PowerBridge: Covert Air-Gap Exfiltration/Infiltration via Smart Plug
Abstract
1. Introduction
1.1. Network Covert Channel
1.2. Air-Gap Covert Channels
1.3. Smart Plug Security Risks
1.4. Our Contribution
- To the best of our knowledge, this is the first air-gap channel that utilizes smart plugs to achieve bidirectional communication through an air-gapped network. It employs smart plugs for power consumption detection and incorporates manufacturing power switches for bidirectional communication. In comparison to the existing PowerHammer method, which enables only one-way communication, our approach achieves bidirectional communication on the laptop end.
- We conducted extensive experiments on smart plugs and various laptop models to determine the effectiveness and maximum communication speed of PowerBridge.
- The code does not require special permissions (such as root or administrator). Users can operate from ordinary user-level processes or applications with a wide range of security risks.
- PowerBridge utilizes a standard CPU to enable air-gap communication, enabling the establishment of communication channels on nearly any computer or device equipped with a CPU.
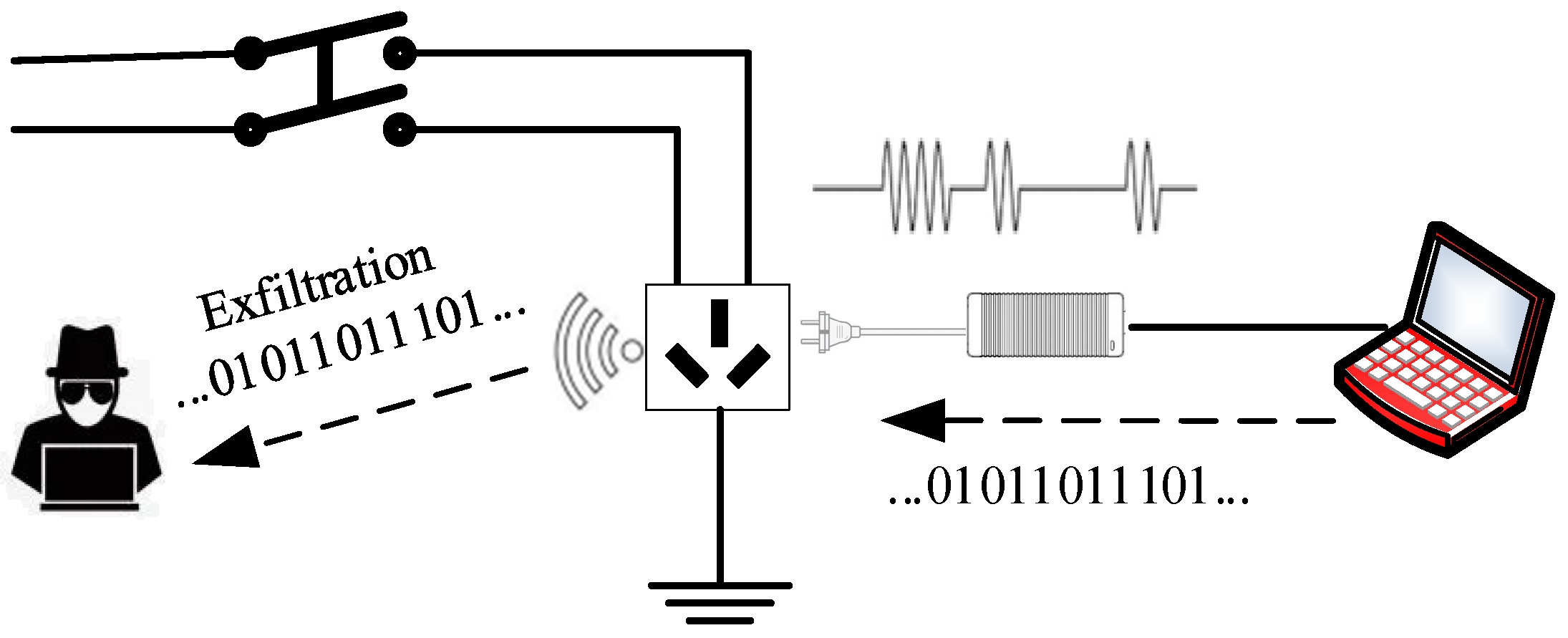
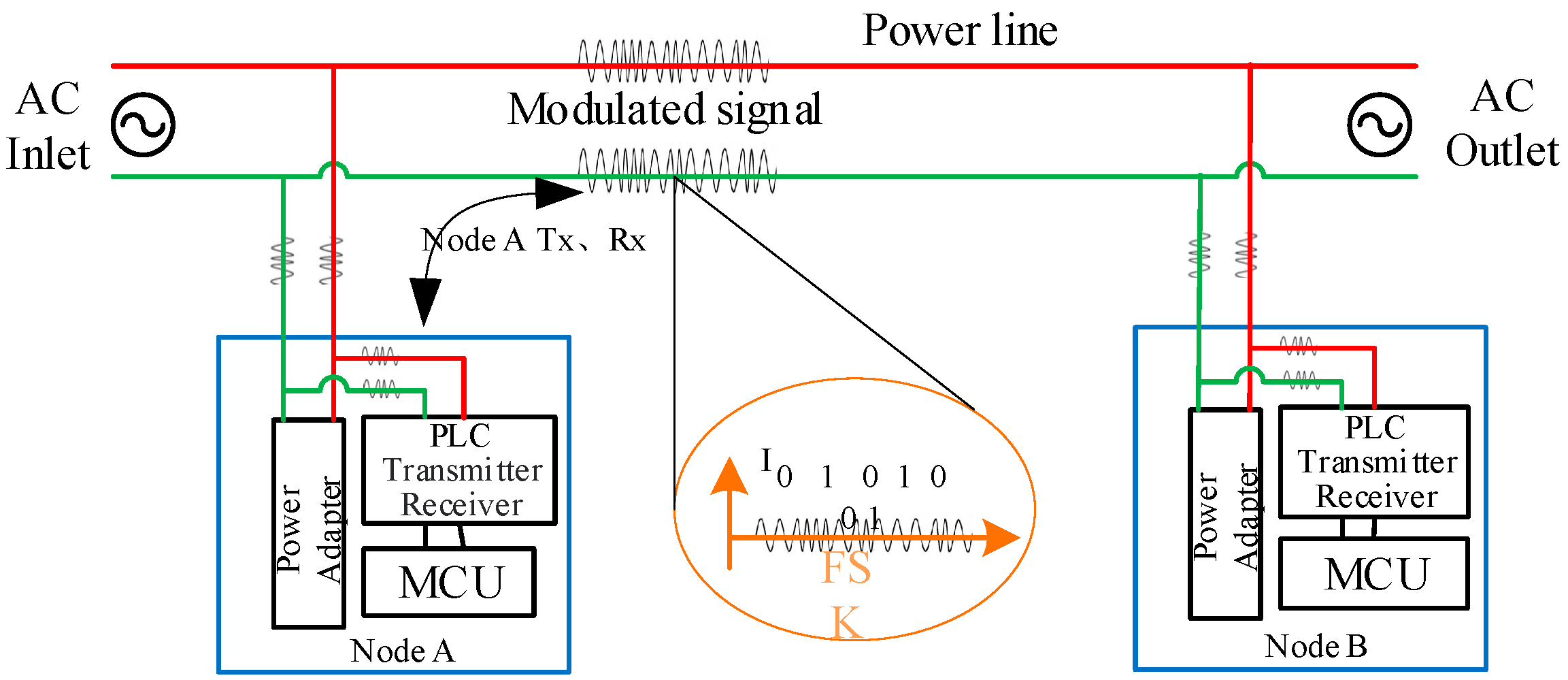
2. Bridge Scenario
2.1. Preparation Work
2.2. Exfiltration
- Data transmission: Malware utilizes the CPU and other hardware to manipulate power consumption fluctuations in devices, encoding and transmitting data through the power line. The attacker can schedule a specific time for malware transmission or send it after receiving instructions from the attacker, which involves bidirectional communication.
- Data reception: The signal transmitted by the air-gapped device can be received by the smart plug that provides power to it. Subsequently, the received signal will be recorded and forwarded to the receiver for decoding. The hardware responsible for receiving signals may either be deployed by internal personnel or consist of IoT devices that have already been remotely controlled.
2.3. Infiltration
2.4. Dangerous Places
2.5. Other Methods
3. Related Work
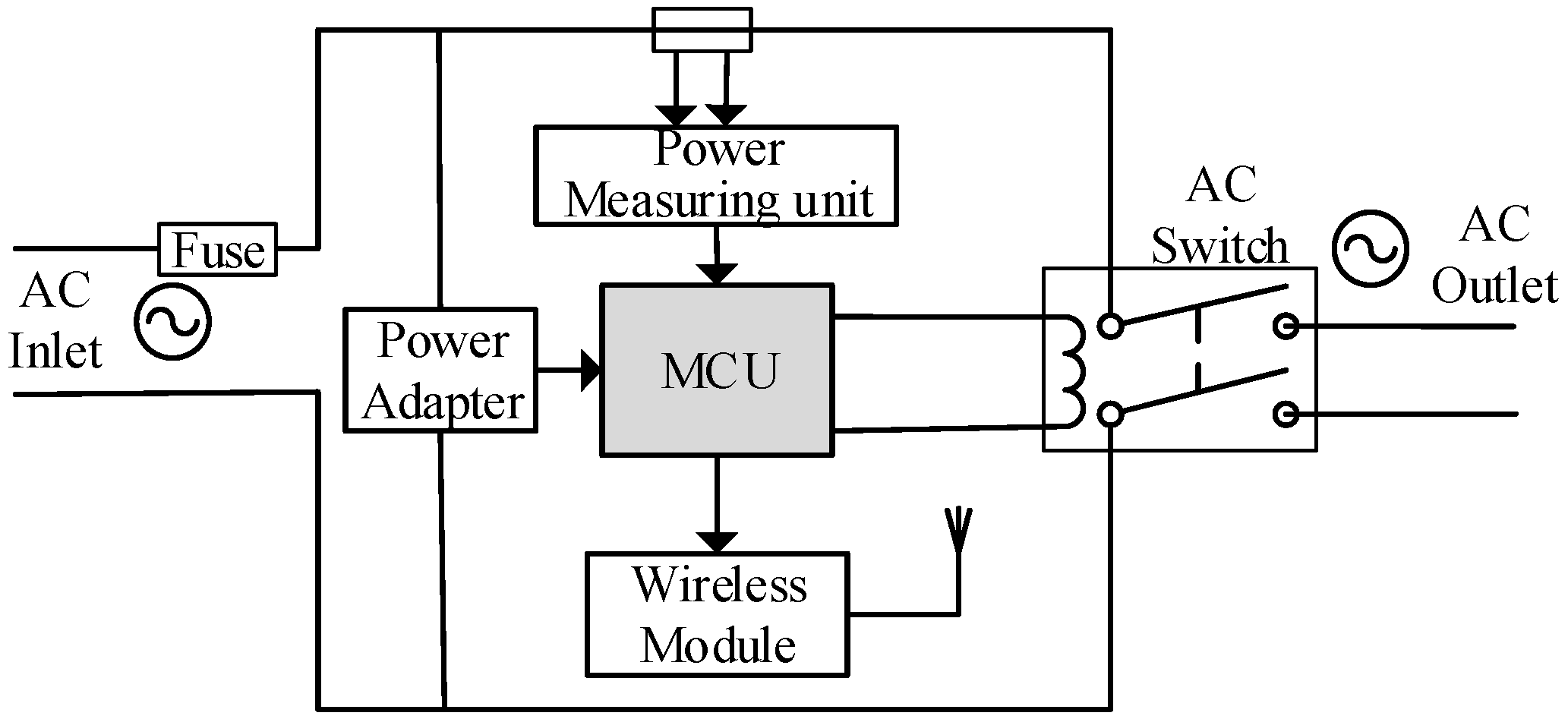
4. Power Line Communication and Smart Plug
4.1. Power Line Communication
4.2. Smart Plug
4.3. Computer Power Management
5. Channel Signal Generation
5.1. Exfiltration (Creating Power Line Current Fluctuations through the CPU)
| Algorithm 1 CPU Power consumption signal modulation algorithm |
|
5.2. Infiltration (Control Power On and Off through Smart Plug)
6. Data Encoding and Decoding
6.1. Communication Modulation
6.1.1. Modulation of Exfiltration Communication
- ASK is a digital modulation technique that utilizes the amplitude of the carrier wave to transmit information by varying the digital baseband signal. The program can regulate the power line current’s magnitude (amplitude) through different CPU load sizes. In the Binary Amplitude Key (2ASK), binary digits “0” and “1” correspond to two distinct states of carrier amplitude, and analog modulation and keying methods can generate the 2ASK signal. Although this modulation algorithm is relatively straightforward and intuitive, it suffers from low communication rate issues. To enhance transmission rate, multi-amplitude-shift keying (MASK) can be employed, where M represents the controllable number of CPU cores. MASK exhibits two notable characteristics: Firstly, in the same channel code source modulation scheme, each symbol has the capacity to carry log2M bits of information. Consequently, when the channel frequency band is constrained, it enables an increase in the transmission rate of information and enhances frequency band utilization. However, this advantage comes at the expense of amplified signal power and increased implementation complexity. Secondly, for a given information rate, multi-level base methods exhibit lower channel transmission rates compared to binary methods. As a result, the duration of multi-level signal code sources is wider than that of binary methods. Expanding the symbol width augments energy within signal symbols, while simultaneously mitigating the inter-symbol interference arising from channel characteristics [43]. Although multi-level MASK modulation serves as an efficient transmission technique, its susceptibility to noise and fading renders it more suitable for scenarios with minimal channel interference. Figure 19 shows the waveform of computer power consumption; with 0–8 cores gradually reaching full load on an 8-core CPU, it can display 24-bit binary sequence data.
- FSK is a digital modulation technique that utilizes the frequency of the carrier wave to transmit information by varying the digital baseband signal. It is well-known that the signal frequency can be manipulated by adjusting the time interval between two CPU loads. Hence, in an exfiltration scenario, binary information “0” and “1” correspond to two distinct frequencies f1 and f2 of the carrier signal, respectively. The implementation of 2FSK is relatively straightforward, exhibiting excellent performance in terms of noise and attenuation resistance, making it extensively employed for medium- and low-speed data transmission applications. When employing a multi-base system for modulation, it is referred to as MFSK, which employs multiple carrier frequencies to represent diverse methods of digital information modulation. Figure 20 illustrates both time-domain signals and the corresponding spectra of a synthesized 4-frequency FSK achieved through fluctuations in CPU power consumption at frequencies of 7 Hz, 13 Hz, 17 Hz, and 23 Hz.
- PSK is a digital modulation scheme that utilizes the phase of the carrier signal to encode input information. Phase-shift keying can be categorized into two types: absolute phase shift and relative phase shift. Absolute phase-shifting refers to phase modulation based on the unmodulated carrier’s initial phase. Taking binary phase modulation as an example, when the symbol is set to “0”, the modulated carrier remains in phase with the unmodulated carrier; whereas, when the symbol is set to “1”, the modulated carrier undergoes a 180° inversion from its original state. The waveform representing the difference in carrier phases between “0” and “1” exhibits a 180° change, and for 2PSK, it follows a modulation pattern of “01001001”, as illustrated in Figure 21.
6.1.2. Modulation of Infiltration Communication
6.2. Data Packets
6.3. Signal Reception and Data Decoding
| Algorithm 2 PIM signal demodulation algorithm |
|
7. Evaluation and Analysis
7.1. Exfiltration
7.1.1. Communication Rate
7.1.2. Universality
7.2. Infiltration
7.2.1. Bit Rate
7.2.2. Universality
8. Discussion
8.1. Exfiltration Countermeasures
8.1.1. Detection
8.1.2. Signal Interference
8.2. Infiltration Countermeasures
9. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Nagendran, K.; Balaji, S.; Raj, B.A.; Chanthrika, P.; Amirthaa, R.G. Web Application Firewall Evasion Techniques. In Proceedings of the 2020 6th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 6–7 March 2020; pp. 194–199. [Google Scholar]
- Michener, D.R.J. Beating the Air-Gap: How Attackers Can Gain Access to Supposedly Isolated Systems. 2018. Available online: https://energycentral.com/c/iu/beating-air-gap-how-attackers-can-gain-access-supposedly-isolated-systems (accessed on 25 June 2024).
- Elsadig, M.A.; Fadlalla, Y.A. Network Protocol Covert Channels: Countermeasures Techniques. In Proceedings of the 2017 9th IEEE-GCC Conference and Exhibition (GCCCE), Manama, Bahrain, 8–11 May 2017; pp. 1–9. [Google Scholar]
- Shen, C.; Liu, T.; Huang, J.; Tan, R. When LoRa Meets EMR: Electromagnetic Covert Channels Can Be Super Resilient. In Proceedings of the 2021 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 24–27 May 2021; pp. 1304–1317. [Google Scholar]
- Kim, T.; Shin, Y. ThermalBleed: A Practical Thermal Side-Channel Attack. IEEE Access 2022, 10, 25718–25731. [Google Scholar] [CrossRef]
- Sherry, R.; Bayne, E.; McLuskie, D. Near-Ultrasonic Covert Channels Using Software-Defined Radio Techniques. In Proceedings of the International Conference on Cybersecurity, Situational Awareness and Social Media; Springer Proceedings in Complexity; Springer: Singapore, 2023. [Google Scholar]
- Guri, M.; Zadov, B.; Bykhovsky, D.; Elovici, Y. PowerHammer: Exfiltrating data from air-gapped computers through power lines. IEEE Trans. Inf. Forensics Secur. 2019, 15, 1879–1890. [Google Scholar] [CrossRef]
- Cronin, P.; Gouert, C.; Mouris, D.; Tsoutsos, N.G.; Yang, C. Covert data exfiltration using light and power channels. In Proceedings of the 2019 IEEE 37th International Conference on Computer Design (ICCD), Abu Dhabi, United Arab Emirates, 17–20 November 2019; pp. 301–304. [Google Scholar]
- Davis, B.D.; Mason, J.C.; Anwar, M. Vulnerability studies and security postures of IoT devices: A smart home case study. IEEE Internet Things J. 2020, 7, 10102–10110. [Google Scholar] [CrossRef]
- Zhou, Z.; Zhang, W.; Li, S.; Yu, N. Potential Risk of IoT Device Supporting IR Remote Control. Comput. Netw. 2019, 148, 307–317. [Google Scholar] [CrossRef]
- Ling, Z.; Luo, J.; Xu, Y.; Gao, C.; Wu, K.; Fu, X. Security vulnerabilities of internet of things: A case study of the smart plug system. IEEE Internet Things J. 2017, 4, 1899–1909. [Google Scholar] [CrossRef]
- Gnad, D.R.; Krautter, J.; Tahoori, M.B. Leaky noise: New side-channel attack vectors in mixed-signal IoT devices. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2019, 2019, 305–339. [Google Scholar] [CrossRef]
- New Security Signals Study Shows Firmware Attacks on the Rise. 2021. Available online: https://www.microsoft.com/en-us/security/blog/2021/03/30/new-security-signals-study-shows-firmware-attacks-on-the-rise-heres-how-microsoft-is-working-to-help-eliminate-this-entire-class-of-threats/ (accessed on 3 May 2024).
- McAfee: Discovers New IoT Vulnerability in Wemo Insight Smart Plugs. 2019. Available online: https://www.mcafee.com/blogs/internet-security/wemo-vulnerability (accessed on 3 May 2024).
- Iqbal, A.; Olegård, J.; Ghimire, R.; Jamshir, S.; Shalaginov, A. Smart Home Forensics: An Exploratory Study on Smart Plug Forensic Analysis. In Proceedings of the 2020 IEEE International Conference on Big Data (Big Data), Atlanta, GA, USA, 10–13 December 2020; pp. 2283–2290. [Google Scholar]
- Khosravi, M.; Ladani, B.T. Alerts Correlation and Causal Analysis for APT Based Cyber Attack Detection. IEEE Access 2020, 8, 162642–162656. [Google Scholar] [CrossRef]
- Kenney, M. Cyber-terrorism in a post-stuxnet world. Orbis 2015, 59, 111–128. [Google Scholar] [CrossRef]
- Rhysida Ransomware Leaks documents Stolen from Chilean Army. 2023. Available online: https://www.bleepingcomputer.com/news/security/rhysida-ransomware-leaks-documents-stolen-from-chilean-army/ (accessed on 3 May 2024).
- PCI Express. 2002. Available online: https://www.intel.com/content/dam/doc/white-paper/pci-express-architecture-power-management-rev-1-1-paper.pdf (accessed on 3 May 2024).
- Powercfg Command-Line Options. 2021. Available online: https://learn.microsoft.com/en-us/windows-hardware/design/device-experiences/powercfg-command-line-options (accessed on 3 May 2024).
- Singh, S.; Sharma, P.K.; Moon, S.Y.; Moon, D.; Park, J.H. A comprehensive study on APT attacks and countermeasures for future networks and communications: Challenges and solutions. J. Supercomput. 2019, 75, 4543–4574. [Google Scholar] [CrossRef]
- Muralidhara, S.; Hegde, N.; Rekha, P.M. An internet of things-based smart energy meter for monitoring device-level consumption of energy. Comput. Electr. Eng. 2020, 87, 106772. [Google Scholar] [CrossRef]
- Zhan, Z.; Zhang, Z.; Koutsoukos, X. BitJabber: The World’s Fastest Electromagnetic Covert Channel. In Proceedings of the 2020 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), San Jose, CA, USA, 7–11 December 2020; pp. 35–45. [Google Scholar]
- Guri, M. AIR-FI: Leaking Data from Air-Gapped Computers Using Wi-Fi Frequencies. IEEE Trans. Dependable Secur. Comput. 2022, 20, 2547–2564. [Google Scholar] [CrossRef]
- Guri, M. RAMBO: Leaking Secrets from Air-Gap Computers bySpelling Covert Radio Signals from Computer RAM. In Secure IT Systems. NordSec 2023. Lecture Notes in Computer Science; Fritsch, L., Hassan, I., Paintsil, E., Eds.; Springer: Cham, Switzerland, 2024; Volume 14324. [Google Scholar]
- Guri, M. Exfiltrating Data from Air-Gapped Computers via ViBrAtIoNs. Future Gener. Comput. Syst. 2021, 122, 69–81. [Google Scholar] [CrossRef]
- Giechaskiel, I.; Zhang, Y.; Rasmussen, K.B. A Framework for Evaluating Security in the Presence of Signal Injection Attacks. In Computer Security—ESORICS 2019. ESORICS 2019. Lecture Notes in Computer Science; Sako, K., Schneider, S., Ryan, P., Eds.; Springer: Cham, Switzerland, 2019; Volume 11735. [Google Scholar]
- de Gortari Briseno, J.; Singh, A.D.; Srivastava, M. InkFiltration: Using Inkjet Printers for Acoustic Data Exfiltration from Air-Gapped Networks. ACM Trans. Priv. Secur. 2022, 25, 1–26. [Google Scholar] [CrossRef]
- Kühnapfel, N.; Preußler, S.; Noppel, M.; Schneider, T.; Rieck, K.; Wressnegger, C. LaserShark: Establishing Fast, Bidirectional Communication into Air-Gapped Systems. In Proceedings of the 37th Annual Computer Security Applications Conference, Virtual, 6–10 December 2021. [Google Scholar]
- Guri, M. ETHERLED: Sending Covert Morse Signals from Air-Gapped Devices via Network Card (NIC) LEDs. In Proceedings of the 2022 IEEE International Conference on Cyber Security and Resilience (CSR), Rhodes, Greece, 27–29 July 2022; pp. 163–170. [Google Scholar]
- Schlauder, B.; Tremblay, C.; Johnson, D. CD-Blink: An External Disk Drive Based Covert Channel. In Proceedings of the 10th International Conference on Control, Dynamic Systems, and Robotics (CDSR 2023), Ottawa, ON, Canada, 1–3 June 2023. [Google Scholar]
- Guri, M. POWER-SUPPLaY: Leaking Sensitive Data From Air-Gapped, Audio-Gapped Systems by Turning the Power Supplies into Speakers. IEEE Trans. Dependable Secur. Comput. 2023, 20, 313–330. [Google Scholar] [CrossRef]
- Dileep, G. A survey on smart grid technologies and applications. Renew. Energy 2020, 146, 2589–2625. [Google Scholar] [CrossRef]
- Huge demands for Power Line Carrier Communication Chip Market 2022-Growing Rapidly with Latest Trends and Future scope. 2021. Available online: Https://www.openpr.com/news/2751815/huge-demands-for-power-line-carrier-communication-chip-market (accessed on 3 May 2024).
- Smart Plug Market. 2023. Available online: https://www.globenewswire.com/news-release/2023/02/16/2610148/0/en/Smart-Plug-Market-Size-Worth-USD-9-24-Billion-by-2030-Growing-at-a-CAGR-of-26-1-during-the-forecast-period-2023-2030-Data-By-Contrive-Datum-Insights.html (accessed on 3 May 2024).
- Smart Plug Market. 2022. Available online: https://www.grandviewresearch.com/industry-analysis/smart-plug-market (accessed on 3 May 2024).
- Rehman, A.U.; Syed, A.R.; Khan, I.U.; Mustafa, A.A.; Anwer, M.B.; Ali, U.A. IoT-enabled smart plug. Wirel. Pers. Commun. 2021, 116, 1151–1169. [Google Scholar] [CrossRef]
- Duflot, L.; Levillain, O.; Morin, B. ACPI: Design Principles and Concerns. In Trusted Computing. Trust 2009. Lecture Notes in Computer Science; Chen, L., Mitchell, C.J., Martin, A., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; Volume 5471. [Google Scholar]
- ACPI System Management Bus Interface Specification. 2021. Available online: https://uefi.org/htmlspecs/ACPI_Spec_6_4_html/13_ACPI_System_Mgmt_Bus_Interface_Spec/ACPI_Sys_Mgmt_Bus_Interface_Specification.html (accessed on 3 May 2024).
- Patent Information. 2020. Available online: https://www.163.com/dy/article/FJGROJ230511RIVP.html (accessed on 3 May 2024).
- Sun, Y.; Agostini, N.B.; Dong, S.; Kaeli, D. Summarizing CPU and GPU Design Trends with Product Data. arXiv 2019, arXiv:1911.11313. [Google Scholar]
- Zhang, H.; Yang, L.-L.; Hanzo, L. LDPC-Coded Index-Modulation Aided OFDM for In-Vehicle Power Line Communications. In Proceedings of the 2016 IEEE 83rd Vehicular Technology Conference (VTC Spring), Nanjing, China, 15–18 May 2016; pp. 1–5. [Google Scholar]
- Modulation Mode. 2022. Available online: https://baike.baidu.com/item/%E8%B0%83%E5%88%B6%E6%96%B9%E5%BC%8F/8971326 (accessed on 3 May 2024).
- Tao, M.; Guan, J.; Peng, T.; Li, S.; Yu, S.; Song, J.; Song, Z.; Gao, L.; Gao, F. Simultaneous realization of laser ranging and communication based on dual-pulse interval modulation. IEEE Trans. Instrum. Meas. 2021, 70, 1–10. [Google Scholar] [CrossRef]
- McEliece, R.J.; Sarwate, D.V. On sharing secrets and Reed-Solomon codes. Commun. ACM 1981, 24, 583–584. [Google Scholar] [CrossRef]
- Hodges, D. Cyber-enabled burglary of smart homes. Comput. Secur. 2021, 110, 102418. [Google Scholar] [CrossRef]
- Rao, A.; McIntyre, W.; Moon, U.K.; Temes, G.C. Noise-shaping techniques applied to switched-capacitor voltage regulators. IEEE J. Solid-State Circuits 2005, 40, 422–429. [Google Scholar] [CrossRef]
- Bhushan, S.; Yaduvanshi, R.S. Cylindrical Dielectric Resonator Antenna for WiFi Jammer for blocking WiFi calls at prison. In Proceedings of the 2022 IEEE 6th Conference on Information and Communication Technology (CICT), Gwalior, India, 18–20 November 2022; pp. 1–4. [Google Scholar]
- Wang, X.H.; Li, S.B.; Jiang, Y.T.; Singh, A.K.; Ma, B.Y.; Huang, L.T.; Yang, M.; Guo, F. Inaudible sound covert channel with anti-jamming capability: Attacks vs. countermeasure. J. Electron. Sci. Technol. 2022, 20, 100181. [Google Scholar] [CrossRef]
- Schloeder-EMV: Magnetic Field Generator and Analyzer. 2018. Available online: https://www.schloeder-emc.com/emc-products/emc-test-and-measurement-system/emc-generators-measurement-systems/magnetic-field-generator-and-analyzer-1.html (accessed on 3 May 2024).



















| Air-Gap Channels | Communication Medium | Sender | Receiver | Method Name |
|---|---|---|---|---|
| Electromagnetic | Electromagnetic | Memory, hard disk | Smartphone, SDR | BitJabber, AIR-FI, RAMBO |
| Sound | Ultrasound, noise, vibration | Loudspeaker, Fan, Power adapter | Mobile phone accelerometer, microphone, gyroscope | AiR-ViBeR, InkFiltration |
| Optical | Laser, Visible light, infrared light | Laser, Hard disk lamp, CD lamp, Network card light, Camera infrared light | Camera | LaserShark, ETHERLED, CD-Blink |
| Thermal | Radiation of heat | air conditioner | Infrared sensor | HVACKer |
| Power sector | Power line | Power adapter | Current transformer, smartphone | PowerHammer, POWER-SUPPLaY |
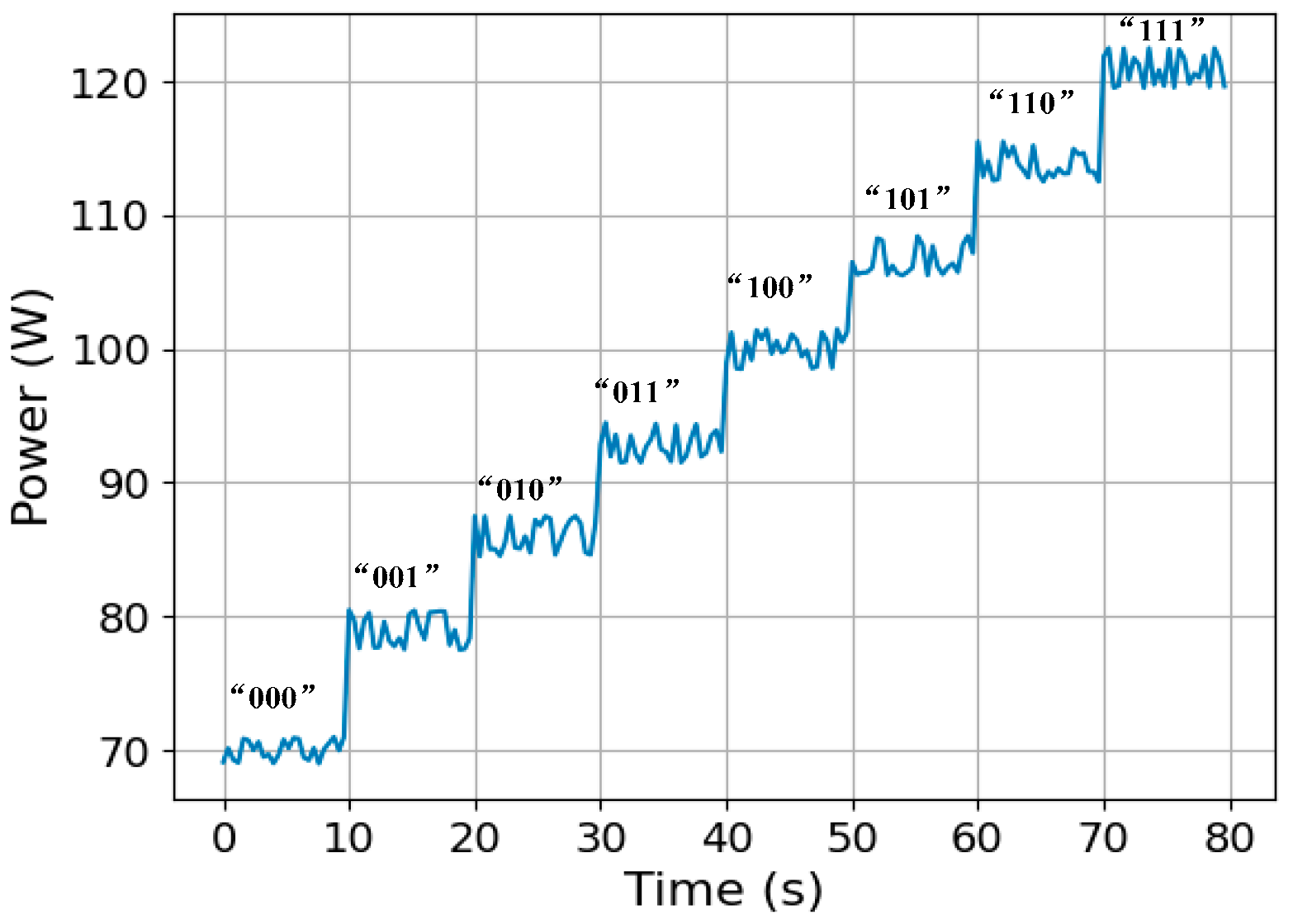
| Interval (s) | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 |
| bits | 000 | 001 | 010 | 011 | 100 | 101 | 110 | 111 |
| Transmission Mode | Sender Unit | Receiver Unit | Content of Communication |
|---|---|---|---|
| Exfiltration (leaking data from an air-gapped computer) | Power adapter for your computer | Smart plug power consumption measurement module | Small amounts of data (sensitive files, passwords, etc.) |
| Infiltration (sending data to the air-gapped computer) | Smart plug switch module | ACPI interface for the computer | Control parameter |
| Laptop Brands | Minimum Symbol Interval Time (ms) | Maximum Bit Rate (2ASK) |
|---|---|---|
| GIGABYTE AERO 15 | 33 | 33.30 bits/s |
| Lenovo X1 | 31 | 32.26 bits/s |
| Dell Precision5570 | 37 | 27.03 bits/s |
| HP Spectre X360 | 34 | 29.41 bits/s |
| Asus Pro Art Q17 | 31 | 32.26 bits/s |
| Laptop Brands | The Minimum Time Interval for the Power Adapter to Be Disconnected (s) | Maximum Bit Rate (2ASK) |
|---|---|---|
| GIGABYTE AERO 15 | 0.85 s | 1.18 bits/s |
| Lenovo X1 | 0.96 s | 1.04 bits/s |
| Dell Precision5570 | 0.81 s | 1.24 bits/s |
| HP Spectre X360 | 0.78 s | 1.29 bits/s |
| Asus Pro Art Q17 | 0.86 s | 1.16 bits/s |
| Method Name | Air-Gap Channels | Communication Capability | Infiltration Bit Rate (bit/s) | Exfiltration Bit Rate (bit/s) |
|---|---|---|---|---|
| BitJabber | Electromagnetic | Unidirectional | \ | 300,000 |
| AIR-FI | \ | 16 | ||
| RAMBO | \ | 1000 | ||
| AiR-ViBeR | Sound | Unidirectional | \ | 0.5 |
| InkFiltration | \ | 0.5 | ||
| ETHERLED | Optical | Unidirectional | \ | 100 |
| CD-Blink | \ | 1 | ||
| HVACKer | Thermal | Bidirectional | 0.011 | 0.011 |
| PowerHammer | Power sector | Unidirectional | \ | 1000 |
| POWER-SUPPLaY | \ | 60 | ||
| PowerBridge | Bidirectional | 1.2 | 33 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liang, Y.; Shan, H.; Luo, Z.; Qi, L.; Xie, Y. PowerBridge: Covert Air-Gap Exfiltration/Infiltration via Smart Plug. Appl. Sci. 2024, 14, 6321. https://doi.org/10.3390/app14146321
Liang Y, Shan H, Luo Z, Qi L, Xie Y. PowerBridge: Covert Air-Gap Exfiltration/Infiltration via Smart Plug. Applied Sciences. 2024; 14(14):6321. https://doi.org/10.3390/app14146321
Chicago/Turabian StyleLiang, Yongyu, Hong Shan, Zelin Luo, Lanlan Qi, and Yi Xie. 2024. "PowerBridge: Covert Air-Gap Exfiltration/Infiltration via Smart Plug" Applied Sciences 14, no. 14: 6321. https://doi.org/10.3390/app14146321
APA StyleLiang, Y., Shan, H., Luo, Z., Qi, L., & Xie, Y. (2024). PowerBridge: Covert Air-Gap Exfiltration/Infiltration via Smart Plug. Applied Sciences, 14(14), 6321. https://doi.org/10.3390/app14146321






