Privacy Protection Based on Special Identifiers of Intersection Base Computing Technology
Abstract
1. Introduction
- The first type of protocol is the perfect computation protocol, which outputs accurate results. Taking the work in literature [3,4,5,6,7,8] as an example, it uses the evaluation method of fuzzy polynomials, selects a polynomial to represent the input set, and combines the intersection of the evaluation set using homomorphic encryption technology.
- The second type of protocol is the imperfect calculation protocol, and the output result of the protocol [9,10] allows a certain amount of error. When faced with a small amount of data, it is often difficult to strike a good balance between efficiency and availability with this type of protocol, and it is often abandoned because of the large errors.
- We propose a new privacy protection intersection cardinality protocol, and this protocol can quickly obtain the union of both sides.
- This protocol has extremely strong compatibility for the intersection of two sets of elements, it can accept any type of data, without knowing any information from either side, and can be 100% accurate in calculating the intersection base of both privacy sets.
- The protocol only needs two rounds of communication to complete, and the efficiency in the offline phase is much better than for the polynomial intersection cardinality protocol.
2. Materials and Methods
2.1. Security Definition
2.2. Paillier Homomorphic Encryption System
2.3. Learning Framework Based on Privacy Protection
2.4. Computer Coding
3. Protocol Process and Proof of Security
- The PSI-CA Construction of This Article
3.1. Protocol Construction
- Alice and Bob encode their elements according to the same encoding rules, converting the original data into binary data. Please refer to Section 2.4 for the specific conversion methods.
- Alice and Bob execute an online interaction protocol, ultimately obtaining .
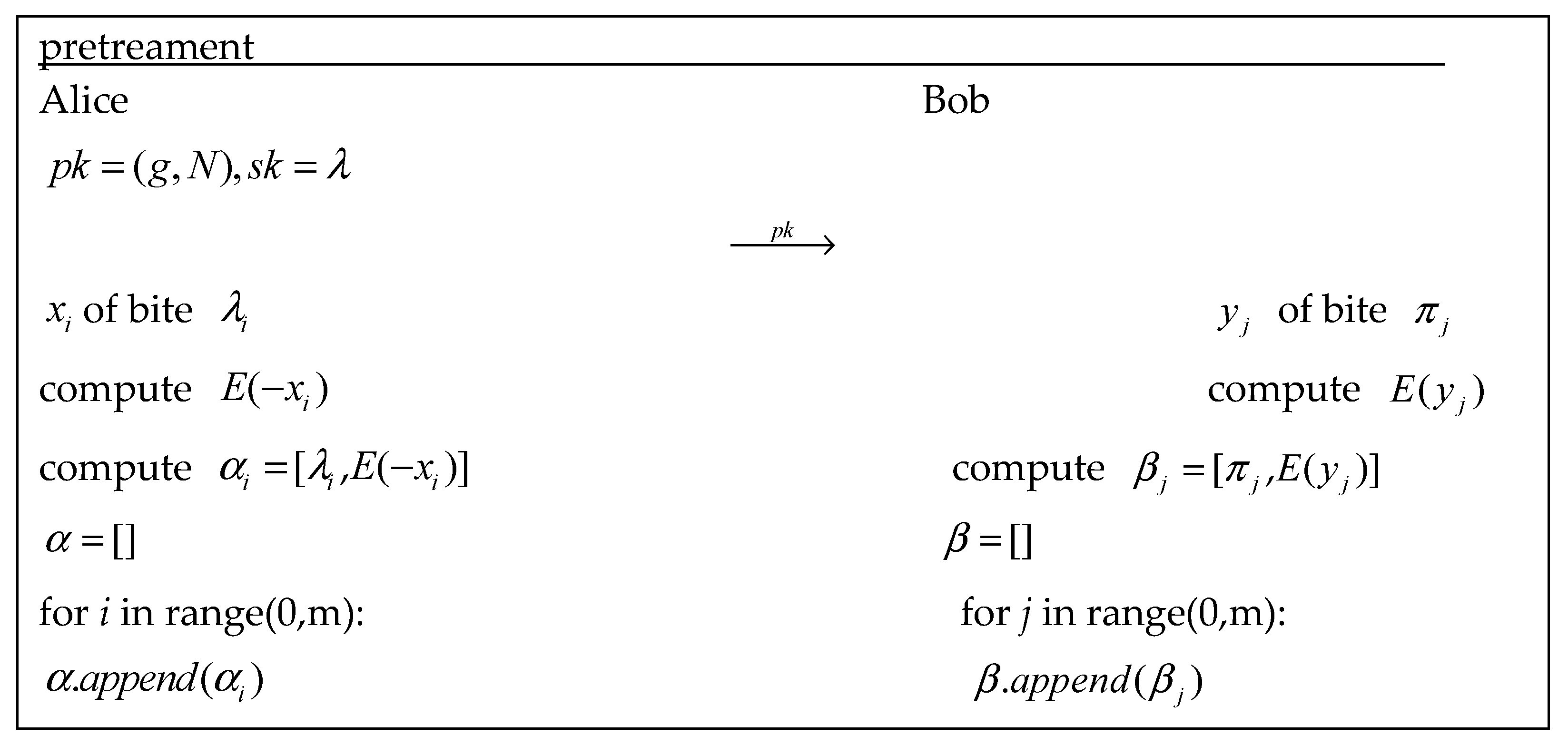
3.1.1. Offline Phase
3.1.2. Interaction Phase
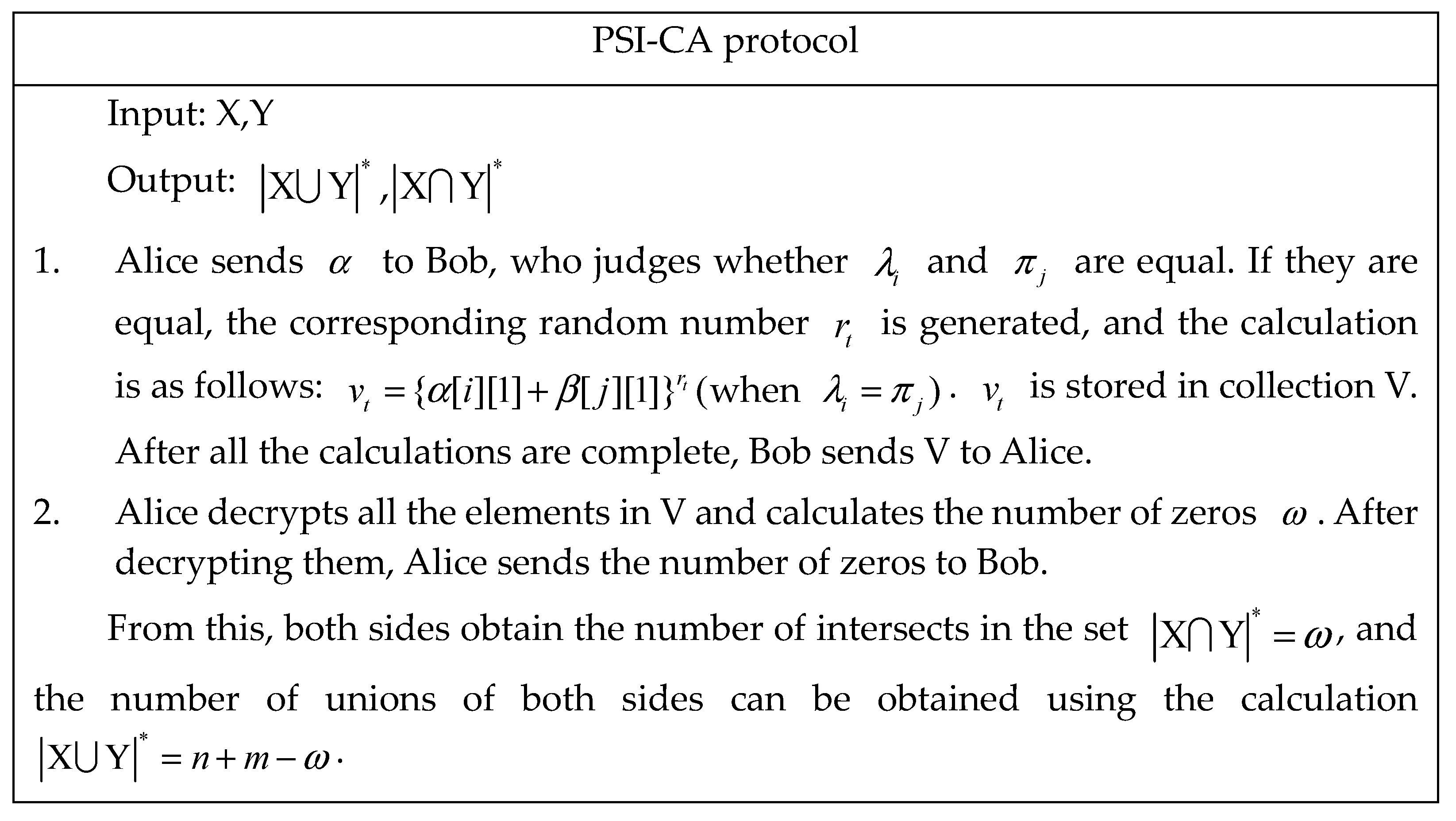
3.2. Correctness of the Protocol
3.3. Protocol Security
- Accept input ; based on the values of , select set , , and let .
- The encryption set obtains and calculates .
- Where gives the element of the encrypted set as , to decrypt it, by calculating the number of zero elements, you can judge the number of intersections of the two sides, and obtain the corresponding result. In protocol execution, :
- Accept input , according to the values of , select the set , , and let .
- The encrypted set gains and calculates .
- obtains the encryption set , decrypts it, and the corresponding result can be obtained by calculating the number of zero elements and judging the number of intersections between the two sides. In the execution of the agreement, , while
4. Discussion
4.1. Theoretical Evaluation
4.2. Experimental Evaluation
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Micali, S.; Goldreich, O.; Wigderson, A. How to play any mental game. In Proceedings of the Nineteenth ACM symposium on Theory of Computing, STOC, New York, NY, USA, 1 January 1987; ACM: New York, NY, USA, 1987; pp. 218–229. [Google Scholar]
- Yao, A.C. Protocols for secure computations. In Proceedings of the 23rd Annual Symposium on Foundations of Computer Science (sfcs 1982), Washington, DC, USA, 3–5 November 1982; pp. 160–164. [Google Scholar]
- Aggarwal, G.; Mishra, N.; Pinkas, B. Secure computation of the kth-ranked element. In EUROCRYPT’04, LNCS; Springer: Berlin/Heidelberg, Germany, 2004; Volume 3027, pp. 40–55. [Google Scholar]
- Kiayias, A.; Mitrofanova, A. Testing disjointness of private datasets. In Proceedings of the International Conference on Financial Cryptography and Data Security, Roseau, Dominica, 28 February–3 March 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 109–124. [Google Scholar]
- Sang, Y.; Shen, H. Efficient and secure protocols for privacy-preserving set operations. ACM Trans. Inf. Syst. Secur. TISSEC 2009, 13, 1–35. [Google Scholar] [CrossRef]
- Hohenberger, S.; Weis, S.A. Honest-verifier private disjointness testing without random oracles. In Proceedings of the Privacy Enhancing Technologies: 6th International Workshop, PET 2006, Cambridge, UK, 28–30 June 2006; Revised Selected Papers 6. Springer: Berlin/Heidelberg, Germany, 2006; pp. 277–294. [Google Scholar]
- Frikken, K. Privacy-preserving set union. In Proceedings of the Applied Cryptography and Network Security: 5th International Conference, ACNS 2007, Zhuhai, China, 5–8 June 2007; Proceedings 5. Springer: Berlin/Heidelberg, Germany, 2007; pp. 237–252. [Google Scholar]
- Hazay, C.; Nissim, K. Efficient set operations in the presence of malicious adversaries. In Proceedings of the Public Key Cryptography–PKC 2010, 13th International Conference on Practice and Theory in Public Key Cryptography, Paris, France, 26–28 May 2010; Proceedings 13. Springer: Berlin/Heidelberg, Germany, 2010; pp. 312–331. [Google Scholar]
- Egert, R.; Fischlin, M.; Gens, D.; Jacob, S.; Senker, M.; Tillmanns, J. Privately computing set-union and set-intersection cardinality via bloom filters. In Proceedings of the Information Security and Privacy: 20th Australasian Conference, ACISP 2015, Brisbane, QLD, Australia, 29 June–1 July 2015; Proceedings 20. Springer International Publishing: Cham, Switzerland, 2015; pp. 413–430. [Google Scholar]
- Dong, C.; Loukides, G. Approximating Private Set Union/Intersection Cardinity with Logarithmic Complexity. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2792–2806. [Google Scholar] [CrossRef]
- Paillier, P. Public-key cryptosystems based on composite degree residuosity classes. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Prague, Czech Republic, 2–6 May 1999; Springer: Berlin/Heidelberg, Germany, 1999; pp. 223–238. [Google Scholar]
- Pinkas, B.; Schneider, T.; Tkachenko, O.; Yanai, A. Efficient circuit-based PSI with linear communication. In Advances in Cryptology–EUROCRYPT 2019, Proceedings of the 38th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Darmstadt, Germany, 19–23 May 2019; Proceedings, Part III 38; Springer International Publishing: Cham, Switzerland, 2019; pp. 122–153. [Google Scholar]
- Pinkas, B.; Schneider, T.; Weinert, C.; Wieder, U. Efficient circuit-based PSI via cuckoo hashing. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Tel Aviv, Israel, 29 April–3 May 2018; Springer International Publishing: Cham, Switzerland, 2018; pp. 125–157. [Google Scholar]
- Huang, Y.; Evans, D.; Katz, J. Private set intersection: Are garbled circuits better than custom protocols? In Proceedings of the 19th Network and Distributed Security Symposium, San Diego, CA, USA, 5–8 February 2012. [Google Scholar]
- Asokan, N.; Dmitrienko, A.; Nagy, M.; Reshetova, E.; Sadeghi, A.R.; Schneider, T.; Stelle, S. Crowdshare: Secure mobile resource sharing. In Proceedings of the Applied Cryptography and Network Security: 11th International Conference, ACNS 2013, Banff, AB, Canada, 25–28 June 2013; Proceedings 11. Springer: Berlin/Heidelberg, Germany, 2013; pp. 432–440. [Google Scholar]
- Bogdanov, D.; Laur, S.; Willemson, J. Sharemind: A framework for fast privacy-preserving computations. In Proceedings of the Computer Security-ESORICS 2008, 13th European Symposium on Research in Computer Security, Málaga, Spain, 6–8 October 2008; Proceedings 13. Springer: Berlin/Heidelberg, Germany, 2008; pp. 192–206. [Google Scholar]
- Demmler, D.; Schneider, T.; Zohner, M. ABY-A framework for efficient mixed-protocol secure two-party computation. In Proceedings of the Network and Distributed System Security (NDSS) Symposium, San Diego, CA, USA, 8–11 February 2015. [Google Scholar]
- Hazay, C.; Scholl, P.; Soria-Vazquez, E. Low cost constant round MPC combining BMR and oblivious transfer. J. Cryptol. 2020, 33, 1732–1786. [Google Scholar] [CrossRef]
- Keller, M. MP-SPDZ: A versatile framework for multi-party computation. In Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, Virtual, 9–13 November 2020; pp. 1575–1590. [Google Scholar]
- Mohassel, P.; Rindal, P. ABY3: A mixed protocol framework for machine learning. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 35–52. [Google Scholar]
- Chaudhari, H.; Rachuri, R.; Suresh, A. Trident: Efficient 4pc framework for privacy preserving machine learning. arXiv 2019, arXiv:1912.02631. [Google Scholar]
- Braun, L.; Demmler, D.; Schneider, T.; Tkachenko, O. Motion—A framework for mixed-protocol multi-party computation. ACM Trans. Priv. Secur. 2022, 25, 1–35. [Google Scholar] [CrossRef]
- Kissner, L.; Song, D. Privacy-Preserving Set Operations. In Advances in Cryptology, Proceedings of the Annual International Cryptology Conference CRYPTO 2005, Santa Barbara, CA, USA, 14–18 August 2005; Lecture Notes in Computer, Science; Shoup, V., Ed.; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3621. [Google Scholar] [CrossRef]

| Framework | N | t | Security | Protocols | License |
|---|---|---|---|---|---|
| ABY [16] | 2 | 1 | ○ | A/B/Y | Lgpl-3.0 |
| PrivC [17] | 2 | 1 | ○ | A/B | -- |
| ABY3 [18] | 3 | 1 | ● or ○ | A/B/Y | No license |
| Sharemind [19] | 3 | 1 | ● or ○ | A/B | Payware3 |
| Trident [20] | 4 | 1 | ● | A/B/Y | |
| MP-SPDZ [21] | 2 | N − 1 | ● or ○ | A/B or Y | MIT-like |
| MOTION [22] | 2 | N − 1 | ○ | A/B/Y | MIT |
| Protocol | Time Complexity | Space Complexity | Rounds |
|---|---|---|---|
| The text’s | 2 | ||
| Reference [23]’s protocol | 6 |
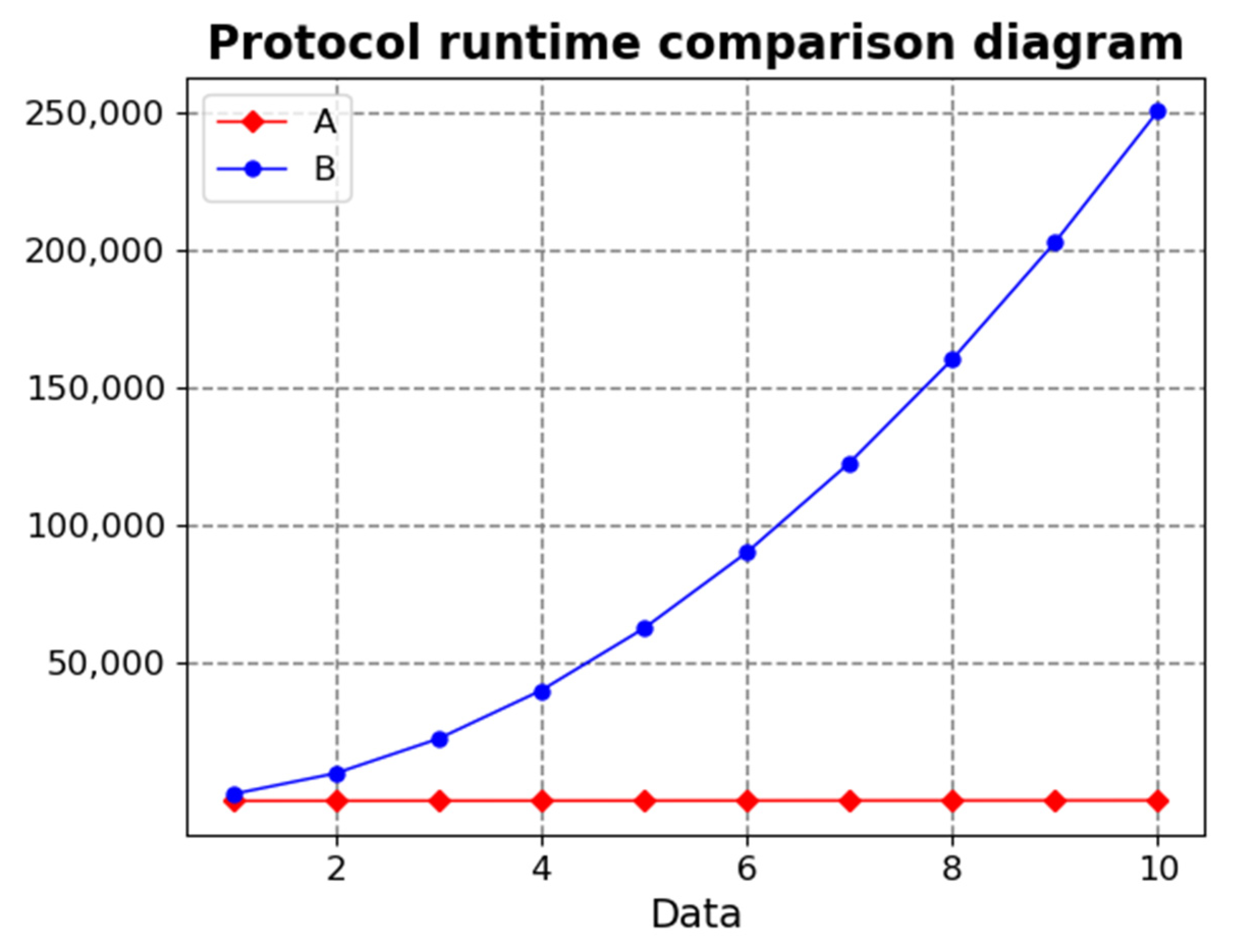
| Protocol | Online Time (s) | Offline Time (s) | Total Time | |
|---|---|---|---|---|
| (100,100) | Text’s protocol | 83.39 | 166.78 | 250.17 |
| Reference [23]’s protocol | 83.33 | 10,021.83 | 10,106.16 | |
| (100,300) | Text’s protocol | 88.64 | 265.92 | 354.56 |
| Reference [23]’s protocol | 265.92 | 90,177.28 | 90,265.92 | |
| (100,500) | Text’s protocol | 73.82 | 295.28 | 369.10 |
| Reference [23]’s protocol | 369.10 | 250,221.46 | 250,590.56 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, P.; Ma, T.; Zhang, Q.; Zhang, J.; Wang, J. Privacy Protection Based on Special Identifiers of Intersection Base Computing Technology. Appl. Sci. 2024, 14, 813. https://doi.org/10.3390/app14020813
Zhang P, Ma T, Zhang Q, Zhang J, Wang J. Privacy Protection Based on Special Identifiers of Intersection Base Computing Technology. Applied Sciences. 2024; 14(2):813. https://doi.org/10.3390/app14020813
Chicago/Turabian StyleZhang, Ping, Tengfei Ma, Qing Zhang, Ji Zhang, and Jiechang Wang. 2024. "Privacy Protection Based on Special Identifiers of Intersection Base Computing Technology" Applied Sciences 14, no. 2: 813. https://doi.org/10.3390/app14020813
APA StyleZhang, P., Ma, T., Zhang, Q., Zhang, J., & Wang, J. (2024). Privacy Protection Based on Special Identifiers of Intersection Base Computing Technology. Applied Sciences, 14(2), 813. https://doi.org/10.3390/app14020813







