Intelligent Transportation System Technologies, Challenges and Security
Abstract
1. Introduction
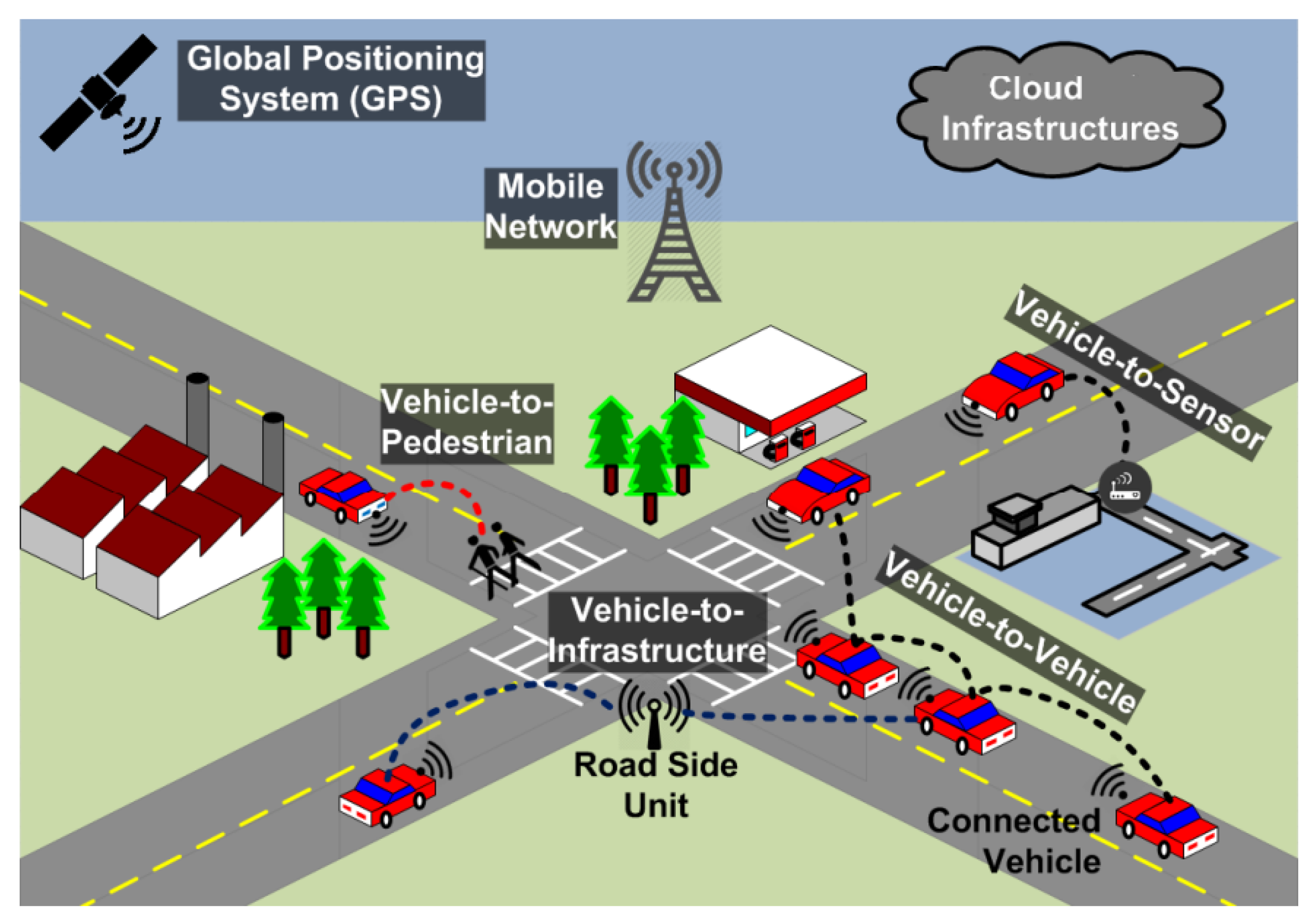
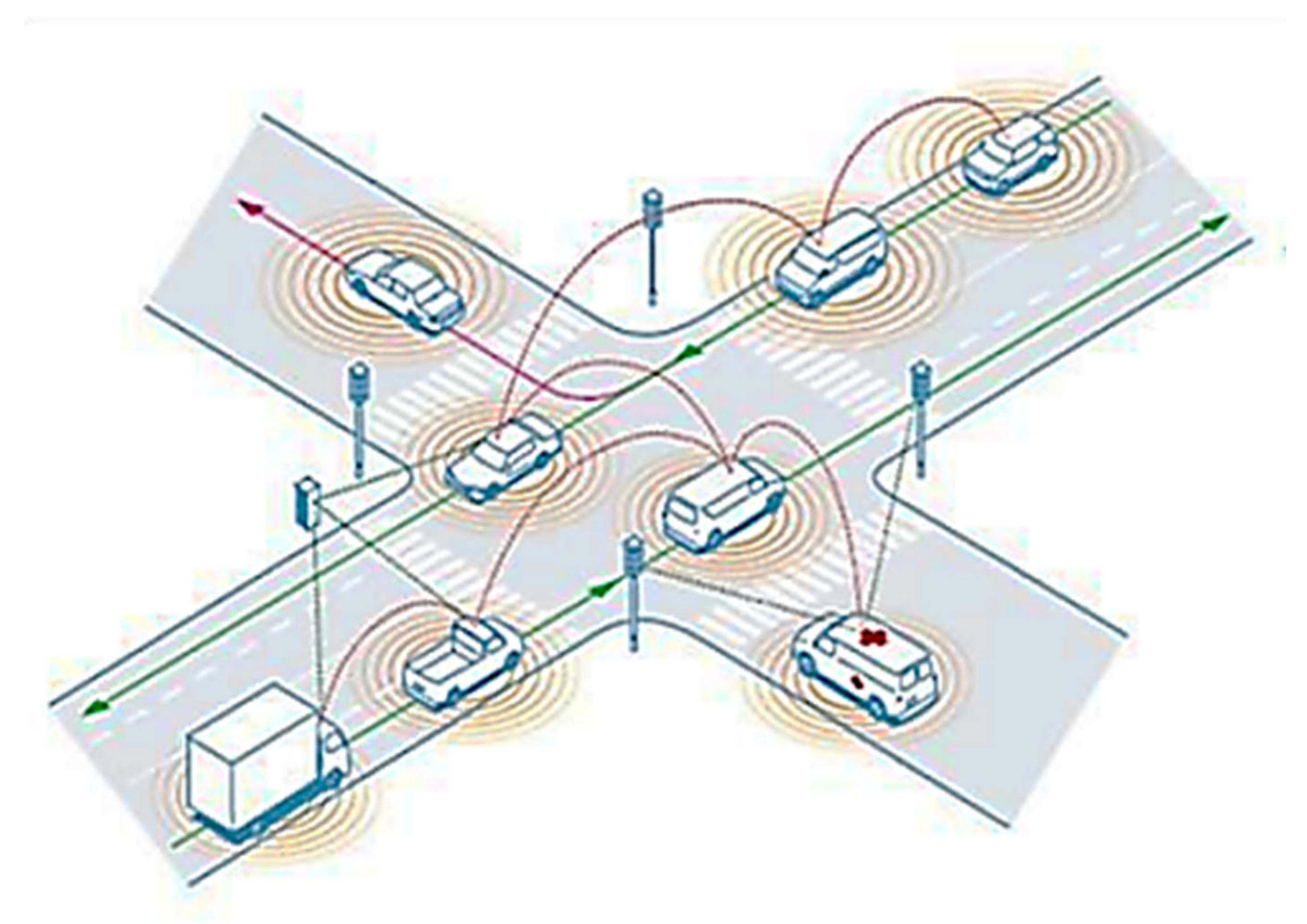
2. Intelligent Transportation Systems
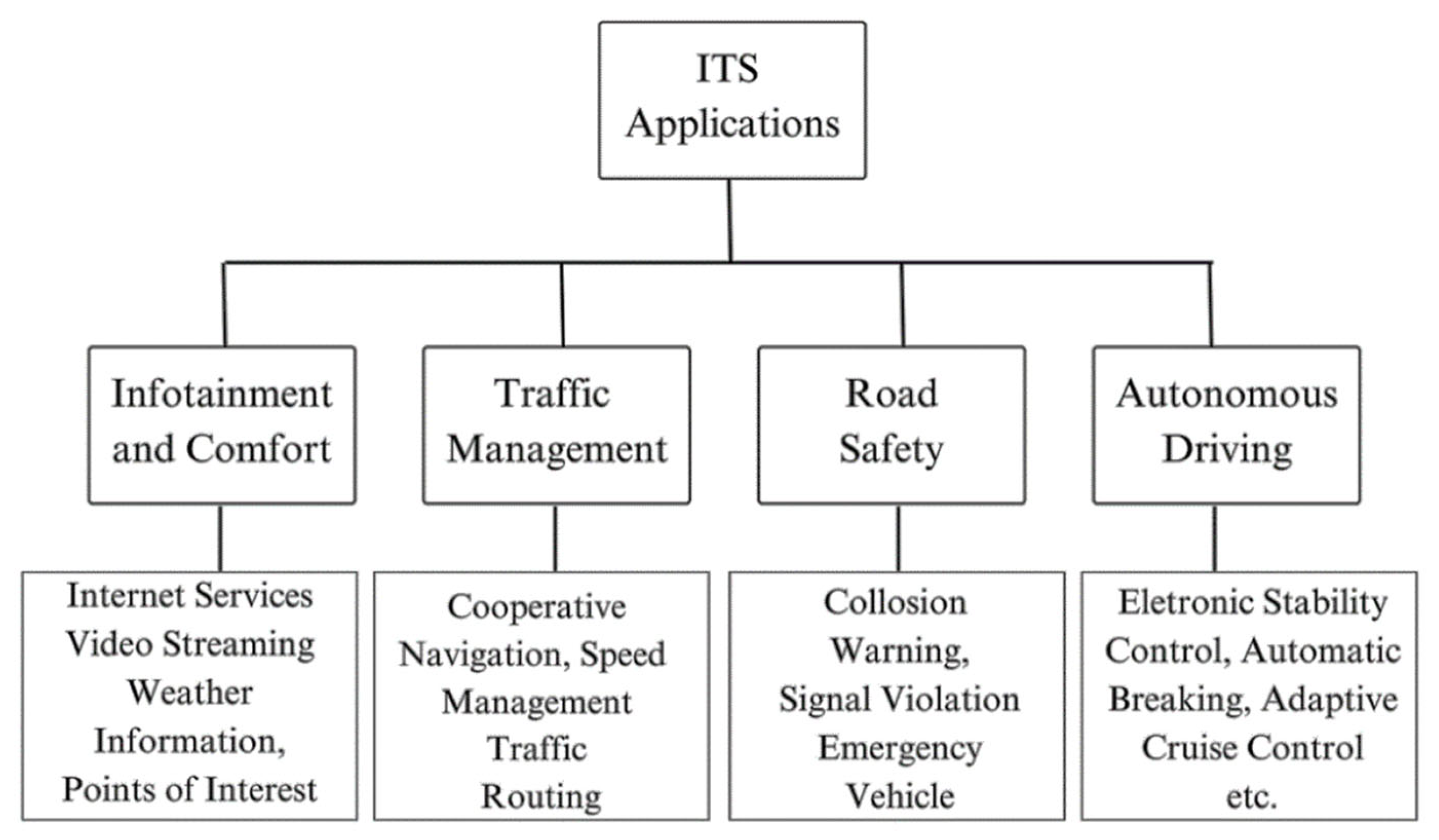
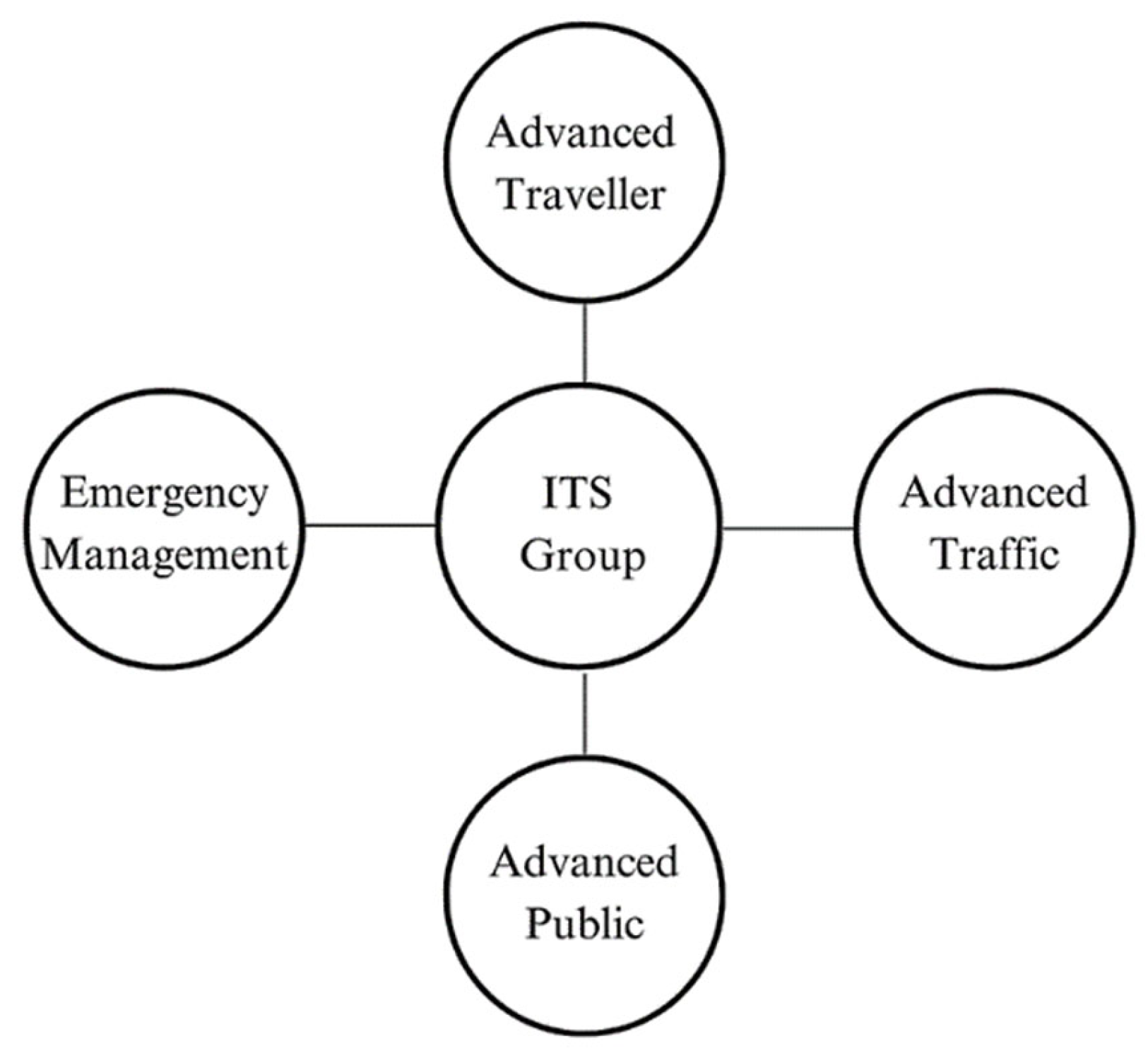
2.1. Intelligent Transportation System Applications
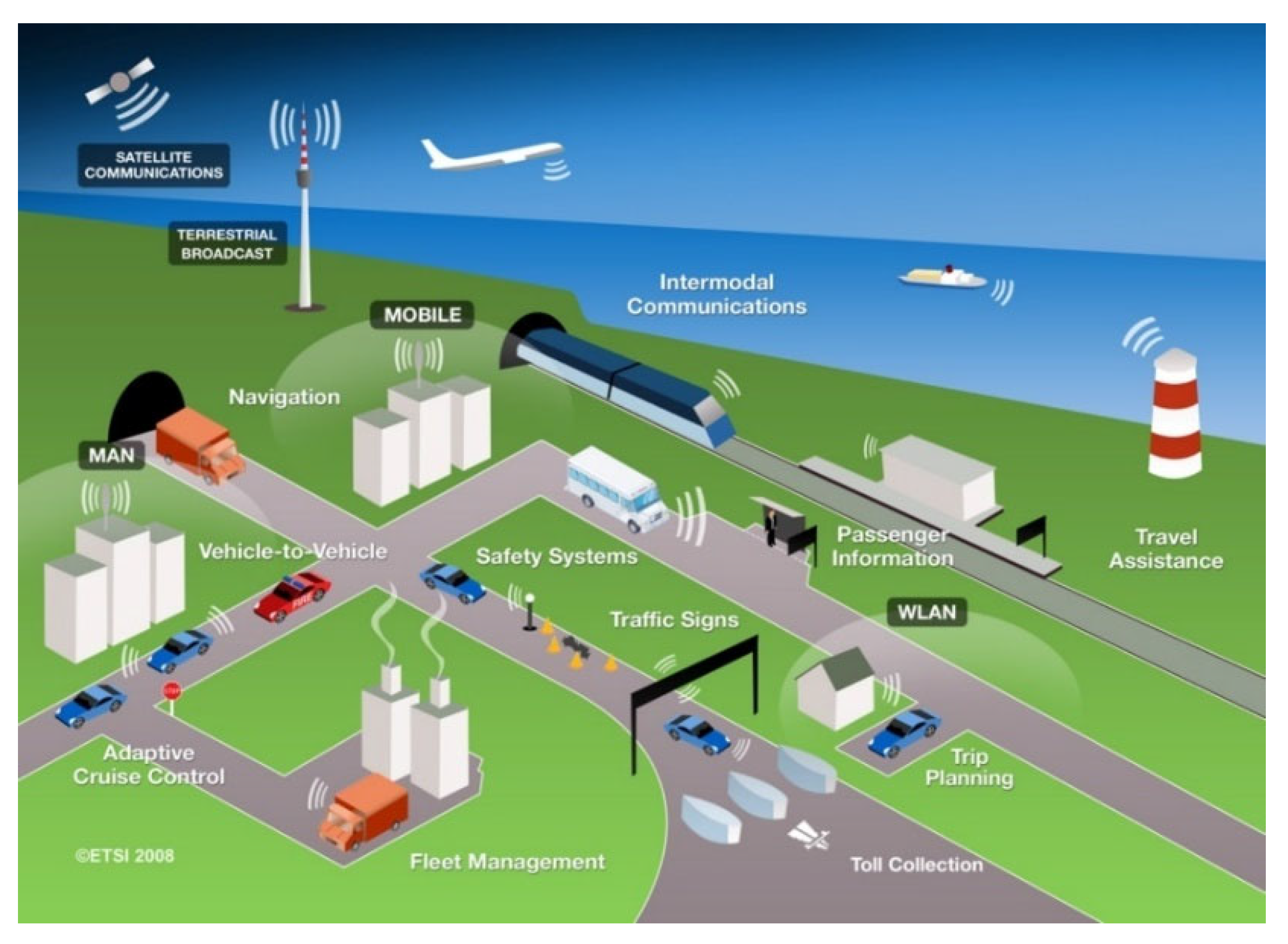
2.2. Intelligent Transportation Communication Technologies
2.2.1. Global Navigation Satellite System
2.2.2. Detection Technologies
2.2.3. Dedicated Short-Range Communications
2.2.4. Radio Frequency Identification
2.2.5. Low-Power Wide-Area Network
2.2.6. Cooperative Intelligent Transportation Systems
2.2.7. Cellular Communication Networks
2.2.8. Near-Field Communication
2.3. Intelligent Transportation System Architecture
2.4. Intelligent Transportation System Infrastructure
2.5. Intelligent Transportation Systems Advantages
- Low CO2 mission,
- Reduced traffic accident,
- Improving the quality of life of people,
- Use of roads following the capacity,
- Reduced transportation time,
- Creation of infrastructure for increasing mobility,
- Reduced traffic jams,
- Elimination of infrastructure problems,
- Development of environmentally friendly systems,
- Increasing the orientation to public transport,
- Improving driver safety and accident management,
- Determination of traffic density,
- Data integration of density,
- Data integration between different systems,
- Superiority in transit, and
- Ensuring improved traffic flow and safety.
3. The Impact of Innovative Technologies on Intelligence Transportation Systems
3.1. Internet of Things
3.2. Cloud Computing
3.3. Big Data
3.4. Artificial Intelligence and Machine Learning
3.5. Blockchain Technologies
3.6. Generation (5G) Mobile Networks
3.7. Quantum Information Technologies in 6G Networks
4. Intelligent Transportation System Security Challenges and Measures
4.1. ITS Security Issues and Challenges
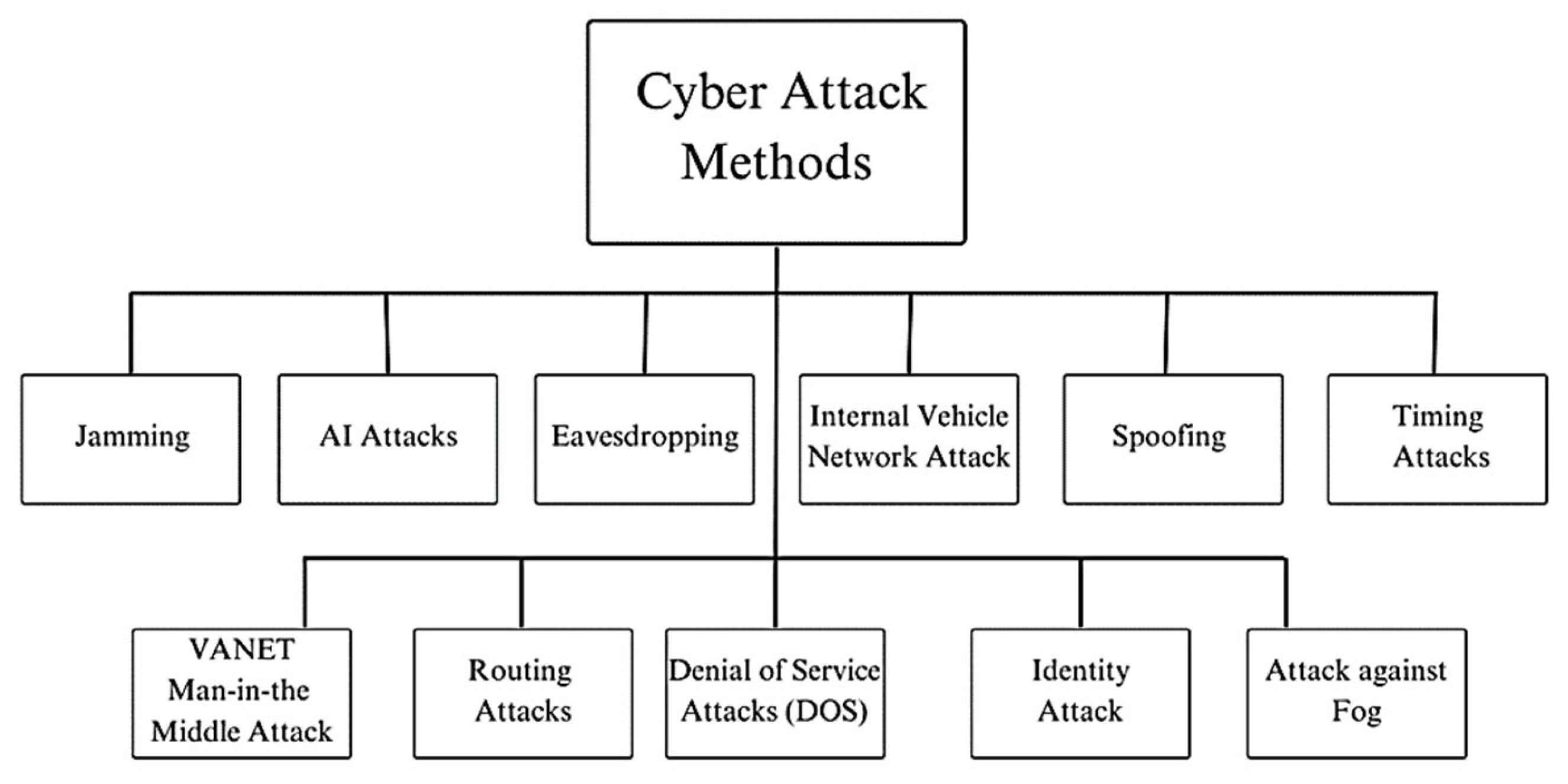
4.2. ITS Cyber Attack Methods
4.3. Basic Security Requirements for ITS
- No universal default passwords,
- Implement manage reports vulnerabilities,
- Keep software updated,
- Securely store sensitive security parameters,
- Communicate securely,
- Ensure software integrity,
- Ensure that personnel data are secure,
- Make it easy for users to delete user data,
- Validate input data,
- Maintenance of devices easy,
- Minimize exposed attack surfaces,
- Examine system telemetry data,
- Make systems resilient to outages,
- Using quantum security method, and
- Using a new generation of security algorithms.
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Nomenclature
| ITS | Intelligent Transportation Systems |
| GPS | Global Positioning System |
| ERTICO | European Road Transport Telematics Implementation Coordination |
| VANET | Vehicular Ad Hoc Network |
| ETSI | European Telecommunications Standards Institute |
| NEMA | National Electrical Manufacturers Association |
| ISO | International Organization for Standardization |
| CACS | Comprehensive Automobile Traffic Control Systems |
| ERGS | Electronic Route Guidance System |
| RSU | Road Side Unit |
| V2V | Vehicle-To-Vehicle |
| V2I | Vehicle-To-Infrastructure |
| V2X | Vehicle-To-Anywhere |
| GNSS | Global Navigation Satellite System |
| DSRC | Dedicated Short-Range Communications |
| APS | Automatic Pass System |
| RFID | Radio Frequency Identification |
| M2M | Machine-To-Machine |
| LPWAN | Low-Power Wide-Area Network |
| LoRa | Long Range |
| C-ITS | Collaborative Intelligent Transportation Systems |
| NFC | Near-Field Communication |
| WAWC | Wide Area Wireless Communication |
| WC | Wireless Communication |
| MIRT | Mobile With Mobile Infrared Transmitters |
References
- Katanalp, B.Y.; Yıldırım, Z.B.; Eren, E.; Uz, V.E. An Evaluation on Intelligent Transportation Systems. In Proceedings of the Second International Symposium on Innovative Approaches in Scientific Studies, Samsun, Turkey, 30 November–2 December 2018. [Google Scholar]
- Sakiz, F.; Sen, S. A survey of attacks and detection mechanisms on intelligent transportation systems: VANETs and IoV. Ad Hoc Netw. 2017, 61, 33–50. [Google Scholar] [CrossRef]
- Özarpa, C.; Avcı, İ.; Kınacı, B.F. Critical Level Analysis of Subsystems Used in Smart Rail Systems. J. Railw. Eng. 2021, 14, 143–153. [Google Scholar] [CrossRef]
- Rafat, M.; Azadi, S. A Novel Flexible Lane Changing (FLC) Method in Complicated Dynamic Environment for Automated Vehicles. J. Appl. Comput. Mech. 2021, 9, 318–331. [Google Scholar] [CrossRef]
- Lamssaggad, A.; Benamar, N.; Hafid, A.S.; Msahli, M. A Survey on the Current Security Landscape of Intelligent Transportation Systems. IEEE Access 2021, 9, 9180–9208. [Google Scholar] [CrossRef]
- Lu, Z.; Qu, G.; Liu, Z. A Survey on Recent Advances in Vehicular Network Security, Trust, and Privacy. IEEE Trans. Intell. Transp. Syst. 2019, 20, 760–776. [Google Scholar] [CrossRef]
- ISO/IEC 27001:2022; Information Security, Cybersecurity and Privacy Protection-Information Security Management Systems. ISO: Geneva, Switzerland, 2022.
- NIST Cybersecurity Framework (CSF) 2.0.; IST Cybersecurity Framework; NIST: Gaithersburg, MD, USA, 2024.
- GDPR. General Data Protection Regulation; European Union: Brussels, Belgium, 2016. [Google Scholar]
- ETSI (European Telecommunications Standards Institute). European Union, Brussels, Belgium. 1988. Available online: https://www.etsi.org/ (accessed on 22 January 2023).
- NEMA (National Electrical Manufacturers Association). Washington, DC, USA. 1926. Available online: https://www.nema.org/ (accessed on 22 January 2023).
- Javed, M.A.; Ben Hamida, E.; Al-Fuqaha, A.; Bhargava, B. Adaptive Security for Intelligent Transport System Applications. IEEE Intell. Transp. Syst. Mag. 2018, 10, 110–120, hal-01591878. [Google Scholar] [CrossRef]
- Kiela, K.; Barzdenas, V.; Jurgo, M.; Macaitis, V.; Rafanavicius, J.; Vasjanov, A.; Kladovscikov, L.; Navickas, R. Review of V2X–IoT standards and frameworks for ITS applications. Appl. Sci. 2020, 10, 4314. [Google Scholar] [CrossRef]
- Meena, G.S.; Sharma, D.; Mahrishi, M. Traffic Prediction for Intelligent Transportation System using Machine Learning. In Proceedings of the 3rd International Conference on Emerging Technologies in Computer Engineering: Machine Learning and Internet of Things (ICETCE), Jaipur, India, 7–8 February 2020; pp. 145–148. [Google Scholar] [CrossRef]
- Hamida, E.B.; Noura, H.; Znaidi, W. Security of Cooperative Intelligent Transport Systems: Standards, Threats Analysis and Cryptographic Countermeasures. Electronics 2015, 4, 380–423. [Google Scholar] [CrossRef]
- ETSI. Available online: https://www.etsi.org/deliver/etsi_en/303600_303699/303645 (accessed on 22 January 2023).
- Eliasson, J.; Hultkrantz, L.; Nerhagen, L.; Rosqvist, L.S. The Stockholm congestion–charging trial 2006: Overview of effects. Transp. Res. Part A Policy Pract. 2009, 43, 240–250. [Google Scholar] [CrossRef]
- Balaban, O.; Puppim de Oliveira, J.A. Finding sustainable mobility solutions for shrinking cities: The case of Toyama and Kanazawa. J. Place Manag. Dev. 2022, 15, 20–39. [Google Scholar] [CrossRef]
- Rozenman, G.G.; Kundu, N.K.; Liu, R.; Zhang, L.; Maslennikov, A.; Reches, Y.; Youm, H.Y. The quantum internet: A synergy of quantum information technologies and 6G networks. IET Quantum Commun. 2023, 4, 147–166. [Google Scholar] [CrossRef]
- Macioszek, E. Architecture of intelligent transportation systems in the world and in Poland. Arch. Transp. Syst. Telemat. 2014, 7, 22–26. [Google Scholar]
- An, S.; Lee, B.-H.; Shin, D.-R. A Survey of Intelligent Transportation Systems. In Proceedings of the 2011 Third International Conference on Computational Intelligence, Communication Systems and Networks, Bali, Indonesia, 26–28 July 2011; pp. 332–337. [Google Scholar] [CrossRef]
- Dovis, F.; Ruotsalainen, L.; Toledo-Moreo, R.; Kassas, Z.Z.M.; Gikas, V. Recent advancement on the use of global navigation satellite system-based positioning for intelligent transport systems [guest editorial]. IEEE Intell. Transp. Syst. Mag. 2020, 12, 6–9. [Google Scholar] [CrossRef]
- Bangui, H.; Buhnova, B. Recent advances in machine-learning driven intrusion detection in transportation: Survey. Procedia Comput. Sci. 2021, 184, 877–886. [Google Scholar] [CrossRef]
- Cheek, E.; Alghodhaifi, H.; Adam, C.; Andres, R.; Lakshmanan, S. Dedicated short range communications used as fail-safe in autonomous navigation. Unmanned Syst. Technol. XXII 2020, 11425, 159–177. [Google Scholar]
- Choy, J.L.C.; Wu, J.; Long, C.; Lin, Y.-B. Ubiquitous and low power vehicles speed monitoring for intelligent transport systems. IEEE Sens. J. 2020, 20, 5656–5665. [Google Scholar] [CrossRef]
- Gu, F.; Niu, J.; Jiang, L.; Liu, X.; Atiquzzaman, M. Survey of the low power wide area network technologies. J. Netw. Comput. Appl. 2020, 149, 102459. [Google Scholar] [CrossRef]
- Vintageroadhaulage. Available online: http://www.vintageroadhaulage.com.au/faq/c-its/ (accessed on 11 January 2023).
- Zhang, H.; Lu, X. Vehicle communication network in intelligent transportation system based on Internet of Things. Comput. Commun. 2020, 160, 799–806. [Google Scholar] [CrossRef]
- Liébana-Cabanillas, F.; Molinillo, S.; Ruiz-Montañez, M. To use or not to use, that is the question: Analysis of the determining factors for using NFC mobile payment systems in public transportation. Technol. Forecast. Soc. Chang. 2019, 139, 266–276. [Google Scholar] [CrossRef]
- Zhu, J.; Xu, W.; Sun, H.; Zhu, H. Research on optimization of shared bicycle real-time multimedia interactive dispatching system for intelligent transportation system. Multimed. Tools Appl. 2019, 82, 22299. [Google Scholar] [CrossRef]
- Vanni, P.R.M.; Jaimes, L.M.S.; Mapp, G.; Moreira, E. Ontology-driven reputation model for VANET. In Proceedings of the Twelfth Advanced International Conference on Telecommunications (AICT 2016), Valencia, Spain, 22–26 May 2016; IARIA: Barcelona, Spain, 2016; pp. 14–19. [Google Scholar]
- Cmu. Available online: https://www.cs.cmu.edu/~pb3a/presentations/aml_ferreira/sld006.html (accessed on 6 May 2023).
- Humayun, M.; Jhanjhi, N.; Hamid, B.; Ahmed, G. Emerging smart logistics and transportation using IoT and blockchain. IEEE Internet Things Mag. 2020, 3, 58–62. [Google Scholar] [CrossRef]
- Ferdowsi, A.; Challita, U.; Saad, W. Deep learning for reliable mobile edge analytics in intelligent transportation systems: An overview. IEEE Veh. Technol. Mag. 2019, 14, 62–70. [Google Scholar] [CrossRef]
- Çelik, U. Intelligent Transportation Systems and Big Data. In Proceedings of the 1st International Conference on Intelligent Transportation Systems (BANU-ITSC’18), Bandırma, Balıkesir, Turkey, 19–21 April 2018. [Google Scholar]
- Fatemidokht, H.; Rafsanjani, M.K.; Gupta, B.B.; Hsu, C.-H. Efficient and secure routing protocol based on artificial intelligence algorithms with UAV-assisted for vehicular ad hoc networks in intelligent transportation systems. IEEE Trans. Intell. Transp. Syst. 2021, 22, 4757–4769. [Google Scholar] [CrossRef]
- Mollah, M.B.; Zhao, J.; Niyato, D.; Guan, Y.L.; Yuen, C.; Sun, S.; Lam, K.-Y.; Koh, L.H. Blockchain for the Internet of Vehicles Towards Intelligent Transportation Systems: A Survey. IEEE Internet Things J. 2021, 8, 4157–4185. [Google Scholar] [CrossRef]
- Guevara, L.; Auat Cheein, F. The role of 5G technologies: Challenges in smart cities and intelligent transportation systems. Sustainability 2020, 12, 6469. [Google Scholar] [CrossRef]
- Akbar, M.A.; Khan, A.A.; Hyrynsalmi, S. Role of quantum computing in shaping the future of 6G technology. Inf. Softw. Technol. 2024, 170, 107454. [Google Scholar] [CrossRef]
- Hahn, D.M.; Munir, A.; Behzadan, V. Security and Privacy Issues in Intelligent Transportation Systems: Classification and Challenges. IEEE Intell. Transp. Syst. Mag. 2021, 13, 181–196. [Google Scholar] [CrossRef]
- Chavhan, S.G.; Gupta, D.; Garg, S.; Khanna, A.; Choi, B.J.; Hossain, M.S. Privacy and Security Management in Intelligent Transportation System. IEEE Access 2020, 8, 148677–148688. [Google Scholar] [CrossRef]
- Avcı, İ.; Özarpa, C.; Özdemir, M.; Kınacı, B.F.; Kara, S.A. Analysis of Multi-Layer Security System in terms of Cyber Attacks in Intelligent Transportation Vehicles. In Proceedings of the 2nd International Intelligent Transportation Systems Conference (BANU-ITSC’21), Bandırma, Turkey, 22–24 October 2021. [Google Scholar]
- Avcı, İ.; Koca, M. Predicting DDoS Attacks Using Machine Learning Algorithms in Building Management Systems. Electronics 2023, 12, 4142. [Google Scholar] [CrossRef]
- Harvey, J.; Kumar, S. A Survey of Intelligent Transportation Systems Security: Challenges and Solutions. In Proceedings of the 2020 IEEE 6th Intl Conference on Big Data Security on Cloud (BigDataSecurity), Baltimore, MD, USA, 25–27 May 2020; pp. 63–268. [Google Scholar]
- Zheng, K.; Zheng, Q.; Chatzimisios, P.; Xiang, W.; Zhou, Y. Heterogeneous Vehicular Networking: A Survey on Architecture, Challenges, and Solutions. IEEE Commun. Surv. Tutor. 2015, 17, 2377–2396. [Google Scholar] [CrossRef]
- Sándor, Z.; Monostori, Á. Traffic Analysis of Specific Motorways with Different Usage Characteristics in Hungary with the Method of Section Control. Acta Tech. Jaurinensis 2020, 13, 211–245. [Google Scholar] [CrossRef]
- Nagy, V.; Horváth, B. Effect of Self-driving Buses on Vehicle Scheduling. Adv. Intell. Syst. Comput. 2021, 1278, 21–29. [Google Scholar] [CrossRef] [PubMed]
- Avcı, İ.; Koca, M. Cybersecurity Attack Detection Model, Using Machine Learning Techniques. Acta Polytech. Hung. 2023, 20, 29–44. [Google Scholar] [CrossRef]
- Kaur, J.; Ramkumar, K.R. The recent trends in cyber security: A review. J. King Saud. Univ.-Comput. Inf. Sci. 2022, 34, 5766–5781. [Google Scholar] [CrossRef]
- Faruk, M.J.H.; Tahora, S.; Tasnim, M.; Shahriar, H.; Sakib, N. A review of quantum cybersecurity: Threats, risks and opportunities. In Proceedings of the 2022 1st International Conference on AI in Cybersecurity (ICAIC), Victoria, TX, USA, 24–26 May 2022; IEEE: Piscataway, NJ, USA, 2022. [Google Scholar]





| 1 | Mobile With Mobile Infrared Transmitters (MIRT)—it is possible to disable traffic lights with a remote computer [39]. |
| 2 | Driving functions can be disabled and traffic flow can be controlled by terrorist attacks on ITS systems. It is very difficult to resist these attacks [39]. |
| 3 | Wireless communication poses a major security risk. With jamming attacks, ITS systems can be disabled by corrupting the signal [40]. In particular, it becomes easier to infiltrate bus systems. |
| 4 | Vehicle Private Networks (VANETs) networks are highly vulnerable to maintaining traffic safety. Sybil attacks are one of the most dangerous cyber attacks on these networks and are very difficult to detect. In addition, Distributed Denial-Of-Service (DDoS) attacks are dangerous attacks. It creates the risk of consuming the resources of the systems against excessive intensity [41]. |
| 5 | Incorrect transmission of vehicle location data is one of the major problems. Thus, incorrect location causes data to be transmitted incorrectly [42]. |
| 6 | With the developing technologies, the security risk is reduced when ITS control units are configured differently from the corporate network. Having a separate firewall prevents erroneous data [43]. |
| 7 | With Intrusion Protection Systems (IPS) and Intrusion Detection Systems (IDS), daily data are analyzed and necessary anomaly controls are made. The lack of these systems makes it very difficult to detect attacks that occur in ITS systems [44]. |
| 8 | It is possible to prevent many cyber attacks when digital signature algorithms are used in ITS systems. These technologies encrypt and secure data. It provides protection, especially against Man-in-the-Middle (MiTM) attacks [45]. |
| 9 | It is possible to analyze the real status of the vehicles with the data fusion software. Data from the entire field is collected and reported. Thus, it becomes easier to perform security analyses on the data [46]. |
| 10 | Biometric authentication is a technique that authenticates people based on their physical and individual characteristics. After the information is collected, it is distributed, stored, and processed within the system. These techniques ensure that the ITS system is secure against spoofing attacks [47]. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Avcı, İ.; Koca, M. Intelligent Transportation System Technologies, Challenges and Security. Appl. Sci. 2024, 14, 4646. https://doi.org/10.3390/app14114646
Avcı İ, Koca M. Intelligent Transportation System Technologies, Challenges and Security. Applied Sciences. 2024; 14(11):4646. https://doi.org/10.3390/app14114646
Chicago/Turabian StyleAvcı, İsa, and Murat Koca. 2024. "Intelligent Transportation System Technologies, Challenges and Security" Applied Sciences 14, no. 11: 4646. https://doi.org/10.3390/app14114646
APA StyleAvcı, İ., & Koca, M. (2024). Intelligent Transportation System Technologies, Challenges and Security. Applied Sciences, 14(11), 4646. https://doi.org/10.3390/app14114646