Blockchain Solutions for Enhancing Security and Privacy in Industrial IoT
Abstract
1. Introduction
Key Contributions
- Proposed Framework: An architecture that integrates blockchain, edge computing, and smart contracts to enhance security and scalability in IIoT systems.
- Comprehensive Security: Combines blockchain with Zero Trust principles and AI-driven anomaly detection to address real-time threats and vulnerabilities.
- Evaluation: Assesses the framework’s feasibility through real-world test bed experiments, performance benchmarks, and case studies in industrial settings.
- Scalability Analysis: Evaluates alternative blockchain platforms, such as Solana and IOTA, to address high-frequency transaction demands in IIoT environments.
2. Literature Review
2.1. Architectural Innovations
2.2. Security and Trust Management
2.3. Data Sharing and Supply Chain Transparency
2.4. Energy Efficiency and Scalability
2.5. Smart Contracts and Automation
3. Background
3.1. Industrial Internet of Things (IIoT)
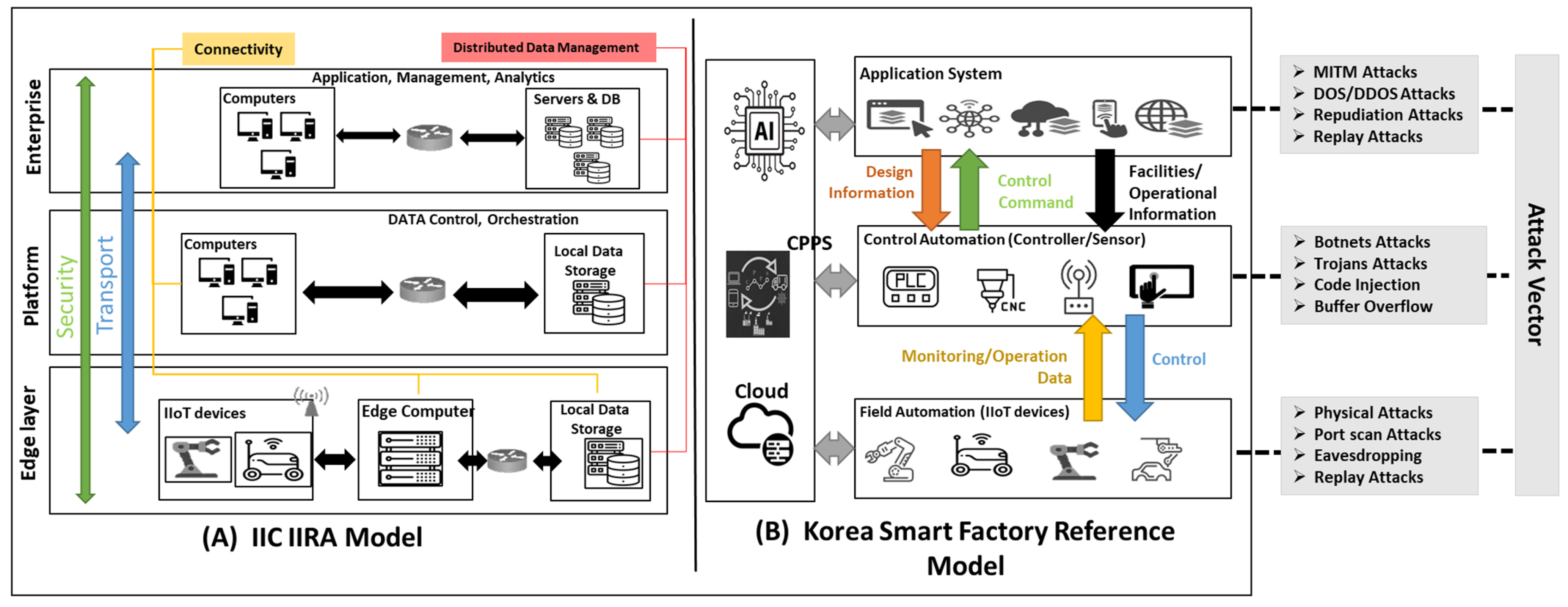
3.2. Integrated Architectural Framework for Smart Industrial Systems
3.3. Blockchain Technology
- Decentralization: Blockchain disperses control across a peer-to-peer network, where each participant maintains a copy of the ledger. This distributed nature eliminates the need for a central authority, reducing the risk of single points of failure. Even if one node is compromised, the rest of the network remains operational, enhancing resilience against cyber threats [28].
- Immutability: Once data is recorded on the blockchain, it cannot be deleted or altered without the consensus of the network. In environments where accuracy is paramount [29], this unchangeability ensures the integrity of critical industrial data, such as sensor readings or manufacturing performance metrics.
- Transparency: Blockchain provides a transparent and auditable record of all transactions visible to all participants. This feature is crucial for IIoT systems, where real-time data tracking and operational monitoring are essential for maintaining efficiency and security [30].
- Cryptographic Security: Blockchain utilizes advanced cryptographic algorithms to safeguard data, rendering unauthorized access or tampering virtually impossible. Hash functions, digital signatures, and consensus algorithms ensure secure device communication and prevent data breaches [31].
- Smart Contracts: These self-executing agreements are embedded in the blockchain and automatically trigger actions when predefined conditions are met. For example, smart contracts can automate device maintenance or registration, enhance security, and optimize operational efficiency [32].
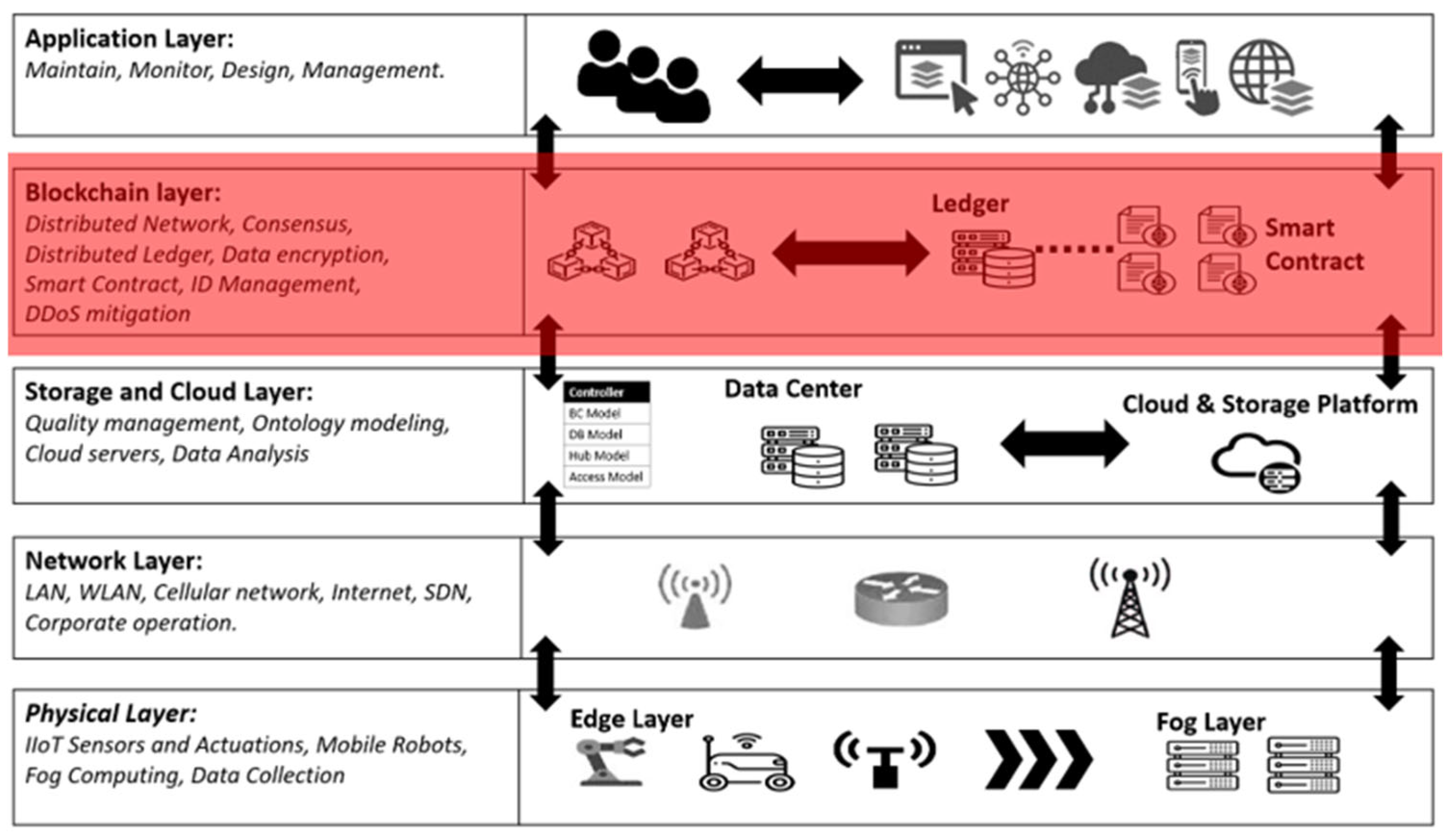
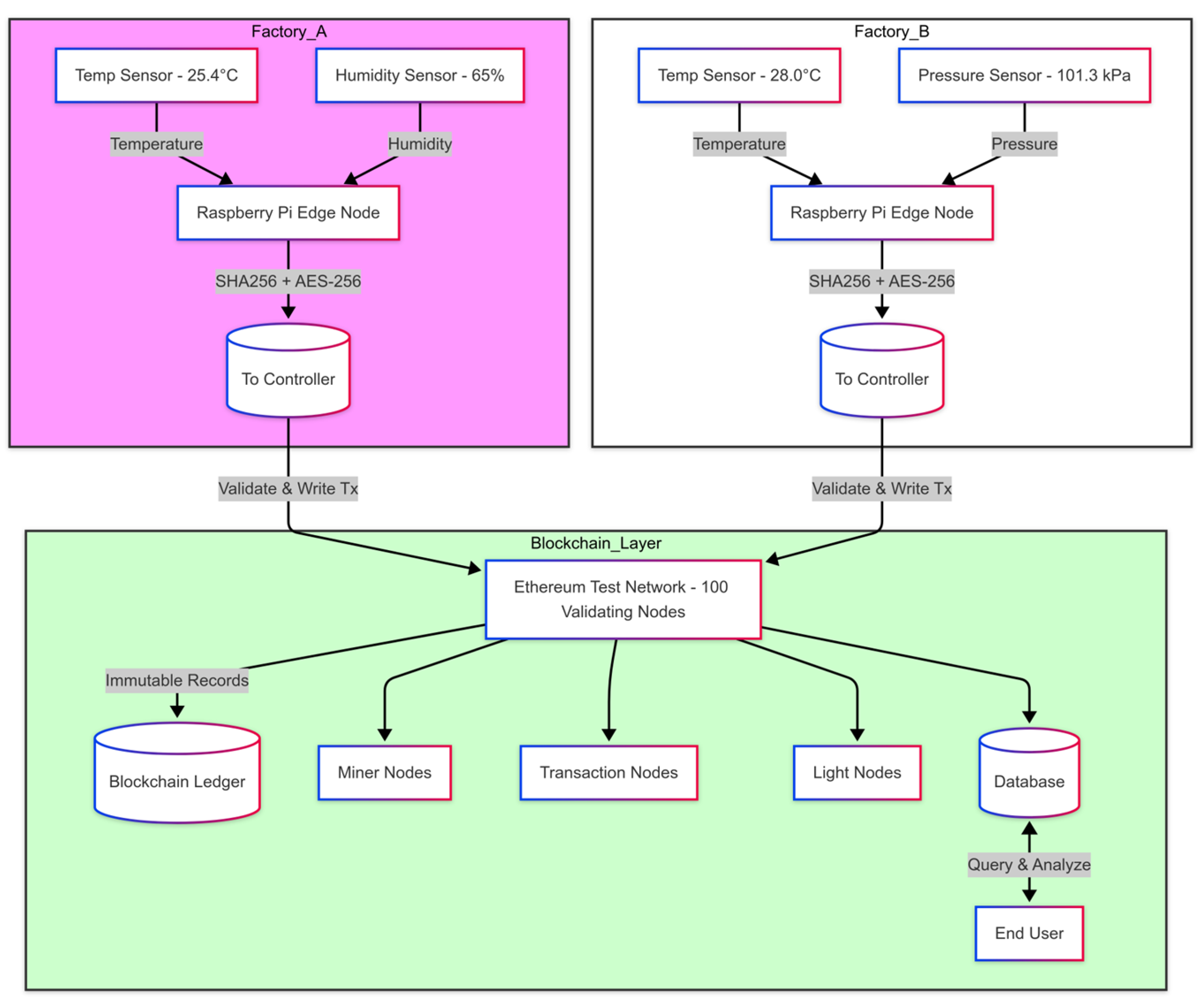
4. Blockchain-Based Architecture and System Design
4.1. Architecture Overview
- Physical Layer: This foundational layer comprises IIoT sensors, actuators, and edge computing devices responsible for real-time data collection and processing. Edge computing is pivotal in reducing latency by performing localized computations and ensuring timely responses in industrial settings where delays can lead to significant operational and financial losses [34].
- Network Layer: The network layer facilitates reliable communication between devices using standardized protocols such as MQTT (Message Queuing Telemetry Transport), HTTP (Hypertext Transfer Protocol), and OPC-UA (Open Platform Communications Unified Architecture). By enabling seamless data exchange across local and remote components, this layer ensures efficient coordination in distributed IIoT systems, laying the groundwork for robust interoperability [35].
- Blockchain Layer: At the core of the architecture lies the blockchain layer, which provides decentralized security and data integrity through distributed ledger technology (DLT). This layer prevents unauthorized access and data tampering by employing consensus algorithms, cryptographic encryption, and identity management. It mitigates Distributed Denial of Service (DDoS) attacks by distributing computational tasks across edge nodes and blockchain miners, enhancing system resilience [36,37,38,39].
- Application Layer: The application layer oversees system operations, including monitoring, control, and logging. Real-time interaction tools notify operators of failures or anomalies, ensuring continuous system functionality and minimizing downtime. This layer is the interface between the system and end users, fostering trust through transparent and tamper-proof data transactions [37].
4.2. System Entities and Interactions
4.3. System Controller and Modules
- Blockchain Management Module: This module generates transactions by encapsulating data, SHA-256 (Secure Hash Algorithm) hashes, device IDs, and database identifiers. These transactions are added to the blockchain, ensuring immutability and traceability.
- Database Management Module: Responsible for calculating the SHA256 hashes of transmitted data, this module securely stores the data in an indexed database. It ensures that the data is well organized and readily accessible to authorized users.
- Edge-Allowing Hub Module: This module manages communication between controllers and hubs, enforcing data transmission schedules and timing policies. Filtering noise and correcting errors ensure the validity and reliability of the data.
- Access Control Module: This module authenticates users through token-based mechanisms, preventing unauthorized access. It ensures that only authorized entities interact with the system, maintaining security and integrity.
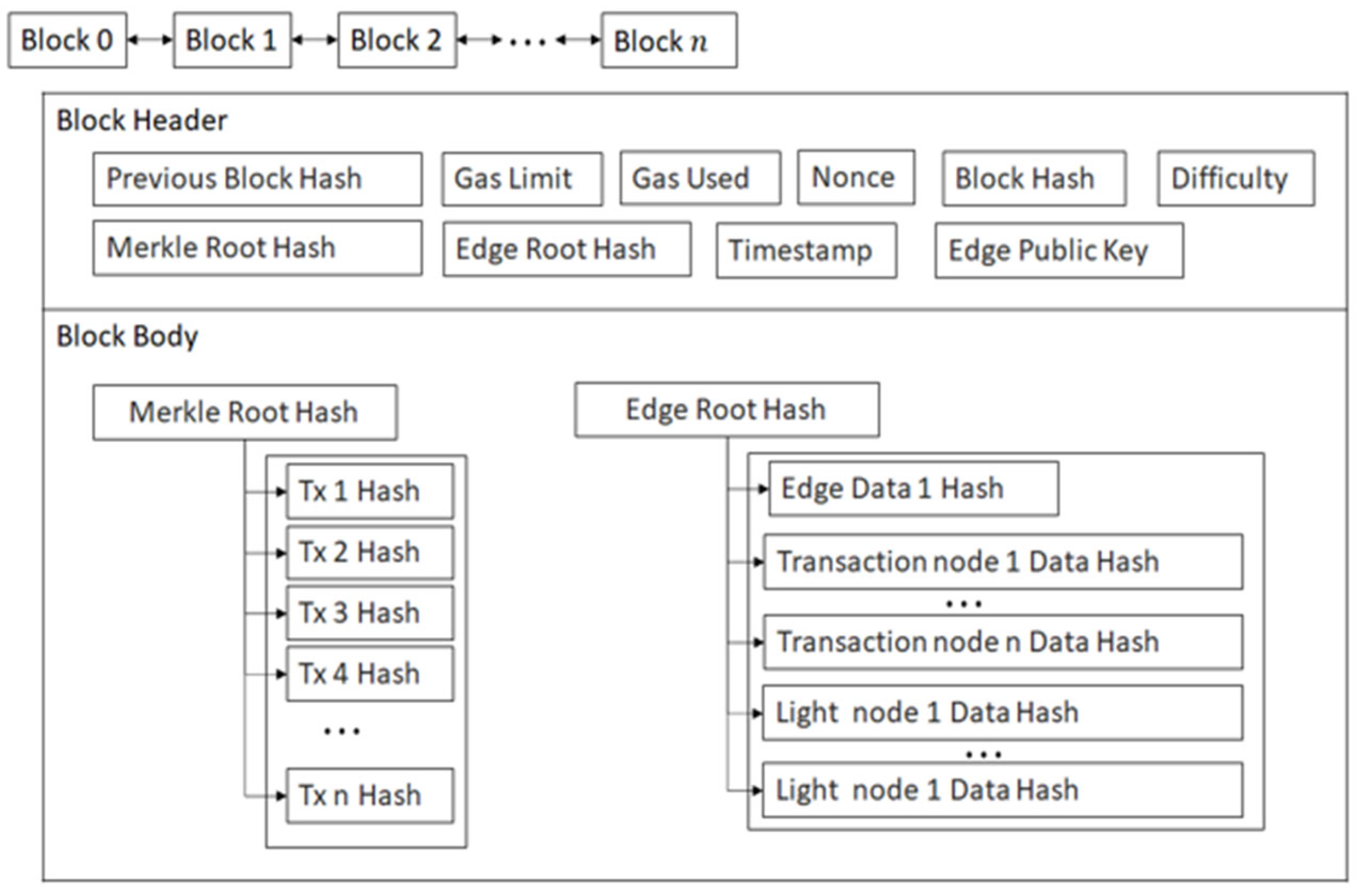
4.4. Authentication and Blockchain Nodes
- Light Nodes: These simple IoT devices with minimal computational power are primarily used for sensing tasks. Light nodes rely on miner nodes for data aggregation and fusion, ensuring efficient data processing [42].
| Algorithm 1. Pseudocode for Blockchain Management Module in the Blockchain-Integrated IIoT System |
| module BlockchainManagement(Controller): # Iterate over each data batch received from the hubs for each data_batch in received_data_batches: # Step 1: Calculate SHA256 hash of the data data_hash = SHA256(data_batch) # Step 2: Generate a transaction transaction = { ‘data_hash’: data_hash, ‘device_id’: data_batch.device_id, ‘database_id’: data_batch.database_id } # Step 3: Append the transaction to the blockchain append_to_blockchain(transaction) # End of data batch processing end module |
4.5. Block Data Structure
4.6. Collaborative DDoS Mitigation
- Deep Learning for Threat Detection: The system utilizes advanced deep learning models, such as Long Short-Term Memory (LSTM) networks, to analyze real-time network traffic patterns. These models are trained to identify anomalies and flag potential DDoS attacks, enabling early detection and rapid response [45]. By continuously monitoring traffic behavior, the system distinguishes between legitimate and malicious activity, significantly reducing false positives while maintaining high detection accuracy.
- Edge Computing for Localized Mitigation: Edge computing plays a crucial role in mitigating DDoS attacks by processing and filtering malicious traffic at the network’s edge. By offloading computational tasks to edge nodes, the system reduces the load on central servers, ensuring an uninterrupted flow of legitimate traffic. This localized approach minimizes latency and enhances the system’s resilience against large-scale attacks. Edge nodes act as the first line of defense, filtering out malicious requests before they reach critical infrastructure, thereby preventing network congestion and maintaining operational continuity.
- Smart Contracts for Automated Response: Smart contracts embedded within the blockchain automate the response to detected threats. When a DDoS attack is identified, smart contracts trigger predefined actions, such as blocking malicious IP addresses or stopping suspicious traffic that causes rate-limiting. These actions are recorded on the blockchain, creating a transparent and tamper-proof audit trail that ensures accountability and traceability [44]. Using smart contracts eliminates manual intervention, enabling faster and more reliable responses to cyber threats.
- Integrated Defense Mechanism: By combining deep learning, edge computing, and smart contracts, the system creates a collaborative defense mechanism that is both proactive and adaptive. This integrated approach improves the system’s ability to withstand DDoS attacks, ensuring continuous operation and data integrity even under adverse conditions. The decentralized nature of this solution further enhances its robustness, making it well suited for the dynamic and interconnected environments of Industrial Internet of Things (IIoT) systems.
- Early Detection: Deep learning models identify anomalies in real-time traffic, enabling proactive threat identification.
- Localized Mitigation: Edge computing filters malicious traffic at the edge, reducing latency and server load.
- Automated Response: Smart contracts execute predefined actions, ensuring rapid and tamper-proof responses to threats.
- Decentralized Resilience: Blockchain integration ensures transparency, accountability, and resistance to single points of failure.
| Algorithm 2. Pseudocode for DDoS Detection and Mitigation Using Fog-Cloud and Blockchain |
| BEGIN // Step 1: Start monitoring network traffic START: WHILE (system_running) DO traffic_data = MonitorNetworkTraffic() // Step 2: Detect and filter suspicious traffic filtered_traffic = DetectAndFilter(traffic_data) // Step 3: Use LSTM-based Deep Learning model to detect DDoS attack_detected = DetectDDoSUsingLSTM(filtered_traffic) IF attack_detected THEN // Step 4: Identify malicious traffic malicious_traffic = IdentifyMaliciousTraffic(filtered_traffic) // Step 5: Forward to Fog Nodes for processing SendToFogNodes(malicious_traffic) // Step 6: Fog nodes filter malicious traffic clean_traffic = FogNodeFiltering(malicious_traffic) // Step 7: Forward cleaned traffic to the Cloud Controller SendToCloudController(clean_traffic) // Step 8: Cloud controller validates traffic validation_result = ValidateTrafficInCloud(clean_traffic) IF validation_result == “malicious” THEN // Step 9: Execute Smart Contract defense_actions = ExecuteSmartContract(validation_result) // Step 10: Initiate smart contract for mitigation InitiateMitigation(defense_actions) // Step 11: Record actions on the blockchain LogOnBlockchain(defense_actions) // Step 12: Collaborative defense by other participants TriggerCollaborativeDefense() // Step 13: Ensure transparency and accountability EnsureTransparencyAndAccountability() // Step 14: Attack mitigated, maintain normal traffic MaintainNormalTraffic() ELSE // Step 15: Allow normal traffic AllowTraffic(clean_traffic) END IF ELSE // Step 16: No attack detected, allow traffic AllowTraffic(filtered_traffic) END IF END WHILE // Step 17: End END |
5. Experiment and Results
5.1. Experiment Setup
5.2. Data Collection and Blockchain Integration
5.3. Data Analysis and Insights
5.4. DDoS Attack Mitigation
5.5. Performance and Scalability
5.6. General Results
5.7. Comparative Analysis of Blockchain-Integrated IIoT Systems with Traditional IIoT Architectures
6. Discussion
6.1. Enhancing Security, Integrity, and Resilience
6.2. Addressing Real-Time Threats
6.3. Evaluating Consensus Mechanisms
6.4. Practical Deployment and Testing
6.5. Transition Feasibility
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Han, S. A review of smart manufacturing reference models based on the skeleton meta-model. J. Comput. Des. Eng. 2020, 7, 323–336. [Google Scholar] [CrossRef]
- Microsoft. IoT Signals Research, Edition 2: Global Insights for 2020 and Beyond. Available online: https://blogs.microsoft.com/conexiones/2020/10/06/iot-signals-research-edition-2-global-insights-for-2020-and-beyond/ (accessed on 3 June 2025).
- Kaspersky. IoT Cyberattacks Escalate in 2021, According to Kaspersky. IoT World Today. 17 September 2021. Available online: https://www.iotworldtoday.com/security/iot-cyberattacks-escalate-in-2021-according-to-kaspersky (accessed on 3 June 2025).
- Kaspersky ICS CERT. Threat Landscape for Industrial Automation Systems. Q1 2024. 2024. Available online: https://ics-cert.kaspersky.com/publications/reports/2025/05/15/threat-landscape-for-industrial-automation-systems-q1-2025/ (accessed on 3 June 2025).
- IBM Security. Cost of a Data Breach Report. 2021. Available online: https://www.ibm.com/security/data-breach (accessed on 3 June 2025).
- PwC. Cybersecurity Coming of Age. 2020. Available online: https://www.pwc.com/id/en/media-centre/press-release/2020/english/cybersecurity-coming-of-age.html (accessed on 3 June 2025).
- Essaid, M.; Park, S.; Ju, H.T. Bitcoin’s dynamic peer-to-peer topology. Int. J. Netw. Manag. 2020, 30, e2106. [Google Scholar] [CrossRef]
- Essaid, M.; Park, S.; Ju, H.T. Visualising Bitcoin’s dynamic P2P network topology and performance. In Proceedings of the 2019 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Seoul, Republic of Korea, 14–17 May 2019; IEEE: New York, NY, USA, 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Essaid, M.; Lee, C.; Ju, H.T. Characterizing the Bitcoin network topology with Node-Probe. Int. J. Netw. Manag. 2023, 33, e2230. [Google Scholar] [CrossRef]
- Gao, Y.; Shi, J.; Wang, X.; Tan, Q.; Zhao, C.; Yin, Z. Topology measurement and analysis of the Ethereum P2P network. In Proceedings of the 2019 IEEE Symposium on Computers and Communications (ISCC), Barcelona, Spain, 29 June–3 July 2019; IEEE: New York, NY, USA, 2019; pp. 1–7. [Google Scholar]
- Tange, K.; De Donno, M.; Fafoutis, X.; Dragoni, N. A Systematic Survey of Industrial Internet of Things Security: Requirements and Fog Computing Opportunities. IEEE Commun. Surv. Tutor. 2020, 22, 2489–2520. [Google Scholar] [CrossRef]
- ISO/IEC/IEEE 42010:2022; Software, Systems, and Enterprise—Architecture Description. International Organization for Standardization: Geneva, Switzerland, 2022. Available online: https://www.iso.org/standard/74393.html (accessed on 3 June 2025).
- Dhar, S.; Bose, I. Securing IoT devices using zero trust and blockchain. J. Organ. Comput. Electron. Commer. 2021, 31, 18–34. [Google Scholar] [CrossRef]
- Alamu, R. AI-Driven Anomaly Detection: Strengthening Data Security and Quality in Large Databases. 2025. Available online: https://www.researchgate.net/publication/389429725_AI-Driven_Anomaly_Detection_Strengthening_Data_Security_and_Quality_in_Large_Databases (accessed on 2 June 2025).
- Dai, H.N.; Zheng, Z.B.; Zhang, Y. Blockchain for Internet of Things: A Survey. Internet Things J. 2019, 6, 8076–8094. [Google Scholar] [CrossRef]
- Aslam, A.; Postolache, O.; Oliveira, S.; Pereira, J.D. Securing IoT Sensors Using Sharding-Based Blockchain Network Technology Integration: A Systematic Review. Sensors 2025, 25, 807. [Google Scholar] [CrossRef]
- Almarri, S.; Aljughaiman, A. Blockchain Technology for IoT Security and Trust: A Comprehensive SLR. Sustainability 2024, 16, 10177. [Google Scholar] [CrossRef]
- Saravanabhavan, C.; Ranjithkumar, S.; Subashini, M.; Baranidharan, K.; Preethi, P.; Ashok, P. Blockchain-Based Secure Menger’s Authentication for Industrial IoT. In Proceedings of the 2022 2nd International Conference on Advance Computing and Innovative Technologies in Engineering (ICACITE), Greater Noida, India, 28–29 April 2022; pp. 1302–1308. [Google Scholar] [CrossRef]
- Hu, T.; Yang, S.; Wang, Y.; Li, G.; Wang, Y.; Wang, G.; Yin, M.Y. N-Accesses: A Blockchain-Based Access Control Framework for Secure IoT Data Management. Sensors 2023, 23, 8535. [Google Scholar] [CrossRef]
- Longo, F.; Nicoletti, L.; Padovano, A.; d’Atri, G.; Forte, M. Blockchain-enabled supply chain: An experimental study. Comput. Ind. Eng. 2019, 136, 57–69. [Google Scholar] [CrossRef]
- Asaithambi, S.; Ravi, L.; Kotb, H.; Milyani, A.H.; Azhari, A.A.; Nallusamy, S.; Varadarajan, V.; Vairavasundaram, S. An energy-efficient and blockchain-integrated software defined network for the industrial internet of things. Sensors 2022, 22, 7917. [Google Scholar] [CrossRef] [PubMed]
- Xu, G.X.; Zhou, Z.J.; Dong, J.N.; Zhang, L.J.; Song, X.L. A blockchain-based federated learning scheme for data sharing in industrial internet of things. Internet Things J. 2023, 10, 21467–21478. [Google Scholar]
- Rashid, A.; Siddique, M.J. Smart contracts integration between blockchain and Internet of Things: Opportunities and challenges. In Proceedings of the 2019 2nd International Conference on Advancements in Computational Sciences (ICACS), Lahore, Pakistan, 18–20 February 2019; pp. 1–9. [Google Scholar]
- Neog, S.; Das, K. Predictive maintenance using machine learning with the support from smart sensors and supply chain management using blockchain. Indian J. Sci. Technol. 2023, 16, 70–75. [Google Scholar] [CrossRef]
- Sizan, N.S.; Dey, D.; Layek, M.A.; Uddin, M.A.; Huh, E.N. Evaluating Blockchain Platforms for IoT Applications in Industry 5.0: A Comprehensive Review. Blockchain Res. Appl. 2025, 2025, 100276. [Google Scholar] [CrossRef]
- Wiktorsson, M.; Do Noh, S.; Bellgran, M.; Hanson, L. Smart Factories: South Korean and Swedish examples on manufacturing settings. Procedia Manuf. 2018, 25, 471–478. [Google Scholar] [CrossRef]
- Lee, S.J.; Cho, H.J. South Korean Smart Manufacturing Strategy. In Proceedings of the 2022 IEEE/ACIS 7th International Conference on Big Data, Cloud Computing, and Data Science (BCD), Danang, Vietnam, 4–6 August 2022; IEEE: New York, NY, USA, 2022; pp. 199–202. [Google Scholar]
- Narayanan, A.; Bonneau, J.; Felten, E.; Miller, A.; Shacham, H. Bitcoin and Cryptocurrency Technologies; Princeton University Press: Princeton, NJ, USA, 2016. [Google Scholar]
- Tapscott, D.; Tapscott, A. Blockchain Revolution: How the Technology Behind Bitcoin and Other Cryptocurrencies is Changing the World; Penguin: London, UK, 2017. [Google Scholar]
- Mougayar, W. The Business Blockchain: Promise, Practice, and the Next Big Thing; Wiley: New York, NY, USA, 2016. [Google Scholar]
- Zhou, J.; Yang, Z.; Lee, S. Security and privacy for Industrial IoT: A survey. IEEE Trans. Ind. Inform. 2020, 16, 2364–2373. [Google Scholar] [CrossRef]
- Kolvart, M.; Poola, M.; Rull, A. Smart contracts. In the Future of Law and Etechnologies; Springer: Cham, Switzerland, 2016; pp. 133–147. [Google Scholar]
- Sadeghi, A.R.; Wachsmann, C.; Waidner, M. Security and privacy challenges in industrial internet of things. In Proceedings of the 52nd Annual Design Automation Conference, San Francisco, CA, USA, 8–12 June 2015; pp. 1–6. [Google Scholar]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Kumar, R.; Kandpal, B.; Ahmad, V. Industrial IoT (IIoT): Security threats and countermeasures. In Proceedings of the 2023 International Conference on Innovative Data Communication Technologies and Application (ICIDCA), Uttarakhand, India, 14–16 March 2023; pp. 829–833. [Google Scholar] [CrossRef]
- Latif, S.; Idrees, Z.; Ahmad, J.; Zheng, L.; Zou, Z. A blockchain-based architecture for secure and trustworthy operations in the industrial Internet of Things. J. Ind. Inf. Integr. 2021, 21, 100190. [Google Scholar] [CrossRef]
- Wang, S.; Liu, J. Blockchain based Secure Data Sharing Model. In Proceedings of the 2021 IEEE 24th International Conference on Computer Supported Cooperative Work in Design (CSCWD), Dalian, China, 5–7 May 2021; pp. 464–469. [Google Scholar]
- Zhang, L.; Wang, T.; Liew, S.C. Speeding up block propagation in Bitcoin network: Uncoded and coded designs. Comput. Netw. 2022, 206, 108791. [Google Scholar] [CrossRef]
- Gao, W.; Hatcher, W.G.; Yu, W. A survey of blockchain: Techniques, applications, and challenges. In Proceedings of the 2018 27th International Conference on Computer Communication and Networks (ICCCN), Hangzhou, China, 30 July–2 August 2018; IEEE: New York, NY, USA; pp. 1–11. [Google Scholar]
- Fehr, R.M.J.M.; Cachin, C.; Lehnherr, D. Analysing Inter-Blockchain Communication. Bachelor Thesis, University of Bern, Bern, Switzerland, 2023. [Google Scholar]
- Qian, K.; Liu, Y.; Han, Y.; Wang, K. Performance Benchmarking and Optimization for IIoT-oriented Blockchain. In Security, Privacy, and Anonymity in Computation, Communication, and Storage, Proceedings of the 13th SpaCCS 2020 International Workshops, Nanjing, China, 18–20 December 2020; Springer International Publishing: Cham, Switzerland, 2021; pp. 395–406. [Google Scholar]
- Selvarajan, S.; Srivastava, G.; Khadidos, A.O.; Khadidos, A.O.; Baza, M.; Alshehri, A.; Lin, J.C.W. An artificial intelligence lightweight blockchain security model for security and privacy in IIoT systems. J. Cloud Comput. 2023, 12, 38. [Google Scholar] [CrossRef]
- Kim, S.; Kwon, Y.; Cho, S. A survey of scalability solutions on blockchain. In Proceedings of the 2018 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Republic of Korea, 17–19 October 2018; pp. 1204–1207. [Google Scholar] [CrossRef]
- Poon, J.; Dryja, T. The Bitcoin Lightning Network: Scalable Off-Chain Instant Payments (Draft Version 0.5 9:14). 2016. Available online: https://lightning.network (accessed on 3 June 2025).
- Wang, S.; Ouyang, L.; Yuan, Y.; Ni, X.; Han, X.; Wang, F. Blockchain-enabled smart contracts: Architecture, applications, and future trends. IEEE Trans. Syst. Man Cybern. Syst. 2019, 49, 2266–2277. [Google Scholar] [CrossRef]
- Althubiti, S.A.; Jones, E.M.; Roy, K. LSTM for anomaly-based network intrusion detection. In Proceedings of the 28th International Telecommunication Networks and Applications Conference (ITNAC), Sydney, Australia, 21–23 November 2018. [Google Scholar]
- Essaid, M.; Kim, D.Y.; Maeng, S.H.; Park, S.; Ju, H.T. A collaborative DDoS mitigation solution based on Ethereum smart contract and RNN-LSTM. In Proceedings of the 2019 20th Asia-Pacific Network Operations and Management Symposium (APNOMS), Matsue, Japan, 18–20 September 2019; IEEE: New York, NY, USA; pp. 1–6. [Google Scholar] [CrossRef]
- Yakovenko, A. Solana: A new architecture for a high-performance blockchain v0.8.13. 2018. Available online: https://solana.com/solana-whitepaper.pdf (accessed on 3 June 2025).
- Conti, M.; Kumar, G.; Nerurkar, P.; Saha, R.; Vigneri, L. A survey on security challenges and solutions in the IOTA. J. Netw. Comput. Appl. 2022, 203, 103383. [Google Scholar] [CrossRef]
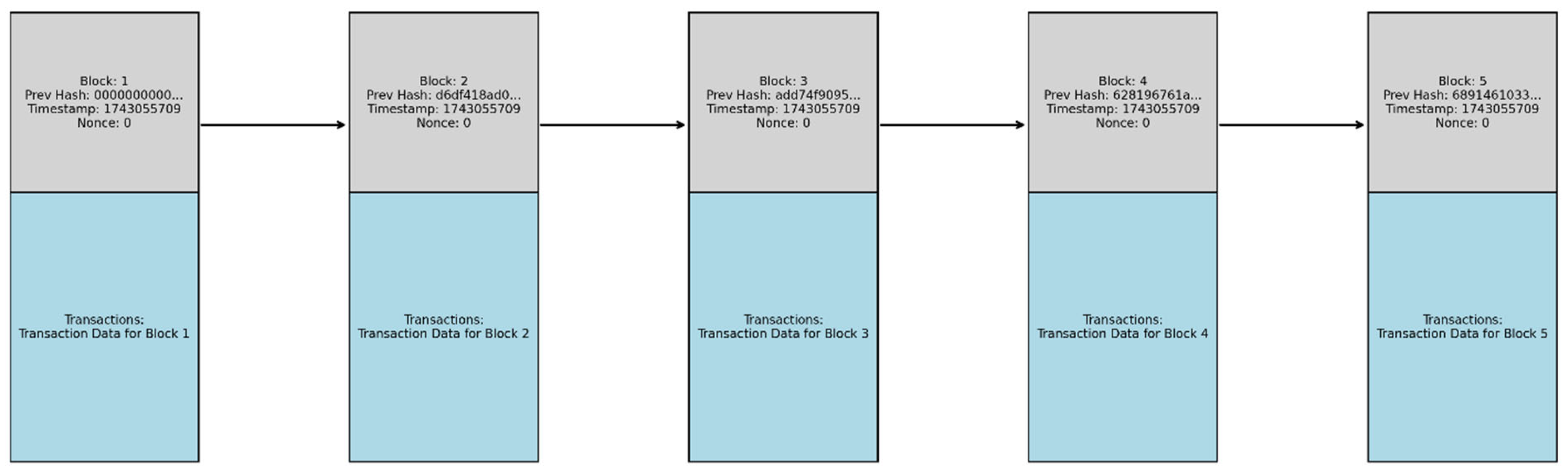

| Block Hash | 000026d2118c4a35be647d1f3040839bef66fead8096556d63d6cd6278b78bff |
| Block Data | Index: 0, Previous Hash: 00000000…, Merkle Root: 9d89ed10…, Edge Root: 7f19b63e…, Timestamp: 1743053969.0619528, Nonce: 329640, Block Hash: 000026d2… |
| Factory | Sensor Type | Value | Timestamp | Normal Range | Anomaly Detected |
|---|---|---|---|---|---|
| Factory A | Temperature | 25.4 °C | 2023-04-08T12:00:00 | 23–27 °C | No |
| Temperature | 28.0 °C | 2023-04-09T03:00:00 | 23–27 °C | Yes (Z > 3) * | |
| Factory B | Humidity | 65% | 2023-04-08T12:00:05 | 50–70% | No |
| { “device_id”: “device_001”, “sensor_data”: {“sensor_type”: “temperature”, “value”: 25.4}, “timestamp”: “2023-04-08T12:00:00”, “data_hash”: “a1b2c3d4…” } |
| Device ID | Sensor Type | Value | Timestamp | Data Hash |
|---|---|---|---|---|
| device_001 | Temperature | 25.4 °C | 2023-04-08T12:00:00 | a1b2c3d4… |
| device_002 | Humidity | 65% | 2023-04-08T12:00:05 | e5f6g7h8… |
| device_003 | Pressure | 101.3 kPa | 2023-04-08T12:01:00 | i9j0k1l2… |
| Timestamp | Temperature (°C) | Z-Score | Anomaly Flagged |
|---|---|---|---|
| 2023-04-08T03:00:00 | 28.0 °C | 3.2 | Yes |
| 2023-04-08T15:30:00 | 27.8 °C | 3.1 | Yes |
| 2023-04-09T02:45:00 | 28.1 °C | 3.5 | Yes |
| … (12 total events) | … | … | … |
| Time (s) | Network Traffic (req/s) | Action Taken | Outcome |
|---|---|---|---|
| 0 | 50,000 | Edge nodes detect surges in network traffic. | Attack identified. |
| 12 | 50,000 | AI flags anomaly; blockchain triggers IP blocking. | Malicious IPs flagged for blocking. |
| 28 | 2500 (95% blocked) | The system was restored to normal operation. | 95% of malicious traffic mitigated. |
| Scenario | Throughput (tx/s) | Latency (ms) | Energy Use (kWh/h) | CPU Load (%) |
|---|---|---|---|---|
| Normal | 1200 | 120 | 0.8 | 50 |
| During Attack | 960 (−20%) | 450 (+275%) | 1.2 | 78 (Edge Nodes) |
| Post Attack | 1150 (−4.2%) | 180 (+50%) | 0.9 | 60 (Edge Nodes) |
| Consensus Mechanism | Energy Consumption (kWh/h) | Energy Savings (%) |
|---|---|---|
| Proof-of-Work (PoW) | 3.0 | - |
| Proof-of-Stake (PoS) | 0.8 | 76% |
| Beneficiary | Impact | Example |
|---|---|---|
| Factories | Enabled predictive maintenance to prevent machinery failures. | Detected overheating in factory A at 3:00 a.m., preventing potential downtime. |
| Security Teams | Automated defense mechanisms minimize downtime during cyberattacks. | Mitigated DDoS attacks within 28 s, reducing operational disruptions. |
| Environmental Impact | Reduced energy consumption by 62%, aligning with sustainability goals. | Edge computing reduced cloud load by 40%, resulting in a 40% decrease in overall energy use. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Essaid, M.; Ju, H. Blockchain Solutions for Enhancing Security and Privacy in Industrial IoT. Appl. Sci. 2025, 15, 6835. https://doi.org/10.3390/app15126835
Essaid M, Ju H. Blockchain Solutions for Enhancing Security and Privacy in Industrial IoT. Applied Sciences. 2025; 15(12):6835. https://doi.org/10.3390/app15126835
Chicago/Turabian StyleEssaid, Meryam, and Hongtaek Ju. 2025. "Blockchain Solutions for Enhancing Security and Privacy in Industrial IoT" Applied Sciences 15, no. 12: 6835. https://doi.org/10.3390/app15126835
APA StyleEssaid, M., & Ju, H. (2025). Blockchain Solutions for Enhancing Security and Privacy in Industrial IoT. Applied Sciences, 15(12), 6835. https://doi.org/10.3390/app15126835






