Abstract
In an era marked by technological advancement, the rising reliance on Virtual Private Networks (VPNs) necessitates sophisticated forensic analysis techniques to investigate VPN traffic, especially in mobile environments. This research introduces an innovative approach utilizing Convolutional Neural Networks (CNNs) and Graph Neural Networks (GNNs) for classifying VPN traffic, aiding forensic investigators in precisely identifying applications or websites accessed via VPN connections. By leveraging the combined strengths of CNNs and GNNs, our method provides an effective solution for discerning user activities during VPN sessions. Further extending this framework, we incorporate blockchain technology to meticulously record all mobile VPN transactions, ensuring a tamper-proof and transparent ledger that significantly bolsters the integrity and admissibility of forensic evidence in legal scenarios. A specific use-case demonstrates this methodology in mobile forensics, where our integrated approach not only accurately classifies data traffic but also securely logs transactional details on the blockchain, offering an unprecedented level of detail and reliability in forensic investigations. Extensive real-world VPN dataset experiments validate our approach, highlighting its potential to achieve high accuracy and offering invaluable insights for both technological and legal domains in the context of mobile VPN usage.
1. Introduction
Protecting sensitive data from threats has become more crucial now for both the individuals and enterprises than the few previous decades with the growing expansion of Internet uses. In this respect, a Virtual Private Network (VPN) works well for offering secure and private communication over public networks which has increased its popularity within the field of the information technology (IT) industry. Through providing a robust solution by this VPN, the data traffic is encrypted, confidentiality is ensured, and the users are allowed to make a secure connection to a remote network.
It is therefore justifiable to exaggerate the significance of VPNs in the IT landscape because it plays a crucial role in protecting sensitive information particularly required in places where corporate networks are accessed by the users or there is a connection to public WiFi, which are considered as potentially insecure networks. To protect data from the unauthorized access and interception, an encrypted tunnel is formed between the VPN server and the user’s device to connect them both. They are therefore essential for companies, governmental agencies, and private users who are concerned with their online privacy and security.
As cybersecurity continues to evolve, stringent Internet regulations introduced by some countries, such as recent bans on VPNs and hefty penalties for their use, highlight the pressing need for more sophisticated methods to monitor and analyze VPN traffic. These countries have enforced laws making VPN use on phones illegal, accompanied by severe fines and potential imprisonment. Such measures underscore the increasing focus on VPN usage globally, particularly when they are employed to circumvent geo-restrictions and access blocked content, raising significant issues regarding cybersecurity and national security [1,2,3].
Furthermore, national telecommunications regulatory authorities have enforced restrictions on numerous websites for various reasons. These reasons often include hosting content that conflicts with government policies or promotes perspectives contrary to national values, among other issues. Such widespread censorship efforts highlight the inherent challenges and complexities of managing Internet usage. These measures illustrate the ongoing struggle to balance digital content management with the need to uphold societal norms, while also preserving free access to information. The continued regulation of online spaces brings into focus the ongoing tension between safeguarding national security and protecting individual rights to information access.
As far the operation of VPN is concerned, it is essential to explore its workings and the different types of protocols it employs in order to thoroughly understand the VPN classification in a forensic manner [4]. VPN protocols offer various performances and levels of security. The protocols, including OpenVPN, PPTP, IPsec, and L2TP, have their own strengths and weaknesses. Forensic investigators familiar with these protocols are able to identify the specific VPN technologies in use, which is also helpful in aiding the analysis of VPN traffic [5].
Recent advancements in machine learning for VPN traffic classification, as explored by Sikha Bagui [6,7] and Shane Miller [8], have demonstrated significant progress in distinguishing between VPN and non-VPN traffic using time-related features and flow statistics data, respectively. Bagui’s work, in particular, highlighted the efficacy of using logistic regression, support vector machine, Naïve Bayes, k-nearest neighbor, and ensemble methods (Random Forest and Gradient Boosting Tree classifiers) for traffic classification, identifying features that contribute to achieving high accuracy. Meanwhile, Miller’s research on using a multi-layered perceptron neural network showcased the potential for high degrees of accuracy in detecting VPN usage, emphasizing the advancements in unauthorized user detection through network traffic analysis.
Despite these advancements, the classification of encrypted VPN traffic using traditional machine learning techniques faces inherent limitations. The most notable challenges include high false-positive rates, as indicated by the research of Fayoumi et al. [9], and a comparatively low accuracy in distinguishing complex traffic patterns. These issues underscore the need for novel approaches that can enhance accuracy and reduce false positives. Moreover, existing machine learning solutions lack mechanisms for ensuring the transparency and security of the classification process, critical in the context of evolving cyber threats and regulatory requirements for data protection.
Our research addresses this pressing need by introducing a novel solution that intertwines the advanced capabilities of Convolutional Neural Networks (CNNs) and Graph Neural Networks (GNNs) with the robustness and transparency of technology. This integrated approach is designed to revolutionize the domain of mobile VPN forensics by offering a more efficient, accurate, and secure method of analyzing VPN traffic. The reliability of VPN traffic classification can be enhanced by comparing the outputs of multiple models. Furthermore, we also propose to correlate the VPN traffic to its source in addition to identifying it merely. This will improve forensic analysis capabilities by allowing investigators to track back VPN connections to certain persons or businesses.
The cornerstone of our solution lies in the utilization of CNN and GNN models. CNNs are renowned for their proficiency in processing and analyzing visual imagery, making them ideal for interpreting complex patterns within VPN traffic data. GNNs, on the other hand, excel in managing data that are structured as graphs, which is particularly pertinent to network traffic analysis. By combining these two neural network models, our approach can effectively discern intricate patterns and relationships in VPN usage, thereby enhancing the accuracy and depth of forensic analysis.
To further augment the integrity and reliability of our forensic process, we integrate blockchain technology into our solution. Blockchain, with its inherent characteristics of decentralization, immutability, and transparency, provides a secure platform for storing and managing forensic data. By recording VPN traffic data on a blockchain, we ensure that the forensic evidence is tamper-proof and traceable, thereby enhancing the credibility and legal acceptability of the forensic process.
Our contribution also includes the identification of the VPN software or protocol by examining the traffic patterns and distinctive features of various VPN clients. Eventually, investigators can use this information to profile the VPN software used by possible threat actors and better understand the methods and tools they are using.
In essence, our proposed solution offers a cutting-edge approach to mobile VPN forensics, responding to the burgeoning challenges posed by the increased scrutiny of VPN usage worldwide. Through the synergistic use of CNN, GNN, and blockchain technology, we pave the way for a new era in digital forensics, marked by enhanced accuracy, security, and trustworthiness.
Paper Organization: The rest of the paper is organized as follows, Section 2 provides the selected literature review in the area of study. Section 3 provides the methodology of our proposed study containing the complete protocol of VPN forensics, blockchain integration, and data classification models. The blockchain implementation is shown in Section 4, and finally, Section 5 focuses on the results of VPN data and the processing, classification, and accuracy results.
2. Literature Review
2.1. Digital Forensics and Blockchain
Forensics, in the context of information technology and cybersecurity, involves the use of scientific methods and techniques to investigate and analyze digital data for legal purposes [10,11]. This field plays a crucial role in identifying, preserving, recovering, analyzing, and presenting facts about digital information. With the rapid advancement of technology, digital forensics has evolved to address complex challenges in the cyber world, such as cybercrime, unauthorized data access, and data breaches. The integration of mobile VPNs in digital forensics signifies a significant leap, enhancing the ability to securely transmit and analyze data remotely while maintaining the integrity and confidentiality of the information [12,13]. The incorporation of Convolutional Neural Networks (CNNs) further augments this field by enabling sophisticated pattern recognition and analysis of large data sets, thereby providing a more accurate and efficient forensic analysis.
Blockchain technology, known for its decentralization, transparency, and security, has found applications in various domains beyond its initial use in cryptocurrency [14,15,16]. In healthcare, blockchain provides a secure platform for managing patient records, ensuring data integrity and accessibility while maintaining patient confidentiality [17,18,19,20]. In vehicle tracking, it offers a reliable and tamper-proof system for logging vehicular data, essential for fleet management and regulatory compliance [21]. Blockchain’s application in property registration introduces an immutable record-keeping system, significantly reducing fraud and streamlining property ownership transfers [22]. In the realm of augmented reality, blockchain facilitates collaborative experiences by securely managing digital assets and interactions [23,24,25]. Lastly, its role in Android malware analysis is groundbreaking; blockchain can be utilized for securely sharing data across multiple entities, enhancing the detection and analysis of malicious software in Android devices, thus bolstering cybersecurity measures [26,27].
2.2. Traditional VPN Classification Methods
Prior to exploring the machine learning-based approaches, it is crucial to be aware of the conventional approaches to VPN classification. Port-based classification or flow-based analysis and Deep Packet Inspection (DPI) are frequently used in these techniques [28]. These techniques have, however, a number of drawbacks, such as the requirement for thorough payload inspection, vulnerability to evasion strategies, and reliance on well-known port numbers [2].
2.3. Machine Learning-Based VPN Classification
The very first crucial step of the machine learning-based classification process begins with the extraction of features. Numerous features obtained from flow statistics, packet headers, and payload information have been tested by researchers. Packet size, flow duration, inter-arrival time, and protocol dispersion are a few typical features [3]. Entropy-based characteristics [9] and features obtained from encrypted payloads using statistical analysis have both been investigated in recent publications [7].
For VPN categorization, a variety of machine learning algorithms, including supervised, semi-supervised, and unsupervised techniques, have been used. Typical supervised algorithms include support vector machines (SVMs), decision trees, neural networks, and k-nearest neighbors (k-NNs) [3]. Without labeled data, unsupervised approaches like clustering have also been used to categorize VPN traffic [28]. To further enhance classification performance and minimize annotation work, semi-supervised techniques that make use of both labeled and unlabeled data have been proposed [7].
2.4. Advanced Machine Learning Techniques for VPN Classification
Since Convolutional Neural Networks (CNNs) are a subset of deep learning models, they have demonstrated outstanding performance in image recognition tests(c.f Figure 1). In the subject of VPN categorization, their capacity to manage significant amounts of data and automatically learn pertinent properties has sparked interest. CNNs have been used to depict network traffic using both image-based representations and time-series. A CNN-based technique was put forth in one study by Okonkwo, Z. et al. (2022) for classifying encrypted traffic, including VPNs [29].
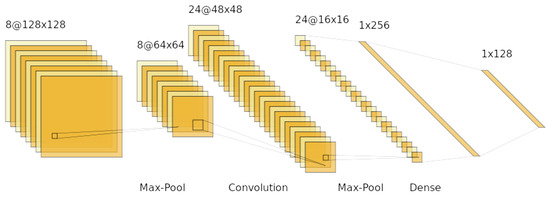
Figure 1.
A Convolutional Neural Network with three hidden layers and an output layer. Further explanation is provided in Section 3.2.
They created a two-dimensional, grayscale image from the raw network traffic and used that as the input for the CNN model. The technique achieved good classification accuracy across a number of datasets, displaying encouraging findings with accuracy ranging from 91% to 99%. A CNN was used in a different study by Hu, X., Gu, and Wei (2021) to categorise network traffic using time-series data [30].
One of the ideas given by Shamsi et al. [31] discusses the limitations of relying solely on neural networks (NNs) for classifying encrypted traffic, asserting that NNs alone cannot achieve 100% classification accuracy. This paper suggests that incorporating the Server Name Indication (SNI) field, which remains unencrypted during the TLS handshake and discloses the server’s hostname, enhances classification algorithms. The rationale is that including SNI data provides additional clear text information that aids in the more accurate classification of encrypted traffic.
However, this critique and the proposed SNI-based solution focus on a specific aspect of network security and do not address the complexities of Virtual Private Networks (VPNs). VPNs are fundamentally designed to secure internet connections by establishing a private network over a public internet infrastructure. They play a crucial role in masking a user’s IP address, thus making online actions virtually untraceable and enhancing privacy and security—areas not covered by the SNI-based classification approach.
Our research diverges significantly from the issues addressed by the SNI-based method. In our paper, “Integrating Blockchain and Deep Learning for Enhanced Mobile VPN Forensics”, we explore the application of advanced neural networks, specifically Convolutional Neural Networks (CNNs) and Graph Neural Networks (GNNs), in the classification of VPN traffic. This approach is not merely about overcoming the encryption challenges but also about providing a method to analyze and understand complex patterns within encrypted VPN traffic, which goes beyond the capabilities of basic SNI data exploitation.
Furthermore, our work incorporates blockchain technology to add a layer of security and transparency that is absent in traditional neural network applications. By leveraging blockchain, we ensure that every transaction and classification operation within the VPN is recorded in an immutable ledger, enhancing the integrity and verifiability of forensic data. This approach not only addresses the limitations of NNs as discussed in the referenced paper but also extends the functionality to meet the stringent requirements of legal and security frameworks in today’s digital landscape.
The network traffic was represented as a sequence of arrival times and packet sizes, which was then eventually used as an input into the CNN model for the network traffic analysis. This approach exceeded traditional machine learning techniques in excellence and demonstrated high classification accuracy. Exploration of GNNs for network traffic analysis and VPN classification are researched lately. Graph neural networks (GNNs) can be classified as a class of deep learning models in order to handle graph-structured data; various domains, including molecular biology, social network analysis, and computer vision, have applied them.
In order to represent the network traffic as a graph, the authors used GNN to stimulate the relationship between various network flows as shown in a study by Zhang, Chen, and Zhang [32] where edges represented the relationships between them while nodes corresponded to the flows. The classification of flows as VPN or non-VPN traffic was ensured through training the GNN model thereby outperforming conventional machine learning methods and achieving high accuracy.
Likewise, a GNN-based approach was proposed for encrypted traffic classification including VPNs [32] in another study conducted by Liu, Zhang, and Cui (2021). Through extracting features from payload content and packet headers, they created a graph representation of network traffic. After training the GNN model, it classified the traffic, excelling the machine learning techniques in terms of performance.
2.5. Challenges and Future Directions
Several challenges are still existing despite the success of machine learning-based VPN classification. For example, there are difficulties in feature selection due to the dynamic nature of VPN traffic, as change may occur in the traffic patterns over time. It might be essential to regularly update the feature set and retrain the models in order to maintain accuracy of classification [2]. Furthermore, the performance of machine learning models can be adversely affected, if there is encrypted traffic present on a network, because it restricts the features that can be used to classify data [7]. Finally, privacy concerns may arise when handling network traffic data, particularly when dealing with payload content [3].
In addition to the challenges mentioned earlier, the adoption of advanced machine learning techniques like CNNs and GNNs presents its own set of difficulties. For instance, these models often require large amounts of training data, which may not always be available for VPN classification tasks. Furthermore, the computational complexity of deep learning models can be an issue, especially in real-time or resource-constrained environments.
Future research directions include developing more efficient CNN and GNN architectures that can handle the challenges specific to VPN classification. Additionally, exploring transfer learning techniques to leverage pre-trained models and investigating methods for combining different types of deep learning models (e.g., CNNs and GNNs) to improve classification performance may be promising avenues to pursue.
3. Methodology
The methodology is divided in to several phases. In the first phase, we have created a formal mathematical model that explains the complete framework of VPN forensics, where each function represents a step in the process, from establishing a VPN connection to recording transactions on the blockchain, and finally analyzing the data with CNN and GNN for forensic reporting depicted in Listing 1. This model provides a structured approach to capturing, recording, and analyzing VPN traffic for forensic purposes.
The mathematical model for our mobile VPN forensics framework integrates various components for a comprehensive analysis. Initially, VPN connections between two mobile devices are established and voice calls are routed through OpenVPN, represented by functions and as depicted in Figure 2. Data transfer during these calls is denoted as . Throughout this process, critical forensic data are collected at various intersections, encapsulated in . These data are then securely logged onto a blockchain through an API function , ensuring integrity and non-repudiation, and undergoes a consensus mechanism . For in-depth analysis, these blockchain-recorded data are processed through a combination of Convolutional Neural Networks (CNNs) and Graph Neural Networks (GNNs), symbolized by and . These networks classify and interpret the data, weighted by parameters and . The output of this analysis, Y, is then synthesized into a comprehensive forensic report R by the function . This model thus offers a robust approach to capturing, recording, and analyzing VPN traffic data for forensic purposes, leveraging the strengths of blockchain technology and advanced neural networks.
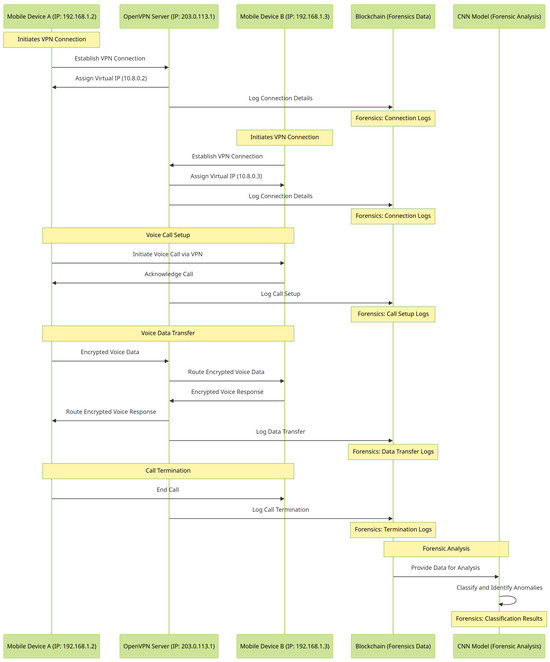
Figure 2.
A comprehensive process of VPN forensic integrating with blockchain and deep learning models, explained with a use case.
The sequence diagram (cf. Figure 2) for the VPN forensics model outlines a process where two mobile devices communicate over a VPN, with the interaction being logged and analyzed for forensic purposes. Mobile Device A and Mobile Device B establish a VPN connection with the OpenVPN Server, each receiving a unique virtual IP address. These connection details, along with subsequent voice call data, are logged onto a blockchain, ensuring a secure and tamper-proof record. The sequence covers the initiation, execution, and termination of a voice call between the two devices, with each significant event—connection establishment, voice call setup, data transfer, and call termination—being recorded on the blockchain. These blockchain-stored data are then fed into a Convolutional Neural Network (CNN) model for forensic analysis. The CNN model classifies the data and identifies any anomalies or patterns of interest. This comprehensive approach integrates secure VPN communication, immutable logging with blockchain technology, and advanced data analysis using CNN, providing a robust framework for mobile VPN forensics.
| Listing 1. Formaly defined the complete process of proposed framework. |
 |
3.1. Data Collection
In addition to our own transactions data as a dataset, the authors effectively collected data from various sources for training purposes, including open-source repositories, VPN service providers, and previous research studies. The dataset contained raw network traffic data in the form of packet captures (PCAP) or flow records, as well as metadata about the users and accessed applications.
It is important to ensure that the dataset is representative of real-world VPN traffic scenarios. It will thus ensure that a diverse range of applications constitute our data including streaming, messaging, browsing, etc. We need a dataset with labeled application types that contains information about VPN traffic in order to train and test our algorithms efficiently. We used the ISCXVPN2016 dataset, a well-known benchmark for VPN traffic classification, in this study. Additionally, in order to ensure the diversity and representativeness of our dataset, we collected the customized VPN traffic data using a variety of VPN protocols.
The ISCXVPN2016 dataset is a sizeable database that offers a complete collection of data in order to analyze the VPN traffic classification methods. The database is created and developed by the University of New Brunswick Information Security Centre of Excellence (ISCX). A variety of activities such as internet browsing, peer-to-peer file sharing, emailing, chat from various applications, streaming video, file transfers, and audio from applications are carried out by the labeled network traffic datasets present in the ISCXVPN2016 datasets. In this regard, number of VPN protocols including Layer 2 Tunneling Protocol (L2TP) and the Point-to-Point Tunneling Protocol (PPTP) are the examples from which data about the traffic are obtained.
The ISCXVPN2016 dataset consisting of a wide range of application kinds and VPN protocols, therefore, offers a strong foundation for our research. At the same time, it is necessary to add to this dataset with new information in order to maintain the relevance of our analysis, also due to the quick evolution of network traffic patterns and the appearance of new applications.
The custom VPN traffic data were captured using various VPN protocols including WireGuard. OpenVPN, and SoftEther in order to ensure that our dataset is representative of real-world VPN traffic scenarios. We covered more VPN protocols by adding custom data not protected by the ISCXVPN2016 dataset, which allowed us to evaluate the efficacy of our models.
In order to ensure that our models can categorize traffic from the most recent applications, we included the data from newer applications that were absent from the ISCXVPN2016 dataset. Adding custom data improved the robustness of our models, enhanced the diversity of our dataset, and their ability to generalize to unseen data. We labeled it with the corresponding application types after capturing the custom VPN traffic data. The ISCXVPN2016 dataset and these data were then integrated to produce a comprehensive dataset for training and assessing our CNN and GNN models.
3.2. Data Preprocessing
The CNN model requires input in the form of pictures, whereas the GNN model works with graph-structured data, and hence, the data preprocessing steps for the two models are different. We describe the updated data preprocessing methods in this section, emphasizing the usage of nPrint to turn network traffic data into images for the CNN model. In order to create organized data, we first parsed the unstructured PCAP or flow records from the combined dataset (ISCXVPN2016 and custom VPN traffic data). Python is used along with Wireshark and Scapy to complete this.
We need to remove extraneous information that could not be helpful for the classification process before turning the structured data into photos. This entails eliminating unnecessary background traffic and only keeping application-specific traffic that is pertinent.
To input the network traffic data into a CNN, we will convert the filtered structured data into images using nPrint, a network traffic fingerprinting tool. nPrint captures packet-level information and represents it as a one-dimensional binary string, capturing the presence or absence of specific features in each packet. These binary strings can then be converted into two-dimensional images, which can be fed as input into the CNN model. The 2D grayscale images are forwarded to the CNN as an input where it is passed through multiple layers of the CNN, where early layers in the CNN typically capture low-level features, while deeper layers capture higher-level, more abstract features such as specific traffic patterns or behaviors. The learned features are automatically determined by the CNN during the training process. Based on specific VPN protocols or applications, we associated each image with the appropriate label based on the application type, using the metadata provided with the dataset(depicted c.f Figure 3).
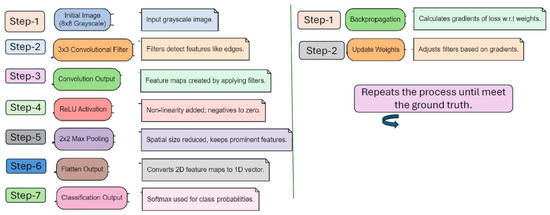
Figure 3.
A complete process of CNN while training the dataset and finally the prediction.
Since the features in the images may have different scales, we have normalized the data to ensure that all features have equal importance during the model training process. This was achieved using min-max scaling and standardization techniques. In addition, to ensure that all classes are equally represented in training, validation, and testing sets, we split the data into separate training and validation sets as well as a testing set in order to evaluate the model’s performance on unseen data and prevent overfitting.
For the data preprocessing of the GNN model, T-Shark and batch scripting were used to convert PCAPs into csv files where we extracted 70 features. These data were then represented as graphs, where nodes represented network entities source and destination port numbers, and edges represented relationships between these entities such as communication links. We created the train and test split for the GNN in the same way as for CNN which is 80% for training and 20% for testing.
3.3. Algorithms Used
3.3.1. Convolutional Neural Networks (CNNs)
The CNN algorithm is a type of deep learning algorithm that takes advantage of the hierarchical nature of the data to build more complex patterns from simpler and smaller patterns that are previously compiled into a single pattern [32]. It is therefore possible for them to take in an image as input and assign importance based on learnable weights and biased to different aspects within that image in order to differentiate between them. In comparison to other classification algorithms, a CNN requires a much smaller amount of pre-processing than those used in other algorithms. Compared to primitive methods in which filters are hand-engineered, CNNs can learn these filters and characteristics with enough training, as opposed to primitive methods where filters are hand-engineered.
In terms of its architecture, CNNs have been inspired by the organization of neurons in the human brain, which is analogous to the connectivity pattern of neurons in the human brain. The receptive fields of these artificial networks are made up of layers of artificial neurons called nodes, which are responsible for processing small portions of the input image. The idea of using smaller, local receptive fields leads to the concept of local receptive fields and two key properties of CNNs, which are sparse connectivity, or sparse weights, and Shared weights. This CNN training process can be represented by the following equation:
where Y represents the actual label, is the predicted label, and N denotes the number of observations.
The goal is to minimize the loss function using optimization algorithms like stochastic gradient descent or Adam optimizer. The process is iteratively repeated until the model’s predictions closely match the actual values, thereby minimizing the loss function [18].
3.3.2. Graph Neural Networks (GNN)
In the context of machine learning, Graph Neural Networks (GNNs) are a powerful tool to extract features from a graph by iteratively aggregating the features that are shared by neighboring nodes in the graph. The neighborhood aggregation method used by GNNs continuously aggregates a node’s neighbors in the network based on their features [19]. More formally, the feature vector of node i in the l-th layer.
is computed as follows:
where
- is the neighborhood of node i;
- is the adjacency matrix;
- D is the degree matrix;
- at the l-th layer is the weight matrix;
- is the node j feature vector at the layer;
- refers to the activation function.
While the feature vectors are steadily updated, the weights are learned during training by gradient descent, backpropagation, or other optimization techniques like Adam. Each layer of the GNN undergoes the same procedures many times. This method enables GNNs to simultaneously capture the node attributes and graph structure, which is especially advantageous for tasks involving graph classification, node classification, and link prediction.
4. Implementation
The provided Python code illustrates a streamlined approach for retrieving VPN forensics data from a blockchain (specifically Hyperledger Fabric) and analyzing it using a Convolutional Neural Network (CNN) (Listing 2).
In selecting Hyperledger Fabric for our blockchain-based VPN traffic classification and forensic analysis framework, we were guided by its distinctive advantages that align closely with our needs. Hyperledger Fabric’s modular architecture enables tailored blockchain solutions, crucial for integrating sophisticated forensic tools effectively. Its support for private channels and data collections ensures the privacy and confidentiality necessary for handling sensitive VPN data. The platform’s high performance and scalability are essential for managing the substantial data volumes in forensic applications, while its permissioned nature allows precise control over network access, enhancing data integrity and security. Additionally, Fabric’s support for chaincodes in various programming languages facilitates the direct implementation of complex analysis algorithms. Rich query capabilities and customizable endorsement policies further empower our forensic analysis, ensuring our platform not only meets the high computational demands but also adheres to rigorous security and privacy standards critical in legal and forensic contexts.
| Listing 2. Python code for CNN model. |
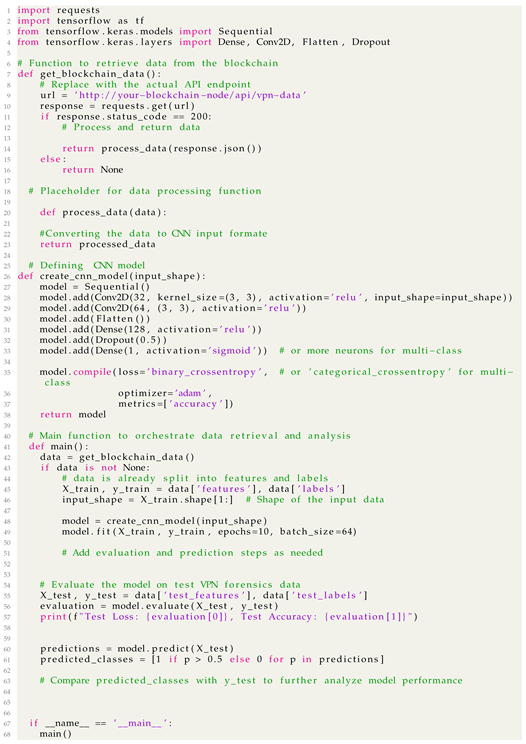 |
Data Retrieval from Blockchain: The function ‘get_blockchain_data’ is responsible for fetching VPN forensics data from the blockchain. It uses the ‘requests’ library to make an HTTP GET request to a specified API endpoint. This endpoint connects to a Hyperledger Fabric node which hosts the VPN data. If the request is successful (status code 200), the data are received in JSON format and then passed to the ‘process_data’ function for processing.
Data Processing: The ‘process_data’ function, currently a placeholder, is intended to convert the raw blockchain data into a format suitable for CNN analysis. This step is crucial as it involves transforming the data into a format that the CNN can efficiently process, such as normalizing values, reshaping arrays, or extracting relevant features.
CNN Model Definition: The ‘create_cnn_model’ function sets up the CNN model for data analysis. The model consists of convolutional layers (‘Conv2D’) for feature extraction, followed by a flattening layer (‘Flatten’) and dense layers (‘Dense’) for classification. A dropout layer (‘Dropout’) is also included to reduce overfitting. The model is compiled with a loss function and optimizer suitable for binary or multi-class classification.
Model Training and Analysis: In the ‘main’ function, the VPN data are retrieved and processed. The CNN model is then instantiated with the appropriate input shape and trained on the prepared data (‘X_train’, ‘y_train’). This training process involves the model learning to classify or predict outcomes based on the VPN forensics data.
Utilizing a Convolutional Neural Network (CNN) for VPN forensics data analysis can yield a diverse range of classifications, pivotal for cybersecurity insights. This advanced analysis can differentiate between normal and anomalous VPN traffic patterns, detect irregularities in user behavior, and identify potential security breaches, such as unauthorized access or data exfiltration. The CNN’s ability to discern geolocation anomalies and scrutinize protocol usage further aids in pinpointing non-compliant or risky activities. These results are essential in forensic investigations, providing critical information to guide response strategies, enforce security policies, and, when necessary, offer robust evidence in legal contexts. The conclusions drawn from the CNN’s classifications thus play a crucial role in understanding the nature and severity of incidents involving VPN usage, ultimately strengthening organizational cybersecurity measures.
For a comprehensive understanding of the implementation details and to access the full source code of our system, please refer to our GitHub repository. The repository includes all necessary components such as the Hyperledger Fabric chaincode, the application layer for interacting with the blockchain, the Convolutional Neural Network models, and configuration settings for setting up and running the system. Detailed documentation is also provided to guide users through the installation process and to assist in deploying and testing the system. The full source code is available at https://github.com/toqeer/vpn-code.git (accessed on 29 April 2024).
5. Results and Analysis
To evaluate the efficiency and predictive potential of our trained models, it is crucial to employ certain performance metrics, forming a fundamental part of the machine learning pipeline. In our research, we have utilized three key metrics, namely, accuracy, recall, and F1-score, which collectively provide a robust assessment of our models’ performance. It is important to note that the term ‘accuracy’ refers to the ratio in which correct predictions per sample are over the total number of samples. It gives us a general understanding of the effectiveness of our model. However, it does not distinguish between the numbers of correctly classified examples of different classes, which might be crucial when the classes are imbalanced. Hence, to further evaluate the performance, we also employ recall and F1-score, which consider both the precision and sensitivity of the model.
Accuracy: In the process of data splitting, we strategically reserved 20% of our total dataset as a test set. This untouched portion of the data serves to test the predictive ability of our models, ensuring that we evaluate their performance on unseen data.
Let us look at the performance of our two models—CNN and GNN. The trained CNN model was tested against our grayscale image representations of network traffic data to determine its ability to differentiate the VPN traffic from non-VPN traffic generated by specific applications. This test phase resulted in a high accuracy of 95.1%, which indicates that the CNN model correctly classified 95.1% of the cases as depicted in Figure 4. This implies that the CNN model was precise enough to detect the type of traffic in 95.1% of the cases, which shows high proficiency in identifying the traffic type over the network. On the other hand, the Graph Neural Network (GNN) model was put through the same test, only this time it was tasked to analyze graph-structured data. Remarkably, the GNN model was able to identify VPN and non-VPN traffic with 99.2% accuracy. One possible explanation for this perfect score could be the comprehensive representation of network traffic as a graph, enabling the model to take into account the dependencies between different network flows, thus making more accurate predictions.
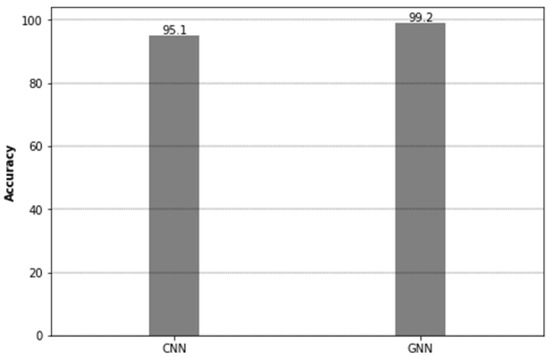
Figure 4.
Accuracy score for CNN and GNN.
F1 score: Machine learning is heavily dependent on the F1 score, which is a metric that is particularly useful when dealing with uneven class distributions as it provides both a precision and recall measure. In machine learning, it is a significant metric. Its worst value is 0%, and its maximum value is 100% (perfect recall and precision). Our trained Convolutional Neural Network (CNN) models in this study distinguished between different classes of network traffic with an F1 score of 95.4%. This score is pretty impressive and demonstrates the model’s strong capability to precisely categorize both VPN and non-VPN traffic associated with multiple applications with a high degree of recall and precision. Our Graph Neural Network (GNN) models performed exceptionally well despite being more complex and requiring considerable training and provided with an F1 score of 99.3% (c.f Figure 5).
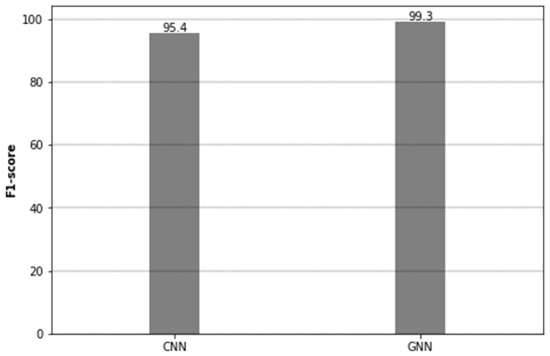
Figure 5.
F1 score for CNN and GNN.
Demonstrating a nearly ideal balance of precision and recall with a great F1 score, GNN was able to discriminate between the various types of VPN and non-VPN traffic connected with various apps; the GNN model achieved better results in this situation than the CNN model as clear from the findings. This could be attributed to the GNN’s central ability to evaluate and maintain complex relationships and dependencies which contributes to the production of higher classification results.
Recall: Analyzing a model’s recall allows one to assess its ability to properly identify positive classes within a dataset that is often referred to as its sensitivity or true positive rate. Recall is the term for this category of the performance metric. In the context of our inquiry, the model’s recall was assessed as a barometer of its ability to correctly differentiate between non-VPN network traffic and VPN network traffic. The recall score for our Convolutional Neural Network (CNN) models was calculated as 95.7%. According to this finding, CNN models were able to accurately classify 96% of non-VPN and VPN traffic related to different applications.In other words, the CNN models were highly efficient in detecting the true positive cases and only missed 4% of the positive classes.
The Graph Neural Network (GNN) models also demonstrated a high recall score which is 99.6% (c.f Figure 6). With its inherent ability to handle complex relationships and dependencies inherent in network traffic, the GNN models were able to efficiently differentiate the diverse classes of VPN and non-VPN traffic linked with various applications. Upon comparison of the recall scores, it is evident that the GNN models surpassed the performance of the CNN models. This suggests that GNN models are better suited for this classification task, providing superior detection rates for true positive cases of VPN and non-VPN traffic related to different applications.
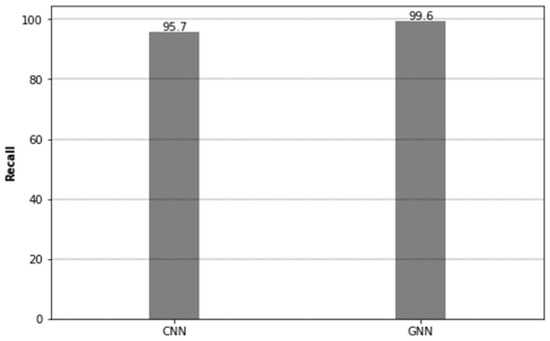
Figure 6.
F1 score for CNN and GNN.
Precision: Machine learning models are also rated in terms of precision, highlighting their capacity to distinguish between occurrences that truly qualify as positive and those that do not, demonstrating their capacity to appropriately select the genuine positive examples from among all those the model labels as positive. As it applies to our research, precision describes the model’s ability to distinguish VPN traffic from non-VPN traffic associated with a number of different types of applications accurately.
Our Convolutional Neural Network (CNN) models demonstrated a precision score of 95.2%. This implies that among all the network traffic instances that the CNN models classified as VPN or non-VPN, 95.2% were indeed correctly classified. Therefore, our CNN models successfully minimized the number of false positives, hence confirming their high precision. Meanwhile, the Graph Neural Network (GNN) models showcased impressive precision in distinguishing between different classes of VPN and non-VPN traffic associated with various applications. The score for GNN was 99.2% (c.f Figure 7). As a result of their ability to capture complex patterns and relationships within a network, GNN models have been able to reduce false positives, thus resulting in increased precision in their prediction of patterns. A comparative analysis of the precision scores reveals that the GNN models outshined the CNN models in our context. The superior precision of the GNN models indicates their enhanced proficiency in accurately identifying VPN and non-VPN traffic types, minimizing the risk of misclassification.
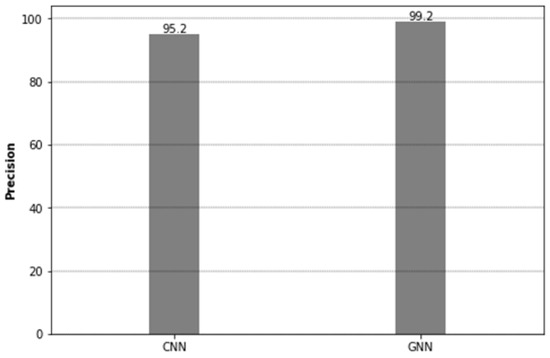
Figure 7.
Precision score for CNN and GNN.
Direct Comparison
To articulate the improvements our approach introduces, we compare our results with those documented in the existing literature, focusing on similar application domains. For instance, while the Convolutional Neural Network (CNN) model demonstrates a high accuracy of 95.1% and an F1 score of 95.4%, it is our Graph Neural Network (GNN) model that marks a significant leap forward, achieving an accuracy of 99.2% and an F1 score of 99.3%. These figures not only surpass those achieved by traditional CNN approaches but also reflect a substantial advancement over results reported in prior studies, where similar metrics rarely breached the 90% threshold.
Moreover, the precision and recall scores of our GNN model, standing at 99.2% and 99.6% respectively, further validate its superior capability in minimizing false positives and accurately identifying VPN and non-VPN traffic, a critical consideration for effective network management and security. This performance contrasts sharply with the existing methods, where the balance between precision and recall often proves challenging, particularly in datasets with complex and nuanced patterns of network traffic.
6. Conclusions
This research introduces a unique method of VPN traffic classification in a forensic setting using Graph Neural Networks (GNNs) and Convolutional Neural Networks (CNNs). Our approach using the strengths of both CNNs and GNNs give a complete solution for VPN traffic classification, allowing forensic investigators to distinguish between VPN and non-VPN traffic pertaining to a particular application. According to our findings, the proposed method can predict VPN traffic with 99.2% accuracy when using GNN models and 95.1% accuracy when using CNN models, both of which are highly accurate when it comes to identifying VPN traffic. These findings imply that by lowering false positives and boosting the dependability of forensic analysis, our approach can greatly increase the accuracy of VPN traffic classification.
Additionally, our method links VPN traffic to its original source in addition to just identifying it. We also suggest identifying the application whose traffic is forwarded via VPN connections, as this may reveal vital information within an organization about any harmful behavior or rule violations. The outcomes so far have been encouraging, but there are still a number of difficult problems that will need to be resolved in the future. These include issues with privacy while processing network traffic data and the dynamic nature of VPN traffic. The use of advanced machine learning techniques, such as CNNs and GNNs, is especially significant since it comes with a number of challenges, including the need for a sizable data collection and the computationally costly nature of deep learning models. As far as a future direction is concerned, the future researchers should include creating more effective CNN and GNN architectures that could handle the difficulties unique to VPN classification, investigating transfer learning strategies to make use of previously trained models, and looking into ways to combine various deep learning model types to enhance classification performance.
By offering a useful way for categorizing VPN data and assisting forensic analysts in their analysis, our work generally makes a contribution to the field of VPN traffic classification in a forensic context. We finally believe that our method can be a useful tool for security experts and forensic analysts in their work to examine VPN traffic and find potential threats.
Author Contributions
Conceptualization, T.A.S. and S.S.A.; methodology, T.A.S.; software, S.S.A.; formal analysis, T.A.S.; investigation, T.A.S.; resources, S.S.A.; data curation, S.S.A.; writing—original draft preparation, T.A.S.; writing—review and editing, S.S.A. and T.A.S.; visualization, T.A.S.; supervision, S.S.A.; project administration, S.S.A.; funding acquisition, S.S.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The original contributions presented in the study are included in the article, further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Ndichu, S.; McOyowo, S.; Okoyo, H.; Wekesa, C. A remote access security model based on vulnerability management. Int. J. Inf. Technol. Comput. Sci. 2020, 5, 38–51. [Google Scholar] [CrossRef]
- Rana, M.U.; Ellahi, O.; Alam, M.; Webber, J.L.; Mehbodniya, A.; Khan, S. Offensive Security: Cyber Threat Intelligence Enrichment With Counterintelligence and Counterattack. IEEE Access 2022, 10, 108760–108774. [Google Scholar] [CrossRef]
- Islam, F.U.; Liu, G.; Zhai, J.; Liu, W. VoIP traffic detection in tunneled and anonymous networks using deep learning. IEEE Access 2021, 9, 59783–59799. [Google Scholar] [CrossRef]
- Dimitriadis, A.; Ivezic, N.; Kulvatunyou, B.; Mavridis, I. D4I-Digital forensics framework for reviewing and investigating cyber attacks. Array 2020, 5, 100015. [Google Scholar] [CrossRef] [PubMed]
- Amato, F.; Castiglione, A.; Cozzolino, G.; Narducci, F. A semantic-based methodology for digital forensics analysis. J. Parallel Distrib. Comput. 2020, 138, 172–177. [Google Scholar] [CrossRef]
- Bagui, S.; Fang, X.; Kalaimannan, E.; Bagui, S.C.; Sheehan, J. Comparison of machine-learning algorithms for classification of VPN network traffic flow using time-related features. J. Cyber Secur. Technol. 2017, 1, 108–126. [Google Scholar] [CrossRef]
- Naas, M.; Fesl, J. A novel dataset for encrypted virtual private network traffic analysis. Data Brief 2023, 47, 108945. [Google Scholar] [CrossRef]
- Miller, S.; Curran, K.; Lunney, T. Detection of virtual private network traffic using machine learning. Int. J. Wirel. Netw. Broadband Technol. (IJWNBT) 2020, 9, 60–80. [Google Scholar] [CrossRef]
- Al-Fayoumi, M.; Al-Fawa’reh, M.; Nashwan, S. VPN and Non-VPN Network Traffic Classification Using Time-Related Features. Comput. Mater. Contin. 2022, 72, 3091–3111. [Google Scholar] [CrossRef]
- Casino, F.; Dasaklis, T.K.; Spathoulas, G.P.; Anagnostopoulos, M.; Ghosal, A.; Borocz, I.; Solanas, A.; Conti, M.; Patsakis, C. Research trends, challenges, and emerging topics in digital forensics: A review of reviews. IEEE Access 2022, 10, 25464–25493. [Google Scholar] [CrossRef]
- Tully, G.; Cohen, N.; Compton, D.; Davies, G.; Isbell, R.; Watson, T. Quality standards for digital forensics: Learning from experience in England & Wales. Forensic Sci. Int. Digit. Investig. 2020, 32, 200905. [Google Scholar]
- Al-Dhaqm, A.; Ikuesan, R.A.; Kebande, V.R.; Abd Razak, S.; Grispos, G.; Choo, K.K.R.; Al-Rimy, B.A.S.; Alsewari, A.A. Digital forensics subdomains: The state of the art and future directions. IEEE Access 2021, 9, 152476–152502. [Google Scholar] [CrossRef]
- Ali, T.; Khan, Y.; Ali, T.; Faizullah, S.; Alghamdi, T.; Anwar, S. An automated permission selection framework for android platform. J. Grid Comput. 2020, 18, 547–561. [Google Scholar] [CrossRef]
- Business, F. The Compound Annual Growth Rate. 2024. Available online: https://www.marketsandmarkets.com/Market-Reports/blockchain-technology-market-90100890.html (accessed on 25 January 2024).
- Bhutta, M.N.M.; Khwaja, A.A.; Nadeem, A.; Ahmad, H.F.; Khan, M.K.; Hanif, M.A.; Song, H.; Alshamari, M.; Cao, Y. A survey on blockchain technology: Evolution, architecture and security. IEEE Access 2021, 9, 61048–61073. [Google Scholar] [CrossRef]
- Guo, H.; Yu, X. A survey on blockchain technology and its security. Blockchain Res. Appl. 2022, 3, 100067. [Google Scholar] [CrossRef]
- Butt, G.Q.; Sayed, T.A.; Riaz, R.; Rizvi, S.S.; Paul, A. Secure healthcare record sharing mechanism with blockchain. Appl. Sci. 2022, 12, 2307. [Google Scholar] [CrossRef]
- Ali, T. Z notation formalization of blockchain healthcare document sharing based on crbac. J. Inf. Commun. Technol. Robot. Appl. 2018, 9, 16–29. [Google Scholar]
- Abutaleb, R.A.; Alqahtany, S.S.; Syed, T.A. Integrity and Privacy-Aware, Patient-Centric Health Record Access Control Framework Using a Blockchain. Appl. Sci. 2023, 13, 1028. [Google Scholar] [CrossRef]
- Abdeen, M.A.; Ali, T.; Khan, Y.; Yagoub, M. Fusing identity management, HL7 and Blockchain into a global healthcare record sharing architecture. Int. J. Adv. Comput. Sci. Appl. 2019, 10. [Google Scholar] [CrossRef]
- Syed, T.A.; Siddique, M.S.; Nadeem, A.; Alzahrani, A.; Jan, S.; Khattak, M.A.K. A novel blockchain-based framework for vehicle life cycle tracking: An end-to-end solution. IEEE Access 2020, 8, 111042–111063. [Google Scholar] [CrossRef]
- Ali, T.; Nadeem, A.; Alzahrani, A.; Jan, S. A transparent and trusted property registration system on permissioned blockchain. In Proceedings of the 2019 International Conference on Advances in the Emerging Computing Technologies (AECT), Al Madinah Al Munawwarah, Saudi Arabia, 10 February 2020; pp. 1–6. [Google Scholar]
- Syed, T.A.; Jan, S.; Siddiqui, M.S.; Alzahrani, A.; Nadeem, A.; Ali, A.; Ullah, A. CAR-tourist: An integrity-preserved collaborative augmented reality framework-tourism as a use-case. Appl. Sci. 2022, 12, 12022. [Google Scholar] [CrossRef]
- Syed, T.A.; Siddiqui, M.S.; Abdullah, H.B.; Jan, S.; Namoun, A.; Alzahrani, A.; Nadeem, A.; Alkhodre, A.B. In-depth review of augmented reality: Tracking technologies, development tools, AR displays, collaborative AR, and security concerns. Sensors 2022, 23, 146. [Google Scholar] [CrossRef]
- Syed, T.A.; Jan, S.; Siddique, S.; Alzahrani, A.; Ullah, S.A.; Nadeem, A. Secure and Collaborative Augmented Reality Tourism and Economy Perspective. Int. J. Energy Environ. Econ. 2021, 29, 179–197. [Google Scholar]
- Jan, S.; Musa, S.; Ali, T.; Nauman, M.; Anwar, S.; Ali Tanveer, T.; Shah, B. Integrity verification and behavioral classification of a large dataset applications pertaining smart OS via blockchain and generative models. Expert Syst. 2021, 38, e12611. [Google Scholar] [CrossRef]
- Jan, S.; Ali, T.; Alzahrani, A.; Musa, S. Deep convolutional generative adversarial networks for intent-based dynamic behavior capture. Int. J. Eng. Technol. 2018, 7, 101–103. [Google Scholar]
- Li, Y.; Xiao, X.; Zhang, Z.; Chen, Z. Research and analysis on hierarchical management balancing strategy of intelligent VPN in colleges and universities under hierarchical protection 2.0 background. In Proceedings of the Third International Conference on Computer Science and Communication Technology (ICCSCT 2022), Beijing, China, 30–31 July 2022; Volume 12506, pp. 1189–1193. [Google Scholar]
- Okonkwo, Z.; Foo, E.; Li, Q.; Hou, Z. A CNN based encrypted network traffic classifier. In Proceedings of the 2022 Australasian Computer Science Week, Brisbane, Australia, 14–18 February 2022; pp. 74–83. [Google Scholar]
- Hu, X.; Gu, C.; Wei, F. CLD-Net: A network combining CNN and LSTM for internet encrypted traffic classification. Secur. Commun. Netw. 2021, 2021, 5518460. [Google Scholar] [CrossRef]
- Shamsimukhametov, D.; Liubogoshchev, M.; Khorov, E.; Akyldiz, I. Are neural networks the best way for encrypted traffic classification? In Proceedings of the 2021 International Conference Engineering and Telecommunication (En&T), Online, 24–25 November 2021; pp. 1–5. [Google Scholar]
- Zhang, C.; Bengio, S.; Hardt, M.; Recht, B.; Vinyals, O. Understanding deep learning (still) requires rethinking generalization. Commun. ACM 2021, 64, 107–115. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).