Comparative Analysis of Deep Convolutional Neural Network—Bidirectional Long Short-Term Memory and Machine Learning Methods in Intrusion Detection Systems
Abstract
1. Introduction
Research Background
2. Related Work
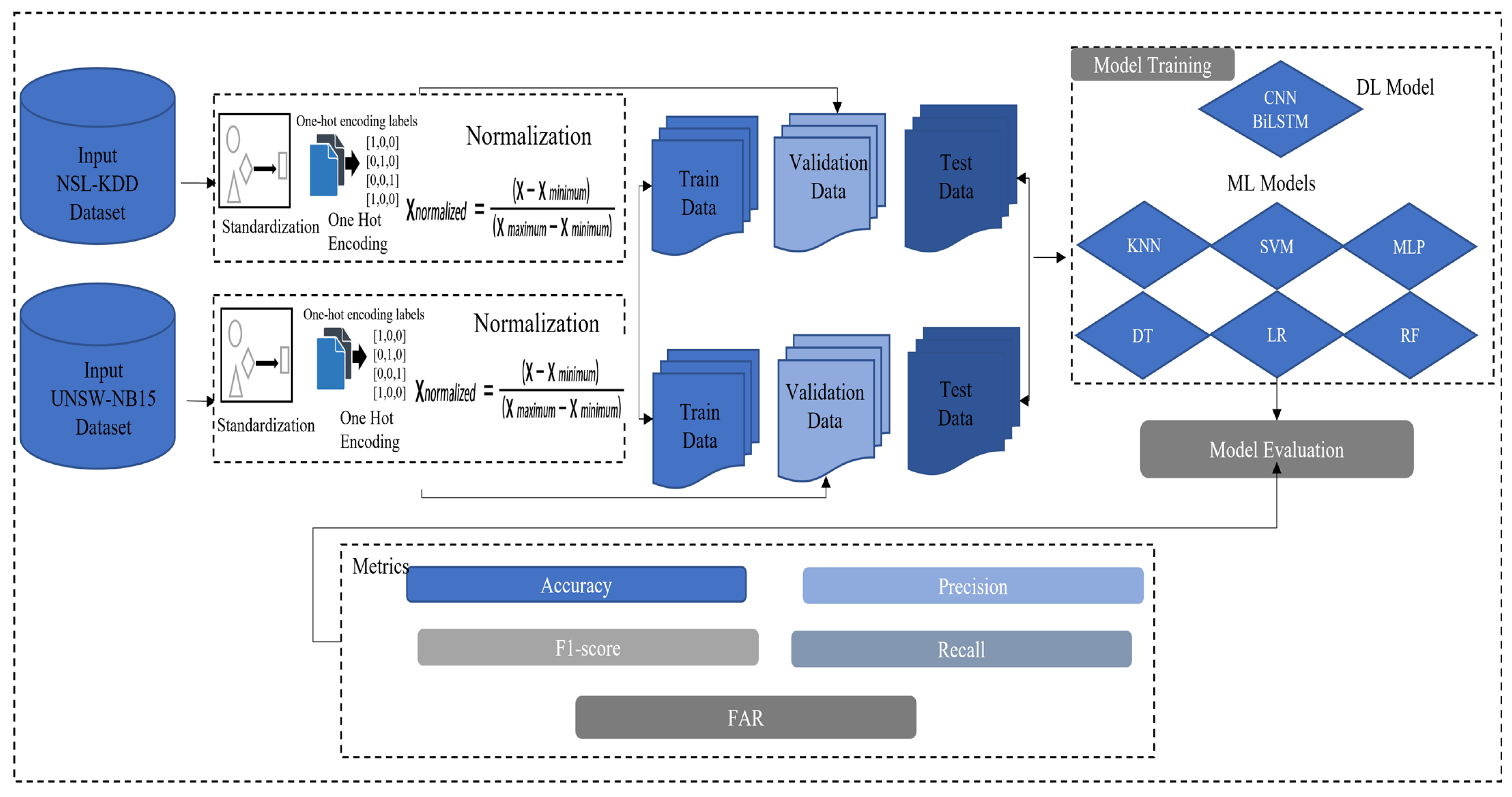
3. Materials and Methodology
3.1. Machine Learning Models
3.1.1. K-Nearest Neighbor
3.1.2. Support Vector Machine
3.1.3. Decision Tree
3.1.4. Multilayer Perceptron
3.1.5. Logistic Regression
3.1.6. Random Forest
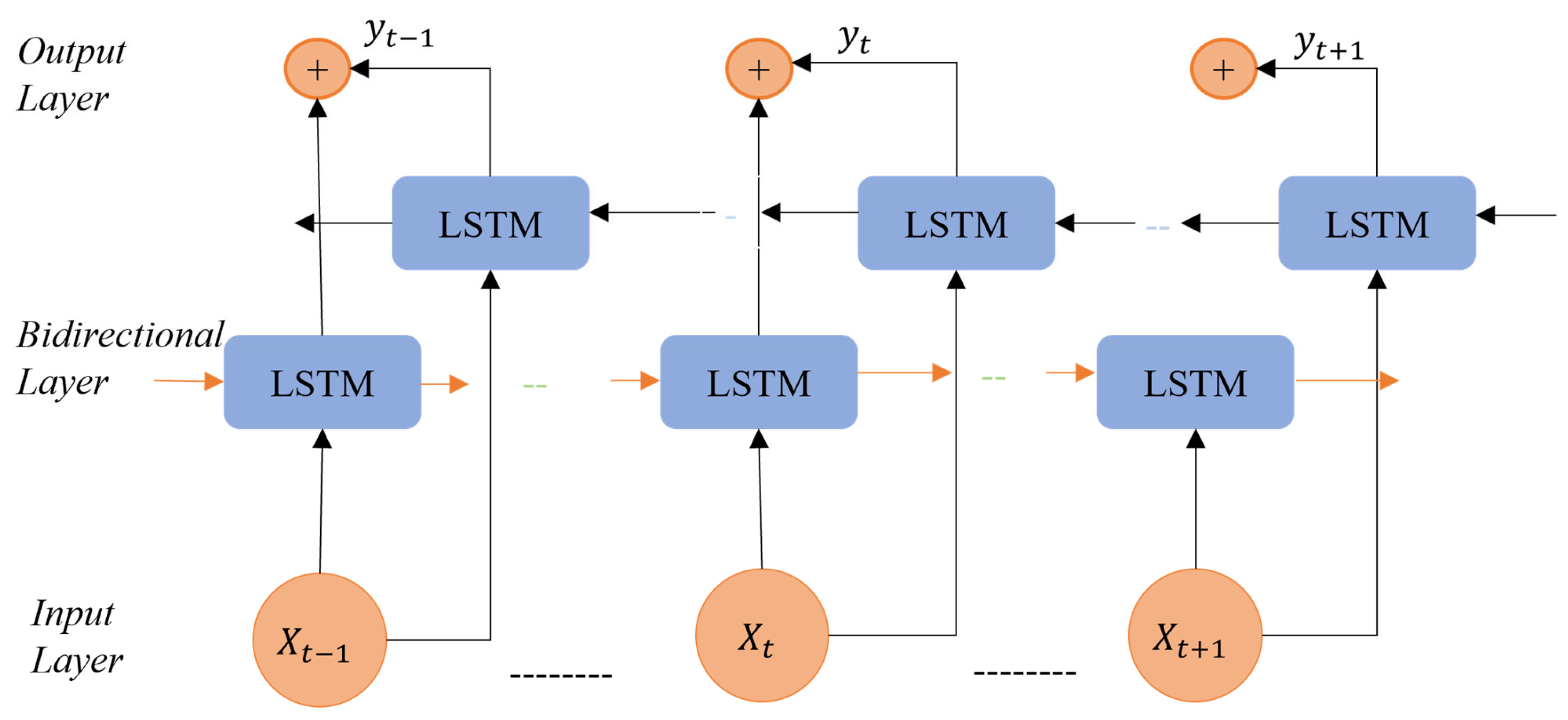
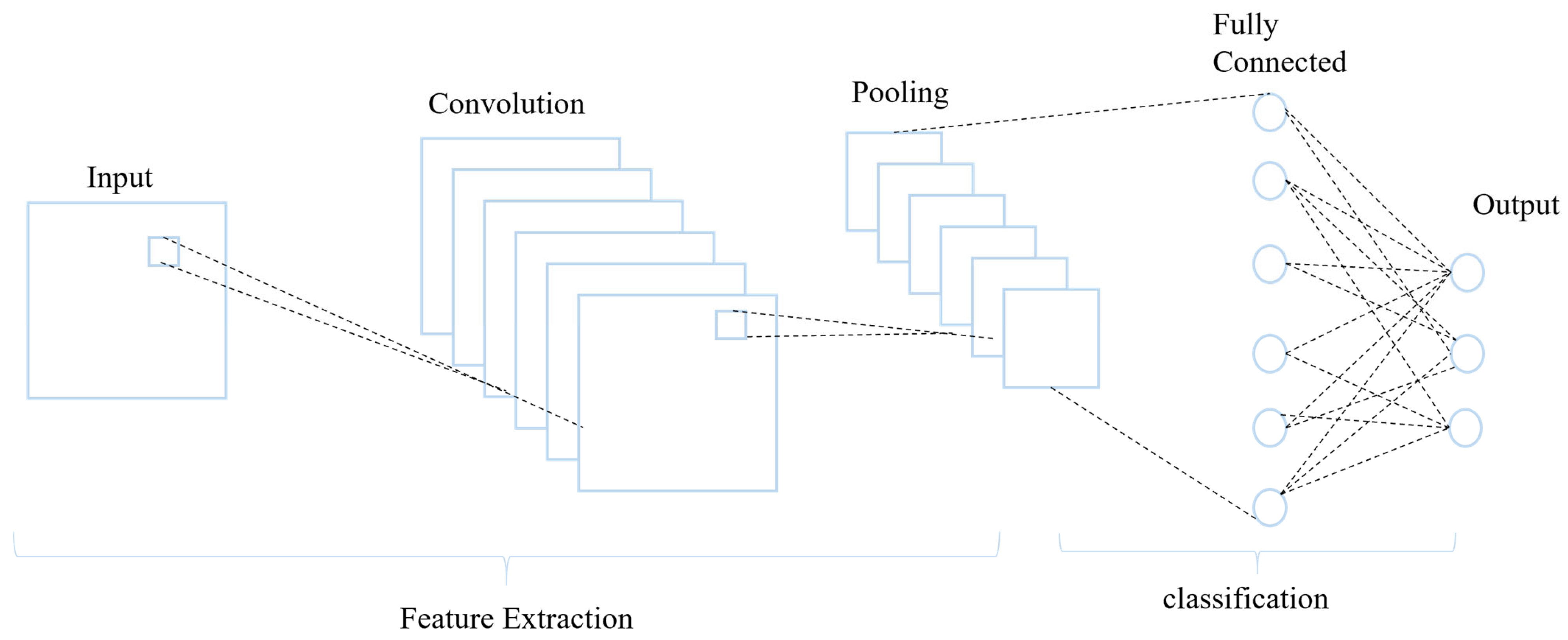
3.2. Deep Learning Models
CNN Bidirectional Long Short-Term Memory
4. Experiments
4.1. Description of the Datasets
4.1.1. NSL-KDD Datasets
4.1.2. UNSW-NB15 Datasets
4.2. Data Pre-Processing
4.3. Evaluation Metrics
5. Discussion
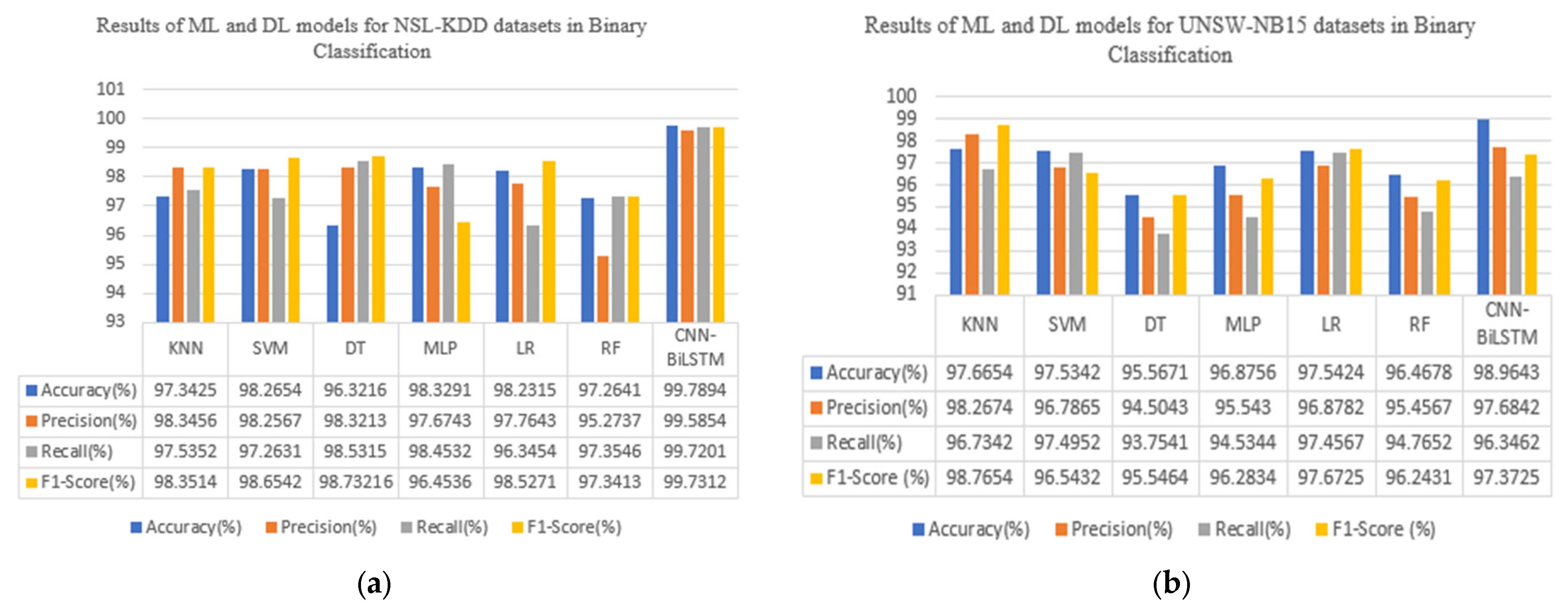
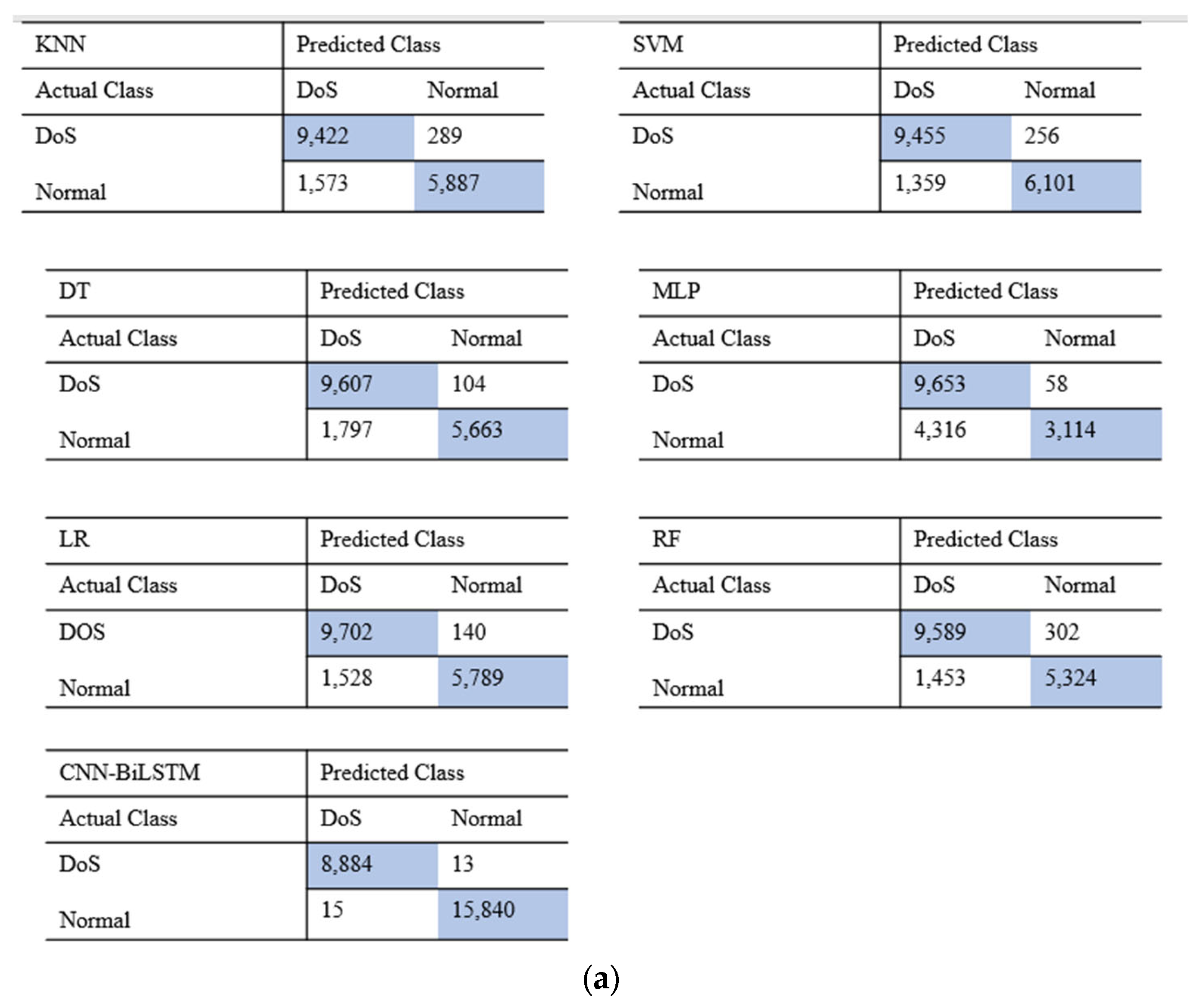
5.1. Comparison with Machine Learning and Deep Learning Models
5.2. Comparison with State-of-the-Art Methods
5.3. Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Zavrak, S.; İskefiyeli, M. Anomaly-Based Intrusion Detection from Network Flow Features Using Variational Autoencoder. IEEE Access 2020, 8, 108346–108358. [Google Scholar] [CrossRef]
- Kim, T.; Pak, W. Early Detection of Network Intrusions Using a GAN-Based One-Class Classifier. IEEE Access 2022, 10, 119357–119367. [Google Scholar] [CrossRef]
- Jan, S.U.; Ahmed, S.; Shakhov, V.; Koo, I. Toward a Lightweight Intrusion Detection System for the Internet of Things. IEEE Access 2019, 7, 42450–42471. [Google Scholar]
- Mishra, P.; Varadharajan, V.; Tupakula, U.; Pilli, E.S. A Detailed Investigation and Analysis of Using Machine Learning Techniques for Intrusion Detection. IEEE Commun. Surv. Tutor. 2019, 21, 686–728. [Google Scholar] [CrossRef]
- Hnamte, V.; Nhung-Nguyen, H.; Hussain, J.; Hwa-Kim, Y. A Novel Two-Stage Deep Learning Model for Network Intrusion Detection: LSTM-AE. IEEE Access 2023, 11, 37131–37148. [Google Scholar] [CrossRef]
- Sun, P.; Liu, P.; Li, Q.; Liu, C.; Lu, X.; Hao, R.; Chen, J. DL-IDS: Extracting features using CNN-LSTM hybrid network for intrusion detection system. Secur. Commun. Netw. 2020, 2020, 8890306. [Google Scholar] [CrossRef]
- Latif, S.; e Huma, Z.; Jamal, S.S.; Ahmed, F.; Ahmad, J.; Zahid, A.; Dashtipour, K.; Aftab, M.U.; Ahmad, M.; Abbasi, Q.H. Intrusion Detection Framework for the Internet of Things Using a Dense Random Neural Network. IEEE Trans. Ind. Inform. 2022, 18, 6435–6444. [Google Scholar] [CrossRef]
- Wang, J.; Miller, D.J.; Kesidis, G. Efficient mining of the multidimensional traffic cluster hierarchy for digesting visualization and anomaly identification. IEEE J. Sel. Areas Commun. 2006, 24, 1929–1941. [Google Scholar] [CrossRef]
- Huang, N.-F.; Kao, C.-N.; Hun, H.-W.; Jai, G.-Y.; Lin, C.-L. Apply data mining to defense-in-depth network security system. In Proceedings of the 19th International Conference on Advanced Information Networking and Applications (AINA’05) Volume 1 (AINA Papers), Taipei, Taiwan, 28–30 March 2005. [Google Scholar]
- Thaseen, I.S.; Kumar, C.A. Intrusion detection model using fusion of PCA and optimized SVM. In Proceedings of the International Conference Contemporary Computer Informatics, Mysore, India, 27–29 November 2014. [Google Scholar]
- Usha, M.; Kavitha, P. Anomaly-based intrusion detection for 802.11 networks with optimal features using SVM classifier. Wirel. Netw. 2017, 23, 2431–2446. [Google Scholar] [CrossRef]
- Pajouh, H.H.; Javidan, R.; Khayami, R.; Dehghantanha, A.; Choo, K.-K.R. A two-layer dimension reduction and two-tier classification model for anomaly-based intrusion detection in IoT backbone networks. IEEE Trans. Emerg. Topics Comput. 2019, 7, 314–323. [Google Scholar] [CrossRef]
- Wang, H.; Gu, J.; Wang, S. An effective intrusion detection framework based on SVM with feature augmentation. Knowl. Based Syst. 2017, 139, 130–139. [Google Scholar] [CrossRef]
- Thanh, H.N.; Lang, T.V. Use the ensemble methods when detecting DoS attacks in network intrusion detection systems. EAI Endorsed Trans. Context Aware Syst. Appl. 2019, 6, e5. [Google Scholar] [CrossRef]
- Xiong, Z.; Xu, H.; Li, W.; Cai, Z. Multi-source adversarial sample attack on autonomous vehicles. IEEE Trans. Veh. Technol. 2021, 70, 2822–2835. [Google Scholar] [CrossRef]
- Cai, Z.; Xiong, Z.; Xu, H.; Wang, P.; Li, W.; Pan, Y. Generative adversarial networks: A survey toward private and secure applications. ACM Comput. Surveys 2021, 54, 1–38. [Google Scholar] [CrossRef]
- Gui, G.; Liu, M.; Tang, F.; Kato, N.; Adachi, F. 6G: Opening new horizons for integration of comfort security and intelligence. IEEE Wirel. Commun. 2020, 27, 126–132. [Google Scholar] [CrossRef]
- Yin, C.; Zhu, Y.; Fei, J.; He, X. A deep learning approach for intrusion detection using recurrent neural networks. IEEE Access 2017, 5, 21954–21961. [Google Scholar] [CrossRef]
- He, H.; Sun, X.; He, H.; Zhao, G.; He, L.; Ren, J. A novel multimodal-sequential approach based on multi-view features for network intrusion detection. IEEE Access 2019, 7, 183207–183221. [Google Scholar] [CrossRef]
- Jaber, A.N.; Zolkipli, M.F.; Shakir, H.A.; Jassim, M.R. Host-based intrusion detection and prevention model against DDoS attack in cloud computing. In Advances on P2P, Parallel, Grid, Cloud and Internet Computing; 3PGCIC 2017. Lecture Notes on Data Engineering and Communications Technologies; Springer: Cham, Switzerland, 2017. [Google Scholar]
- Garg, S.; Kaur, K.; Kumar, N.; Kaddoum, G.; Zomaya, A.Y.; Ranjan, R. A hybrid deep learning-based model for anomaly detection in cloud data center networks. IEEE Trans. Netw. Service Manag. 2019, 16, 924–935. [Google Scholar] [CrossRef]
- Vinayakumar, R.; Soman, K.P.; Poornachandran, P. Applying convolutional neural network for network intrusion detection. In Proceedings of the International Conference Advance Computer Informatics (ICACCI), Udupi, India, 13–16 September 2017. [Google Scholar]
- Zhang, Y.; Chen, X.; Jin, L.; Wang, X.; Guo, D. Network intrusion detection: Based on deep hierarchical network and original flow data. IEEE Access 2019, 7, 37004–37016. [Google Scholar] [CrossRef]
- Vinayakumar, R.; Alazab, M.; Soman, K.; Poornachandran, P.; Al-Nemrat, A.; Venkatraman, S. Deep learning approach for intelligent intrusion detection system. IEEE Access 2019, 7, 41525–41550. [Google Scholar] [CrossRef]
- Kasongo, S.M.; Sun, Y. A deep long short-term memory-based classifier for wireless intrusion detection system. ICT Exp. 2020, 6, 98–103. [Google Scholar] [CrossRef]
- Zhang, J.; Ye, L.; Lai, Y. Stock Price Prediction Using CNN-BiLSTM-Attention Model. Mathematics 2023, 11, 1985. [Google Scholar] [CrossRef]
- Staffini, A. A CNN–BiLSTM Architecture for Macroeconomic Time Series Forecasting. Eng. Proc. 2023, 39, 33. [Google Scholar] [CrossRef]
- Tang, C.; Zhang, Y.; Wu, F.; Tang, Z. An Improved CNN-BILSTM Model for Power Load Prediction in Uncertain Power Systems. Energies 2024, 17, 2312. [Google Scholar] [CrossRef]
- Cui, K.X.; Xia, X.J. ECG Signal Anomaly Detection Algorithm Based on CNN-BiLSTM. In Proceedings of the 2022 11th International Conference of Information and Communication Technology (ICTech)), Wuhan, China, 4–6 February 2022; pp. 193–197. [Google Scholar]
- Naseer, S.; Saleem, Y.; Khalid, S.; Bashir, M.K.; Han, J.; Iqbal, M.M.; Han, K. Enhanced Network Anomaly Detection Based on Deep Neural Networks. IEEE Access 2018, 6, 48231–48246. [Google Scholar] [CrossRef]
- He, K.; Kim, D.D.; Asghar, M.R. Adversarial Machine Learning for Network Intrusion Detection Systems: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2022, 25, 538–566. [Google Scholar] [CrossRef]
- He, M.; Wang, X.; Wei, P.; Yang, L.; Teng, Y.; Lyu, R. Reinforcement Learning Meets Network Intrusion Detection: A Transferable and Adaptable Framework for Anomaly Behavior Identification. IEEE Trans. Netw. Serv. Manag. 2024, 21, 2477–2492. [Google Scholar] [CrossRef]
- Halbouni, A.; Gunawan, T.S.; Habaebi, M.H.; Halbouni, M.; Kartiwi, M.; Ahmad, R. CNN-LSTM: Hybrid Deep Neural Network for Network Intrusion Detection System. IEEE Access 2022, 10, 99837–99849. [Google Scholar] [CrossRef]
- Khan, M.A.; Khan, M.A.; Jan, S.U.; Ahmad, J.; Jamal, S.S.; Shah, A.A.; Pitropakis, N.; Buchanan, W.J. A Deep Learning-Based Intrusion Detection System for MQTT Enabled IoT. Sensors 2021, 21, 7016. [Google Scholar] [CrossRef] [PubMed]
- De Carvalho Bertoli, G.; Júnior, L.A.; Saotome, O.; Dos Santos, A.L.; Verri, F.A.; Marcondes, C.A.; Barbieri, S.; Rodrigues, M.S.; De Oliveira, J.M. An End-to-End Framework for Machine Learning-Based Network Intrusion Detection System. IEEE Access 2021, 9, 106790–106805. [Google Scholar] [CrossRef]
- Azam, Z.; Islam, M.M.; Huda, M.N. Comparative Analysis of Intrusion Detection Systems and Machine Learning-Based Model Analysis Through Decision Tree. IEEE Access 2023, 11, 80348–80391. [Google Scholar] [CrossRef]
- Ghanem, W.A.H.M.; Jantan, A.; Ghaleb, S.A.A.; Nasser, A.B. An Efficient Intrusion Detection Model Based on Hybridization of Artificial Bee Colony and Dragonfly Algorithms for Training Multilayer Perceptrons. IEEE Access 2020, 8, 130452–130475. [Google Scholar] [CrossRef]
- Xu, C.; Shen, J.; Du, X.; Zhang, F. An Intrusion Detection System Using a Deep Neural Network with Gated Recurrent Units. IEEE Access 2018, 6, 48697–48707. [Google Scholar] [CrossRef]
- Liu, C.; Gu, Z.; Wang, J. A Hybrid Intrusion Detection System Based on Scalable K-Means+ Random Forest and Deep Learning. IEEE Access 2021, 9, 75729–75740. [Google Scholar] [CrossRef]
- Kasongo, S.M. An Advanced Intrusion Detection System for IIoT Based on GA and Tree-Based Algorithms. IEEE Access 2021, 9, 113199–113212. [Google Scholar] [CrossRef]
- Putchala, M.K. Deep Learning Approach for Intrusion Detection System (IDS) in the Internet of Things (IoT) Network Using Gated Recurrent Neural Networks (GRU). Master’s Thesis, Wright State University, Dayton, OH, USA, 2017. [Google Scholar]
- Xu, W.; Jang-Jaccard, J.; Singh, A.; Wei, Y.; Sabrina, F. Improving Performance of Autoencoder-Based Network Anomaly Detection on NSL-KDD Dataset. IEEE Access 2021, 9, 140136–140146. [Google Scholar] [CrossRef]
- Moustafa, N.; Slay, J. UNSW-NB15: A comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set). In Proceedings of the IEEE Military Communication Information System Conference (MilCIS), Canberra, Australia, 10–12 November 2015. [Google Scholar]
- Martinez-Vega, B.; Tkachenko, M.; Matkabi, M.; Ortega, S.; Fabelo, H.; Balea-Fernandez, F.; La Salvia, M.; Torti, E.; Leporati, F.; Callico, G.M.; et al. Evaluation of Preprocessing Methods on Independent Medical Hyperspectral Databases to Improve Analysis. Sensors 2022, 22, 8917. [Google Scholar] [CrossRef]
- Gao, Y.; Wu, H.; Song, B.; Jin, Y.; Luo, X.; Zeng, X. A Distributed Network Intrusion Detection System for Distributed Denial of Service Attacks in Vehicular Ad Hoc Network. IEEE Access 2019, 7, 154560–154571. [Google Scholar] [CrossRef]
- Idhammad, M.; Afdel, K.; Belouch, M. Semi-supervised machine learning approach for DDoS detection. Appl. Intell. 2018, 48, 3193–3208. [Google Scholar] [CrossRef]
- Elsayed, S.; Mohamed, K.; Madkour, A. A Comparative Study of Using Deep Learning Algorithms in Network Intrusion Detection. IEEE Access 2024, 10, 1109. [Google Scholar] [CrossRef]
- Al-Garadi, M.; Mohammed, A.; Ali, K.; Guizani, M. A Survey of Machine and Deep Learning Methods for Internet of Things Security. IEEE Commun. Surv. Tutor. 2020, 22, 1646–1685. [Google Scholar] [CrossRef]
- Shone, N.; Phai, D.; Shi, Q. A Deep Learning Approach to Network Intrusion Detection. IEEE Trans. Emerg. Top. Comput. Intell. 2018, 2, 41–50. [Google Scholar] [CrossRef]

| Group | Feature Numbers | Count |
|---|---|---|
| Basic feature | 1, 2, 3, 4, 5, 6, 7, 8, 9 | 9 |
| Content feature | 10, 11, 12, 13, 14, 15, 16, 17, 18, 19, 20, 21 | 13 |
| Time feature | 23, 24, 25, 26, 27, 28, 29, 30, 31 | 9 |
| Host feature | 32, 33, 34, 35, 36, 37, 38, 39, 40, 41 | 10 |
| Type | Training Dataset | Testing Dataset | ||
|---|---|---|---|---|
| KDD_Train | KDD_Train_20percent | KDD_Test | KDDTest-21 | |
| Normal | 67,343 | 13,449 | 9711 | 2152 |
| Probe | 11,656 | 2289 | 2421 | 2402 |
| DoS | 45,927 | 9234 | 7458 | 4343 |
| U2R | 52 | 11 | 200 | 200 |
| R2L | 995 | 209 | 2751 | 2754 |
| Total | 125,973 | 25,192 | 22,544 | 11,850 |
| Group | Feature Numbers | Count |
|---|---|---|
| Flow feature | 2 | 1 |
| Basic feature | 1, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15 | 14 |
| Content feature | 20, 21, 22, 23, 27, 28, 29, 30 | 8 |
| Time feature | 16, 17, 18, 19, 24, 25, 26, 42 | 8 |
| Additional feature | 31, 32, 33, 34, 35, 36, 37, 38, 39, 40, 41 | 11 |
| Type | Training Dataset | Testing Dataset |
|---|---|---|
| Normal | 56,000 | 37,000 |
| Generic | 40,000 | 18,871 |
| Exploits | 33,393 | 11,132 |
| Fuzzers | 18,184 | 6062 |
| DoS | 12,264 | 4089 |
| Reconnaissance | 10,491 | 3496 |
| Analysis | 2000 | 677 |
| Backdoor | 1746 | 583 |
| Shellcode | 1133 | 378 |
| Worms | 130 | 44 |
| Total | 175,341 | 82,332 |
| Classifiers | Accuracy (%) | Precision (%) | Recall (%) | F1-Score (%) | FARnorm (%) | FARattacks (%) |
|---|---|---|---|---|---|---|
| KNN | 97.42 ± 0.510 | 98.45 ± 0.655 | 97.67 ± 0.567 | 98.77 ± 0.460 | 0.2231 | 0.1320 |
| SVM | 98.65 ± 0.538 | 99.76 ± 0.669 | 97.54 ± 0.453 | 98.54 ± 0.577 | 0.2325 | 0.1551 |
| DT | 96.54 ± 0.610 | 98.54 ± 0.506 | 98.01 ± 0.601 | 98.74 ± 0.543 | 0.2539 | 0.1810 |
| MLP | 98.32 ± 0.407 | 97.46 ± 0.494 | 98.42 ± 0.422 | 96.28 ± 0.340 | 0.0215 | 0.0601 |
| LR | 98.44 ± 0.313 | 97.35 ± 0.404 | 96.25 ± 0.334 | 98.45 ± 0.422 | 0.1692 | 0.1024 |
| RF | 97.75 ± 0.461 | 95.56 ± 0.388 | 97.12 ± 0.492 | 97.42 ± 0.420 | 0.2009 | 0.1253 |
| CNN-BiLSTM | 99.89 ± 0.510 | 99.85 ± 0.532 | 99.83 ± 0.532 | 99.84 ± 0.532 | 0.0088 | 0.0017 |
| Classifiers | Accuracy (%) | Precision (%) | Recall (%) | F1-Score (%) | FARnorm (%) | FARattacks (%) |
|---|---|---|---|---|---|---|
| KNN | 97.78 ± 0.012 | 98.17 ± 0.027 | 96.61 ± 0.014 | 98.89 ± 0.027 | 0.0466 | 0.0439 |
| SVM | 97.42 ± 0.004 | 96.88 ± 0.026 | 97.38 ± 0.004 | 96.62 ± 0.026 | 0.0042 | 0.0264 |
| DT | 95.32 ± 0.044 | 94.60 ± 0.011 | 93.66 ± 0.044 | 95.69 ± 0.011 | 0.0241 | 0.0111 |
| MLP | 96.98 ± 0.018 | 95.46 ± 0.016 | 94.41 ± 0.018 | 96.19 ± 0.016 | 0.0177 | 0.0159 |
| LR | 97.32 ± 0.005 | 96.84 ± 0.027 | 97.34 ± 0.006 | 97.58 ± 0.027 | 0.0056 | 0.0265 |
| RF | 96.25 ± 0.021 | 95.36 ± 0.011 | 94.86 ± 0.021 | 94.11 ± 0.011 | 0.0205 | 0.0114 |
| CNN-BiLSTM | 98.95 ± 0.017 | 97.73 ± 0.018 | 96.20 ± 0.017 | 96.16 ± 0.018 | 0.0172 | 0.0183 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Udurume, M.; Shakhov, V.; Koo, I. Comparative Analysis of Deep Convolutional Neural Network—Bidirectional Long Short-Term Memory and Machine Learning Methods in Intrusion Detection Systems. Appl. Sci. 2024, 14, 6967. https://doi.org/10.3390/app14166967
Udurume M, Shakhov V, Koo I. Comparative Analysis of Deep Convolutional Neural Network—Bidirectional Long Short-Term Memory and Machine Learning Methods in Intrusion Detection Systems. Applied Sciences. 2024; 14(16):6967. https://doi.org/10.3390/app14166967
Chicago/Turabian StyleUdurume, Miracle, Vladimir Shakhov, and Insoo Koo. 2024. "Comparative Analysis of Deep Convolutional Neural Network—Bidirectional Long Short-Term Memory and Machine Learning Methods in Intrusion Detection Systems" Applied Sciences 14, no. 16: 6967. https://doi.org/10.3390/app14166967
APA StyleUdurume, M., Shakhov, V., & Koo, I. (2024). Comparative Analysis of Deep Convolutional Neural Network—Bidirectional Long Short-Term Memory and Machine Learning Methods in Intrusion Detection Systems. Applied Sciences, 14(16), 6967. https://doi.org/10.3390/app14166967








