1. Introduction
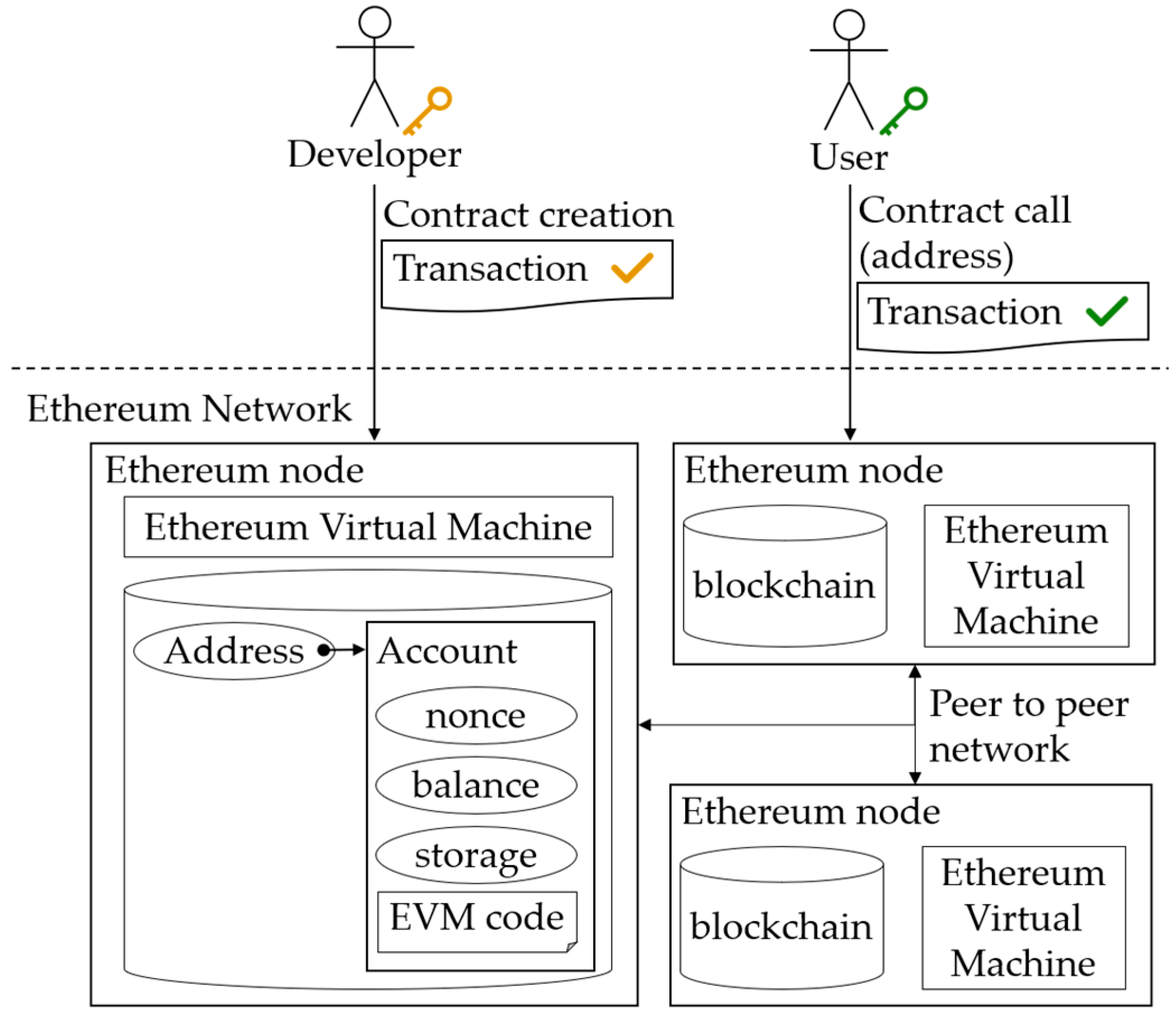
Blockchain technology connects blocks in a chain using hash algorithms and stores multiple nodes in a distributed manner, making it impossible to falsify or alter the data within a block. This ensures safe transactions and data processing even in the absence of a dependable certification authority [
1]. The Ethereum network, which combines blockchain technology with the Ethereum Virtual Machine (EVM), allows for the automatic execution of contracts between individuals without a certification authority [
2]. The emergence of Decentralized Applications (DApps) that utilize these smart contracts enables users to easily use smart contracts and execute contracts with low fees [
3].
However, the absence of such certification authorities increases the risk and potential damage from fraud. Specifically, “Rug-pull” is a form of fraud in which project developers hide backdoor codes in smart contracts and perform abnormal operations to steal funds under certain conditions, causing significant damage to users [
4]. A typical example is the SQUID GAME TOKEN, which concealed backdoor codes allowing only the developer to sell the tokens, forcing users who invested in the tokens to lose all their investments [
5]. Even when such frauds occur, it is difficult for a central authority to control or regulate them due to the freedom of programming and the decentralization of the blockchain on the Ethereum network.
Currently, to reduce the damages caused by Rug-pull, DApp developers are creating Rug-pull lists to notify users of the risks and discourage them from making investments [
6,
7]. However, these lists are provided only after damage has occurred, making it challenging to prevent damage in advance. Additionally, there is a limitation in that it takes time to evaluate a project before it can be added to the list [
8]. Consequently, DApp developers are encouraging users to investigate projects themselves before making investments [
9].
Users determine the risk of Rug-pull by reviewing the project’s content and the security of the smart contract’s source code. However, among the 68,268,300 smart contracts deployed on Ethereum, only 705,010 smart contracts disclose their source code, which is approximately 1% [
10]. Due to this low disclosure rate, it is difficult to analyze smart contracts to assess their risks. Therefore, users rely on commercial services such as GoPlus to test the security level of smart contracts and detect backdoor codes [
11]. These commercial services detect backdoor codes based on previously known code patterns. However, they cannot detect backdoor codes that have altered the location of the operator conducting the actual backdoor operation through modifications to existing patterns or backdoor codes hidden in atypical parts. Consequently, smart contracts equipped with such backdoor codes continue to create new victims on the Ethereum network [
12].
To address these problems, this paper proposes a balance-tracking-based backdoor code detection model. The proposed model extracts functions from Ethereum bytecode and inspects the extracted functions to detect the presence of backdoor code. It achieves this by tracking the balance changes that occur within each function, enabling the detection of backdoor code encapsulation. The model identifies six types of backdoor codes based on these balance changes: token generation, token destruction, transfer limitation, funds manipulation, transfer fee, and proxy. This model detects backdoor codes that can cause direct financial loss through these mechanisms. This study aims to analyze 989 smart contracts for each attack type and measure accuracy, recall, and precision, thereby verifying the effectiveness of this model.
Section 2 explains the backdoor code types in Ethereum smart contracts and Rug-pull projects, as well as existing backdoor code detection models.
Section 3 details the structure and operational methodology of the proposed backdoor code detection model, highlighting improvements over existing limitations.
Section 4 describes the experiments conducted to classify backdoor codes in smart contracts, measuring the model’s accuracy and presenting the analysis results. Finally,
Section 5 summarizes the entire content and provides concluding remarks.
3. Balance-Tracking-Based Backdoor Detection Model
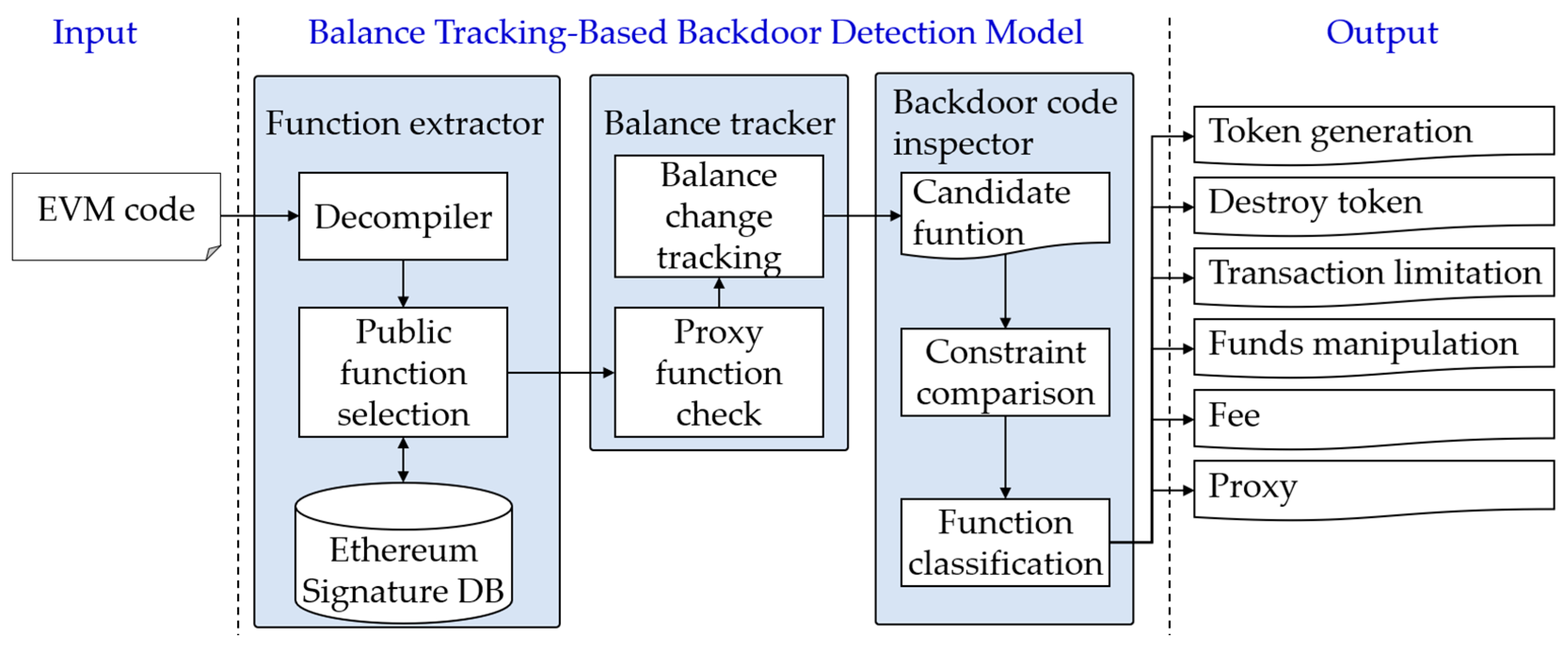
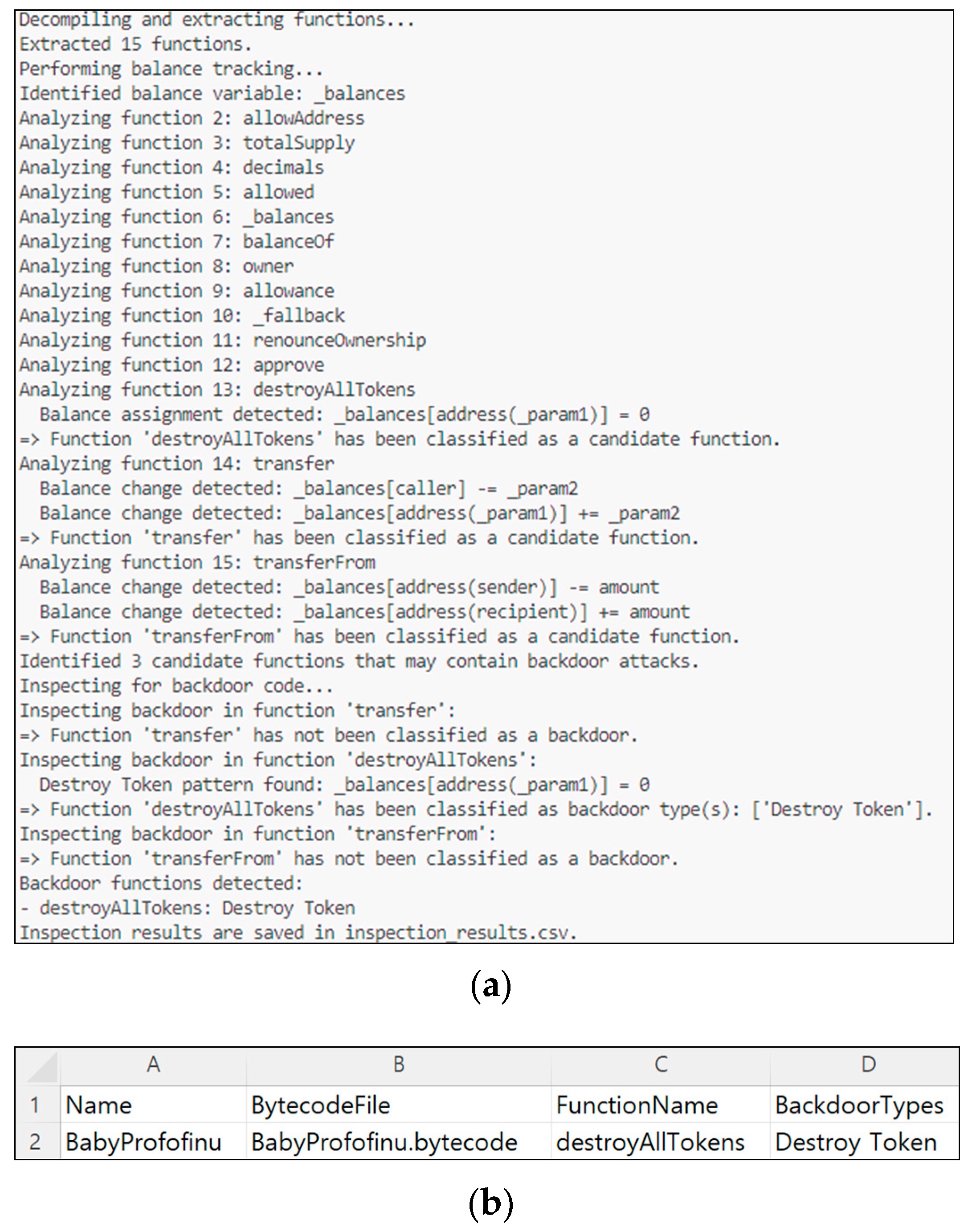
This study proposes a balance-tracking-based backdoor detection model to efficiently detect backdoor codes hidden in Ethereum smart contracts. The proposed model aims to detect even modified backdoor codes that are difficult to identify using existing detection models by analyzing the balance changes in internal functions, using the EVM code of a smart contract as input. The proposed balance-tracking-based backdoor detection model consists of three elements, as shown in
Figure 3. First, the Function Extractor preprocesses the input EVM code to extract functions for backdoor detection. Then, the extracted functions track the balance changes that occur in the Balance Tracker to identify candidate functions that contain backdoor attacks. Finally, the Backdoor Code Inspector detects conditional logic and analyzes patterns to identify the presence of backdoor codes.
3.1. Function Extractor
Panoramix Decompiler is an open-source decompiler that recovers high-level function structures from EVM code [
28]. EVM code is composed of stack-based bytecodes, making it difficult for humans to interpret them directly. Panoramix analyzes these bytecodes to extract the start and end of functions, control flow, operations, etc., and then decompiles them into a high-level language similar to Solidity. In this process, function signatures are used to identify each function. A function signature is a 4-byte identifier generated by hashing a string that connects the function name and input variable types using the Keccak-256 hash function. For example, the transfer(address to, uint256 amount) function has a signature of 0xa9059cbb. However, due to the unilateral nature of the hash function, it is difficult to directly identify the original function name or parameter types with the signature alone. This makes it challenging to accurately understand the meaning of the function in the decompiled code. To solve this problem, the Ethereum Signature Database is used [
29]. This database, a community-based open-source project, stores various function signatures and their corresponding function names and parameter information. Developers register and share new function signatures to help others easily identify the functions. Therefore, Panoramix Decompiler compares the function signatures extracted from the EVM code with the Ethereum Signature Database, allowing it to clearly identify the original names and parameters of the restored functions. The Function Extractor identifies all public functions in the smart contract based on the matched information. Public functions can be called externally and perform the main functions of the smart contract, making them particularly important in security analysis. It collects information on the structure, parameters, return values, and other functions or operations called internally within each function, providing a basis for tracking balance changes and detecting backdoor codes in subsequent stages.
3.2. Balance Tracker
The Balance Tracker analyzes the public functions generated by the Function Extractor to classify candidate functions that pose a risk of being backdoor functions. A candidate function is defined as a function that has balance changes within it or contains a proxy-type function. To this end, the proxy function patterns are inspected, and balance changes are tracked.
First, the command to call another contract is inspected to examine the proxy function pattern. The method for calling another contract on the Ethereum network can be divided into Call, DELE-GATECALL, and STATICCALL, as shown in
Table 1 below. CALL and STATICCALL can execute the code of the called contract and receive the result. For example, looking at the staticTransfer function in Algorithm 4, the ADD and SUB functions that process the increase and decrease of the balance are called from the calculator address, and the results are received and applied. If the developer modifies the address of the calculator function, they can execute the backdoor code. In addition, DELEGATECALL is a method that is executed directly in the context of the caller through the function call, enabling direct backdoor code application. For example, looking at the transfer function in Algorithm 4, the transfer function is called from the calculator address, and the transfer is processed without directly calculating the balance within the function. If the developer modifies the calculator address, they can execute the backdoor code. Therefore, the presence of CALL, DELEGATECALL, and STATICCALL commands is inspected and then classified as candidate functions.
Then, for the functions, the balance changes that may occur when the function is executed are tracked and classified as candidate functions. Except for proxy, all of the backdoor code types explained in
Section 2.2—token generation, destroy token, transfer limitation, funds manipulation, and transfer fee—cause balance changes. For example, in the case of the token generation backdoor, the balance increases when the function is executed, but a new balance is generated without a corresponding decrease or by a larger amount compared to the existing balance. To track such balance changes, it is necessary to first identify the balance to be tracked. In the smart contract, the balance is managed as a Mapping structure that stores the user wallet address as a key and the balance as data, as shown in Algorithm 7, and can be queried using the balanceOf function, which is an ERC-20 standard function [
30]. Therefore, to identify the balance variable, the variables in the mapping structure are identified, and the variables returned by the balanceOf function are tracked to identify the variable that stores the balance.
| Algorithm 7. Solidity code of the balanceOf function. |
| 1| | mapping(address => uint256) private balance; |
| 2| | function balanceOf(address account) public view returns (uint256) { |
| 3| | return balance[account]; |
| 4| | } |
After that, whether there is an operation on the balance variable in each function is closely inspected. Operations on the balance variable can be largely divided into two cases. The first case is when the balance variable is directly used for the operation, which means the balance variable is directly used within the function, as in line 4 of Algorithm 1. In this case, all locations where the balance variable is used are found, and the result of the operation and the location where the operation occurred are recorded. The second case is when the operation is performed using another variable and the result is stored in the balance variable, which means the value assigned to the balance variable is the result of the operation of other variables, as in line 12 of Algorithm 4. In this case, all variables that assign values to the balance variable must be tracked back. To this end, a variable tracing process is performed. Variable tracing identifies the variables assigned to the balance variable and confirms the declaration location and initial value of the variable. Then, the operation of the identified variables is tracked, and the location of the operation and the result value are recorded. Finally, the candidate functions are classified by integrating the results of all functions in which balance changes occurred and proxy function patterns. The candidate functions identified in this way are then finally classified as backdoor codes in the backdoor code inspector.
3.3. Backdoor Code Inspector
The backdoor code inspector analyzes balance changes and conditional statements of the candidate function generated in the balance tracker and classifies them as backdoor codes. To this end, it analyzes the balance change pattern of the candidate function and identifies the cause and characteristics of the balance change through conditional statements to determine the existence of a backdoor. The type of backdoor code is classified into the six attack types outlined in
Section 2.2: token generation, destroy token, transaction limitation, funds manipulation, fee, and proxy.
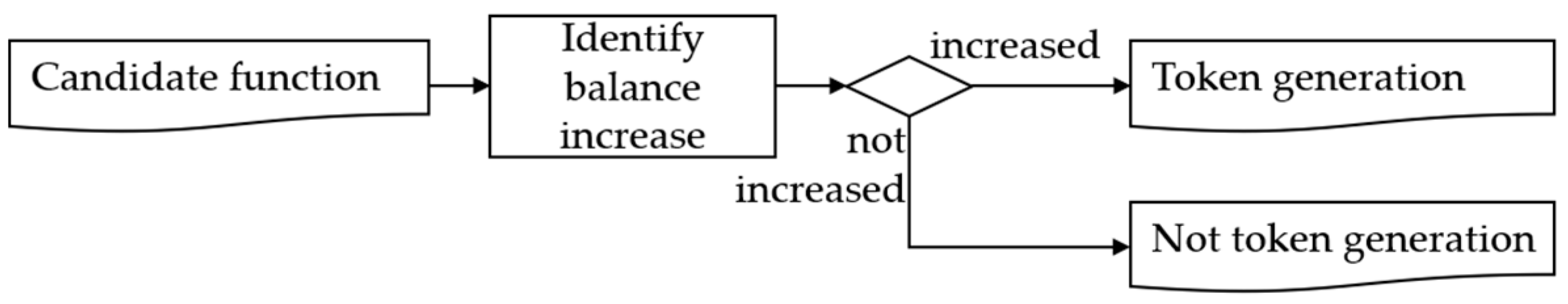
Token generation causes the result of balance tracking to lead to an increase in the balance. To detect this, the balance tracking results of the candidate function are analyzed as shown in
Figure 4, and if a new balance is generated without decreasing the balance or if a larger amount of balance is increased compared to the existing one, it is classified as a token generation backdoor.
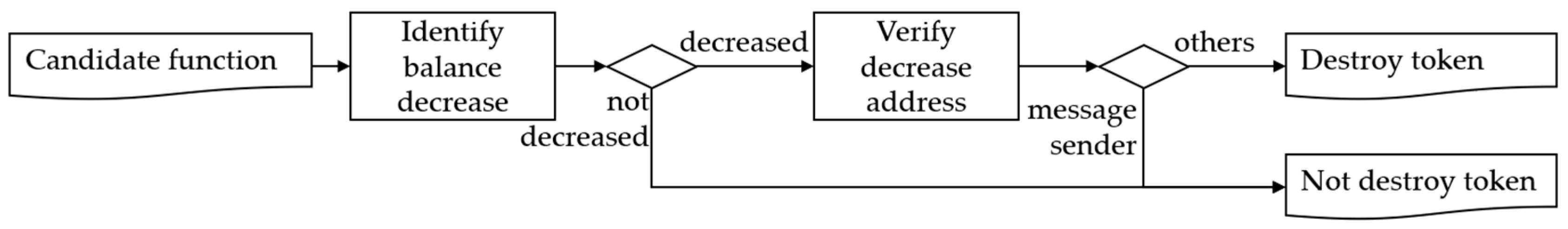
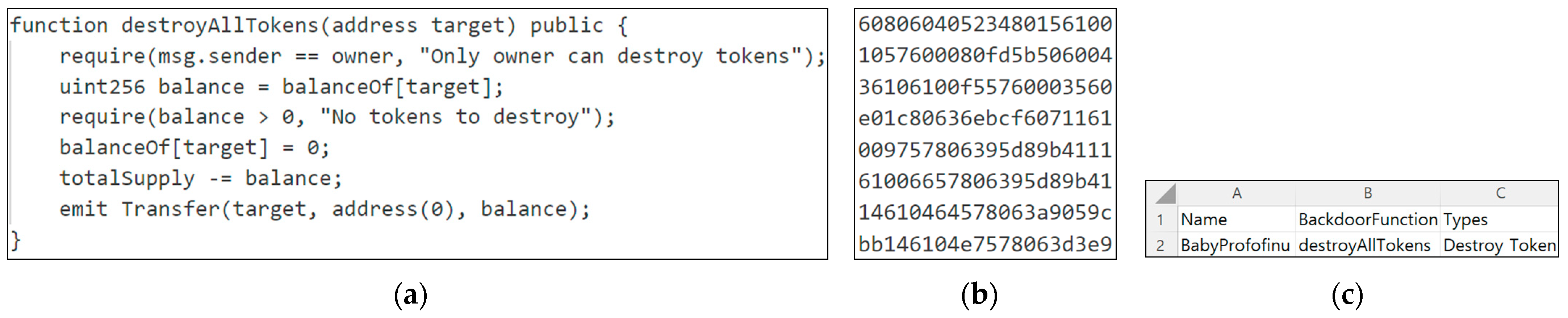
Destroy token causes the result of balance tracking to lead to a decrease in someone else’s balance. To detect this, the balance tracking result of the candidate function is analyzed as shown in
Figure 5 to inspect whether there is only a decrease in the balance or whether there is a decrease in the balance that is greater than the input value. Then, whether the address, in which the decrease occurs, is the message sender is inspected, and if it is not the message sender, it is classified as a destroy token backdoor.
Transaction limitation restricts balance transfers through a conditional statement before the balance transfer. To detect this, candidate functions are analyzed as shown in
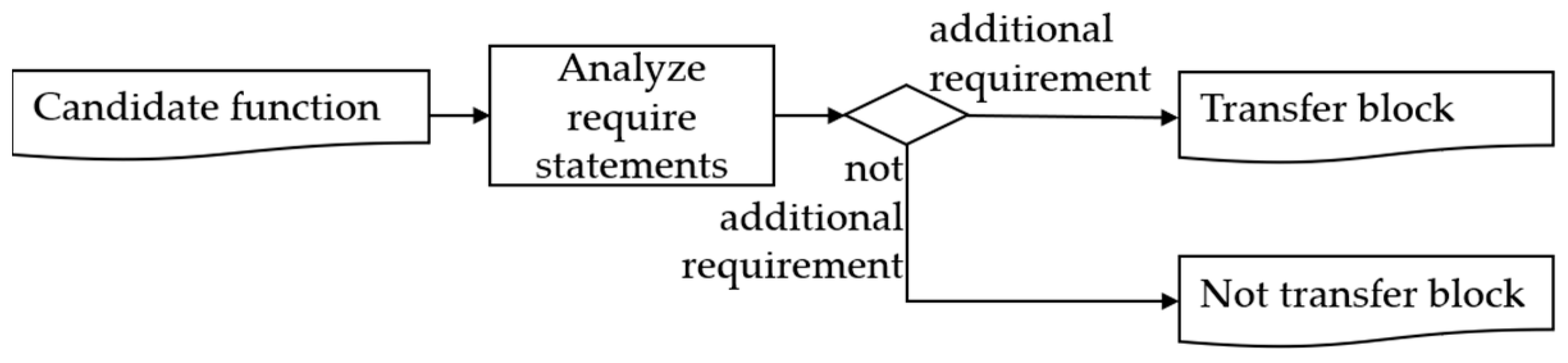
Figure 6, and conditional statements of the function with the balance transfer are analyzed to see if there is an additional conditional statement. The additional conditional statement is not a general conditional statement that inspects balance or overflow, but a conditional statement that allows or prohibits the transfer, depending on a variable or an account. If an additional conditional statement is found as a result of the analysis, it is classified as a transaction limitation backdoor.
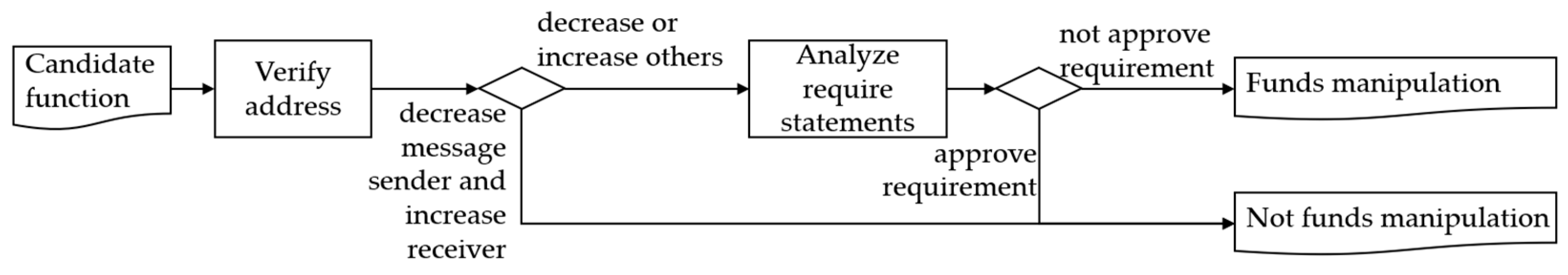
Funds manipulation causes the balance transfer after a call from an unauthorized user. To detect this, whether the message sender’s balance decreases and the balance of the input address increases in the candidate function is inspected, as shown in
Figure 7. This confirms whether the balance of another account decreases, or whether the recipient’s balance increases normally. Then, the conditional statements of the function approval are inspected, and if they do not match the approval process, it is classified as a funds manipulation backdoor.
Transfer fee causes a decrease in the resulting value of the transfer by the amount of the fee. To detect this, the calculation of the fee is analyzed regarding the balance change in the candidate function, as shown in
Figure 8. If a small value is sent or if there is a fee transfer, it is classified as a transfer fee backdoor.
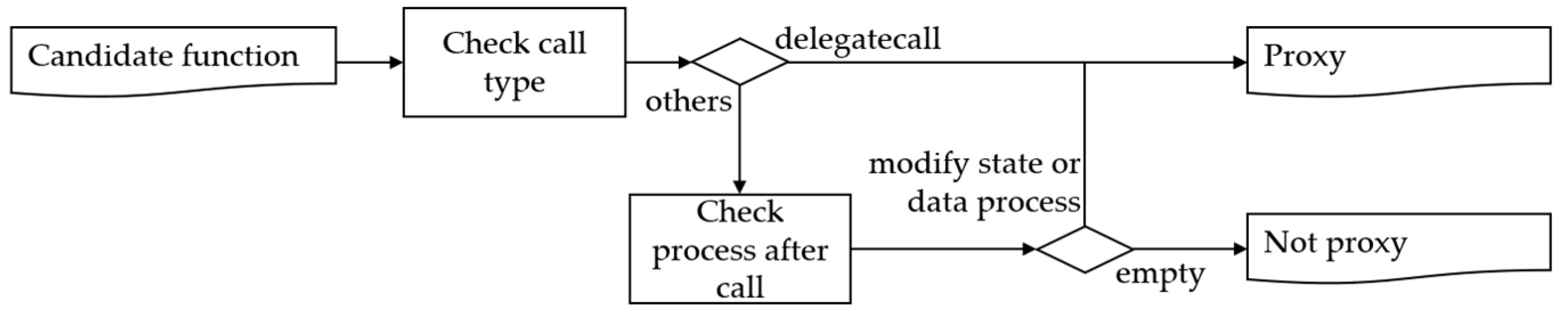
Proxy can execute backdoor code by calling the functions of other addresses. To detect this, the method of calling other functions is confirmed in the candidate function, as shown in
Figure 9. In the case of DELEGATECALL, it is classified as a proxy backdoor since it can directly execute backdoor code in the present contract. Additionally, in the case of CALL and STATICCALL, if there is a balance change or state change after the call, it is classified as a proxy backdoor.
Whether backdoor code is detected for each function is determined based on the final classified results. Through this process, users can determine whether a specific function has a potential security risk.
3.4. Extending the Model to Other Platforms
The proposed balance-tracking-based backdoor detection model’s applicability can be enhanced by extending it to blockchain environments beyond the Ethereum platform. The model operates by analyzing the EVM code of standard Ethereum smart contracts. Platforms such as Binance Smart Chain, which also utilizes EVM, do not present significant challenges for application. However, platforms that employ different smart contract architectures, such as Solana or Sui, pose challenges due to differences in the languages and formats of their smart contracts. To address this issue, there needs to be an interface.
The interface for inspecting smart contracts on other platforms can be accessed through the model’s balance tracker. However, if the contracts on these platforms do not comply with the ERC-20 standard, the model’s accuracy may decrease. In order to resolve this, the standards of each platform need to be converted to conform to the ERC-20 standard.
Table 2 lists the ERC-20 standard functions necessary for this conversion, and functions corresponding to these descriptions should be mapped accordingly. The balanceOf function, which returns an account’s balance, is essential for accurate balance tracking in the model. The transfer function, responsible for token transfers, is crucial for analyzing transfer restrictions and fees. Similarly, the transferFrom, approve, and allowance functions play important roles in permission tracking, which is vital for detecting unauthorized access or manipulation.
5. Conclusions
This study proposed a balance-tracking-based backdoor code detection model to efficiently detect backdoor codes hidden in Ethereum smart contracts. To overcome the limitations of existing static and dynamic detection models, the model was designed to effectively detect even modified or hidden backdoor codes by tracking balance changes within functions and analyzing conditional statements.
The proposed model consists of three major components. First, public functions were extracted from EVM codes through the Function Extractor to identify the target functions for analysis. Then, balance changes that occurred in the extracted functions were tracked using the Balance Tracker, and proxy patterns were identified to select candidate functions that had the potential to be backdoor codes. Finally, in the Backdoor Code Inspector, the conditional statements and patterns of candidate functions were analyzed in detail to classify backdoor codes into six types.
As a result of the experiment, the proposed model achieved 98% accuracy in detecting backdoor codes. Specifically, the model’s accuracy ranged from 97.4% to 99.4% across different backdoor code types, with precision values between 0.95 and 0.98 and recall values from 0.95 to 1.0. This means that the proposed model can accurately detect various types of backdoor codes with minimal false positives and false negatives. In particular, the reliability and effectiveness of the model were proven since it accurately identified almost all backdoor codes in smart contracts with multiple backdoor codes. These results demonstrate the model’s effectiveness in responding to complex attacks that combine multiple backdoors.
This study presented a practically applicable backdoor code detection method to enhance the security level of smart contracts, contributing to allowing users to recognize the risks of smart contracts in advance and prevent damage. In addition, it has high practical applicability in that it can perform analysis with only bytecode, regardless of whether the source code is disclosed.
Future studies will focus on developing a generalized backdoor code detection model that can be applied to other blockchain platforms beyond Ethereum, contributing to enhancing the security of the entire blockchain ecosystem.