1. Introduction
Privacy and the right to keep private information confidential are key issues facing computer security experts. There are always attempts from unauthorized individuals to access information and data for various reasons, whether for the mere reason of prying into people’s private affairs or for hacking attempts to cause damage. Regardless of the motives, computer security experts are constantly developing innovative techniques to encrypt and hide data so that even if it falls into the wrong hands, they will be able to neither decrypt nor see where the data are hidden. Steganography refers to hiding secret information or messages in multimedia objects using complex mathematical techniques in a way that does not show that information is being hidden. It is usually referred to as the technology and science of choice involving communicating secret data in different types of appropriate multimedia carriers such as audio, text, video, or image [
1]. Though the field of cryptography has matured considerably, sometimes even the presence of a secret message is not desirable to prevent interception and possible decryption. While many do not differentiate between cryptography and steganography because both are used for sending secret messages, the distinction between these is very clear. Steganography refers to the process of concealing a secret message in a cover image so that it has no meaning except to the intended receiver, while cryptography converts the secret text message to an unreadable format [
2].
The most common techniques for hiding messages are steganography and watermarking. However, invisible messages can only be sent through the steganography methods. In steganography, the messages are hidden in other forms of media, which are called carriers or covers. The media used as cover could be audio, text, or an image file. In this paper, carrier media will be referred to as a cover image since image files will be used as the carrier. The hidden secret will be called “payload,” and a payload embedded in a cover image will be called a stego image throughout this paper. To judge a good stego image, the statistical properties must stay intact so that the secret message is ensured to stay hidden. Only the receiving end should be able to detect the hidden message. Among the many existing steganography techniques, least significant bit (LSB) has been the most widely used and researched method.
Medical Health Records are considered highly private data and must be protected from unauthorized user access. Patient confidentiality entails that only authorized physicians and medical personnel have access to such records. Many hospitals and medical institutions use medical health record systems. However, even these systems can be susceptible to hacking and other vulnerabilities that could result in patient data becoming available to unauthorized users. Thus, as an additional precaution, we also propose a method to hide the text-based portions of medical health records within medical images. Therefore, even if an unauthorized user accesses the file, they will only be able to see a medical image with no identifying marks or text-based health records to indicate the personal information of the patient. Overall, the objective of the proposed technique is to generate an embedded image that is the original one since a minor part of the pixel values will be changed. Consequently, neither decryption algorithms nor bare eyes can identify or detect any change in that stego image color and its cover image.
In this paper, we propose a novel method in which the original text document is first encrypted, and then the document is fragmented into several documents, each containing a portion of the original document that is not comprehendible on its own, even if detected and decrypted. A key generator is proposed to randomly select medical images from the patient’s file according to the number of files generated from the fragmentation. These portions are then embedded into the images using the proposed novel steganography method. The defragmentation information, decryption key, and selection key are each sent to the recipient in a separate communication. This ensures that the recipient can identify the stego images, reconstruct the order of the embedded documents, and then decrypt them accurately. The additional layers of security make the proposed technique resilient to data privacy attacks. The proposed method is also proven to be robust and impermeable to repeated attacks.
The rest of the paper is organized as follows.
Section 2 provides an overview of the work related to concealing and revealing hidden information using steganography.
Section 3 describes the proposed methodology.
Section 4 details the experimental setup and performance results.
Section 5 concludes the paper and presents future work.
2. Recent Studies
In ref. [
3], the authors present an image steganography technique based on framelet transform to hide secret images in the cover image. Application of various steganalysis techniques showed poor detection accuracy, while visual properties and quality were better and more robust. In [
4], the authors presented a review of both steganography and cryptography techniques and proposed a combined hybrid system that utilized the strengths of both techniques. The authors conclude that a hybrid system consisting of both concealed cryptographic messages using steganography will be more secure than using each one individually. In ref. [
5], the authors propose a cloud-based reversible dynamic steganography technique for embedding pathological reports into medical images. The technique is based on dividing the image into five sub-regions, and a secret key generator is used to randomly select one of the sub-regions for hiding the pathological reports. The key is communicated to the receiving end through other means so that it can be used to extract pathological reports from the images. The quality of the image was intact, which was also shown through the analysis of the mean square error (MSE) and peak signal-to-noise ratio (PSNR) metrics.
In ref. [
6], the authors proposed a new way for steganography to be applied to medical images using LSB. This technique is based on the Local Binary Pattern (LBP). They divided the cover images into several non-overlapping patterns. The LBP operator is utilized to identify pixel embedding positions, while the LBP values are employed to determine the method and location for embedding the secret image pixel. The LSB method is used to embed the secret message within the cover image pixels. The method was evaluated using MSE and PSNR, demonstrating improved efficiency. In ref. [
7], the author proposed a method that utilizes deep neural networks to hide and reveal hidden information via steganography. The method does not use LSB but rather compresses and distributes the secret data (image) representation across all of the available bit pixels. In ref. [
8], the authors propose a coverless image steganography method using scale invariant transform and a set of features. The authors claim that their method transmits natural images that have the concealed information and yet have the same features as the secret data to the receiver. In their method, the secret data are converted into a bitstream. An inverted index is used to send the images with concealed data. Their proposed method resists steganalysis tools since the original image is never modified. In ref. [
9], the authors proposed an image steganography technique for images sent over social media. They take the channel-compressed version of the image and conceal data in the compressed image using any JPEG stenographic method, thus producing the stego image. The coefficient adjustment method is then applied to the stego image for minor modification while still maintaining the image to stay the same as the stego image. On the receiving end, secret data are extracted with 100% accuracy.
In ref. [
10], the authors proposed a method based on generative adversarial networks for generating secure and suitable covers for steganography. One generative network and two discriminative networks are used in the proposed method. The generative networks check the visual quality, while the discriminative networks check the technical suitability of the images for data hiding. Improved convergence speed, image quality, and training stability are reported. The method was tested and found to be effective and robust. In [
11], the authors propose a steganographic technique based on object detection and relationship mapping using coverless data hiding and steganography. Using object detection, the object color, type, and secret messages are mapped, and suitable locations are identified to hide the secret messages. In ref. [
12], the authors proposed a medical JPEG image steganography method using dependencies of interblock coefficients. Their method has the objective of keeping the difference among the discrete cosine transform (DCT) coefficient at the same position in neighboring blocks as much as possible. Their method was proven effective and robust. In ref. [
13], the authors proposed a steganography method using a new operation adversarial embedding (ADV-EMB) for embedding secret messages in the cover image and proving robustness against Convolutional Neural Network (CNN) steganalysis.
In ref. [
14], the authors proposed a method for creating a stego image without altering the cover image. Instead, they proposed using partially identical sets of secret images as stego images, which can be obtained from a natural image dataset. Essentially, they have a dataset of natural images, and when they want to embed a secret message, they search the dataset for images that contain partial duplicates of the secret image while the receiving end uses the patches to recover the secret message. This approach can approximately recover secret messages but is still resistant to steganalysis tools. In ref. [
15], the authors proposed a method to embed the secret message in quantized DCT coefficients of the JPEG file through the addition of the independent realizations of the heteroscedastic noise to pixels to make the stego image resemble the cover image. In ref. [
16], the authors proposed a channel-dependent payload partition strategy using amplification of channel modification probabilities, thus embedding adaptive capacity. The modification probabilities of the RGB channels are increased all at once, and thereby, embedding could be clustered. This method achieved better performance against color image steganalysis techniques.
In ref. [
17], the authors proposed a secure image steganography framework using the stego key-directed adaptive LSB (SKA-LSB) substitution technique as well as multilevel cryptography. Two-level encryption is used to encrypt the stego key, while the secret message is encrypted using multilevel encryption. Adaptive LSB is then used to embed the encrypted message in the cover image. The method was proven to be effective in maintaining visual image quality and security. In ref. [
18], the authors proposed a bit-flipping technique for hiding secret data in a cover image. Blocks are divided into two pixels, and thus, they flip one or two LSBs of the pixel in order to conceal information. The method achieved good results in PSNR, Quality Index (Q.I), and hiding capacity. In ref. [
19], the authors investigated three quantum color image steganography techniques based on LSB. The first method uses only one channel to conceal data. The second is based on the LSB XORing Method, and the last uses two channels to conceal data. MATLAB is used to analyze the schemes. Acceptable performance was achieved by analyzing the metrics such as PSNR and Histogram graphs. In ref. [
20], the authors proposed a steganography method that is a combination of both edge detection and XOR coding, which is used to hide data in the Integer Wavelet Transform (IWT) or spatial domain of the cover image. Better imperceptibility and security against the texture feature steganalysis method were achieved.
In ref. [
21], the authors proposed a technique that is a combination of steganography, cryptography, and watermarking, which they dubbed as Next Gen. The patient’s information was encrypted initially, and then steganography and watermarking techniques were used for authenticity using LSB methods. The results were a good tradeoff between payload, security, and visual characteristics. In ref. [
22], the authors proposed a steganography method to increase the payload. Their method relies on the similarity between pixels. Different metrics, including MSE and PSNR, were used for testing. They were able to hide 10,000 characters in 256 × 256 images without using compression techniques. In ref. [
23], the authors enhanced medical record security by proposing the use of 3DES and LSB. Java programming was used as the tool, and results showed good security and reliability. In ref. [
24], the authors proposed a steganography technique using a Bit Invert System (BIS) with three control random parameters. The Henan Map Function (HMF) is used to make random selections. Both the Huffman Method and Affine Cipher are used for encryption as an added security measure. The method showed good security while maintaining image quality.
In ref. [
25], the authors presented various techniques to preserve the security and integrity of medical images using both steganography and watermarking, as well as the use of images for authentication. In ref. [
26], the authors presented a review of remote user authentication methods used in healthcare to ensure that medical records are accessed by only authorized persons. They also propose a three-layer authentication method for use in healthcare. In ref. [
27], the author proposed a method for the security of Electronic Health Records (EHRs) in a cloud-based environment. Biometric images are proposed for a unified identification across cloud environments. The proposed method is based on watermarking and encryption. The method was impermeable to repeated attacks. In ref. [
28], the authors presented the importance of security in telemedicine as many medical services can now be offered remotely. They present a complete system for home care medical services while ensuring security and integrity. In ref. [
29], the authors propose an optimized bias correction method that integrates both the variational denoised term and pre-piecewise fitting function into the energy function for low-contrast and low-intensity inhomogeneity images. They reported superior results for prime ACMs and deep learning methods in image segmentation.
Medical images contain vital data that are used for diagnostics, so the image quality and image characteristics must be ensured to keep the vital information in the images intact. Otherwise, this might cause misdiagnosis. For example, medical images contain vital information for cancer diagnosis or other medical conditions [
30,
31], and these are just a few examples of the importance of medical images in diagnosis. Therefore, any proposed method for steganography must ensure that the vital image characteristic remains unchanged or at least ensure medical personnel use only the original cover image for diagnosis purposes.
3. Materials and Methods
In this paper, we propose a secure steganographic technique that involves distributing ciphertext across multiple digital images.
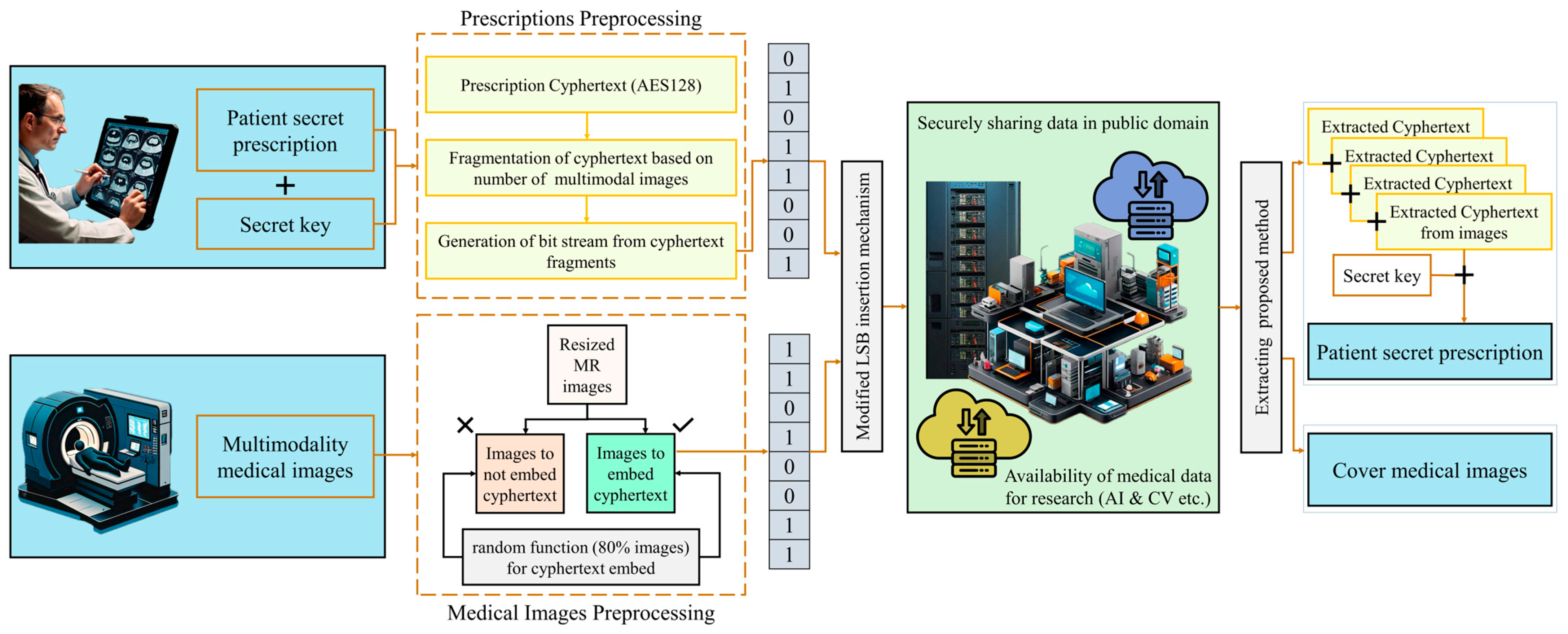
Figure 1 illustrates the system model of the proposed technique for securely sharing medical image data along with patients’ prescriptions for research purposes. Initially, the plaintext (patient information and/or prescription) is encrypted using 128 bits key based advanced encryption standard algorithm (AES128) to generate the ciphertext. The latter is then divided into segments, each of which is embedded into a distinct image chosen from a predetermined set of the patient’s medical images. The selection of images for embedding is performed in a random fashion, a strategy that is crucial to enhancing data security. This random distribution has the advantage of obscuring the presence of the steganographic content, making it difficult to detect without specific knowledge of the selection process and the associated key. During the data recovery phase, the segments are extracted from the sequence of images, reassembled, and eventually decrypted to retrieve the original plaintext. This approach ensures that the data confidentiality and integrity are sustained from the point of encryption to decryption, making it suitable for sensitive communication scenarios. Additionally, this method would not affect the image quality, so images are still useful for diagnosis using AI techniques or manual diagnosis methods.
3.1. Dataset Description
This research introduces an efficient method to securely send medical images with patient personal information and physician prescriptions embedded inside images without degrading the image quality through the use of a novel steganography technique. The proposed method is applied by hiding texts inside Brain MRI scans. Therefore, in this research, we utilized two datasets: one containing digital images and another containing text files. The first dataset consists of 3255 MRI scans of 21 patients, each having 155 slices of Brain MRI Flair scans. The dimensions of each of these images are 240 × 240 grayscale, and they are saved in PNG format. The Brain MRI dataset was acquired from the MICCAI BraTS, which was introduced as a competition in the MICCAI (Medical Image Computing and Computer-Assisted Intervention) conference in 2012 [
32,
33,
34,
35]. The data have been updated and revised multiple times, including in 2015 and 2020. The MRI scans in this dataset include multiple imaging modalities: T1-weighted, T1-weighted with contrast enhancement (T1c), T2-weighted, and Fluid Attenuated Inversion Recovery (FLAIR). These images are preprocessed to a uniform resolution. The second dataset contains plain text files of sample patient personal information and physician prescriptions. The size of those text files ranges from 300 to 5000 characters.
Figure 2 shows MRI sample slice sets for different patients acquired from the first dataset, while
Table 1 and
Table 2 show the sample patient information and a prescription that will be hidden inside MRI scans.
3.2. Least Significant Bit (LSB) Steganography
In computers, an image is defined as a group of gathered numerical values that create many light intensities in different regions of that image. These numerical values in bits represent a form of individual points, which are called pixels. In steganography, techniques and algorithms can be classified into two main categories: the first category is the image domain, while the second is the transformation domain. In the image domain, which is also known as a special domain, people use techniques to directly encrypt messages in each pixel intensity before the transformation is complete. In the transform (frequency) domain, people use techniques by transforming the images first and then encrypting the message inside the transformed images [
10]. However, manipulation is necessary in these two methods, especially when spatial techniques are utilized. Also, there are many useful methods within the spatial domain technique itself. For example, the least significant bits (LSB) substitution technique, Exploiting Modification Direction (EMD), and Pixel Value Differencing (PVD). In addition, DWT, FFT, and DCT techniques are the most well-known methods in the transform domain.
In this research, we utilized the LSB substitution technique, which is one of the most important techniques applied in steganography in the image domain. Overall, the objective of this technique is to generate an embedded image that is the original one since a minor part of the pixel values will be slightly changed. Therefore, neither machine learning nor bare eyes can identify or detect the change in that embedded image color and its original one [
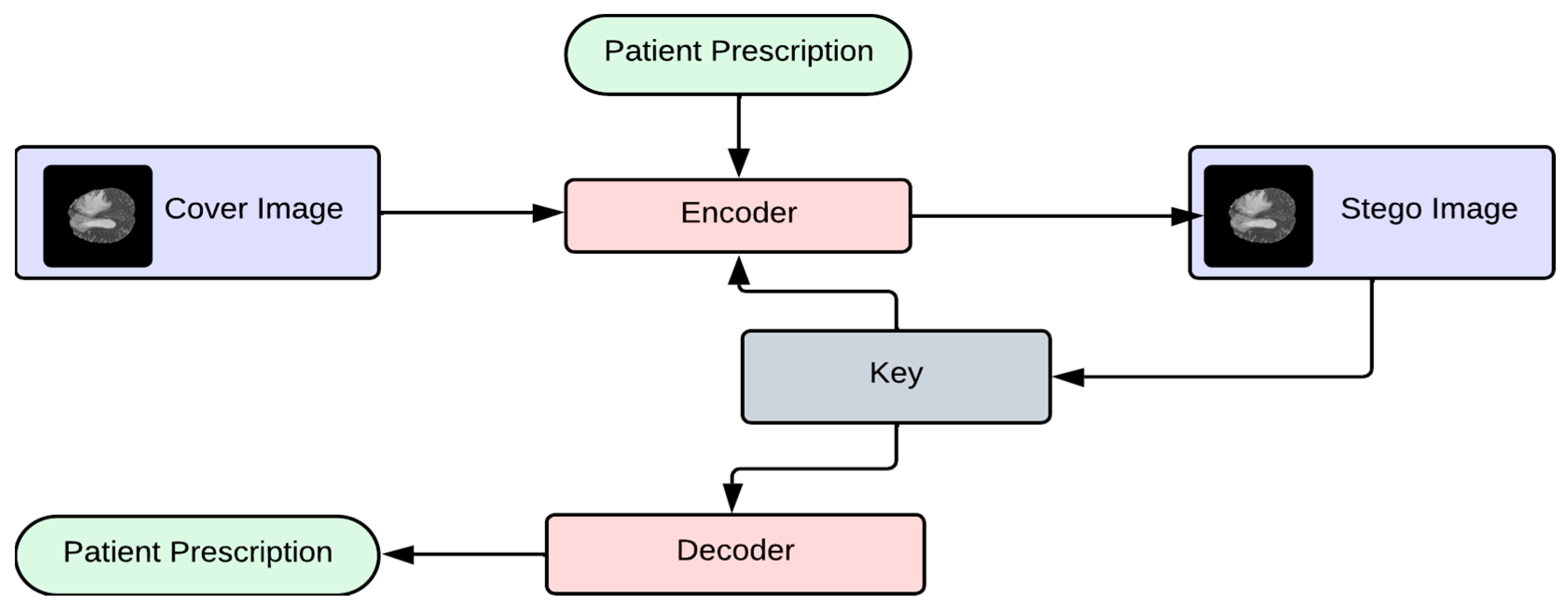
14]. Image steganography consists of two phases: the embedding and extracting phases.
Figure 3 shows a basic block diagram of the embedding phase and extracting phase of LSB-based steganography.
As stated earlier, hiding private information inside different types of digital images is known as the LSB steganography method. The idea of image steganography is very simple and basic. Digital images consist of pixels, and each pixel shows a certain color intensity of that particular region of the original image. In a black-and-white grayscale picture, the pixel’s amount of gray color ranges between 0 and 255 shades. Zero represents a black, and 255 represents a white color. The idea of the LSB data encrypting method is used for the least significant bit of each pixel. The main goal behind LSB planting is that if we replace the last pixel’s value, no visible change should appear in the original picture. For example, a grayscale image has 256 shades of gray color. If 0 is black and we change it into 1, then it means the pixel is still black, but we make it a little bit lighter, i.e., the shade has been changed, not the color, making it almost impossible to be detected.
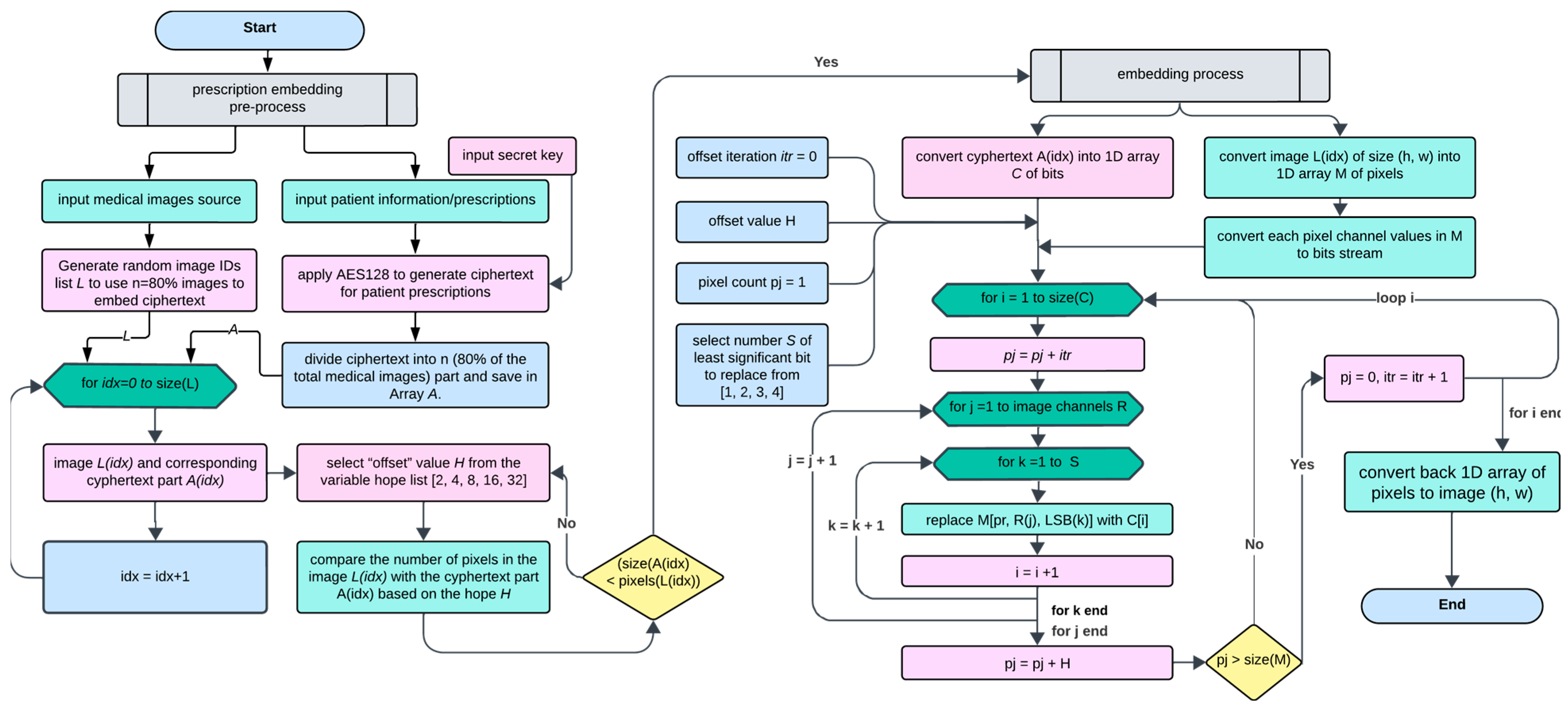
3.3. Proposed Modified LSB Embedding Process for Medical Images
The process that is needed to hide a secret message in a cover image to generate a new image is called the embedding process. When any information is hidden, there is a stego-key, which could come in different forms, such as a password or face recognition for more security measures. The output of hiding a secret message inside a cover image is called stego-image or stego-object. The following are the proposed steps for the securely embedding phase of the patient’s prescription text to the medical images.
- Step 1:
The patient’s confidential text-based information is encrypted using a well-known encryption algorithm (e.g., AES128) with the secret key (password) to generate the ciphertext.
- Step 2:
The ciphertext document is fragmented into several documents, each containing a portion of the original message, which is not comprehendible on its own, even if it is detected and decrypted.
- Step 3:
Typically, 100 to 180 medical images (CT/MRI/Ultrasound) are captured for analysis of a particular human brain; therefore, only selected medical images are used to embed the cipher text instead of using all medical images, which makes it more challenging to find the images with the patient information.
- Step 4:
A key generator is proposed to randomly select the medical images for a patient according to the number of files generated from the fragmentation.
- Step 5:
Each fragmented cipher text is embedded into the corresponding image using the modified LSB insertion mechanism with an offset value.
Cyphertext part will be converted into a 1D array of bits;
Corresponding image (h, w) will be converted into a 1D array of pixels;
Each pixel channel value of the image will be converted into bits;
Value for the number of LSB bits to replace will be selected from [1, 2, 3, 4];
Pixel offset value will be chosen from the list [1, 2, 4, 8, 16, 32];
Based on the pixel offset value, the pixel will be skipped for LSB replacement and will be repeated with offset iterations until all cyphertext bits are embedded in the image;
The 1D pixels array will be converted back to the image (h, w).
As shown in
Figure 4, the system starts with a user entering a secret key, which, upon validation, allows the choice of either embedding or extracting text. For the embedding route, medical images and patient information are input, with the latter being encrypted into ciphertext using AES128. This ciphertext is then divided and distributed across various medical images to ensure discrete embedding. The system uses an offset value from a predefined list to determine the embedding intervals within the image pixels to ensure that each image has enough pixel capacity to embed the ciphertext. The flowchart also includes a checkpoint to verify the image’s capacity to hold the data segment before proceeding with the embedding, which, upon completion, yields a stego-image that securely conceals the information for transmission.
The LSB insertion mechanism consists of randomly inserting the hidden text bits within the image to be verified by the offset. This mechanism applies to every bit to embed the hidden message into 8 pixels. The secret of this operation is the offset number or hop number, which is basically the power of two (2, 4, 8, …32). For instance, when the offset is (4), the processor will plug in the first bit in byte number one, the next bit in byte number five, and the third bit in byte number nine. When a particular image end is reached, the loop will start back from byte two to six, then ten, and so on. The randomization aspects ingrained in this process ensure more secure data embedding within the image. The proposed method is not merely a technical procedure but a precisely orchestrated process that enhances data security while maintaining image fidelity.
Algorithm 1 presents the steps of the proposed modified LSB embedding process for medical images. The process for embedding encrypted data into an image starts by converting the ciphertext into a one-dimensional array of bits (C) and the image into a one-dimensional array of pixels (M), additionally breaking down each pixel’s color channels into a bit stream. A selection is made for the number of least significant bits (LSBs) to replace in the image pixels to embed the encrypted data, offering a choice from one to four bits. The embedding process iterates over the size of the ciphertext, incrementing the pixel position (pj) by an offset iteration (itr) each time. For each bit of ciphertext, the corresponding LSBs in the RGB channels of the pixel at position pj are replaced with the ciphertext bits, advancing through the image’s channels and the selected number of LSBs. If the pixel count exceeds the size of the array of pixels (M), the pixel count resets, and the offset iteration increases to ensure a comprehensive and evenly spread embedding. After the embedding is complete, the modified one-dimensional array of pixels is converted back into an image with the original dimensions (height h, width w), now containing the hidden encrypted information.
| Algorithm 1: Proposed Modified LSB Embedding Process for Medical Images |
|
Input: |
| patient_info //patient’s confidential text-based information (string) |
| secret_key //secret key (password) for encryption (string) |
| medical_images //list of medical images (CT/MRI/Ultrasound) |
| num_fragments //number of fragments to create from the encrypted data |
|
Output: |
| watermarked_images //modified medical images |
|
Steps: |
|
ciphertext = encryt(patient_info, AES128) |
|
fragments = subStrings(ciphertext, num_fragments) |
|
selected_images = random(medical_images, num_fragments) |
| lsb_replace = 2 //LSB to replace from [1, 2, 3, 4] |
| pixel_offset = 4 //pixel offset value from [1, 2, 4, 8, 16, 32] |
|
|
for
each fragment f in fragments do |
| fragment_bits = reshape(binary(f),-1)//1D reshape |
|
img = selected_images[index(f)] |
|
h,w = shape(img) |
|
image_pixels = reshape(img,-1) |
|
pixel_bits = binary(image_pixels) |
|
bits_inPixel = length(pixel_bits(1)) |
|
counter c = 0 |
|
counter j = 0 |
|
|
for
i= 1; i<length(fragment_bits); i++ do |
|
pixel_bits(c, bits_inPixel-1)= fragment_bits(i) |
|
i = i + 1 |
|
pixel_bits(c, bits_inPixel)= fragment_bits(i) |
|
c = c + pixel_offset |
|
|
if c > length(pixel_bits) then |
|
j = j + 1 |
|
c = j |
|
end if |
|
end for |
|
|
image_pixels = int(pixel_bits) |
|
img = reshape(image_pixels, [h,w]) |
|
watermarked_images.append(img) |
|
end for |
| return watermarked_images |
3.4. Proposed Modified LSB Extracting Process for Medical Images
The embedded information extraction process involves retrieving the hidden message from the stego object. To extract an embedded message from a stego image, we use a method known as extraction. This concept originates from cryptographic techniques, though there are certain differences when it comes to breaking the steganographic framework. In the context of creating and transmitting the stego object over an assumed ideal communication channel, we rely on a decoder circuit equipped with two inputs, a secret key for extraction and the cover image, to unveil the hidden message within the stego object. This decoder circuit outputs a single piece of data, the concealed text.
This extraction process involves several steps performed in reverse order, starting with manipulating the LSB of the stego image, as shown in
Figure 5. Following this, the encrypted text is retrieved in byte form, culminating with the final stage of AES128 decryption. The images that contain the embedded ciphertext are converted to a one-dimensional array of pixel values, from which bits are extracted according to a specified pattern determined by the embedding process. These bits are then assembled to form the ciphertext array. Once the complete ciphertext is extracted and converted from its bit representation, AES128 decryption is applied to decipher the original text, which contains sensitive information, such as patient prescriptions. This marks the completion of the extraction process, successfully retrieving the encrypted data without visibly altering the image, thereby maintaining confidentiality.
4. Results and Discussion
Several experiments were performed using the proposed method with the datasets described in
Section 3.1. The robustness of the original and stego images was measured through the calculation of the PSNR. The PSNR value indicates the quality of the stego image in comparison to the original cover image; a higher PSNR value suggests a higher quality stego image that closely resembles the original, while a lower PSNR value indicates a lower quality stego image with more noticeable differences from the original. The MSE is required for the PSNR calculation, which is determined using Equations (1) and (2).
where “
I” is the original image and “
I′” is the stego image. The highest achievable value of the original image is designated
Imax.
The structural similarity between the original and stego images is assessed using the structure similarity index measure (
SSIM) metric and multi-scale
SSIM (MS-SSIM). The SSIM is calculated between the original image (
I) and the steganographic image (
), which have the same dimensions of M × M pixels size based on the contrast (
c), structure (
s), and luminance (
l) using Equation (3).
where
is the mean of
and
is the mean of
, while
and
are variance of
and
, respectively.
is the covariance of
and
. Two stabilizer variables are used as
and
, which are calculated based on the maximum pixel value multiplied by constant values (0.01 for
and 0.03 for
). The SSIM value closer to 1 indicates a higher level of similarity between the images, while a value closer to 0 indicates a lower level of resemblance between the images. MS-SSIM is an advanced variant of SSIM that evaluates image quality at multiple scales through a progressive down-sampling process, mirroring the multiscale processing mechanisms in the early visual system. This approach enables MS-SSIM to perform equally well or even better than SSIM, particularly when assessing the quality of multimodal images.
Table 3 shows the results of the proposed steganography method using patient prescription text of various sizes, between 100 and 5000 characters, embedded into randomly selected medical images along with different LSB bits. The high values of PSNR indicate that the hidden message is highly imperceptible, and there is a high similarity between the stego image and the original.
Table 4 shows the comparison results based on the average PSNR, MSE, SSIM, and MS-SSIM of the proposed steganography method using prescription text of various sizes between 100 and 5000 characters for all patients’ multimodal images. Again, the high values of PSNR indicate that the hidden message is highly imperceptible, and there is a high similarity between the stego image and the original. SSIM values in
Table 4 show that all SSIM values are close to 1, indicating that the stego image and original image are almost identical. The MSE value closer to 0 indicates that the stego and original images are almost identical in a pixel-by-pixel comparison.
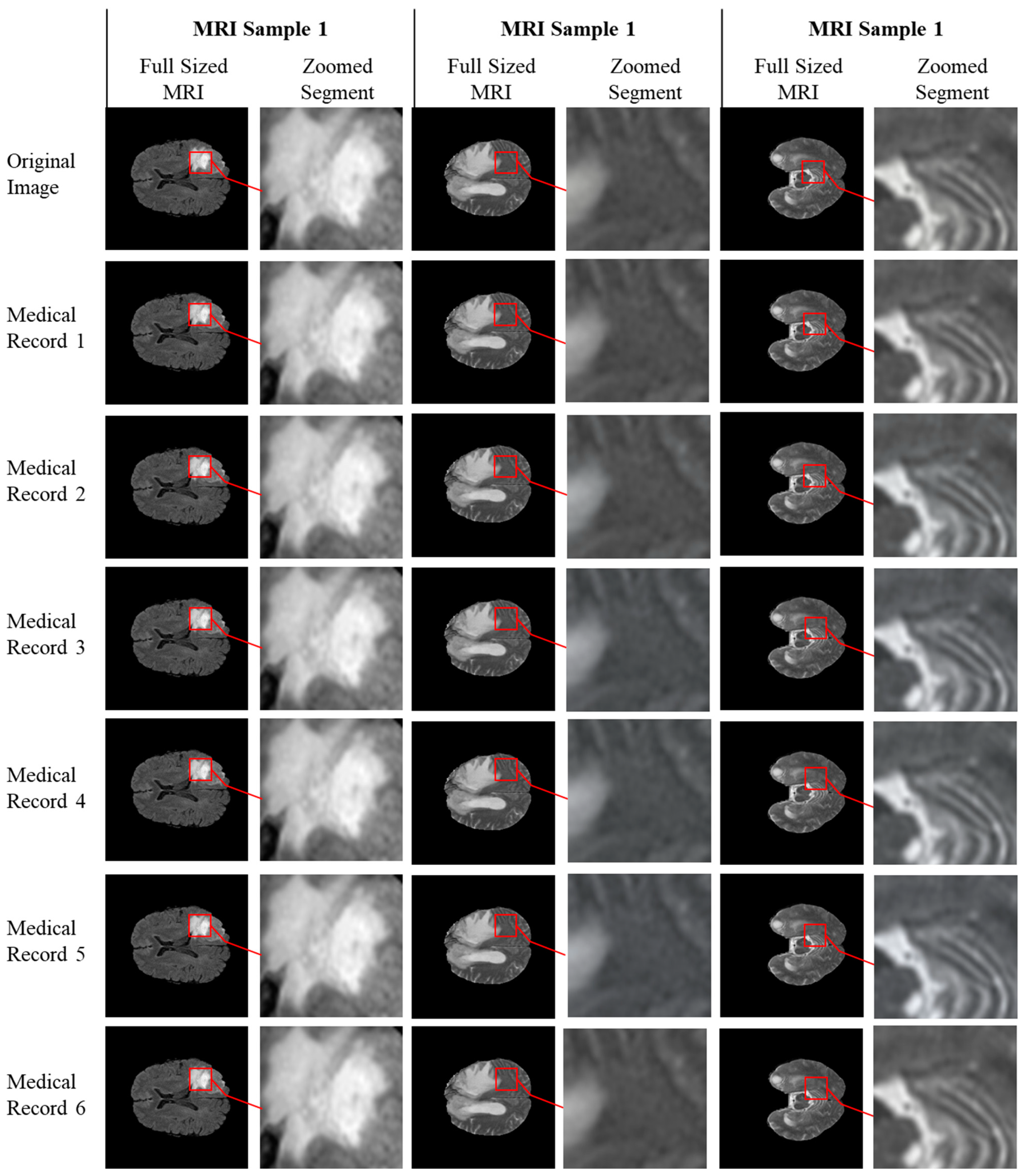
The degree of imperceptibility can be evaluated by visually inspecting the quality of the stego image.
Figure 5 shows the original and stego images with different patient prescriptions hidden ranges in text size between 100 characters and 5000 characters. Visual examination clearly shows that the structure of the original image is preserved even after hiding the text.
Figure 6 shows the SSIM values for 21 patients’ images hidden with perception with various character sizes. It is observed that when running the experiment for multiple patients and various character sizes of prescription, the SSIM values were almost 1, indicating that the original image and the stego image are almost identical. With medical images being used for medical diagnosis, the fear is that the hiding of information and altering the image may somehow affect the quality of the image for diagnosis. Nowadays, research is being performed on using deep learning models to aid physicians in the automatic diagnosis of medical conditions based on medical images. The ultimate test of a proposed steganography method is to prove that the image quality will not jeopardize the diagnosis process for patients, which is a serious matter. For this purpose, we used a Residual Network (ResNet) Convolutional Neural Network (CNN) model proposed in [
36] for the automatic detection of brain tumors. We executed this approach on the original and stego images. If the results are excellent, then this would indicate the stego image is highly similar to the original image and will not affect the diagnosis process. Several metrics, such as accuracy, precision, recall, and F1-measure, are used to measure classification fidelity.
Table 5 shows that the accuracy of diagnosis using the original image is 97.62% and that the accuracy after hiding 100–5000 characters never decreased below the accuracy using the original image. This clearly indicates that the structure of the original image was preserved and will not affect the diagnosis process negatively. Other results of precision, recall, and F1-measure indicate the same result when comparing the value for the original image and the stego image with different character sizes hidden.
The proposed system achieves a high level of security for several reasons. The transfer of the stego-image occurs without the need for the original image, enhancing system security by minimizing the impact of the actual image on security measures. The proposed system’s security architecture is layered, featuring multiple stages of protection. This means that if an external entity compromises the stego-object’s original copy, a secondary layer of security is in place. This layer significantly complicates the task for attackers attempting to decrypt the embedded text within the image, making the analysis of the ciphered text nearly impossible. In the proposed system, the complexity of the cipher key directly influences the system’s security. This particular security measure is distinct from the first two layers and involves a unique set of security considerations not apparent through conventional techniques. This layer significantly enhances the system’s robustness and overall security.
In the proposed system, steganography is designed to complement cryptography rather than replace it. Encrypting the message adds an additional layer of protection, decreasing the likelihood of the text being detected. The system incorporates a secret key that must be exchanged between the parties involved in the transmission. This exchange does not necessitate any knowledge of the extraction process or the details of the original cover image. The capacity for embedding information within the cover image is determined by its statistical properties. Regardless of the size of the embedded text, the proposed system achieves rapid extraction speeds without affecting the overall performance.