Abstract
The access control system is a critical element in intelligent buildings. In this paper, we present SPCL, an innovative access control system designed to facilitate building entry through the use of mobile phones. Our system aims to provide a secure and convenient solution for building access, capitalizing on the widespread availability and capabilities of mobile devices. Additionally, we propose a lightweight authentication protocol to enhance security. The performance of the protocol is measured for different curves at different frequencies, proving that the protocol is more suitable for door lock systems than the benchmark protocol. In addition, we investigated the security and usability of SPCL. Finally, a comparison of the security of human-lock interfaces for smart locks and blockchain-based payment methods are discussed.
1. Introduction
A lock is the core of an entire access control system. The oldest known key-operated lock can be traced back to ancient Egypt, approximately 4000 years ago [1]. Locks are also indispensable to modern people’s daily lives. For example, mechanical locks, which may be one of the most familiar objects to everyone, have been used for hundreds of years [2]. However, as the pace of modern life is accelerating, more features are expected from access control systems, and locks also evolve incessantly, especially in the field of intelligent buildings [3,4,5]. Consequently, a smart lock [6] is surfacing to improve life quality [7], while also decreasing the security risks and costs effectively [8]. Nowadays, smart locks have become a necessary part of intelligent buildings.
A huge amount of studies have been done in the domain of smart locks over the last couple of years. For instance, Park et al. [9] presented a smart digital door lock solution for home automation. Padmapriya and KalaJames [10] put forward an improved face recognition approach for a vehicle security system. Furthermore, Chang and Jiang studied a binary single-key-lock system [11], and Wu [12] studied a matrix-based lock system in order to enhance security further.
After entering the mobile internet age, more and more smart devices, e.g., smart locks, can be managed by mobile devices easily. For instance, Iftode et al. [13] designed a mobile phone based architecture that enables users to interact with embedded systems by cell phones. In [14], a remote monitoring intelligence system based on fingerprints through wireless transmitting and receiving, was introduced. In [15], the authors developed and implemented a remote lock system utilizing wireless communication on a smart phone by a dedicated Android application. In 2007, Bauer et al. [16] deployed a demo smartphone-based system in university buildings, aiming to replace existing access control technologies. The authors in [17] proposed an access control system for intelligent buildings in 2016. In 2018, Patil et al. [18] proposed a security protocol between smartphones, smart locks, and cloud servers, and discussed possible security vulnerabilities. In 2021, Taslim et al. [19] proposed a smart home door lock system using security protocol in the Internet of Things (IoT) scenario is proposed, which has the problems of unencrypted data transmission and insufficient authentication methods. Ahmad et al. [20] developed an enhanced access control system for smart locks, using cloud and edge computing to improve authorization, focusing on scalability and performance. Unfortunately, the approach adds complexity in deploying and enforcing policies. In 2023, Guntur et al. [21] designed an IoT-enhanced smart door lock using Radio-Frequency Identification (RFID) for secure access, which is affordable, user-friendly, and includes a fire alarm for additional safety, but it’s vulnerable to card loss attacks and unauthorized access. Mehmood et al. [22] proposed a smart disposable door lock system based on invisible touch sensors to prevent the carrying, loss and copying of cards.
Traditional smart lock solutions, while offering convenience, often harbor significant security flaws, including susceptibility to cyber-attacks, data breaches, and unauthorized access. These vulnerabilities primarily stem from their reliance on centralized databases and a lack of robust encryption methodologies. Additionally, the opaque nature of transaction and access logs within these systems has raised concerns regarding their trustworthiness and auditability—critical aspects for both residential and commercial applications. In recent years, there have been some blockchain-based solutions in IoT device scenarios [23,24,25], but these solutions are difficult to ensure communication security. The integration of blockchain smart contracts with authentication protocol, especially within the context of smart lock systems, signifies a paradigm shift towards more secure, transparent, and efficient operations. This paper presents a smart lock solution that supports blockchain, aimed at addressing the prevalent security gaps and operational inefficiencies inherent in conventional centralized smart lock solutions.
Building on the aforementioned studies, we suggest implementing a smartphone-based smart building access control system. It boasts high security and availability, while ensuring efficiency and user privacy. The main contributions of this paper can be outlined as follows:
- (1)
- A novel access control system, named “Smart-Phone-Controlled-Lock” (SPCL), integrating smart lock technology with mobile phone-based access, has been designed and developed. A lightweight privacy protection protocol called the “SPCL protocol” is proposed and implemented. Its performance works best when the computing performance of the two devices is similar to each other.
- (2)
- The proposed SPCL protocol is formally analyzed using the eCK security model to prove that SPCL achieves the required security goals. Other security features of the protocol are discussed as well.
- (3)
- Survey approaches, including a questionnaire and a focus group, are used to study the attitudes of candidates towards access control systems and several unlocking mechanisms, e.g., biometric identification, password pad and sliding card. It should be a jumping-off point for future studies.
- (4)
- Security comparison regarding human-lock interfaces and blockchain based payment methods for smart locks are discussed.
The remainder of the paper is organized as follows. Section 2 outlines the SPCL system and describes its security mechanism. Section 3 proposes the SPCL protocol and describes its process for establishing authentication. Section 4 provides a proof of the eCK model, as well as an analysis of the security properties of the proposed protocol. Section 5 investigates the performance of SPCL through extensive experiments. Section 6 describes the research methodology used in our survey as well as the survey results and discussion. Section 7 provides a more in-depth discussion of SPCL security mechanisms, popular unlocking methods, and blockchain-based solutions. Section 8 compares SPCL with several of the most representative related works. Section 9 draws conclusions and outlines the future.
2. SPCL Overview
In this section, we introduce SPCL, a smart lock- and smartphone-based access control system that offers a convenient and secure solution for implementing access control in intelligent buildings. The security mechanism in the system is also studied.
2.1. SPCL Architecture
SPCL is a prototypical system which can be used to control smart locks through mobile applications. It is comprised of five primary parts: cloud server, mobile client, desktop/laptop client, switch and smart devices. The system architecture is shown in Figure 1.
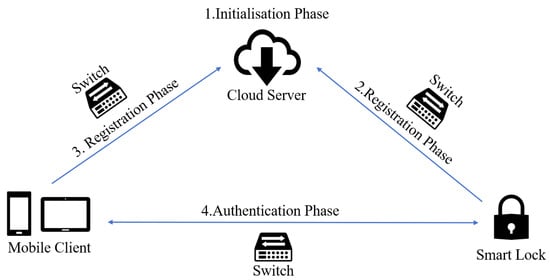
Figure 1.
System architecture of SPCL.
A cloud server (CS) acts as a trusted third party. It is used for the registration of smart locks and mobile clients. It also stores registration information and unlocking log data.
A mobile client (MC) is often a smart phone or tablet PC. It can authenticate with the smart lock, after registering with the cloud server. It works like a key for the user to open the door.
Switches forward messages. They work like a bridge between the cloud server and the smart devices.
Smart devices refer to devices such as smart locks (), shared charging facilities and smart home appliances. They can connect to the cloud server or mobile client via a wireless channel.
2.2. Security Model
We utilize the eCK security model [26] to analyze our proposed scheme. Let represent the communicating parties; n represents the total number of parties; represents the session identifier of a completed session; and represent the messages sent by . The eCK security experiment is conducted by an adversary against an AKE protocol with a challenger , which captures real-world attacks through the queries issued by :
- (): This query allows to run the protocol by sending message to the session . It returns the next message according to the protocol conversation so far.
- (): This query returns the ephemeral private keys held by the session to .
- (): This query return the session key for a session to .
- (A): This query returns the long-term private key of party A to .
- (): At some point, selects one session for a query. This session must be fresh. (defined in Definition 1).
Definition 1
(Fresh Session). Let owned by an honest party with peer , and is also honest. Let be the session identifier of the matching session (defined in Definition 2) of , if it exists. The session is fresh if none of the following conditions hold:
- (1)
- issues () or () query (if exists);
- (2)
- exists and makes one of the following queries:
- (A) and (), or
- (B) and ;
- (3)
- does not exist and makes one of the following queries:
- (A) and (), or
- (B)
Definition 2
(Matching session). The party executing the session is called the owner of the session and the other party is called the peer. Two sessions: owned by A with peer B and owned by B with peer A, are matching sessions if all messages sent (or received) by A are identical to those received (or sent) by B.
In the eCK security experiment, plays with a challenger of a hard problem as follows:
- Queries: makes queries as defined aforementioned at will.
- Test: chooses a fresh session as the session.
- Queries after test: makes queries as in Queries step but cannot query the session.
- Guess: flips a fair coin , and returns with the session key held by if , or a random string of the same length otherwise. outputs .
wins the eCK experiment if .
Definition 3
(eCK security). An AKE protocol π is eCK-secure if the advantage for all probabilistic polynomial time (PPT) adversary against π in winning the eCK experiment, denoted by
is negligible.
2.3. Security Mechanisms
An elliptic curve based on the prime field is defined as follow [27]:
Let be an additive group on the elliptic curve and G be a generator of . Hardness assumptions are defined as follows [27].
Definition 4
(Discrete Logarithm (DLOG) Problem). Given , where , compute x.
Definition 5
(Computational Diffie-Hellman (CDH) Problem). Given , , where , compute .
Definition 6
(Decisional Diffie-Hellman (DDH) Problem). Given , where , determine whether or not.
Definition 7
(Gap Diffie-Hellman (GDH) Problem). Given , where , as well as an oracle that solves the DDH problem on , compute .
3. The Proposed Scheme SPCL
This section introduces SPCL protocol, including the initialisation phase, the registration phase and the authentication phase. Notations and corresponding descriptions are given in Table 1.

Table 1.
Symbols used in SPCL.
3.1. Initialisation Phase
This part introduces the initialisation method [27]. The cloud server () initialises system parameters: , E, G, , u, v, and and .
3.2. Registration Phase
In the registration phase, the mobile client () and the smart lock () will register with the cloud server ().
- (1)
- Smart lock registration.generates an identity identifier for and calculates , . stores in its registry and sends it to via secure channel.
- (2)
- Registration information access.The user uses to scan the QR code on and obtains from . stores in its registry. The process of scanning the QR is considered a secure channel.
- (3)
- Mobile client registration.① generates its unique identifier and sends to via secure channel.② checks and matches with . If there is already matching , checks whether is in its registry; otherwise, picks a public-private key pair and for : picks a random number , calculates , and checks whether is in its registry.③ After that, stores in its registry and sends it to .④ receives from and completes the registration phase of .
3.3. Authentication Phase
In the authentication phase, the mobile client () establishes authentication with the smart lock ().
- (1)
- Requesting authentication.① picks a random value and computes . chooses the identifier of the smart lock you want to open. picks a random value and computes .② generates the current time-stamp and computes . sends message to via wireless channels.
- (2)
- Responding to the mobile client.① Upon receiving , verifies and decrypts as . computes and .② After that, calculates and the current time-stamp .③ Then, sends message to .
- (3)
- Accepting the mobile client’s session key.① Upon receiving , verifies and . If the verification succeeds, calculates and .② Then, calculates and checks whether . If verification is successful, computes and the session key . Then, sends message to .
- (4)
- Accepting the smart lock’s session key.Upon receiving , computes . Then checks whether . If verification is successful, calculates the session key . Thus, and successfully establish session keys.
4. Security Analysis
4.1. Provable Security of SPCL Protocol
The eCK model [26] is used to conduct a provable security proof for the SPCL protocol. The practical reasons for each step in the proof process are based on the formal proof process followed by the NAXOS protocol.
Theorem 1.
The SPCL protocol eCK-security if is modeled as independent random oracles and and problems are hard in G.
For any PPT adversary against SPCL that runs in time at most t, involves at most n honest parties, and activates at most k sessions, there exists a problem solver and a problem solver such that
where runs in time and runs in time .
Proof.
Let be any AKE adversary against SPCL protocol. The session key of the session is computed as for a 4-tuple . We will demonstrate how to use ’s ability to construct a solver for solving the problem. first selects the system parameter , and then sends to . As is a random oracle, can distinguish a session key from a random string with a significantly higher probability than in one of the following events:
- Guessing attack: correctly guesses the . The probability of guessing is , which is negligible.
- Key replication: If an adversary forces two distinct non-matching sessions to have the same session key, it can select one of the sessions as the session and query the key of the other session. This is because two non-matching sessions cannot have the same communicating parties and ephemeral public keys. The replication of keys is equivalent to finding a collision for the hash function . Therefore, the probability of Event occurring is , which is negligible.
- Forging attack: Adversary queries on the value () in the session owned by communicating with . We will construct a solver using an adversary that succeeds in a forging attack with non-negligible probability. simulates the game outlined above. During the game, has to answer all queries of the adversary . The following two sub-events should be considered.
- The session has a matching session owned by another honest party.
- No honest party owns a session matching with the session.
□
4.1.1. The Analysis of Event
selects matching sessions executed by honest parties and at random. If two matching sessions are selected, proceeds with probability . generates , and , . sets (instead of ) and (instead of ). With a probability of , chooses one of the selected sessions as a session and the other as its matching session. If wins in this event, can solve the problem. The session key for the selected session is supposed to be , where the 4-tuple includes the value . In order to win, must have queried to the random oracle .
If the selected session is indeed the session, is permitted to reveal a subset of . But is not allowed to reveal both or . The only way for to differentiate between this simulated eCK experiment and a real eCK experiment is by querying or (this way, will discover that and were not computed correctly). Probability that makes such queries is at most
Therefore, we have
4.1.2. The Analysis of Event
If selects a session for which no matching session exists, modifies the experiment as follows.
: randomly selects an eCK session in which is the owner.
picks a random party , and sets as its long-term public key. Note that doesn’t know long-term private key corresponding to . Therefore, it cannot effectively simulate eCK sessions executed by . sets instead of . sets a session key ( to be a random value. can manage session key and ephemeral secret key reveals by making and queries.
Assuming is an adversary-controlled party, can compute the session key, reveal the session key , and detect that it is fake. To mitigate this issue, monitors ’s random oracle queries, and if ever queries to (for some , ), checks if , and if yes, replies with the session key . Similarly, while computing , checks if matches any previous response from the random oracle. cannot detect that it is in the simulated eCK experiment unless it queries or reveals ’s long-term private key using the query. The first event reveals , and allows to solve the problem, which occurs with probability at most
: also randomly selects an eCK session in which is the peer.
Let the owner of this session be denoted by . normally generates , and , . Then, sets (instead of and (instead of ). With probability at least (where is to pick the correct party , and is to pick the correct session), picks the selected session as the session and solves the problem if it wins. is not allowed to reveal both , and cannot corrupt . In this event, the only way that can distinguish this simulated eCK experiment from a true eCK experiment is if queries . By Event it happens with probability at most
Overall, the success probability of is at most
Therefore, we have:
Finally, under the GDH assumption, is negligible. Therefore, is negligible, and SPCL protocol has security.
4.2. Security Properties
Regarding security properties, this paper thoroughly examines the security properties of the SPCL protocol and highlights the advantages it offers compared to baseline protocols.
4.2.1. Perfect Forward Security
In our scheme, even if can query the long-term secrets of , and , is unable to compute the session key without the ephemeral secrets of or .
4.2.2. Identity Anonymity
In our scheme, uses the pseudonym identifier so that cannot obtain from the message transmitted by . This prevents potential identity leaks and protects user privacy.
4.2.3. Man-in-the-Middle Attack
has the ability to impersonate one of the communicating parties as well as eavesdrop on the message. In our scheme, is unable to compute (, ) or (, ), and is unable to verify that and and thus establish communication.
4.2.4. Impersonation Attack
Assume that successfully eavesdrops on the long-term key ( or ). Since the ephemeral secrets cannot be obtained, cannot generate the messages (,) or and pass from checking ( and ). Therefore, impersonation attacks can be eliminated.
4.2.5. Replay Attack
In our scheme, there are time stamps (, ) and random numbers (, ). In order to implement a replay attack, must forge the timestamp to pass the verification, and still needs to obtain the long-term private keys and temporary secrets of and . It is extremely difficult for to crack and obtain this information, so the probability of a successful replay attack is extremely low and can almost be ignored.
4.2.6. Advantage of SPCL
Firstly, the SPCL protocol provides perfect forward secrecy, in contrast to the Llakep [28] and PSLA [27]. This secrecy ensures the protection of users’ ephemeral secrets in scenarios involving smartphone-controlled locks. Secondly, the SPCL protocol surpasses the Llakep [28], ESEAP [29], Xie et al. [30], and SM2 [31] in terms of user anonymity. This highlights the SPCL protocol’s greater emphasis on the privacy and security of users. In conclusion, the SPCL protocol is more suitable for the smart phone controlled lock system.
5. Implementation and Evaluation
In the implementation and evaluation section, the performance of the SPCL protocol is evaluated. During our experiment, we used two Raspberry Pis as the smart lock and the mobile client, respectively. The primitive access system is shown in Figure 2 below.
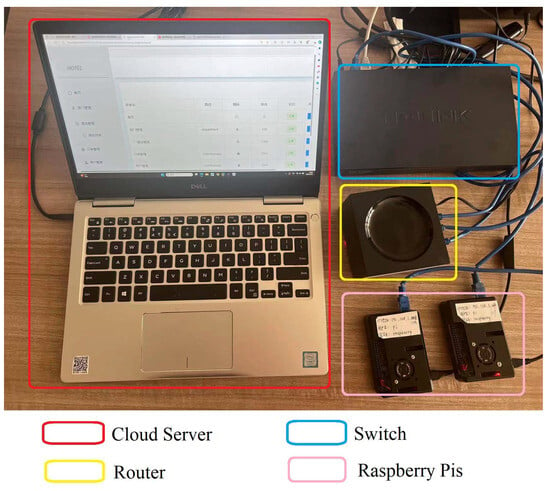
Figure 2.
A primitive implementation of the proposed SPCL system.
5.1. System Setup
We have implemented an online hotel reservation system using a combination of Windows, Apache, MySQL, and PHP. Through our system, users can conveniently manage and control smart locks associated with their reservations using mobile clients. Table 2 provides a comprehensive overview of the features available in our experimental system.

Table 2.
Features of SPCL system.
5.2. Theoretical Analysis
Let , , , and represent elliptic curve point scalar multiplication operation time, encryption and decryption time, key derivation function time, hash, bitwise XOR operation time. We run the above operations in a simulated environment. The results of the simulation is that ms, ms, ms, ms and ms. The performance comparison between the SPCL protocol and the baseline protocol is shown in Table 3.

Table 3.
Comparison of computational costs and running time.
Table 3 shows that SPCL requires the least computational cost in , so the final total running time is the shortest. Regarding the computational cost for , SPCL ranks as having the second lowest.
5.3. Experiment I
In Experiment I, the frequencies of two Raspberry Pis are set to 1.2 GHz each. During the experiment, the running time and calculation time of each protocol under five elliptic curves were measured ten times and the average values were calculated. The experimental results under the elliptic curve P-256 are shown in Figure 3. We find that the running time and calculation time of SPCL are the lowest among all elliptic curves.
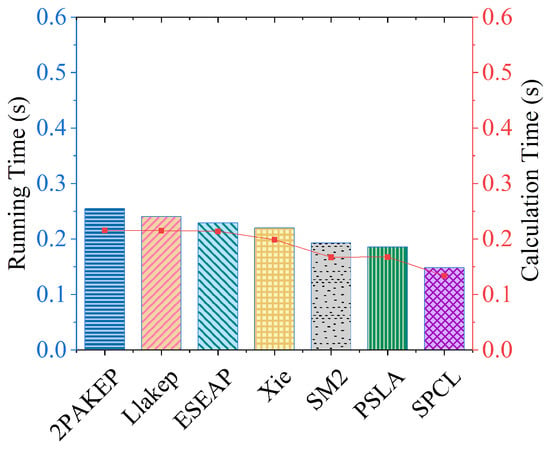
Figure 3.
Comparison of average computational and running time under balanced computing power.
5.4. Experiment II
In Experiment II, the frequency of the mobile client Raspberry Pi was changed to 0.6 GHz, 0.7 GHz, 0.8 GHz, 0.9 GHz, 1.0 GHz, and 1.1 GHz, and then each protocol was tested in different elliptic curves. The average values are calculated after ten running times and calculation times. The experimental results on elliptic curve P-256 are shown in Figure 4 and show that SPCL calculation time is the shortest in different curves and different frequencies. SPCL has the shortest running time under all curves when the Raspberry Pi frequency is set to 0.8/1.2 GHz, 0.9/1.2 GHz, 1.0/1.2 GHz, and 1.1/1.2 GHz, respectively. Under all curves, the Raspberry Pi frequency is 0.7/1.2 GHz and 0.6/1.2 GHz, and the running time of SPCL is second only to PSLA.
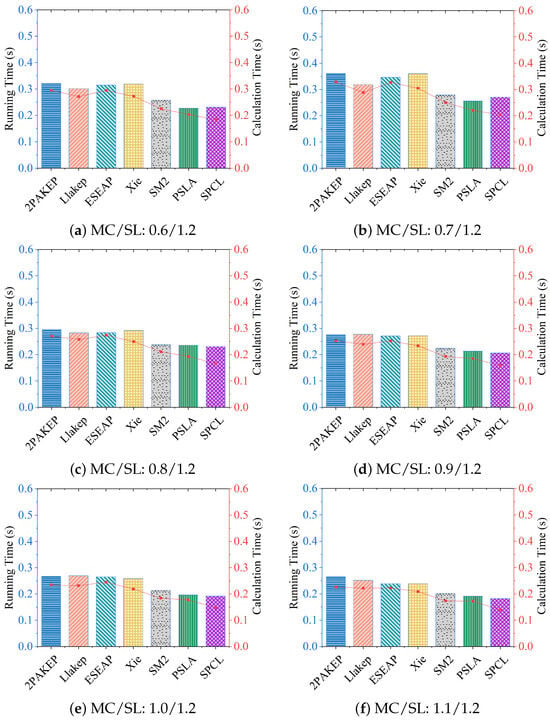
Figure 4.
Comparisons of average computational and running time in different curves and different frequencies.
5.5. Summary
Based on experiments and comparisons with other solutions, it can be observed that SPCL exhibits higher performance advantages as the computing power of mobile clients improves. Especially in the scenario where the computing power of both communicating parties is balanced, the SPCL protocol shows the best performance. In common door lock systems, the balanced computing power of the mobile client and the smart lock indicates that the SPCL protocol is more suitable for the hotel reservation system.
6. Survey and Focus Group
The survey mainly focuses on the following research questions:
- (i)
- What are the important features of smart locks?
- (ii)
- Which unlocking method is preferred?
It is hypothesized that:
- (i)
- Security is the most important feature of lock.
- (ii)
- The fingerprint-based unlocking method is the most desirable unlocking method.
6.1. Quantitative Methodology
In order to verify the hypotheses, we utilized a questionnaire as the primary research method. The questionnaire used in the survey is an online one with eighteen questions. The kinds of questions contain multiple choice, demographic, dichotomous and Likert Scale questions. Since the subjects are principally Chinese, in order to prevent the language barrier, we translated the questionnaire into Chinese. On average, it took two minutes for the voluntary participants to answer the questions. Furthermore, all the respondents remained anonymous in order to protect their privacy.
The samples are composed of 45 (37%) females and 77 males (63%), having different backgrounds, such as occupation and education levels. The pie chart below (Figure 5) illustrates the occupational composition of these samples. Table 4 below displays whether they know smart locks and whether they accept smart locks.
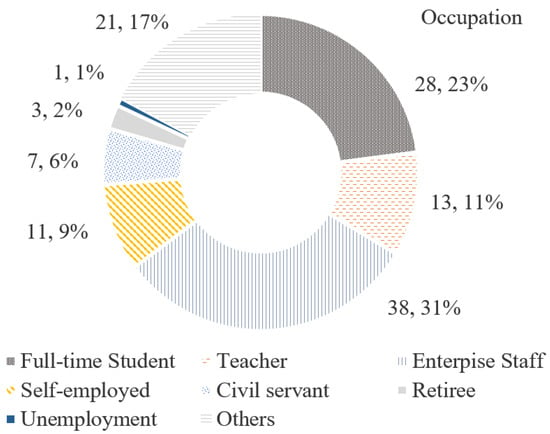
Figure 5.
Composition of the participant’s occupation.

Table 4.
Acceptance of smart locks from different Age Groups.
6.2. Qualitative Methodology
We used the focus group as an auxiliary research approach. A focus group is a recognized and valuable qualitative research approach that empowers researchers to establish causal relationships and delve into individuals’ subjective perceptions of their own experiences. Eight people (one teacher and seven students) took part in our focus group for about 45 min. Table 5 shows the basic characteristics of these eight candidates in our focus group. We use “♂” to represent male and “♀” to represent female. Our task was to conduct the discussion and develop sub-questions derived from the two basic questions mentioned above. The entire meeting conversation was recorded on a smartphone.

Table 5.
Individual background in the focus group.
6.3. Questionnaire
It is hypothesized that security is the most important factor when people select a lock between traditional and smart ones. Figure 6 below shows a histogram of the factors that will affect informants’ choices when they buy new locks. The result illustrates that security (86.89%) is the first important factor of all.
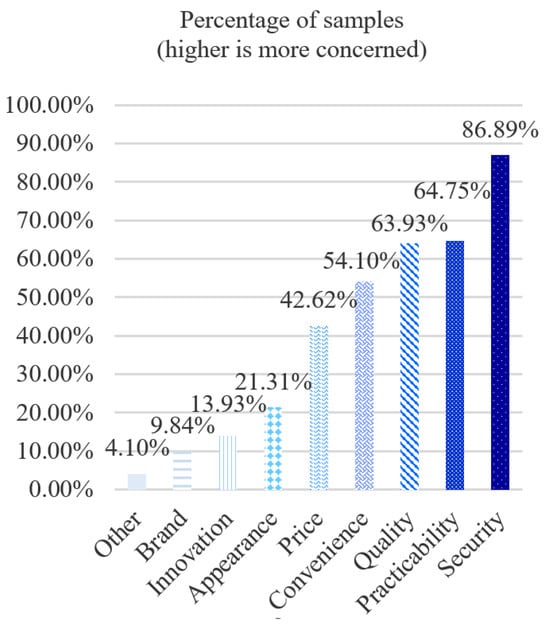
Figure 6.
Factors affecting people’s choice of smart locks.
In the following assessment questions, informants were asked to give marks (1 lowest, 5 highest) to both smart locks and traditional locks. The average mark of each aspect can be distinctly seen in Figure 7. As expected, smart locks acquire a better mark in the aspects of security.
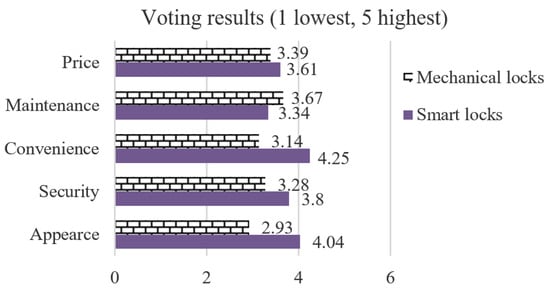
Figure 7.
Comparison of smart locks and mechanical locks.
Next, we let the participants give a mark for a series of unlocking styles. Figure 8 provides the average marks for each method. Fingerprint is the only one whose value is over 4. Facial recognition obtains 3.8 points, which is in the second place, followed by smart mobile devices.
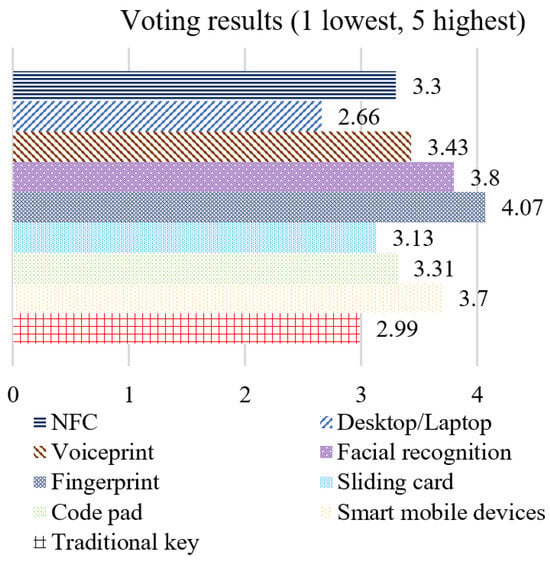
Figure 8.
Comparison of various unlocking styles.
Finally, Figure 9 indicates that the biometric unlocking style is the preferable method compared with the other two methods. In other words, people are more prone to using patterns rather than passwords to unlock doors.
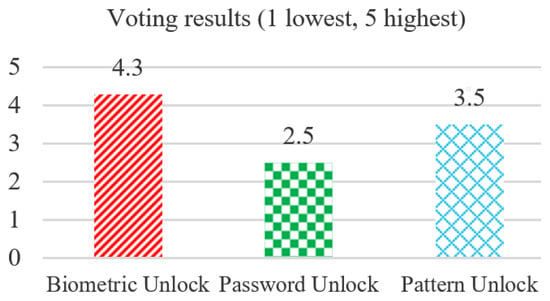
Figure 9.
Comparison of different unlocking styles by using smart phone.
6.4. Focus Group and Discussion
All of the group participants’ answers to smart locks were very meaningful and positive. A heated debate on the two topics mentioned previously was well organized and developed. The pros and cons of security mechanisms used in smart locks are analysed as well.
The first goal of the research was to wonder if security is significant in the eyes of modern people. Participants in this group totally agreed that security was the most important factor, and they believed that the smart lock had a high level of security.
The second purpose was to discover the most popular unlocking style. The results show that people like fingerprint unlocking style most. However, some focus group members expressed their worries about losing their fingerprints. Losing personal finger information might incur bigger risks rather than losing a key. Furthermore, one participant put forward a viewpoint that a fingerprint can be stolen and duplicated easily in our technologically advanced society.
The last aim of this focus group was to investigate people’s opinions towards “smart-phone-controlled-lock”. Most of the participants were more likely to use smart phones to control the smart locks owing to their expandability and convenience. Based on the survey results, we have proposed the SPCL solution, which utilizes both smartphones and smart locks for authentication. Furthermore, we have taken into consideration the concerns expressed by group members regarding fingerprint authentication and have incorporated a combination of smartphone passcodes and hardware authentication methods. This approach ensures security while enhancing user usability.
In addition, the focus group participants highlighted some detailed cases of security mechanisms on smart locks. For example, the smart lock should send a message to the host as a notification if the password of the smart lock is changed; some advanced smart locks even own a monitor that can take photos or record video. These powerful functionalities further enhance security, and we will prioritize their consideration in future improvements to SPCL.
7. Discussion
Security is vitally essential for access control systems like SPCL. In this section, a deep and detailed discussion of the unlocking methods is analyzed. Additionally, solutions supporting blockchain are introduced in detail.
7.1. Security Comparisons
This section of this paper summarizes a few common security mechanisms of unlocking methods that can be applied to the SPCL system to control smart locks conveniently.
7.1.1. Password
Password is the oldest and most basic encryption scheme, which is still continuing to be used widely. It is very common to set up a series of particular characters that are known by oneself to ensure security. There is no doubt that a long password means high security. However, it would lose the convenience when high security is guaranteed. Security and convenience appear to be conflicted with each other. If the length is short and has limited characters, it will be easy to remember and vice versa. Figure 10 shows a typical password input interface. In terms of the focus group’s conclusion, the favorable length of a password is six characters, and people tend to use only numbers to comprise their own passwords. When faced with higher security or more convenience, the user seems to have only one choice.
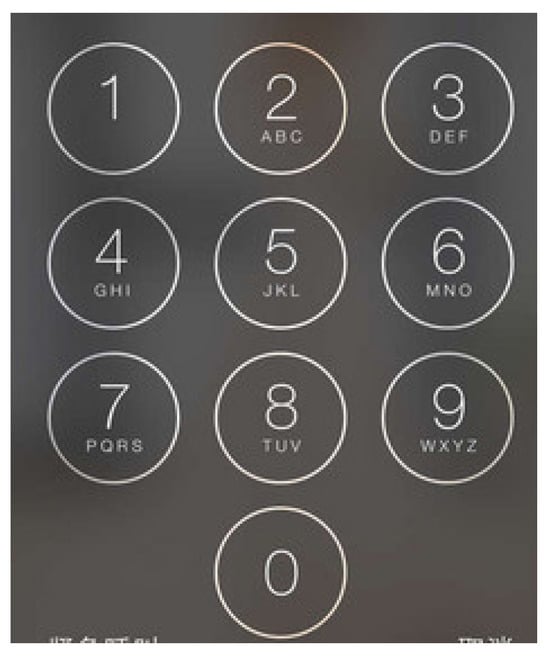
Figure 10.
Password panel.
7.1.2. Pattern
As another prevalent unlocking method, pattern unlock is also welcomed by the public. It largely improves both security and convenience. After all, drawing a pattern is much faster and simpler than inputting a long string of characters. Generally speaking, pattern unlock has found an ideal tradeoff between security and convenience. For another thing, compared with long passwords consisting of numbers and alphabets, the current pattern cipher strength is weaker and easier to break. For example, in Figure 11 the number of available Android unlock pattern is 389,112 [33]. Another potential issue is that the path of a certain pattern is fixed; the pattern (generally nine points) can be traced by the remaining trail on the screen. In spite of weaker security, according to the survey result, people prefer patterns to codes. Perhaps it is easier to remember a simple pattern than a series of characters.
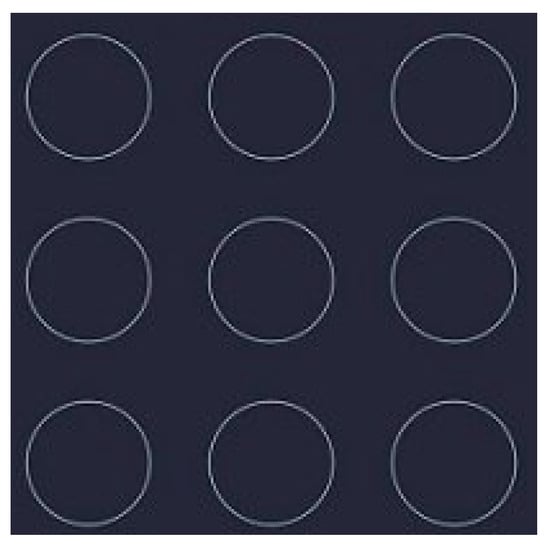
Figure 11.
Pattern panel.
7.1.3. Knock Code
Knock code (see Figure 12) refers to allowing users to unlock their devices by tapping the quadrants of the screen in a sequence. The system will automatically record the user’s knock sequence as the unlock password. One can knock on any position of the screen, even if the screen is off. This could be another solution that offers both security and convenience if a long enough tapping order is set. This innovative unlock style can also be easily used in our SPCL system to enhance security.
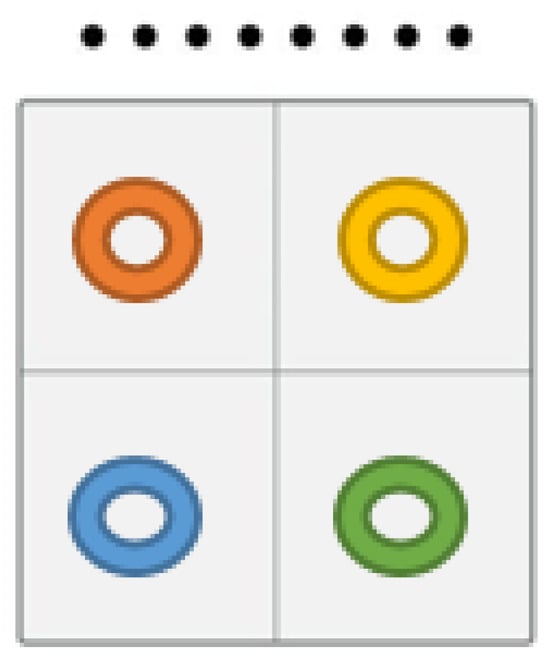
Figure 12.
Knock panel.
7.2. Supporting Blockchain
In this section, we proposed a blockchain based smart lock system. Suppose a user wants to pay and stay at a hostel for just one night. For SPCL, smart locks could be updated to support blockchains and crypto-currency. In this case, the user can directly pay to the smart lock without a cashier and open the hostel door.
A typical design is illustrated in Figure 13. The system consists of a Central Unit (CU) storing wallets for cryptocurrencies, smart locks, and the blockchain. The blockchain component is powered by smart contracts that provide functionalities for transferring, recording transactions, and querying transaction records, aimed at ensuring the transparency and immutability of transaction records.
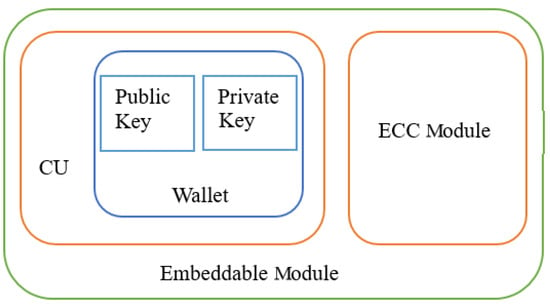
Figure 13.
Updated smart lock.
The general process is illustrated in Figure 14:
- (1)
- Authenticate: Users authenticate with the smart lock using their cryptocurrency wallet via the SPCL protocol.
- (2)
- Generation payment message: The smart lock generates a payment message . is the payment information. The smart lock sent the message to the user’s wallet.
- (3)
- Sign the payment message: After the user’s wallet receives , it verifies the message . If the verification is successful, the user signs the message .
- (4)
- Send signed payment information: The user wallet sends the signature message to the blockchain. Then, the blockchain verifies the signature .
- (5)
- Transaction execution by blockchain: If the verification is successful, the user’s identity is confirmed and the transfer operation is performed.
- (6)
- Payment information upload: The smart contract uploads on the blockchain.
- (7)
- Query the transaction Order: Users or hotel administrators can query through the smart contract on the blockchain.
- (8)
- Return transaction order: The smart contract returns to the user or the hotel administrators after querying the message.
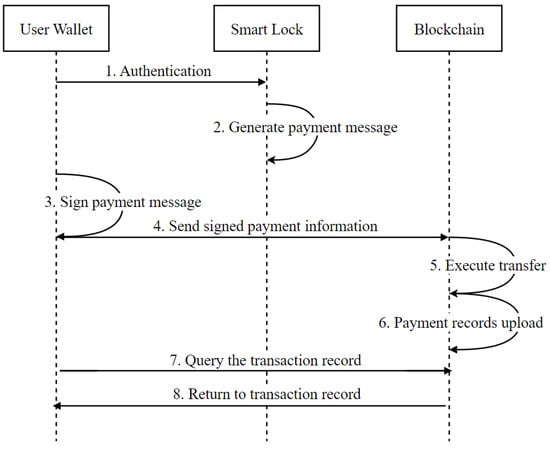
Figure 14.
Payment procedure for blockchain based smart lock system.
Our smart contract code can be viewed on this website (https://github.com/wujiax/SPCL.git, accessed on 16 March 2024).
Our blockchain system meticulously balances security with utility, offering enhanced authentication via the SPCL protocol to mitigate unauthorized access risks. Secure payment processing is achieved through encrypted transactions, safeguarding payment details against unauthorized interception. Blockchain’s autonomous verification further reduces fraud and error risks, ensuring transactions proceed transparently without third-party interference. In addition, the immutability of blockchain provides permanent verification of all transactions, thereby establishing a safe, reliable and transparent system to manage access and transactions in the hotel reservation system.
8. Related Work
In this section, we have compared and analyzed three categories of related work. The first category is a comparison of several similar intelligent access control solutions proposed previously. The second category is SPCL-related benchmark protocol comparison. The third category is a comparison of the differences in related solutions that support blockchain.
At present, smart phones are becoming considerably popular and ubiquitous in our daily lives [13,34]. With the widespread popularity of smart phones, the smart phone based applications have also gained growing attention. In this paper, we have built a prototype of SPCL, using a smart phone and a cloud server. SPCL can be applied to access control in intelligent buildings to enhance security and convenience. In the architecture presented by Jeong et al. [15], the mobile phone connects with the smart devices directly. Nevertheless, security mechanisms rely on the security of Bluetooth. In addition, the security solution is not quite flexible compared with SPCL. Patil et al. [18] proposed a security protocol for smart lock systems, but this solution did not fully consider user privacy. Guntur et al. [21] used RFID tags to unlock the lock. However, the loss of the card will bring risks to the security of the smart lock. The smart disposable door lock system based on invisible touch sensors by Mehmood et al. [22] is difficult to apply to hotels and other commercial occasions and lacks usability.
In SPCL-related benchmark protocol, Xie et al. [30] introduced an innovative access control scheme leveraging smart cards, albeit this approach has been critiqued for its vulnerability to attacks aimed at compromising long-term secrets. Similarly, the framework proposed by kumari et al. [29], while ambitious, demonstrates limitations in warding off replay attacks and fails to establish mutual authentication, thereby undermining the security integrity of smart lock systems. In an intriguing deviation from conventional methods, Zhang et al. [28] ventured into the metaverse realm, proposing an authentication protocol utilizing smart glasses for server authentication, in contrast to the ubiquitous smartphone-based approaches. However, when benchmarked against the SPCL framework, it becomes evident that SPCL not only offers a more energy-efficient and cost-effective solution but also excels in usability without necessitating the deployment of additional Virtual Reality (VR) equipment. Moreover, the PSLA scheme [27], despite its tailored applicability to environments characterized by disparate computing capabilities, is deemed less conducive for smart door lock scenarios due to its inadequacy in offering perfect forward security and potential exposure of short-term secrets.
Blockchain solutions have garnered widespread attention in recent years. In 2017, Zhang et al. [35] introduced a blockchain data sharing scheme for the healthcare sector. This system utilizes blockchain to store addresses (instead of actual health data) to maintain privacy and efficiency, allowing nodes to securely access and share health data. More recently, Zhang et al. [36] proposed a web3-based academic paper access control system for sharing papers. Due to the lack of blockchain support in current smart lock systems, SPCL provides a blockchain-enabled solution to provide safe and useful credentials for users using online hotel reservation systems.
9. Conclusions and Future Work
Nowadays, the advent of mobile technology, along with cloud computing, has drastically changed the way modern people connect with the world. With the continuous development of the IoT, wireless network control of smart devices has become more important for people. This paper integrates mobile and IoT technologies with cloud computing, offering a smart access control system for intelligent buildings. As a result, the building administrators are able to use mobile phones to control smart locks remotely and securely.
In order to enhance security, we designed and developed the SPCL protocol, providing proof of its security and usability and evaluating the performance of the security protocol. It is crucial to note, however, that while the SPCL protocol offers robust security features, it may not perform optimally in scenarios where computing power is unbalanced. Following that, we conducted an investigation into the issues arising from wireless network-controlled smart devices and discussed and summarized the findings of the investigation. Finally, we compared various popular unlocking methods and proposed a solution supported by blockchain technology.
For future work, more features and extensions will be applied to our system to enhance security and convenience, e.g., Near Field Communication (NFC), facial recognition, and fingerprint functions, which are already integrated into smart phones. In addition, we anticipate the incorporation of multiple authentication factors in future developments, which includes biometric systems and smart card technology. This strategic expansion in authentication methods is expected to significantly augment the system’s robustness and user accessibility.
Author Contributions
Conceptualization, J.W., N.X. and X.H. (Xin Huang); methodology, J.W., N.X., Z.L., X.H. (Xianbin Hong) and Y.Z.; software, J.W. and N.X.; validation, Z.L. and X.H. (Xianbin Hong); formal analysis, J.W., N.X. and J.Z.; investigation, J.W. and N.X.; resources, X.H. (Xin Huang) and J.Z.; data curation, J.W., N.X. and Y.Z.; writing—original draft preparation, J.W. and N.X.; writing—review and editing, N.X., Z.L., X.H. (Xianbin Hong) and Y.Z.; visualization, J.W. and Z.L.; supervision, X.H. (Xin Huang) and J.Z.; project administration, X.H. (Xin Huang); funding acquisition, X.H. (Xin Huang) and J.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research is supported by Shanxi Scholarship Council of China 2021-038, Applied Basic Research Project of Shanxi Province No. 20210302123130, and the National Natural Science Foundation of China under Grant No. 62002296; the Natural Science Foundation of Jiangsu Province under Grant No. BK20200250; and Xi’an Jiaotong-Liverpool University Research Development Fund under Grant No. RDF-21-02-014.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data supporting the conclusions of this article will be made available by the authors on request.
Acknowledgments
We would like to extend our heartfelt gratitude to Youjia Zhang for his invaluable contributions to this paper.
Conflicts of Interest
Author Zhen Li was employed by the company Shanghai Grandhonor Information Technology Co., Ltd. The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
References
- Ashley, S. Under lock and key. Mech. Eng. 1993, 115, 62. [Google Scholar]
- McCrie, R.D. A history of security. In The Handbook of Security; Palgrave Macmillan: London, UK, 2006; pp. 21–44. [Google Scholar]
- Son, J.Y.; Park, J.H.; Moon, K.D.; Lee, Y.H. Resource-aware smart home management system by constructing resource relation graph. IEEE Trans. Consum. Electron. 2011, 57, 1112–1119. [Google Scholar] [CrossRef]
- Zhang, L.; Liu, B.; Tang, Q.; Wu, L. The development and technological research of intelligent electrical building. In Proceedings of the 2014 China International Conference on Electricity Distribution (CICED), Shenzhen, China, 23–26 September 2014; pp. 88–92. [Google Scholar]
- Shao, H.; Fu, H. Design and implementation of intelligent building engineering information management system. In Proceedings of the 2014 7th International Conference on Intelligent Computation Technology and Automation, Changsha, China, 25–26 October 2014; pp. 158–161. [Google Scholar]
- Bott, E. Help: Working smarter lock, stock and password. Comput. Secur. 1995, 1, 39. [Google Scholar]
- Kaklauskas, A.; Zavadskas, E.K.; Naimavicienė, J.; Krutinis, M.; Plakys, V.; Venskus, D. Model for a complex analysis of intelligent built environment. Autom. Constr. 2010, 19, 326–340. [Google Scholar] [CrossRef]
- Ulusoy, C. Android Library Design and Implementation for Smart Lock Access Control Systems. Master’s Thesis, Aalto University, Espoo, Finland, 2015. [Google Scholar]
- Park, Y.T.; Sthapit, P.; Pyun, J.Y. Smart digital door lock for the home automation. In Proceedings of the TENCON 2009—2009 IEEE Region 10 Conference, Singapore, 23–26 November 2009; pp. 1–6. [Google Scholar]
- Padmapriya, S.; KalaJames, E.A. Real time smart car lock security system using face detection and recognition. In Proceedings of the 2012 International Conference on Computer Communication and Informatics, Chennai, India, 3–5 August 2012; pp. 1–6. [Google Scholar]
- Chang, C.K.; Jiang, T.M. A binary single-key-lock system for access control. IEEE Trans. Comput. 1989, 38, 1462–1466. [Google Scholar] [CrossRef]
- Wu, T. A refined key-lock access control system. In Proceedings of the IEEE 1993 National Aerospace and Electronics Conference-NAECON 1993, Dayton, OH, USA, 24–28 May 1993; pp. 583–587. [Google Scholar]
- Iftode, L.; Borcea, C.; Ravi, N.; Kang, P.; Zhou, P. Smart phone: An embedded system for universal interactions. In Proceedings of the 10th IEEE International Workshop on Future Trends of Distributed Computing Systems, Suzhou, China, 26–28 May 2004; pp. 88–94. [Google Scholar]
- Ping, W.; Guichu, W.; Wenbin, X.; Jianguo, L.; Peng, L. Remote Monitoring Intelligent System Based on Fingerprint Door Lock. In Proceedings of the 2010 International Conference on Intelligent Computation Technology and Automation, Changsha, China, 11–12 May 2010; Volume 2, pp. 1012–1014. [Google Scholar]
- Jeong, H.D.J.; Lee, W.; Lim, J.; Hyun, W. Utilizing a Bluetooth remote lock system for a smartphone. Pervasive Mob. Comput. 2015, 24, 150–165. [Google Scholar] [CrossRef]
- Bauer, L.; Cranor, L.F.; Reiter, M.K.; Vaniea, K. Lessons learned from the deployment of a smartphone-based access-control system. In Proceedings of the 3rd Symposium on Usable Privacy and Security, Pittsburgh, PA, USA, 18–20 July 2007; pp. 64–75. [Google Scholar]
- Xue, N.; Liang, L.; Zhang, J.; Huang, X. An access control system for intelligent buildings. In Proceedings of the 9th EAI International Conference on Mobile Multimedia Communications, Xi’an, China, 18–20 June 2016; pp. 11–17. [Google Scholar]
- Patil, B.; Vyas, P.; Shyamasundar, R. SecSmartLock: An architecture and protocol for designing secure smart locks. In Proceedings of the Information Systems Security: 14th International Conference, ICISS 2018, Bangalore, India, 17–19 December 2018; Proceedings 14. Springer: Berlin/Heidelberg, Germany, 2018; pp. 24–43. [Google Scholar]
- Ahmad Taslim, H.; Md Lazam, N.A.; Mohd Yahya, N.A. Development of smart home door lock system. In Advances in Robotics, Automation and Data Analytics: Selected Papers from iCITES 2020; Springer: Berlin/Heidelberg, Germany, 2021; pp. 118–126. [Google Scholar]
- Ahmad, T.; Morelli, U.; Ranise, S.; Zannone, N. Extending access control in AWS IoT through event-driven functions: An experimental evaluation using a smart lock system. Int. J. Inf. Secur. 2022, 21, 379–408. [Google Scholar] [CrossRef]
- Guntur, J.; Raju, S.S.; Niranjan, T.; Kilaru, S.K.; Dronavalli, R.; Kumar, N.S.S. IoT-Enhanced Smart Door Locking System with Security. SN Comput. Sci. 2023, 4, 209. [Google Scholar] [CrossRef]
- Mehmood, M.Q.; Malik, M.S.; Zulfiqar, M.H.; Khan, M.A.; Zubair, M.; Massoud, Y. Invisible touch sensors-based smart and disposable door locking system for security applications. Heliyon 2023, 9, e13586. [Google Scholar] [CrossRef]
- Song, H.; Tu, Z.; Qin, Y. Blockchain-based access control and behavior regulation system for IoT. Sensors 2022, 22, 8339. [Google Scholar] [CrossRef]
- Zhai, P.; He, J.; Zhu, N. Blockchain-based Internet of Things access control technology in intelligent manufacturing. Appl. Sci. 2022, 12, 3692. [Google Scholar] [CrossRef]
- Hasan, M.R.; Alazab, A.; Joy, S.B.; Uddin, M.N.; Uddin, M.A.; Khraisat, A.; Gondal, I.; Urmi, W.F.; Talukder, M.A. Smart Contract-Based Access Control Framework for Internet of Things Devices. Computers 2023, 12, 240. [Google Scholar] [CrossRef]
- LaMacchia, B.; Lauter, K.; Mityagin, A. Stronger security of authenticated key exchange. In International Conference on Provable Security; Springer: Berlin/Heidelberg, Germany, 2007; pp. 1–16. [Google Scholar]
- Chai, S.; Yin, H.; Xing, B.; Li, Z.; Guo, Y.; Zhang, D.; Zhang, X.; He, D.; Zhang, J.; Yu, X.; et al. Provably Secure and Lightweight Authentication Key Agreement Scheme for Smart Meters. IEEE Trans. Smart Grid 2023, 14, 3816–3827. [Google Scholar] [CrossRef]
- Zhang, X.; Huang, X.; Yin, H.; Huang, J.; Chai, S.; Xing, B.; Wu, X.; Zhao, L. Llakep: A low-latency authentication and key exchange protocol for energy internet of things in the metaverse era. Mathematics 2022, 10, 2545. [Google Scholar] [CrossRef]
- Kumari, A.; Jangirala, S.; Abbasi, M.Y.; Kumar, V.; Alam, M. ESEAP: ECC based secure and efficient mutual authentication protocol using smart card. J. Inf. Secur. Appl. 2020, 51, 102443. [Google Scholar] [CrossRef]
- Xie, Q.; Wong, D.S.; Wang, G.; Tan, X.; Chen, K.; Fang, L. Provably Secure Dynamic ID-Based Anonymous Two-Factor Authenticated Key Exchange Protocol With Extended Security Model. IEEE Trans. Inf. Forensics Secur. 2017, 12, 1382–1392. [Google Scholar] [CrossRef]
- GM/T 0003-2012; SM2 Elliptic Curve Public Key Cryptographic Algorithms. Chinese Cryptography Administration: Beijing, China, 2010.
- Park, K.; Park, Y.; Park, Y.; Das, A.K. 2PAKEP: Provably secure and efficient two-party authenticated key exchange protocol for mobile environment. IEEE Access 2018, 6, 30225–30241. [Google Scholar] [CrossRef]
- Aviv, A.J.; Budzitowski, D.; Kuber, R. Is bigger better? Comparing user-generated passwords on 3×3 vs. 4×4 grid sizes for Android’s pattern unlock. In Proceedings of the 31st Annual Computer Security Applications Conference, Los Angeles, CA, USA, 7–11 December 2015; pp. 301–310. [Google Scholar]
- Ballagas, R.; Borchers, J.; Rohs, M.; Sheridan, J.G. The smart phone: A ubiquitous input device. IEEE Pervasive Comput. 2006, 5, 70–77. [Google Scholar] [CrossRef]
- Zhang, J.; Xue, N.; Huang, X. A secure system for pervasive social network-based healthcare. IEEE Access 2016, 4, 9239–9250. [Google Scholar] [CrossRef]
- Zhang, D.; Wang, C.; Xue, N.; Li, Z.; Zhang, H.; Huang, X. Blockchain papers depository system based on web 3.0. In Proceedings of the International Conference on Computer Application and Information Security (ICCAIS 2022), SPIE, Wuhan, China, 23–24 December 2022; Volume 12609, pp. 623–629. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).