Secure Monitoring System for IoT Healthcare Data in the Cloud
Abstract
:1. Introduction
- The proposed system integrates the benefits of IoT with the computational power of cloud computing through a wireless network.
- The proposed model immediately detects, predicts, and notifies the responsible surveillance personnel.
- The proposed model could be established in public service buildings, such as hospitals.
- The proposed system has a high transmission data rate based on its operation over a wireless network and additionally aims to have more direct notifications due to the IoT data produced by mobile devices.
2. Related Work
3. Limitations and Barriers of Conventional Medical Methods
Limitations Could Be Addressed by IoT
4. Technological Challenges in Microbiology
Technological Challenges in Microbiology Addressed by IoT
5. Proposed System
5.1. Involved Technologies
5.1.1. Internet of Things (IoT)
- Data collection and monitoring: IoT devices in the healthcare industry are able to continuously collect patient health information, including vital signs like heart rate, blood pressure, temperature, and glucose levels. These gadgets send the information to the cloud for centralized storage and supervision.
- Real-time data streaming: Real-time data streaming is frequently provided by IoT devices, allowing healthcare providers and medical experts to view and track patients’ health conditions remotely. For the purpose of identifying anomalies and making any necessary interventions in a timely manner, real-time monitoring is essential.
- Cloud-based data storage: To securely store the collected data, IoT healthcare devices often rely on cloud-based storage options. In order to ensure that patient health data is available from any location while protecting data integrity and confidentiality, cloud storage enables scalable and cost-effective data management.
- Secure data transmission: It is critical to use secure communication protocols (like SSL/TLS) to encrypt data when it is being transported from IoT devices to the cloud. This guarantees data confidentiality and avoids illegal interception.
- Authentication and access control: Strong authentication procedures are needed for a secure monitoring system for IoT healthcare data in order to confirm the legitimacy of users accessing the cloud system. Based on the user’s role and rights, Role-Based Access Control (RBAC) can be used to limit data access.
- Data encryption and decryption: Using encryption methods, such as the previously described Fernet encryption, guarantees that private medical information is encrypted before being saved in the cloud. Only authorized users are permitted to decrypt files, protecting the secrecy of the data.
- Monitoring and anomaly detection: IoT devices and cloud systems can be fitted with monitoring and anomaly detection methods to detect any strange patterns or potential security breaches in real time. As a result, the system can better react quickly to security problems.
- Regulatory compliance: Cloud-based IoT healthcare systems must abide by all applicable rules, including the GDPR, HIPAA, and other data protection legislation. Compliance guarantees patient confidentiality and the safe handling of medical data.
- Data backup and redundancy: In order to guarantee data accessibility and disaster recovery in the event of hardware breakdowns or system outages, cloud-based IoT systems can make use of the redundancy and backup options offered by the cloud provider.
5.1.2. Wireless Sensor Networks (WSN)
5.1.3. Cloud Computing (CC)
5.1.4. Machine Learning (ML)
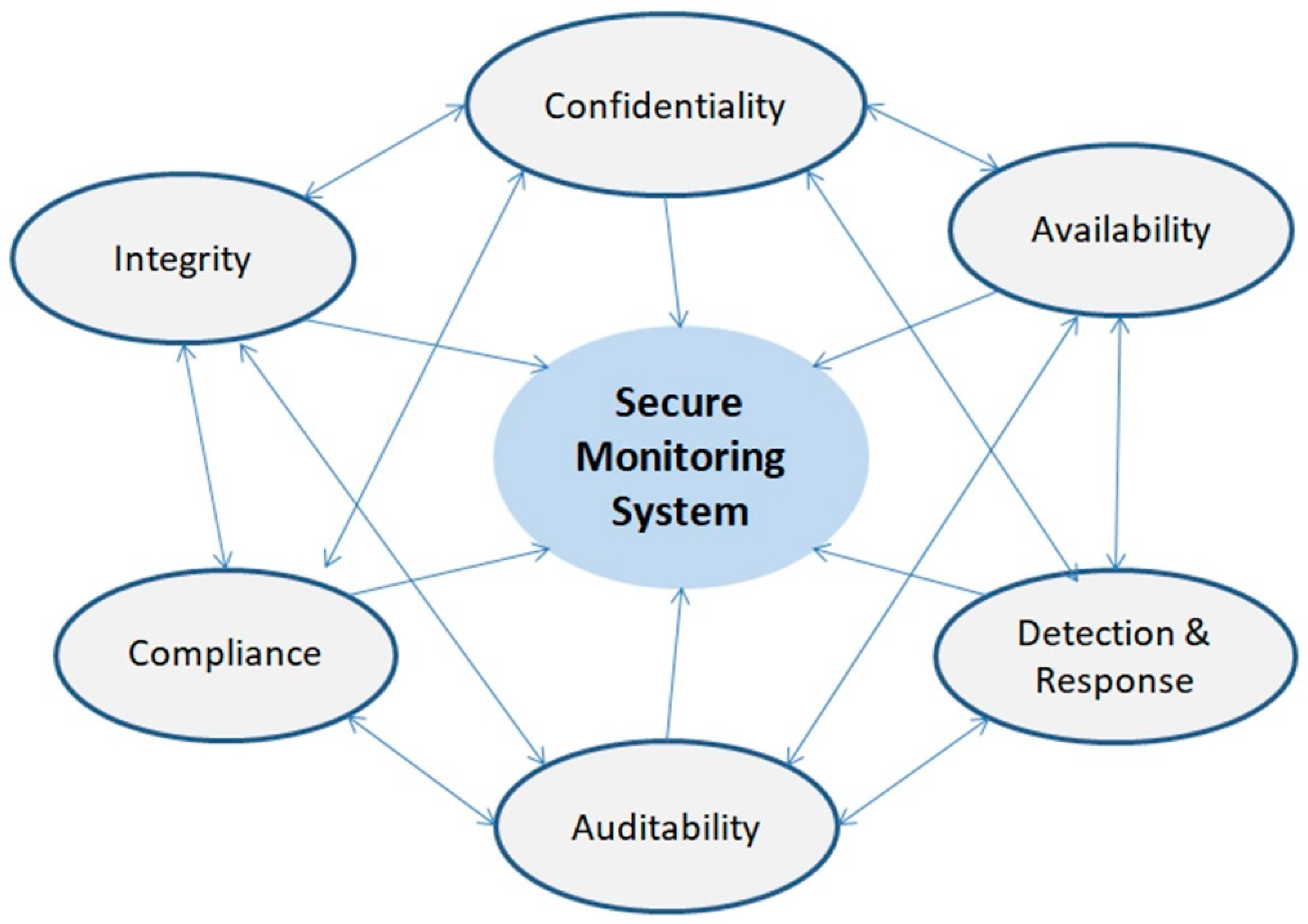
5.2. System’s Primary Goals
- Confidentiality: Protect the privacy and confidentiality of sensitive healthcare data, preventing unauthorized access or disclosure.
- Integrity: Ensure the accuracy, consistency, and reliability of healthcare data by preventing unauthorized modification or tampering.
- Availability: Maintain high availability of healthcare data and systems, minimizing downtime and ensuring that authorized users can access the data when needed.
- Compliance: Meet the legal and regulatory requirements for protecting healthcare data, such as HIPAA, GDPR, or any other applicable regulations.
- Detection and response: Detect and respond to security incidents, anomalies, or breaches in a timely manner to minimize the impact on patient safety and data security.
- Auditability: Enable comprehensive logging and auditing capabilities to track and monitor user activities, system events, and data access for forensic analysis and compliance purposes.
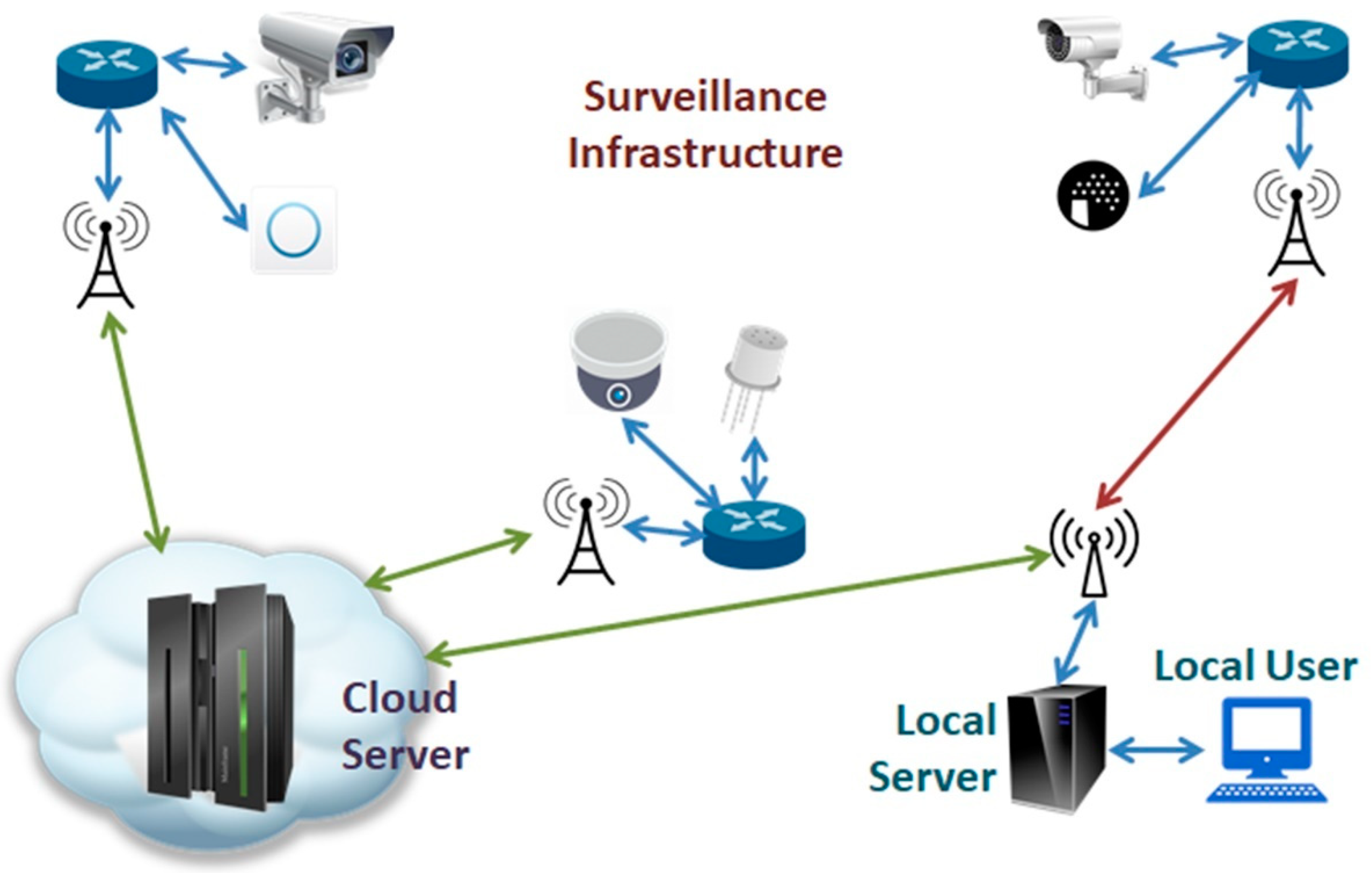
5.3. System Architecture
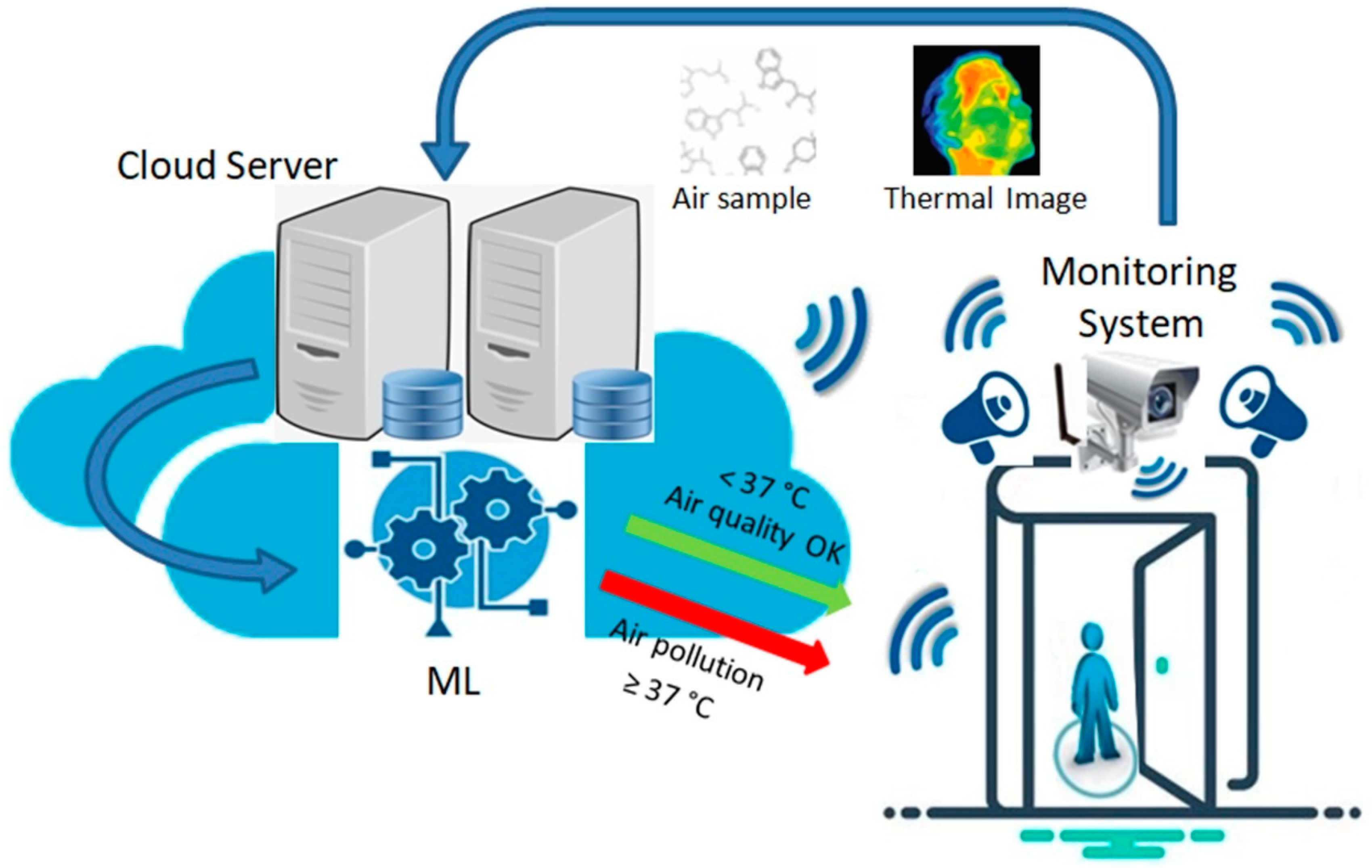
5.4. System’s Algorithm Approach
| Algorithm 1. Secure IoT Healthcare Data in Cloud |
| import ssl import hashlib import socket import cryptography from cryptography.fernet import Fernet # Example IoT device data iot_data = { “patient_id”: “123456”, “heart_rate”: 75, “temperature”: 37.2 } # Generate encryption key encryption_key = Fernet.generate_key() cipher_suite = Fernet(encryption_key) # Encrypt IoT data encrypted_data = cipher_suite.encrypt(str(iot_data).encode()) # Secure communication with SSL/TLS context = ssl.create_default_context(ssl.Purpose.related-client) context.check_hostname = False context.verify_mode = ssl.CERT_NONE # Connect to cloud server securely cloud_server = “cloud server’s host” cloud_port = 443 cloud_socket = context.wrap_socket(socket.socket(socket.AF_INET), server_hostname=cloud_server) cloud_socket.connect((cloud_server, cloud_port)) # Send encrypted data to the cloud server cloud_socket.sendall(encrypted_data) # Receive response from cloud server response = cloud_socket.recv(1024) # Decrypt and validate the response decrypted_response = cipher_suite.decrypt(response) if hashlib.md5(response).hexdigest() == hashlib.md5(decrypted_response).hexdigest(): print(“Response integrity verified: “, decrypted_response) else: print(“Response tampering detected!”) # Close the connection cloud_socket.close() |
6. Application Fields
IoT in Healthcare Application Fields
7. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Oniani, S.; Marques, G.; Barnovi, S.; Pires, I.M.; Bhoi, A.K. Artificial Intelligence for Internet of Things and Enhanced Medical Systems. In Bio-Inspired Neurocomputing. Studies in Computational Intelligence; Springer: Singapore, 2020; Volume 903, pp. 43–59. [Google Scholar] [CrossRef]
- Stergiou, C.L.; Psannis, K.E.; Gupta, B.B. InFeMo: Flexible Big Data Management Through a Federated Cloud System. ACM Trans. Internet Technol. 2022, 22, 46. [Google Scholar] [CrossRef]
- Bai, L.; Yang, D.; Wang, X.; Tong, L.; Zhu, X.; Zhong, N.; Bai, C.; Powell, C.A.; Chen, R.; Zhou, J.; et al. Chinese experts’ consensus on the Internet of Things-aided diagnosis and treatment of coronavirus disease 2019. Clin. Ehealth 2020, 3, 7–15. [Google Scholar] [CrossRef]
- Maghdid, H.S.; Ghafoor, K.Z.; Sadiq, A.S.; Curran, K.; Rawt, D.B.; Rabie, K. A Novel AI-enabled Framework to Diagnose Coronavirus COVID 19 using Smartphone Embedded Sensors: Design Study. In Proceedings of the 2020 IEEE 21st International Conference on Information Reuse and Integration for Data Science (IRI), Las Vegas, NV, USA, 11–13 August 2020; Volume 1, pp. 180–187. [Google Scholar] [CrossRef]
- Muthukumar, S.; Mary, W.S.; Rajkumar, R.; Dhina, R.; Gayathri, J.; Mathivadhani, A. Smart Humidity Monitoring System for Infectious Disease Control. In Proceedings of the 2019 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, Tamil Nadu, India, 23–25 January 2019; pp. 127–132. [Google Scholar] [CrossRef]
- Quy, V.K.; Chehri, A.; Quy, N.M.; Han, N.D.; Ban, N.T. Innovative Trends in the 6G Era: A Comprehensive Survey of Architecture, Applications, Technologies, and Challenges. IEEE Access 2023, 11, 39824–39844. [Google Scholar] [CrossRef]
- Quy, V.K.; Hau, N.V.; Anh, D.V.; Ngoc, L.A. Smart healthcare IoT applications based on fog computing: Architecture, applications and challenges. Complex Intell. Syst. 2021, 8, 3805–3815. [Google Scholar] [CrossRef]
- George, K.; Michaels, A.J. Designing a Block Cipher in Galois Extension Fields for IoT Security. IoT 2021, 2, 669–687. [Google Scholar] [CrossRef]
- Shreya, S.; Chatterjee, K.; Singh, A. A smart secure healthcare monitoring system with Internet of Medical Things. Comput. Electr. Eng. 2022, 101, 107969. [Google Scholar] [CrossRef]
- Butpheng, C.; Yeh, K.-H.; Hou, J.-L. A Secure IoT and Cloud Computing-Enabled e-Health Management System. Secur. Commun. Netw. 2022, 2022, 300253. [Google Scholar] [CrossRef]
- Tang, Z. A Preliminary Study on Data Security Technology in Big Data Cloud Computing Environment. In Proceedings of the International Conference on Big Data & Artificial Intelligence & Software Engineering (ICBASE), Bangkok, Thailand, 30 October–1 November 2020. [Google Scholar] [CrossRef]
- Ogiela, L.; Castiglione, A.; Gupta, B.B.; Agrawal, D.P. IoT-based health monitoring system to handle pandemic diseases using estimated computing. Neural Comput. Appl. 2023, 35, 13709–13710. [Google Scholar] [CrossRef] [PubMed]
- Butpheng, C.; Yeh, K.-H.; Xiong, H. Security and Privacy in IoT-Cloud-Based e-Health Systems—A Comprehensive Review. Symmetry 2020, 12, 1191. [Google Scholar] [CrossRef]
- Stergiou, C.; Plageras, A.P.; Psannis, K.E.; Gupta, B.B. Secure Machine Learning scenario from Big Data in Cloud Computing via Internet of Things network. In Handbook of Computer Networks and Cyber Security: Principles and Paradigms, Multimedia Systems and Applications; Springer: Cham, Switzerland, 2020; pp. 525–554. [Google Scholar] [CrossRef]
- Tsiknas, K.; Taketzis, D.; Demertzis, K.; Skianis, C. Cyber Threats to Industrial IoT: A Survey on Attacks and Countermeasures. IoT 2021, 2, 163–186. [Google Scholar] [CrossRef]
- Plageras, A.P.; Stergiou, C.; Psannis, K.E.; Kokkonis, G.; Ishibashi, Y.; Kim, B.-G.; Gupta, B. Efficient Large-Scale Medical Data (eHealth Big Data) Analytics in Internet of Things. In Proceedings of the 19th IEEE International Conference on Business Informatics (CBI’17), International Workshop on the Internet of Things and Smart Services (ITSS2017), Thessaloniki, Greece, 24–26 July 2017. [Google Scholar] [CrossRef]
- Stergiou, C.; Psannis, K.E.; Kim, B.-G.; Gupta, B. Secure integration of IoT and Cloud Computing. Future Gener. Comput. Syst. 2018, 78, 964–975. [Google Scholar] [CrossRef]
- Sahu, S.; Dhote, Y. A study on big data: Issues, challenges and applications. Int. J. Innov. Res. Comput. Commun. Eng. 2016, 4, 10611–10616. [Google Scholar]
- Singh, A.; Chatterjee, K. Edge computing based secure health monitoring framework for electronic healthcare system. Clust. Comput. 2023, 26, 1205–1220. [Google Scholar] [CrossRef] [PubMed]
- Rao, A.S.S.; Vazquez, J.A. Identification of COVID-19 can be Quicker through Artificial Intelligence Framework using a Mobile Phone-Based Survey in the Populations when Cities/Towns are Under Quarantine. Infect. Control Hosp. Epidemiol. 2020, 41, 820–830. [Google Scholar] [CrossRef]
- Wang, Y.; Hu, M.; Li, Q.; Zhang, X.; Zhai, G.; Yao, N. Abnormal respiratory patterns classifier may contribute to large-scale screening of people infected with COVID-19 in an accurate and unobtrusive manner. arXiv 2020, arXiv:2002.05534. [Google Scholar]
- Shi, F.; Wang, J.; Shi, J.; Wu, Z.; Wang, Q.; Tang, Z.; He, K.; Shi, Y.; Shen, D. Review of Artificial Intelligence Techniques in Imaging Data Acquisition, Segmentation and Diagnosis for COVID-19. EEE Rev. Biomed. Eng. 2021, 14, 4–15. [Google Scholar] [CrossRef] [PubMed]
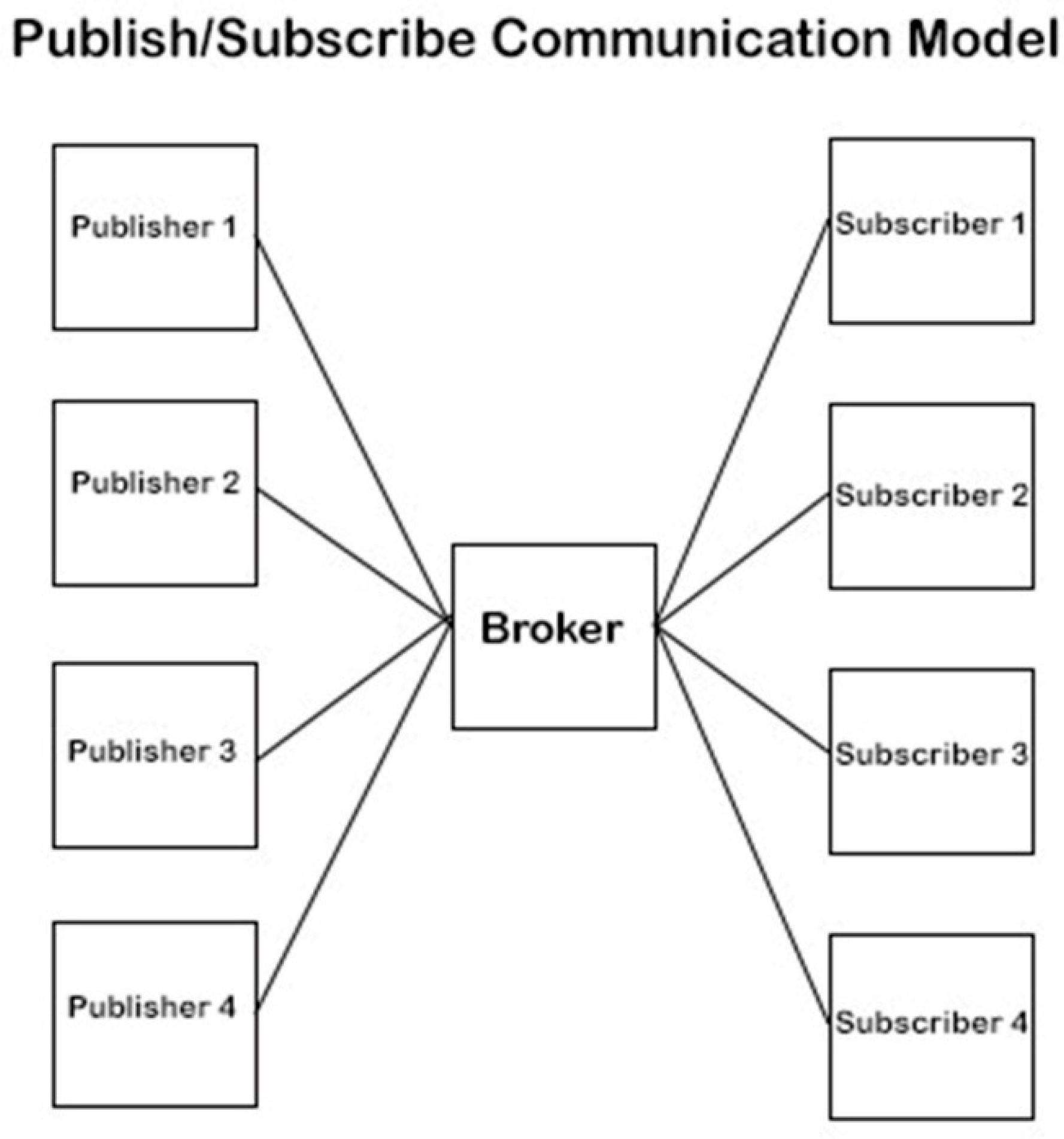
- Wang, H.; Xiong, D.; Wang, P.; Liu, Y. A Lightweight XMPP Publish/Subscribe Scheme for Resource-Constrained IoT Devices. IEEE Access 2017, 5, 16393–16405. [Google Scholar] [CrossRef]
| Research Work | Integrated Technologies | Framework System | Detection | Network-Based | Security | Privacy | Real-Time Data Management |
|---|---|---|---|---|---|---|---|
| [3] | Cloud, Internet of Things, wireless network | nCapp | COVID-19 diagnosis | Yes | N/A | N/A | Yes |
| [4] | Smartphones, AI, cameras, microphones, multiple sensors, Internet of Things, WSNs | Smartphone-based | COVID-19 detection | Yes | Yes | Yes | Yes |
| [5] | ATMEGA328, ESP8266-12F, mobile app, humidity, and temperature sensors | AC/Humidifier IoT Module | Infectious disease control | Yes | N/A | N/A | Yes |
| [7] | Cloud computing, edge computing, fog computing, Internet of Health Things | Based on fog computing for Internet of Health Things (Fog-IoHT) applications | N/A | Yes | N/A | N/A | Yes |
| Proposal | Cloud computing, machine learning, AI, IoT | Secure IoT-based Monitoring System | COVID-19 detection, fever detection, diagnosis of other infectious diseases, indication of air pollution level in rooms | Yes | Yes | Yes | Yes |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Stergiou, C.L.; Plageras, A.P.; Memos, V.A.; Koidou, M.P.; Psannis, K.E. Secure Monitoring System for IoT Healthcare Data in the Cloud. Appl. Sci. 2024, 14, 120. https://doi.org/10.3390/app14010120
Stergiou CL, Plageras AP, Memos VA, Koidou MP, Psannis KE. Secure Monitoring System for IoT Healthcare Data in the Cloud. Applied Sciences. 2024; 14(1):120. https://doi.org/10.3390/app14010120
Chicago/Turabian StyleStergiou, Christos L., Andreas P. Plageras, Vasileios A. Memos, Maria P. Koidou, and Konstantinos E. Psannis. 2024. "Secure Monitoring System for IoT Healthcare Data in the Cloud" Applied Sciences 14, no. 1: 120. https://doi.org/10.3390/app14010120
APA StyleStergiou, C. L., Plageras, A. P., Memos, V. A., Koidou, M. P., & Psannis, K. E. (2024). Secure Monitoring System for IoT Healthcare Data in the Cloud. Applied Sciences, 14(1), 120. https://doi.org/10.3390/app14010120










