Abstract
In emergency situations, ensuring the secure transmission of medical information is critical. While existing schemes address on-road emergencies, off-road scenarios present unique challenges due to hazardous locations inaccessible to conventional vehicles. This research introduces a protocol for off-road emergencies, leveraging flying ad hoc networks (FANETs) formed by drones. The protocol, designed for users receiving emergency treatment, employs cryptographic techniques to protect sensitive information. To overcome the challenge of decrypting user medical records at emergency centers without the healthcare provider’s key, proxy re-encryption is employed. The control center (CC) securely generates encryption and decryption keys, facilitating the re-encryption process by the cloud server (CS) and transmission to the emergency center (E). The proposed protocol, free from pairing functions, underwent security and efficiency analyses, demonstrating resilience against chosen-ciphertext attacks (CCA) and collusion resistance (CR). Execution times of approximately 0.02 and 0.0 s for re-encryption and decryption processes, respectively, for a message size of 2000 bytes highlighted the efficiency of the protocol. The research contributes a secure and efficient proxy re-encryption protocol for off-road emergency medical information transmission within FANETs.
1. Introduction
In emergency situations, the secure transmission of medical information requires significant security technologies. Ref. [1] proposed a scheme for safe medical information transmission in on-road emergency situations. However, emergencies can occur not only on-road, but also off-road, presenting the challenge that off-road emergency locations are often inaccessible to conventional vehicles due to their hazardous nature. This became my motivation and expanded into the following research. To address hazardous emergency locations, drones are commonly employed for initial situational assessment, forming a communication network known as FANET (flying ad hoc network) with other participants.
In this paper, we establish off-road emergency scenarios and design an information transmission protocol for users who are receiving emergency treatment at a hospital with a smartphone. The protocol utilizes cryptographic techniques to prevent the exposure of sensitive user information. For a patient arriving at the emergency room of a nearby hospital due to an accident, accurate and effective treatment requires healthcare providers to have detailed knowledge of the patient’s medical history. Typically, user medical records are encrypted with the secret key of the healthcare provider and stored on a cloud server. Notably, the challenge arises as to whether the medical staff of the emergency center, without knowledge of the healthcare provider’s key, can decrypt the user’s medical records stored in encrypted form. To solve this issue, we employed proxy re-encryption.
The trusted third party, the control center (CC), generates encryption and decryption keys for re-encryption and securely transmits them to the cloud server (CS) and emergency center (E). The semi-trusted entity CS then uses these keys to re-encrypt the user’s medical records, sending them to the emergency center. The emergency center can subsequently decrypt the re-encrypted medical records using the received key from CC.
The proposed proxy re-encryption protocol does not use pairing functions and is secure against chosen-ciphertext attacks (CCA) and is collusion-resistant (CR). The re-encryption keys are also transmitted in encrypted form, ensuring the confidentiality of the original encryption keys. Security analysis is conducted in Section 5, where we formally prove unidirectional proxy re-encryption CCA security, prove unidirectional proxy re-encryption collusion-resistant (CR) security, and explain the defense mechanism against proxy forgery attacks. In Section 6, an efficiency analysis is conducted. The complexity of the proposed scheme is analyzed, and based on that, a comparative analysis is performed with relevant studies. When compared with the best efficient paper [2], it was found to exhibit the same complexity. The implementation of the re-encryption and decryption processes, for time measurements for a message size of 2000 bytes, resulted in execution times of approximately 0.02 and 0.0 s, respectively. Consequently, the paper proposes that the proxy re-encryption protocol demonstrates a secure and efficient performance, free from the use of pairing functions, and resilient against CCA and collusion attacks.
Our paper is structured as follows: Section 1 is an introduction, providing an overview of the research’s significance, methodology, and overall results. In Section 2, we delve into related studies and establish the application scenarios to be employed in this paper. Section 3 constitutes the security building blocks of this paper, introducing seven algorithms. Utilizing these algorithms, Section 4 constructs a protocol for the application scenarios. Section 5 conducts a security analysis, while Section 6 performs an efficiency analysis. Finally, Section 7 concludes the paper.
2. Related Works and Applications
2.1. Related Works
The suggested scheme focuses on the proxy re-encryption protocol for medical information within FANET (flying ad hoc network) environments. Considering a scenario involving off-road accidents, real-time video recording by drones becomes essential, necessitating a security protocol for transmission in the FANET environment.
FANETs are a system in which unmanned aerial vehicles (UAV) or drones exchange information by forming a network. It is primarily a collection of communication technologies that allows drones or unmanned aerial devices to work together and share information. In particular, FANETs can be used to implement autonomous flight systems. Drones or UAVs can communicate with each other to monitor and control the situation while performing a given mission. This allows them to be applied to a variety of missions and applications: exploration and surveillance, rescue operations in disaster situations, crop surveillance in agriculture, and building communications infrastructure. FANETs implement various technologies related to security and safety through efficient communication and cooperation, and this is an area where more research and development is expected as the use of unmanned aerial devices increases.
Consequently, this section will explore existing drone security protocols and research on securing medical information during emergency situations as related works. Subsequently, a specific focus will be given to proxy re-encryption, particularly unidirectional proxy re-encryption.
First, we looked at drone-security-related protocols. Ref. [3] introduced a key management and delegation system to enhance multi-drone control system security. It minimizes the storage of sensitive data like group keys and flight information, employing a “saveless” property. Future work aims to adapt the system for small IoT devices and determine an optimal key renewal period balancing low computation cost and high security. Ref. [4] focused on a group authentication-based solution for drone swarm security, ensuring rapid and secure verification of new drones. The novel authentication scheme is faster than 3GPP Release 17, with credentials not transmitted to the core network. Group authentication by guard drones and new parties facilitates swarm integration with reduced complexity. Ref. [5] discussed a lightweight authentication and key agreement (AKA) scheme for the internet of drones, addressing security challenges and privacy issues in a cost-effective manner. The scheme ensures secure data transmission using a lightweight encryption algorithm and a secure key exchange protocol. Ref. [6] introduced an anonymous mutual and batch authentication scheme with location privacy for UAVs (unmanned aerial vehicles) in FANETs. It ensures mutual authentication, batch authentication, and location privacy using group and ring signature schemes. The proposed scheme has potential applications in various fields, including military surveillance, emergency management, and environmental monitoring.
The following is a study on medical information transmission security protocols. Ref. [1] proposed a secure medical record access scheme for on-road emergencies using a patient’s smartphone and a cloud server. It ensures user privacy through pseudonyms and password-based authentication, improving the efficiency of accessing medical records during emergencies. The scheme enables timely healthcare in life-threatening situations. However, because this paper dealt with on-road emergency situations, drones were not involved. Ref. [7] is a review paper to discuss the security protocols for medical information using UAVs. It aimed to analyze the applicability of UAVs to support emergency medical systems in the areas of delivery and emergency urgent care.
Next, we address proxy re-encryption. In emergency situations, having access to the previous medical records of the injured patient is crucially necessary. Therefore, a proxy re-encryption process is required, where the STP (semi-trusted party) transmits the previously encrypted sensitive medical information to emergency medical institutions without decrypting it. The information is re-encrypted by the STP before transmission, delegating the decryption process to emergency institutions.
Ref. [8] is known as the first method introduced for delegating decryption rights, which marked an improvement over the traditional decrypt-and-then-encrypt approaches. In [9], Blaze et al. suggested an application called atomic proxy re-encryption, where a semi-trusted proxy converts a ciphertext for Alice into a ciphertext for Bob without seeing the underlying plaintext. Ref. [10] proposed a distributed-based authentication mechanism for drones in a swarm compatible with 5G D2D ProSe standard [11] mechanisms. It relies on a delegation-based proxy signature authentication scheme, reducing drones’ communication overhead to the core network. The authentication scheme is lightweight, efficient, and scalable, suitable for resource-constrained drone networks. Ref. [12] presented a privacy-preserving sharing scheme for drone videos in public safety scenarios, using proxy re-encryption. It allows secure access for third parties, like first responders, without compromising video content privacy. The original encryption key remains confidential, and the scheme minimizes overhead, making it feasible for live streaming. Ref. [13] suggested a proxy re-encryption (PRE) scheme for decentralized storage networks using permissionless blockchains. It allows data owners to delegate access rights without revealing content. The PRE scheme is efficient, scalable, and resistant to collusion attacks, providing secure data access control in decentralized storage networks. Ref. [14] covered improved proxy re-encryption schemes for secure distributed storage, including their design, implementation, and performance measurements. It also discussed the benefits of using proxy re-encryption for access control in a secure file system. The pairing-based schemes introduced significant advancements, including the protection of the delegator’s master secret key from collusion between the proxy and delegate.
We now address proxy re-encryption papers that are secure against CCAs (chosen-ciphertext attacks). Ref. [15] presented a new definition of security against chosen-ciphertext attacks for PRE schemes and proposed a scheme that satisfies the definition. The construction is efficient and based only on the decisional bilinear Diffie–Hellman assumption in the standard model.
The main contribution of Ref. [16] was the first construction of a unidirectional proxy re-encryption scheme with chosen-ciphertext security in the standard model. The construction is efficient and requires a reasonable complexity assumption in bilinear map groups. Ref. [2] proposed a new scheme for more efficient unidirectional proxy re-encryption and analyzed its security in detail, demonstrating its robustness against various attacks. The scheme has potential applications in various real-world scenarios and can contribute to the advancement of cryptography and data protection. Ref. [17] proposed a new scheme for proxy re-encryption that is secure against chosen-ciphertext attacks and collusion attacks, and does not require pairings. The scheme is unidirectional and the first of its kind with CCA security and collusion resistance. Ref. [18] proposed a unidirectional proxy re-encryption and proved its chosen-ciphertext security in the adaptive corruption model without random oracles, addressing an important question in the field. Overall, the paper’s contribution laid in advancing the state of the art in secure proxy re-encryption schemes.
2.2. Participants
- Smartphone (S): It is the user’s smartphone, to which various sensors (wearable devices) are connected to monitor the patient’s health condition. The smartphone periodically transmits encrypted records to the healthcare provider and stores them in the cloud server.
- Healthcare provider (H): It refers to an institution that provides and records medical practice. H manages the user’s health status monitored through the S, and performs medical treatment when users visit.
- Emergency center (E): An institution that carries out medical practice in case of emergency.
- Vehicle (including ambulances, V): V means vehicles or helicopters that transport users. It may or may not have medical equipment installed.
- Cloud server (CS): CS is a storage space. It stores the user’s medical records (medical practices performed by H, the patient’s conditions measured by S’s sensors, etc.) and video files taken by drones. This is assumed to be a semi-trusted party.
- First responders (F): F stands for police, fire engines, rescue helicopters, etc.
- Drone (D): The drone is registered in the CC in advance.
- Control center (CC): This is a kind of trusted third party (TTP), which controls security-related matters such as the generation and management of encryption keys and the registration of participants. Hence, CC knows all the security keys for every participant.
2.3. Application Scenario
Ref. [1] covered secure medical records in on-road emergencies. However, emergencies often occur not only on-road but also off-road. In other words, numerous incidents, such as a vehicles rolling down a cliff or a natural disaster on a beach, often occur in places where vehicles cannot approach. In preparation for this situation, we propose a security system in which drones participate by assuming the following specific accident scenarios:
- CC receives and checks reports from a citizen or a drone monitoring an accident situation in the air.
- CC orders D to take a detailed shot, and F to respond first.
- According to CC’s orders, the drone takes some actions, encrypts and transmits the video taken in detail to the CC in real time. F also notifies the CC of the processing status.
- CC analyzes it and transmits the information about nearby E to the available F or vehicle, which transfers the patient to E.** The patient’s condition is measured with the sensor device of the smartphone and vehicle, and the record is encrypted and transmitted to the arriving E.
- In the meantime, CC generates secret key values for re-encryption/decryption and transmits them to CS and E.
- CS re-encrypts the user’s medical records encrypted by H and transmits them to E.
- E decrypts the record that has been re-encrypted by CS using the decryption key sent by CC.
- After decrypting the records, E proceeds to treat the patient. Following the treatment, the results are encrypted and sent to H, where they are subsequently stored in CS.
Figure 1 shows the communication between each participant according to the application scenario.
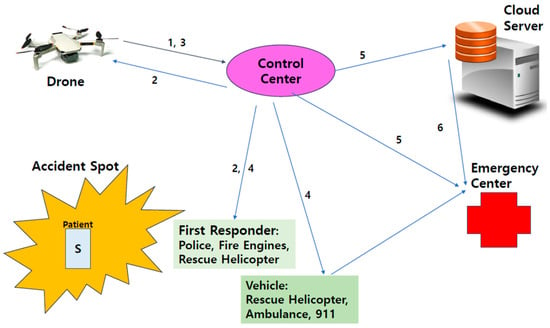
Figure 1.
Participants and scenario flow.
3. Preliminaries
3.1. Notations
- ·
- : pseudorandom function.
- ·
- : reverse function of , in other words, decryption function of .
- ·
- i or j: each participant such as H or E.
- ·
- : secret key between participant i and CC.
- ·
- : encryption using pseudorandom function with a secret key .
- ·
- : private key of participant I.
- ·
- : public key of participant I.
- ·
- : a message.
- ·
- : ElGamal-style ciphertext of .
- ·
- : decryption of .
- ·
- : re-encryption of .
- ·
- : randomly generated numbers every time.
- ·
- : an order from CC to participant i.
- ·
- : report of participant i.
- ·
- : re-encryption/decryption keys.
- ·
- : oracle.
3.2. Security Building Blocks
Definition 1.
Discrete Logarithm Problem (DLP): It is a hard problem that involves finding the integer x ) such that (mod p), given a prime p, a generator α of , and an element [19].
Definition 2.
Decisional Diffie–Hellman Problem (DDH): Let G be a group with prime order q, and let g be a generator of G. The decisional Diffie–Hellman (DDH) problem involves distinguishing between two types of triplets: ) and (), where random elements .
The experiment with a polynomial-time adversary A is as follows: flip a coin δ to obtain either 0 or 1, if It is said that the DDH problem is hard if, for any polynomial-time adversary A, the absolute value of the difference between the probability is negligible [19].
Definition 3.
Group Decisional Diffie–Hellman (GDDH): The problem is ()–intractable if there is no ()–-distinguisher in G for all polynomial and non-negligible . (Refer to [20]):
The ()–-distinguisher in G is a probabilistic Turing machine running in time such that .
Remark 1.
The Decisional Diffie–Hellman Assumption: Let us define two additional distributions from the GDH-Distribution:
Definition 4.
Pseudorandom Function (PRF): It is said that -secure pseudorandom function if any oracle algorithm, which makes a maximum of q oracle queries and has a running time of at most t, exhibits an advantage . The advantage , representing the probability of adversary A succeeding in an attack, is defined as follows: . Here, R denotes a randomly chosen function uniformly selected from the set of all mappings from X to . The probabilities are considered with respect to the selection of k and R [21].
Definition 5.
Pseudorandom Generator (PRG): It is said that is a -secure pseudorandom generator if any algorithm A, operating within a time limit of t, demonstrates an advantage . The advantage is defined as follows: . The random variables and are uniformly distributed over the sets and S, respectively [21].
Definition 6.
Public Key Encryption (PKE). The PKE system consists of three probabilistic polynomial-time (PPT) algorithms (KGen, EnC, DeC):
- -
- KGen() → (pk, sk). Given the security parameter , the key generation algorithm KGen produces a public key pk and a secret key sk.
- -
- EnC(pk, m) → C. Given a public key pk and a message m in the message space, the encryption algorithm EnC produces a ciphertext C.
- -
- DeC(sk, C) → m. With the input of a secret key sk and a ciphertext C, the decryption algorithm DeC robustly generates a message m within the message space or ⊥ [17].
ElGamal: ElGamal cryptography provides security based on the difficult mathematical problem of finding the private key x from the public key y.
- ·
- Key generation:
- ·
- Select a mathematically secure large prime p and a primitive root g modulo p.
- ·
- Choose a random private key x. Compute the public key mod p.
- ·
- Encryption:
- ·
- Choose a random k such that 0 < r < p − 1.
- ·
- Compute: mod p and mod p to generate the ciphertext .
- ·
- Decryption:
- ·
- Compute: [19].
Definition 7.
Unidirectional Proxy Re-Encryption. The UniPRE(unidirectional proxy re-encryption) scheme is comprised of a set of PPT algorithms (KGen, RKeyGen, EnC, PrxyRE, DeC):
- -
- KGen, EnC, DeC: Similar to those found in public key encryption.
- -
- RKeyGen(, ) → . Given a secret key , a public key , the re-encryption key generation algorithm, RKeyGen, produces a unidirectional re-encryption key .
- -
- PrxyRE (, ) → . Given a re-encryption key and a ciphertext , the re-encryption algorithm PrxyRE produces a re-encrypted ciphertext or ⊥ [17].
Definition 8.
Uni-PRE-CCA game. This security game based on [17] is too long and will be explained later in the proof. So, here, we will omit it for now and refer to [17] for details.
Definition 9.
Uni-PRE-CR(collusion resistance) security. It is said that a UniPRE scheme is collusion-resistant if, for any polynomially bounded adversary , the probability described below is negligible:
| Pr[(, ) ← KGen(), {(, ) ← KGen()}, |
| {← ReKeyGen(, )}, |
| { ← ReKeyGen(, )}, |
| i = 2, ⋯, |
| α ← A(, {, }, {}, {}): |
| α = ] |
| [17]. |
3.3. Algorithms
Our scheme consists of the following algorithm, which is based on [17] and that we modified:
- ·
- SysParm() → λ: The parameter generating algorithm SysParm takes a security parameter s as input and generates a set of system parameters λ.
- ·
- KGen() → pk, sk, k: Given λ as input, the key generating algorithm KGen generates a public key pk, a private key sk and a secret key k with a control center CC for a symmetric cryptographic system(pseudorandom function).
- ·
- EnC(pk,m) → C: Given a public key pk and a message m as input, the encryption algorithm EnC produces a ciphertext C.
- ·
- Ord_ → : CC analyses the report R, produces an Order and transmits it to a participant P.
- ·
- Rpt_CC( → Act: According to the received order , P reacts the Act and reports it to CC.
- ·
- RKeyGen() → : Given secret keys and as input, the re-encryption key generation algorithm RKeyGen generates unidirectional re-encryption keys .
- ·
- PrxyRE( → RE: STP (semi-trusted party) decrypts the encryption of the re-encryption key . With this, STP re-encrypts C, then produces the re-encryption RE.
- ·
- DeC ) → m: Given a re-encryption key and as input, the decryption algorithm DeC outputs the original message m.
- ·
- Trt_Str → : Upon input of a treatment by the participant P, this treatment and storage algorithm outputs the encryption for . Then, is stored in CS.
4. Construction of UPF Model
In this section, we construct a security model UPF (unidirectional proxy re-encryption in FANETs) which is composed of ten algorithms.
4.1. System Setup
SysParm(1s) Construction
- Input: s: security parameter.
- Output: λ = {}: system parameters’ set.
The basis of the unidirectional proxy re-encryption system is established. → is a pseudorandom function and is a pseudorandom generator. G is a group of order p which is a large prime and g is a generator of a group G. i is each participant of group G. C and D are encryption and decryption functions, and RE is a re-encryption function.
4.2. Registration and Encryption
4.2.1. KGen() Construction
- Input: .
- Output: pk, sk, k.
Key materials are generated. pk and sk are the public key and private key for ElGamal encryption and k is the secret key shared with CC in advance for pseudorandom function f.
4.2.2. EnC Construction
- Input: pk,m.
- Output: .
The first encryption for message m is processed, where an ElGamal algorithm is used as an encryption function. When we assume that the healthcare provider (H) encrypts their information m, the public key is and the ciphertext is
4.3. Accident Occurrence
4.3.1. Ord_P(R) Construction
- Input: R(reporting).
- Output: .
CC checks R (reporting) for an accident, then gives orders to each participant P (D and F). CC orders D to take a detailed shot, and F to make an initial response. The communications in this step are made in plaintext.
4.3.2. Rpt_CC() Construction
- Input: .
- Output: , .
According to the order , the drone takes some actions. Then, it encrypts and transmits the detailed video file report to the CC in real time, and F also reports the processing status to the CC. All communications from this step are encrypted.
4.3.3. Ord_F Construction
- Input: .
- Output: .
CC checks and analyzes after decrypting with security key . Then, CC sends F the encrypted order , which includes information about emergency medical agencies nearby.
4.4. Proxy Re-Encryption
4.4.1. RKeyGen() Construction
- Input: , .
- Output: , .
This algorithm is for the setting of re-encryption keys. CC generates random numbers and then computes , . We put as re-encryption key and as decryption key for the re-encrypted message. With this, CC encrypts with the secret key , and with . Then, CC transfers the generated re-encryption/decryption keys to CS and E.
4.4.2. PrxyRE ( Construction
- Input: .
- Output: .
CS decrypts the received encryption of , where CS is a STP(semi-trusted party). With them, CS re-encrypts the stored user cipher text C =) as follows:
. Here, .
Then, CS transmits the re-encryption to E.
4.5. Treatment
4.5.1. DeC( ) Construction
- Input: .
- Output: .
E decrypts the cipher text received from CC to obtain the decryption keys . Then, it decrypts with .
4.5.2. Trt_Str Construction
- Input: .
- Output: .
E treats the patient. Thereafter, E encrypts the resulting of treating the patient with H’s public key and sends it to H. H checks the received and stores it in CS.
4.6. Whole Protocol Flow
| 1. System Setup •SysParm |
| 2. Registration and Encryption 2.1. KGen → pk, sk, k 2.2. EnC → |
| 3. Accident Occurrences 3.1. Ord_P • 3.2. Rpt_CC • 3.3. Ord_F • |
| 4. Proxy Re-Encryption 4.1. RKeyGen • • 4.2. PrxyRE •- • |
| 5. Treatment 5.1. DeC • 5.2. Trt_Str • • |
5. Security Analysis
5.1. Proof of Security
Theorem 1.
(Unidirectional Proxy Re-Encryption CCA Security) UPF(unidirectional proxy re-encryption in FANETs) is secure according to Uni-PRE-CCA game, if GDDH is hard.
Proof.
We use contraposition. A is assumed as an adversary that wins the Uni-PRE-CCA game with advantage ε. We construct the adversary which uses A as a subroutine and breaks the GDDH with non-negligible advantage. □
Phase 1. The adversary A initiates queries , with each being one of the following:
The oracle (public key generation): When provided with an index i, conclusively determines whether is the attacked public key .
- ·
- If affirmative, Δ initializes ) and records this information in table .
- ·
- Otherwise, executes KGen → , ) and provides to A, and records ) in .
(secret key generation): Given the input , verifies the existence of in .
- ·
- If is not found, terminates.
- ·
- In case is the attacked public key, reports failure and aborts.
- ·
- Otherwise, replies to A with ) and records into .
(re-encryption key generation): Given the input ), verifies the existence of both in .
- ·
- If either is missing, terminates.
- ·
- Subsequently, checks whether , ) is present in . If it is, returns ) to A. If not:
- -
- If is in , or not the guessed attacked public key, responds with , ) = , ), recording , ) in .
- -
- If is the guessed attacked public key and is not in , selects random numbers , computes , sets = , and records , ) in .
- -
- If is the guessed attacked public key and is in , reports failure.
(re-encryption): Upon receiving input ), verifies the existence of both and in . If either is absent, terminates. Subsequently, parses .
- ·
- If is the guessed attacked public key and is in , selects random numbers , puts = , and returns ) to A, stores it in
- ·
- Otherwise, calls to obtain , and returns PrxyRE( and stores it in
: When receiving input ), checks whether is present in either or . If it is absent in both, terminates. However:
- ·
- If is not the guessed attacked re-encryption key, knows = from . responds A with
- ·
- If is the guessed attacked re-encryption key and , searches ) in or in , for .
- -
- If it does exist,
- -
- If it does not exist, aborts.
Challenge. At a certain stage, A issues a challenge tuple . If is not the public key guessed in oracle , declares failure and terminates. On the contrary, if aligns with the guessed public key, responds by randomly selecting and choosing random numbers then sets: ).
Phase 2.
: follows the Phase 1 response protocol.
: When provided with , if = , or , ) is found in the table , immediately terminates. Otherwise, follows the Phase 1 response protocol.
: When receiving input , ), if = , and is in table , terminates. Otherwise, responds in line with the Phase 1 protocol.
: On input , ), if , C) = , and is present in the table , terminates. Otherwise, responds as in Phase 1, except when = and =. should record the result in
: On input ), if ) = , or is in , or , terminates. Otherwise, responds as in Phase 1.
Guess. A outputs a guess b’. If b = b’, outputs 0 (GDDH instance). Otherwise, it outputs 1 (not a GDDH instance), because the encryption will be random for RE if and only if the challenge is not a GDDH tuple, solves the GDDH challenge with the same advantage as A. In more detail, in the case of b = 0, . If b = 1, returns a random value in reply to the GDDH challenge. If , it is the encryption of RE. Otherwise, it is not an encryption.
It is shown that can solve the GDDH problem ) with non-negligible probability.
Theorem 2.
(Unidirectional Proxy Re-Encryption Collusion-Resistant(CR) Security) If f is a secure pseudorandom function and random numbers are generated from a secure pseudorandom generator, then scheme UPF is collusion-resistant.
Remark 2.
The cryptographic elements for the whole protocol are PRF (pseudorandom function, e.g., 128 bit-AES) and PRG (pseudorandom generator, e.g., middle-square method, Naor–Reingold pseudorandom function, etc.).
Proof.
We assume C as an adversary against the Uni-PRE-CR with advantage ε and as a distinguisher between random and pseudorandom. Here, we also use contraposition, so all we have to do is to construct using C as a subroutine. C can collude and know the secret key (k) values of other pre-registered members. Since the encrypted and transmitted , can be decrypted to using the secret key, the re-encrypted message can be decrypted to the original message m. Then, will also be able to distinguish whether the challenged message is the result of an encrypted value or a random value. □
5.2. Proxy Forgery Attack
A proxy forgery attack is a type of security breach in which an attacker uses a forged proxy server to intercept or manipulate data on a specific network. Proxies are responsible for relaying or filtering communications between clients and servers, and attackers can forge such proxies to intercept and manipulate communications in the middle. The main characteristics and process of proxy forgery attacks are as follows:
- (1)
- Proxy server forgery: Attackers either build proxy servers under their control or exploit and use proxy servers that already exist.
- (2)
- Man-in-the-middle attack: An attacker intercepts communications between the victim (client) and the target server. We assume that the proxy server is controlled by an attacker.
- (3)
- Data manipulation or interception: An attacker can intercept communications in the middle and view or manipulate data. This can lead to attacks such as leaking confidential information, stealing session tokens, or injecting malicious code.
Defense mechanism:
- (1)
- To successfully carry out a forgery attack, instead of CC (Control Center), the CS (Cloud Server) needs to compute , , then transmit RE= and to E. CS can calculate , by generating random values for private keys , and random numbers α, γ. The re-encryption values are computed as . CS then sends and to E for decryption. However, a challenge arises in transmitting to allow E to decrypt , the value of must be known. Since is a secret key pre-registered for secure communication between E and CC, an attacker cannot determine its value, preventing the creation of a valid . Consequently, E cannot decrypt it, rendering RE undecryptable.
- (2)
- In order for the CS to intercept and succeed in MitMs (man-in-the-middle attacks) and data manipulation, the attacker must first intercept and decrypt and transmitted by CC to CS and E. However, as the attacker cannot know the secret keys and of CS and E, respectively, eavesdropping becomes impossible, and as a result, MitMs and data manipulation also become impossible.
6. Efficiency Analysis
6.1. Complexity Analysis
When L represents the number of bits in the prime used in the ElGamal scheme, efficiency is analyzed by representing the time and space complexity for each construction as a Big-O notation.
System Setup
- SysPrm Construction:
- ·
- Time Complexity: O(g(s)), where g is the complexity of the parameter generation algorithm.
- ·
- Space Complexity: O(L).
Registration and Encryption - KeyGen Construction:
- ·
- Time Complexity: O(L) for selecting random values.
- ·
- Space Complexity: O(L).
- Enc Construction:
- ·
- Time Complexity: O() for modular exponentiation.
- ·
- Space Complexity: O(L).
Accident Occurrence - Ord_P(R) Construction:
- ·
- Time Complexity: O(1).
- ·
- Space Complexity: O(L).
- Rpt_CC Construction:
- ·
- Time Complexity: O(1).
- ·
- Space Complexity: O(L).
- Ord_F Construction:
- ·
- Time Complexity: O(1).
- ·
- Space Complexity: O(L).
Proxy Re-Encryption - RKeyGen Construction:
- ·
- Time Complexity: O(L).
- ·
- Space Complexity: O(L).
- PrxyRE Construction:
- ·
- Time Complexity: O() (involving exponentiation and multiplication of keys and messages).
- ·
- Space Complexity: O(L).
Treatment - Dec Construction:
- ·
- Time Complexity: O() (involving exponentiation and decryption).
- ·
- Space Complexity: O(L).
- Trt_Str Construction:
- ·
- Time Complexity: O(1) (assuming treatment and storage are basic operations).
- ·
- Space Complexity: O(L).
Simplifying, we can approximate the overall complexity as:Ototal(L).
6.2. Complexity Comparison with Other Methods
Ref. [16] was the first paper to present unidirectional chosen-ciphertext secure proxy re-encryption published in 2008. Ref. [17], published by Shao et al. in 2009, was the first study to consider not only CCA but also CR. Ref. [2] was the most efficient unidirectional proxy re-encryption published in 2010. Ref. [13] was a scheme announced in 2022 that is not unidirectional, but is secure for CCA and CR.
We compared and analyzed the computational complexity of the four papers above to evaluate the proposed scheme. Here, L represents the number of bits in the modulus used in the scheme, k is the length of the generated key.
As shown in Table 1, the paper focusing on efficiency published in 2010 had the best performance out of the papers published before our study was proposed. So, it is necessary to compare our paper with the paper published in 2010. The computational complexity of the 2010 paper was , and our paper was . In complexity notation, and can be said to have the same complexity.

Table 1.
Comparison with previous schemes.
All schemes are based on the assumption that the ‘Diffie Hellman problem is difficult’, and papers did not use pairing functions, apart from (2008).
6.3. Performance Analysis for Re-Encryption/Decryption
To evaluate the actual performance of the proposed proxy re-encryption protocol, we not only conducted a complexity analysis but also implemented the re-encryption and decryption processes to measure the time. Because the whole protocol heavily depends on network conditions and event situations, we only measured the core components of the proposed protocol, which are the re-encryption and decryption processes. The experimental environment is shown in Table 2.

Table 2.
Experimental environments.
Cryptographic parameters and libraries are addressed in the following Table 3.

Table 3.
Cryptographic parameters and libraries.
The experiment involved measuring the time for the re-encryption and decryption processes with message sizes set to 10 bytes, 100 bytes, 500 bytes, and 1000 bytes. The result is as follows in the Table 4.

Table 4.
Processing time for each message size.
For the re-encryption process, it was observed that as the message size increased, the process time gradually increased. For a message size of 2000 bytes, an exceptionally fast performance of approximately 0.02 s was demonstrated. For the decryption process, all recorded times showed as 0.0 s. This was likely due to the elapsed time being extremely small and showing as 0 s.
7. Conclusions
This paper presents a secure proxy re-encryption protocol for FANETs that can be used to securely transmit medical information in off-road emergency situations. The proposed protocol utilizes cryptographic techniques, including proxy re-encryption, to protect sensitive user information and enables authorized participants to access the encrypted medical records without revealing the original encryption key. The use of proxy re-encryption allows for secure transmission of medical information even when the original encryption key is not known by the recipient.
The use of drones and smartphones in emergency communication networks can significantly improve the response time and accuracy of emergency medical services. The analysis results show that the proposed protocol is resistant to CCA, collusion attacks, and forgery attacks and effective in protecting user privacy and ensuring the secure transmission of medical information.
Our proposed protocol did not use a pairing function with severe computational overhead, but because it used an exponential operation, it required a time complexity of . The proposed protocol can be further improved by incorporating more advanced cryptographic techniques such as lightweight encryption or hybrid encryption technologies and optimizing the communication network.
Funding
This study was supported by research funds from Honam University, 2023.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The author declares no conflict of interest.
References
- Rabieh, K.; Akkaya, K.; Karabiyik, U.; Qamruddin, J. A secure and cloud-based medical records access scheme for on-road emergencies. In Proceedings of the 15th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 12–15 January 2018. [Google Scholar]
- Chow, S.; Weng, J.; Yang, Y.; Deng, R. Efficient Unidirectional Proxy Re-Encryption. In Proceedings of the AFRICACRYPT 2010, Stellenbosch, South Africa, 3–6 May 2010; Volume 6055, pp. 316–332. [Google Scholar]
- Bae, M.; Kim, H. Authentication and Delegation for Operating a Multi-Drone System. Sensors 2019, 19, 2066. [Google Scholar] [CrossRef] [PubMed]
- Aydinm, Y.; Kurt, G.; Ozdemir, E.; Yanikomeroglu, H. Group Authentication for Drone Swarms. In Proceedings of the 2021 IEEE International Conference on Wireless for Space and Extreme Environments (WiSEE), Cleveland, OH, USA, 12–14 October 2021. [Google Scholar]
- Zhang, Y.; He, D.; Li, L.; Chen, B. A lightweight authentication and key agreement scheme for Internet of Drones. Comput. Commun. 2020, 154, 455–464. [Google Scholar] [CrossRef]
- Sekar, A.; Maria, A.; Al-Turjman, F.; Altrjman, C. Anonymous Mutual and Batch Authentication with Location Privacy of UAV in FANET. Drones 2022, 6, 14. [Google Scholar]
- Robakowska, M.; Ślęzak, D.; Żuratyński, P.; Tyrańska-Fobke, A.; Robakowski, P.; Prędkiewicz, P.; Zorena, K. Possibilities of Using UAVs in Pre-Hospital Security for Medical Emergencies. Int. J. Environ. Res. Public Health 2022, 19, 10754. [Google Scholar] [CrossRef] [PubMed]
- Mambo, M.; Okamoto, E. Proxy cryptosystems: Delegation of the power to decrypt ciphertexts. IEICE Trans. Fund. Electron. Commun. Comput. Sci. 1997, 80, 54–63. [Google Scholar]
- Blaze, M.; Bleumer, G.; Strauss, M. Divertible protocols and atomic proxy cryptography. In Proceedings of the Eurocrypt ’98, Helsinki, Finland, 31 May–4 June 1998; Volume 1403, pp. 127–144. [Google Scholar]
- Abdel-Malek, M.; Akkaya, K.; Bhuyan, A.; Ibrahim, A. A Proxy Signature-Based Swarm Drone Authentication With Leader Selection in 5G Networks. IEEE Access 2022, 10, 57485–57498. [Google Scholar] [CrossRef]
- 5G D2D ProSe; Technical Speci_Cation Group Services and System Aspects; Proximity-Based Services (ProSe); Security Aspects, Document TS 33.303 V16.0.0 Technical Specifkcation (Release 16). 3GPP: Valbonne, France, 2020.
- Rabieh, K.; Mercan, S.; Akkaya, K.; Baboolal, V.; Aygun, R.S. Privacy-preserving and efficient sharing of drone videos in public safety scenarios using proxy re-encryption. In Proceedings of the 2020 IEEE 21st International Conference on Information Reuse and Integration for Data Science, Las Vegas, NV, USA, 11–13 August 2020. [Google Scholar]
- Kan, J.; Zhang, J.; Liu, D.; Huang, X. Proxy Re-Encryption Scheme for Decentralized Storage Networks. Appl. Sci. 2022, 12, 4260. [Google Scholar] [CrossRef]
- Ateniese, G.; Fu, K.; Hohenberger, S.; Green, M. Improved proxy re-encryption schemes with applications to secure distributed storage. In ACM Transactions on Information and System Security; Association for Computing Machinery: New York, NY, USA, 2006; Volume 9. [Google Scholar] [CrossRef]
- Canetti, R.; Hohenberger, S. Chosen-ciphertext secure proxy re-encryption. In Proceedings of the CCS ‘07: Proceedings of the 14th ACM conference on Computer and Communications Security, Alexandria, VA, USA, 29 October–2 November 2007; pp. 185–194. [Google Scholar]
- Libert, B.; Vergnaud, D. Unidirectional Chosen-Ciphertext Secure Proxy Re-encryption. In Proceedings of the PKC 2008, Barcelona, Spain, 9–12 March 2008; Volume 4939, pp. 360–379. [Google Scholar]
- Shao, J.; Cao, Z. CCA-Secure Proxy Re-Encryption without Pairings. In Proceedings of the PKC 2009, Irvine, CA, USA, 18–20 March 2009; Sringer: Berlin/Heidelberg, Germany, 2009; Volume LNCS 5443, pp. 357–376. [Google Scholar]
- Weng, J.; Chen, M.; Yang, Y.; Deng, R.; Chen, K.; Bao, F. CCA-Secure Unidirectional Proxy Re-Encryption in the Adaptive Corruption Model without Random Oracles. Inf. Sci. 2010, 53, 593–606. [Google Scholar] [CrossRef][Green Version]
- Menezes, A.J.; Oorschot, P.C.; Vanstone, S.A. Handbook of Applied Cryptography, 1st ed.; CRC Press: Boca Raton, FL, USA, 1996. [Google Scholar]
- Bresson, E.; Chevassut, O.; Pointcheval, D. The Group Diffie-Hellman Problems. In Proceedings of the SAC 2002, St. John’s, NF, Canada, 15–16 August 2002; Volume LNCS 2595, pp. 325–338. [Google Scholar]
- Song, D.X.; Wagner, D.; Perrig, A. Practical techniques for searches on encrypted data. In Proceedings of the IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 14–17 May 2000; pp. 44–55. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).