Formal Analysis of Ratchet Protocols Based on Logic of Events
Abstract
1. Introduction
- A formal analysis framework for ratchet protocols based on LoET. We extend the LoET event class system by introducing DH (Diffie–Hellman) and ratchet event classes and by developing dedicated axioms and inference rules tailored to the characteristics of ratchet protocols. This framework addresses the limitations of conventional formal methods in accurately modeling ratchet-based encryption mechanisms.
- Construction of a bidirectional authentication formal model for the Signal protocol. To capture the dynamic nature of ratchet encryption, we abstract its key negotiation and update processes. By integrating LoET, we formally define the security properties of protocol interactions, precisely characterizing the requirements for bidirectional authentication.
- Formal verification of strong authentication properties in the Signal protocol. Leveraging our extended LoET rules, we rigorously prove the strong authentication properties of the ratchet mechanism in message exchange scenarios. This work also extends the applicability of LoET to the analysis of ratchet protocols.
2. Logic of Events Theory
2.1. Notation
2.2. Fundamental Concepts
- Act List: is an action list (Act List), representing a sequence of protocol actions (such as Send, Receive, Encrypt, etc.) executed by a single participant. The condition indicates that the events in this list are arranged in order, i.e., local causal ordering holds: each preceding event occurs before the next one and all events belong to the same participant’s thread.
- Thread (Thread): An ordered sequence of events executed by a single principal, satisfying intra-participant causal ordering .
- Weak Match (): The send and receive events contain identical message content (), without requiring causal order.
- Strong Match (): A weak match that additionally satisfies causal precedence (), ensuring the chronological execution of the events.
2.2.1. Threads and Matching Sessions
2.2.2. Strong Authentication Properties of Protocols
2.2.3. Axioms of the Logic of Events Theory
2.3. Logic of Event Theory Extensions
2.3.1. Event Class Extension
2.3.2. Related Axiomatic Extension
2.3.3. Rule Extension
- Prior to event e, all events executed by the same participant (loc(e)) must not include atom a in any attacker-observable operation, such as Send, Rcv, or unprotected Encrypt. This condition can be verified using the extended has rule in combination with the local order relation ().
- The occurrence of a in event e must originate from secure events (e.g., DH or ratchet) and must not be derivable from any previously exposed message. This corresponds to the flow relation defined in AxiomF.
3. Formal Analysis of the Signal Protocol
3.1. Overview of the Signal Protocol
- Registration. Initiator A and Responder B respectively register their identity and prekey bundles with the server. Each prekey bundle contains the party’s respective public keys.
- Session setup. A requests B’s prekey bundle from the server and establishes a secure communication channel with B. Using these public keys, A generates an initial symmetric encryption key, encrypts a message, and sends it to B. This process is known as the Triple Diffie–Hellman (3DH) handshake. Upon receiving the message, B fetches A’s prekey bundle from the server and derives the shared secret.
- Symmetric Ratchet Phase. If A needs to send another message to B before receiving a reply, A derives a new symmetric encryption key via the ratchet mechanism, generates a temporary ratchet public key, attaches it to the message, and sends it to B for use in the response.
- Asymmetric Ratchet Phase. When B receives A’s message and needs to reply, B generates a new temporary ratchet public key, encrypts the message, and sends it to A. When A replies in turn, A generates another temporary ratchet public key based on the received message, encrypts the response, and sends it back to B—thus completing the asymmetric ratchet process.
3.2. Formal Verification Framework
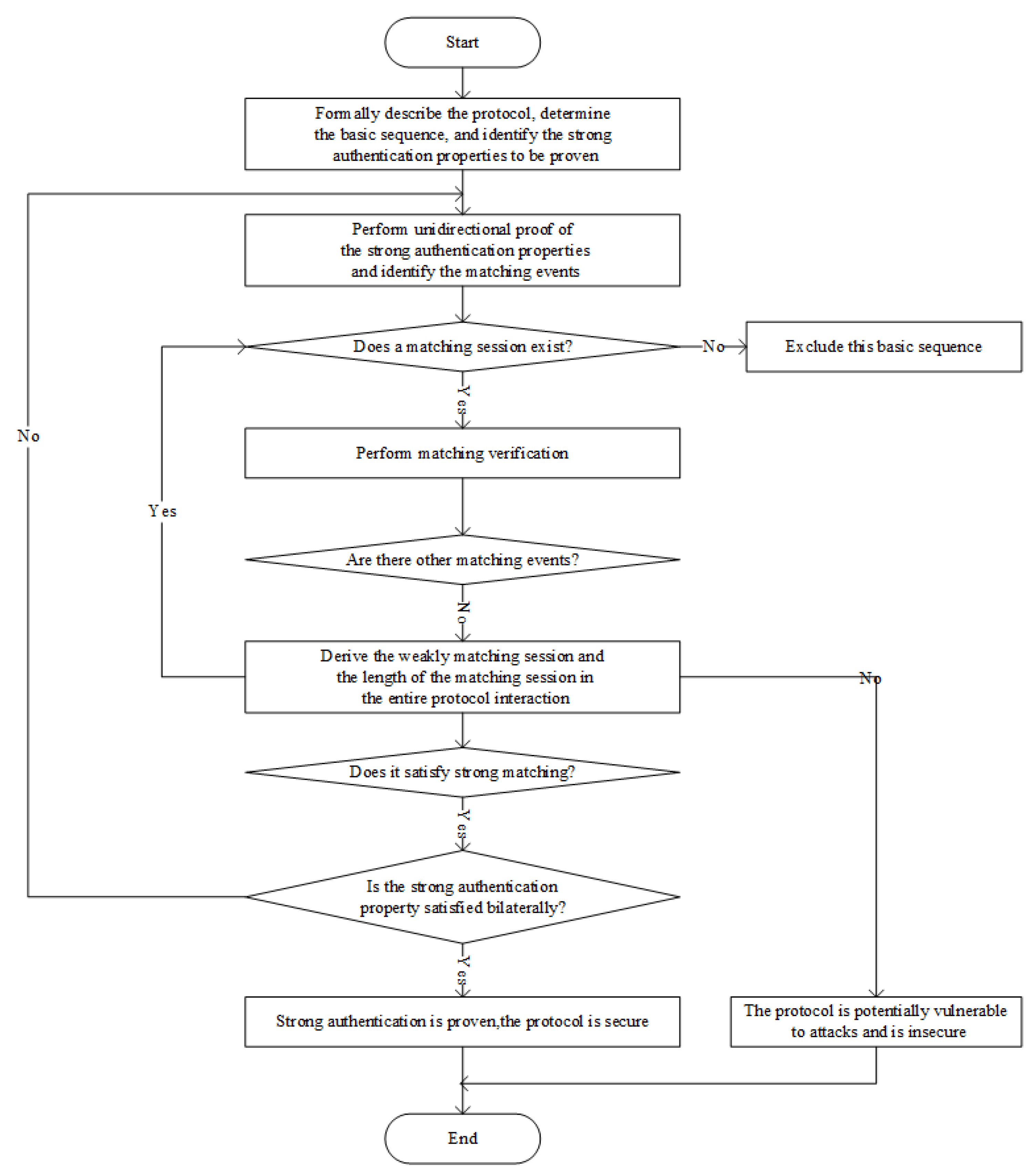
- Use LoET and its extensions to formally describe the ratcheting mechanism of the Signal protocol. Define the actions between initiator A and responder B, specify the basic sequence, and identify the strong authentication properties to be verified.
- Prove the unidirectional strong authentication property. Assume both A and B are honest. For any instance of the basic sequence, identify matching events and exclude non-matching ones.
- Check whether the matching events satisfy the session conditions. If so, prove the matching session; otherwise, continue filtering. If only weak matching is found, analyze the sequence length and verify strong matching based on the axioms.
- After completing the unidirectional proof, verify the bidirectional property. The protocol is secure only if both directions hold. If any event fails even weak matching, the protocol lacks strong authentication and is vulnerable to impersonation.
3.3. Formal Verification of Strong Authentication Properties
3.3.1. Formal Description of Basic Sequences
- captures the initial message transmission from A to B, where A uses Diffie–Hellman (DH) to generate an ephemeral key and encrypts the message;
- models the reception of B’s response, including decryption using A’s previous key and updating A’s ratchet key for forward secrecy;
- reflects A’s subsequent message to B, built upon the updated ratchet state.
- depicts the initial decryption of the received ciphertext from A using the ratcheted key, enabling B to retrieve the plaintext message;
- represents the generation of a new ratchet key by B and the encryption of a response message to A, establishing a new ratcheted state;
- shows the reception and decryption of a subsequent message from A using the updated ratchet key.
3.3.2. Analysis of the Asymmetric Ratchet
3.3.3. Analysis of the Symmetric Ratchet
3.3.4. Computational Complexity and Scalability
4. Comparison
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A
Appendix A.1. Attack Scenario Demonstration: DH Key Substitution and Clean Predicate Violation
- Assume Alice initiates a session and sends Bob her DH public key: DH(A) = aG.
- An attacker, Mallory, intercepts the message and replaces aG with her forged DH key DH(M) = mG.
- Bob, unaware of this manipulation and without enforcing AxiomE (which links DH to subsequent ratchet operations), uses his private key b to compute .
- Bob proceeds to generate a new ratchet state using , encrypts a message using this state, and sends it back to Alice.
- Alice, expecting as the DH input, uses her private key a and Bob’s original public key to compute .
- Since , Alice is unable to decrypt the message. Worse, if Bob had continued without verification, Mallory could use m to decrypt the message and impersonate Bob by replying with forged messages under her control.
Appendix A.2. Tool Comparison: LoET vs. Tamarin and ART
| Tool | Modeling Abstraction | Ratchet Support | Match Semantics | Avg. Verification Steps |
|---|---|---|---|---|
| LoET (ours) | Event classes + logic axioms | ✓ Native support via DH, ratchet events | ✓ Explicit session and causality rules (Equations (2) and (3)) | 6–10 |
| Tamarin Prover | Multiset rewriting with manual lemma definitions | ✓ Indirectly encoded via states | × Implicit via message/state replay tracking | 20–30 |
| ART | Asynchronous tree-based state modeling | ✓ Partially supports tree ratchets | × Implicit through tree structure | >30 |
Appendix B
Appendix B.1. Verification of Signal Ratchet Authentication Using Tamarin
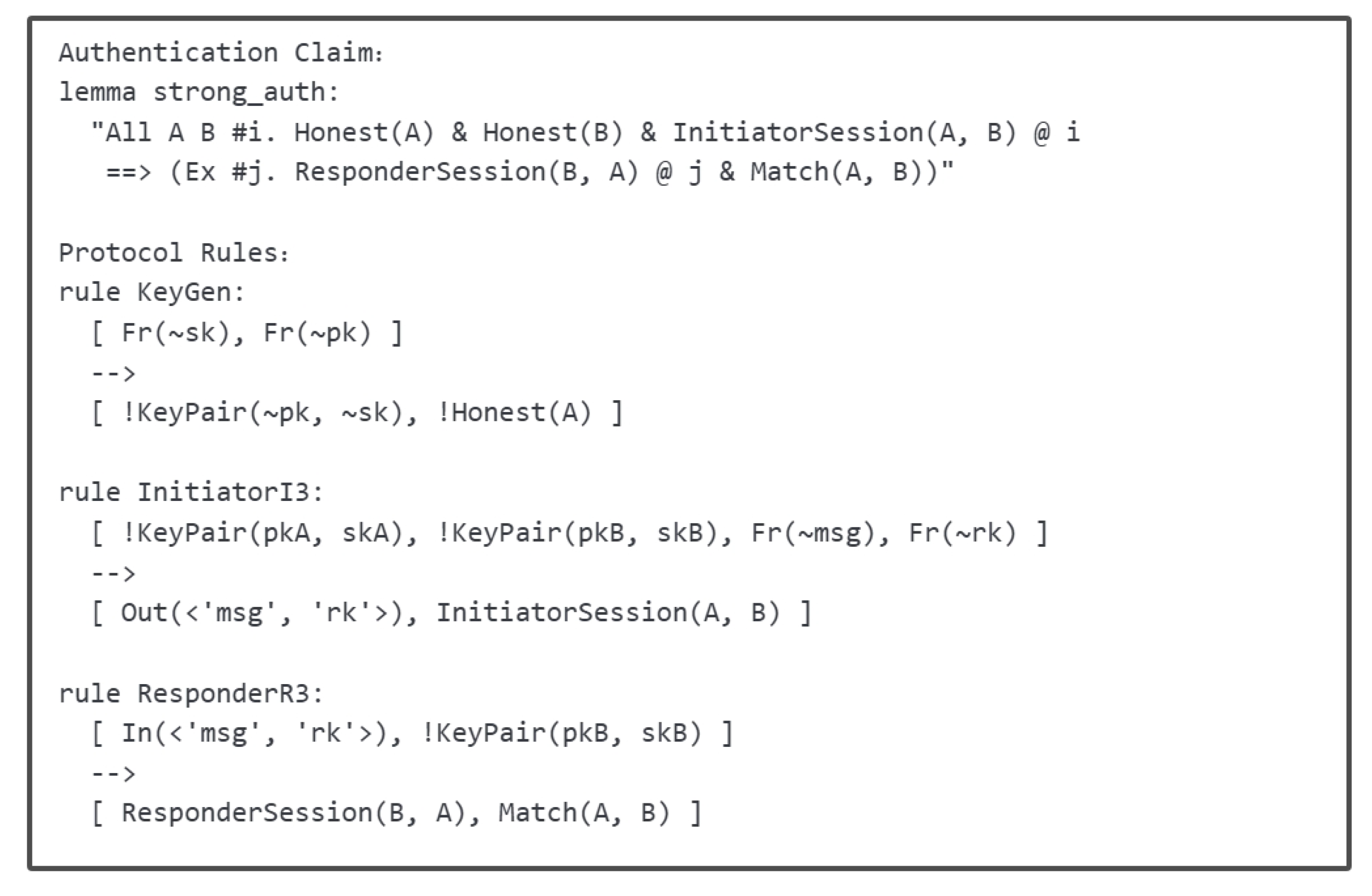
Appendix B.2. Constructive Derivation of the Clean Predicate

References
- Feng, H. Real-World Security Protocols. IEEE Secur. Priv. 2024, 11, 9–10. [Google Scholar]
- Bellare, M.; Yee, B. Forward-Security in Private-Key Cryptography. In Proceedings of the CT-RSA Conference, Heidelberg, Germany, 13–17 April 2003; pp. 1–18. [Google Scholar]
- Wei, J.; Chen, X.; Wang, J.; Hu, X.; Ma, J. Enabling (End-to-End) Encrypted Cloud Emails with Practical Forward Secrecy. IEEE Trans. Dependable Secur. Comput. 2022, 7, 2318–2332. [Google Scholar] [CrossRef]
- Yu, S.J.; Lee, Y.C.; Lin, L.H.; Yang, C.H. An Energy-Efficient Double Ratchet Cryptographic Processor with Backward Secrecy for IoT Devices. IEEE J. Solid-State Circuits 2023, 6, 1810–1819. [Google Scholar] [CrossRef]
- Afzal, A.; Hussain, M.; Saleem, S.; Shahzad, M.K. Encrypted Network Traffic Analysis of Secure Instant Messaging Application: A Case Study of Signal Messenger App. Appl. Sci. 2021, 11, 7789. [Google Scholar] [CrossRef]
- Ahmed, W.; Shahzad, F.; Javed, A.R.; Iqbal, F.; Ali, L. WhatsApp Network Forensics: Discovering the IP Addresses of Suspects. In Proceedings of the 2021 11th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 19–21 April 2021. [Google Scholar]
- Nabeel, M. The Many Faces of End-to-End Encryption and Their Security Analysis. In Proceedings of the 2017 IEEE International Conference on Edge Computing (EDGE), Honolulu, HI, USA, 25–30 June 2017. [Google Scholar]
- Bhargavan, K.; Jacomme, C.; Kiefer, F.; Schmidt, R. Formal Verification of the PQXDH Post-Quantum Key Agreement Protocol for End-to-End Secure Messaging. In Proceedings of the 33rd USENIX Security Symposium (USENIX Security 2024), Philadelphia, PA, USA, 14–16 August 2024. [Google Scholar]
- Poettering, B.; Rösler, P. Towards Bidirectional Ratcheted Key Exchange. In Advances in Cryptology—CRYPTO 2018: Proceedings of the 38th Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2018; Shacham, H., Boldyreva, A., Eds.; Springer: Berlin/Heidelberg, Germany, 2018. [Google Scholar]
- Cohn-Gordon, K.; Cremers, C.; Dowling, L.; Garratt, L.; Stebila, D. A Formal Security Analysis of the Signal Messaging Protocol. In Proceedings of the 2017 IEEE European Symposium on Security and Privacy, Paris, France, 26–28 April 2017. [Google Scholar]
- Lv, C. The Dilemma and Countermeasures of Personal Privacy Protection in the Era of Big Data. In Proceedings of the 2022 3rd International Conference on Electronic Communication and Artificial Intelligence (IWECAI), Zhuhai, China, 24–26 June 2022. [Google Scholar]
- Perrin, T. The X3DH Key Agreement Protocol. Available online: https://whispersystems.org/docs/specifications/x3dh (accessed on 28 April 2025).
- Perrin, T. The Double Ratchet Algorithm. Available online: https://whispersystems.org/docs/specifications/doubleratchet (accessed on 28 April 2025).
- Borisov, N.; Goldberg, L.; Brewer, E. Off-the-Record Communication, or, Why Not to Use PGP. In Proceedings of the 2004 ACM Workshop on Privacy in the Electronic Society (WPES), Washington, DC, USA, 28 October 2004. [Google Scholar]
- Bienstock, A.; Paul, R.; Yi, T. Asmesh: Anonymous and Secure Messaging in Mesh Networks Using Stronger, Anonymous Double Ratchet. In Proceedings of the 2023 ACM SIGSAC Conference on Computer and Communications Security (CCS), New York, NY, USA, 26–30 November 2023. [Google Scholar]
- Bhati, A.S.; Dufka, A.; Andreeva, E.; Roy, A.; Preneel, B. Skye: An Expanding PRF-Based Fast KDF and Its Applications. In Proceedings of the 19th ACM Asia Conference on Computer and Communications Security (AsiaCCS 2024), New York, NY, USA, 1–5 July 2024. [Google Scholar]
- Marlinspike, M. Advanced Cryptographic Ratcheting. Available online: https://signal.org/blog/advanced-ratcheting (accessed on 28 April 2025).
- Frosch, T.; Mainka, C.; Bader, C.; Bergsma, F.; Schwenk, J.; Holz, T. How Secure is TextSecure? In Proceedings of the 2016 IEEE European Symposium on Security and Privacy (EuroS&P), Saarbrücken, Germany, 21–23 March 2016. [Google Scholar]
- Cohn-Gordon, K.; Cremers, C.; Garratt, L.; Millican, J.; Milner, K. On Ends-to-Ends Encryption: Asynchronous Group Messaging with Strong Security Guarantees. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security (CCS), New York, NY, USA, 15–19 October 2018. [Google Scholar]
- Bellare, M.; Singh, A.C.; Jaeger, J.; Nyayapati, M.; Stepanovs, I. Ratcheted Encryption and Key Exchange: The Security of Messaging. In Proceedings of the 37th Annual International Cryptology Conference (CRYPTO 2017), Santa Barbara, CA, USA, 20–24 August 2017. [Google Scholar]
- Beguinet, H.; Chevalier, C.; Ricosset, T.; Senet, H. Formal Verification of a Post-Quantum Signal Protocol with Tamarin. In Proceedings of the International Conference on Verification and Evaluation of Computer and Communication Systems (VECoS 2023), Marrakech, Morocco, 13–15 November 2023. [Google Scholar]
- Li, Z.; Xiao, M.; Xu, R. Formal Analysis of Signal Protocol Based on Logic of Events Theory. Sci. Rep. 2024, 14, 71666. [Google Scholar] [CrossRef] [PubMed]
- Almuzaini, N.Z.; Ahmad, I. Formal Analysis of the Signal Protocol Using the Scyther Tool. In Proceedings of the 2019 2nd International Conference on Computer Applications & Information Security (ICCAIS), Riyadh, Saudi Arabia, 1–3 May 2019. [Google Scholar]
- Linker, F.; Sasse, R.; Basin, D. A Formal Analysis of Apple’s iMessage PQ3 Protocol. Report No. 1395. 2024. Available online: https://eprint.iacr.org/2024/1395 (accessed on 28 April 2025).
- Xiao, M.; Bickford, M. Logic of Events for Proving Security Properties of Protocols. In Proceedings of the 2009 International Conference on Web Information Systems and Mining (WISM), Shanghai, China, 7–8 November 2009. [Google Scholar]
- Bickford, M.; Constable, R. Automated Proof of Authentication Protocols in a Logic of Events. In Proceedings of the 6th International Verification Workshop (VERIFY 2010), Washington, DC, USA, 15 July 2010. [Google Scholar]
- Datta, A.; Derek, A.; Mitchell, J.; Roy, A. Protocol Composition Logic (PCL). Electron. Notes Theor. Comput. Sci. 2007, 172, 311–358. [Google Scholar] [CrossRef]
- Kobeissi, N.; Bhargavan, K.; Blanchet, B. Automated Verification for Secure Messaging Protocols and Their Implementations: A Symbolic and Computational Approach. In Proceedings of the 2017 IEEE European Symposium on Security and Privacy (EuroS&P), Paris, France, 26–28 April 2017; pp. 435–450. [Google Scholar]
- Kobeissi, N.; Nicolas, G.; Tiwari, M. Verifpal: Cryptographic Protocol Analysis for the Real World. In Progress in Cryptology—INDOCRYPT 2020: 21st International Conference on Cryptology in India, Bangalore, India, 13–16 December 2020; Lecture Notes in Computer Science; Bhargavan, K., Oswald, E., Prabhakaran, M., Eds.; Springer: Cham, Switzerland, 2020; Volume 12578, pp. 153–177. [Google Scholar]
- AlSobeh, A.M.R. OSM: Leveraging Model Checking for Observing Dynamic Behaviors in Aspect-Oriented Applications. Online J. Commun. Media Technol. 2023, 13, e202355. [Google Scholar] [CrossRef]
- AlSobeh, A.M.R.; Magableh, A.A. BlockASP: A Framework for AOP-Based Model Checking Blockchain System. IEEE Access 2023, 11, 115062–115075. [Google Scholar] [CrossRef]



| Notation | Semantics | Example |
|---|---|---|
| ID | Identifier of protocol participant | A, B |
| Atom | Unpredictable information | nonce, key, signature |
| Data | Message content or plaintext | “Hello”, session key |
| e | An individual event | Encrypt(e) |
| E | A set of events | E = {e1, e2, e3} |
| nonce | Random number generated in protocol | r = New(e) |
| has | Predicate indicating data is contained in event | e has a |
| bs | Basic event sequence for a participant | I1, R2 |
| < | Causal ordering of events | e1 < e2 |
| loc(e) | Principal executing event e | loc(e) = A |
| key(e) | Cryptographic key used in event e | key(e) = PrivKey(A) |
| New(e) | Random atom introduced by event e | New(e) = r |
| Send(e) | Sending message event | Send(e) = “msg” |
| Rcv(e) | Receiving message event | Rcv(e) = “msg” |
| Encrypt(e) | Encryption event with message, key, atom | Encrypt(e) = |
| Decrypt(e) | Decryption event corresponding to Encrypt(e) | Decrypt(e) = |
| Notations | Description |
|---|---|
| PKB-X | Prekey bundle of X |
| The x-th ratchet key generated by party y | |
| The x-th ciphertext of the sender | |
| The x-th message |
| Reference | Research Method | Analysis of Ratchet | Verification Efficiency |
|---|---|---|---|
| This paper | LoET (Extended) | Models bidirectional authentication; introduces DH and ratchet event types, AxiomE, and Clean predicate; supports full ratchet evolution. | ✓ Structured logic; supports over three strong matching events; short reasoning paths; modular logic; suitable for pre-integration with automated tools; the time complexity is . |
| Ref. [18] | TextSecure source analysis | Only validates modules; lacks formal modeling and global security reasoning. | × No formal reasoning structure; depends on source code details; verification cannot be generalized |
| Ref. [19] | ART | Supports asynchronous group ratchet; suffers from complexity, sync issues, and weak verification support. | × Complex state transitions; cannot support systematic authentication; low verification efficiency |
| Ref. [20] | Syntax for ratcheted encryption | Models unidirectional ratchet; does not capture Signal’s double ratchet logic. | × Cannot construct complete authentication chains; lacks modeling for complex causal event dependencies; limited verification |
| Ref. [21] | Tamarin | Automates partial proofs; lacks native support for causality or bidirectional authentication semantics. | × Automated but requires model rewriting; lacks efficient matching for structured events; leads to long and fragmented verification;the time complexity is . |
| Ref. [22] | Original LoET | Early LoET use; no AxiomE/Clean support; only basic match rules used. | × Coarse-grained modeling; fewer verification steps and weak completeness; lacks Clean and AxiomE support; incomplete reasoning paths |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xiao, M.; Wan, H.; Fan, H.; Shao, H.; Li, Z.; Yang, K. Formal Analysis of Ratchet Protocols Based on Logic of Events. Appl. Sci. 2025, 15, 6964. https://doi.org/10.3390/app15136964
Xiao M, Wan H, Fan H, Shao H, Li Z, Yang K. Formal Analysis of Ratchet Protocols Based on Logic of Events. Applied Sciences. 2025; 15(13):6964. https://doi.org/10.3390/app15136964
Chicago/Turabian StyleXiao, Meihua, Hongbin Wan, Hongming Fan, Huaibin Shao, Zehuan Li, and Ke Yang. 2025. "Formal Analysis of Ratchet Protocols Based on Logic of Events" Applied Sciences 15, no. 13: 6964. https://doi.org/10.3390/app15136964
APA StyleXiao, M., Wan, H., Fan, H., Shao, H., Li, Z., & Yang, K. (2025). Formal Analysis of Ratchet Protocols Based on Logic of Events. Applied Sciences, 15(13), 6964. https://doi.org/10.3390/app15136964






