
7.2.4. Resistance to Replay and Impersonation Attacks
7.2.5. Key Compromise Impersonation (KCI) Resilience
7.2.6. Side-Channel Resistance Considerations
7.3. Formal Security Proof in the Canetti-Krawczyk Model
Security Model
- Send: Deliver arbitrary messages to protocol instances.
- Reveal: Obtain session keys from completed sessions.
- Corrupt: Reveal long-term keys of a party.
- Test: Challenge a session with a random key or the real session key.
- The ECDLP over E is hard;
- The hash function is modeled as a random oracle;
- The encryption scheme is IND-CPA secure.
- Then, the refined GN-AK protocol using double-base scalar multiplication and point halving is AKE-secure in the CK model.
- Security Scenario 0: —Real Execution of the Protocol
- The hash function is treated as a standard deterministic function;
- The encryption function is evaluated using the real asymmetric encryption scheme;
- Session keys are derived aswhere are independently and uniformly sampled ephemeral scalars, and is the fixed public base point.
- Send: deliver messages to protocol participants and receive their outputs;
- Reveal: obtain the session key of a completed session;
- Corrupt: learn the long-term private key of a party;
- Test: challenge a session with either the real session key or a uniformly random value.
- Neither the session nor its partner has been subjected to a Reveal query;
- The long-term private key of the owner has not been revealed via Corrupt.
- Security Scenario 1: —Replacement of the Hash Function with a Random Oracle
- On input , if x has not been queried before, sample uniformly at random and store in a global table.
- If x was queried previously, return the same y as before.
- Security Scenario 2 —Simulation of Ciphertexts
- Security Scenario 3: —Session Key Replaced with Random
- Transition from to replaces the hash function with a random oracle. An adversary capable of distinguishing this transformation contradicts the assumption that H behaves as an ideal random oracle. Let the distinguishing advantage be denoted .
- Transition from to replaces ciphertexts and with random values. An adversary who detects this change can be used to build an IND-CPA distinguisher for the encryption scheme . Let the corresponding advantage be .
- Transition from to replaces the real session key with a uniformly random key. Any non-negligible distinguishing advantage in this step implies that the adversary has obtained information about from and without knowledge of the ephemeral scalars, violating the hardness of the ECDLP. Let this advantage be denoted .
- , due to the random oracle assumption on H;
- , from the IND-CPA security of ;
- , by the hardness of the ECDLP;
- remains as is, by definition.
8. Implementation and Performance Evaluation
- ATmega328P: 8-bit AVR microcontroller, 16 MHz clock, compiled with avr-gcc 11.1.0 using size and speed optimizations.
- STM32F411RE: 32-bit ARM Cortex-M4 microcontroller, 100 MHz clock, compiled with ARM-GCC 10.3 and hardware floating-point support disabled.
8.1. Implementation Notes and Challenges
- Take as input the point such that .
- Compute the slope as .
- Derive the x-coordinate of P as .
- Compute the y-coordinate as .
- Return the point .
8.2. Implementation Considerations
- NIST B-163, B-233, B-283 (binary fields).
- Koblitz curves, which further optimize arithmetic.
- 8-bit microcontrollers: Reduction in field inversions translates directly to less CPU usage.
- IoT devices: Battery-powered nodes benefit from energy-efficient ECC operations.
- Smart cards: Limited RAM and ROM favor arithmetic simplifications.
- Extend the scalar multiplication function to parse and apply DBC representation.
- Implement field-specific point halving routines.
- Ensure constant-time execution to resist timing attacks.
- Use of constant-time conditional logic for DBC traversal.
- Randomized representation of scalars to prevent pattern leakage.
- Disabling hardware acceleration (e.g., DMA) if it introduces timing side-channels.
- Binding public keys to X.509 certificates.
- Managing key lifetimes and session expiration securely.
- Supporting revocation and rotation of long-term keys.
8.2.1. Side-Channel Threat Model
8.2.2. Architectural Motivation for Combining DBSM and Point Halving in GN-AK
8.3. Comparative Analysis with Other Protocols
8.3.1. Security Comparison
- F. Secrecy—Forward Secrecy: Compromise of long-term keys does not compromise past session keys.
- KCI-Resist.—Key Compromise Impersonation Resistance: The protocol resists impersonation attacks even when a user’s private key is compromised.
- PFS—Perfect Forward Secrecy: session keys remain secure even if long-term keys are later compromised.
- Mutual Auth.—Mutual Authentication: both entities verify each other’s identity during the protocol.
8.3.2. Performance Comparison
8.3.3. Suitability for Constrained Devices
- Smart cards (e.g., EMV chips)
- Sensor nodes (e.g., Zigbee, Bluetooth LE)
- RFID tags and embedded authentication modules
9. Discussion and Future Work
10. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Stephanides, G.; Constantinescu, N. The GN-authenticated key agreement. Appl. Math. Comput. 2005, 170, 531–544. [Google Scholar] [CrossRef]
- Duica, L.; Antonescu, E.; Silisteanu, S.C. Contribution of mechanical and electrical cardiovascular factors in patients with ischemic stroke. Pak. J. Pharm. Sci. 2020, 33, 2455–2460. [Google Scholar]
- Silisteanu, S.C.; Antonescu, E.; Duica, L. The importance of balance and postural control in the recovery of stroke patients. Balneo Res. J. 2020, 11, 372–378. [Google Scholar] [CrossRef]
- Duțescu, M.M.; Popescu, R.E.; Pirlog, M.C. Social Functioning in Schizophrenia Clinical Correlations. Curr. Health Sci. J. 2018, 44, 151–156. [Google Scholar] [PubMed]
- Silisteanu, S.C.; Antonescu, E.; Duica, L. Strategies for the recovery of patients with post stroke sequelae in the context of the COVID-19 pandemic. Balneo Res. J. 2020, 11, 507–511. [Google Scholar] [CrossRef]
- Ding, Y.; Hong, Y.F.; Gui, F.; Zheng, Z.X. An Efficient Algorithm for Elliptic Curve Scalar Multiplication Using Extended Double-Base Chain and Point Halving. J. Internet Technol. 2011, 12, 593–599. [Google Scholar]
- Almajed, H.N.; Almogren, A.S.; Altameem, A. A resilient smart body sensor network through pyramid interconnection. IEEE Access 2019, 7, 51039–51046. [Google Scholar] [CrossRef]
- Tyagi, M.; Manoria, M.; Mishra, B. A framework for data storage security with efficient computing in cloud. In Proceedings of the International Conference on Advanced Computing Networking and Informatics; Springer: Singapore, 2019; pp. 109–116. [Google Scholar]
- Azouaoui, M.; Durvaux, F.; Poussier, R.; Standaert, F.X.; Papagiannopoulos, K.; Verneuil, V. On the worst-case side-channel security of ECC point randomization in embedded devices. In Proceedings of the INDOCRYPT 2020; Bhargavan, K., Oswald, E., Prabhakaran, M., Eds.; Springer: Heidelberg, Germany, 2020; Volume 12578, pp. 205–227. [Google Scholar]
- Huawei Edge Networking. Huawei Community Forums. 2023. Available online: https://forum.huawei.com/enterprise/en/edge-networking/thread/690495115774279680-667213860102352896 (accessed on 10 February 2024).
- He, D.; Zeadally, S. An Analysis of RFID Authentication Schemes for Internet of things in Healthcare Environment Using Elliptic Curve Cryptography. IEEE Internet Things J. 2015, 2, 72–83. [Google Scholar] [CrossRef]
- Ahmed, A.A.; Ahmed, W.A. An effective multifactor authentication mechanism for health care data. J. Netw. Commun. Syst. 2019, 2, 10–19. [Google Scholar]
- Ali, R.; Pal, A.K. An efficient three factor—Based authentication scheme in multi-server environment using ECC. Int. J. Commun. Syst. 2017, 31, 1–22. [Google Scholar]
- Aazam, M.; St-Hilaire, M.; Lung, C.H.; Lambadaris, I. PRE-Fog: IoT trace based probabilistic resource estimation at Fog. In Proceedings of the 13th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2016. [Google Scholar]
- Arenas, M.P.; Fotiadis, G.; Lenzini, G.; Rakeei, M. Remote Secure Object Authentication: Secure Sketches, Fuzzy Extractors, and Security Protocols. Comput. Secur. 2025, 148, 104–131. [Google Scholar] [CrossRef]
- Javadi, A.; Sadeghi, S.; Pahlevani, P.; Bagheri, N.; Rostampour, S.; Bendavid, Y. Secure and Efficient Lightweight Authentication Protocol (SELAP) for Multi-Sector IoT Applications. Internet Things 2025, 30, 101499. [Google Scholar] [CrossRef]
- Xu, L.; Wu, F. An improved and provable remote user authentication scheme based on elliptic curve cryptosystem with user anonymity. Secur. Commun. Netw. 2015, 8, 245–260. [Google Scholar] [CrossRef]
- Chen, C. NTRU-Algorithm Specifications and Supporting Documentation (Round 3 Submission); Technical Report; 2020. [Google Scholar]
- Rodríguez-Muñoz, J.D.; Tlelo-Cuautle, E.; De La Fraga, L.G. Chaos-Based Authentication of Encrypted Images under MQTT for IoT Protocol. Integration 2025, 102, 102378. [Google Scholar] [CrossRef]
- Yalli, J.S.; Hasan, M.H.; Jung, L.T.; Al-Selwi, S.M. Authentication Schemes for Internet of Things (IoT) Networks: A Systematic Review and Security Assessment. Internet Things 2025, 30. [Google Scholar] [CrossRef]
- Miranda, C.; Kaddoum, G.; Bou-Harb, E.; Garg, S.; Kaur, K. A collaborative security framework for software-defined wireless sensor networks. IEEE Trans. Inf. Forensics Secur. 2020, 15, 2602–2615. [Google Scholar] [CrossRef]
- Bos, J. CRYSTALS - Kyber: A CCA-Secure Module-Lattice-Based KEM. In Proceedings of the 2018 IEEE European Symposium on Security and Privacy (EuroS&P), London, UK, 24–26 April 2018; pp. 353–367. [Google Scholar]
- Pakniat, N.; Shiraly, D.; Eslami, Z. Certificateless authenticated encryption with keyword search: Enhanced security model and a concrete construction for industrial IoT. J. Inf. Secur. Appl. 2020, 53, 102525. [Google Scholar] [CrossRef]
- Kanda, G.; Antwi, A.O.; Ryoo, K. Hardware architecture design of aes cryptosystem with 163-bit elliptic curve. In Advanced Multimedia and Ubiquitous Engineering; Springer: Singapore, 2018; pp. 423–429. [Google Scholar]
- Yunakovsky, S.E. Towards security recommendations for public-key infrastructures for production environments in the post-quantum era. EPJ Quantum Technol. 2021, 8, 14. [Google Scholar] [CrossRef]
- Raavi, M. Performance characterization of post-quantum digital certificates. In Proceedings of the 2021 International Conference on Computer Communications and Networks (ICCCN), Athens, Greece, 19–22 July 2021. [Google Scholar]
- Wong, K.W.; Lee, E.C.W.; Cheng, L.M.; Liao, X. Fast Elliptic Scalar Multiplication using New Double-base Chain and Point Halving. Appl. Math. Comput. 2006, 183, 1000–1007. [Google Scholar] [CrossRef]
- Garrett, K.; Talluri, S.; Roy, S. On vulnerability analysis of several password authentication protocols. Innov. Syst. Softw. Eng. 2015, 11, 167–176. [Google Scholar] [CrossRef]
- Grover, H.; Kumar, D. Cryptanalysis and improvement of a three factor user authentication scheme for smart grid environment. J. Reliab. Intell. Environ. 2020, 6, 249–260. [Google Scholar] [CrossRef]
- Kim, Y.; Hakak, S.; Ghorbani, A. Detecting Distributed Denial-of-Service (DDoS) Attacks That Generate False Authentications on Electric Vehicle (EV) Charging Infrastructure. Comput. Secur. 2024, 144, 103989. [Google Scholar] [CrossRef]
- Yang, Z.; Kong, J. Cue-Based Two Factor Authentication. Comput. Secur. 2024, 146, 104068. [Google Scholar] [CrossRef]
- Yue, X.; Yang, P.; Si, H.; Yang, H.; Zhou, F.; Wang, Q.; Yang, Z.; Bai, S.; He, Y. A2SHE: An Anonymous Authentication Scheme for Health Emergencies in Public Venues. Inform. Sci. 2025, 703, 121944. [Google Scholar] [CrossRef]
- Krawczyk, H. HMQV: A High-Performance Secure Diffie-Hellman Protocol. In Proceedings of the CRYPTO 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 546–566. [Google Scholar]
- SEC 1: Elliptic Curve Cryptography; Technical Report, Certicom Research; Standards for Efficient Cryptography; 2000.
- LaMacchia, B.; Lauter, K.; Mityagin, A. Stronger Security of Authenticated Key Exchange. In Proceedings of the ProvSec 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 1–16. [Google Scholar]
| Platform | Original GN-AK | Improved GN-AK |
|---|---|---|
| ATmega328P | 8523 | 6411 |
| STM32F411RE | 2181 | 1653 |
| Platform | Original GN-AK | Improved GN-AK |
|---|---|---|
| ATmega328P | 34.1 | 25.6 |
| STM32F411RE | 19.6 | 14.2 |
| Protocol | Auth. | F. Secrecy | KCI-Resist. | K-Confirm |
|---|---|---|---|---|
| GN-AK (orig.) | Yes | Yes | Partial | Optional |
| Enhanced GN-AK | Yes | Yes | Yes | Optional |
| HMQV | Yes | No | Partial | No |
| ECKAS-DH1 | Yes | Yes | No | No |
| NAXOS | Yes | Yes | Yes | No |
| Protocol | Mult. | Invers. | Add./Half. |
|---|---|---|---|
| GN-AK (orig.) | 300+ | 15 | 80/0 |
| Enhanced GN-AK | 215 | 7 | 35/55 |
| HMQV | 240+ | 14 | 70/0 |
| ECKAS-DH1 | 280 | 12 | 65/0 |
| NAXOS | 250 | 10 | 50/0 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Constantinescu, N.; Hunyadi, I.D.; Ticleanu, O.-A. An Improved GN-AK Protocol Using Double-Base Scalar Multiplication and Point Halving over Elliptic Curves. Appl. Sci. 2025, 15, 7492. https://doi.org/10.3390/app15137492
Constantinescu N, Hunyadi ID, Ticleanu O-A. An Improved GN-AK Protocol Using Double-Base Scalar Multiplication and Point Halving over Elliptic Curves. Applied Sciences. 2025; 15(13):7492. https://doi.org/10.3390/app15137492
Chicago/Turabian StyleConstantinescu, Nicolae, Ioan Daniel Hunyadi, and Oana-Adriana Ticleanu. 2025. "An Improved GN-AK Protocol Using Double-Base Scalar Multiplication and Point Halving over Elliptic Curves" Applied Sciences 15, no. 13: 7492. https://doi.org/10.3390/app15137492
APA StyleConstantinescu, N., Hunyadi, I. D., & Ticleanu, O.-A. (2025). An Improved GN-AK Protocol Using Double-Base Scalar Multiplication and Point Halving over Elliptic Curves. Applied Sciences, 15(13), 7492. https://doi.org/10.3390/app15137492







