Abstract
The incorporation of Driver Monitoring Systems (DMSs) in vehicles is fundamental to enhancing road safety by continuously assessing driver behavior and identifying signs of fatigue or distraction. However, as these technologies evolve, they also present considerable cybersecurity challenges. This research undertakes an extensive Threat Analysis and Risk Assessment (TARA) of DMSs, adhering to the ISO/SAE 21434 standard, to methodically detect and assess potential security threats. A total of 115 threats were recognized and classified into 95 low-risk, 16 medium-risk, and 4 high-risk scenarios, underscoring key vulnerabilities in data transmission, sensor reliability, and communication frameworks. To mitigate these risks, we suggest a range of countermeasures, including enhanced encryption techniques, stringent authentication protocols, and reinforced access control mechanisms, designed to strengthen the security posture of DMSs in practical applications. This study introduces a structured framework for evaluating and addressing cybersecurity threats in alignment with industry regulations, facilitating the dependable and safeguarded implementation of DMSs in future vehicle architectures while contributing to ongoing progress in automotive cybersecurity.
1. Introduction
In recent years, a growing number of intelligent motor vehicles have been equipped with complex systems designed to improve driving convenience and comfort. Motor vehicles remain one of the most widely used modes of transportation worldwide, with annual production surpassing 90 million vehicles. To provide better customer experiences, services are expected to grow in the coming years, driving Original Equipment Manufacturers (OEMs) to prioritize the development of autonomous driving technologies and intelligent mobility solutions. In response, many OEMs have developed vehicle monitoring and driving assistance systems to decrease the number of safety incidents [1]. Despite technological advances in vehicle automation and driver assistance, human errors, such as inattention, fatigue, and delayed reaction, remain a leading cause of traffic accidents. These issues are particularly pronounced in scenarios where drivers retain full or partial control of the vehicle, highlighting the need for systems that can continuously assess driver condition. The considerable number of accidents caused by human errors has led to the development of systems designed to monitor and evaluate driver conditions in real time. Human factors such as fatigue, distraction, or lack of concentration are difficult to predict and prevent through traditional safety measures, making advanced technological solutions necessary. Among these, Driver Monitoring Systems (DMSs) have emerged as a key enabling technology to reduce these risks through continuous observation of driver behavior and the provision of early warnings when unsafe conditions are detected [2]. However, integrating such systems is risky, especially regarding their vulnerabilities to cyberattacks. Several studies have shown that driver assistance systems, such as DMSs, are subject to a variety of threats, including adversarial attacks and Spoofing attempts, which can compromise the integrity of the monitoring systems and consequently driver safety [3,4]. Targeted attacks could interfere with sensors or introduce false alarms that distract the driver, increasing the risk of accidents even when the vehicle is not mechanically compromised. These vulnerabilities arise from the increasing use of interconnected technologies and artificial intelligence (AI) algorithms in vehicles, which expands the attack surface and introduces new risks. Given the critical role of DMSs in future autonomous and semi-autonomous vehicles, ensuring their cybersecurity has become a priority at both the academic and industrial levels. In this context, regulatory frameworks such as the International Organization for Standardization (ISO)/Society of Automotive Engineers (SAE) 21434 standard and threat modeling methodologies like STRIDE provide solid foundations for the structured identification, analysis, and mitigation of cybersecurity threats in automotive systems. However, the existing literature still lacks systematic studies that apply these frameworks rigorously to DMSs. Therefore, it is crucial to consider how possible cyberattacks could not only distract the driver but also inhibit the ability of a DMS to detect early signs of fatigue or distraction. In extreme scenarios, targeted attacks could even inhibit or manipulate warning systems, making the driver unaware of dangerous situations [3,5]. Although such attacks do not necessarily alter the mechanical operation of the vehicle, their influence on the ability of the DMS to properly monitor the driver could lead to accidents with serious consequences. This is why it is crucial to conduct a thorough analysis of the security threats associated with DMSs, following the guidelines provided by the ISO/SAE 21434 standard, which establishes the basic requirements for cybersecurity in vehicles [6]. A comprehensive Threat Analysis and Risk Assessment (TARA) is necessary to identify threat scenarios and propose effective mitigation measures to ensure driver safety and reduce the risk of distraction or human error incidents. Given their critical role in enhancing road safety, it is imperative to ensure that DMSs are designed and implemented in accordance with established standards and security best practices. Regulatory frameworks such as ISO/SAE 21434 and structured threat modeling methodologies like STRIDE offer systematic approaches for identifying, analyzing, and mitigating risks in automotive systems. Despite their relevance, the current literature lacks targeted applications of these frameworks specifically tailored to DMSs. In this regard, this research aims to perform a TARA specifically for DMSs. This study is based on the framework established by the ISO/SAE 21434 standard, focusing on identified threats and attack scenarios that could compromise the security of these systems. Using a systematic methodology, the objective is to identify the most critical threats and propose effective mitigation measures to ensure the security of DMSs in modern vehicles. This study makes the following contributions to the field of automotive cybersecurity, specifically concerning Driver Monitoring Systems:
- It provides a comprehensive Threat Analysis and Risk Assessment (TARA) tailored explicitly to a representative, modern DMS architecture, systematically applying the methodology outlined in the ISO/SAE 21434 standard;
- It identifies and categorizes a detailed set of 115 potential cybersecurity threats targeting various DMS components and dataflows, with a particular emphasis on analyzing risks related to the sensitive nature of driver biometric data and potential privacy violations (Information Disclosure);
- It proposes specific mitigation strategies designed to address the unique High- and Medium-risk vulnerabilities identified within the DMS, offering actionable insights to improve system security and driver privacy.
The organization of this paper is designed to provide a comprehensive and structured exploration of the challenges and solutions in the domain of DMS security. Each section builds on the previous one to create a cohesive narrative that systematically addresses the research objectives and findings. Section 2 reviews the related literature, situating the research within the broader context of existing studies. This section identifies the prevailing gaps in the field of DMS security and highlights the need for a systematic and targeted threat analysis. Section 3 details the research methodology, describing the systematic approach used to analyze and evaluate DMS architectures. This section includes the criteria for system selection and the formulation of research questions that guided the investigation, ensuring a solid foundation for the study. In Section 4, the design and functional features of DMSs are examined, with a particular focus on system architecture, data processing workflows, and sensor integration. This section establishes the technical foundation necessary to understand vulnerabilities and security challenges. Section 5 presents the TARA, the core contribution of this work. This section identifies and categorizes 115 potential threats to DMSs by applying the ISO/SAE 21434 standard and the STRIDE framework. It provides a detailed risk assessment, prioritizes vulnerabilities, and lays the groundwork for mitigation strategies. Based on the findings from the TARA, Section 6 proposes comprehensive mitigation strategies to address the identified risks. These include advanced authentication mechanisms, robust encryption protocols, and strict access control measures. The proposed solutions aim to improve the resilience of DMSs against a broad spectrum of security threats. Section 7 explores the application of the STRIDE framework to a DMS architecture. This section provides a detailed evaluation of critical system components, such as sensors, computational units, and data communication channels. It also incorporates visual aids and modeling techniques to clarify security challenges and validate the effectiveness of proposed countermeasures. Finally, Section 8 synthesizes the study findings, presenting their implications for the automotive industry. This section also outlines directions for future research, emphasizing the need for ongoing advancements in DMS security to address emerging threats and technological developments.
2. Related Work
This section examines existing research in driver monitoring systems, presenting an overview of current monitoring technologies and their safety aspects. The analysis covers various approaches and technologies developed to improve driver safety and system security.
2.1. Monitoring Technologies Overview
In recent years, the focus on improving vehicle safety has led to the development of various monitoring technologies that assess the condition of the driver and passenger compartments. These systems use multiple types of sensors, including image-based cameras, radar systems, eye-blink sensors, and chemical breath analysers, to detect potential driver impairment and alertness.
Su et al. [7] developed an approach using deep learning algorithms to process input from infrared cameras, focusing on critical indicators such as face detection, head pose estimation, eye state analysis, and gaze direction. These indicators are vital for evaluating whether a driver can take control of an autonomous system, especially in critical situations where human intervention may be necessary. In a different study, Joe et al. [8] presented a system that leverages continuous eye monitoring to detect signs of fatigue, particularly by calculating the aspect ratio of the eyes. Their approach analyzes blinking patterns and eye closure duration to identify drowsiness, triggering alerts to prevent potential accidents.
Lazaro et al. [9] explored radar-based systems as non-contact solutions to monitor both the driver and passengers within the vehicle. Their study used a Pulsed Coherent Radar (PCR) system operating at 60 GHz, demonstrating the ability to detect seat occupancy and estimate breathing rate by analyzing subtle body movements. This technology provides accurate detection even in the presence of car vibrations, highlighting its robustness in real-world conditions. Chen et al. [10] advanced this field further by using frequency-modulated continuous wave (FMCW) radar to generate point clouds for occupant monitoring. Their approach efficiently maps in-cabin environments, distinguishing between multiple passengers and their movements through advanced clustering and state machine algorithms.
Beyond image- and radar-based solutions, other sensor technologies contribute to road safety. Singh et al. [11] investigated the use of eye-blink sensors integrated with microcontrollers to detect driver drowsiness. Unlike camera-based systems, these sensors monitor eye closure duration without recording visual data, ensuring privacy. Ansari et al. [12] focused on breath analyzer systems integrated into vehicles to prevent drunk driving. Their system detects ethanol traces in the driver’s breath, disabling the vehicle and sending alerts with location details to designated contacts.
2.2. Security Aspects in Driver Monitoring Systems
The integration of DMSs in modern vehicles has become essential for enhancing driver safety and compliance with regulatory standards. As these systems increasingly rely on sensor data, artificial intelligence, and network connectivity, ensuring cybersecurity has become a critical challenge. While safety has been a predominant focus, fewer studies have rigorously addressed the cybersecurity aspects of DMSs, which are vital for protecting against unauthorized access and potential cyberattacks.
Pande et al. [13] presented an approach using the AM62A System-on-Chip (SoC) for monitoring drivers and passengers. Their architecture emphasizes security measures to protect sensitive in-cabin data and prevent system breaches. Given the increasing use of in-vehicle cameras, sensors, and Internet connectivity, the risks of cyberthreats—such as data theft, unauthorized system control, or communication disruption—are significant. The authors implement security features, including a dedicated hardware security module, cryptographic accelerators, and secure boot processes to enforce a root of trust. This approach aligns with automotive cybersecurity standards such as E-Safety Vehicle Intrusion Protection Applications and ISO/SAE 21434.
Mishra et al. [14] examined the challenges related to data privacy in DMSs. Their work highlights how the use of multiple cameras to monitor the driver and passengers raises concerns about capturing personally identifiable information (PII). How the accumulation of such sensitive data could expose occupants to privacy breaches if the system is compromised is discussed. However, they do not provide specific solutions for protecting against such risks.
The complexity of modern DMS architectures, which often integrate with ADAS and other networked components, increases the attack surface for potential adversaries. Pande et al. [13] address this by implementing encryption and hashing to protect data integrity, along with specialized hardware configurations that limit physical access to critical interfaces, such as General Purpose Input/Output (GPIO) and Joint-Test Action Group (JTAG) ports. Their work also introduces the use of cryptographic keys injected during the manufacturing process to increase the resilience of the system.
2.3. Comparison of Contributions
Table 1 provides a comparative analysis of features found in various DMS implementations from the reviewed literature. It categorizes studies based on their focus on key metrics analyzed (e.g., security, general safety, and performance) and the technologies used (e.g., ML models, cameras, sensors, and communication protocols).

Table 1.
Comparison of features in Driver Monitoring System (DMS) implementations. This table categorizes the reviewed studies based on key metrics (e.g., security, safety, and performance) and technologies (e.g., ML models, cameras, sensors, and communication protocols).
A checkmark (✓) indicates the presence of a feature or technology in a specific study, and a blank cell indicates its absence. The analyzed features can be categorized into two main groups:
- Addressed metrics: These characteristics define the robustness of a DMS, encompassing the following:
- –
- Security: This refers to the protection of the vehicle environment from attackers who could cause unauthorized access or damage. Notably, the analysis reveals that most reviewed papers contained no reference to security, highlighting a significant gap in current research;
- –
- General safety: General safety refers to protection against physical harm in the car in case of an accident or a malfunction. This metric appears consistently across most implementations, indicating its primary importance in DMS design;
- –
- Performance: Performance evaluates how well the DMS realizes its intended function, such as alerting an inattentive driver in a timely manner. The table shows significant attention to this metric.
- Technologies used: The analysis reveals diverse technological approaches across the reviewed papers:
- –
- ML model: An ML model is used to monitor the driver. This represents a critical piece of the architecture, as drivers exhibit varied facial features, making it challenging for a generic program to assess driver attentiveness accurately;
- –
- Camera: Cameras capture images of the driver and provide input to ML algorithms. The implementations vary between infrared cameras, which excel in low-light conditions, and visible light cameras, which offer more detailed image data but require adequate lighting. Some systems combine both technologies to enhance performance;
- –
- Radar: Radar technology, using radio waves for object detection, appears as an alternative or complement to camera-based systems in several implementations;
- –
- Driver availability sensor: This specialized system determines whether a driver maintains sufficient alertness to operate the vehicle safely;
- –
- Thermal sensor: These sensors utilize infrared radiation, complementing camera or radar systems by providing additional data to the ML model;
- –
- Communication: The analysis reveals various communication technologies across implementations, each with distinct security implications:
- *
- GPIO: These pins facilitate communication with the microcontroller and provide security by requiring physical access;
- *
- Controller Area Network (CAN) bus: This automotive communication protocol presents moderate security concerns due to its vulnerability to local attacks;
- *
- Internet of Things (IoT): IoT integration represents one of the highest security risks due to potential remote access vulnerabilities;
- *
- Cloud: Cloud infrastructure provides functionality but also introduces potential security issues due to Internet connectivity;
- *
- Ethernet: This high-bandwidth protocol supports real-time sensor communications but introduces network-based security risks;
- *
- Serial Peripheral Interface (SPI): This synchronous short-distance protocol offers relative security through its local-only accessibility;
- *
- Universal Asynchronous Receiver Transmitter (UART): Similar to SPI, this two-way protocol maintains security through limited physical access requirements.
2.4. Gaps in Existing Research
The literature review reveals that current DMS research predominantly focuses on system architectures and functionality exploration. A significant gap exists in comprehensive security analysis, with Pande et al. [13] representing the primary contribution in this area. Most existing studies lack a thorough examination of security vulnerabilities, particularly regarding information flow through the system. The impact of different communication protocols on the security of DMSs remains unexplored, despite their critical role in system security.
User experience and system acceptance in continuous driver monitoring represent another understudied area. While this aspect warrants deeper investigation, the present work addresses the technical gaps through a detailed analysis of a generic DMS architecture, with particular attention paid to information flow paths.
While recent research has explored the design and performance of Driver Monitoring Systems (DMSs), the cybersecurity dimension has often been addressed only at a high level, without systematic threat modeling or alignment with established standards such as ISO/SAE 21434. Some studies focus primarily on hardware-based monitoring techniques (e.g., eye tracking, facial recognition, or heart-rate sensors), emphasizing functionality and usability but overlooking potential vulnerabilities in data processing and communication layers.
In contrast, this study contributes a detailed Threat Analysis and Risk Assessment (TARA) tailored to a representative DMS architecture, integrating the STRIDE threat modeling framework to systematically categorize and prioritize risks. Unlike prior works that either discuss security conceptually or focus on isolated threats, our approach provides a structured methodology for identifying and mitigating realistic attack scenarios across system components and dataflows. Moreover, we highlight privacy concerns associated with the handling of biometric driver data, an aspect often under-represented in DMS research.
This work does not aim to propose a novel monitoring modality or sensing solution. Instead, it focuses on enhancing the resilience of existing architectures through context-aware cybersecurity analysis, offering practical guidance aligned with industry standards for safe DMS deployment in automotive environments. Building on the gaps identified in current DMS research—particularly regarding systematic threat modeling and protocol-specific vulnerabilities—the next section introduces the methodological framework adopted to carry out a comprehensive security assessment aligned with ISO/SAE 21434.
3. Research Methodology
To address the research gaps identified in Section 2, this section presents the structured methodological framework adopted to investigate the cybersecurity threats affecting DMSs. A rigorous and systematic approach was applied to ensure a comprehensive analysis of system architectures, vulnerabilities, and associated risks. As illustrated in Figure 1, the proposed methodology is organized into sequential phases, from system selection to risk mitigation. This framework provides the foundation for the technical and analytical depth necessary to evaluate the security posture of modern DMS implementations.
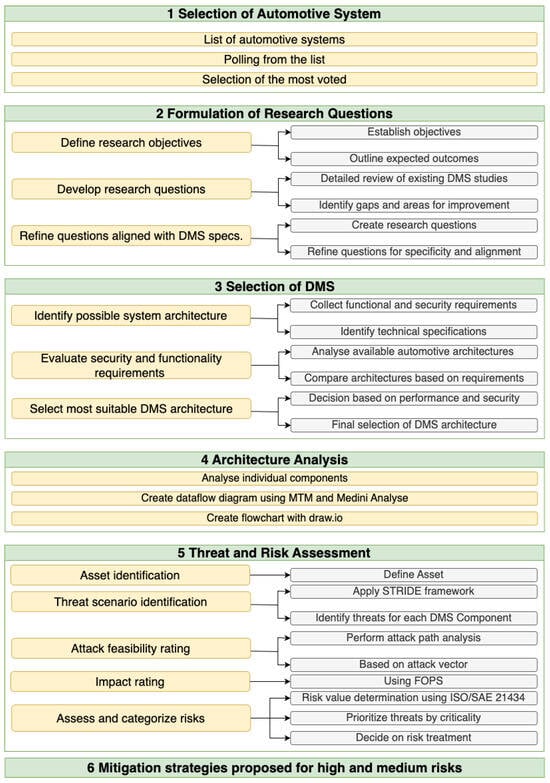
Figure 1.
Workflow showing the main phases of the research process.
3.1. Selection of Automotive System
The initial phase involved identifying a relevant automotive system to focus the cybersecurity investigation. Due to the broad scope of modern vehicle subsystems, a comparative evaluation was carried out across five categories: Advanced Driver Assistance Systems (ADASs), infotainment systems, DMSs, predictive maintenance, and automatic emergency braking. These categories were assessed based on their technological maturity, adoption trends in the automotive industry, and the relevance of cybersecurity concerns, as outlined by ISO/SAE 21434 [6]. While all considered systems present important security challenges, DMSs were selected as the target of this study due to their increasing integration in modern vehicles, their reliance on biometric data processing, and the critical implications of cybersecurity breaches on driver safety and privacy. Among the candidate domains, DMSs offer a particularly rich attack surface, including real-time sensor input, AI-based decision modules, and in-vehicle communication protocols, all of which make them ideal for a structured threat modeling and risk assessment exercise. To support the architectural and threat modeling analysis, a structured literature review was conducted to identify relevant studies on DMSs published between 2020 and 2024. The goal was to extract architectural models and implementation details from credible sources, ensuring a comprehensive understanding of current design practices and security concerns. The selection and data extraction process is summarized in Figure 2. The process began with the identification of primary studies through manual searches in key scientific databases, including Google Scholar, IEEE Xplore, ACM Digital Library, and ScienceDirect. The search targeted peer-reviewed publications within the fields of automotive systems, cybersecurity, and artificial intelligence. A total of 30 publications were retrieved across these databases: A total of 10 from Google Scholar, 14 from IEEE Xplore, 3 from ACM, and 3 from ScienceDirect. Following the initial search, a relevance screening was conducted based on title and abstract review. Studies were retained if they were published after 2020, addressed the design or implementation of DMSs, and related specifically to automotive systems. Publications that did not meet these criteria were excluded from further consideration. After this stage, 25 studies remained eligible for full-text analysis. Each of the 25 remaining studies was then reviewed in detail to assess methodological rigor and technical relevance. The inclusion criteria at this stage focused on the presence of architectural schematics, component-level descriptions, and discussions of dataflow or system integration. Studies that lacked such content, or that were limited to general surveys without in-depth analysis of specific architectures, were excluded. Ultimately, 21 publications satisfied all conditions and were included in the final corpus for data extraction. Key information concerning component configurations, system workflows, communication protocols, sensor integration, and existing cybersecurity mechanisms was extracted from these studies. This knowledge base informed the selection of a representative DMS architecture and provided input for the subsequent threat modeling and risk assessment phases.

Figure 2.
Workflow of the study selection and data extraction process.
3.2. Formulation of Research Questions
Oriented by the framework in Figure 1, this phase aimed to define the analytical scope by formulating precise research questions. The process began with a review of the existing literature to identify open problems in the security of DMSs, including architectural blind spots, risk exposure, and under-addressed attack surfaces. The main objective was to select a representative DMS architecture that encapsulates critical safety functionalities (e.g., distraction detection and biometric analysis) and to assess its exposure to cybersecurity risks. The research questions serve as the conceptual foundation of this study. They define the investigative scope and guide the systematic evaluation of DMS architectures, component integration, and associated security risks. Each question addresses a specific dimension relevant to the secure design and assessment of driver monitoring technologies:
- RQ1: Which components and functionalities are commonly integrated into contemporary Driver Monitoring Systems?
- RQ2: What are the communication mechanisms between these components within the broader vehicle architecture?
- RQ3: What architectural variations exist among current DMS implementations, and how do they differ in terms of performance, integration, and reliability?
- RQ4: What cybersecurity risks are associated with different DMS configurations, and how can these threats be systematically addressed?
- RQ5: Which DMS architecture demonstrates the most favorable balance among functionality, security, and integration with vehicle systems?
These questions provide a structured framework for assessing DMS solutions in terms of design robustness, architectural soundness, and threat mitigation potential.
3.3. Selection of DMS Architecture
The selection of a concrete DMS architecture was essential to support a contextualized and realistic threat assessment. A comparative analysis was performed on architectures documented in the recent literature, prioritizing solutions that integrated core safety-critical capabilities such as driver behavior tracking, alert mechanisms, and fail-safe triggers.
Following the formulation of the research questions, the study proceeded with a comparative evaluation of several DMS architectures to identify the most suitable candidate for analysis. This selection was informed by three criteria: Component integration: The degree to which the system incorporated essential functionalities such as biometric sensing, distraction recognition, and driver intent analysis. Security posture: Evaluation of the system’s exposure to typical threat classes using the STRIDE methodology (Figure 3). Standards compliance: Adherence to ISO/SAE 21434 guidelines for cybersecurity in automotive systems. The threat modeling process employed in this phase relied on STRIDE to detect vulnerabilities such as Spoofing, Tampering, Repudiation, and data leakage. Tools such as Ansys Medini Analyze version 2024 R1 were used to construct threat models, enabling a precise mapping of security concerns across the system architecture. The selected architecture demonstrated strong integration of safety-critical components and sufficient modularity to support mitigation strategies, thereby qualifying it as the reference design for the remainder of the study.
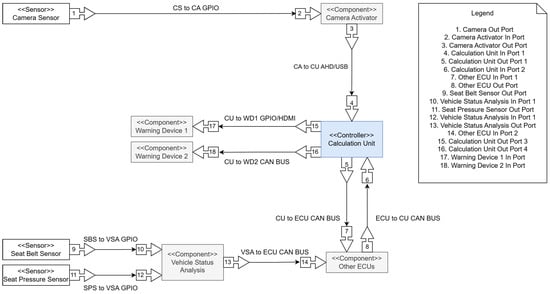
Figure 3.
STRIDE threat-modeling diagram, created using Ansys Medini Analyze.
3.4. Architecture Analysis
This phase focused on dissecting the selected DMS architecture to understand its internal components, operational flow, and exposure to cyberthreats. Key elements such as data collection modules, communication protocols, and access points were examined. Particular attention was given to safety-related sensors (e.g., seat pressure and seat belt status), which play a pivotal role in contextualizing driver behavior. Threat-modeling techniques were then applied to the identified system components to characterize potential security weaknesses. Visual models such as dataflow diagrams were created using Ansys Medini Analyze and Microsoft Threat Modeling Tool (MTM), enabling a detailed representation of asset interconnections and communication pathways. These models facilitated the identification of critical zones susceptible to attack vectors or data compromise. A complete version of these threat modeling diagrams, including the STRIDE model created with Medini Analyze, is provided in the Supplementary Materials.
3.5. Threat and Risk Assessment
The TARA phase adopted a standards-based approach to identify, classify, and evaluate threats targeting the selected DMS architecture. Using Ansys Medini Analyze, the architectural components and dataflows were modeled, generating an initial set of relevant threats through semi-automated analysis functions. Each threat was exported into a structured Excel framework for in-depth evaluation. This framework enabled a multidimensional risk assessment based on the following: Impact factors, including implications for driver safety, economic cost, operational continuity, and data protection compliance; and feasibility criteria, assessing attack complexity, required capabilities, and likelihood of exploitation. The resulting scores were aggregated into an overall risk level using a quantitative matrix, aligning with ISO/SAE 21434 recommendations. The risk treatment strategies were then determined, including mitigation, acceptance, transfer, or avoidance. Each treatment decision was accompanied by a detailed justification and proposed countermeasures. Throughout the analysis, STRIDE classification was applied to categorize each threat scenario. The tools (Medini Analyze and MTM) were used iteratively to validate threat propagation paths and visualize the potential attacker entry points and their impact on the system.
3.6. Mitigation Strategies for High and Medium Risks
Based on the output of the TARA, a dedicated phase focused on defining mitigation strategies for high- and medium-severity threats was conducted. These strategies included technical countermeasures such as secure communication protocols, hardware-based authentication modules, encryption schemes, and access control policies. The goal was to reduce both the probability of successful exploitation and the potential impact on safety and compliance.
4. DMS Architecture and Functional Overview
In this section, we present the architecture of the DMS selected for analysis in this study. We begin by describing its core components, including sensors, processing units, and communication modules, along with their functional roles within the system. Particular attention is given to the interactions among these elements and the dataflows that enable continuous driver state monitoring. Understanding the architecture is essential for identifying potential cybersecurity vulnerabilities, which will be systematically assessed in the following TARA section.
4.1. Definition and Functionality
A DMS serves the role of a critical safety component in modern vehicles, designed to continuously assess driver focus and responsiveness to the environment. By analyzing specific behaviors and conditions such as gaze, head position, and alertness levels, a DMS actively works to mitigate potential hazards by identifying distracted or impaired driving. With advancements in artificial intelligence, ML, and sensor technologies, today’s DMS solutions have become increasingly sophisticated, allowing for real-time, accurate monitoring that not only identifies potentially dangerous driver states but also interfaces with the vehicle’s safety mechanisms to respond appropriately. In doing so, the DMS is essential in enhancing road safety and supporting driver and passenger welfare.
4.2. Data Processing
A DMS needs specialized modules that communicate with the sensors and each other to process the data extracted from the driver.
4.2.1. Camera Activator
The Camera Activator is a module that acts as the connecting element between the central calculation unit and the IR camera sensor. This activator triggers the collection of images taken by the camera at a set interval. The raw data are then processed into pictures that can be used in image recognition software.
4.2.2. Vehicle Status Analysis
The other module is the VSA, which acts as a driver recognition system. The VSA unit monitors and assesses the real-time status of vehicle occupants through a variety of sensors. The output from the seatbelt sensor is combined with the seat pressure sensor to identify driver and passenger presence, seat posture, and other factors. This helps to analyse whether the driver is adequately restrained and in the correct position to handle the vehicle [9]. The information is also shared with the rest of the vehicle’s ECU on the CAN bus by the VSA to add to the overall safety and functionality of the vehicle’s monitoring system [10].
4.2.3. Calculation Unit
The Calculation Unit acts as the central hub for all information and all dataflows incoming from the sensors. It also acts as the key decision maker for all actions performed by the system. In the original architecture proposed in [7], this device is an embedded platform containing an Nvidia JETSON XAVIER NX processing unit. This unit was designed for use in autonomous machines and is capable of accessing up to six cameras and numerous sensors using a wide array of serial and network connections, like Peripheral Component Interconnect Express (PCIe), Universal Serial Bus (USB), Gigabit-Ethernet, CAN, SPI, and UART [28]. The Camera Activator uses USB for data transmission to the Calculation Unit. The NVIDIA JETSON features the “Deep Learning Accelerator (DLA)” [29] technology, which supports real-time data processing in the AI model pipe, as proposed in the architecture. The image data from the camera is used to calculate the head pose and estimate the gaze and eye state. In addition, the configuration of this device is stored, allowing interaction with the system via a user interface. The computing unit acts as the ECU of the DMS and is connected to the other ECUs in the vehicle via the CAN bus.
4.2.4. AI Component
The AI-powered module is responsible for continuously assessing driver alertness using the Mediapipe face model. It processes real-time visual input, specifically facial landmarks, head orientation, gaze direction, and eye opening to determine cognitive states such as focus, distraction, or drowsiness [30]. Pre-processed video frames from the in-cabin camera serve as input to the AI model, which applies machine learning algorithms to classify the driver’s state. The model’s outputs inform higher-level safety decisions by indicating whether the driver is alert, distracted, or potentially incapacitated [7].
4.2.5. Communication
A DMS requires robust and efficient communication among its various components to ensure accurate and timely safety interventions. These systems rely on multiple communication interfaces to facilitate high-speed and reliable data exchange between sensors, processing units, and actuators. A key element is the integration of the Calculation Unit (CU) with other ECU components via the Controller Area Network (CAN) bus, which serves as a standardized backbone for real-time data transfer in automotive environments. This architecture enables the coordination of safety-critical tasks, ensuring consistent communication between modules. In addition to CAN, specialized interfaces are used to handle high-bandwidth visual data. The Camera Serial Interface Receiver (CSI-RX), for instance, supports the reception of RGB-IR camera streams. This separation enables parallel processing: infrared (IR) data are used for real-time driver attentiveness analysis (e.g., eye-blink rate and yawning frequency), while RGB data feeds deep learning models for occupant detection and classification, which operate at lower sampling rates [13]. The processed output, such as alerts or diagnostic messages, is transmitted over high-speed interfaces like the Reduced Gigabit Media Independent Interface (RGMII) or Reduced Media Independent Interface (RMII), which are used to forward encoded images or alerts to external modules or data loggers [13]. Additionally, GPIO interfaces support low-level tasks such as sensor triggering and data relay to the CU or Vehicle Safety Application (VSA) unit [31]. UART interfaces support low-latency, serial communication between lightweight processing units within the DMS, enabling the consistent transmission of biometric signals such as heart rate or eye-blink metrics at synchronized baud rates [17]. Additionally, USB interfaces offer a dual function by combining data transmission with power delivery over a single cable, reducing wiring complexity and supporting compact, energy-efficient designs suitable for embedded automotive applications [17]. Lastly, Ethernet may be employed as a high-throughput link between in-cabin cameras and processing units, supporting continuous image transfer with low latency and high reliability. This is particularly useful for real-time driver behavior monitoring and video streaming to centralized systems [17].
4.2.6. System Calibration and User Interface Integration
To ensure accurate interpretation of driver behavior under varying conditions, the system includes calibration mechanisms and an integrated user interface for adjusting AI parameters and sensor configurations. These tools allow the DMS to adapt to a wide range of driver postures, lighting scenarios, and cabin environments, ensuring consistent detection of alertness and distraction cues. Calibration is essential to match sensor inputs such as camera positioning, sensitivity thresholds, and environmental compensation to real-world driving conditions, minimising false detections and increasing robustness [21]. The user interface facilitates real-time monitoring by displaying system status, issuing alerts, and providing diagnostic feedback to both drivers and technicians. In addition, the interface allows for the fine-tuning of operational parameters such as gaze tracking sensitivity and alert delay settings, enabling customization based on driving context and regulatory requirements. This adaptability supports continuous system optimization, ensuring reliable long-term performance while maintaining a user-friendly experience [15].
4.3. Overview of Driver Monitoring System
The architecture described in this paper is based on the research conducted by Su et al. [7] on an image-based driver monitoring system, which is designed to enhance the safety and reliability of autonomous driving by continuously assessing the driver’s condition and readiness to take control of the vehicle [7]. An overview of the system architecture can be seen in Figure 4. The system integrates multiple components, including sensing modules, a robust computing platform, and an alert mechanism, to ensure that the driver remains alert and available according to established safety standards, such as UN R157 [7]. The architecture leverages advanced deep learning algorithms running on an embedded platform to perform real-time analysis of driver behaviors, such as head posture, eye state, and gaze direction. This integrated approach enables the system to detect and respond to signs of driver inattention or fatigue, providing timely warnings to prevent accidents.
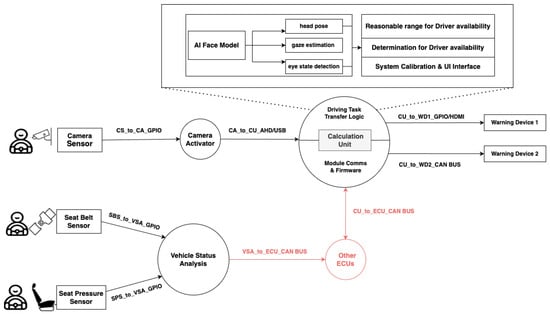
Figure 4.
System architecture diagram based on [7]. The component highlighted in red was added to facilitate communication.
4.4. Sensors and Hardware Modules
The system architecture relies on an array of sensors to monitor the driver’s status with high accuracy and reliability. Among these, the seat pressure sensor is crucial in detecting whether the driver’s seat is occupied. This sensor is a reliable method to confirm the presence of a driver, as it is unlikely that any other object would exert similar pressure on the seat during vehicle operation. Additionally, the seat belt sensor, another widely used component in modern vehicles, ensures that the driver is adhering to safety protocols by wearing the seat belt. The pressure sensor sends a HIGH signal above a specified pressure on the driver’s seat; otherwise, it is LOW. The same is valid for the seat belt sensor, which sends a HIGH signal when the seat belt lock is closed and a LOW signal when the seat belt lock is open. However, the most critical element of the sensing module is the infrared (IR) camera mounted above the dashboard and aimed directly at the driver’s face. This camera is the primary input for the system’s advanced image-based monitoring. It features a resolution of 720P and a horizontal viewing angle of approximately 70 degrees, ensuring comprehensive coverage of the driver’s facial area. In addition, the camera is equipped with an IR fill light, allowing it to function effectively in various lighting conditions, including low-light environments.
The dataflows of the sensors mentioned above are presented below:
4.4.1. Cameras
The process initiates with a start command, meaning that the engine is powered on, so the camera sensor starts capturing visual data, including the driver’s face. These data are in the form of images and include information about the driver’s head posture, gaze direction, and eye state. An overview of this process is shown in Figure 5. Once the sensor collects data, it is sent to the Camera Activator, a preliminary filter based on motion detection and gaze estimation. Then, the flagged data are forwarded to the Calculation Unit, the core hub where complex analyses are made, for in-depth processing. Based on the decision outcome, the data can be routed through two different pathways:
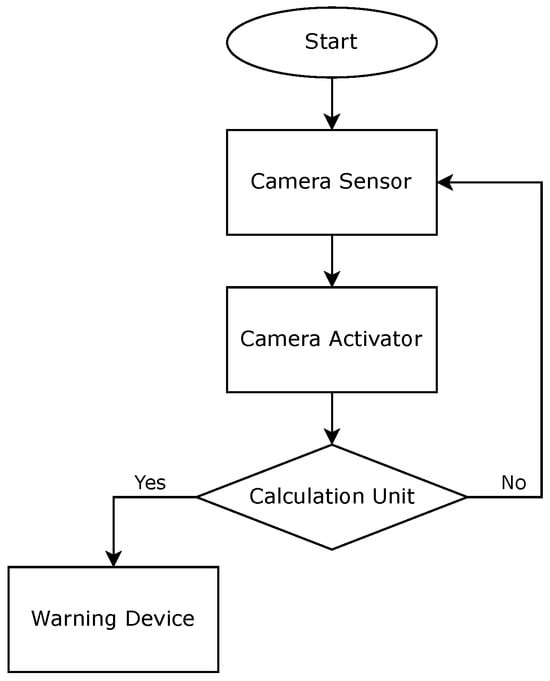
Figure 5.
Logical diagram of the camera sensor.
- The “Yes” path means that action is required: The data indicate that the driver is not attentive (behaving abnormally), and the system will set off the warning device that will alert the driver;
- The “No” path means that no action is required: The data indicate that the driver is attentive, and the system prepares for new data acquisition, maintaining a continuous operational loop.
4.4.2. Pressure Sensors
The process begins with the system’s initialization, marked by the start command, meaning that the engine is powered on and the Seat Pressure Sensor has started continuously detecting an occupant on the driver seat. An overview of this process is shown in Figure 6. Once the sensor detects the driver, it transmits data to the VSA. Here, the system determines whether the pressure detected corresponds to a typical occupant and distinguishes between a person and other objects. The filtered information is then relayed to other ECU units for further analysis, including correlation with other systems or forwarding to the Calculation Unit. Based on the decision outcome, the data can be routed through two different pathways:
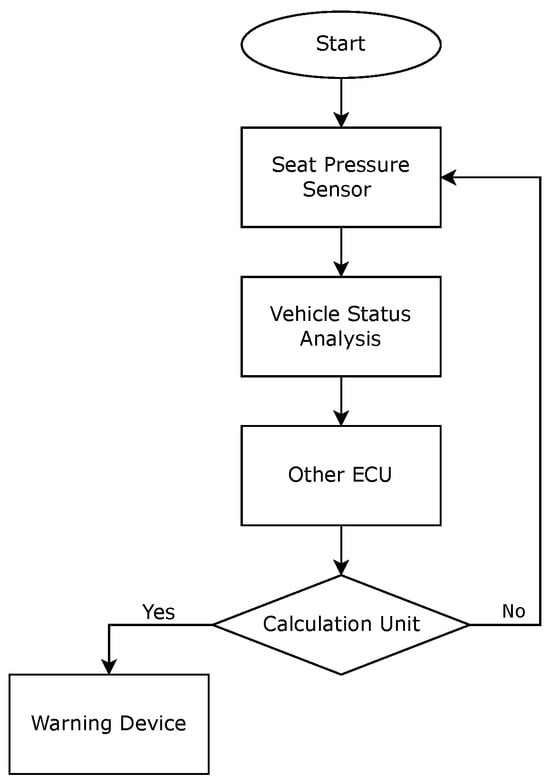
Figure 6.
Logical diagram of the seat pressure sensor.
- The “Yes” path means that action is required: The data indicate a risk, so the system will set off the warning device that will alert the driver;
- The “No” path means that no action is required: The data indicate no immediate risk, and the system prepares for new data acquisition, maintaining a continuous operational loop.
4.4.3. Seatbelt Sensors
The seatbelt monitoring system activates immediately upon engine start, continuously monitoring the engagement status of driver restraints. Collected status data are analyzed by the VSA in correlation with vehicle operational parameters. An overview of this process is shown in Figure 7 These integrated data are then transmitted to the appropriate ECU components for safety protocol verification. Based on the comprehensive risk assessment, the following applies:
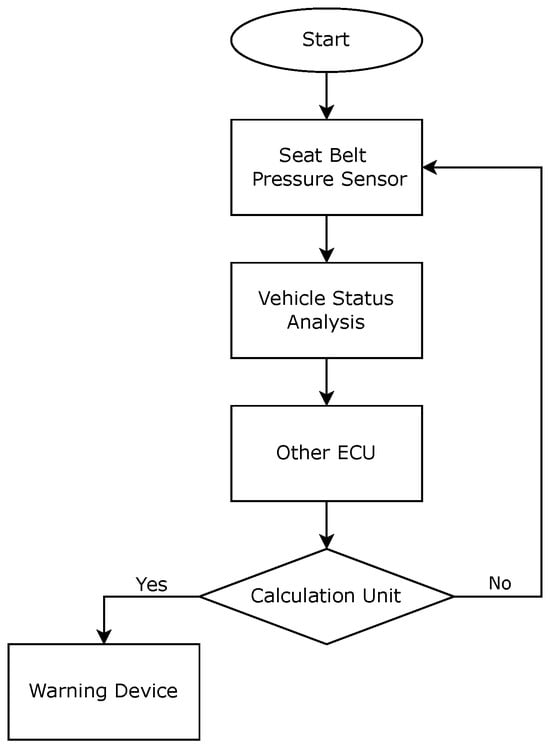
Figure 7.
Logical diagram of the seat belt sensor.
- The “Yes” path means that action is required: The data indicate a risk, and then the system outputs to the warning device, which is crucial for drawing the user’s attention;
- The “No” path means no action is required: The data indicate no immediate risk, and the system prepares for new data acquisition, maintaining a continuous operational loop.
4.4.4. Warning Devices
Other notable modules are the warning devices. The system has two warning devices, one connected to the computer unit via High Definition Multimedia Interface (HDMI) and the other via a CAN bus. The main function of warning devices is to call the driver’s attention to a detected fault state. According to the proposed architecture, one of the warning devices is a horn that produces an alerting sound, and the other is a simple warning light. For the data to be collected and utilized, the numerous sensors are connected to two different data processing modules via GPIO connection.
5. Threat Analysis and Risk Assessment
DMSs are complex systems that require rigorous analysis to ensure their resilience against potential threats. TARA provides a structured approach to identifying, evaluating, and mitigating risks. It helps to systematically assess the security posture of a DMS, ensuring the system is protected against the most critical vulnerabilities. This methodology is integrated with the STRIDE framework to identify and categorize various types of threats.
TARA is a cybersecurity methodology designed to evaluate the risks associated with each potential threat. Unlike traditional methods that focus solely on identifying threats, TARA takes a more holistic approach by evaluating the severity of each threat and its potential impact on the system. This enables system architects and security professionals to prioritize mitigations based on the most critical vulnerabilities, ensuring a robust security architecture.
Within the TARA process for DMSs, the STRIDE threat-modeling framework is employed to systematically categorize potential threats into six distinct classes, each aligned with key cybersecurity principles such as confidentiality, integrity, availability, authentication, non-Repudiation, and authorization:
- Spoofing: Unauthorized entities impersonate legitimate users or devices, often leveraging stolen credentials;
- Tampering: Malicious modification of data or components, undermining system integrity;
- Repudiation: Actions are performed without traceability, preventing accountability;
- Information Disclosure: Sensitive data is exposed to unauthorized parties, compromising confidentiality;
- Denial of Service (DoS): Attacks that disrupt service availability by overwhelming system resources;
- Elevation of Privilege: Gaining unauthorized access to higher system permissions, enabling broader control or damage.
By utilizing STRIDE within TARA, we can effectively assess the security risks associated with a DMS and take the necessary steps to mitigate them. To ensure a structured and reliable threat analysis, we employed a combination of software tools tailored to different phases of the assessment.
The primary tool used was Ansys Medini Analysis, which was chosen for its robust capabilities in conducting risk and hazard analysis within the automotive context. This tool facilitated the structured identification of system assets, allowing us to map critical components such as sensors, actuators, ports, and dataflows. Ansys Medini enabled the automatic generation of threat lists based on the defined system architecture and allowed us to apply the STRIDE framework systematically to each identified asset.
Furthermore, the Microsoft Threat Modeling Tool was used to represent the system architecture visually, identifying dataflows and potential entry points for malicious actors. This tool was particularly valuable for creating threat diagrams that depicted the relationships between system components and potential vulnerabilities.
5.1. Threat Identification Process
The approach combined multiple methodologies to ensure a comprehensive and credible threat assessment. This included the use of Ansys Medini Analysis for asset identification, the STRIDE framework for threat categorization, and the integration of expert judgment to validate the identified risks. The combination of software tools, structured methodologies, and domain expertise enabled a systematic and robust evaluation of potential vulnerabilities within the DMS architecture. The threats were initially identified using two industry-standard tools: Ansys Medini Analyze and Microsoft Threat Modeling Tool (MTMT). These tools enabled system-level modeling of assets and threat surfaces. The output was then organized into a structured spreadsheet (Microsoft Excel), which allowed for manual classification under STRIDE categories and mapping to specific components (e.g., sensors, ECUs, and ports). Each row in the spreadsheet included the threat description, potential attack vector, STRIDE category, and associated component. The Excel file provided in the Supplementary Materials includes the complete list of identified threats along with their classification and quantitative risk assessment according to the TARA methodology.
Identifying threats in a DMS using TARA involves several steps, beginning with identifying critical assets in the system. These assets include hardware components (sensors, cameras, and actuators), software components (data processing units), and communication channels. Once these assets are identified, the next step is to evaluate how malicious actors could attack or exploit them.
For example, sensors could be spoofed by sending false data to the system, and dataflows could be intercepted and manipulated. The attack vectors are then analyzed, considering potential entry points for an attacker, such as remote access or physical access to system components. Each identified threat is assigned an impact rating based on its potential effects on safety, privacy, and system functionality.
The risk evaluation process used a structured methodology based on peer review among participants and historical data. Furthermore, several rounds of analysis were conducted to validate and enhance the robustness of the assessment. Each threat was analyzed by identifying its attack vector, assumptions, and potential attack paths. Severity levels were determined by evaluating the threat’s safety, financial, operational, privacy, and legislative impacts using a standardized scale (negligible, moderate, major, and severe). These factors were combined to calculate a risk value based on feasibility and overall impact, following ISO/SAE 21434 recommendations. An automated tool was employed to ensure consistency and transparency in calculations, integrating expert inputs with predefined risk assessment formulas.
The number of threats identified for a given system can be calculated using the following equation:
where is the number of components of a particular type (e.g., processes, ports, etc.), and is the number of possible attacks that could affect that component. This allows for a comprehensive analysis of the total number of threats present within the system.
5.2. Overview of System Components and Threats
A DMS consists of several critical components, each susceptible to specific threats. These components include the following:
- Processes: These are the core functional units responsible for processing sensor data and making decisions based on that information. Processes are highly vulnerable to all six STRIDE threat categories because they are central to the system’s operation;
- Sensors: These collect data on driver behavior and environmental conditions, such as steering input and facial recognition. Sensors can be targeted by Spoofing attacks or tampered with to deliver incorrect data to the system;
- Actuators: These devices, such as steering systems and brakes, respond to the system’s decisions and influence vehicle operation. Actuators are vulnerable to Tampering, where unauthorized changes could lead to dangerous vehicle behavior;
- Dataflows: Data transmission between components, from sensors to the processing unit, is crucial for system operation. These flows must maintain confidentiality, integrity, and availability to prevent data interception and Tampering;
- Ports: These are the physical or logical entry points through which external devices and systems communicate with the DMS. Ports are at risk of DoS attacks and unauthorized access.
The total number of threats in the system is computed by categorizing each component and determining the potential attacks it might face. For example, processes are susceptible to all six STRIDE categories, ports are vulnerable to three, and data stores need to follow the three Confidentiality, Integrity, and Availability (CIA) principles. Using this method, the total number of threats in the system was calculated to be 115, consistent with the findings from running the analysis using Ansys Medini Analyse.
5.3. Mitigation Strategies
A combination of technical, organizational, and procedural measures is necessary to mitigate the identified threats. The DMS must implement strong authentication mechanisms to prevent Spoofing. Multi-factor authentication (MFA) and biometric verification ensure that only legitimate users and components can access the system, thereby reducing the risk of impersonation. These methods are crucial for protecting sensitive data and ensuring only authorized entities interact with the system.
Tampering, which involves the unauthorized modification of data or system components, can be addressed through robust cryptographic measures. All data in transit and at rest should be encrypted using advanced encryption protocols, ensuring that they cannot be altered or misused even if the data are intercepted. Additionally, tamper-resistant hardware can protect critical components such as sensors and processors, making it significantly more difficult for attackers to modify the system’s behavior.
To safeguard against Information Disclosure, all sensitive data must be encrypted during transmission and stored within the system. This prevents unauthorized access and ensures that only those with the appropriate credentials can retrieve sensitive driver and vehicle data. Furthermore, implementing strict access control measures ensures that only authorized users are granted access to specific system components or data, limiting the risk of exposure.
DoS attacks, which seek to disrupt the system’s availability by overwhelming it with malicious requests, can be mitigated through rate-limiting and redundancy strategies. By applying rate-limiting mechanisms, the system can prevent excessive requests from overloading the system. Additionally, the system architecture should incorporate failover mechanisms and redundant components to ensure continued operation in case of an attack, thus maintaining DMS availability and reliability.
Finally, role-based access control (RBAC) and the principle of least privilege should be enforced across the system to prevent the Elevation of Privilege. Each user and process must only have access to the resources and functions necessary for their roles. This limits the potential damage an attacker can cause if they gain unauthorized access to the system, as their privileges would be restricted to a minimal set of actions.
Together, these strategies form a comprehensive approach to securing the DMS against the full range of identified threats, ensuring the system operates reliably and securely.
5.4. Visual Representation of Threat Analysis
The analysis of the DMS architecture was visualized using the Microsoft Threat Modeling Tool, providing a clear representation of the system’s components and their interactions. Figure 8 shows the architecture diagram, which includes critical elements such as sensors, actuators, and dataflows.
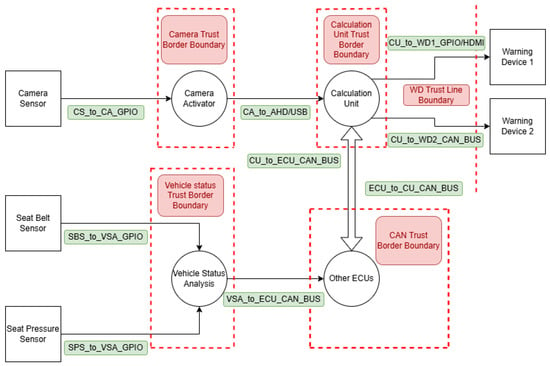
Figure 8.
The chosen architecture, replicated in the Microsoft Threat Modeling Tool 2016.
In the diagram, boundaries represent the divisions between internal system components and external entities. The “Border Boundary” lines are drawn to indicate where data enters or exits the system, highlighting the potential attack vectors. The “Line boundaries” show where communication occurs between internal components and external systems, marking potential points of failure or exposure. This representation is a tool to pinpoint vulnerabilities and design appropriate security measures to protect the DMS architecture.
6. Risk Analysis
Risk analysis is a fundamental step in ensuring the security of a DMS. It involves identifying, categorizing, and interpreting threats that may compromise the system. This section organizes threats using the STRIDE framework, combining damage scenarios, risk evaluations, and mitigation strategies.
6.1. Risk Categorization and Scenarios
Threat analysis is structured according to the STRIDE framework, which includes Spoofing, Tampering, Repudiation, Information Disclosure, DoS, and Elevation of Privilege. The primary system components—processes, sensors, actuators, dataflows, and ports—are analyzed for specific damage scenarios, illustrating potential vulnerabilities and impacts.
Processes encompass components that receive data, analyze it, and issue commands or results. In the proposed architecture, the processes include the Camera Activator, Calculation Unit, Vehicle Status Analyzer, and ECU. These are vulnerable to all STRIDE threat categories:
- Spoofing: An attacker impersonates a process, sending false data. For example, Spoofing the Camera Activator may continuously activate warning signals, distracting the driver;
- Tampering: The attacker modifies transmitted data, disrupting the system and confusing the driver;
- Repudiation: Signatures of processes are altered or erased, making the data untraceable and potentially causing erroneous activations;
- Information Disclosure: Unauthorized access to process data may range from insignificant (e.g., seat belt status) to highly sensitive (e.g., driver images);
- Denial of Service: Overloading processes can lead to crashes or slowdowns, disabling the system;
- Elevation of Privilege: Attackers may execute unauthorized functions by gaining access to high-privilege operations.
Sensors measure environmental factors and send results for processing. The architecture includes seat belt sensors, seat pressure sensors, and a camera sensor. These are vulnerable to the following:
- Spoofing: Attackers simulate sensors, sending fake data such as repetitive images of a sleeping driver, which may distract the driver and drain energy;
- Repudiation: Signatures are altered, rendering data untraceable and potentially causing the system to reject valid sensor data.
Actuators respond to process signals. In this architecture, warning devices alert the driver when necessary. They are vulnerable to the following:
- Spoofing: Attackers may impersonate warning devices, triggering constant alerts and distracting the driver;
- Repudiation: While technically possible, Repudiation does not significantly affect system functionality, given the limited role of actuators.
Dataflows facilitate communication between components and are subject to the following:
- Tampering: Data modification disrupts the system, confusing the driver;
- Information Disclosure: Unauthorized data access varies in impact from trivial to severe, depending on the data’s sensitivity;
- Denial of Service: Overloading dataflows may slow or crash the system entirely.
Ports serve as entry and exit points for dataflows, requiring protection against the following:
- Tampering: Modified data at ports can disrupt alarms and confuse drivers;
- Information Disclosure: Access to port data may lead to privacy violations or misuse of sensitive information;
- Denial of Service: Overwhelmed ports can disable communications, leading to system shutdowns.
6.2. Risk Evaluation and Interpretation
The TARA methodology employed in this study involved a structured and systematic evaluation of each system asset and its associated threats using the STRIDE framework. This approach ensures a detailed and transparent risk assessment by identifying critical assets within the DMS architecture—such as sensors, actuators, dataflows, and ports—and categorizing potential threats under the six STRIDE threat types. Each threat was further analyzed by defining specific attack paths and documenting assumptions about feasibility. For example, scenarios involving Information Disclosure were linked to attackers gaining access to sensitive dataflows, whereas Tampering scenarios focused on the unauthorized modification of communication data.
To ensure consistency and alignment with industry standards, the evaluation relied on detailed impact criteria across four key dimensions:
- Safety Impact (S): This dimension assessed the threat’s potential to cause life-threatening or non-life-threatening injuries. Severe impacts (assigned a value of 10) included scenarios involving fatal injuries, while moderate impacts (4) included partial degradation of system functionality without life-threatening consequences;
- Operational Impact (O): This dimension evaluated the effect on system functionality. Severe operational impacts included complete loss of critical vehicle functions, whereas minor impacts referred to degraded but still functional systems;
- Financial Impact (F): This dimension assessed the potential economic consequences, ranging from negligible financial losses (value of 1) to significant economic costs (value of 10) associated with mitigating or responding to threats;
- Privacy and Legislative Impact (P): This dimension addresses the implications of data breaches or violations of regulatory standards, with severe impacts involving highly sensitive data breaches (value of 10).
The combined severity of each threat was calculated using a weighted formula to account for the varying importance of each impact dimension:
The numerical coefficients presented in (2) were derived based on a rational evaluation of the relative importance of each impact dimension within the context of the DMS. The coefficient assigned to Safety Impact (S) is set to 5, reflecting its paramount significance in the context of automotive systems, where safety is the primary consideration. This coefficient ensures that the formula heavily weights the potential for life-threatening consequences.
The coefficient for Operational Impact (O) is 1, indicating its secondary importance compared to safety. Although operational disruptions can affect the functionality of the system, they generally do not pose direct risks to human life. The moderate weighting reflects the need to maintain the operability of the system without overshadowing safety concerns.
The coefficient for Financial Impact (F) is set at , reflecting the lower priority assigned to economic loss compared to safety and operational functionality. In the context of automotive safety, financial considerations, while relevant, do not take precedence over protecting human lives and maintaining critical functions.
The coefficient for Privacy and Legislative Impact (P) is , representing the lowest priority among the considered factors. Although data privacy breaches and legislative violations are significant, they do not directly compromise immediate physical safety or system functionality. This minimal weight prevents these factors from disproportionately influencing the overall severity score.
Thus, the weighted formula is carefully structured to prioritize human safety while adequately considering other factors in a balanced manner. The division by 4 ensures normalization, keeping the severity values within a consistent and interpretable range.
Attack Feasibility Evaluation: The feasibility of each attack was assessed based on access level, complexity of tools, and the attacker’s expertise. Feasibility was categorized into four levels:
- High (network level): Attacks requiring no physical access and are executable remotely, such as exploitation of network vulnerabilities (value 10);
- Medium (adjacent level): Attacks requiring logical or physical proximity but not direct access (value of 7);
- Low (local level): Attacks requiring direct access to the system (value of 4);
- Very Low (physical level): Attacks requiring specialized tools and physical interaction with system components (value 1).
Risk Score Calculation: Each threat’s risk score () was calculated as the product of its probability (P), derived from feasibility and its severity ():
This scoring mechanism provided a quantitative assessment, categorizing threats into risk levels (negligible, low, medium, high, or critical). The methodology clearly defined the thresholds for each level, ensuring consistency across evaluations.
Results and Risk Prioritization: The analysis identified 115 threats, with the following breakdown:
- Low Risk: 82.6%: These threats had minimal impact or low feasibility and primarily required minimal attention;
- Medium Risk: 13.9%: These threats targeted communication channels and processes, often involving Tampering or Spoofing;
- High Risk: 3.5%: These involved critical scenarios, such as Elevation of Privilege or DoS attacks, which required immediate mitigation.
Table 2 provides an overview of the threats and their distribution across STRIDE categories, highlighting the predominance of Tampering, DoS, and Information Disclosure as key risks.

Table 2.
Distribution of threats by STRIDE and risk level.
Risk Treatment: Based on the risk assessment, specific mitigation strategies were employed:
- Risk Reduction: Introducing or strengthening security controls to minimize residual risks (e.g., encryption and multi-factor authentication);
- Risk Retention: Retaining low-risk threats that pose a negligible impact on system functionality or safety;
- Risk Avoidance: Removing system features or functions that introduce unacceptable risks;
- Risk Transfer: Sharing risks with external entities, such as vendors or insurers, who could, for example, offer product liability coverage.
This structured and weighted evaluation framework ensured a balanced approach to risk management, prioritizing safety and operational reliability while addressing potential financial and privacy concerns.
6.3. STRIDE Application to System Components
Before analyzing the risks in detail, it is crucial to assess the safety impact of the identified threats. This analysis focuses on evaluating how different threats could affect the safety of the vehicle occupants, as the most critical factor in any DMS is the protection of the driver and passengers. The safety impact is categorized into different levels, from critical to negligible, depending on the potential consequences of each threat.
In our analysis, we found that the most significant safety threats stem from Spoofing, Tampering, and Elevation of Privilege attacks. These threats, if not mitigated, could lead to hazardous driving conditions, incorrect system behavior, or even complete system failure.
Table 3 presents an overview of the safety impact of potential failures across key components of the DMS, structured according to the STRIDE framework. The table categorizes each component’s susceptibility to Spoofing (S), Tampering (T), Repudiation (R), Information Disclosure (I), Denial of Service (D), and Elevation of Privilege (E), assessing the severity of each safety impact.

Table 3.
STRIDE safety impact table.
The color-coded classification represents the level of safety impact:
- Severe: Failures that pose a direct and significant safety risk, potentially leading to system failure or hazardous driving conditions;
- Major: Failures that degrade system performance and could contribute to unsafe conditions under specific scenarios;
- Moderate: Failures that affect system functionality but have limited direct safety consequences;
- Negligible: Failures that have minimal or no meaningful safety impact.
Key findings from the safety impact table:
- The Calculation Unit (CU) exhibits the highest criticality, with Severe (Red) safety impacts in multiple STRIDE categories. This underscores its central role in processing sensor data and issuing control commands;
- The Camera Sensor (CS) and Camera Activator (CA) are primarily affected by Major (Orange) and Severe (Red) risks, reflecting their importance in driver monitoring and potential vulnerability to incorrect or delayed image processing;
- Warning devices (WD1 and WD2) are largely categorized under Negligible (Green) or Moderate (Yellow) impacts, indicating that while failures may reduce system effectiveness, they do not directly compromise vehicle safety;
- Data integrity threats, such as Tampering (T) and Information Disclosure (I), generally have lower safety impacts but may still influence the reliability of safety-critical decisions;
- Denial of Service (D) failures, particularly for the Calculation Unit and Vehicle Status Analysis, are Severe (Red) or Moderate (Yellow), highlighting their potential to disrupt real-time monitoring and intervention.
This analysis provides a structured safety impact assessment of DMS vulnerabilities, guiding the prioritization of fault tolerance mechanisms, redundancy strategies, and real-time monitoring enhancements to mitigate high-risk failures effectively.
The application of the STRIDE framework to the DMS architecture provides a systematic method for identifying potential threats and evaluating the effectiveness of security measures. This chapter analyzes critical components of the DMS—including sensors, calculation units, communication interfaces, and actuators—and assesses vulnerabilities using the STRIDE model.
6.3.1. Calculation Unit
The Calculation Unit, acting as the central processor of data from sensors and the issuer of commands to actuators, is a pivotal component of the DMS. Due to its role as a central hub, it is a primary target for various threats. Spoofing attacks pose a significant risk, allowing adversaries to impersonate the Calculation Unit and inject falsified data into the system, potentially leading to operational disruptions and endangering driver safety. Tampering with the Calculation Unit’s data can compromise privacy and disrupt functionality, involving unauthorized modifications to sensitive information or the insertion of malicious commands. Repudiation risks arise when malicious actions by the Calculation Unit cannot be traced or verified, hindering accountability. Information Disclosure is particularly relevant due to the processing of sensitive driver data (biometric and behavioral), where unauthorized access constitutes a privacy breach. DoS attacks threaten the availability of the Calculation Unit, potentially rendering it unresponsive under a flood of malicious requests. Finally, Elevation of Privilege attacks exploit vulnerabilities to gain unauthorized access to critical functions, potentially enabling attackers to manipulate system behaviors.
To mitigate these risks, several security measures are considered. Authentication mechanisms, such as message authentication codes (MACs), are effective against Spoofing by ensuring communication authenticity. Robust encryption and intrusion detection/prevention systems (Intrusion Detection System (IDS)/Intrusion Prevention System (IPS)) address Tampering by protecting data integrity and detecting unauthorized access; these IDS/IPS systems could be further enhanced in future implementations by incorporating artificial intelligence (AI) or machine learning (ML) models for adaptive anomaly detection based on learned normal system behavior. Cryptographic digital signatures mitigate Repudiation risks by binding actions to a verifiable identity, and exploring decentralized ledger technologies like blockchain could offer enhanced, immutable logging capabilities for critical operations, further bolstering non-Repudiation. Encryption techniques (Advanced Encryption Standard (AES) and key encapsulation mechanism (KEM)/Data Encapsulation Mechanism (DEM)) [32] are necessary to prevent Information Disclosure. Rate-limiting mechanisms and anomaly detection through next-generation firewalls effectively address DoS risks by filtering abnormal traffic, although AI-based approaches could potentially improve the accuracy of distinguishing attacks from legitimate peaks. Comprehensive access control frameworks, like Authentication, Authorization, and Accounting (AAA), enforce strict role-based permissions to counter Elevation of Privilege threats [33].
While these proposed mitigations provide a strong baseline, they may not address all practical challenges, leading to residual risks. Balancing security with computational efficiency for authentication (Spoofing) is critical in embedded systems. Encryption and IDS/IPS (Tampering), especially AI-enhanced versions, introduce complexity and potential performance overheads. Digital signatures and potential blockchain implementations (Repudiation) depend on secure key management and robust consensus mechanisms, respectively, with tamper-proofing in automotive environments remaining an open question. Secure key distribution for encryption (Information Disclosure) is challenging in interconnected vehicles. DoS defenses may struggle to differentiate legitimate traffic surges from attacks, causing false positives or degraded responsiveness, even with advanced detection. Access controls (Elevation of Privilege) are not immune to misconfigurations or zero-day vulnerabilities. Furthermore, reliance on cryptography assumes adequate hardware support without introducing latency, and the expanding attack surface due to integration requires periodic re-evaluation. Future research should explore lightweight cryptography, adaptive AI-based security, and efficient blockchain applications suitable for the automotive domain.
6.3.2. Camera Activator
The Camera Activator is a crucial interface between the camera sensor and processing units, enabling precise image capture and data transmission. Its compromise could impact the system’s ability to monitor the driver accurately and promptly. This component faces multiple threats: Spoofing attacks could enable an attacker to transmit falsified activation signals, leading to inappropriate system responses. Tampering with the activator’s data or ports could cause unnecessary or misleading warnings. Repudiation risks occur when malicious activities involving the activator cannot be verified or traced. Information Disclosure is a critical concern due to handling sensitive visual data or metadata. DoS attacks could overwhelm the activator, disrupting its functionality. Elevation of Privilege risks involve attackers gaining unauthorized access to its functions.
Mitigation strategies include secure communication protocols (Transport Layer Security (TLS) and Secure Sockets Layer (SSL)) to ensure authenticity and integrity against Spoofing. Encryption of data, physical port security, and adherence to Automotive Open System Architecture (AUTOSAR) protocols [34] address Tampering. Implementing digital signatures for commands mitigates Repudiation by ensuring accountability; exploring blockchain for logging activation commands could provide an additional layer of tamper-evident history. Encrypting all data exchanges prevents Information Disclosure, with hybrid protocols balancing security and performance. Proxies with rate-limiting and anomaly detection (potentially AI-enhanced) ensure availability during DoS attacks. Robust authentication and AAA frameworks enforce privilege boundaries against Elevation of Privilege. Additionally, given the processing of biometric data (facial images), compliance with General Data Protection Regulation (GDPR) [35] is paramount, requiring explicit consent or other valid legal bases (vital interests and substantial public interest) and implementation of data protection measures like encryption, anonymization, minimization, and consent mechanisms.
Residual risks and challenges remain. Spoofing mitigations rely on certificate management, which is complex and potentially latency-inducing in embedded systems [36]. Tampering mitigations like physical security increase costs, while AUTOSAR integration can be resource-intensive. Repudiation depends on secure key storage (for signatures) or the overheads and complexities associated with potential blockchain solutions. Information Disclosure mitigations (encryption) may require hardware acceleration for real-time performance, and ensuring robust encryption under varying loads is an open question. DoS defenses are not infallible against sophisticated attackers. Elevation of Privilege controls depend on proper configuration and maintenance. Overall, trade-offs between security, cost, and performance, especially in low-cost models, require careful evaluation and potentially lightweight security protocols.
6.3.3. Warning Devices
Warning devices deliver critical safety alerts to the driver and are susceptible to threats that could undermine their effectiveness. Spoofing attacks could lead to false, excessive, or suppressed alerts, distracting the driver or hiding real dangers. Tampering with devices or connections could silence critical alerts or generate false warnings. Repudiation risks involve attackers denying responsibility for malicious activations. While less critical, Information Disclosure through intercepted commands could reveal system behaviors. DoS attacks could render devices unresponsive, preventing critical alerts.
Mitigations include access controls (AAA frameworks) [32] to prevent unauthorized activation (Spoofing). Redundant device configurations enhance resilience against Tampering, supplemented by health monitoring. Digital signatures on commands ensure accountability, addressing Repudiation, potentially logged immutably using blockchain in future designs. Lightweight encryption protects command data against Information Disclosure. Redundancy and anomaly detection (possibly AI-driven for subtle attacks) also help maintain availability during DoS attacks.
Challenges and residual risks include careful configuration of access controls (Spoofing) to avoid delays or scalability issues. Redundancy (Tampering, DoS) adds cost and complexity and does not preclude common-mode failures. Digital signature security (Repudiation) relies on secure key management and faces challenges in shared vehicle contexts; blockchain logging would introduce its own overheads. Lightweight encryption (Information Disclosure) needs evaluation against emerging attacks. DoS anomaly detection can be bypassed. Balancing cost, complexity, and security remains an unresolved issue, requiring innovative approaches to simplify implementation without compromising effectiveness.
6.3.4. Vehicle Status Analysis
The Vehicle Status Analysis (VSA) module monitors real-time data (e.g., seat occupancy and belt usage), playing a vital safety role. Threats could compromise its functionality and reliability. Spoofing attacks could involve sending false status data, disrupting system responses. Tampering with the module or ports could alter critical information, leading to inappropriate warnings. Repudiation risks arise when unauthorized modifications cannot be traced. Information Disclosure, while less critical, could compromise operational insights if communication is intercepted. DoS attacks threaten availability, potentially causing system malfunctions due to missing data. Elevation of Privilege risks involve exploiting VSA vulnerabilities to gain wider system access.
Mitigations involve strong authentication protocols for input data to counter Spoofing. Encryption and intrusion detection mechanisms protect against Tampering, potentially enhanced by tamper-evident hardware, integrity checks, and AI-based monitoring for unusual data patterns. Digital signatures ensure accountability for Repudiation [37], with blockchain offering a potential future avenue for immutable logging of status changes. Encrypting communications addresses Information Disclosure. Rate-limiting and redundant configurations ensure operational continuity during DoS attacks. Role-based access controls (AAA) restrict privileges to mitigate Elevation of Privilege risks [32].
Residual risks include potential latency/overhead from authentication (Spoofing). Sophisticated physical attacks may bypass Tampering defenses. Repudiation mitigation depends on secure key infrastructure or the complexities of blockchain deployment. Long-term cryptographic resilience (Information Disclosure) requires planning (e.g., quantum-safe crypto). Advanced DoS attacks might evade detection. Elevation of Privilege mitigation relies on a comprehensive design-phase assessment and ongoing monitoring. Trade-offs between security, cost, and complexity need further research, especially considering interactions within broader vehicle ecosystems.
6.3.5. Sensors
Sensors capture environmental and biometric data, forming the DMS foundation. Their exposure makes them vulnerable. Spoofing attacks could introduce falsified data (e.g., fake images and incorrect readings), undermining accuracy and leading to erroneous decisions. Tampering with sensor data or physical connections poses a severe risk, potentially disrupting information flow or introducing malicious inputs. Repudiation risks arise when sensor actions or data origins cannot be verified, hindering traceability and accountability. Information Disclosure is critical for sensitive data (e.g., camera images), with privacy violations having significant legal/ethical implications. DoS attacks could overwhelm communication channels, disrupting functionality and causing delays.
Mitigation strategies include robust authentication (MACs) [38] against Spoofing, possibly augmented by hardware-based methods or AI-driven anomaly detection looking for subtle signs of data manipulation. Tamper-resistant hardware, physical enclosures, and error detection (cyclic redundancy check (CRC)) address Tampering. Lightweight digital signatures provide accountability against Repudiation; moreover, blockchain technology presents a potential future solution for creating tamper-evident, verifiable records of sensor data provenance or critical readings, particularly for sensitive biometric data. Encryption of data exchanges is essential against Information Disclosure, supplemented by secure firmware practices and potentially privacy-preserving computation techniques where applicable. Redundant configurations and access controls provide resilience against DoS, enhanced by anomaly detection and adaptive filtering algorithms, potentially leveraging AI.
Challenges and residual risks persist. Advanced adversaries might bypass Spoofing authentication or sophisticated AI detection models. Physical Tampering protection involves cost/complexity trade-offs, and CRC is only reactive. Repudiation measures face key management and performance overhead issues, and blockchain implementation in real-time sensor streams is challenging. Encryption (Information Disclosure) is not infallible against key/protocol vulnerabilities or side-channel attacks. DoS defenses strain resources and may not stop sophisticated attacks. Balancing security, performance, cost, and privacy remains a key challenge, demanding continuous evaluation, proactive threat-modeling, the development of robust AI security techniques, and potentially novel uses of technologies like blockchain for these critical components.
7. Results and Discussion
Implementing a DMS represents a significant advancement in automotive safety, enabling real-time monitoring of driver behavior to detect signs of fatigue and distraction. As these systems evolve, they also introduce considerable cybersecurity challenges. This study employs a comprehensive TARA methodology, in accordance with ISO/SAE 21434, to systematically identify and categorize security threats.
A total of 115 threats were classified as follows:
- 95 low-risk threats;
- 16 medium-risk threats;
- 4 high-risk threats.
The majority of low-risk threats are attributed to the localized architecture of the DMS, which limits external communication and reduces the system’s attack surface. However, several high- and medium-risk threats emerged, particularly in unauthorized sensor manipulation, data Spoofing, and Denial of Service attacks, necessitating multi-layered mitigation strategies.
Component risk profiles and residual risks. Each key component was analyzed for residual risk after primary mitigations were applied:
- Calculation Unit (CU): High initial risk from Spoofing, Tampering, DoS, and Elevation of Privilege, mitigated through MACs, encryption, IDS/IPS, and access controls. Residual risks stem from key management complexities, real-time performance constraints, and susceptibility to zero-day exploits;
- Camera Activator (CA): Exposed to Spoofing and Elevation of Privilege; mitigated via TLS/SSL, AAA frameworks, and digital signatures. However, certificate management latency and the integration burden of AUTOSAR remain unresolved;
- Warning devices (WD): Moderate initial risks managed by access control and redundancy. Still, they face scalability challenges and anomaly detection evasion scenarios;
- Vehicle Status Analysis (VSA): Subject to Spoofing and Tampering; secured through encryption, tamper-evident hardware, and role-based access controls. Risks persist in maintenance overhead and ensuring cryptographic agility;
- Camera sensors (CS): Exposed to Spoofing, Repudiation, and Information Disclosure; mitigated via digital signatures, encryption, and anomaly detection. Nevertheless, physical exposure and key lifecycle issues remain significant.
Overall Risk Reduction Assessment. Table 4 summarizes the assessed risk reduction achieved for the most critical threats identified across key system components, illustrating the effectiveness of applying the primary security controls discussed throughout Section 6.3. As the table indicates, implementing standard mitigations like authentication (MACs), encryption, access controls (AAA), and baseline IDS/IPS significantly lowers the initial risk severities. For example, threats initially assessed as High are generally reduced to Medium, and Medium threats often decrease to Low.

Table 4.
Overall risk reduction summary for key components and threats.
However, the table also highlights that notable residual risks persist, particularly for components like the Calculation Unit (CU) and camera sensor (CS) under specific threat categories (Spoofing, Tampering, DoS, and Elevation of Privilege). The persistence of Medium residual risks even after applying primary controls stems directly from the inherent limitations of these mechanisms in the automotive context. For instance, while authentication hinders basic Spoofing (S) for the CU, the Medium residual risk reflects challenges in perfectly secure key management for MACs, the difficulty of implementing complex authentication protocols without performance overhead in embedded systems, and the potential for sophisticated attacks designed to bypass standard verification methods. Similarly, the Medium residual risk for Tampering (T) on the CU, despite encryption and IDS/IPS, acknowledges the complexity of tuning detection systems effectively against novel threats without causing false positives, the unavoidable performance overhead, and the possibility of attacks targeting implementation flaws rather than the cryptographic algorithms themselves.
Addressing these specific limitations that lead to Medium or Low (rather than Negligible) residual risks points towards the necessity for continuous improvement and potentially the adoption of the more advanced security paradigms discussed earlier Section 6.3. Techniques such as AI-driven adaptive IDS could offer better detection of sophisticated DoS or Tampering attacks that evade signature-based systems. Likewise, blockchain technology could provide stronger guarantees for data integrity and non-Repudiation, potentially mitigating residual risks associated with lightweight digital signatures or complex logging requirements, especially for sensitive sensor data (CS).
Therefore, while Table 4 presents the outcome of applying the core set of security controls analyzed within this TARA cycle, the accompanying rationale underscores that achieving even lower residual risk levels likely requires exploring and validating these more advanced, context-aware security solutions in future development iterations.
In response to reviewer suggestions, we emphasize the need for advanced threat detection mechanisms beyond static controls. AI-driven, adaptive intrusion detection systems (IDSs) are capable of learning new threat patterns and outperforming signature-based IDS in detecting evolving DoS or Tampering attacks. Such systems also support dynamic policy enforcement and anomaly classification tailored to driving contexts.
DMS systems increasingly interact with V2X networks, which introduce broader cybersecurity exposure. However, this connectivity also enables cooperative detection, such as shared anomaly alerts between vehicles and infrastructure nodes. To secure this extended perimeter, decentralized key management schemes, such as blockchain-based trust anchors and threshold cryptography, can offer tamper-proof audit trails and enhance the verifiability of system logs.
Recent studies propose blockchain-enhanced logging systems that ensure data integrity and non-Repudiation while maintaining processing efficiency through lightweight consensus mechanisms. Furthermore, smart contract integration can facilitate automated key revocation and trust policy enforcement across multi-domain vehicular ecosystems.
Data privacy and GDPR compliance. A critical dimension of modern DMS deployment lies in safeguarding user privacy. The biometric and behavioral data collected demand rigorous adherence to GDPR. This includes the following:
- Data minimization (Art. 5): Employing edge-based processing architectures (e.g., containerized analytics or federated learning) that avoid raw data transmission;
- Right to erasure (Art. 17): Implementing off-chain anonymized indexing and user-controlled data lifecycles to support selective deletion;
- Consent management: Using verifiable digital consent records tied to cryptographically secure identities.
To strengthen compliance and transparency, we recommend that future DMS implementations adopt Data and Impact Privacy Integrated Assessments (DIPIA), which combine security threat modeling and legal risk assessments from the earliest design phases.
This analysis confirms that the evaluated DMS architecture is effective in reducing security risks through established mitigation practices. However, achieving higher assurance levels and aligning with modern legal standards necessitates the integration of adaptive AI, secure V2X protocols, privacy-enhancing technologies, and decentralized trust infrastructures. This holistic approach responds directly to reviewer recommendations and reflects the broader direction of intelligent and ethically aligned vehicular cybersecurity.
8. Conclusions
This study successfully addressed the research questions posed in Section 3.2, offering a comprehensive assessment of the cybersecurity posture of a representative DMS. The analysis confirmed that the system’s architecture—built upon localized communication interfaces such as GPIO ports and CAN buses—significantly reduces exposure to external threats. Nevertheless, the Threat Analysis and Risk Assessment (TARA) identified 115 threats, with a small but notable subset (16 medium-risk and 4 high-risk) requiring targeted mitigation strategies.
Through the STRIDE-based evaluation, we demonstrated that while conventional security controls such as MACs, access controls (AAA), encryption, and IDS/IPS effectively reduce most risks to acceptable levels, some residual vulnerabilities remain. These are largely due to implementation constraints in embedded automotive environments—particularly in secure key management, real-time processing limitations, and the dynamic nature of vehicular ecosystems.
In response to emerging challenges and reviewer feedback, we explored the integration of advanced countermeasures, including adaptive AI-based intrusion detection systems, blockchain-based key management and logging frameworks, and edge-computing techniques for localized anomaly detection. We argue that these technologies are well-suited to further lower residual risks and bolster trust and verifiability, particularly in more connected and cooperative environments like Vehicle-to-Everything (V2X) networks.
Moreover, this study underscores the importance of addressing legal and ethical dimensions—most notably, compliance with General Data Protection Regulation (GDPR). By leveraging edge analytics, anonymized data indexing, and user-centric consent mechanisms, DMS architectures can support both functional safety and data sovereignty. To institutionalize privacy-by-design principles, we recommend the adoption of integrated assessments such as the Data and Impact Privacy Integrated Assessment (DIPIA), which merges security modeling with legal accountability frameworks.
In conclusion, the analyzed DMS architecture exhibits a strong foundational security posture but must evolve in parallel with technological, regulatory, and societal expectations. Future developments should prioritize the following:
- Deployment of adaptive threat detection via AI-enhanced IDS;
- Integration with V2X infrastructures to facilitate distributed anomaly awareness;
- Application of blockchain for decentralized key and log management;
- Embedding of DIPIA-driven compliance practices throughout the design lifecycle.
By addressing these multidimensional considerations, future DMS implementations can achieve greater resilience, regulatory alignment, and public trust in increasingly autonomous and data-driven vehicular environments.
Supplementary Materials
The following supporting information can be downloaded at: https://www.mdpi.com/article/10.3390/app15105571/s1, The detailed TARA analysis.
Author Contributions
Conceptualization, R.K.; data curation, E.J.; investigation, I.-C.Ș.; methodology, M.D.S.; software, E.J.; supervision, C.E.; validation, R.K.; writing—original draft, M.D.S., E.J., and I.-C.Ș.; writing—review and editing, M.D.S. All authors have read and agreed to the published version of the manuscript.
Funding
The research work was completed by the on-site participants of the 3rd version of Automotive Cybersecurity Academy (ACSA) 2024, which is funded by the European Commission as part of Erasmus+ Blended Intensive Program (BIP). More information about this edition of mobility can be found at the following address: https://www.autocybersec.ro/all-acsas/acsa-2024 (accessed on 12 May 2025). Led by Rahamatullah Khondoker, students, teachers, and researchers from multiple international academic institutions and industry partners collaborated in this BIP. The academic contributors included University of Salerno in Italy, Gheorghe Asachi Technical University of Ia¸si in Romania, Technische Hochschule Mittelhessen in Germany, University Politehnica Timisoara in Romania, University of Coimbra in Portugal, University of Naples Federico II in Italy, Technische Hochschule Ingolstadt in Germany, Politehnica University of Bucharest in Romania, and Hochschule Darmstadt in Germany. Industry partners encompassed a diverse range of automotive and technology companies such as Continental Automotive Romania, CES Automotive in Germany, Veoneer US Safety Systems, STMicroelectronics, Cyber4People, ARRK Engineering GmbH, HORIBA MIRA, Drass, PlaxidityX, SAPAR, and ARRK Europe Limited. Appreciations to ANSYS and CADFEM Germany for providing us with free access to Ansys Medini Analyze. The work of the previous (2nd) ACSA was published in the MDPI journal [39].
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The original contributions presented in this study are included in the article/Supplementary Materials. Further inquiries can be directed to the corresponding author.
Acknowledgments
This paper was written during the mobility part of an Erasmus+ Blended Intensive Program (BIP) titled Automotive Cyber Security Academy (ACSA) that took place at the University of Salerno, Italy, from 22 August 2024 to 4 September 2024. We would like to acknowledge all the other contributors to this paper: Corina Balasoiu, Joao Silva, Davide Amoruso, Francesco Giuseppe Zammarrelli, Gebremichael T. Welegergs, Joao Monteiro, Krister Herban, Matteo Greco, and Monika Bandhamravuri.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
| AAA | Authentication, Authorization, and Accounting |
| AES | Advanced Encryption Standard |
| AI | Artificial intelligence |
| ADASs | Advanced Driver Assistance Systems |
| AUTOSAR | Automotive Open System Architecture |
| CAN | Controller Area Network |
| CIA | Confidentiality, Integrity, and Availability |
| CRC | Cyclic Redundancy Check |
| DEM | Data Encapsulation Mechanism |
| DMS | Driver Monitoring System |
| DoS | Denial of Service |
| ECU | Electronic Control Unit |
| GPIO | General Purpose Input/Output |
| GDPR | General Data Protection Regulation |
| HDMI | High Definition Multimedia Interface |
| IDS | Intrusion Detection System |
| IoT | Internet of Things |
| IPS | Intrusion Prevention System |
| ISO | International Organization for Standardization |
| JTAG | Joint-Test Action Group |
| KEM | Key encapsulation mechanism |
| MAC | Message authentication code |
| ML | Machine learning |
| OEM | Original Equipment Manufacturer |
| PCIe | Peripheral Component Interconnect Express |
| SPI | Serial Peripheral Interface |
| SAE | Society of Automotive Engineers |
| SSL | Secure Sockets Layer |
| TARA | Threat Analysis and Risk Assessment |
| TLS | Transport Layer Security |
| UART | Universal Asynchronous Receiver Transmitter |
| USB | Universal Serial Bus |
| V2X | Vehicle-to-Everything |
| VSA | Vehicle Status Analysis |
References
- Campos-Ferreira, A.E.; Lozoya-Santos, J.d.J.; Tudon-Martinez, J.C.; Mendoza, R.A.R.; Vargas-Martínez, A.; Morales-Menendez, R.; Lozano, D. Vehicle and Driver Monitoring System Using On-Board and Remote Sensors. Sensors 2023, 23, 814. [Google Scholar] [CrossRef] [PubMed]
- Dong, Y.; Hu, Z.; Uchimura, K.; Murayama, N. Driver Inattention Monitoring System for Intelligent Vehicles: A Review. IEEE Trans. Intell. Transp. Syst. 2011, 12, 596–614. [Google Scholar] [CrossRef]
- Mehta, A.A.; Padaria, A.A.; Bavisi, D.J.; Ukani, V.; Thakkar, P.; Geddam, R.; Kotecha, K.; Abraham, A. Securing the Future: A Comprehensive Review of Security Challenges and Solutions in Advanced Driver Assistance Systems. IEEE Access 2024, 12, 643–678. [Google Scholar] [CrossRef]
- Pekaric, I.; Sauerwein, C.; Haselwanter, S.; Felderer, M. A taxonomy of attack mechanisms in the automotive domain. Comput. Stand. Interfaces 2021, 78, 103539. [Google Scholar] [CrossRef]
- Kloukiniotis, A.; Papandreou, A.; Lalos, A.; Kapsalas, P.; Nguyen, D.V.; Moustakas, K. Countering Adversarial Attacks on Autonomous Vehicles Using Denoising Techniques: A Review. IEEE Open J. Intell. Transp. Syst. 2022, 3, 61–80. [Google Scholar] [CrossRef]
- ISO/SAE21434; Road Vehicles—Cybersecurity Engineering. SAE International: Warrendale, PA, USA, 2021.
- Su, Y.F.; Hsu, C.Y.; Wang, Y.C.; Yeh, C.Y. (Eds.) Image-Based Driver Status Monitoring System for Determining the Transfer of Dynamic Driving Tasks in Autonomous Vehicles; SAE Technical Paper Series; SAE International: Warrendale, PA, USA, 2024. [Google Scholar] [CrossRef]
- Joe, L.Y.; Wang, N.N.P.; Celine, K.K.Y.; Regan, G.L.K.; Hanafi, E.; Illias, H.A. IoT-Based Smart Driver Monitoring System With Emergency Response Mechanism. In Proceedings of the 2023 Innovations in Power and Advanced Computing Technologies (i-PACT), Kuala Lumpur, Malaysia, 8–10 December 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Lazaro, A.; Lazaro, M.; Villarino, R.; Girbau, D. Seat-Occupancy Detection System and Breathing Rate Monitoring Based on a Low-Cost mm-Wave Radar at 60 GHz. IEEE Access 2021, 9, 115403–115414. [Google Scholar] [CrossRef]
- Chen, Y.; Luo, Y.; Ma, J.; Qi, A.; Huang, R.; de Paulis, F.; Qi, Y. Non-Contact In-Vehicle Occupant Monitoring System Based on Point Clouds from FMCW Radar. Technologies 2023, 11, 39. [Google Scholar] [CrossRef]
- Singh, S.; Singh, A.P.; Singh, H.P.; Kalyani, I.N.; Sharma, G. A Review on Drowsy Driving Detection Device Using Arduino and Eye-Blink Sensor. Int. J. Eng. Appl. Sci. Technol. 2023, 8, 320–323. [Google Scholar] [CrossRef]
- Ansari, H.R.; Kordrostami, Z.; Mirzaei, A. In-vehicle wireless driver breath alcohol detection system using a microheater integrated gas sensor based on Sn-doped CuO nanostructures. Sci. Rep. 2023, 13, 7136. [Google Scholar] [CrossRef] [PubMed]
- Pande, T.; Shin, K.; Prabhu, R.; Muralidharan, N.; Garud, H.; Jagannathan, S.; Haas, S. Driver and Occupancy Monitoring Systems with AM62A. In Proceedings of the 2024 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 6–8 January 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Mishra, A.; Kim, J.; Kim, D.; Cha, J.; Kim, S. An Intelligent In-cabin Monitoring System in Fully Autonomous Vehicles. In Proceedings of the 2020 International SoC Design Conference (ISOCC), Yeosu, Republic of Korea, 21–24 October 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 61–62. [Google Scholar] [CrossRef]
- Vijay, A. Intelligent Driver Monitoring System for Safe Driving. In Proceedings of the 2023 IEEE International Conference on Electrical Systems for Aircraft, Railway, Ship Propulsion and Road Vehicles & International Transportation Electrification Conference (ESARS-ITEC), Venice, Italy, 29–31 March 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Agarkar, A.S.; Gandhiraj, R.; Panda, M.K. Driver Drowsiness Detection and Warning using Facial Features and Hand Gestures. In Proceedings of the 2nd IEEE International Conference on Vision Towards Emerging Trends in Communication and Networking Technologies, Vellore, India, 5–6 May 2023; Thanikaiselvan, V., Ed.; pp. 1–6. [Google Scholar] [CrossRef]
- Elhawawsha, A.; Zeine, C.; Zeid Daou, R.A.; Kalinowski, D.; Khattar, J.; Telawi, S.; Boercsoek, J. Design of a Novel Safe Approach to Monitor Drivers While Operating Their Cars. In Proceedings of the 2023 Seventh International Conference on Advances in Biomedical Engineering (ICABME), Beirut, Lebanon, 12–13 October 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 54–58. [Google Scholar] [CrossRef]
- Qu, Y.; Hu, H.; Liu, J.; Zhang, Z.; Li, Y.; Ge, X. Driver State Monitoring Technology for Conditionally Automated Vehicles: Review and Future Prospects. IEEE Trans. Instrum. Meas. 2023, 72, 1–20. [Google Scholar] [CrossRef]
- Heenetimulla, H.D.S.M.; Das, S.K.; Sahoo, G.K.; Singh, P. An FPGA System for Driver Mobile Usage Detection and Heart Rate-Based Health Monitoring. In Proceedings of the 2022 2nd Odisha International Conference on Electrical Power Engineering, Communication and Computing Technology (ODICON), Bhubaneswar, India, 11–12 November 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Mohammed, K.; Abdelhafid, M.; Kamal, K.; Ismail, N.; Ilias, A. Intelligent driver monitoring system: An Internet of Things-based system for tracking and identifying the driving behavior. Comput. Stand. Interfaces 2023, 84, 103704. [Google Scholar] [CrossRef]
- Wang, X.; Zhao, Q. A new method for monitoring the state of drivers-occupant based on infrared 3D camera. In Proceedings of the 2022 China Automation Congress (CAC), Xiamen, China, 25–27 November 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 6944–6949. [Google Scholar] [CrossRef]
- Li, W.; Li, G.; Tan, R.; Wang, C.; Sun, Z.; Li, Y.; Guo, G.; Cao, D.; Li, K. Review and Perspectives on Human Emotion for Connected Automated Vehicles. Automot. Innov. 2024, 7, 4–44. [Google Scholar] [CrossRef]
- Gebert, M.; Kobiela, F.; Leibinger, J.; Mueller, H. Towards In-vehicle Driver Fainting Detection. In Proceedings of the Proceedings of the 15th International Conference on Automotive User Interfaces and Interactive Vehicular Applications, Ingolstadt, Germany, 18–22 September 2023; ACM Digital Library: New York, NY, USA, 2023; pp. 244–255. [Google Scholar] [CrossRef]
- Jha, S.; Marzban, M.; Hu, T.; Mahmoud, M.; Busso, C. The Multimodal Driver Monitoring Database: A Naturalistic Corpus to Study Driver Attention. IEEE Trans. Intell. Transp. Syst. 2022, 23, 10736–10752. [Google Scholar] [CrossRef]
- Koch, K.; Maritsch, M.; van Weenen, E.; Feuerriegel, S.; Pfäffli, M.; Fleisch, E.; Weinmann, W.; Wortmann, F. Leveraging driver vehicle and environment interaction: Machine learning using driver monitoring cameras to detect drunk driving. In Proceedings of the CHI ’23: CHI Conference on Human Factors in Computing Systems, Hamburg, Germany, 23–28 April 2023. [Google Scholar]
- Gao, N.; Marschall, M.; Burry, J.; Watkins, S.; Salim, F.D. Understanding occupants’ behaviour, engagement, emotion, and comfort indoors with heterogeneous sensors and wearables. Sci. Data 2022, 9, 261. [Google Scholar] [CrossRef] [PubMed]
- Shahverdy, M.; Fathy, M.; Berangi, R.; Sabokrou, M. Driver behavior detection and classification using deep convolutional neural networks. Expert Syst. Appl. 2020, 149, 113240. [Google Scholar] [CrossRef]
- NVIDIA. NVIDIA Jetson Xavier Series; NVIDIA: Santa Clara, CA, USA, 2024; Available online: https://www.nvidia.com/en-us/autonomous-machines/embedded-systems/jetson-xavier-series/ (accessed on 12 May 2025).
- NVIDIA Developer. Deep Learning Accelerator (DLA); NVIDIA: Santa Clara, CA, USA, 2024; Available online: https://developer.nvidia.com/deep-learning-accelerator (accessed on 12 May 2025).
- Ebrahim Shaik, M. A systematic review on detection and prediction of driver drowsiness. Transp. Res. Interdiscip. Perspect. 2023, 21, 100864. [Google Scholar] [CrossRef]
- Wang, S.; Hou, Y.; Gao, F.; Ji, X. A novel IoT access architecture for vehicle monitoring system. In Proceedings of the 2016 IEEE 3rd World Forum on Internet of Things (WF-IoT), Reston, VA, USA, 12–14 December 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 639–642. [Google Scholar] [CrossRef]
- Shoup, V. A Proposal for an ISO Standard for Public Key Encryption (Version 2.1) 2002. Available online: https://www.shoup.net/papers/iso-2_1.pdf (accessed on 12 May 2025).
- Nakhjiri, M.; Nakhjiri, M. AAA and Network Security for Mobile Access: Radius, Diameter, EAP, PKI and IP Mobility; Wiley: Hoboken, NJ, USA, 2005. [Google Scholar] [CrossRef]
- Bella, G.; Biondi, P.; Costantino, G.; Matteucci, I. Designing and implementing an AUTOSAR-based Basic Software Module for enhanced security. Comput. Netw. 2022, 218, 109377. [Google Scholar] [CrossRef]
- European Parliament & Council of the European Union. REGULATION (EU) 2016/ 679 of the European Parliament and of the Council—of 27 April 2016—on the protection of Natural Persons with Regard to the Processing of Personal Data and on the Free Movement of Such Data, and Repealing Directive 95/46/EC (General Data Protection Regulation). Available online: https://eur-lex.europa.eu/eli/reg/2016/679/oj/eng (accessed on 12 May 2025).
- Satapathy, A.; Livingston, J. A Comprehensive Survey on SSL/ TLS and their Vulnerabilities. Int. J. Comput. Appl. 2016, 153, 31–38. [Google Scholar] [CrossRef]
- Digital Signature Standard (DSS). Available online: https://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.186-5.pdf (accessed on 12 May 2025).
- Wagner, E.; Bauer, J.; Henze, M. Take a Bite of the Reality Sandwich: Revisiting the Security of Progressive Message Authentication Codes. In Proceedings of the WiSec ’22: 15th ACM Conference on Security and Privacy in Wireless and Mobile Networks, San Antonio, TX, USA, 16–19 May 2022; pp. 207–221. [Google Scholar] [CrossRef]
- Boi, B.; Gupta, T.; Rinhel, M.; Jubea, I.; Khondoker, R.; Esposito, C.; Sousa, B.M. Strengthening Automotive Cybersecurity: A Comparative Analysis of ISO/SAE 21434-Compliant Automatic Collision Notification (ACN) Systems. Vehicles 2023, 5, 1760–1802. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).